Amendment 20070105.006.A.002 Between StarTek, Inc. And AT&T Services, Inc.
EXHIBIT 10.9
Amendment
20070105.006.A.002
Between
StarTek, Inc.
And
AT&T Services, Inc.
AGREEMENT NO. 20070105.006.C
This Amendment, effective on the date when signed by the last Party (“Effective Date”), and amending Agreement No. 20070105.006.C, is by and between StarTek, Inc., a Delaware corporation (“Supplier”), and AT&T Services, Inc., a Delaware corporation (“AT&T”), each of which may be referred to in the singular as a “Party” or in the plural as the “Parties.”
WITNESSETH
WHEREAS, Supplier and AT&T entered into Agreement No. 20070105.006.C on January 26, 2007 (the “Agreement”); and
WHEREAS, Supplier and AT&T desire to amend the Agreement as hereinafter set forth.
NOW, THEREFORE, in consideration of the premises and the covenants hereinafter contained, the Parties hereto agree as follows:
1) Section 2.0 “Definitions”, is hereby amended as follows:
a. Sub-section 2.11, “Information”, is hereby deleted in its entirely and replaced with the following:
“Information”, with respect to a Party, means all confidential, proprietary or trade secret information belonging to such Party, including discoveries, ideas, concepts, know-how, techniques, processes, procedures, designs, specifications, strategic information, proposals, requests for proposals, proposed products, drawings, blueprints, tracings, diagrams, models, samples, flow charts, data, computer programs, marketing plans, customer information, employee personal information, health or financial information, authentication credentials, and other technical, financial or business information, whether disclosed in writing, orally, visually, in tangible or intangible form, including in electronic mail or by other electronic communication.
b. Sub-section 2.19, “Services”, is deleted in is entirety and replaced with the following:
“Service(s)” means any labor or service provided pursuant to this Agreement or an applicable Order, including, but not limited to, engineering, installation, removal, maintenance, training, technical support, repair and Call Center Services. The term “Service”
Proprietary and Confidential
This Agreement and information contained therein is not for use or disclosure outside of AT&T, its Affiliates, and third party representatives, and Supplier except under written agreement by the contracting Parties.
1
shall also include any Material, including any Documentation, provided by Supplier pursuant to this Agreement or an applicable Order in connection with providing the Services. For the sake of clarity, Services (including Call Center Services) specifically excludes consulting and professional services whereby enhancements, modifications or any development activities related to software will occur (i.e., development of customized software).
c. Sub-section 2.23, “Deliverables”, is hereby added to the Agreement and is fully incorporated therein by this reference:
“Deliverables” means any and all deliverables set forth in an Order to be provided by Supplier pursuant to such Order. Deliverables include, but are not limited to, any reports, data, designs, plans, specifications, models, prototypes, performance requirements, and/or Documentation delivered pursuant to this Agreement or such Order.
2) The Section 3.37, “Title to Work Product”, is hereby deleted in its entirety and is replaced with the following, “Ownership of Work Product”:
3.37 Ownership of Work Product
Supplier’s Intellectual Property. The Parties acknowledge that Supplier and/or third-parties own certain intellectual property, including pre-existing or independently developed Materials, software, processes, tools, methodologies and other intellectual property used to create the Work Product (the “Supplier’s IP”). The notion of “independently developed” refers to development performed outside of this Agreement without use of or access to any Information provided by or on behalf of AT&T. Something that is independently developed remains Supplier’s IP, even though Supplier may use it in connection with providing Services. AT&T makes no claim to such Supplier’s IP which is not defined in or to be delivered pursuant to this Agreement or in an applicable Order.
Work Product. Excluding the Supplier’s IP and Supplier’s Information, ownership and all rights in the work product resulting from or is the outcome produced as a result of the Services or Call Center Services set forth in an Order (“Work Product”) including new trademarks, patents, copyrights, and trade secrets applicable to same, hereby vests exclusively in AT&T regardless of whether Work Product was created solely by Supplier or jointly by the Parties. The Parties expressly agree to consider as a “work made for hire” any Work Product which qualifies as such under the laws of the United States or other jurisdictions. To the extent that the Work Product does not qualify as a “work made for hire”, or where necessary for any other reason to perfect the rights of AT&T thereto, Supplier hereby assigns to AT&T all right, title and interest thereto. Supplier agrees to provide other assistance, at AT&T’s expense, which AT&T may need through trademark, patent or copyright applications, or otherwise, to obtain the full benefit of the rights provided for herein, and will execute all documents necessary to carry such assignment into full effect. NOTE: The notion of “work
Proprietary and Confidential
This Agreement and information contained therein is not for use or disclosure outside of AT&T, its Affiliates, and third party representatives, and Supplier except under written agreement by the contracting Parties.
