AMENDMENT NUMBER TWO TO GOOGLE SERVICES AGREEMENT ORDER FORM
EXHIBIT 10.14.4
CONFIDENTIAL TREATMENT REQUESTED
EXECUTION COPY
AMENDMENT NUMBER TWO TO GOOGLE SERVICES AGREEMENT ORDER FORM
This Amendment Number Two to the Order Form (as defined below) (“Amendment Two”) is entered into
by and between Google Inc. (“Google”), a Delaware corporation and Synacor, Inc., a Delaware
corporation (“Customer”) effective as of December 16, 2005 (the “Amendment Two Effective Date”)
RECITALS
| 1. | Customer and Google entered into that certain Google Services Agreement dated June 25, 2004 (“GSA”) and Google Services Agreement Order Form dated June 22, 2004, as amended (“Order Form” and together with the GSA, the “Agreement”). | ||
| 2. | Under this Amendment Two, Customer wishes to implement client applications. |
NOW, THEREFORE, in consideration of the mutual covenants set forth herein and pursuant to the terms
and conditions of the Agreement, the parties hereby agree as follows:
TERMS
| 1. | The Order Form shall be amended to include the following definition for Client Application: |
“Client Application” means the Synacor, Inc. Toolbar. A “WebSearch Client Application”
and “AFS Client Application” means the Synacor, Inc. Toolbar that has been approved by
Google to access the WebSearch Services and AFS Services, respectively, as approved by
Google in writing from time to time during the Services Term.
| 2. | Customer’s Client Application set forth on Exhibit A, attached hereto is hereby approved by Google for purposes of (a) sending WebSearch Queries and AFS Results Sets to resolve to approved Results Pages on the WebSearch Sites and AdSense for Search Sites, respectively; provided that, at all times during the Services Term, Customer, and Customer’s Client Application(s), will comply with Google’s Client Application Guidelines, the current form of which is attached hereto as Schedule I, as such Guidelines may be updated by Google from time to time. Customer represents and warrants that (a) it has read and understands the Client Application Guidelines; and (b) it does, and at all times during the Services Term it will, own, operate and control one hundred percent (100%) of the approved Client Application(s) set forth in the Cover Page(s) of this Order Form. The list of Approved Client Applications may be updated from time to time subject to Google’s prior written consent. | ||
| 3. | Section 4.1 of the Order Form is hereby amended and restated in its entirety as follows: |
“Section 4.1 Scope of WebSearch Services. If selected on the cover page(s) of
this Order Form, during the Services Term and subject to the terms and conditions of
this Agreement, Google will provide Customer with WebSearch search results (“WebSearch
Results”) through its WebSearch service (the “WebSearch Service”) for display on the
WebSearch Sites as permitted herein. Customer agrees to implement the WebSearch
Service as provided herein on the WebSearch Sites and WebSearch Client Application in
existence as of the date hereof within thirty (30) days of the Order Form Effective
Date, and to maintain such implementation thereafter during the Services Term.
Customer agrees to implement the WebSearch Service on any WebSearch Site and WebSearch
Client Application added thereafter as contemplated by Section 3.3 herein.”
| 1 of 20 |
EXECUTION COPY
| 4. | Section 4.2.1 of the Order Form is hereby amended and restated in its entirety as follows: |
“4.2.1. Search Boxes and Queries. Customer shall implement on each WebSearch
Site and in each WebSearch Client Application a search box (each, a “WebSearch Box”)
for End Users (as defined below) to enter queries to search the Web (each, a “WebSearch
Query”). Customer shall send any and all WebSearch Queries received by Customer from
End Users to Google in accordance with the requirements provided by Google, without
editing, filtering, truncating or otherwise modifying such WebSearch Queries, either
individually or in the aggregate. Customer understands and agrees that WebSearch
Queries sent to Google for processing hereunder may be initiated only by End Users
entering search queries into WebSearch Boxes implemented on a WebSearch Site and
WebSearch Client Application as provided herein, unless otherwise approved by Google in
writing. As used herein, “End Users” of a particular Site or Client Application means
individual, human end users who visit or use the applicable Site or Client Application,
and “Valid WebSearch Queries” means Queries sent to Google in compliance with the
requirements of this Agreement.”
