CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS...
Exhibit 10.2
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
Between
Triple-S Salud, Inc.
and
OptumInsight, Inc.
Dated
August 29, 2017
| Master Services Agreement | Triple-S/Supplier Confidential |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
TABLE OF CONTENTS
| 1. PREAMBLE | 1 |
| 1.1 Background and Purpose | 1 |
| 1.2 Goals and Objectives | 1 |
| 1.3 Structure of Agreement | 2 |
| 1.4 Defined Terms | 3 |
| 2. SERVICES | 3 |
| 2.1 Provision of the Services | 3 |
| 2.2 New Services | 4 |
| 2.3 “Master” Nature of the General Terms and Conditions | 5 |
| 2.4 Services Commencement | 6 |
| 2.5 Evolution and Innovation of the Services | 6 |
| 2.6 Users of the Services | 6 |
| 2.7 Services Not Exclusive; Variable | 7 |
| 2.8 Cooperation and Coordination with Other Parties | 8 |
| 3. TERM AND REGULATORY APPROVALS | 9 |
| 3.1 Initial Term | 9 |
| 3.2 Renewal Terms | 9 |
| 3.3 Regulatory and Regulatory Contract Approvals | 9 |
| 3.4 Customer Approvals | 9 |
| 3.5 Additional Contract Clauses | 10 |
| 4. PERFORMANCE | 10 |
| 4.1 Performance, Generally | 10 |
| 4.2 Place of Performance | 10 |
| 4.3 Time of Performance | 11 |
| 4.4 Triple-S Policies and Procedures | 12 |
| 4.5 Quality Assurance and Continuous Improvement | 12 |
| 4.6 Medicare Attestations | 13 |
| 5. SERVICE LEVELS AND CREDITS | 13 |
| 5.1 General | 13 |
| 5.2 Credits | 13 |
| 6. SUPPLIER PERSONNEL | 13 |
| 6.1 Responsibility for Supplier Personnel, Generally | 13 |
| 6.2 Screening and Background Checks | 14 |
| 6.3 Key Supplier Positions and Other Requirements | 15 |
| 6.4 Removal and Replacement of Supplier Personnel | 16 |
| 6.5 Controlling Turnover of Supplier Personnel | 17 |
| 6.6 Subcontracting | 17 |
| 7. TRIPLE-S RESPONSIBILITIES | 19 |
| 7.1 Appointment of Triple-S Program Management Office (PMO) Personnel | 19 |
| 7.2 Triple-S Cooperation Duties | 19 |
| 7.3 Savings Clause | 19 |
| 8. CHARGES | 20 |
| 9. USE OF TRIPLE-S RESOURCES | 20 |
|
Triple-S / Supplier Confidential Page i |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
Table of Contents
| 9.1 Use Rights | 20 |
| 9.2 Triple-S Equipment | 20 |
| 9.3 Triple-S Third Party Service Contracts | 21 |
| 9.4 Triple-S Software and Triple-S Tools | 21 |
| 9.5 Triple-S Facilities | 22 |
| 9.6 Terms Applicable to Triple-S Facilities | 22 |
| 9.7 Required Consents | 23 |
| 10. RESPONSIBILITY FOR RESOURCES DURING THE TERM | 23 |
| 10.1 General Responsibility and Compatibility | 24 |
| 10.2 Equipment | 24 |
| 10.3 Third Party Services | 24 |
| 10.4 Supplier Software and Tools | 25 |
| 10.5 License During the Term and Disengagement Assistance Periods | 26 |
| 10.6 Network Connectivity | 27 |
| 10.7 Triple-S Personnel | 27 |
| 10.8 Flow Down Terms | 28 |
| 11. TRANSITION | 28 |
| 11.1 Transition Overview | 28 |
| 11.2 Transition Defined and Start of Transition | 28 |
| 11.3 Transition Documents | 29 |
| 11.4 Transition Deliverables and Transition Milestones | 29 |
| 11.5 Conduct of the Transition | 30 |
| 11.6 Triple-S Cooperation and Support | 30 |
| 11.7 Completion of Transition | 30 |
| 11.8 In Flight Projects | 31 |
| 12. TRANSFORMATION AND CRITICAL MILESTONES | 31 |
| 12.1 Transformation | 31 |
| 12.2 Critical Milestones | 32 |
| 13. COMPLIANCE WITH LAWS | 33 |
| 13.1 Parties’ Compliance Obligations, Generally | 33 |
| 13.2 Other Compliance Requirements | 34 |
| 13.3 Import/Export Controls | 36 |
| 13.4 Compliance with Data Privacy and Data Protection Laws, Regulations and Policies | 36 |
| 13.5 Business Associate Agreement | 37 |
| 14. DATA SECURITY AND PROTECTION | 37 |
| 14.1 Triple-S Data, Generally | 37 |
| 14.2 Data Security | 37 |
| 14.3 Security Breach | 39 |
| 14.4 Intrusion Detection/Interception | 40 |
| 14.5 Litigation and Investigation Requests | 40 |
| 15. INTELLECTUAL PROPERTY RIGHTS | 42 |
| 15.1 Independent IP | 42 |
| 15.2 Intellectual Property Rights in Work Product | 43 |
| 15.3 Intellectual Property Rights Agreements with Supplier Personnel | 45 |
|
Triple-S / Supplier Confidential Page ii |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
Table of Contents
| 15.4 Rights on Bankruptcy of Supplier | 45 |
| 16. TERMINATION | 45 |
| 16.1 Termination by Triple-S | 45 |
| 16.2 Termination by Supplier | 49 |
| 16.3 Extension of Termination/Expiration Date | 49 |
| 16.4 Partial Termination | 50 |
| 17. DISENGAGEMENT ASSISTANCE | 51 |
| 17.1 General | 51 |
| 17.2 Required Consents | 53 |
| 17.3 Charges for Disengagement Assistance | 54 |
| 17.4 Bid Assistance | 55 |
| 18. GOVERNANCE AND MANAGEMENT | 56 |
| 18.1 Governance Structure and Processes | 56 |
| 18.2 Reports | 56 |
| 18.3 Procedures Manual | 56 |
| 18.4 Change Control Process | 57 |
| 18.5 Audits and Records | 59 |
| 19. REPRESENTATIONS, WARRANTIES AND COVENANTS | 59 |
| 19.1 Work Standards | 59 |
| 19.2 Maintenance | 59 |
| 19.3 Efficiency and Cost-Effectiveness | 59 |
| 19.4 Deliverable Warranty | 59 |
| 19.5 Intentionally Omitted | 60 |
| 19.6 Documentation | 60 |
| 19.7 Compatibility | 60 |
| 19.8 Open Source Code | 60 |
| 19.9 Non-Infringement | 60 |
| 19.10 Viruses Impacting Triple-S | 61 |
| 19.11 Disabling Code | 62 |
| 19.12 Delivery Platforms | 62 |
| 19.13 Corporate Social Responsibility | 63 |
| 19.14 Foreign Corrupt Practices Act | 63 |
| 19.15 Debarment from Federal Contracts and Termination. | 64 |
| 19.16 Claims Procedures, Appeals and External Review | 65 |
| 19.17 No Improper Inducements | 65 |
| 19.18 Immigration | 65 |
| 19.19 [***] Software | 65 |
| 19.20 Non-Infringement | 66 |
| 19.21 Viruses Impacting Supplier | 67 |
| 20. MUTUAL REPRESENTATIONS AND WARRANTIES; DISCLAIMER | 67 |
| 20.1 Mutual Representations and Warranties | 67 |
| 20.2 Disclaimer | 68 |
| 21. CONFIDENTIALITY | 68 |
| 21.1 “Confidential Information” Defined | 68 |
| 21.2 Obligations of Confidentiality | 70 |
|
Triple-S / Supplier Confidential Page iii |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
Table of Contents
| 21.3 No Implied Rights | 71 |