2
product” refers to a deliverable or outcome that must be produced to complete a project and achieve its objectives (See definition at XxxxxxxxXxxxxxxxxx.xxx)
License. If the Work Product contains Supplier’s IP or other elements Supplier or others on its behalf previously or independently developed, then Supplier grants to AT&T, or agrees to obtain for AT&T, a non-exclusive, unrestricted, perpetual, worldwide, royalty-free license to use, copy, modify, distribute, publicly display, publicly perform, import, manufacture, have made, sell, offer to sell (whether directly or through channels of distribution), exploit and sublicense such elements (and have others do any of the foregoing acts on AT&T’s behalf) to the extent necessary for AT&T to exercise its rights in the Work Product. Any such license shall include AT&T’s right to grant an unrestricted, royalty-free sublicense to its Affiliates for the purposes stated herein.
Miscellaneous. Supplier shall place a copyright or other proprietary notice on the Work Product at AT&T’s request. All non-public aspects of the Work Product shall constitute AT&T’s Information under this Agreement.
Reservation of Rights and Residuals. Except as otherwise expressly provided in this Section entitled “Ownership of Work Product,” Supplier retains all right, title, and interest in and to all Supplier’s IP and Supplier’s Information. The Parties agree that either Party may use, without an obligation to the other Party, any general knowledge and expertise, skills, techniques, concepts or know-how incidentally (and not intentionally) retained in the unaided memory of the Party’s employees to develop or provide similar services for other customers, provided that such use is without reference to the other Party’s Information. No license is granted under this Section by either Party to the other Party for any patent, trademark, Work Product, trade secret or copyright.
3) The following Section 4.19, “Payment Card Industry (PCI) Data Security Standards and Credit Card Information”, is hereby added to the Agreement and is fully incorporated therein by this reference:
Section 4.19, “Payment Card Industry (PCI) Data Security Standards and Credit Card Information
The Payment Card Industry (PCI) data security standards are network security and business practice guidelines developed for Visa, MasterCard, American Express and Discover Card. They were developed to establish a minimum security standard with regards to the protection of cardholder’s account and transaction information. The PCI Security Standards Council, LLC (a non-AT&T entity) owns, develops, maintains and distributes the PCI Data Security Standard (DSS). If Supplier (including its subcontractor, agent or any third party, acting through, or on behalf of Supplier) collects, processes, handles, and/or maintains credit card data and/or related transaction status or identity information through, for, or on behalf of
Proprietary and Confidential
This Agreement and information contained therein is not for use or disclosure outside of AT&T, its Affiliates, and third party representatives, and Supplier except under written agreement by the contracting Parties.
3
AT&T (including, without limitation, for itself, or in connection with AT&T’s joint or co-branded relationships and/or its, or their customers, as the case may be), Supplier represents and warrants that it is, and shall remain PCI DSS compliant, including, but not limited to being, DSS certified, current and in good standing, if applicable, at no cost to AT&T, for the longer of the term of this Agreement or any of Supplier’s applicable obligation periods under this Agreement, in accordance with the requirements of the PCI DSS. Notwithstanding anything to the contrary contained within the clause entitled Information or any other provision within this Agreement, Supplier acknowledges that credit card information shall be deemed, and shall be treated as Information under this Agreement irrespective of whether or not such Information is conspicuously marked as confidential or proprietary and Supplier’s obligation to treat credit card related Information as confidential shall survive the Termination, Cancellation or expiration of this Agreement. Supplier shall indemnify and hold AT&T harmless from and against any proved or alleged claims, demands or suits, or any losses, damages, liabilities, fines, penalties and expenses (including reasonable attorney’s fees) that arise out of, relate to or result from Supplier’s (and/or its subcontractor, agent or any third party, if any, acting through or on behalf of Supplier) failure to comply with its obligations under this clause. Except as may be provided elsewhere in this Agreement, nothing contained within this clause shall be construed to mean, or means that Supplier is authorized to delegate, assign or subcontract any portion of its obligations under this clause to any third party.
4) The following Section 4.20, “Worker’s Exit Process from AT&T’s Program(s)”, is hereby added to the Agreement and is fully incorporated therein by this reference:
“4.20 Worker’s Exit Process from AT&T’s Program(s)
“Workers” Exit Process from AT&T’s Program(s). If the Work is transitioning to another AT&T program, some of these provisions may not apply.
a. Upon Worker’s completion of Services, including attrition of Worker, dismissal of Worker, and program expiration or termination, Supplier shall:
· Immediately notify AT&T’s Hiring/Program Manager and identify the Worker(s) so the applicable attuid can be deleted.
· Ensure that Worker’s critical knowledge as to the performance of Services is transferred via training of other Worker(s) and/or documented.
· Ensure that any roles assigned to the Worker are appropriately reassigned, such as:
· Project team/committee member
· Functional representative for internal/external interfaces
· Advise the AT&T Hiring/Program Manager if a security clearance exists.
· Advise the AT&T Contract Manager, as applicable, if there is reason to believe the Worker should not be engaged for future assignments.
Proprietary and Confidential
This Agreement and information contained therein is not for use or disclosure outside of AT&T, its Affiliates, and third party representatives, and Supplier except under written agreement by the contracting Parties.
4
· Remind the Workers of their obligation to maintain confidentiality of AT&T proprietary information.