| 5. | Section 7.1 of the Order Form is hereby amended and restated in its entirety as follows: |
7.1. Scope of AdSense for Search Services. If selected on the cover page(s) of
this Order Form, during the Services Term and subject to the terms and conditions of
this Agreement, Google will provide Customer with advertisements (“AFS Ads”) through
its AdSense for Search Service (the “AFS Service”) for display on the AFS Sites and
AFS Client Application as permitted herein. Customer agrees to implement the AFS
Service as provided herein on the AFS Sites and AFS Client Application in existence as
of the date hereof within thirty (30) days of the Order Form Effective Date, and to
maintain such implementation thereafter during the Services Term. Customer agrees to
implement the AFS Service on any AFS Site and AFS Client Application added thereafter
as contemplated by Section 3.3 herein.
| 6. | Section 7.2.1 of the Order Form is hereby amended and restated in its entirety as follows: |
7.2.1. Search Boxes and Queries. Customer shall send any and all WebSearch Queries
received by Customer from End Users to Google in accordance with the requirements
provided by Google, without editing, filtering, truncating or otherwise modifying such
WebSearch Queries, either individually or in the aggregate. Customer understands and
agrees that WebSearch Queries sent to Google for processing hereunder may be initiated
only through WebSearch Boxes (and not, for example, from News Search or Image Search
Boxes) implemented on a Site and Client Application as provided herein, unless
otherwise approved by Google in writing.
| 7. | [*] |
*CERTAIN
INFORMATION IN THIS EXHIBIT HAS BEEN OMITTED AND FILED SEPARATELY
WITH THE COMMISSION. CONFIDENTIAL TREATMENT HAS BEEN REQUESTED WITH
RESPECT TO THE OMITTED PORTIONS.
EXECUTION COPY
| 8. | Unless otherwise defined herein, capitalized terms used herein shall have the same meanings as set forth in the Agreement. | ||
| 9. | Except as modified by the provisions of this Amendment Two, all of the terms and conditions of the Agreement shall remain in full force and effect. | ||
| 10. | This Amendment Two may be executed in one or more counterparts, including facsimile counterparts, each of which shall be deemed an original and all of which together shall be considered one and the same agreement. |
IN WITNESS WHEREOF, the parties have caused this Amendment Two to be executed as of the
Amendment Two Effective Date.
| GOOGLE INC. |
||||
| By: | /s/ ▇▇▇▇ ▇▇▇▇▇▇▇▇ | |||
| Name: | ▇▇▇▇ ▇▇▇▇▇▇▇▇ | |||
| Title: | Director, Web Search & Syndication | |||
| SYNACOR, INC. |
||||
| By: | /s/ M. ▇▇▇▇ ▇▇▇▇▇▇▇ | |||
| Name: | M. ▇▇▇▇ ▇▇▇▇▇▇▇ | |||
| Title: | V.P. BUSINESS DEVELOPMENT | |||
| 3 of 20 |
EXECUTION COPY
Exhibit A
Client Application — Synacor Toolbar
[*]
| 4 of 20 |
| * | CERTAIN INFORMATION IN THIS EXHIBIT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE COMMISSION. CONFIDENTIAL TREATMENT HAS BEEN REQUESTED WITH RESPECT TO THE OMITTED PORTIONS. |
EXECUTION COPY
SCHEDULE I
Policy Guidelines for Access of Google Services Through Client Applications
Effective Date: July 26, 2004
Google has observed a significant increase in the number of reports of software that is engaging in
deceptive, malicious and other annoying practices that significantly diminish user perception and
enjoyment of the internet. These practices include but are not limited to installing software on
computers without obtaining informed end user consent (the so-called “drive-by download”),
inundating end users with advertisements without adequate attribution or labeling, exposing users
to pornographic material without obtaining informed end user consent, obtaining or transmitting
personal information about an end user without obtaining informed end user consent, and interfering
with an end user’s ability to easily uninstall applications the end user does not wish to be on his
or her computer.