| 21.4 Compelled Disclosure | 72 |
| 21.5 Confidential Treatment of this Agreement | 72 |
| 21.6 Disclosure of Information Concerning Tax Treatment | 72 |
| 21.7 Return or Destruction | 73 |
| 21.8 Destruction Obligations | 74 |
| 21.9 Exceptions to Retention and Destruction Obligations | 74 |
| 21.10 Duration of Confidentiality Obligations | 74 |
| 22. INSURANCE | 75 |
| 22.1 General Terms | 75 |
| 22.2 Types and amounts of coverage | 75 |
| 22.3 Terms of coverage | 77 |
| 23. INDEMNIFICATION | 78 |
| 23.1 Indemnification by Supplier | 78 |
| 23.2 Infringement Claims | 80 |
| 23.3 Indemnification by Triple-S | 80 |
| 23.4 Indemnification Procedures | 82 |
| 23.5 Subrogation | 85 |
| 24. LIABILITY | 85 |
| 24.1 General Intent | 85 |
| 24.2 Limitations of Liability | 85 |
| 24.3 Exceptions to Limitations of Liability | 86 |
| 24.4 Force Majeure | 88 |
| 24.5 Disaster Recovery and Business Continuity | 89 |
| 25. DISPUTE RESOLUTION | 90 |
| 25.1 Informal Dispute Resolution | 90 |
| 25.2 Litigation | 90 |
| 25.3 Continued Performance | 91 |
| 25.4 Equitable Remedies | 91 |
| 25.5 Disclaimer of Uniform Computer Information Transactions Act | 91 |
| 26. RULES OF CONSTRUCTION | 92 |
| 26.1 Entire Agreement | 92 |
| 26.2 Contracting Parties; No Third Party Beneficiaries | 92 |
| 26.3 Contract Amendments and Modifications | 92 |
| 26.4 Governing Law | 92 |
| 26.5 Relationship of the Parties | 92 |
| 26.6 Consents and Approvals | 92 |
| 26.7 Waiver | 93 |
| 26.8 Remedies Cumulative | 93 |
| 26.9 References | 93 |
| 26.10 Rules of Interpretation | 93 |
| 26.11 Order of Precedence | 94 |
| 26.12 Severability | 94 |
| 26.13 Counterparts | 94 |
| 26.14 Reading Down | 94 |
|
Triple-S / Supplier Confidential Page iv |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
Table of Contents
| 27. GENERAL PROVISIONS | 94 |
| 27.1 Survival | 94 |
| 27.2 Binding Nature and Assignment | 95 |
| 27.3 Notices | 95 |
| 27.4 Non-solicitation of Employees | 96 |
| 27.5 Covenant of Good Faith | 96 |
| 27.6 Public Disclosures | 96 |
| 27.7 Service Marks | 96 |
| 27.8 Mutually Negotiated | 97 |
|
Triple-S / Supplier Confidential Page v |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
This Master Services Agreement, effective as of August 31, 2017 (the “Effective Date”), is between Triple-S Salud, Inc., a Puerto Rico corporation, with principal offices located at #1441 ▇.▇. ▇▇▇▇▇▇▇▇▇ ▇▇▇▇▇▇, ▇▇▇ ▇▇▇▇, ▇▇▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇ (“Triple-S”), and OptumInsight, Inc. (“Supplier”), a Delaware corporation, having a primary place of business at ▇▇▇▇▇ ▇▇▇▇▇ ▇▇▇▇▇▇, ▇▇▇▇ ▇▇▇▇▇▇▇, ▇▇ ▇▇▇▇▇ (each, a “Party” and collectively, the “Parties”). The Parties agree that the following terms and conditions shall apply to the services to be provided by Supplier to Triple-S under this Agreement, in consideration of certain payments to be made by Triple-S, all as more specifically described below.
| 1. | PREAMBLE |
| 1.1 | Background and Purpose |
This Agreement is made and entered into with reference to the following:
| (a) | Triple-S is dedicated to providing its members with access to high-quality care at an affordable price. |
| (b) | Supplier and its Affiliates are providers of infrastructure, application development and maintenance, business process, hosting and consulting services. |
| (c) | After a comprehensive evaluation and negotiation process, Triple-S has decided to contract with Supplier for Supplier to provide services to Triple-S, as more fully described in this Agreement. |
| (d) | The Parties are entering into this Agreement to set forth the terms under which Supplier shall provide the Services to Triple-S, and Triple-S shall receive such Services from Supplier. |
| 1.2 | Goals and Objectives |
| (a) | Triple-S and Supplier have the following over-arching goals and objectives associated with the execution of this Agreement and Supplier’s performance hereunder: |
| (i) | Improve the quality, effectiveness and efficiency of Triple-S operations; |
| (ii) | Improve customer service and stakeholder satisfaction, including consistent repeatable process models to reduce compliance risk; |
| (iii) | Reduce Triple-S’s overall cost of providing services to its Members; |
| (iv) | Implement a governance model in which Supplier is a single point of contact for Triple-S with respect to the services and platforms provided by Supplier and other third parties required for Triple-S to receive the Services under this Agreement; |
| (v) | Provide Triple-S with a predictable and inclusive pricing model that aligns with Triple-S business metrics; |
|
Triple-S / Supplier Confidential Page 1 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
| (vi) | Implement a smooth and timely Transition and Transformation of, as applicable, personnel, systems, suppliers and processes with no disruption in Supplier’s provision of service to Triple-S and no disruption to Triple-S in the general conduct of its business; |
| (vii) | Through Supplier’s provision of the Services to Triple-S, allow Triple-S to focus its efforts on creating membership growth for its existing products and plans as well as driving business expansion into new service offerings; and |
| (viii) | For Supplier to establish a new services center based in Puerto Rico to service Triple-S and other Supplier customers throughout the Americas and for Triple-S to share in the financial benefits as the services center grows during the Term. The Parties intend for this service center to create additional jobs in Puerto Rico. |
| (b) | The goals and objectives set out in this Section 1.2 are intended to be a general introduction to, and statement of the spirit of, this Agreement. |
| 1.3 | Structure of Agreement |
This document (the “General Terms and Conditions”) sets out the basic terms and conditions under which the Parties will conduct the transactions contemplated by this Agreement. The following are additional Schedules that are a part of the Agreement.