· Perform an inventory of AT&T records (paper and electronic) in Worker’s office or telework/virtual office and arrange for appropriate retention or destruction pursuant to an Order or as directed by AT&T’s Hiring/Program Manager.
· Have Worker establish “Out of Office” Voice Mail message and have the Supplier’s Team Manager, or its delegate, review for appropriateness.
· If a reservation or reservationless conference bridge is assigned to the Worker for AT&T’s Program, Supplier’s Team Manager, or its delegate, shall ensure that such reservation and reservationless conference bridges are cancelled.
· When transition of Worker’s job responsibilities under an AT&T Program is complete, Supplier Team Manager, or its delegate, requests cancellation of other system / job specific UserIDs, access codes, and access privileges that the Worker may have to support AT&T’s Programs, such as:
· Shared drives (transfer ownership, if applicable)
· Financial systems
· Data warehouses
· Internet and database services
· Digital Certificates
· Other systems
|
|
· |
|
|
|
|
· |
|
|
|
|
· |
|
|
· If reasonably possible to do so, collect and return SecurID Card/Token to AT&T, if applicable.
NOTE: At the same time, AT&T shall promptly disable access to AT&T assets by means of such SecurID Card/Token so that access cannot be achieved even if the SecurID Card/Token cannot be collected.
· If TACACS/Config service, applies, notify the AT&T Hiring/Program Manger to delete TACACS/config server ID, if applicable.
· Recover and secure AT&T assets, which may include AT&T assets, in Worker’s possession (including those kept at the individual’s home):
· Personal computers
· Software
· Monitors
· Modems
· Printers
Proprietary and Confidential
This Agreement and information contained therein is not for use or disclosure outside of AT&T, its Affiliates, and third party representatives, and Supplier except under written agreement by the contracting Parties.
5
· Fax machines
· Speakers
· PDAs
· Pagers
· Cell phones
· If Workers used a non-Supplier PC or Supplier’s PC (collectively “PC”), Supplier shall ensure that AT&T Proprietary information is cleaned off the PC by having them re-imaged.
· Have Supplier Team Manager, or its delegate, ensure that the office space of exiting Worker is cleaned and ready for next occupant.
· If Services are performed at remote locations, Supplier Team Manager, or its delegate, ensures the following installed services are disconnected at Worker’s location (home and/or other work location):
· Phone lines
· DSL lines
· Cable modem connections
· If Services are performed at Supplier Locations, Supplier Team Manager, or its delegate, ensures the following services are disconnected:
· Office Telephone
· Voice Mail
· LAN Port
· Have Supplier Team Manager, or its delegate, collect all property used for AT&T’s Program(s). This includes but is not limited to:
· Worker’s identification badges, portal passes, parking decals and passes, building access cards, security ID cards, smart cards, key cards, toll pass cards
· Keys to desks, file cabinets, storage cabinets, offices, conference rooms, and other work areas
· Keys to buildings, gates and vehicles used for AT&T’s Program(s)
· Other equipment or property used for AT&T’s Program(s) not mentioned in previous tasks, including any items that the Worker has at home or other remote location, such as:
· Microphones, video recorders, cameras and answering machines
· Manuals, library materials, software, documentation for software and hardware
· Office furniture (and keys to same) and artwork
· Special devices (e.g., scanners, 2-way radios)
· Tools and Uniforms
· Prepare AT&T files for storage:
Proprietary and Confidential
This Agreement and information contained therein is not for use or disclosure outside of AT&T, its Affiliates, and third party representatives, and Supplier except under written agreement by the contracting Parties.
6
· Supplier Team Manager, or its delegate, reviews office records for compliance with AT&T’s retention schedule pursuant to an Order and as required by law, and transfer active records with retention obligations to appropriate person or group inheriting work function. For inactive records with retention obligations, follow procedures for sending to off-site vendor storage.
· Material for which there is no retention obligation or as may be required by law, can be destroyed in accordance with the Order or as directed by AT&T’s Hiring/Program Manager.
b. Obtain Worker’s certification that Worker has returned or destroyed all physical and electronic copies of AT&T proprietary information.
a. Upon Worker’s completion of Services, including the attrition of Worker, dismissal of Worker, and program expiration or termination, Supplier shall use reasonable commercial efforts to cause such Worker to complete and sign the “Written Certification of Return or Destruction of AT&T Information or Data”, Appendix L.
b. Supplier shall deliver either an executed copy of Appendix L to the AT&T Hiring/Program Manager or a statement explaining why such copy cannot be provided, within five (5) business days of completion of Services, and retain the original, if any, to be placed in the Worker’s personal file as a permanent record, If such executed copy of Appendix L cannot be obtained, Supplier shall nevertheless use reasonable commercial efforts to obtain .the return of any AT&T Proprietary Information from the Worker and either return the same to AT&T or destroy it.
5.) The following Section 4.21 AT&T Supplier Information Security Requirements (SISR)”, is hereby added to the Agreement and is fully incorporated therein by this reference:
“Supplier shall comply with the requirements of Appendix “O” entitled “AT&T Supplier Information Security Requirements (SISR).”