Google does not wish to be associated with these types of practices. Accordingly, Google has
developed the Guidelines set forth below to prevent its trademark, other intellectual property, and
services from being used in connection with these practices. Google believes that these Guidelines
are necessary to protect Google from any allegation that it has contributed to practices that might
be viewed as unlawful or actionable; to preserve the reputation of Google as a provider of trusted
software and services in a manner that is beneficial and fair to users and other constituents; and
to stem the rising incidence of practices that harm users and diminish the perceived value and
reliability of the internet, which are essential to Google’s business.
With this objective in mind, Google has established the following Guidelines to apply to customer
Applications that are used to access our search and/or advertising syndication services. Except to
the extent Google has otherwise specifically agreed in writing, Google does not grant permission
to, and you will not, access Google services using one or more of your Applications unless you
ensure that those Applications comply with these Guidelines. Examples of accessing Google services
in this context include Applications that send end user queries or other information to Google to
generate search or ad results, or Applications that alter browser or other application settings to
permit error traffic to be sent to Google to generate search or ad results.
For the avoidance of doubt, by these Guidelines Google does not intend to, and does not, impose any
restrictions on what you may do with any Application that is not used to access, or is not bundled
with any Application that is used to access, Google services; you remain free to sell any
Application you wish (whether or not it complies with these Guidelines) so long as it is not used
to access Google services.
In these Guidelines: (a) “you” and “your” refer to the legal entity(ies) that has entered into the
contract with Google into which these Guidelines are incorporated, as well as any person or entity
acting on your behalf; and (b) “Application” means any application, plug-in, helper, component or
other executable code that runs on a user’s computer, examples of which include those that provide
browser helper objects, instant messaging, chat, email, data, file viewing, media playing, file
sharing, games, internet navigation, search and other services.
| 5 of 20 |
EXECUTION COPY
Google welcomes input about these Guidelines from you and from other interested parties, and
is always willing to consider revisions as appropriate to encourage innovation while protecting
against deceptive, unfair and harmful practices. Accordingly, Google may update these Guidelines,
including the Exhibits, from time to time as provided in Section 10 below.
1. General.
1.1. Approval and Ongoing Compliance. You may access Google services from
Applications only to the extent permitted in the signed written agreement into which these
Guidelines have been incorporated. In such instance, you must ensure that your Application both (1)
has been approved by Google for the purpose of accessing Google services in writing in advance, and
(2) complies at all times with the requirements outlined herein. To obtain Google’s approval for
any Applications not expressly approved in your agreement, you must submit a written request.
1.2. Implementation. The incorporation of Google services into your Application must
conform to the implementation requirements set forth in your agreement with Google. For example, in
the case of Applications that access Google’s WebSearch and/or AdSense for Search Services, end
user queries initiated from your Application must resolve to a Google-approved Web page on a
permitted Web site as provided in your agreement with Google (refer to your agreement for a
complete description of the scope of approved Web pages and sites). In any event, unless your
agreement with Google expressly authorizes otherwise, Google results may only appear on the Web
pages expressly approved by Google for such display, and, except for the display of those pages in
the main content area of a Web browser, Google results may not appear anywhere in your Applications
(e.g., Google results may not appear in the “chrome” of your Application unless your
agreement expressly contemplates otherwise).
1.3. No Google Branding or Attribution. Your Application, and any related collateral
material (including any Web pages promoting your Application or from which your Application is made
available), must not contain any Google branding, trademarks or attribution unless (and then only
to the extent) Google expressly consents otherwise in writing. In addition, queries entered into
Applications may not resolve to a results page that contains any Google branding, trademarks or
attribution unless (and then only to the extent) Google expressly consents otherwise in writing.
2. Prohibited Content. You may not access Google services from an Application that: (a)
contains any viruses, worms, trojan horses, or the like; and (b) is distributed primarily for the
purpose of (i) distributing pornographic, obscene, excessively profane, gambling-related,
deceptive, fraudulent or illegal content, or (ii) distributing content related to “hacking” or
“cracking.”
