THE SYMBOL “[*]” INDICATES MATERIAL WHERE CERTAIN IDENTIFIED INFORMATION HAS BEEN EXCLUDED FROM THE EXHIBIT BECAUSE IT IS BOTH (i) NOT MATERIAL AND (ii) WOULD LIKELY CAUSE COMPETITIVE HARM TO THE COMPANY IF PUBLICLY DISCLOSED. Amendment 2 To Agreement...
EXHIBIT 4.a.4
Agreement No. 53258.A.002
THE SYMBOL “[*]” INDICATES MATERIAL WHERE CERTAIN IDENTIFIED INFORMATION HAS BEEN EXCLUDED FROM THE EXHIBIT BECAUSE IT IS BOTH (i) NOT MATERIAL AND (ii) WOULD LIKELY CAUSE COMPETITIVE HARM TO THE COMPANY IF PUBLICLY DISCLOSED.
To
Agreement No. 53258.C
between
AT&T Services, Inc.
and
Amdocs Development Limited
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
1
Agreement No. 53258.A.002
AMENDMENT ▇▇.▇
▇▇
▇▇▇▇▇▇▇▇▇ ▇▇. ▇▇▇▇▇.▇
This Amendment No. 2, effective as of the last date signed by a Party (“Effective Date”) and amending Agreement No. 53258.C, is by and between Amdocs Development Limited, a Cyprus corporation (hereinafter referred to as “Supplier” or “Amdocs”), and AT&T Services, Inc., a Delaware corporation (hereinafter referred to as “AT&T”), each of which may be referred to in the singular as a “Party” or in the plural as the “Parties.”
WITNESSETH
WHEREAS, Supplier and AT&T are parties to the Master Services Agreement No.53258.C entered into on/with the effective date of on February 28, 2017 (as previously amended, the “Agreement”); and
WHEREAS, Supplier and AT&T now desire to amend the Agreement as hereinafter set forth.
NOW, THEREFORE, in consideration of the premises and the covenants hereinafter contained, the Parties hereto agree as follows:
| 1. | As of the Effective Date of this Amendment No. 2, Section 3.10 “Technology Standards” is hereby amended to add the following as subsection g: |
| ▇. | ▇▇▇▇ Terms |
| 1. | For purposes of this Section, “▇▇▇▇” means any and all freeware Open Source Software or shareware used or included in, or combined by or on behalf of Supplier with, the deliverables or otherwise provided by or on behalf of Supplier under this Agreement; and a “▇▇▇▇ Disclosure” means a complete, current, and accurate listing of all ▇▇▇▇, which identifies for each ▇▇▇▇ component: (i) the component name; (ii) its version or release number; (iii) its web site URL of origin; (iv) the applicable software license and its version number; (v) the URL where Supplier identifies or sets forth the applicable software license and (vi) a brief (e.g., one-line) description of the purpose of the component; (vii) how the component is linked within the Deliverables or as otherwise provided. A ▇▇▇▇ Disclosure may be provided in the form of a web site made accessible to AT&T where Supplier posts the foregoing information. |
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
2
Agreement No. 53258.A.002
| 2. | Upon AT&T’s request, but not more than once a year, Supplier shall promptly, but in any event within sixty (60) days of such request, furnish to AT&T a ▇▇▇▇ Disclosure that is complete, current and accurate when furnished. For the avoidance of doubt, such ▇▇▇▇ Disclosure will govern deliverables provided under an Order issued after the Effective Date of this Amendment. Neither response nor non-response by AT&T concerning the receipt or non-receipt of any ▇▇▇▇ Disclosure or any reference to ▇▇▇▇ in the Agreement shall be deemed as acceptance, approval or acquiescence by AT&T that Supplier’s use of the ▇▇▇▇ complies with the legal requirements of applicable ▇▇▇▇ license(s), or is suitable for the intent and purposes furnished hereunder. After receiving any ▇▇▇▇ Disclosure, [*]. |
| 3. | If the term “Viral Open Source Software” is defined elsewhere in this Agreement, then in the event of any conflict between the provisions of this Section and any representations or warranties concerning Viral Open Source Software that may appear elsewhere in this Agreement, this Section shall take precedence. |
| 2. | As of the Effective Date of this Amendment No. 2, Section 3.43.c “Additional Supplier Warranties” is hereby amended to add the following as subsection vii: |
| vii. | Supplier has (i) satisfied all its obligations to any third parties with respect to all ▇▇▇▇ and the applicable ▇▇▇▇ licenses (including, for example, any obligation to make publicly available the ▇▇▇▇ source code for modifications to such ▇▇▇▇); (ii) that use of the ▇▇▇▇ in such form for such intent and purposes in no manner creates any added obligation on the part of AT&T (including, for example, the payment of any additional monies), or diminishes, conditions or eliminates any of the rights, title, or interest that Supplier grants AT&T in or to any Deliverables or that Supplier may otherwise provide AT&T under this Agreement; and (iii) that use of the ▇▇▇▇ in such form for such intent and purposes, including, but not limited to, AT&T’s use or combination of the ▇▇▇▇, in the form provided to AT&T, with any proprietary software of AT&T or AT&T’s third-party suppliers, does not subject AT&T to any obligation of disclosure or distribution to any third party or to the public of any such proprietary software, or otherwise make such proprietary software subject to the terms of any ▇▇▇▇ license or impair AT&T’s or its third-party suppliers’ rights, title, or interest in or to such proprietary software. |
| 3. | As of the Effective Date of this Amendment No. 2, Section 3.15 “Indemnity” is hereby amended to add the following as subsection h: |
| h. | In the event that AT&T notifies Supplier or Supplier becomes aware of Supplier’s noncompliance with any ▇▇▇▇ license term, then in either case, Supplier shall use all reasonable efforts promptly to cure such noncompliance so as to eliminate risks of public disclosure of proprietary software and prevent |
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
3
Agreement No. 53258.A.002
| disruption of any AT&T business activity. Supplier shall promptly notify AT&T of all actions taken by Supplier to cure such noncompliance. Should AT&T receive notice from any third party alleging acts or omissions which, notwithstanding AT&T’s use of the ▇▇▇▇ for the intent and purposes furnished hereunder, constitute noncompliance with any ▇▇▇▇ license term, then promptly upon AT&T’s notice to Supplier of such allegation, Supplier shall indemnify, defend and hold harmless AT&T against such allegation in accordance with Supplier’s obligations to do so as set forth elsewhere in this Agreement, in a manner that preserves any proprietary software of AT&T or its third-party suppliers from any public disclosure obligation or any other ▇▇▇▇ license noncompliance allegations. |
| 4. | Section 3.21 Limitation of Damages is hereby amended by adding the words “or Access” at the end of subparagraphs a.(ii) and b.(ii). |
| 5. | Section 4.1 Access is hereby deleted and replaced in its entirety with Section 4.1 Access to AT&T Premises and Non-Public Information Systems as follows: |
4.1 Access to AT&T Premises and Non-Public Information Systems
| a. | When appropriate, Supplier Representatives shall have reasonable access to AT&T’s premises during normal business hours, and at such other times as may be agreed upon by the Parties, to enable Supplier to perform its obligations under this Agreement. Supplier shall coordinate such access with AT&T. Where required by governmental regulations, Supplier shall submit satisfactory clearance from the U.S. Department of Defense and/or other federal, state or local authorities. |
| b. | Supplier shall ensure that Supplier Representatives, while on or off AT&T’s premises, (i) protect AT&T’s materials, buildings and structures, (ii) perform Services which do not unreasonably interfere with AT&T’s business operations, and (iii) perform such Services with care and due regard for the safety, convenience and protection of AT&T, its employees, and property. |
| c. | AT&T may require Supplier Representatives to exhibit AT&T-issued identification credentials, to gain unescorted access to AT&T’s premises for the performance of Services. In addition, if any Supplier Representatives requires access to AT&T’s Nonpublic Information Resources (as defined in the AT&T Supplier Information Security Requirements) Supplier must obtain from AT&T an ATT UID for each such Supplier Representative. ATT UIDs are provisioned upon successful opening of a worker record within the vendor management system (VMS). Supplier Representatives |
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
4
Agreement No. 53258.A.002
| shall also exhibit their company’s photo identification, if any. If, for any reason, any Supplier Representative is no longer performing Services or no longer has a need to have access to AT&T’s Nonpublic Information Resources, then Supplier shall immediately close the Supplier Representatives record in the VMS and promptly return any AT&T-issued identification credentials. In cases where a Supplier Representatives is being removed due to misconduct involving work at AT&T, Supplier will immediately inform the AT&T sponsoring manager of the nature of the misconduct. |
| d. | AT&T currently uses a third-party VMS vendor and reserves the right to change the VMS vendor at any time and from time to time. Supplier shall enter into an agreement with AT&T’s designated VMS vendor, at no cost to AT&T, and supply any information about its Supplier Representatives reasonably required by the VMS vendor to create a worker record and enable provisioning of identification credentials and ATT UIDs. If Supplier fails to enter into an agreement with AT&T’s VMS vendor to use the VMS, Supplier’s Supplier Representatives will not be allowed access to AT&T’s premises (other than on an escorted basis) or to AT&T’s Nonpublic Information Resources. AT&T reserves the right to restrict Supplier or Supplier Representatives’ access to AT&T’s facilities and/or Nonpublic Information Resources, without liability to AT&T, until AT&T is satisfied that Supplier is compliant with its obligations under this Section. |
| e. | Supplier shall ensure that information provided to AT&T or the VMS vendor for its Supplier Representatives is 1) input accurately into the VMS (including the SSN/Security ID for the Supplier Representatives, the Agreement number in the “Contract or PO #” field as it may be changed, the start and end dates (end date must not be after the expiration date of the Agreement), and the worker classification obtained from the AT&T sponsoring manager), 2) maintained properly throughout the term of the engagement, and 3) closed on a timely basis upon the termination or expiration of the engagement or the need for the Supplier Representatives to have access to AT&T’s premises or Nonpublic Information Resources. Supplier shall not enable or allow any Supplier Representatives to let anyone else use the AT&T identification credentials or an ATT UID issued to that Supplier Representatives to gain access to AT&T premises or Nonpublic Information Resources. |
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
5
Agreement No. 53258.A.002
| 6. | Appendix B, Exhibit 1 – For Orders requiring signature is hereby deleted in its entirety and the attached Appendix B, Exhibit 1 – For Orders requiring signature is inserted in lieu thereof. |
| 7. | Appendix B, Exhibit 2 – For use when issuing a Purchase Order is hereby deleted in its entirety and the attached Appendix B, Exhibit 1 – For use when issuing a Purchase Order is inserted in lieu thereof. |
| 8. | Appendix C – Offshore Locations is hereby deleted in its entirety and the attached Appendix C – Offshore Locations is inserted in lieu thereof. |
| 9. | Appendix D – Security and Offshore Requirements: is hereby deleted in its entirety and the attached Appendix D – Security and Offshore Requirements: is inserted in lieu thereof. |
| 10. | The terms and conditions of the Agreement in all other respects remain unmodified and in full force and effect. |
Original signatures transmitted and received via facsimile or other electronic transmission of a scanned document, (e.g., ..pdf or similar format) are true and valid signatures for all purposes hereunder and shall bind the Parties to the same extent as that of an original signature. This Amendment may be executed in multiple counterparts, each of which shall be deemed to constitute an original but all of which together shall constitute only one document.