6.) The attached Appendix L — “Written Certification of Return or Destruction of AT&T Information or Data” is hereby added to the Agreement and fully incorporated therein by this reference.
7.) The attached Appendix O, “Supplier Information Security Requirements (SISR)”, is hereby added to the Agreement and fully incorporated therein by this reference.
Proprietary and Confidential
This Agreement and information contained therein is not for use or disclosure outside of AT&T, its Affiliates, and third party representatives, and Supplier except under written agreement by the contracting Parties.
7
The terms and conditions of Agreement No. 20070105.006.C in all other respects remain unmodified and in full force and effect.
The Parties hereto acknowledge that they have read this Amendment, understand it, and agree to be bound by its terms and conditions. They further agree that Agreement No. 20070105.006.C together with Amendment No. 20070105.006.A.001 and this Amendment No. 20070105.006.A.001 constitute the entire agreement between the Parties hereto with respect to the subject matter hereof.
IN WITNESS WHEREOF, the Parties have caused this Amendment to Agreement No. 20070105.006.C to be executed, which may be in duplicate counterparts, each of which will be deemed to be an original but all of which together will constitute only one instrument, as of the date the last Party signs.
|
StarTek, Inc. |
|
AT&T Services, Inc. |
||
|
|
|
|
||
|
By: |
/s/ A. Xxxxxxxx Xxxxx |
|
By: |
/s/ Xxxxxxx Xx Xxxxx |
|
|
|
|
|
|
|
Printed Name: |
A. Xxxxxxxx Xxxxx |
|
Printed Name: Xxxxxxx Xx Xxxxx |
|
|
|
|
|
|
|
|
Title: |
President and CEO |
|
Title: Sourcing Director - Contact Centers and Marketing, AT&T Supply Chain Operations |
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
|
|
|
Date: |
4/14/09 |
|
Date: |
4/14/09 |
Proprietary and Confidential
This Agreement and information contained therein is not for use or disclosure outside of AT&T, its Affiliates, and third party representatives, and Supplier except under written agreement by the contracting Parties.
8
Appendix L
Written Certification of Return or Destruction of AT&T Information or Data
Pursuant to the terms of the Worker Agreement dated , 20XX between me and [NAME OF AT&T COMPANY] (“AT&T”), I hereby certify that I have returned to AT&T or have destroyed all physical and electronic copies of all Information, as that term is defined in the Worker Agreement.
|
|
|
|
[NAME AND ATTUID OF WORKER] |
|
|
|
|
|
|
|
|
Signature |
|
|
|
|
|
|
|
|
Date |
|
Proprietary and Confidential
This Agreement and information contained therein is not for use or disclosure outside of AT&T, its Affiliates, and third party representatives, and Supplier except under written agreement by the contracting Parties.
1
Appendix O
Information Security Policy
AT&T Supplier Information Security Requirements
The following AT&T Supplier Information Security Requirements apply to the employees and/or temporary workers of Supplier and its suppliers, contractors, vendors and/or agents, that perform services for, on behalf of, and/or through AT&T, which require access to AT&T’s infrastructure, systems or applications or handle, process, or store, AT&T, AT&T Branded and/or AT&T Co-branded Information (for the purpose of this Section, each or all “Supplier”). Supplier represents and warrants that during the term of this Agreement and thereafter (as applicable with respect to Supplier’s obligations under the Survival of Obligations and Compliance with Laws clauses) Supplier is, and shall continue to be in compliance with its obligations as set forth herein.” AT&T’s failure to audit and/or exercise any of its rights under this Section shall not be construed or deemed to be a waiver of any rights under this Agreement, equity or law. In addition to all other remedies specified in the Agreement, Supplier agrees that AT&T shall be entitled to seek an injunction and be reimbursed the costs (including reasonable attorney’s fees) by Supplier to cease any breach of any obligation that survives termination or expiration of this Agreement. The following provisions shall not be deemed to, and shall not limit any more stringent security or other obligations contained within this Agreement.
Definitions:
Unless otherwise set forth or expanded herein, defined terms shall have the same meaning as set forth in the main body of the Agreement.
“AT&T Branded Information” means Information owned, labeled, marked, or collected, which contains any of AT&T’s or its affiliates identifying markings or trademarks.
“AT&T Co-branded Information” means AT&T Branded Information that is jointly marketed or shared under a co-branding arrangement with a Supplier, irrespective of dominance or emphasis of the co-branding relationship.
As used herein, the term “Information” is limited to:
(a) The “Confidential Information” to which the obligations in Section 3.16 of the Agreement apply, and
(b) The “Customer Information” to which the obligations in Section 4.9 of the Agreement apply.
“Information Resources” means any systems, applications, and network elements, and the information stored, transmitted, or processed with these resources in conjunction with supporting AT&T and/or utilized by Supplier in fulfillment of its obligations under this Agreement.