3. Prohibited Behavior. You may not access Google services from an Application that
engages in deceptive, unfair, harassing or otherwise annoying practices. For example, the
Application may not:
| (a) | use, or permit an unaffiliated person to use, an end user’s computer system for any purpose not understood and affirmatively consented to by the end user (including, without limitation, for purposes of consuming bandwidth or computer resources, sending email messages, launching denial of service attacks, accruing toll charges through a dialer or obtaining personal information from an end user’s computer such as login, password, account or other information personal to the end user); | ||
| (b) | intentionally create or exploit any security vulnerabilities in end user computers; |
| 6 of 20 |
EXECUTION COPY
| (c) | trigger pop-ups, pop-unders, exit windows, or similar obstructive or intrusive functionality, that materially interfere with an end user’s Web navigation or browsing or the use of his or her computer; | ||
| (d) | repeatedly ask an end user to take, or try to deceive an end user into taking, an action that the end user has previously declined to take (such as repeatedly asking an end user to change his or her home page or some other setting or configuration); | ||
| (e) | redirect browser traffic away from valid DNS entries (except that your Application may direct unresolved URLs to an alternative URL designated by you, provided that the page to which the end user resolves adequately informs the end user that you and your Application are the source of that page); | ||
| (f) | interfere with the browser default search functionality (except that your Application may permit an end user to change his or her default search engine with proper disclosure, consent and attribution as provided below); or | ||
| (g) | engage in activity that violates any applicable law or regulation. |
4. Disclosure and Consent.
4.1. Disclosure and Consent before Installation. You may not access Google services
from Any Application unless you and your distribution and bundling partners design the installation
of your Application in a manner that ensures that it is installed by end users in a knowing and
willful manner — e.g., no “drive-by” downloads or installs. By “distribution partner” we
mean any third party who distributes your Application and by “bundling partner” we mean any third
party who installs your Application in combination with or alongside one or more other
Applications. At a minimum, compliance with this provision requires that, prior to installing your
Application, you and any third party distributing or bundling your Application:
(a) first, fully, accurately, clearly and conspicuously disclose to end users:
| (i) | that they are installing an application, | ||
| (ii) | the name of the Application, identifying you as the entity responsible for it, and | ||
| (iii) | the principal and significant features and functionality of the Application; and |
(b) then, obtain the end user’s affirmative consent to install the Application.
Notwithstanding the foregoing, the disclosure and consent requirements of this Section 4.1 will not
apply to those of your Applications that are installed on computers prior to sale.
4.2. Disclosure and Consent for Collection and Transmission of Personally Identifiable
Information. You may not access Google services from any Application that (1) collects or
transmits to any entity other than the end user personally identifiable information, or (2)
collects or transmits information related to a user’s computer or Internet usage or activity in a
manner that could collect or transmit such user’s personally identifiable information (such as
through keystroke logging), unless prior to the first occurrence of any such collection or
transmission you:
(a) first, fully, accurately, clearly and conspicuously disclose:
| (i) | the type of information collected (described with specificity in the case of personally identifiable information), | ||
| (ii) | the method of collection (e.g., by registration, etc.), and |
| 7 of 20 |
EXECUTION COPY
| (iii) | the location of (i.e., a link to) the privacy policy that governs the collection, use and disclosure of the information; and |
(b) then, obtain the end user’s affirmative consent to such collection and/or
transmission.
4.3. Disclosure and Consent for Setting Changes. You may not access Google services
from any Application that makes a change to any operating system or Application data setting which
will impact the user experience of other Applications (e.g., changing the browser default
home page or changing the default application for a file type, such as the default email, browser
or media player application), unless prior to making such change you:
| (a) | first, fully, accurately, clearly and conspicuously disclose the change in a manner that will explain the practical effect of such change; and | ||
| (b) | then, obtain the end user’s affirmative consent to make such change. |
Notwithstanding the foregoing, (i) no disclosure and consent need be made for changes to operating
system or Application data settings that have only a minor impact on user experience, such as
adding a small number of bookmarks to the browser menu or adding an item to a start menu, and (ii)
the disclosure and consent requirements of this Section 4.3 will not apply to those setting changes
that may be made prior to sale to the end user.