| General Terms and Conditions |
| Schedule A (Cross Functional Services) |
| Schedule B (Service Level Methodology) |
| Schedule C (Charging Methodology) |
| Schedule C-1 (Charges) |
| Schedule C-2 (T&M Rates) |
| Schedule C-3 (Financial Responsibility Matrix) |
| Schedule C-4 (Termination Charges) |
| Schedule C-5 (TSS Transferred Contracts) |
| Schedule D (Key Supplier Positions) |
| Schedule E (Supplier Facilities) |
| Schedule F (Governance) |
| Schedule G (Form of In-Scope Employee Agreement) |
| Schedule H (Form of Business Associate Agreement) |
| Schedule I (Disengagement Assistance) |
| Schedule J (Triple-S Policies and Procedures) |
| Schedule K (Reports) |
| Schedule L (IT Security Addendum) |
| Schedule M (Audit and Record Retention Requirements) |
| Schedule N (Project Framework) |
| Schedule N-1 (Deliverable and Milestone Acceptance Procedures) |
| Schedule O (Change Control Process) |
| Schedule P (In-Flight Projects) |
| Schedule Q (Supplier Affiliates) |
|
Triple-S / Supplier Confidential Page 2 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
| Schedule R (Approved Subcontractors) |
| Schedule S (Supplier Software and Supplier Tools) |
| Schedule T (Background Checks) |
| Schedule U (CMS Attestation) |
| Schedule V (Intentionally Omitted) |
| Schedule W (Regulatory and Customer Flow Down Requirements) |
| Schedule X (Source of Truth) |
| Schedule Y (Subcontractor Flow-Down Terms) |
| Schedule AA (Glossary) |
| 1.4 | Defined Terms |
Schedule AA (Glossary) lists each defined term used in this Agreement and sets forth either its definition or a cross-reference to the document containing the definition. Those terms, acronyms, and phrases utilized in the information technology outsourcing or health and wellness industry which are not otherwise defined in this Agreement shall be interpreted in accordance with their generally understood meaning in such industry or business context.
2. SERVICES
| 2.1 | Provision of the Services |
| (a) | The “Services” consist of and include the following functions, responsibilities, activities and tasks (collectively, “Functions”), as they may evolve and be supplemented, enhanced, modified or replaced during the Term and in accordance with this Agreement: |
| (i) | any Functions expressly described in this Agreement; |
| (ii) | the Transition Services, as further described in Section 11 (Transition) and in the applicable Transition Documents; |
| (iii) | the Transformation, as further described in Section 12 (Transformation) and in the Transformation Documents; |
| (iv) | Disengagement Assistance, as further described in Section 17 (Disengagement Assistance) and Schedule I (Disengagement Assistance); |
| (v) | any related services, Functions or responsibilities not specifically described in this Agreement that are an inherent, necessary or customary part of the Services or are required or customary for proper performance or provision of the Services (including to complete Transition) in accordance with this Agreement; and |
| (vi) | any Functions that (A) are related to the Services described in this Agreement; and (B) were performed during the twelve (12) months prior to the Service Commencement Date of this Agreement (or during the twelve (12) months prior to the execution of any document executed after the Effective Date (i.e., |
|
Triple-S / Supplier Confidential Page 3 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
Statement of Work, Task Order, Change Order) regarding the Functions added by such document) by Triple-S’s personnel (including employees and contractors and the incumbent provider of such services) who were transitioned to Supplier or displaced, or whose Functions were displaced, as a result of this Agreement or such document (as applicable).
| (b) | The “Services” do not include those Functions expressly designated as Functions for which Triple-S is responsible or otherwise expressly excluded from scope through express qualifications, limitations and exclusions in this Agreement. |
| (c) | Triple-S’s or its Affiliates’ has certain obligations pursuant to that certain Resolution Agreement entered into by Triple-S Management Corporation and The United States Department of Health and Human Services, Office for Civil Rights (“HHS”) dated November 20, 2015, including the Corrective Action Plan incorporated into such Resolution Agreement (the Resolution Agreement and the Corrective Action Plan collectively may be referred to as the “CAP”). Triple-S remains responsible for compliance with the CAP. Supplier understands that Supplier remains responsible for complying under the terms of this Agreement with Triple-S Policies and Procedures and performing Services in accordance with this Agreement, some of which impact Triple-S’ and its Affiliates’ ability to comply with the CAP. |
| 2.2 | New Services |
| (a) | Requests. If Triple-S requires the performance of New Services, Triple-S may deliver to Supplier a written request, in such form as Triple-S reasonably determines, for Supplier to implement such services, specifying the proposed work and desired timeline with reasonable detail. |
| (b) | Response. Within ten (10) Business Days (or, if the requested services cannot reasonably be evaluated within such time period, then such longer period of time as mutually agreed by Triple-S and Supplier) after the date of such request, Supplier shall, at no charge to Triple-S, provide Triple-S with a written evaluation of such request containing high level estimates of the scope of the work and the cost and estimated timing of implementing such work, as well as any impact on the pricing and Service Levels provided hereunder. |
| (c) | Proposal. If Triple-S so requests, Supplier shall then provide a written proposal (a “New Service Proposal”) containing, at a minimum, the following: (i) reasonably detailed specifications, implementation plans, work schedules, timeframes for performance, and Acceptance Criteria; and (ii) a price quote of the fees that Supplier would charge for the services described therein, together with adequate detail concerning the price quote for Triple-S to evaluate it, including, where requested by Triple-S, details regarding the “total cost of ownership,” including, as applicable, initial purchase price of hardware, software (supplier owned and third party software), or services; labor hours; labor skill levels; training; operations support; inventory management; warranty support; transportation; licensing costs; and cost and quality criteria and data. If the price is quoted on a T&M basis, the rates shall not exceed those specified in the Skills |
|
Triple-S / Supplier Confidential Page 4 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
Matrix Rate Card for the applicable resources; provided, however, that Supplier will provide T&M Rates in the New Service Proposal for any resources not specified on the Skills Matrix Rate Card and required for the New Services. Supplier shall also include in the proposal a draft Statement of Work for New Services in a form specified by Triple-S in its reasonable discretion (a “New Service Statement of Work”) and, to the extent applicable, a proposed amendment to the Agreement for approval in accordance with Section 26.3 (Contract Amendments and Modifications).
| (d) | New Service Statement of Work. Upon each Party’s written acceptance and execution of the New Services Statement of Work, the draft New Service Statement of Work shall be binding on the Parties and governed by and subject to the terms of this Agreement. |
| (e) | Documentation. Supplier will not perform, and will not be obligated to perform, any additional Functions that would constitute New Services prior to informing Triple-S of what the additional charges would be for performing them (which shall take into account Supplier’s account resources and expenses for the then-existing Services that would no longer be provided or incurred), and receiving Triple-S’s written authorization to proceed. Upon execution of appropriate documentation for New Services as described above, such New Services shall be governed by this Agreement. If Supplier does perform the additional Functions that constitute New Services without Triple-S’s prior written authorization, such services will be deemed to have been performed as part of the Services at no additional charge. Triple-S shall not be obligated to pay for, and Supplier will not be obligated to perform, any New Service which has not been properly authorized by Triple-S and agreed to in writing by Supplier. |
| 2.3 | “Master” Nature of the General Terms and Conditions |
The Parties intend that these General Terms and Conditions and this Agreement will govern the Services and any New Services that the Parties agree will be provided by Supplier after the Effective Date.