“Personally Identifiable Information” or (“PII”) means any information that could be used to uniquely identify, locate, or contact a single person (or potentially be exploited to steal the identity of an individual, commit fraud or perpetuate other crimes). Examples of PII include personal telephone
Proprietary and Confidential
This Agreement and information contained therein is not for use or disclosure outside of AT&T, its Affiliates, and third party representatives, and Supplier except under written agreement by the contracting Parties.
1
numbers, social security numbers, national, state or province, issued identification number, drivers license number, date of birth, bank account numbers, credit card numbers and expiration dates, and other credit related information, PINs, passwords, passcodes, password hint answers, Protected Health Information as defined by the Health Insurance Portability and Accountability Act (HIPAA), biometric data, digitized signatures, and background check details.
In accordance with the foregoing, Supplier shall:
System Security
|
1. |
|
Actively monitor industry resources (e.g. xxx.xxxx.xxx, pertinent software vendor mailing lists & websites) for timely notification of all applicable security alerts pertaining to Supplier networks and computers. |
|
|
2. |
|
Scan its externally-facing systems with applicable industry standard security vulnerability scanning software (including, but not limited to, network, server, & application scanning tools) at a minimum monthly. |
|
|
3. |
|
Scan its internal systems with applicable industry standard security vulnerability scanning software (including, but not limited to, network, server, application & database scanning tools) at a minimum monthly. |
|
|
4. |
|
Upon AT&T’s request, furnish to AT&T its most current scanning results for those resources used to support AT&T. |
|
|
5. |
|
Deploy an Intrusion Detection System(s) (IDS) in an active mode of operation. |
|
|
6. |
|
Remediate security vulnerabilities, including, but not limited to, those discovered through industry publications, vulnerability scanning, virus scanning, and the review of security logs, and apply applicable security patches in a timely manner, according to the following minimal guidelines: If: |
|
|
|
|
· |
A vulnerability exists and attack is underway: Supplier shall work on remediating/patching 24x7 |
|
|
|
· |
A vulnerability exists and attack is determined to be imminent: Supplier shall remediate/patch within seven (7) days |
|
|
|
· |
A vulnerability exists and attack is determined to not be imminent: Supplier shall remediate/patch within thirty (30) days |
|
All other security patches shall be applied within ninety (90) days. |
|||
|
7. |
|
Assign security administration responsibilities for configuring host operating systems to specific individuals. |
|
|
8. |
|
Ensure its security staff has reasonable and necessary experience in information/network security. |
|
|
9. |
|
Ensure all Supplier’s systems are and remain ‘hardened’ including, but not limited to, removing or disabling unused network services (e.g. finger, rlogin, ftp, simple tcp/ip services) and installing a system firewall, TCP Wrappers or similar technology. |
|
|
10. |
|
Change all default account names and/or default passwords in accordance with password requirements as set forth within requirement number 35, below. |
|
|
11. |
|
Limit system administrator/root access to host operating systems only to individuals requiring high-level access in the performance of their jobs. |
|
|
12. |
|
Require system administrators to restrict access by users to only the commands, data and systems necessary to perform authorized functions. |
|
|
Physical Security
|
|||
|
13. |
|
Ensure all Supplier’s networks and computers are located in secure physical facilities with limited and restricted access by authorized individuals only. |
|
Proprietary and Confidential
This Agreement and information contained therein is not for use or disclosure outside of AT&T, its Affiliates, and third party representatives, and Supplier except under written agreement by the contracting Parties.
2
|
14. |
|
Monitor and record, for audit purposes, access to the physical facilities containing networks and computers used in connection with Supplier’s performance of its obligations under this Agreement. |
|
|
|
|
|
Network Security |
||
|
|
||
|
15. |
|
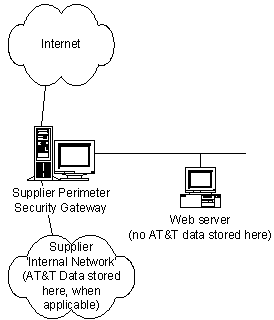
Separate AT&T’s data from the Internet and the destination web servers with a perimeter security gateway (e.g. firewall). For additional clarification of this requirement, see diagram, however, the written requirements shall control with respect to the interpretation of this provision. |
|
|
|
|
|
|
||
|
|
||
|
16. |
|
Upon AT&T’s request, provide to AT&T a logical network diagram detailing the Information Resources (including, but not limited to firewalls, servers, etc) that will support AT&T. |
|
17. |
|
Have a process and controls in place to detect and handle unauthorized attempts to access AT&T data. |
|
18. |
|
Utilize strong encryption technologies (minimum 256-bit encryption) for the transfer of AT&T Information outside AT&T controlled facilities and network. This also applies to electronically transmitted email communications containing proprietary AT&T data or Information. |
|
19. |
|
Utilize strong authentication (e.g. two factor token or digital certificates) for remote access. |
Proprietary and Confidential
This Agreement and information contained therein is not for use or disclosure outside of AT&T, its Affiliates, and third party representatives, and Supplier except under written agreement by the contracting Parties.