4.4. Method of Disclosure and Consent. In order to satisfy the requirements above, the
disclosure of the items specified above (a) must be provided in both (1) the End User License
Agreement (▇▇▇▇) or privacy policy (to the extent required by law or otherwise by industry custom)
and (2) separately from the ▇▇▇▇ and/or privacy policy (e.g., in installation screens or
message boxes, as the case may be), and (b) must be designed so that it will be read by, adequately
inform and evidence the consent of a typical Internet user. See Exhibit A for sample
disclosure and consent implementations that would satisfy certain of the requirements above.
4.5. ▇▇▇▇ and Privacy Policy. You may not access Google services from any Application
unless it conforms, and is distributed pursuant to a ▇▇▇▇ that conforms, with all applicable laws
and regulations. In addition, you and your Application must comply with the agreements and
representations you make with your end users in your ▇▇▇▇ and privacy policy. Your privacy policy
must be accessible from your Application in an easily found location. If your Application collects
or transmits any other information related to the user’s use of his or her computer, but not
required to be disclosed and consented to pursuant to Section 4.2, then the collection and use of
such other information must be disclosed in your privacy policy.
5. Transparency. Neither you nor any of your third party distribution or bundling
partners may mislead end users or create end user confusion with regard to the source or owner of
an Application or any portion of its purpose, functionality or features. For example, all elements
of your Application that are visible to the end user must clearly identify their source through its
branding and attribution, and that identification, whatever form it takes, must correspond to the
identification of your application in the menu that permits end users to remove programs. You must
clearly label advertisements provided by your Application (if any) as such and clearly identify
your Application as the source of those advertisements. In addition, if your Application modifies
the operation or display of other applications or Web sites (other than Web sites that you own),
then in each instance you must clearly and conspicuously attribute the source of that
modification to your Application (as distinct from the application or Web site modified) in a
manner that will inform a typical Internet user; provided that this requirement will not apply to
| 8 of 20 |
EXECUTION COPY
modifications for which you obtain disclosure and consent pursuant to Section 4.3. See
Exhibit A for examples of modifications that are clearly and conspicuously disclosed to end
users.
6. Deactivation. You may not access Google services from any Application that impairs an
end user’s ability to change any preferences or settings set by the Application in accordance with
the way that such preferences or settings ordinarily may be changed by the applicable Application.
Once disabled by an end user, your Application may not be re-enabled without an affirmative action
by the end user to explicitly re-enable your application. Accordingly, no use, update, installation
or re-enablement of a separate Application, and no code downloaded as a result of browsing a Web
site, may operate to re-enable your Application. Your Application must permit end users to
uninstall it (in the customary place the applicable operating system has designated for adding or
removing programs, e.g., Add/Remove Programs control panel in Windows) in a straightforward
manner, without undue effort or skill. In addition, your Application, when running, must provide
(in an easily found location) clear and concise instructions on how it may be uninstalled. Once
uninstalled, your Application must not leave behind any functionality or design elements, and all
setting changes made by the application, but not explicitly agreed to by the end user, should be
reversed to the extent practicable.
7. Bundling of Applications.
7.1. Bundling. Your Application may be distributed through bundling arrangements
(referring to the distribution of your Application in a “bundle” that installs your Application
with one or more other Applications). However, in such case, you may not access Google services
from any such Application unless each of the following requirements is satisfied:
| (a) | the end user is made aware of all of the Applications included in the bundle prior to any installation; | ||
| (b) | all such Applications included in the bundle or download comply with the provisions of Section 2 through 6 of these Application Guidelines; | ||
| (c) | if Applications in a bundle in which you are participating are supported in part by revenue generated by advertising displayed in another independent Application included in that bundle and the continued use of the Application is conditioned on such other independent Application remaining installed and active on the end user’s computer, the end user must be made aware of that relationship; and | ||
| (d) | either (1) the bundle must provide for a master uninstaller that will enable the end user to uninstall every Application in the bundle without undue effort or skill, or (2) if no master uninstaller is provided, the de-installation of any Application may not be dependent or conditioned upon the de-installation of any other Application included in the bundle. |
7.2. PC OEM.
7.2.1.