| (a) | The Parties shall enter into statements of work (each a “Statement of Work” or “SOW”) that will reflect the terms under which Services shall be provided by Supplier to Triple-S. |
| (i) | As of the Effective Date, the Parties are entering into the Initial SOWs. |
| (ii) | If, after the Effective Date, the Parties agree upon additional services that they desire to be governed by these General Terms and Conditions, they shall enter into additional SOWs (“Future SOWs”) each in substantially the same format and containing the same information as in the Initial SOWs. |
| (b) | Changes to Services previously contracted for will be considered and carried out in accordance with the terms relating to the Change Control Process set forth in Section 18.4 and the Change Control Process set forth in Schedule O (Change Control Process). |
| (c) | Each Statement of Work, Task Order, Change Order and similar document entered into under this Agreement is part of this Agreement as if fully set forth herein and shall be governed by and subject to the terms of this Agreement. |
|
Triple-S / Supplier Confidential Page 5 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
| (d) | A duly executed Statement of Work, Task Order, Change Order or similar document may override this Agreement with respect to that particular document if, and only if, the document expressly states that the Parties intend to deviate from the terms and conditions of this Agreement for that particular document. Superseding provisions that pertain to the following will not be effective unless first reviewed and approved in writing by the legal department of each Party: (A) Section 14 (Data Security and Protection); (B) Section 15 (Intellectual Property Rights); (C) Supplier’s representations, warranties and covenants set forth in Sections 19.4 (Deliverable Warranty) and 19.9 (Non-Infringement); (D) Section 23 (Indemnification); or (E) Section 24 (Liability). |
| 2.4 | Services Commencement |
| (a) | Initial SOWs. Supplier shall commence performing applicable Transition Services for the Initial SOWs on the Effective Date (or the date specified in the Initial SOW, if later), and shall commence performing the steady state Services for the Initial SOWs on the applicable Service Commencement Date for such Services. |
| (b) | Future Services. For future Services, Supplier shall commence providing the Transition Services on the date of the applicable Statement of Work, Task Order, Change Order or amendment adding such Services (or the date specified in the applicable Statement of Work, Task Order, Change Order or amendment, if later), and shall commence performing the steady state Services on the applicable Service Commencement Date for such Services. |
| 2.5 | Evolution and Innovation of the Services |
Throughout the Term, Supplier will improve the quality, efficiency and effectiveness of the Services to keep pace with advances in technology and the delivery of similar business process services to Supplier’s commercial customers that support Triple-S’s (and its Affiliates’) evolving business needs and efforts to maintain competitiveness in the markets in which it (and they) competes. Without limiting the generality of the foregoing, Supplier will: (a) identify and apply industry standards and Supplier’s ‘best practice’ or ‘leading’ techniques and methodologies in performing and delivering the Services (subject to other obligations and other requirements under this Agreement); (b) train Supplier Personnel in new techniques and technologies used generally within Supplier’s organization for commercial customers; and (c) make investments reasonably required to maintain the currency of Supplier’s Tools, infrastructure, Software and other resources used by Supplier to render the Services. Changes in the Services pursuant to this Section 2.5 will not be considered New Services.
| 2.6 | Users of the Services |
| (a) | Supplier will provide the Services to Triple-S and, as designated by Triple-S from time to time: |
| (i) | to existing and future Triple-S Affiliates; |
| (ii) | to Former Triple-S Affiliates; |
|
Triple-S / Supplier Confidential Page 6 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
| (iii) | in support of employer groups to which Triple-S provides contracted administrative services; |
| (iv) | in support of any delegation or TPA (third party administrator) arrangements existing as of the Effective Date or into which Triple-S or its Affiliates may enter in the future; and |
| (v) | to support any of Triple-S’s or Triple-S’s Affiliates’ contractual obligations and business relationships with its customers, members and providers. |
(each such entity above “Service Recipient”), upon the terms and conditions (including Charges) set forth in this Agreement.
| (b) | Services provided to such entities under this Agreement shall be deemed to be Services provided to Triple-S.Triple-S shall be directly responsible for (i) the payment of all Charges associated with Supplier’s provision of Services to Service Recipients under this Agreement and (ii) as and to the extent related to any Service Recipient’s use of the Services, the performance, breach or other wrongful conduct of any such Service Recipient, as if they were Triple-S (including acts or omissions of such Service Recipient) for purposes of determining Triple-S’s liability under this Agreement (including Triple-S’s indemnification and confidentiality obligations). Triple-S may exercise its rights pursuant to this Section by providing written notice to Supplier of any such Service Recipient. |
| (c) | With respect to Former Triple-S Affiliates, Supplier will continue to provide the Services being provided as of the date of divestiture as is requested by Triple-S for as long as such entity continues to meet the definition of Former Triple-S Affiliate (or such shorter period of time designated by Triple-S) so long as (i) Triple-S continues to pay all applicable Charges with respect to any such Services and remains responsible for the Former Triple-S Affiliates as set forth in Section 2.6(b); and (ii) such Services remain subject to the Change Control Process if material technology or other Changes are required to provide Services to the Former Triple-S Affiliate. |
| (d) | There shall be no additional charge or fee (i.e., charges or fees in addition to the Charges for the actual Services as provided in this Agreement) for the provision of Services to Service Recipients so long as the Services remain subject to the Change Control Process if material technology or other Changes are required to provide Services to the Service Recipients. |
| 2.7 | Services Not Exclusive; Variable |
| (a) | This Agreement is non-exclusive. Nothing in this Agreement shall be construed to limit in any way Triple-S’s ability to reduce the volumes of Services being provided by Supplier pursuant to this Agreement or to contract with other third parties to provide products or services that are the same as or similar to the Services or that are part of the Services. Triple-S (and its Affiliates) may also insource any such product or service and provide such product or service to itself or its Affiliates. In the case of Triple-S’s withdrawal of portions of the Services from Supplier (including a withdrawal by Triple-S |
|
Triple-S / Supplier Confidential Page 7 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
of any volumes of Services or Functions from the scope of this Agreement), the Charges shall be reduced using the unit rates and charging methodologies provided in Schedule C (Charging Methodology), or otherwise in an equitable manner to the extent such unit rates and charging methodologies do not apply to the withdrawn portions of the Services.
| (b) | The Services are variable in volume. Such variations are provided for in the charging mechanisms set forth in Schedule C (Charging Methodology). Supplier shall be responsible for adjusting the resources used to provide the Services to accommodate the changes in volume (regardless of the amount of time remaining in the Term) in such a manner as to comply with all Service Levels. Supplier shall not be entitled to receive an adjustment to the Charges resulting from such variations in volume except as set forth in Schedule C (Charging Methodology). |
| (c) | Triple-S (and its Affiliates) makes no commitment for any minimum or maximum volume, scope, or value of the Services under this Agreement or to any minimum or maximum payments to be made to Supplier (except to the extent that Triple-S makes an express commitment to provide Supplier with such a minimum or maximum volume, scope or payments in Schedule C (Charging Methodology)). |
| (d) | This Section 2.7 is not intended to limit or modify any exclusivity, minimum volume or minimum fee or Charge commitments (including any binding forecasts or minimum membership levels) that may be expressly set forth in a Statement of Work or in Schedule C (Charging Methodology). |
| (e) | This Section 2.7 is subject in all respects to Section 16.4(c) (Partial Termination). |
| 2.8 | Cooperation and Coordination with Other Parties |
If Triple-S performs itself, or retains a third party to perform, any services for Triple-S that interface or interact with the Services, or that formerly were part of the Services, Supplier will cooperate and coordinate with Triple-S or such third party as reasonably required for Triple-S or the third party to perform such services. Supplier’s cooperation and coordination will include, as applicable: (a) providing access to the facilities being used by Supplier to provide the Services as necessary for Triple-S or the third party to perform its work; (b) providing reasonable access to the Equipment and Software used in providing the Services; and (c) providing such information regarding the operating environment, system constraints and other operating parameters as a person with reasonable commercial skills and expertise would find reasonably necessary for Triple-S or the third party to perform its work. Triple-S will require any such third parties to enter into an agreement with Triple-S with confidentiality terms substantially similar to those in Section 21 (Confidentiality) of these General Terms and Conditions and to comply with the other applicable terms of this Agreement. Notwithstanding anything in this Section 2.8, Triple-S will not provide any such access to proprietary Supplier Software or Supplier Tools to a third party under this Section 2.8 unless such third party first enters into a user access or similar agreement directly with Supplier that contains terms substantially similar to the terms of this Agreement with respect to use, and restrictions on use, of Supplier Software, Supplier Tools or Supplier Equipment, as applicable; provided that Supplier acknowledges such access with be at no additional charge.