IN WITNESS WHEREOF, the Parties have caused this Amendment to Agreement No. 53258.C to be executed, as of the date the last Party signs.
| Amdocs Development Limited | AT&T Services, Inc. | |||||||
| By: |
|
By: |
| |||||
| Name: |
|
Name: | ▇▇▇▇▇ ▇▇▇▇▇▇▇▇▇ | |||||
| Title: |
|
Title: | Sr. Sourcing Manager | |||||
| Date: |
|
Date: |
| |||||
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
6
Agreement No. 53258.A.002
Appendix B, Exhibit 1 – For Orders requiring signature
Order
No. 53258.W.<XXX>
Between
Amdocs Development Limited
And
AT&T Services, Inc.
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
7
Agreement No. 53258.A.002
Order
This Order is by and between Amdocs Development Limited, a Cyprus corporation (“Supplier” or “Amdocs”), and AT&T Services, Inc., a Delaware corporation (“AT&T”), and shall be governed pursuant to the terms and conditions of Master Services Agreement Number 53258.C (as amended, the “Master Services Agreement”), which by this reference are incorporated as if fully set forth herein. Any terms and conditions in this Order that vary from or are inconsistent with the terms and conditions of the Master Services Agreement shall apply to this Order only, and shall survive the termination or expiration of the Master Services Agreement.
| 1. | AT&T Agreement Number: 53258.W.<XXX> must appear on all invoices |
| Amdocs Order Number: <Enter No.> |
| 2. | Term of Services: Effective dates are <Month, DD, YYYY>, through <Month, DD, YYYY>. |
| 3. | Project Name and Description: <Enter Details> |
| 4. | The Custom Software and Program Material and/or Scope of Other Services Ordered: |
| This Order is to <Enter specific details> |
| 5. | Third Party Software: <Enter here if any; “None” is acceptable> |
| 6. | Additional Items Ordered: <Enter here if any; “None” is acceptable> |
| 7. | Milestones/Resources: |
| a. | Milestones: |
Planned milestones as of the Effective Date of this Order are as follows:
<Table below is an example and may be modified as required>
| Milestone No. |
Description |
Date | ||
| 1 |
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
8
Agreement No. 53258.A.002
| b. | Offshore Resources: |
Amdocs Offshore resources working on this Order may be located at AT&T-approved locations found in the Master Services Agreement, and at the following address(es):
<Address Number Street and Room>
<City, State/Province Zip>
<Country>
Amdocs Offshore resources can only access AT&T Systems/data in accordance with the Master Services Agreement, Appendix D, “Security and Offshore Requirements”.
| c. | USA-Based Resources: |
Amdocs USA-based resources shall work pursuant to the general directions provided by AT&T to Amdocs towards the assigned milestones but shall not in any way be deemed to be employees of AT&T.
| d. | Staffing Details: |
Planned roles and full time equivalent (“FTE”) resources needed:
<Table below is an example and may be modified as required>
| Role |
USA-Based FTEs |
Offshore FTEs |
Total |
| 8. | Deliverables/Release Items: |
Amdocs will provide the deliverables and/or release items for the Project as defined in this Section and the table below.
<Table below is an example and may be modified as required>
| Milestone No. |
Deliverable |
Description |
Estimated Delivery Date |
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
9
Agreement No. 53258.A.002
| 9. | Application Components: <Enter details below, “None” is acceptable and delete table> |
The following applications are included in the scope of this Order.
| MOTS ID |
Application Name |
% of time spent on Application |
||||||
| Total |
100 | % | ||||||
| 10. | Amdocs Responsibilities: <Enter details below, “None” is acceptable> |
In addition to providing the deliverables herein, Amdocs will be responsible for the following:
| • | <List additional Amdocs Responsibilities> |
| 11. | AT&T Responsibilities: <Enter details below, “None” is acceptable> |
In addition to AT&T Responsibilities defined in Section 3.43f of the Master Services Agreement, AT&T will be responsible for the following:
| • | <List additional AT&T Responsibilities> |
| 12. | Compensation: |
This is a <fixed price or Time and Materials (“T&M”)> Order for the total amount of <Enter amount> for the Work effort. The total price is based on <Enter basis for pricing, e.g. rate, monthly or hourly, any proration, and/or assumed hours>.
<Enter Travel and living expenses language in accordance with the Master Services Agreement, if applicable>
The following table represents the payment schedule for this Order:
Payment Schedule:
<Table below is an example and may be modified as required>
| Activity During |
FTEs | Rate | Total Invoice | Invoice Date | ||||||||||||
| Total |
||||||||||||||||
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
10
Agreement No. 53258.A.002
| 13. | Project Managers: |
AT&T:
<AT&T Contact Name>
<Title>
<Street and Room>
<City, State Zip>
<▇▇▇▇▇@▇▇▇.▇▇▇>
Amdocs:
<Amdocs PM Contact Name>
<Title>
<Street and Room>
<City, State Zip>
<▇▇▇▇▇@▇▇▇▇▇▇.▇▇▇>
| 14. | Special Terms and Conditions: |
| a. | Invoice/Billing |
Invoices and billing information are to be sent electronically to:
<Enter applicable AT&T Business Unit/Finance Name>: <▇▇▇▇▇@▇▇▇.▇▇▇>
Copies of all invoices are to be sent to:
<AT&T Contact Name>
<Title>
<Street and Room>
<City, State Zip>
<▇▇▇▇▇@▇▇▇.▇▇▇>
AT&T will notify Amdocs of any changes regarding invoices and billing information at <Enter Phone Number (xxx)xxx-xxxx> or email: <▇▇▇▇@▇▇▇▇▇▇.▇▇▇>.
| 15. | Liquidated Damages for Delay in Delivery: |
Delayed Delivery Dates under this Custom Software Order shall be handled in accordance with Section 4.9, “Liquidated Damages for Delay in Delivery,” of the Master Services Agreement.
| 16. | Error Severity Level Description And Resolution Plan: |
Errors found in the Custom Software or Ongoing Support provided under this Order shall be handled in accordance with Section 4.8, “Error Severity Level Description And Resolution Plan,” of the Master Services Agreement.
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
11
Agreement No. 53258.A.002
| 17. | Payment Terms: |
Payment terms for invoices issued under this Order shall be in accordance with Section 3.19, “Invoicing and Payment,” of the Master Services Agreement, which is, as of the Effective Date of this Order, net days from the date of receipt of the invoice.
| 18. | Ownership of Paid-For Development: |
For the avoidance of doubt, and for purposes of interpreting AT&T’s right to Program Material and Documentation created hereunder, title to all Work output hereunder shall be determined in accordance with the Master Services Agreement, Section 3.27, “Ownership of Paid-For Development, Use and Reservation of Rights”.
| 19. | Information: |
In addition to all other rights provided by Section 3.16, “Information”, pursuant to the Master Services Agreement, any Information received by Amdocs from AT&T or other parties engaged in this Work shall be considered and treated as confidential Information under the Order, regardless of any requirement to put it in writing under the Master Services Agreement or separate Non-Disclosure Agreement (NDA).
| 20. | Termination: |
The Termination and Partial Termination provisions applicable to this Order are contained in Section 3.36, “Termination”, of the Master Services Agreement.
IN WITNESS WHEREOF, the Parties have caused this Order to be executed as of the Effective Date.
| Amdocs Development Limited | AT&T Services, Inc. | |||||||
| By: |
|
By: | ||||||
| Name: | <Supplier Signatory Name> | Name: | <AT&T Signatory Name> | |||||
| Title: | <Supplier Signatory Title> | Title: | <AT&T Signatory Title> | |||||
| Date: |
|
Date: |
| |||||
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
12
Agreement No. 53258.A.002
Appendix B, Exhibit 2 – For use when issuing a Purchase Order
Statement of Work
No. 53258.Z.<XXX>
Between
Amdocs Development Limited.
And
AT&T Services, Inc.
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
13
Agreement No. 53258.A.002
Statement of Work
This Statement of Work (“SOW”) is by and between Amdocs Development Limited, a Cyprus corporation (“Supplier” or “Amdocs”), and AT&T Services, Inc., a Delaware corporation (“AT&T”), and shall become a part of a Purchase Order which is governed pursuant to the terms and conditions of Master Services Agreement Number 53258.C (as amended, the “Master Services Agreement”), which by this reference are incorporated as if fully set forth herein. Any terms and conditions in this SOW that vary from or are inconsistent with the terms and conditions of the Master Services Agreement shall apply to this SOW only, and shall survive the Termination or expiration of the Master Services Agreement.
For the avoidance of doubt, terms and conditions preprinted on any Purchase Order, Purchase Order acceptance or acknowledgement (if any) shall not be given any effect as they are superseded by the terms and conditions herein.
| 1. | AT&T Agreement Number: 53258. Z.<XXX> must appear on all invoices |
| Amdocs Order Number: <Enter No.> |
| 2. | Term of Services: Effective dates are <Month, DD, YYYY>, through <Month, DD, YYYY>. |
| 3. | Project Name and Description: <Enter Details> |
| 4. | The Custom Software and Program Material and/or Scope of Other Services Ordered: |
| This SOW is to <Enter specific details> |
| 5. | Third Party Software: <Enter here if any; “None” is acceptable> |
| 6. | Additional Items Ordered: <Enter here if any; “None” is acceptable> |
| 7. | Milestones/Resources: |
| a. | Milestones: |
Planned milestones as of the Effective Date of this SOW are as follows:
<Table below is an example and may be modified as required>
| Milestone No. |
Description |
Date | ||
| 1 |
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
14
Agreement No. 53258.A.002
| b. | Offshore Resources: |
Amdocs Offshore resources working on this SOW may be located at AT&T-approved locations found in the Master Services Agreement, and at the following address(es):
<Address Number Street and Room>
<City, State/Province Zip>
<Country>
Amdocs Offshore resources can only access AT&T Systems/data in accordance with the Master Services Agreement, Appendix D, “Security and Offshore Requirements”.
| c. | USA-Based Resources: |
Amdocs USA-based resources shall work pursuant to the general directions provided by AT&T to Amdocs towards the assigned milestones but shall not in any way be deemed to be employees of AT&T.
| d. | Staffing Details: |
Planned roles and full time equivalent (“FTE”) resources needed:
<Table below is an example and may be modified as required>
| Role |
USA-Based FTEs |
Offshore FTEs |
Total |
| 8. | Deliverables/Release Items: |
Amdocs will provide the deliverables and/or release items for the Project as defined in this Section and the table below.