[*]
*CERTAIN
INFORMATION IN THIS EXHIBIT HAS BEEN OMITTED AND FILED SEPARATELY
WITH THE COMMISSION. CONFIDENTIAL TREATMENT HAS BEEN REQUESTED WITH
RESPECT TO THE OMITTED PORTIONS.
EXECUTION COPY
7.2.2.
[*]
7.3. [*]
7.4. General. When entering into any bundling arrangements, it is your responsibility
to ensure that your direct and indirect distribution or bundling partners (and any applications
included in any bundle with your Application to the extent required herein) comply with the
applicable requirements of these Guidelines.
8. Information and Assistance. Subject to any confidentiality obligations owed to third
parties, you must provide Google with such information as Google may reasonably request about the
distribution of those of your Applications that are used to access Google services. For example, we
may ask you to share with us: (a) the means by and/or the locations from which your Applications
are distributed; or (b) the identity of any applications included in any of your bundling
relationships (and the entities responsible for such applications). In addition, you must provide
such assistance as Google may reasonably request to investigate and stop potential violations of
these Guidelines that may be connected to your Application, including by way of using such number
of identifiers and other tracking parameters as Google may reasonably request. This would include
providing Google with “golden masters” of any bundle or other distribution that includes your
Application, or working with Google to stop any entities that may be financially benefiting from
your Application from engaging in any of these proscribed practices. You understand, however, that
Google has no obligation to provide support to end users of your Application. For the avoidance of
doubt, these information and assistance rights do not extend to any of your Applications that are
not used to access Google services.
9. Legal. You must maintain ownership and control of your Application at all times to the
extent required to practically and legally enforce the requirements of these guidelines. If you are
seeking to permit a third party Application to incorporate or access our services, then you must
also obtain Google’s written approval of that third party Application (in addition to the approval
required for your Application). If Google approves the third party Application, you are responsible
for ensuring that such third party Application also complies with these Guidelines. You agree to be
responsible and liable for your Application’s access of Google’s results. Special indemnity and
other suspension and/or termination provisions may apply. These are addressed in your agreement
with Google.
10. Updates.
| 10 of 20 |
*CERTAIN
INFORMATION IN THIS EXHIBIT HAS BEEN OMITTED AND FILED SEPARATELY
WITH THE COMMISSION. CONFIDENTIAL TREATMENT HAS BEEN REQUESTED WITH
RESPECT TO THE OMITTED PORTIONS.
EXECUTION COPY
10.1. General. As mentioned above, Google may update these Guidelines, including
the Exhibits, from time to time; provided, however, that no updates will be effective until Google
provides you with thirty (30) days’ written notice thereof. Once you receive that notice, you will
be required to bring your Application into compliance within thirty (30) days.
10.2. Extended Compliance Period. If, solely as a result of an updated requirement,
one or more of your Applications no longer complies with these Guidelines, as updated, and you are
incapable of bringing such Application into compliance prior to the scheduled effective date of
such update (the “Update Effective Date”), you agree to provide Google with written notice thereof
as soon as reasonably practicable, but in any event no later than the Update Effective Date,
identifying the Application and the reasons why it may not be brought into compliance prior to the
Update Effective Date, and providing such other detail as Google may reasonably request with
respect thereto (consistent in any event with your confidentiality obligations). Thereafter, the
parties will consult, and you agree to will work, diligently and in good faith to develop and
execute a plan to bring such Application into compliance with these Guidelines, as updated, as soon
as reasonably practicable, but in any event within ninety (90) days of the Update Notice Date (the
“Maximum Compliance Period”). You agree that you will provide Google with such information as
Google reasonably requests during this period to keep Google apprised of your progress in bringing
your Application into compliance. Notwithstanding the foregoing (but subject to the next sentence),
in no event may a new requirement provided for in the update to these Guidelines require
you to take any action which would violate the terms of any agreement between you and any
unaffiliated third party that is in effect on the date that Google delivers notice of the proposed
update. In any event, if you are unable to bring any Application into compliance during the Maximum
Compliance Period, Google may elect, by providing at least thirty (30) days prior written notice,
to cease providing services to either the specific non-conforming Application or to those versions
of the Application which are, or are distributed, in violation of the Guidelines, as updated; it
being understood that, at such time, you will be entitled to procure services from an alternative
source for those Applications (or versions thereof) to which Google elects to cease providing
services as provided herein.