3
|
Information Security |
||
|
|
||
|
20. |
|
Not co-locate AT&T’s application/data on the same physical servers with other customers’ or Supplier’s own application/data unless approved in advance in writing by AT&T. If physical separation does not exist, documented controls must be in place and approved by AT&T to ensure separation of data and security of Information between customer, supplier, and AT&T applications. |
|
|
|
eWFM is a scheduling application that managed the agent schedules. Verint is Supplier’s call recording system, and there are on separate servers, by client. XXX, is Supplier’s data warehouse. Supplier has logical controls around database access with specific group memberships permitting access only to StarTek’s DBAs. XXX is in SOX scope requiring regular reviews and is also governed by Change Control for any changes that need to be made or transactions that would need to be run at the database level. The process that surrounds the XXX is as follows. Only technical (IT) people “who require such database access” can gain access to the XXX. This access has to be approved by Supplier’s VP of Technology Operations prior to access being granted. Once approved, the individual is assigned specific access based on the necessary requirements to perform their jobs. |
|
21. |
|
Have a procedure approved in advance in writing by AT&T for the backup, secure transport and storage of AT&T Information. |
|
22. |
|
Maintain and furnish to AT&T a business continuity plan that ensures Supplier can meet its contractual obligations under the Agreement, including the requirements of any applicable Statement of Work or Service Level Agreement. |
|
23. |
|
Store sensitive AT&T data elements utilizing strong encryption technologies (minimum 256-bit encryption). Sensitive data elements include, but are not limited to, the following: social security number, national, state or province, issued identification number, drivers license number, date of birth, bank account number, credit card number and expiration date, and other credit related information, PINs, passwords, passcodes, password hint answers, Protected Health Information as defined by the Health Insurance Portability and Accountability Act, HIPAA, biometric data, digitized signature, and background check details. |
|
24. |
|
Limit access to AT&T Information, including paper hard copies, only to persons or systems authorized by AT&T under written agreement. |
|
25. |
|
Be compliant with any applicable government and industry mandated information security requirements including, but not limited to the Payment Card Industry- Data Security Standards (PCI) and HIPAA. |
|
26. |
|
Retain records according to and in compliance with any applicable federal, state, local and foreign laws, ordinances, regulations and/or codes, and as otherwise directed by AT&T, for a period of no less than three (3) years, or longer as may be set forth herein or as may be required pursuant to a court order or civil or regulatory proceeding. |
|
27. |
|
Return all AT&T Information, including electronic and hard copies within thirty (30) days upon the sooner of: (a) expiration or termination of the Agreement; (b) AT&T’s request for the return of Information; or (c) when Supplier (or its suppliers or representatives) no longer need the Information. In the event AT&T approves the destruction as an alternative to returning the Information, then Supplier shall certify the destruction (e.g., degaussing, overwriting, performing a secure erase, performing a chip erase, shredding, cutting, punching holes, breaking) in a manner approved in advance in writing by AT&T. |
Proprietary and Confidential
This Agreement and information contained therein is not for use or disclosure outside of AT&T, its Affiliates, and third party representatives, and Supplier except under written agreement by the contracting Parties.
4
|
28. |
|
Unless otherwise instructed by AT&T, when collecting, generating or creating Information for, through or on behalf of AT&T or the AT&T brand, Supplier shall utilize the following AT&T proprietary marking: |
|
|
|
|
|
|
|
“AT&T Proprietary Information (Internal Use Only)
Not for use or disclosure outside the AT&T companies
except under written agreement” |
|||
|
|
|
|
|
|
Identification and Authentication |
|||
|
|
|||
|
29. |
|
Assign unique userids to individual users. |
|
|
30. |
|
Have and utilize a documented Userid Lifecycle Management process including procedures for approved account creation, timely account removal, and account modification (e.g. changes to privileges, span of access, functions/roles) for all applications and across all environments (production, test, development, etc). |
|
|
31. |
|
Enforce the rule of least privilege (i.e. limiting access to only the commands and Information necessary to perform authorized functions according to one’s job function). |
|
|
32. |
|
Limit failed login attempts to no more than six successive attempts and lock the user account upon reaching that limit. Access to the user account can subsequently be reactivated through a manual process requiring verification of the user’s identity or, where such capability exists, can be automatically reactivated after at least three minutes from the last failed login attempt. |
|
|
33. |
|
Terminate interactive sessions that have been inactive for a designated period of time, not to exceed fifteen (15) minutes. |
|
|
34. |
|
Require password expiration at regular intervals not to exceed ninety (90) days unless approved in advance and in writing by AT&T. |
|
|
35. |
|
Use an AT&T-approved authentication method based on sensitivity of Information. When passwords are used, they must meet these requirements: |
|
|
|
|
· |
Passwords must be a minimum of six (6) characters in length. |
|
|
|
· |
Passwords must contain characters from at least two (2) of these groupings: alpha, numeric, and special characters. |
|
|
|
· |
Password construction must be complex and not contain names, dictionary words, combinations of words, or words with substitutions of numbers for letters, e.g., s3cur1ty. |
|
|
|
· |
Passwords must not contain repeating or sequential characters or numbers. |
|
|
|
· |
Passwords must not contain sequences of three (3) or more characters from the USERID or system name. |
|
|
|
· |
The new password must not contain sequences of three (3) or more characters from any of the previous four (4) passwords. |
|
|
|
· |
Passwords must not contain a sequence of two (2) or more characters more than once, e.g., a12x12. |
|
|
|
Note: (Applications housing Restricted Proprietary Information may require an authentication mechanism stronger than passwords and the authentication mechanism must be approved by AT&T in advance in writing. Examples of stronger authentication methods include tokens, digital certificates, passphrase, and biometrics.) |
|
|
36. |
|
Use a secure method for the conveyance of authentication credentials (e.g. passwords) and authentication mechanisms (e.g. tokens or smart cards). |
|
Proprietary and Confidential
This Agreement and information contained therein is not for use or disclosure outside of AT&T, its Affiliates, and third party representatives, and Supplier except under written agreement by the contracting Parties.