<Table below is an example and may be modified as required>
| Milestone No. |
Deliverable |
Description |
Estimated Delivery Date |
| 9. | Application Components: <Enter details below, “None” is acceptable and delete table> |
The following applications are included in the scope of this SOW.
| MOTS ID |
Application Name | % of time spent on Application | ||||||
| Total |
|
100 | % | |||||
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
15
Agreement No. 53258.A.002
| 10. | Amdocs Responsibilities: <Enter details below, “None” is acceptable> |
In addition to providing the deliverables herein, Amdocs will be responsible for the following:
| • | <List additional Amdocs Responsibilities> |
| 11. | AT&T Responsibilities: <Enter details below, “None” is acceptable> |
In addition to AT&T Responsibilities defined in Section 3.43f of the Master Services Agreement, AT&T will be responsible for the following:
| • | <List additional AT&T Responsibilities> |
| 12. | Compensation: |
This is a <fixed price or Time and Materials (“T&M”)> SOW for the total amount of <Enter amount> for the Work effort. The total price is based on <Enter basis for pricing, e.g. rate, monthly or hourly, any proration, and/or assumed hours>.
<Enter Travel and living expenses language in accordance with the Master Services Agreement, if applicable>
The following table represents the payment schedule for this SOW:
Payment Schedule:
<Table below is an example and may be modified as required>
| Activity During |
FTEs | Rate | Total Invoice | Invoice Date |
||||||||||||
| Total |
||||||||||||||||
| 13. | Project Managers: |
AT&T:
<AT&T Contact Name>
<Title>
<Street and Room>
<City, State Zip>
<▇▇▇▇▇@▇▇▇.▇▇▇>
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
16
Agreement No. 53258.A.002
Amdocs:
<Amdocs PM Contact Name>
<Title>
<Street and Room>
<City, State Zip>
<▇▇▇▇▇@▇▇▇▇▇▇.▇▇▇>
| 14. | Special Terms and Conditions: |
| a. | Invoice/Billing |
Invoices and billing information are to be sent electronically to:
<Enter applicable AT&T Business Unit/Finance Name>: <▇▇▇▇▇@▇▇▇.▇▇▇>
Copies of all invoices are to be sent to:
<AT&T Contact Name>
<Title>
<Street and Room>
<City, State Zip>
<▇▇▇▇▇@▇▇▇.▇▇▇>
AT&T will notify Amdocs of any changes regarding invoices and billing information at <Enter Phone Number (xxx)xxx-xxxx> or email: <▇▇▇▇@▇▇▇▇▇▇.▇▇▇>.
| 15. | Liquidated Damages for Delay in Delivery: |
Delayed Delivery Dates under this Custom Software SOW shall be handled in accordance with Section 4.9, “Liquidated Damages for Delay in Delivery,” of the Master Services Agreement.
| 16. | Error Severity Level Description And Resolution Plan: |
Errors found in the Custom Software or Ongoing Support provided under this SOW shall be handled in accordance with Section 4.8, “Error Severity Level Description And Resolution Plan,” of the Master Services Agreement.
| 17. | Payment Terms: |
Payment terms for invoices issued under this SOW shall be in accordance with Section 3.19, “Invoicing and Payment” of the Master Services Agreement, which is, as of the Effective Date of this SOW, net days from the date of receipt of the invoice.
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
17
Agreement No. 53258.A.002
| 18. | Ownership of Paid-For Development: |
For the avoidance of doubt, and for purposes of interpreting AT&T’s right to Program Material and Documentation created hereunder, title to all Work output hereunder shall be determined in accordance with the Master Services Agreement, Section 3.27, “Ownership of Paid-For Development, Use and Reservation of Rights”.
| 19. | Information: |
In addition to all other rights provided by Section 3.16, “Information”, pursuant to the Master Services Agreement, any Information received by Amdocs from AT&T or other parties engaged in this Work shall be considered and treated as confidential Information under the SOW, regardless of any requirement to put it in writing under the Master Services Agreement or separate Non-Disclosure Agreement (NDA).
| 20. | Termination: |
The Termination and Partial Termination provisions applicable to this SOW are contained in Section 3.36, “Termination”, of the Master Services Agreement.
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
18
Agreement No. 53258.A.002
Appendix C – Offshore Locations
The Parties agree that the following are AT&T-approved locations as of the Effective Date of this Agreement and any modifications to this list shall be managed in accordance with Section 3.24.
| Country(ies) where services are authorized by AT&T to be performed (physical location address is also required if the Services involve Information Technology-related work or if a “virtual” or “work-from-home” address is authorized) |
City(ies) where services will be performed for AT&T |
Services to be performed at approved Physical Location |
Name of Supplier / Supplier Affiliate, and/ or Subcontractor performing the services | |||||
| Brazil |
[*] | [*] | [*] | [*] | ||||
| Brazil |
[*] | [*] | [*] | [*] | ||||
| Brazil |
[*] | [*] | [*] | [*] | ||||
| Brazil |
[*] | [*] | [*] | [*] | ||||
| Brazil |
[*] | [*] | [*] | [*] |
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
19
Agreement No. 53258.A.002
| Country(ies) where services are authorized by AT&T to be performed (physical location address is also required if the Services involve Information Technology-related work or if a “virtual” or “work-from-home” address is authorized) |
City(ies) where services will be performed for AT&T |
Services to be performed at approved Physical Location |
Name of Supplier / Supplier Affiliate, and/ or Subcontractor performing the services | |||||
| Brazil |
[*] | [*] | [*] | [*] | ||||
| Brazil |
[*] | [*] | [*] | [*] | ||||
| Brazil |
[*] | [*] | [*] | [*] | ||||
| Brazil |
[*] | [*] | [*] | [*] | ||||
| Canada |
[*] | [*] | [*] | [*] | ||||
| Canada |
[*] | [*] | [*] | [*] | ||||
| Cyprus |
[*] | [*] | [*] | [*] | ||||
| Cyprus |
[*] | [*] | [*] | [*] | ||||
| India |
[*] | [*] | [*] | [*] |
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
20
Agreement No. 53258.A.002
| Country(ies) where services are authorized by AT&T to be performed (physical location address is also required if the Services involve Information Technology-related work or if a “virtual” or “work-from-home” address is authorized) |
City(ies) where services will be performed for AT&T |
Services to be performed at approved Physical Location |
Name of Supplier / Supplier Affiliate, and/ or Subcontractor performing the services | |||||
| India |
[*] | [*] | [*] | [*] | ||||
| India |
[*] | [*] | [*] | [*] | ||||
| India |
[*] | [*] | [*] | [*] | ||||
| India |
[*] | [*] | [*] | [*] | ||||
| India |
[*] | [*] | [*] | [*] | ||||
| India |
[*] | [*] | [*] | [*] | ||||
| India |
[*] | [*] | [*] | [*] | ||||
| India |
[*] | [*] | [*] | [*] | ||||
| India |
[*] | [*] | [*] | [*] | ||||
| India |
[*] | [*] | [*] | [*] |
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
21
Agreement No. 53258.A.002
| Country(ies) where services are authorized by AT&T to be performed (physical location address is also required if the Services involve Information Technology-related work or if a “virtual” or “work-from-home” address is authorized) |
City(ies) where services will be performed for AT&T |
Services to be performed at approved Physical Location |
Name of Supplier / Supplier Affiliate, and/ or Subcontractor performing the services | |||||
| India |
[*] | [*] | [*] | [*] | ||||
| India |
[*] | [*] | [*] | [*] | ||||
| India |
[*] | [*] | [*] | [*] | ||||
| India |
[*] | [*] | [*] | [*] | ||||
| India |
[*] | [*] | [*] | [*] | ||||
| India |
[*] | [*] | [*] | [*] | ||||
| India |
[*] | [*] | [*] | [*] | ||||
| India |
[*] | [*] | [*] | [*] | ||||
| India |
[*] | [*] | [*] | [*] | ||||
| India |
[*] | [*] | [*] | [*] | ||||
| India |
[*] | [*] | [*] | [*] | ||||
| India |
[*] | [*] | [*] | [*] |
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
22
Agreement No. 53258.A.002
| Country(ies) where services are authorized by AT&T to be performed (physical location address is also required if the Services involve Information Technology-related work or if a “virtual” or “work-from-home” address is authorized) |
City(ies) where services will be performed for AT&T |
Services to be performed at approved Physical Location |
Name of Supplier / Supplier Affiliate, and/ or Subcontractor performing the services | |||||
| India |
[*] | [*] | [*] | [*] | ||||
| India |
[*] | [*] | [*] | [*] | ||||
| India |
[*] | [*] | [*] | [*] | ||||
| India |
[*] | [*] | [*] | [*] | ||||
| India |
[*] | [*] | [*] | [*] | ||||
| India |
[*] | [*] | [*] | [*] | ||||
| India |
[*] | [*] | [*] | [*] | ||||
| India |
[*] | [*] | [*] | [*] | ||||
| India |
[*] | [*] | [*] | [*] | ||||
| India |
[*] | [*] | [*] | [*] | ||||
| India |
[*] | [*] | [*] | [*] | ||||
| India |
[*] | [*] | [*] | [*] | ||||
| India |
[*] | [*] | [*] | [*] | ||||
| India |
[*] | [*] | [*] | [*] | ||||
| India |
[*] | [*] | [*] | [*] | ||||
| India |
[*] | [*] | [*] | [*] | ||||
| Israel |
[*] | [*] | [*] | [*] |
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
23
Agreement No. 53258.A.002
| Country(ies) where services are authorized by AT&T to be performed (physical location address is also required if the Services involve Information Technology-related work or if a “virtual” or “work-from-home” address is authorized) |
City(ies) where services will be performed for AT&T |
Services to be performed at approved Physical Location |
Name of Supplier / Supplier Affiliate, and/ or Subcontractor performing the services | |||||
| Israel |
[*] | [*] | [*] | [*] | ||||
| Israel |
[*] | [*] | [*] | [*] | ||||
| Israel |
[*] | [*] | [*] | [*] | ||||
| Israel |
[*] | [*] | [*] | [*] | ||||
| Israel |
[*] | [*] | [*] | [*] | ||||
| Israel |
[*] | [*] | [*] | [*] | ||||
| Israel |
[*] | [*] | [*] | [*] | ||||
| Israel |
[*] | [*] | [*] | [*] | ||||
| Mexico |
[*] | [*] | [*] | [*] | ||||
| Mexico |
[*] | [*] | [*] | [*] | ||||
| Mexico |
[*] | [*] | [*] | [*] | ||||
| Mexico |
[*] | [*] | [*] | [*] | ||||
| Mexico |
[*] | [*] | [*] | [*] |
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
24
Agreement No. 53258.A.002
| Country(ies) where services are authorized by AT&T to be performed (physical location address is also required if the Services involve Information Technology-related work or if a “virtual” or “work-from-home” address is authorized) |
City(ies) where services will be performed for AT&T |
Services to be performed at approved Physical Location |
Name of Supplier / Supplier Affiliate, and/ or Subcontractor performing the services | |||||
| Mexico |
[*] | [*] | [*] | [*] | ||||
| Mexico |
[*] | [*] | [*] | [*] | ||||
| Mexico |
[*] | [*] | [*] | [*] | ||||
| Mexico |
[*] | [*] | [*] | [*] | ||||
| Mexico |
[*] | [*] | [*] | [*] | ||||
| Mexico |
[*] | [*] | [*] | [*] |
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
25
Agreement No. 53258.A.002
| Country(ies) where services are authorized by AT&T to be performed (physical location address is also required if the Services involve Information Technology-related work or if a “virtual” or “work-from-home” address is authorized) |
City(ies) where services will be performed for AT&T |
Services to be performed at approved Physical Location |
Name of Supplier / Supplier Affiliate, and/ or Subcontractor performing the services | |||||
| UK |
[*] | [*] | [*] | [*] | ||||
| UK |
[*] | [*] | [*] | [*] |
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
26
Agreement No. 53258.A.002
Appendix D – Security and Offshore Requirements:
Supplier Information Security Requirements (“SISR”); Offshore Information Technology Services Requirements; Requirements for Offshore Information Technology Services Requiring Elevated Rights; and Limited Offshore Remote Access (“▇▇▇▇”)
| 1.0 | AT&T Supplier Information Security Requirements (SISR) – v6.3, January 2018 |
The following AT&T Supplier Information Security Requirements (“Security Requirements”) apply to Supplier Entities (as defined below) when performing any action, activity or work under the Agreement where any of the following occur (hereinafter referred to as “In-Scope Work”):
| 1. | The collection, storage, handling, backup, disposal, and/or access to In-Scope Information (as defined below); |
| 2. | Providing or supporting AT&T branded applications and/or services using non-AT&T Information Resources (as defined below); |
| 3. | Connectivity to AT&T’s Nonpublic Information Resources (as defined below); |
| 4. | The development or customization of any software for AT&T; or |
| 5. | Website hosting and development for AT&T and/or AT&T’s customers. |
These Security Requirements (i) are not intended to apply to products or applications acquired from the Supplier by AT&T for use by AT&T, and (ii) shall not limit more stringent security or other obligations set forth elsewhere in the Agreement.