| 11 of 20 |
EXECUTION COPY
EXHIBIT A
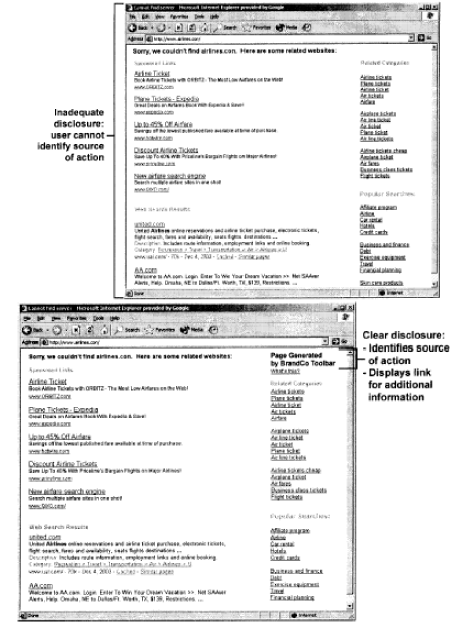
Prohibited Behavior and Content
The application may not impact the display of other applications unless you provide clear
disclosure in each instance
| 12 of 20 |
EXECUTION COPY
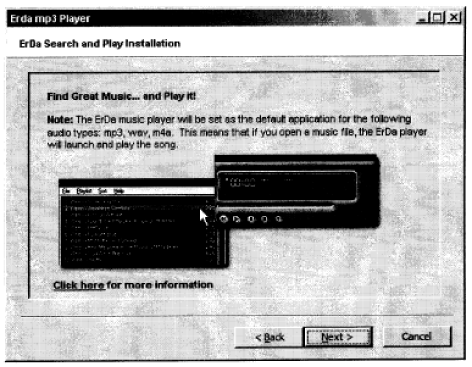
Disclosure and Consent
Clear and conspicuous disclosure is required prior to download or install: what it is, what it
does, and how it will be displayed to the end user
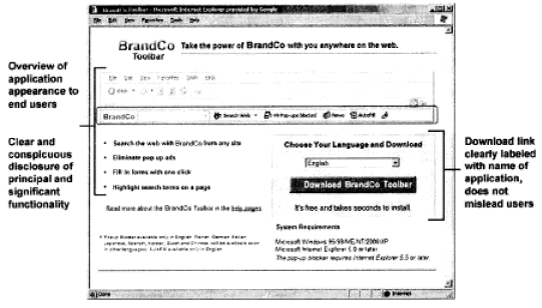
Disclosure and Consent
Describe type, method, and use of personal information, if applicable. Point user to privacy policy

Identify the changes that will occur if the application is installed
| 13 of 20 |
EXECUTION COPY
| 14 of 20 |
EXECUTION COPY
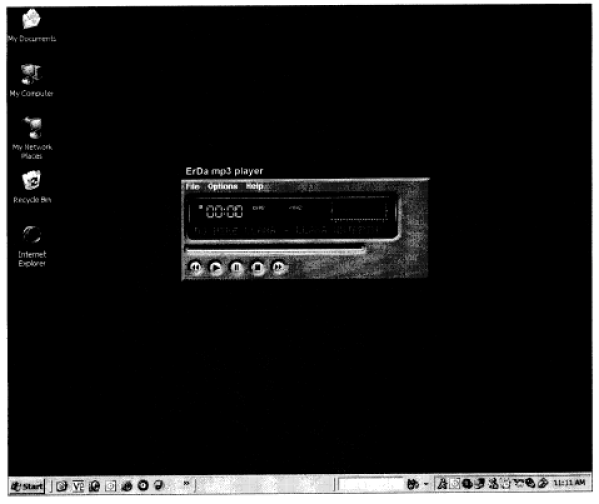
Branding & Attribution
The visible elements of the application should be easily identifiable to the end user
| 15 of 20 |
EXECUTION COPY
Implementation, Transparency and Deactivation
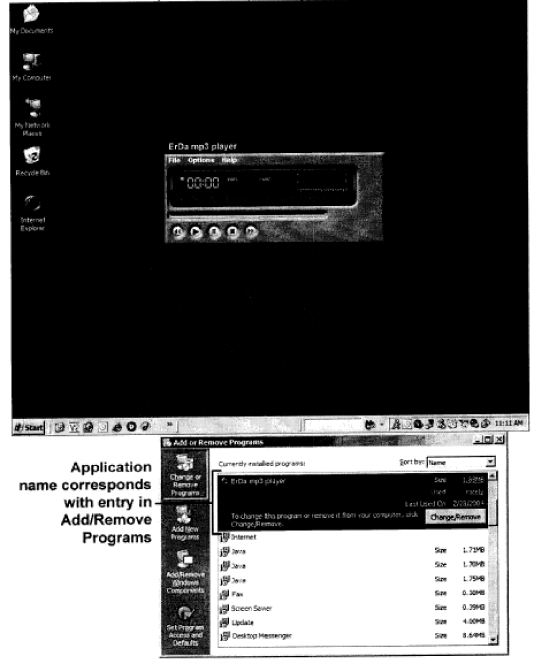
The Application must permit end users to uninstall it in the customary place the applicable