|
Triple-S / Supplier Confidential Page 8 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
| 3. | TERM AND REGULATORY APPROVALS |
| 3.1 | Initial Term |
| (a) | The term of this Agreement shall commence on the Effective Date and expire as of midnight Eastern Time on August 31, 2027, unless it is terminated earlier or is extended pursuant to the terms of this Agreement (such period, together with all extensions and Renewal Periods, the “Term”). |
| (b) | The term of each Statement of Work, Task Order, and Change Order shall commence on the Effective Date for such document and shall expire on the date set forth in such document, unless it is terminated earlier or is extended pursuant to the terms of this Agreement (such period, together with all extensions and applicable Renewal Periods, the “Document Term”); provided, however, that no Document Term will extend beyond the Term of this Agreement (except those relating to Disengagement Assistance). |
| 3.2 | Renewal Terms |
| (a) | By giving notice to Supplier no less than ninety (90) days prior to the then-existing expiration date of this Agreement, Triple-S may extend the Term for a period designated by Triple-S of up to one (1) year (each, a “Renewal Period”) on the terms and conditions then in effect (including the Charges and any applicable cost of living adjustments and applicable productivity increases set forth in Schedule C (Charging Methodology)). Triple-S shall have two (2) such extension options of up to one (1) year each. |
| (b) | With respect to each Statement of Work, Task Order, Change Order or similar document, Triple-S shall have the same rights to extend the applicable Document Term that it has to extend the Term under this Section 3.2, unless such document expressly provides otherwise, or by such other period as may be agreed by the Parties, provided, however, that no Document Term will extend beyond the Term of this Agreement (except those relating to Disengagement Assistance). |
| 3.3 | Regulatory and Regulatory Contract Approvals |
The Parties acknowledge that Triple-S must obtain regulatory approvals or approvals pursuant to Applicable Law or contracts involving government programs in order for certain of the Functions and geographic scope that the Parties contemplate to be included in the scope of this Agreement to be actually included in the scope of this Agreement after the Effective Date. If Triple-S is not able to obtain such approvals, or if Triple-S obtains such an approval that is later revoked or threatened to be revoked (in each case, Triple-S will provide Supplier prompt notice) and, in either case, the Parties are unable to agree upon an equitable adjustment in the Charges or the scope of the affected Services and other terms of this Agreement that would enable Triple-S to obtain such approval or retain an approval that may be revoked (without adverse impact to Triple-S), then (a) Triple-S shall have the right to remove any impacted Services or volumes from the scope of the Agreement in accordance with Section 2.7(a), and (b) Triple-S shall have the termination rights set forth in Section 16.1(h) (Termination Relating to Regulatory Approval).
|
Triple-S / Supplier Confidential Page 9 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
| 3.4 | Customer Approvals |
The Parties acknowledge that Triple-S must obtain approvals from certain customers in order for certain of the Functions and geographic scope that the Parties contemplate to be included in the scope of this Agreement to be actually included in the scope of this Agreement after the Effective Date. If Triple-S is not able to obtain any such approval, and the Parties are unable to agree upon an equitable adjustment in the Charges or the scope of the affected Services and other terms of this Agreement that would enable Triple-S to obtain such approval (without adverse impact to Triple-S), then Triple-S shall have the right to remove any impacted Services or volumes from the scope of the Agreement in accordance with Section 2.7(a).
| 3.5 | Additional Contract Clauses |
Schedule W (Regulatory and Customer Flow-Down Terms) contains provisions which Triple-S is obligated to include in any contract with any subcontractor. Such provisions are hereby incorporated into this Agreement by reference. Supplier agrees to comply with all such provisions to the extent such provisions are applicable to Supplier as a Triple-S subcontractor. Supplier further agrees to pass through such obligations to any Supplier Subcontractor (other than Non-Key Subcontractors) in a similar manner and where the applicable agreement with the Subcontractor is being entered into specifically for performance of the Services or is up for a negotiated renewal between the parties (i.e., excluding evergreen renewals).
4. PERFORMANCE
| 4.1 | Performance, Generally |
| (a) | Supplier is responsible for managing and successfully performing, completing, and delivering the Services, subject to any overall direction provided by Triple-S and with the cooperation and support of Triple-S, Service Recipients and Managed Third Parties as specified in this Agreement. |
| (b) | In cases where this Agreement does not prescribe or otherwise regulate the manner or quality of Supplier’s performance, Supplier will render the Services with at least the same degree of accuracy, quality, timeliness, responsiveness and efficiency as was generally achieved or obtained by (or for) Triple-S (and its Affiliates) prior to Supplier assuming responsibility under this Agreement for the affected Functions. |
| 4.2 | Place of Performance |
| (a) | Schedule E (Supplier Facilities) describes the Supplier facilities in the United States and outside the United States from which Supplier is authorized to provide Services as of the Effective Date, and identifies which Services are authorized to be provided from each such Supplier facility (collectively, the “Supplier Facilities”); provided, however, that Supplier may also perform Services using field and remote (i.e., work from home) resources located in the United States and (i) any location at which such Services are performed by field or remote resources does not constitute a Supplier Facility for purposes of this Agreement; and (ii) Supplier will cause all such Services to be performed in accordance with Supplier’s policies and procedures for field and remote resources and with applicable Triple-S Policies and Procedures. |
|
Triple-S / Supplier Confidential Page 10 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
| (b) | During the Term and any Disengagement Assistance Period, Supplier will not (i) change any location from which it provides Services to Triple-S, or (ii) materially reallocate the volume or nature of work being performed from one facility to another facility, without Triple-S’s prior written consent, which Triple-S may grant or withhold in its reasonable discretion, provided that if a proposed change in location or reallocation of volumes or nature of work involves a change in location from a facility located in the United States to a facility located in any other country, or a change from a facility located in one country to a facility located in another country, then Triple-S’s prior approval may be granted or withheld in Triple-S’s sole discretion. This Section 4.2(b) is not intended to limit Supplier’s right to change locations from a production Supplier Facility to a back-up Supplier Facility listed in Schedule E when necessary to execute its disaster recovery and business continuity plans. |
| (c) | Notwithstanding anything else set forth in this Section 4.2 to the contrary, all Supplier Facilities from which Services are provided shall be Top Tier Facilities with respect to physical security, data security, employee background checks and similar matters, and Supplier shall provide Services from Supplier Facilities that are not Top Tier Facilities only with the prior written approval of Triple-S, which prior approval may be granted or withheld in Triple-S’s reasonable discretion and subject to such conditions as Triple-S considers appropriate in the circumstances. |
| (d) | Supplier will manage any relocations or reallocations of work in accordance with standards practiced by tier 1 providers of services similar to the Services, and in accordance with a migration plan to be prepared by Supplier, which migration plan shall (i) be provided by Supplier to Triple-S not less than sixty (60) days prior to the scheduled relocation or reallocation date, and (ii) be subject to the prior written approval of Triple-S. |