Definitions:
Unless otherwise set forth in these Security Requirements, defined terms shall have the same meaning as set forth in the Agreement.
“Cloud Service” is a service delivered via an “as a Service” cloud service model, e.g., Software as a Service (SaaS), Storage as a Service (▇▇▇▇▇), Database as a Service (DBaaS), Platform as a Service (PaaS), and Infrastructure as a Service (IaaS).
“Demilitarized Zone” or “DMZ” is a network or sub-network that sits between a trusted internal network, such as a corporate private Local Area Network (LAN), and an untrusted external network, such as the Internet. A DMZ helps prevent outside users from gaining direct access to internal Information Resources. Inbound packets from the untrusted external network terminate within the DMZ and are not allowed to flow directly through to the trusted internal network. All inbound packets which flow to the trusted internal network originate within the DMZ.
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
27
Agreement No. 53258.A.002
“Information Resource(s)” means systems, applications, websites, networks, network elements, and other computing and information storage devices, along with the underlying technologies and delivery methods (e.g., social networks, mobile technologies, cloud services, call and voice recording, Application Program Interfaces (APIs)), used in connection with In-Scope Work.
“In-Scope Information” means confidential data, including, Sensitive Personal Information (SPI), Sensitive Customer Data (SCD), intellectual property, proprietary data and/or trade secret data of AT&T, data of others that AT&T is obligated to protect, general AT&T internal operational information, network architecture and/or engineering information, Customer Proprietary Network Information (CPNI), software source code for software developed or customized for AT&T, information security incident reports, nonpublic marketing and financial information, and AT&T end user customer contact lists.
“Mobile and Portable Devices” means mobile and/or portable computers, devices, media and systems capable of being easily carried, moved, transported or conveyed that are used in connection with In-Scope Work. Examples of such devices include laptop computers, tablets, USB hard drives, USB memory sticks, Personal Digital Assistants (PDAs), and mobile phones, such as smartphones.
“Multi-Factor Authentication” (also known as Two-Factor Authentication and Strong Authentication) means the use of at least two of the following three types of authentication factors:
| • | A physical or logical credential the user has, such as an electronically readable badge, a token card or a digital certificate; |
| • | A knowledge-based credential, such as a password or PIN; and |
| • | A biometric credential, such as a fingerprint or retina image. |
“Nonpublic Information Resources” means Information Resources used in connection with In-Scope Work that are not directly reachable from the public Internet.
“Privileged User” means a user with enhanced administrative permissions and/or expanded or super user access greater than that of a general user. Examples of such access include: system administration; the management of accounts, log reviews, encryption, databases, Security Gateways, Intrusion Detection Systems/Intrusion Prevention Systems (IDS/IPS), virtual machines (VM), networks, image instances, and APIs; Cloud Service Provider (CSP) management and security portals; and development and operations (DevOps) privileged activities. Privileged access by privileged users is applicable regardless of the types of devices and environments managed, including environments that are production, development, and test, within Supplier’s facilities and/or within CSP cloud environments.
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
28
Agreement No. 53258.A.002
“Sensitive Customer Data” or “SCD” means the data elements listed in the “Table 2—AT&T SCD Data Elements” located at the end of these Security Requirements. All data elements in Table 2 are considered In-Scope Information.
“Sensitive Personal Information” or “SPI” means the data elements listed in the “Table of AT&T SPI Data Elements” located at the end of these Security Requirements. All SPI Data Elements are considered In-Scope Information.
“Security Gateway” means a set of control mechanisms between two or more networks having different trust levels which filter and log traffic passing, or attempting to pass, between networks, and the associated administrative and management servers. Examples include firewalls, firewall management servers, hop boxes, session border controllers, proxy servers, and intrusion prevention devices.
“Strong Encryption” means the use of encryption technologies with minimum key lengths of 128-bits for symmetric encryption and 2048-bits for asymmetric encryption whose strength provides reasonable assurance that it will protect the encrypted information from unauthorized access and is adequate to protect the confidentiality and privacy of the encrypted information, and which incorporates a documented policy for the management of the encryption keys, including the expiration of encryption keys at least once every two years, and associated processes adequate to protect the confidentiality and privacy of the keys and credentials used as inputs to the encryption algorithm. Supplier must ensure that the rule of least privilege and separation of duties are properly implemented and maintained.
“Supplier Entity” or “Supplier Entities” means Supplier, its affiliates and subcontractors.
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
29
Agreement No. 53258.A.002
In accordance with the foregoing, Supplier shall, and shall cause Supplier Entities to:
System Security
| 1. | Actively monitor industry resources (e.g., ▇▇▇.▇▇▇▇.▇▇▇, pertinent software vendor mailing lists and websites, and information from subscriptions to automated notifications) for timely notification of all applicable security alerts that pertain to Information Resources. |
| 2. | At least quarterly scan Information Resources with industry-standard security vulnerability scanning software to detect security vulnerabilities, and remediate all critical, high, and medium risk security vulnerabilities identified. Scan must cover all Information Resources utilized to perform In-Scope Work. |
| 3. | Install and use Intrusion Detection Systems (IDS) and/or Intrusion Prevention Systems (IPS) that monitor all traffic entering and leaving Information Resources in connection with In-Scope Work. |
| 4. | Maintain and adhere to a documented process to remediate security vulnerabilities that may impact Information Resources, including those discovered through industry publications, vulnerability scanning, virus scanning, IDS/IPS alerts, and the review of security logs, and promptly apply appropriate security patches. |
| 5. | Assign security administration responsibilities for configuring the security parameters of host operating systems to authorized users only. |
| 6. | ▇▇▇▇▇▇ Information Resources by utilizing a minimum security baseline configuration based upon industry best practices to reduce available ways of attack. This typically includes changing default passwords, the removal of unnecessary software, unnecessary UserIDs, usernames or logins, and the disabling or removal of unnecessary services. Such hardening of the system’s security configurations, operating system software, firmware and applications are to prevent exploits that attack flaws in the underlying code. |
| 7. | a. Enforce the rule of least privilege by requiring application, database, network and system administrators to restrict access of all users to only the commands, In-Scope Information and Information Resources necessary for them to perform authorized functions. Log all successful and unsuccessful login attempts along with logoffs. Supplier shall ensure that the use of AT&T’s Information Resources by Supplier Entities shall only be for the performance of In-Scope Work. |
| b. | Ensure that controls are in-place to limit, protect, monitor, detect and respond to all Privileged User activities. |
Examples of such controls include enforcing:
| 1. | The rule of least privilege; |
| 2. | Separation of duties; |
| 3. | Individual accountability; |
| 4. | Change management; |
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
30
Agreement No. 53258.A.002
| 5. | Auditability of Privileged User accounts and their activities in production environments since we do not store end customer’s data in non-production environments; and |
| 6. | Audit log retention for a minimum of (6) six months. |
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
31
Agreement No. 53258.A.002
Physical Security
8. a. Ensure all Information Resources intended for use by multiple users are located in secure physical facilities with access limited and restricted to authorized individuals only.
b. Monitor and record, for audit purposes, access to the physical facilities containing Information Resources intended for use by multiple users in connection with Supplier’s performance of In-Scope Work.