operating system has designated for adding or removing programs (e.g., Add/Remove Programs
control panel in Windows) in a straightforward manner
| 16 of 20 |
EXECUTION COPY
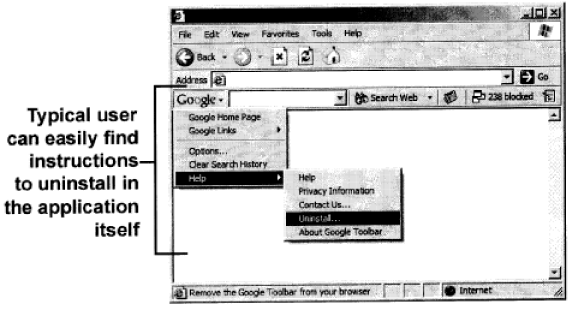
Implementation, Transparency and Deactivation
The Application must contain (in an easily found location) clear and concise instructions on how it may be uninstalled
| 17 of 20 |
EXECUTION COPY
Bundling of Applications
When bundling, the end user must be made aware of all the applications included prior to
installation.

| 18 of 20 |
EXECUTION COPY
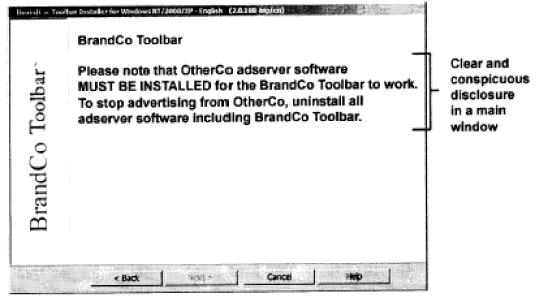
Bundling of Applications
When bundling, the end user must be made aware of advertising revenue relationships to other
applications, if the continued use of the primary application is conditioned on the other
applications being installed and active on the end user’s computer
| 19 of 20 |
EXECUTION COPY
Exhibit B
[*]
| * | CERTAIN INFORMATION IN THIS EXHIBIT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE COMMISSION. CONFIDENTIAL TREATMENT HAS BEEN REQUESTED WITH RESPECT TO THE OMITTED PORTIONS. |
20 of 20