| (e) | Supplier will fully examine and evaluate the risks and anticipated effects of the contemplated relocation or reallocation on the Services and Triple-S, including the operational, technical, security, regulatory, and other effects, and will prepare and submit to Triple-S an analysis of the effects not less than sixty (60) days prior to the scheduled relocation or reallocation date. |
| (f) | Supplier will be responsible for all direct and indirect costs, taxes and other expenses incurred by Supplier, and any new or additional costs, taxes and other expenses incurred by Triple-S, arising out of any Supplier-initiated relocation of an operational facility from which the Services are provided or any reallocation of volume or nature of Services being provided from one Supplier Facility to another. |
| (g) | The Parties acknowledge and agree that Supplier may use certain Triple-S facilities (as agreed to by the Parties and documented in Schedule C-3 (Financial Responsibility Matrix)) to perform certain of the Services and the requirements of Sections 4.2(a) through 4.2(d) (Place of Performance) do not apply to Supplier’s use of such Triple-S facility. |
|
Triple-S / Supplier Confidential Page 11 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
| 4.3 | Time of Performance |
| (a) | Supplier will (and will provide the resources necessary to) complete the Services in accordance with any applicable time schedules set forth in this Agreement. |
| (b) | Supplier will promptly notify Triple-S upon becoming aware of any circumstances that may reasonably be expected to jeopardize the timely and successful completion (or delivery) of any Service in a material manner. Supplier will use Commercially Reasonable Efforts to avoid or minimize any delays in performance and will inform Triple-S of the steps Supplier is taking or will take to remediate any such problem, and the projected actual completion (or delivery) time for remediating any such problem. |
| 4.4 | Triple-S Policies and Procedures |
| (a) | Except as this Agreement expressly provides otherwise, Supplier will perform the Services in compliance with Triple-S Policies and Procedures, provided that: |
| (i) | any new Triple-S Policies and Procedures or modifications to Triple-S Policies and Procedures will be disclosed to Supplier either (A) in writing or (B) upon Supplier Personnel being notified of, and provided access to, such new or modified Triple-S Policies and Procedures in the same manner as Triple-S notifies its employees and other third parties (for example, posting a sign or via Triple-S’ Compliance360 (or successor) portal); and |
| (ii) | if compliance with any such new or modified Triple-S Policies and Procedures introduced or modified after the Effective Date requires Supplier to incur additional costs, and such compliance is not otherwise required by Supplier under this Agreement (including as set forth in Section 13 (Compliance with Laws), then such Changes shall be implemented through the Change Control Process. |
| (b) | Notwithstanding the foregoing, the date Supplier is required to comply with any such new or revised Triple-S Policies and Procedures shall be the compliance or effective date listed in the applicable Statement of Work, Task Order or Change Order executed by both Parties, provided that in no event shall such date be later than any date required by Law or Other Compliance Obligation for implementation of such Change. |
| 4.5 | Quality Assurance and Continuous Improvement |
In performing the Services, Supplier will follow commercially reasonable quality assurance procedures designed to provide that the Services are performed with a high degree of professional quality and reliability. Such procedures shall include checkpoint reviews, testing, acceptance, and other procedures for Triple-S to confirm the quality of Supplier’s performance. Supplier, as part of its quality management process, will provide continuous quality assurance and quality improvement through: (a) the identification and application of proven techniques and tools from other installations within its operations; (b) the implementation of programs, practices and measures designed to improve performance (including the Service Levels); and (c) annual certification of the quality and currency of all Documentation (e.g., procedures and runbooks). Supplier will utilize project management tools, including productivity aids and project management systems, as appropriate in performing the Services. Supplier shall comply with any continuous improvement clauses set forth in the Regulatory Contracts.
|
Triple-S / Supplier Confidential Page 12 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
| 4.6 | Medicare Attestations |
At Triple-S’ request, Supplier shall complete an offshore attestation(s) in the form substantially similar to Schedule U (Offshore Attestation Form) no later than fifteen (15) Business Days after the receipt of such request. Schedule U-1 (Completed Offshore Attestation) contains a completed attestation from Supplier relating to the Services that Supplier is authorized to provide from outside the United States as of the Effective Date.
| 5. | SERVICE LEVELS AND CREDITS |
| 5.1 | General |
Service Levels are set forth in Schedule B (Service Level Methodology). Supplier shall perform the Services at a level of performance that is equal to or better than the Service Levels identified in Schedule B (Service Level Methodology) to this Agreement. If Supplier fails to meet a Critical Service Level (as defined in Schedule B (Service Level Methodology)), Supplier shall pay a Service Level Credit to Triple-S in accordance with Schedule B (Service Level Methodology).
| 5.2 | Credits |
| (a) | Service Level Credits will not be construed as a penalty or as liquidated damages and will not be deemed to constitute Triple-S’s remedy, exclusive or otherwise, for any actual damages caused by a failure to meet a Critical Service Level; provided, however, that if Triple-S receives any Service Level Credits as a result of such a failure, then the amount of damages then recoverable by Triple-S with respect to such failure shall equal (i) the total amount of damages then recoverable under this Agreement by Triple-S with respect to such failure, without consideration of whether any Service Level Credits resulting from such failure had been provided to Triple-S; less (ii) any amounts received by Triple-S as Service Level Credits that result from such failure. |
| (b) | Nothing set forth in this Agreement shall preclude Triple-S from exercising its termination rights (to the extent they would otherwise be available as set forth in this Agreement) for a failure to meet a Critical Service Level, or from exercising any other remedies available to Triple-S under the Agreement, at law, or in equity to address any other non-duplicative damages Triple-S or its Affiliates may suffer or incur as a result of such a failure by Supplier (or another entity or person for which Supplier is responsible). Supplier hereby irrevocably waives any claim or defense that Service Level Credits are not enforceable or that they constitute Triple-S’s sole and exclusive remedy with respect to a failure to meet a Critical Service Level. |
| 6. | SUPPLIER PERSONNEL |
| 6.1 | Responsibility for Supplier Personnel, Generally |
| (a) | Supplier will manage, supervise and provide direction to Supplier Personnel and cause them to comply with the obligations and restrictions applicable to Supplier under this Agreement. Supplier will make Supplier Personnel aware of, and cause them to comply with, applicable Triple-S Policies and Procedures (including those regarding safety and |
|
Triple-S / Supplier Confidential Page 13 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
security) while they are performing Services at Triple-S Facilities or accessing Triple-S Data or Triple-S systems. As between Supplier and Triple-S, Supplier is responsible for all wages, salaries and other amounts due Supplier Personnel, and for all tax withholdings, unemployment insurance premiums, pension and social welfare plan contributions, and other employer obligations with respect to Supplier Personnel, in each case to the extent such amounts are owed for periods when such employees are employed by Supplier. Supplier is responsible for the acts and omissions of Supplier Personnel under or relating to this Agreement.