| 9. | Physically secure any area where In-Scope Information is accessible to prevent access by unauthorized persons. In addition, Supplier shall monitor and record the physical access to any facilities where In-Scope Information is accessible to prevent access by unauthorized persons. |
Network Security
| 10. | When providing Internet accessible services to AT&T, have Denial of Service (DoS/DDoS) and gateway security protections in place. Web servers must reside in a DMZ and Information Resources storing In-Scope Information (such as application and database servers) must reside in a trusted internal network. |
| 11. | For the purpose of demonstrating compliance with certain Security Requirements applicable to network architecture and network topology, if requested by AT&T, provide AT&T with a high-level copy of their logical network diagram. The network diagram needs to provide information regarding placement of Information Resources and security devices (such as Security Gateways, servers, DMZs, IDS/IPS, DoS/DDoS protections, databases, application servers, virtual private clouds (VPCs), and instances, etc.) used by Supplier Entities to perform or support AT&T In-Scope Work. |
| 12. | Use Strong Encryption for the transmission of In-Scope Information outside of AT&T-controlled or Supplier-controlled networks or when transmitting In-Scope Information over any untrusted network. This applies to all technologies used for the transmission of In-Scope Information. |
| 13. | Require Multi-Factor Authentication for any remote access use of Nonpublic Information Resources. |
Information Security
| 14. | Segregate AT&T’s applications and In-Scope Information from any other customer’s or Supplier’s own applications and information, either by using logical access controls and/or physical access controls to provide protection from unauthorized access. |
| 15. | Maintain and adhere to documented processes for: |
| a. | the backup and recovery of In-Scope Information and Information Resources in accordance with any disaster recovery requirements; and |
| b. | the timely destruction and/or return of In-Scope Information in accordance with any retention, return, and/or destruction requirements under this Agreement. |
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
32
Agreement No. 53258.A.002
| 16. | Limit access to In-Scope Information only to authorized users or systems on a need to know basis. |
| 17. | Maintain documented processes and controls to detect and terminate unauthorized attempts to access, collect, modify, store, handle and/or dispose of In-Scope Information; and monitor, and remediate unauthorized access and/or changes to system and application configuration files in production environments. Supplier does not store end customer data in non-production environments. Supplier is managing the access in all environments and access with wrong credentials/passwords will be blocked to address unauthorized access. |
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
33
Agreement No. 53258.A.002
Identification and Authentication
| 18. | Assign unique UserIDs to authorized individual users, assign individual ownership to system service accounts,
and ensure that system service accounts are not |
| 19. | Maintain a documented UserID lifecycle management process that includes manual and/or automated processes for approved account creation, account removal within one (1) business day, and account modification for all Information Resources and across all environments. Such process shall include review of access privileges and account validity to be performed at least each calendar year. |
| 20. | Limit failed login attempts by no more than six (6) consecutive failed login attempts by locking the user account. Access to the user account can be reactivated through the use of a manual process requiring verification of the user’s identity or, where such capability exists, can be automatically reactivated after at least three (3) minutes from the last failed login attempt. |
| 21. | Terminate interactive sessions on a user’s workstation, or activate a secure, locking screensaver requiring authentication, after a period of inactivity not to exceed fifteen (15) minutes. On all other Information Resources terminate inactive interactive sessions not to exceed thirty (30) minutes, excluding inactive scenarios where processing is needed to be ran in the background. |
| 22. | a.Use an authentication method based on the sensitivity of In-Scope Information. Whenever authentication credentials are stored, Supplier shall use Strong Encryption and/or one-way hashing based upon strong cryptography. |
| b. | Passwords must be complex and meet the following password construction requirements: |
| • | Be a minimum of eight (8) characters in length. |
| • | Include characters from at least two (2) of these groupings: alpha, numeric, and special characters. |
| • | Not be the same as the UserID with which they are associated. |
| c. | PINs must meet the following: |
| • | Be a minimum of four (4) numbers; and |
| • | Effective June 30, 2019, PINs shall not contain repeating or sequential numbers. |
| d. | Require expiration of password and, effective June 30, 2019 also expiration of PIN, at regular intervals not to exceed ninety (90) calendar days. |
| 23. | When providing users with a new or reset password, or other authentication credentials, use a secure method to provide this information, and require reset at first login whenever a temporary credential is used. |
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
34
Agreement No. 53258.A.002
Warning Notice
| 24. | In jurisdictions where unauthorized access to Information Resources and In-Scope Information is a violation of the law, add the following statement to the warning notice: “Unauthorized access is a violation of law” or similar warning language. |
Software, Software Code, and Data Integrity
| 25. | Have and use documented procedures to: |
| a. | Install and run current antivirus software to scan for and promptly remove or quarantine viruses and other malware. |
| b. | Configure end user devices to ensure users are restricted from the ability to install unauthorized software, or to disable required software. |
| 26. | Separate non-production Information Resources from production Information Resources, and separate In-Scope Information from non-production Information Resources. |
| 27. | Maintain a documented change control process including back-out procedures for all production environments. |
| 28. | For applications which utilize a database that allows modifications to In-Scope Information, logs for forensic analysis purposes shall be created, retained and available to AT&T for a minimum of six (6) months either on-line or on backup media as follows: |
| a. | where transaction logging is supported have database transaction logging features enabled; or |
| b. | where transaction logging is not supported have some other mechanism that logs all modifications to In-Scope Information stored within the database including timestamp, UserID and information modified. |
| 29. | a. For all software developed or customized for AT&T under the Agreement, review and scan such software to find and remediate malicious code and/or security vulnerabilities prior to initial deployment, upon code changes and/or at least annually, based on potential risk that a given vulnerability is or can be exploited as follows: |
| i. | Source code vulnerability scanning must be performed where such tools are commercially available. Where such tools are not commercially available, automated and/or manual processes and procedures must be documented and used. |
| ii. | Scan results and remediation plans must be made available to AT&T upon request. |
| b. | Where technically feasible, for all software used, furnished and/or supported under the Agreement, review and scan such software to find and remediate security vulnerabilities prior to initial deployment, upon code changes and/or at least annually based on potential risk that a given vulnerability is or can be exploited. |
| 30. | Perform quality assurance testing for the security components (e.g., testing of identification, authentication and authorization functions), as well as any other activity designed to validate the security architecture, during initial implementation and upon any modifications and updates. |
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
35
Agreement No. 53258.A.002
Monitoring and Auditing Controls
| 31. | Restrict access to security logs to authorized individuals, and protect security logs from unauthorized modification. |
| 32. | Review, on no less than a weekly basis, all anomalies from security and security-related audit logs and document and resolve logged security problems in a timely manner. |
| a. | Such reviews may initially be performed by automated processes that promptly issue alarms and/or alerts when such processes detect significant anomalies so that the issuance of such alarms and/or alerts causes prompt investigation and review by responsible individuals; and |
| b. | If automated processes successfully resolve a logged security problem, no further action by responsible individuals is required. |
| 33. a. | When presented with evidence by AT&T of a threat to AT&T or AT&T’s customers’ Nonpublic Information Resources originating from the Supplier’s network (e.g., worm, virus or other malware, bot infection, Advanced Persistent Threat (APT), DoS/DDoS attack, etc.), Supplier shall promptly cooperate with AT&T and take all reasonable and necessary steps to isolate, mitigate, and/or terminate all known or suspected threats. |
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
36
Agreement No. 53258.A.002
| b. | When Supplier learns of or discovers a known or suspected threat/vulnerability impacting AT&T (including but not limited to notifications received from security researchers or industry resources, bug bounty program, etc.), Supplier must promptly notify and cooperate with AT&T, and take all reasonable and necessary steps to isolate, mitigate, and/or remediate such known or suspected threat/vulnerability. |
| c. | In the event Supplier discovers that it is non-compliant with, or AT&T finds Supplier to be non-compliant with these Security Requirements, then Supplier shall implement corrective action promptly, but in no less than the earlier of [*] days of Supplier’s initial discovery of, or AT&T’s initial notification to Supplier of such non-compliance. |
Reporting Violations
| 34. | Maintain a documented procedure to be followed in the event of a suspected attack upon, intrusion upon, unauthorized access to, loss of, or other security breach involving In-Scope Information in which Supplier shall: |
| a. | Promptly investigate and determine if such an attack has occurred; and |
| b. | If a successful attack has occurred involving In-Scope Information or it is impossible to determine whether the attack was successful then Supplier shall promptly notify AT&T by contacting: |
| i. | Asset Protection by telephone at ▇-▇▇▇-▇▇▇-▇▇▇▇ from within the US and at ▇-▇▇▇-▇▇▇-▇▇▇▇ from elsewhere; and |
| ii. | Supplier’s contact within AT&T for service-related issues. |
| 35. | After notifying AT&T whenever there is a successful attack upon, intrusion upon, unauthorized access to, loss of, or other breach of In-Scope Information, provide AT&T with regular status updates, including, actions taken to resolve such incident, at mutually agreed intervals or times for the duration of the incident and, within seven (7) calendar days of the closure of the incident, provide AT&T with a written report describing the incident, actions taken by the Supplier during its response and Supplier’s plans for future actions to prevent a similar incident from occurring. |
Mobile and Portable Devices
| 36. | Use Strong Encryption to protect all In-Scope Information stored on Mobile and Portable Devices. |
| 37. | Use Strong Encryption to protect all In-Scope Information transmitted using or remotely accessed by network-aware Mobile and Portable Devices. |
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
37
Agreement No. 53258.A.002
| 38. | Maintain documented policies, standards and procedures for Mobile and Portable Devices used to access and/or store In-Scope Information that include the following requirements: |
| a. | All users must be authorized for such access and their identity authenticated; |
| b. | Mobile and Portable devices must be physically secured and/or in the physical possession of authorized individuals; |
| c. | Where technically feasible, use a remote wipe capability on such devices to promptly and securely delete In-Scope Information, when such devices are not in the physical possession of authorized individuals nor otherwise physically secured; and |
| d. | Jailbroken or rooted smartphones cannot be used to perform In-Scope Work. |
| 39. | Implement and maintain a documented policy that prohibits the use of any: |
| a. | Supplier-issued Mobile and Portable Devices to access and/or store In-Scope Information unless the device is administered and/or managed by Supplier; and |
| b. | Non-Supplier issued Mobile and Portable Devices to access and/or store In-Scope Information unless adequately segregated and protected by utilizing a Supplier administered and/or managed secure container-based and/or sandbox solution. |
Security Gateways
| 40. | Require Multi-Factor Authentication for administrative and/or management access to Security Gateways, including any access for the purpose of reviewing log files. |
| 41. | Maintain documented controls, policies, processes and procedures to ensure that unauthorized users do not have administrative and/or management access to Security Gateways, and that user authorization levels to administer and manage Security Gateways are appropriate. |
| 42. | At least annually, ensure that each Security Gateway rule was properly authorized and is traceable to a specific business request, and that all rule sets either explicitly or implicitly end with a “DENY ALL” statement. |
| 43. | Use monitoring tools to ensure that all aspects of Security Gateways (e.g., hardware, firmware, and software) are operational at all times. Ensure that all non-operational Security Gateways are configured to deny all access. |
Wireless Networking
| 44. | When using radio frequency (RF) based wireless networking technologies (e.g., Bluetooth and Wi-Fi) to perform or support In-Scope Work for AT&T, ensure that all In-Scope Information transmitted must use appropriate encryption technologies sufficient to protect the confidentiality of In-Scope Information; provided, however, in any event such encryption shall use no less than key lengths of 256-bits for symmetric encryption and 2048-bits for asymmetric encryption. The use of RF-based wireless headsets, keyboards, microphones, and pointing devices, such as mice, touch pads, and digital drawing tablets, is excluded from this requirement. |
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
38
Agreement No. 53258.A.002
Connectivity Requirements
| 45. | In the event that Supplier has, or will be provided, connectivity to AT&T’s or AT&T’s customers’ Nonpublic Information Resources in connection with In-Scope Work, then Supplier shall not establish additional interconnections to AT&T’s and AT&T’s customers’ Nonpublic Information Resources without the prior consent of AT&T and shall: |
| a. | Use only the mutually agreed upon facilities and connection methodologies to interconnect AT&T’s and AT&T’s customers’ Nonpublic Information Resources with Supplier’s Information Resources. |
| b. | If the agreed upon connectivity methodology requires that Supplier implement a Security Gateway, maintain logs of all sessions using such Security Gateway. Such session logs must include sufficiently detailed information to assist with a security incident or a forensic investigation (e.g., identification of the end user or application accessing AT&T). Such session logs must include origination IP address, destination IP address, ports/service protocols used and duration of access. Such session logs must be retained for a minimum of six (6) months. |
Supplier Entity Compliance
| 46. | Supplier shall: |
| a. | Ensure all Supplier Entities performing In-Scope Work are aware of, and in compliance with, these Security Requirements. |
| b. | Ensure all Supplier Entities performing any In-Scope Work are contractually obligated to comply with these Security Requirements, or in any event, requirements that are no less stringent. |
| c. | Ensure the use of AT&T’s Information Resources and In-Scope Information by Supplier Entities will only be for the performance of In-Scope Work. |
| d. | Upon AT&T’s request, Supplier will provide documentation and/or evidence to adequately substantiate such compliance. |
Protection of AT&T’s SPI & SCD
| 47. | Use Strong Encryption to protect AT&T’s SPI and/or AT&T’s SCD (see Table 1 and 2 below) when transmitted over all networks. This applies to all technologies used for the transmission of SPI and/or AT&T’s SCD. |
| 48. | Use Strong Encryption to protect AT&T’s SPI and/or AT&T’s SCD (see Table 1 and 2 below) when stored. |
Cloud Services
| 49. | When storing In-Scope Information in a Cloud Service, ensure all In-Scope Work performed by Supplier Entities is in compliance with these Security Requirements, or in any event, requirements that are no less stringent. |
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
39
Agreement No. 53258.A.002
| 50. | When utilizing a Cloud Service enforce. |
| a. | Multi-Factor Authentication for all Privileged Users. |
| b. | In addition to Strong Encryption of SPI and SCD use Strong Encryption to protect all In-Scope Information when: |
| i. | Transmitted over all networks to, from, and within a Cloud Service. |
| ii. | Stored within a Cloud Service. |
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
40
Agreement No. 53258.A.002
Table 1—AT&T SPI Data Elements
Data elements in the following tables must be treated as SPI when used in their entirety, unless explicitly stated in the following table. This applies to all data formats including scanned images, PDFs, JPGs and any other unified communication, and collaboration tools/content.