5
|
Warning Banner |
||
|
|
||
|
37. |
|
Display a warning or “no-trespassing” banner on applicable login screens or pages when in Supplier’s environment and not an AT&T Branded product or service. |
|
|
|
|
|
|
|
(example long version): |
|
|
|
|
|
|
|
This is an <company name> system, restricted to authorized individuals. This system is subject to monitoring. Unauthorized users, access, and/or modification will be prosecuted. |
|
|
|
|
|
|
|
(example short version): |
|
|
|
|
|
|
|
<company name> authorized use ONLY, subject to monitoring. All other use prohibited. |
|
|
|
|
|
|
|
For AT&T Branded products or services or for software developed for AT&T, the Supplier shall display a warning banner on login screens or pages as provided by AT&T. |
|
|
|
|
|
Software and Data Integrity |
||
|
|
||
|
38. |
|
Scan for and promptly remove viruses. |
|
39. |
|
Separate non-production systems and data from production systems and data. |
|
40. |
|
Have a documented software change control process including back out procedures. |
|
41. |
|
Have database transaction logging features enabled and retain database transaction logs for a minimum of six (6) months. |
|
|
|
eWFM is not in scope for SOX therefore no database logging is required. Supplier has logical controls around database access with specific group memberships permitting access only to StarTek’s DBAs. XXX is in SOX scope requiring regular reviews and is also governed by Change Control for any changes that need to be made or transactions that would need to be run at the database level. The process that surrounds the XXX is as follows. Only technical (IT) people “who require such database access” can gain access to the XXX. This access has to be approved by Supplier’s VP of Technology Operations prior to access being granted. Once approved, the individual is assigned specific access based on the necessary requirements to perform their jobs. While eWFM provides workforce information, it is strictly a workforce management tool used for scheduling agents. XXX provides the metric and call data that is then used for invoicing and billing back to the Client. |
|
42. |
|
Regarding software developed, used or furnished and/or supported under this Agreement, review code for which Supplier has or is permitted access, to find and remediate security vulnerabilities. |
|
43. |
|
Perform quality assurance testing for the application functionality and security components (e.g. testing of authentication, authorization, and accounting functions, as well as any other activity designed to validate the security architecture). |
|
|
|
|
|
Privacy Issues |
||
|
|
||
|
44. |
|
NOT publicly disclose, sell, rent, lend, trade or lease any AT&T Information (including, Information obtained on AT&T’s behalf). |
|
45. |
|
Restrict access to any Personally Identifiable Information to authorized individuals. |
|
|
|
|
|
Monitoring and Auditing Controls |
||
|
|
||
|
46. |
|
Restrict access to security logs to authorized individuals. |
|
47. |
|
Regularly review security logs for anomalies and document and resolve all logged security problems in a timely manner. |
|
48. |
|
Keep security logs for a minimum of six (6) months. |
Proprietary and Confidential
This Agreement and information contained therein is not for use or disclosure outside of AT&T, its Affiliates, and third party representatives, and Supplier except under written agreement by the contracting Parties.