| (b) | As between Supplier and Triple-S, Triple-S is responsible for all wages, salaries and other amounts due to Triple-S employees, and for all tax withholdings, unemployment insurance premiums, pension and social welfare plan contributions, and other employer obligations with respect to Triple-S employees, in each case to the extent such amounts are owed for periods when such employees are employed by Triple-S. |
| (c) | Supplier shall provide any training reasonably necessary for Supplier Personnel to perform the Services (including technical training). Training required for Supplier Personnel shall not be chargeable to Triple-S. |
| (d) | Supplier shall maintain staffing levels as required for Supplier to properly perform Supplier’s obligations under and in accordance with this Agreement. If any Supplier Personnel leave the employment of Supplier or the Triple-S account, Supplier will provide any replacement personnel (as may be necessary for Supplier’s continued performance of the Services) who have experience, skills and technical expertise required to perform the related Services and are in the same location as the Supplier Personnel they are replacing. Supplier shall ensure (to the extent reasonably possible) that any outgoing Supplier Personnel leaving the Triple-S account spend a reasonable period of time training the new Supplier Personnel, if any, who will be replacing such outgoing personnel. Furthermore, if the scope of the Services changes in a manner requiring staffing adjustments of Supplier Personnel, the Parties shall work in good faith to develop a mutually agreed solution for Supplier to staff the revised scope of Services accordingly, which solution will be agreed to in the Statement of Work, Change Order or Task Order. Supplier is responsible for taking action at its own expense to ensure that Supplier Personnel assigned to perform Services have the legal right to work in the countries in which they are assigned to work. |
| 6.2 | Screening and Background Checks |
Supplier shall perform the screening, Background Checks and drug testing described in Schedule T (Background Checks) for all Supplier Personnel; provided, however, that (a) Supplier may omit the drug testing required under Section 2(i) Schedule T (Background Checks) for certain Approved Subcontractors in its reasonable discretion where such testing is not otherwise required by Supplier’s internal compliance and subcontracting policies; and (b) Supplier may omit other requirements of Schedule T (Background Checks) for Approved Subcontractors so long as screening and Background Checks performed by Approved Subcontractors comply with applicable Law and are substantially similar to the other screening and Background Checks described in Schedule T (Background Checks).
|
Triple-S / Supplier Confidential Page 14 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
| 6.3 | Key Supplier Positions and Other Requirements |
| (a) | The “Key Supplier Positions” as of the Effective Date are listed in Schedule D (Key Supplier Positions – Account Level) and in each Statement of Work. The Supplier Account Executive will be one of the Key Supplier Positions. Supplier will cause each of the Supplier Personnel filling the Key Supplier Positions (whether as of the Effective Date, or replacement personnel filling such Key Supplier Position during the Term or the Disengagement Assistance Period) to be dedicated to the provision of the Services, except as otherwise specified on Schedule D (Key Supplier Positions – Account Level). Supplier Personnel approved as of the Effective Date to fill the Key Supplier Positions are listed in Schedule D (Key Supplier Positions – Account Level) and in each SOW. |
| (b) | Before the initial and each subsequent assignment of an individual to a Key Supplier Position, Supplier will notify Triple-S of the proposed assignment and, consistent with Supplier’s personnel practices, provide Triple-S a curriculum vitae and other job-relevant information legally permissible under applicable privacy Laws about the individual reasonably requested by Triple-S. Upon Triple-S’s reasonable request, Supplier will provide Triple-S representatives an opportunity to meet the individual. If Triple-S in good faith objects to the proposed assignment, the Parties will attempt to resolve Triple-S’s concerns on a mutually agreeable basis. If the Parties have not been able to resolve Triple-S’s concerns within ten (10) Business Days, Supplier may not assign the individual to that position and must propose the assignment of another suitably qualified individual. |
| (c) | Triple-S may, no more than once in each twelve (12) month period, change the positions designated as Key Supplier Positions under this Agreement by providing at least one hundred eighty (180) days prior written notice and so long as such change does not increase the number of individuals filling Key Supplier Positions, without Supplier’s consent. The provisions of this Section 6.3 will extend to any re-designated positions, but will no longer apply to any positions which were formerly a Key Supplier Position. |
| (d) | Without prior written approval by Triple-S, which may be withheld in Triple-S’s discretion (provided that Triple-S will not unreasonably withhold its approval where Supplier requests relief from this requirement), and subject to the last sentence of this Section and any exceptions set forth on Schedule D (Key Supplier Positions – Account Level), Supplier will not reassign or replace any person assigned to a Key Supplier Position during the first [***] of his or her assignment to such Key Supplier Position. Subject to the prior sentence and the last sentence of this Section, Supplier will give Triple-S at least 45 days advance notice of a proposed change in personnel filling a Key Supplier Position, and will discuss with Triple-S any objections Triple-S may have. Supplier will arrange, at no charge, for the proposed replacement to work side-by-side with the individual being replaced for not less than 30 days during the notice period to effectuate a seamless transfer of knowledge prior to the incumbent leaving the Key Supplier Position, unless the outgoing Supplier Personnel is not available due to the circumstances described in the last sentence of this Section. Subject to the last sentence of this Section, individuals filling Key Supplier Positions may not be transferred or re-assigned until a suitable replacement has been approved by Triple-S, and no such re-assignment or transfer may occur at a time or in a manner that would have a materially |
|
Triple-S / Supplier Confidential Page 15 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
adverse impact on delivery of the Services or Triple-S’s operations. Notwithstanding anything herein to the contrary, Supplier may remove an individual filling a Key Supplier Position for reasons of death, disability, resignation, military leave, termination from employment by Supplier, leave pursuant to the Family Medical Leave Act or maternity leave and other leaves required by Law.
| (e) | Account Executives. |
| (i) | During the Term and the Disengagement Assistance Period, Supplier will provide a Supplier Account Executive (the “Supplier Account Executive”) dedicated to the Triple-S account. The Supplier Account Executive shall be available for meetings and work at the Triple-S San ▇▇▇▇ offices or such other Triple-S office as Triple-S reasonably requests. The Supplier Account Executive will be a Key Supplier Position. The Supplier Account Executive will be authorized to act as Supplier’s primary contact with respect to Supplier’s obligations under this Agreement. The Supplier Account Executive will have day-to-day responsibility for managing the delivery of the Services and coordinating the delivery of the Services with the Program Manager (as defined below). The Supplier Account Executive may designate in writing additional Supplier Personnel to be a point of contact for Triple-S. |
| (ii) | The Triple-S Program Manager described in Section 7 will be authorized to act as Triple-S’s primary contact for Supplier with respect to Triple-S obligations under this Agreement. |
| (f) | Organizational Chart of Supplier and Supplier Personnel. On a quarterly basis, Supplier will provide to Triple-S a reasonably detailed organizational chart of Supplier’s then-current organization providing the Services. |
| (g) | Resumes. Upon Triple-S’s request, Supplier shall provide copies of the resumes of the Supplier Personnel filling Key Supplier Positions. |
| 6.4 | Removal and Replacement of Supplier Personnel |
| (a) | Triple-S may immediately remove any individual Supplier Personnel from any Triple-S Facilities if the person is threatening or abusive, commits a crime, engages in an act of dishonesty while performing Services for Triple-S or materially violates Triple-S Policies and Procedures, including those pertaining to harassment, alcohol and drug free workplace, safety, or security or use of Triple-S Facilities. |
| (b) | If Triple-S determines in good faith that the continued assignment to Triple-S’s account of any individual who is a Supplier Personnel is not in the best interests of Triple-S, then Triple-S may give Supplier written notice to that effect. After receipt of such a notice, Supplier will: (i) temporarily remove such Supplier Personnel from the performance of the Services; and (ii) have a reasonable period of time (not to exceed ten (10) Business Days after receipt of Triple-S’s notice) in which to investigate the matters stated in the notice, discuss its findings with Triple-S and resolve Triple-S’s concerns. If, following such process, Triple-S requests permanent replacement of the individual, Supplier will |
|
Triple-S / Supplier Confidential Page 16 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
(A) promptly remove such Supplier Personnel from the Triple-S account, and (B) replace such Supplier Personnel or cause such Supplier Personnel to be replaced with another suitably qualified person.