Individual Identification
| Data Element |
Description | |
| Driver’s License Number |
||
| Taxpayer Identification Number | ||
| U.S. Social Security Number (SSN) | ||
| Nationally-Issued Identification Number | Includes visa and/or passport values. Excludes any such numbers that are issued on the understanding that they must be a matter of public record, e.g. U.S. FCC Radio License. | |
| State or Province-Issued Identification Number | ||
Financial Data
| Data Element |
Description | |
| Payment Card Number | Primary Account Number (PAN) for all types of payment card (corporate, personal, etc.) | |
| Payment Card Security Data | The security data used in association with a payment card (corporate, personal, etc.) in order to confirm legitimate use. Includes for example Card Security Codes and Personal Identification Numbers (PINs) used with payment cards but excludes PINs used to authenticate access to AT&T systems. | |
| Bank Account Number | Includes all types of bank accounts (savings, checking, etc.) both personal and business in an individual’s name. Excludes bank routing number. | |
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
41
Agreement No. 53258.A.002
Computer Identification and Authentication
| Data Element |
Description | |
| Customer Authentication Credentials
Applies to Customers only |
Values used by customers to authenticate and permit access to:
• The customers’ personal information, including CPNI and AT&T Proprietary (Sensitive Personal Information) — or —
• An application enabling the customer to subscribe to, or unsubscribe from, AT&T services — or —
• An AT&T service the customer is subscribed to
Includes: Personal Identification Numbers (PINs), passwords or passcodes. Excludes Card Security Codes and PINs used in association with payment cards. | |
| Customer Authentication Credential Hints
Applies to Customers only |
Answers to questions used to retrieve customer authentication credentials, for example mother’s maiden name. | |
| Location-Based Information (LBI) | Information that identifies the current or past location of a specific individuals’ mobile device. This element contains two factors both of which must be present and able to be associated with each other:
1. A mobile device’s location (e.g. a map address, or latitude and longitude together with altitude where known) derived from the mobile device through activities such as GPS or network connectivity rather than as a result of user action (e.g. revealing location in the content of an email, or SMS)
-and -
2. An individual’s identity derived from a unique identifier assigned to that mobile device such as customer name, MSISDN, IMSI, IMEI or ICCID, or similar persistent identifier, e.g. VIN. | |
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
42
Agreement No. 53258.A.002
Other Data
| Data Element |
Description | |
| Date of Birth (DOB) | An individual’s full and complete DOB, i.e. including Month, Day and Year. Excludes partial DOB where only Month and Day are used without Year. This element contains two factors both of which must be present and able to be associated with each other:
1. A full and complete DOB
- and -
2. The individual’s identity, either explicitly or via a unique identifier that can be linked to that individual. | |
| Biometric Data | Measures of human physical and behavioral characteristics used for authentication purposes, for example fingerprint, voiceprint, retina or iris image. Excludes templates that contain discrete data points derived from biometric data that do not hold the complete biometric image, where the template cannot be reverse engineered back to the original biometric image. | |
| Criminal History
Subject to non-U.S. jurisdiction1 |
Information about an individual’s criminal history, e.g. criminal check portion of a background check. | |
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
43
Agreement No. 53258.A.002
| Background Checks | Includes credit history, employment history, driving records. Excludes Criminal History (see above). | |
| Racial or Ethnic Origin
Subject to non-U.S. jurisdiction1 |
Data specifying and/or confirming an individual’s racial or ethnic origin. | |
| Trade Union Membership
Subject to non-U.S. jurisdiction1 |
Data specifying and/or confirming an individual is a member of a trade union outside of the U.S. | |
| Information Related to an Individual’s Political Affiliation, Religious Belief, or Sexual Orientation
Subject to non-U.S. jurisdiction1 |
Data specifying and/or confirming an individual’s political affiliation, religious or similar beliefs, or sexual life or orientation. | |
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
44
Agreement No. 53258.A.002
The following “Human Resources” data elements have been classified as AT&T Proprietary (Sensitive Personal Information) when they apply to an employee, contractor, customer or supplier:
Health Data
| Data Element |
Description | |
| U.S. Protected Health Information (PHI) | Includes any U.S. health information used in AT&T’s Group Health Care plans or belonging to AT&T’s customers that identifies the individual or for which there is a reasonable basis to believe it can be used to identify the individuals that include information about:
• The individual’s past, present or future physical or mental health or condition,
• The provision of health care to the individual — or —
• The past, present, or future payment for the provision of health care to the individual.
Health information of retirees, employees, or employee beneficiaries used by AT&T for purposes other than a group health plan is not PHI. | |
| Medical and Health Information
Subject to non-U.S. jurisdiction1 |
Any information concerning physical or mental health or condition. Includes disability information. | |
| Genetic Information | Includes information about an individual’s genetic tests. | |
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
45
Agreement No. 53258.A.002
Customer Privacy Data
| Data Element |
Description | |
| Customer Web Browsing History | Information about what websites our customers visit and applications they use on our network (wireline and wireless including Wi-Fi); this does not include browsing and activities associated with customers’ use of official AT&T corporate websites or history captured at the network level prior to “processing” (e.g. raw data streams not associated with a customer). |
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
46
Agreement No. 53258.A.002
Customer Privacy Data (continued)
| Data Element |
Description | |
| Customer Viewing History | Information about programs watched or recorded, games and applications used, etc. (e.g. DIRECTV® (DTV) Set Top Box viewing, DIRECTV NOW® viewing) | |
| Customer Web communications payload | Limited to communication payload captured as part of service analysis, e.g. Deep Packet Inspection (DPI) data. (AT&T use) | |
Footnotes:
Where data elements have the term “Subject to non-U.S. jurisdiction” associated with them, that data element is to be classified as AT&T Proprietary (Sensitive Personal Information) when applied to data elements subject to non-U.S. jurisdiction, irrespective of whether the data is created, handled, processed, destroyed or sanitized inside or outside the United States.
Table 2—AT&T SCD Data Elements
Data elements in the following table must be treated as SCD when used in their entirety, unless explicitly stated in the following table. This applies to all data formats including scanned images, PDFs, JPGs and any other unified communication, and collaboration tools/content.
Sensitive Customer Data (Customer Privacy)
| Data Element |
Description | |
| Customer “messaging” content | Including:
Email, text messages, conference call recording, and voice mail call recording.
Excluding:
1. “Messaging” between customers and AT&T in conducting official AT&T corporate business.
2. Any other data. | |
| Customer Telemetry Data | Automated communications for monitoring by the customer (rather than AT&T). Including all data that is generated by our customers’ use of the Digital Life® service or any other IoT service that is used by the customer to monitor or control the service. For example, video files. (Customer use) | |
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
47
Agreement No. 53258.A.002
| 2.0 | Offshore Information Technology Services Requirements |
In the event Supplier currently provides or will be providing Offshore Information Technology Services in conjunction with this Agreement, then, in addition to the foregoing, the following requirements shall apply to Supplier:
| 1 | Strong authentication controls must be established for firewalls, firewall management servers, and firewall hop boxes. Options for strong authentication may include two-factor authentication methods such as tokens, smart-cards and/or one-time passwords. |
| 2 | Supplier must ensure that firewall configurations are hardened by selecting a sample of firewalls and verifying that the default rule set ensures the following: |
| a. | IP source routing is disabled. |
| b. | Loopback address is prohibited from entering the internal network, |
| c. | Anti-spoofing filters are implemented. |
| d. | Broadcast packets are disallowed from entering the network, |
| e. | ICMP redirects are disabled. |
| f. | Fragmented packets are dropped. |
| g. | Ruleset ends with a DENY ALL statement |
| 3 | Screen savers or connection timeouts are required to prevent unauthorized access to unattended workstations. |
| 4 | Perform monthly revalidations on the user account list on firewalls, firewall management servers, and firewall hop boxes to ensure that only those users authorized for access to manage these devices have an account. This includes the need to revalidate the authorization level of each user account to ensure appropriate permission levels are maintained. |
| 5 | Production support personnel and development personnel must have enough separation and auditable controls to ensure that standard change management procedures are always consistently followed. |
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
48
Agreement No. 53258.A.002
| 6 | Developers cannot access production platforms “at will”. For some trouble-shooting situations, developers may be provided access to production platforms but only on an “as needed basis” and for a limited duration. All temporary access should be documented (who, what, when, where and why). |
| 7 | Track and approve changes to firewall rules is required and must be validated annually. Inappropriate firewall rules must be removed immediately. |
| 8 | Require a clean desk policy at the end of the day. |
| 9A | Supplier resources shall be notified of the restriction that AT&T Data may not be downloaded and taken offsite. |
| 9B | Wireless networking technologies must not be used for communicating unless the following steps are taken by Amdocs to maintain the confidentiality and integrity of the communication and to prevent unauthorized access to the transmitting device and/or receiving device. When wireless networking technologies are used: |
(i) All communications over wireless networks must be transmitted via Virtual Private Network (VPN) session(s) using Strong Encryption.