6
|
49. |
|
Provide, and hereby provides to AT&T audit rights to verify Supplier’s compliance with its contractual obligations in connection with these AT&T Supplier Information Security Requirements. Upon AT&T’s request for audit, Supplier shall schedule an audit to commence within thirty (30) days from such request. In the event AT&T, in its sole discretion, deems a security breach has occurred, Supplier shall schedule the audit to commence within one (1) day of AT&T’s notice requiring an audit. This provision shall not be deemed to, and shall not limit any more stringent audit obligations permitting the examination of Supplier’s records contained in this Agreement. |
|
50. |
|
Provide AT&T within thirty (30) days from the publication of the audit report identifying any noncompliance with the contractual security requirements, a written report of completed or proposed corrective actions and implementation timeframes unless otherwise stipulated herein, as soon as possible, but not to exceed ninety (90) days addressing each noncompliance found within the audit. Supplier shall provide periodic, at least monthly, updates to AT&T on the implementation of the corrective action plan in order to track the work to completion. |
|
|
|
|
|
Reporting Violations |
||
|
|
||
|
51. |
|
Have and utilize a documented procedure to follow when an unauthorized intrusion or other security violation, including but not limited to, a physical security or computer security incident (e.g. hacker or attempted hacker activity or the introduction or attempted introduction of a virus or malicious code), is suspected which includes immediate notification to the AT&T Computer Security Incident Response Team (ACSIRT). |
|
|
|
ACSIRT 24 hour contact information: |
|
|
|
· Phone: 0 000 000-0000, prompt 8 (U.S.) |
|
|
|
· Phone: 0 000 000-0000 (International) |
|
52. |
|
In addition to providing AT&T with immediate notice of any security incident, provide AT&T with regular status updates including but not limited to actions taken to resolve such incident, at four-hour intervals (or at other mutually agreed intervals or times) for the duration of the incident, and within five days of the closure of the incident, a written report describing the incident, actions taken by the Supplier during its response and the Supplier’s plans for future actions to prevent a similar incident from occurring in the future. |
|
|
|
|
|
Software Development and Implementation |
||
|
|
||
|
53. |
|
Ensure, prior to furnishing or development of software that such software incorporates applicable AT&T security requirements. |
|
|
||
|
Interconnectivity |
||
|
|
||
|
54. |
|
Use only the AT&T Chief Security Office (CSO) approved facilities and connection methodologies to interconnect AT&T’s data facilities with Supplier’s data facilities and to provide access to the data for each connection. |
|
55. |
|
NOT establish interconnection to endpoint resources other than in the United States. Interconnections to endpoint resources other than in the United States require the express prior written consent of AT&T. |
|
56. |
|
Permit limited access to Information Resources and the transmission of Information only to those individuals necessary to carry out the intent and purpose of the Agreement. |
|
57. |
|
Maintain logs of user sessions (including application to application sessions) involving access to AT&T. These logs must include: login identification, user request records, system configuration, and timestamps and/or duration of access. These logs must be retained for six (6) months. |
|
58. |
|
Provide AT&T access to any Supplier facilities during normal business hours for the maintenance and support of any AT&T equipment (e.g. router) used for the transmission of Information under this Agreement. |
Proprietary and Confidential
This Agreement and information contained therein is not for use or disclosure outside of AT&T, its Affiliates, and third party representatives, and Supplier except under written agreement by the contracting Parties.
7
|
59. |
|
Use any AT&T equipment provided under this Agreement only for the furnishing of those services explicitly defined in this Agreement. |
|
60. |
|
Consent and hereby consents to AT&T’s gathering of information relating to Supplier’s access to AT&T networks, processing systems and applications. This information may be collected, retained and analyzed by AT&T to identify potential security risks without further notice. This information may include trace files, statistics, network addresses, and the actual data or screens accessed or transferred. |
|
61. |
|
Ensure that all Supplier interconnections to AT&T pass through the designated AT&T perimeter security gateway (e.g. firewall). |
|
62. |
|
Ensure that Supplier interconnections to AT&T must terminate at a perimeter security gateway (e.g. firewall) at the Supplier end of the connection. |
|
63. |
|
Consent and hereby provides advance consent to AT&T’s immediately suspending or terminating any interconnection if AT&T, in its sole discretion, believes there has been a breach of security or unauthorized access to or misuse of AT&T data facilities or Information. (Notwithstanding the foregoing, AT&T does not require Supplier’s consent to terminate in whole or in part any connection if AT&T believes, in its sole discretion, that disconnection is warranted.) |
|
|
|
|
|
Security Policies and Procedures |
||
|
|
||
|
64. |
|
Ensure that all personnel, subcontractors or representatives performing work on any AT&T resources or the resources used to interconnect to AT&T resources or the resources used to house AT&T or AT&T Branded Information under this Agreement are in compliance with these Information Security Requirements. |
|
65. |
|
Notify AT&T of any policy changes that could impact the security controls put in place to secure AT&T’s data. |
|
66. |
|
Periodically review these Information Security Requirements to ensure that Supplier is in compliance with the requirements. |
|
67. |
|
Return all AT&T owned or provided access devices (including SecurID tokens, information storage devices, software, and/or computer equipment, as soon as practicable, but in no event more than fifteen (15) business days after AT&T provides Supplier with specific, written instructions for the return thereof (including without limitation the destination for such return) following the sooner of: (a) expiration or termination of the Agreement; (b) AT&T’s request for the return of such property; or (c) when Supplier (or its suppliers or representatives) no longer need such property. If AT&T fails to provide such instructions within fifteen (15) business days after Supplier’s request for such instructions, then all such tokens, devices, software, and equipment shall be returned to the current AT&T Business Unit contact at the location on file with Startek. |
Proprietary and Confidential
This Agreement and information contained therein is not for use or disclosure outside of AT&T, its Affiliates, and third party representatives, and Supplier except under written agreement by the contracting Parties.
8