(ii) Strong authentication (e.g., two factor token or digital certificates) must be used for authenticating VPN access.
(iii) Wireless hardware (with the exception of wireless network cards and access points) must be located in a physically secure area (e.g., in a locked wiring closet or locked machine room).
(iv) All services not being used on the access point, router, and VPN concentrator must be disabled.
(v) Enable Media Access Control (MAC)-based filtering so that only specified wireless cards can communicate to the access point.
| 10 | Supplier must implement procedures to ensure that AT&T Data is not downloaded and removed by Supplier. To the extent Supplier suspects that AT&T Data may have been removed, Supplier agrees to conduct searches of suspected persons and their belongings when exiting AT&T restricted areas and Supplier’s premises to the extent such searches are permissible by local law. |
| 11 | Notify individuals that removal of AT&T Data from the work area or Supplier’s premises is not allowed, to include signage that communicates this policy and that people and personal property including, without limitation, packages, briefcases, and purses are subject to inspection prior to exiting AT&T restricted areas and Supplier’s premises. |
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
49
Agreement No. 53258.A.002
| 12 | Verify that all printed media containing AT&T Data (any information obtained from or provided by AT&T, including information about AT&T Systems, its employees and its customers) is securely stored, and that a mechanism is in place to protect the security and privacy of AT&T Data. Procedures are required to restrict access to AT&T Data to authorized Supplier personnel only, and to ensure that all media containing AT&T Data is accounted for and reconciled on a weekly basis to ensure that the information is not removed from Supplier’s premises. |
| 13 | All access to electronic documentation of AT&T Data retained locally must be password protected and restricted to the very minimum number of Supplier personnel. Supplier must implement procedures to ensure that AT&T Data is not downloaded and removed by Supplier personnel, including, at a minimum, searches. To the extent Supplier suspects that AT&T Data may have been removed, Supplier agrees to conduct searches of persons and their belongings when exiting AT&T restricted areas and Supplier’s premises to the extent searches are permissible under local law. |
| 14 | All electronically stored or printed AT&T Data no longer needed must be shredded onsite or destroyed onsite by authorized Supplier personnel assigned to AT&T projects. Shred bins must be located in AT&T restricted areas and locked until the shredding takes place. |
| 15 | A monthly Metric Report of Perimeter Security on the Supplier’s system should be reported to AT&T that consists of: |
| • | Location |
| • | Date |
| • | # of Intrusions |
| • | Type of Intrusions |
| • | Source |
| • | Destination |
| • | Detail |
| • | Actions |
Security IDS audit logs must be retained online for thirty (30) days and offline for a period of at least one year.
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
50
Agreement No. 53258.A.002
| 16 | Remote access to AT&T Networks or AT&T Data is prohibited. All work on AT&T projects must be performed within the AT&T restricted area on Supplier’s premises and any exceptions must be in accordance with the Limited Offshore Remote Access in this Appendix D. Prior written exception to this prohibition must be obtained from the AT&T Offshore Compliance & Enablement team (▇▇▇▇▇▇@▇▇▇.▇▇▇). Supplier’s use of laptops offsite must have written approval from the AT&T Offshore Compliance & Enablement team (▇▇▇▇▇▇@▇▇▇.▇▇▇). |
| 17 | Randomly check Supplier-based email and internet-based email so that AT&T Data is not sent to an unauthorized recipient. Effective January 1, 2011, Amdocs must check for the AT&T Proprietary – Restricted and AT&T Proprietary – Sensitive Personal Information markings in emails and attachments sent from Amdocs to non-AT&T personnel outside. Any unauthorized transmissions must be reported by Amdocs in an email to the AT&T Offshore Compliance and Enablement team (▇▇▇▇▇▇@▇▇▇.▇▇▇) promptly but in any case within twenty four (24) hours. |
| 18 | B2B VPN connections to AT&T are required to be secured from other remote connections. |
| 19 | Device-specific monitoring tools must be used to assure that firewall hardware is operational. |
| 20 | To minimize the risk exposure to visiting AT&T employees in locations that are of medium-high risk of terrorist attacks, Supplier shall take necessary security measures customary for the location. |
| 21 | All access points into the Supplier’s building(s) where AT&T work is being performed must be locked by either physical keys or a card key system, or controlled by a guard service to restrict access only to authorized individuals. These mechanisms must be in working order and utilized at all times. Proper identification must be worn by all persons inside the Supplier’s building and a procedure in place to challenge those not wearing appropriate identification in the Supplier’s building. The cable vault, electrical and telephone areas should be secured to give access only to those authorized. |
| 22 | Card key access lists and event logs must be reviewed by Supplier at a minimum of weekly to validate that building card key access is limited to only those individuals with a need to be in the Supplier’s building and restricted area where AT&T work is being performed. Ensure that all keys are accounted for and limited to those individuals with a need to be in the Supplier’s building and restricted areas and all locks are changed on a regular interval (at a minimum annually). Ensure that Supplier personnel surrender company identification, keys and access cards before leaving the premises when access to an area is no longer required or upon voluntarily or involuntarily ceasing to work for Supplier and that the access cards are deactivated. Weekly reviews should include employee, contractor and supplier termination records and any associated unauthorized access attempts in the event logs. |
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
51
Agreement No. 53258.A.002
| 23 | Alarmed doors and monitored electronic systems are required to detect unauthorized access or access attempts with a plan to respond to and document incidents. 24/7 recorded video surveillance is required of the area where work on AT&T projects is performed, including entry and exit points. |
| 24 | Prior to permitting any person access to an AT&T project source or origin code (for example, software development), and at annual intervals thereafter, Supplier must ensure that such person (employee, contractor, subcontractor) is not on the Denied Persons List or the Specially Designated Nationals List of the US Department of Commerce – Bureau of Industry and Security. – Those lists are located at ▇▇▇▇://▇▇▇.▇▇▇.▇▇▇.▇▇▇/▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇/▇▇▇▇▇▇▇▇▇▇▇▇.▇▇▇. |
Prior to permitting any person direct or indirect access, whether physical, virtual, or otherwise, to any of AT&T’s company, employee, or customer information, or any of AT&T’s or AT&T’s customers’ premises, systems, software, or networks, Supplier must have a reputable security company perform a criminal background check and verification of the identity of such person (employee, contractor, or subcontractor including onsite security guards responsible for physical security of Supplier’s premises and AT&T restricted areas, and unescorted cleaning/maintenance personnel).
| 25 | A security plan must be in place to include training of Supplier personnel to report suspicious activity/security incidents and complaints that did or could affect AT&T, to include documentation, follow-up and reporting to the AT&T IT:OFFSHORE organization and, as necessary, law enforcement. |
Information to be reported to the Executive Director of the IT:OFFSHORE organization would consist of at least:
| • | Date of Incident |
| • | Who - Identify those involved and be descriptive (suspects, vehicles, property, license plate numbers, …) |
| • | What - What happened and how? |
| • | When - When did the incident occur? |
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
52
Agreement No. 53258.A.002
| • | Where - Where did the incident take place? |
| • | Action Taken – What action was taken? Was law enforcement notified? |
| 26 | An exercise of Supplier’s recovery strategy must be conducted annually. Within thirty (30) days from the completion of a disaster recovery exercise by Amdocs, Amdocs will produce a documented conclusion with a corrective action plan and proposed committed timeframes for corrective action upon which the Parties will agree within thirty (30) days from receipt of the action plan. |
| 27 | Failover processes and procedures are required to support AT&T applications and these failover processes and procedures are exercised annually (at a minimum). |
| 28 | Business continuity communication documents, processes, and procedures must be readily available and current. |
| 29 | As soon as reasonably possible after the execution of this Agreement and on an annual basis thereafter, Supplier will, at no charge to AT&T, perform a security audit utilizing a reputable independent auditor, as agreed by the Parties. Such security audit shall ensure that Supplier will strictly follow these AT&T Supplier Information Security Requirements. |
| 3.0 | Requirements for Offshore Information Technology Services Requiring Elevated Rights |
In the event Supplier currently provides or will be providing system, database, and or network administrator/root (or privileged, super user, or the like) access to host operating systems located on AT&T non-public networks in conjunction with this Agreement from an Offshore Location, then, in addition to the foregoing, the following requirements shall apply to Supplier:
| 1 | Access for privileged offshore users will be via a front-end Citrix farm that requires SecurID authentication, with front end Citrix servers located in a DMZ segment. An alternative to this is an AT&T-provided Client VPN with a SecurID token used over a secure connection (NOT the public Internet) as reviewed and approved by AT&T’s Chief Security Office (CSO). |
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
53
Agreement No. 53258.A.002
| 2 | Auditing options must be enabled on any Supplier perimeter equipment which controls access to the Supplier equipment used to do AT&T work. To ensure integrity of audit log entries, all Supplier system clocks must be synchronized to the same time source. Synchronization to AT&T clocks is not required. At a minimum, security audit log(s) must be automatically updated for the following system events: |
| a. | Successful and unsuccessful login attempts. |
| b. | Successful and unsuccessful attempts to switch to another user’s account (where applicable). |
| c. | Logoffs. |
| d. | User attempts to access files or resources outside their privilege level. |
| e. | User access to all privileged files and/or processes. |
| f. | Operating system configuration changes. |
| g. | Operating system program changes. |
| h. | All changes that can feasibly be captured, to system hardware and software. |
| i. | All security-related changes, including adding users. |
| j. | Failures for computer, program, communications, and operations. |
| k. | Starting and stopping of audit logging. |
Security audit logs must be maintained online for thirty (30) days and offline for a period of at least one (1) year.
| 3 | AT&T reserves the right to perform vulnerability scans and review the scanning results of Supplier systems in a pre-announced, scheduled manner on Supplier’s equipment on an AT&T isolated LAN segment and Supplier Network equipment used to access AT&T Networks, systems, and data or Supplier agrees to reveal to the AT&T IT Offshore Compliance and Enablement Team (IT OCE) at (▇▇▇▇▇▇@▇▇▇.▇▇▇) the detailed scanning findings and closure activities related to vulnerabilities found once a year. |
Information to be reported to the AT&T-IT OCE would consist of at least:
| • | Date of discovery of vulnerability |
| • | How it was remediated |
| • | What was remediated |
| • | What are the plans to remediate |
| • | Estimated Date of closure |
| 4 | An Intrusion Prevention System (IPS) is required on Supplier’s data network to prevent unauthorized access. |
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
54
Agreement No. 53258.A.002
| 4.0 | Limited Offshore Remote Access (“▇▇▇▇”) to AT&T Systems |
The following outlines the AT&T requirements and procedures to which the Supplier must adhere for allowance of select pre-authorized offshore Supplier personnel to have remote access to AT&T systems, for which the Supplier is already under contract with AT&T to perform IT support services.
This remote access program (the “Limited Offshore Remote Access”) set forth herein defines the program requirements and how the Supplier shall work with the AT&T Offshore Compliance and Enablement organization to determine if Supplier can utilize the ▇▇▇▇ for an existing or new information technology Services engagement. Examples of engagements where AT&T will consider Supplier’s request for ▇▇▇▇ would be a Work Order where offshore Supplier personnel are required to perform after-hours work monitoring support services and access AT&T data.
I. Definitions
AT&T IT Offshore Compliance & Enablement (IT OCE) – AT&T Information Technology organization that manages oversight of the Limited Offshore Remote Access program. The IT OCE will serve as the front door and provide authorization to Supplier. IT OCE point of contact is identified below.
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
55
Agreement No. 53258.A.002
“AT&T Proprietary – Restricted Information” or “Restricted Information” means: any Information that has a higher level of sensitivity and therefore must be shared only among persons with a clear business need to know; or any Information that requires a high degree of protection by law and loss or unauthorized disclosure could require notification by AT&T to government agencies, individuals or law enforcement; or any Information that if revealed widely could present an increased risk of compromising computer systems, fraud, or increased likelihood of disrupting business operations. Examples of Restricted Information include, but are not limited to, unpublished financial information, designs and development plans for new or improved products, services, or processes, Customer Proprietary Network Information (CPNI), marketing information including customer contact lists, software source code for business critical applications, other companies’ confidential information that is shared with AT&T under contract or an NDA, internal AT&T authentication credentials (e.g., passwords, PINs and password hint answers), and security and/or network information including: logs, engineering or architecture diagrams, configuration files, firewall rules, security incident reports, and vulnerability information.
Limited Offshore Remote Access (“▇▇▇▇”)—the ability, with prior AT&T IT OCE approval, for an Offshore Supplier resource to connect to AT&T systems via AT&T client VPN from their Resource Home Location for the purposes of completing contracted work for AT&T.
“Remote Access Laptop”- limited in use by Amdocs Offshore resources that require a laptop to perform their day-to-day duties, who support the AT&T account, from the Amdocs facility, Resource Home Location or travel. There will be no transfer of or storage of SPI and AT&T Proprietary – Restricted Information or Restricted Information on this device. For clarity the only access to SPI and AT&T Proprietary – Restricted Information or Restricted Information will be as defined in Article II #3 below, “Remote Access Laptop with AT&T Data other than SPI”.
Resource Home Location – The home residence of a Supplier resource. Each approved Supplier resource can have ▇▇▇▇ from only one Resource Home Location.
Controlled and Audited Supplier Facility – The designated offshore Supplier work location, which is governed by controls specified by AT&T. This is the Supplier resource’s primary work location.
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
56
Agreement No. 53258.A.002
Remote Access Solution – From the Resource Home Location, an approved Supplier resource will use a Remote Access Laptop/Desktop to connect to the AT&T Secure VPN Gateway.
Permanent Workstation/Virtual Workstation—A laptop or desktop located in a controlled and audited Supplier facility that is used to access the AT&T network for contracted services.
II. ▇▇▇▇ requirements:
| 1. | General requirements: Supplier shall adhere to the following: |
| a. | Each individual ▇▇▇▇ user shall be reviewed and either approved or denied within two (2) weeks from receipt of written request to the AT&T IT Offshore Compliance & Enablement (IT OCE). |
| b. | Each individual ▇▇▇▇ request must be linked with a specific statement of work covered under an existing or pending Work Order issued under a current Master Agreement between AT&T and the Supplier. |
| c. | Supplier is to maintain a history log of all requests for ▇▇▇▇. |
| d. | Supplier is to submit all new ▇▇▇▇ requests to IT OCE, in a format specified by AT&T. |
| e. | The IT OCE Sr. Technical Director or equivalent will approve or deny each request. |
| f. | ▇▇▇▇ ▇▇▇▇▇▇▇ (gm1945) is the AT&T IT OCE interface at the time of this document being implemented. This is subject to change by AT&T. |
| g. | Supplier may also request AT&T IT OCE approval for temporary remote access from a location other than the Resource Home Location. |
| h. | Resource Home Location shall be subject to voluntary inspection /verification, as agreed upon by the Parties, by Supplier or AT&T representative if AT&T information/resource is present. The Supplier resource must notify AT&T/Supplier of any changes in Resource Home Location. |
| i. | Amdocs will notify AT&T immediately upon an Amdocs resource’s change in status that would no longer require them to have ▇▇▇▇. |
| 2. | Once a year and immediately upon approval, all offshore Supplier personnel approved for ▇▇▇▇ must complete Supplier-provided compliance training, which shall include but not be limited to: |
| a. | A review of all of the requirements outlined in this Agreement that pertain to the end-users of the Remote Access Solution. The review shall include but not be limited to: the use of the Remote Access Solution from only a single Resource Home Location; the Remote Access Laptop theft/loss reporting requirements; and the prohibition of the use of the Remote Access Solution for anything other than responding to on-call situations. |
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
57
Agreement No. 53258.A.002
| b. | Review of the following guidelines: ▇▇▇▇▇://▇▇▇▇▇▇.▇▇▇.▇▇▇.▇▇▇/▇▇▇▇▇/▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇/▇▇▇/▇▇▇▇▇▇▇▇▇▇▇▇▇▇/▇▇▇▇▇▇▇▇▇▇▇▇.▇▇▇▇. |
| c. | Upon AT&T request, Supplier shall provide to the AT&T IT Offshore Compliance & Enablement (IT OCE) team confirmation that the above training has been completed annually and upon ▇▇▇▇ approvals. |
| 3. | Remote Access Laptop with AT&T Data other than SPI or AT&T Proprietary – Restricted Information (“APRI”) or Restricted Information (“RI”) requirements: |
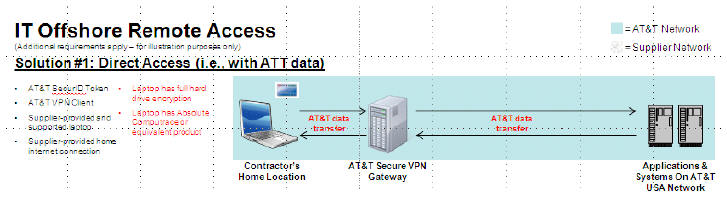
Supplier shall adhere to the following:
| a. | Supplier shall designate, provide and support the Remote Access Laptop to be used from the Resource Home Location, Amdocs Facility and travel. |
| b. | Each Remote Access Laptop shall have anti-virus and firewall software installed and operating. |
| c. | The configuration file that controls these settings required for ▇▇▇▇ shall be read only for the user and editable only by authorized domain administrators (e.g., settings that control full hard drive encryption, antivirus and Absolute Computrace, for application installations) or resources approved for ▇▇▇▇ shall not have administrator rights on the Remote Access Laptop. |
| d. | Each Remote Access Laptop shall have a full hard drive encryption solution, such as PointSec, installed and operating, with all data encrypted as long as the laptop is “locked” (screensaver has turned on) or the Remote Access Laptop is shut down. The configuration file that controls the above settings shall be read only for the user and editable only by authorized domain administrators. |
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
58
Agreement No. 53258.A.002
| e. | Remote Access Laptops with no Absolute Computrace software or equivalent product installed must require both a password and biometric (i.e., thumb print scan) authentication for both logging into the device and “unlocking” the device (gaining control of the device after the screensaver has turned on). The configuration file that controls the above settings shall be read only for the user and editable only by authorized domain administrators. |
| f. | Password and/or biometric-protected screensavers must be set with the inactivity timeout set to fifteen (15) minutes or less. The configuration file that controls the above settings shall be read only for the user and editable only by authorized domain administrators. |
| g. | Each Remote Access Laptop shall have the Absolute Computrace or equivalent product installed and operating, with the configuration file that controls the above settings set to be read only for the user and editable only by authorized domain administrators. Supplier shall initiate the Absolute Computrace or equivalent data wipe process for all lost or stolen laptops within four (4) hours of the reported theft or loss of a Remote Access Laptop. Supplier is to notify AT&T at ▇▇▇-▇▇▇-▇▇▇▇ of a lost or stolen Remote Access Laptop within four (4) hours, including in such notification a description of AT&T information that was on the Remote Access Laptop. Supplier shall provide full and proactive cooperation with any investigation related to AT&T. In addition to Amdocs’ obligation to indemnify, in the event of such a loss of equipment, if it is determined that the lost equipment included personnel Information (personal data such as HR information, SSN, address, etc.) and the Supplier has failed to comply with the provisions of subsections b, c, d, e, and f, above the Supplier shall provide a minimum of twelve months credit monitoring services for each impacted individual, whose information may have been compromised, at no additional cost to AT&T or the Supplier shall reimburse AT&T for the cost of providing the credit monitoring services. |
| h. | Each Remote Access Laptop shall only be able to connect to a single network at any one time. |
| i. | Remote Access Laptops shall use either (i) a VPN connection to AT&T through AT&T’s approved Client VPN or (ii) another VPN connection to connect to the Supplier’s corporate network. The Remote Access Laptop may not use both (i) and (ii) at the same time or any other connection method(s). |
| j. | The data and voice connection in the Resource Home Location and all associated costs shall be provided by the Supplier per the Supplier’s policy and will be either a wired or wireless connection. AT&T will not be required to cover the charges for data and voice connections in the Resource Home Locations. Wired data connections are preferred. However, if the connection is wireless (e.g., WIFI or cellular wireless connection), the connection must be encrypted and adequately secured. |
| k. | Supplier resources shall be notified of the restriction that AT&T Data may not be downloaded and taken offsite. |
| l. | Except where expressly stated, all aforementioned software and hardware shall be provided by the Supplier. |
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
59
Agreement No. 53258.A.002
| m. | Security audit logs shall be maintained by the Supplier to track system events, including login attempts, user sessions, logoffs, configuration changes, and other pertinent events and data. Logs shall be retained online for at least thirty (30) days and offline for at least one (1) year. |
| n. | At all times, the Remote Access Laptop shall be kept in the possession of either the AT&T-approved offshore Supplier resource to whom Supplier has assigned the device or Supplier personnel that are responsible for administering the ▇▇▇▇. |
| 4. | Changes in Program: |
| a. | The Limited Remote Offshore Access program is subject to change as directed by AT&T. |
| b. | AT&T reserves the right to cancel any approved Limited Remote Offshore Access requests upon written notice to the Supplier |
Proprietary and Confidential
This Amendment is not for use or disclosure outside of AT&T, its Affiliates, and its and their third-party representatives, and Supplier except under written agreement by the contracting Parties.
60