| 6.5 | Controlling Turnover of Supplier Personnel |
| (a) | Triple-S and Supplier agree that it is in their mutual best interests to keep the turnover rate of Supplier Personnel to a reasonably low level. Accordingly, if Triple-S believes that Supplier’s turnover rate is so excessive that the Services are adversely affected in a material manner (in Triple-S’s reasonable judgment), and so notifies Supplier, Supplier will provide data concerning its turnover rate and meet with Triple-S to discuss the reasons for, and impact of, the turnover rate. If requested by Triple-S, Supplier will submit to Triple-S its proposals for reducing the turnover rate, and in addition to any rights that Triple-S may have pursuant to Schedule B (Service Level Methodology), if any, the Parties will mutually agree on a program to bring the turnover rate down to an acceptable level. Supplier will provide Triple-S a report describing Supplier Personnel turnover from time-to-time upon request, but not more than once per twelve (12) month period. |
| (b) | Notwithstanding any turnover of Supplier Personnel, Supplier remains obligated to perform the Services in compliance with the requirements of this Agreement. |
| 6.6 | Subcontracting |
Supplier may subcontract or delegate the performance of Services only in accordance with the following:
| (a) | Except as set forth in Section 6.6(g) and 6.6(h), Supplier shall not subcontract for performance of, or delegate any of, its responsibilities under this Agreement (including to any current or future Affiliates) without first obtaining the prior written approval of Triple-S, which may be granted or withheld in Triple-S’s reasonable discretion. When seeking such approval, Supplier will give Triple-S reasonable prior written notice specifying the components of the Services affected, the scope of the proposed subcontract, and the identity and qualifications of the proposed Subcontractor. Supplier further recognizes that it may not subcontract for performance of, or delegate any of, its responsibilities under this Agreement without, to the extent approvals are required, first obtaining certain regulatory approvals as set forth in Schedule W (Regulatory Requirements) and certain customer approvals as set forth in Section 3.4. Any such Subcontractor that meets the required regulatory approvals and is approved by Triple-S (where such approval is required) and all other Subcontractors for which Triple-S approval is not required (i.e., Non-Key Subcontractors) shall be an “Approved Subcontractor” hereunder. |
| (b) | For avoidance of doubt, nothing in this Section 6.6 (Subcontracting) will limit the requirements under Section 4.2 (Place of Performance); provided that such requirements do not apply to Non-Key Subcontractors. |
| (c) | The Subcontractors that Triple-S has approved (where such approval is required) as of |
|
Triple-S / Supplier Confidential Page 17 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
the Effective Date are listed in Schedule Q (Supplier Affiliates) and Schedule R (Approved Subcontractors), and are deemed Approved Subcontractors by Triple-S for the Functions applicable to each such Subcontractor set forth in Schedule Q and Schedule R, respectively. If Triple-S approves (where such approval is required) any additional Subcontractors after the Effective Date, they shall be added to Schedule Q or Schedule R (as applicable). In addition, the Parties may add Approved Subcontractors via letter or other informal written document signed by both Parties.
| (d) | Supplier may use Approved Subcontractors to perform the Services to the extent permitted by Triple-S’s approval (where such approval is required) as set forth in Section 6.6(a) or, where Triple-S’s approval is not required, as determined by Supplier. Supplier is responsible for managing all Subcontractors. Supplier remains responsible for all Functions subcontracted or delegated to Subcontractors to the same extent as if such Functions were to be or were performed by Supplier acting through its officers, directors, employees, and agents and, for purposes of this Agreement, such Functions will be deemed Functions performed by Supplier. |
| (e) | Supplier shall not restrict or prevent (including by contract) any Subcontractor from entering into an agreement with Triple-S to perform services directly for Triple-S. |
| (f) | As between the Parties, Supplier shall be responsible for all acts and omissions of: |
| (i) | Supplier independent contractors and other Subcontractors as if they were Supplier’s employees (including acts or omissions of such independent contractors and Subcontractors) for purposes of determining Supplier’s liability under this Agreement (including Supplier’s indemnification and confidentiality obligations); |
| (ii) | Supplier Personnel and Supplier Affiliates; and |
| (iii) | any third party to whom Supplier permits access to Triple-S Data or Triple-S Confidential Information. |
| (g) | For clarification, Managed Third Parties (as defined in Schedule A (Cross Functional Services)) shall not be considered Subcontractors for purposes of this Agreement and all resources or items provided by Managed Third Parties shall be deemed to be provided by Triple-S and shall be treated as such for purposes of this Agreement, including provisions relating to facilities, equipment, contracts, Software and Tools; provided Supplier remains responsible for performing the vendor management services described in Schedule A (Cross Functional Services) with respect to such Managed Third Parties. |
| (h) | Supplier may, in the ordinary course of business and without obtaining the prior approval of Triple-S, subcontract for third party services or products (which include services and products from non-wholly owned Supplier Affiliates) that satisfy each of the following conditions: (i) any such third party may not be dedicated to performance of Services for Triple-S, (ii) any such subcontracted services or products are not material to the performance of the Services, and (iii) any such subcontracted services or products do not result in a material change in the way Supplier conducts its business, and (iv) any such |
|
Triple-S / Supplier Confidential Page 18 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
third party does not have access to Triple-S’s PHI or Personally Identifiable Information or Other Sensitive Confidential Information (collectively, “Non-Key Subcontractors”). “Other Sensitive Confidential Information” means any Confidential Information of Triple-S pertaining to Triple-S business strategy, marketing strategy, trade secrets, pricing. Supplier will provide Triple-S with a list of Non-Key Subcontractors on a quarterly basis. Each of the subcontracted entities described in this Section 6.6(h) shall be considered Subcontractors for the purposes of the Agreement. As of the Effective Date, there are no Non-Key Subcontractors. All of the Subcontractors approved by Triple-S in Schedule R are “key” Subcontractors.
| (i) | Notwithstanding anything to the contrary in this Agreement (including Schedule Q (Supplier Affiliates) or Schedule R (Supplier Subcontractors) and without limiting the restrictions in Section 19.19, Supplier shall not permit personnel from any Affiliate or other entity other than Supplier, Optum Services (Puerto Rico) LLC and Optum Global Services, Inc., to access the [***] Software. |
| 7. | TRIPLE-S RESPONSIBILITIES |
| 7.1 | Appointment of Triple-S Program Management Office (PMO) Personnel |
Triple-S will designate an individual to serve as Triple-S’s “Program Manager”, who will be Supplier’s principal point of contact for obtaining decisions, information, approvals and acceptances required from Triple-S.
| 7.2 | Triple-S Cooperation Duties |
| (a) | In support of Supplier’s performance of the Services and subject to Section 7.3 (Savings Clause), Triple-S will perform the Functions identified in this Agreement as retained Triple-S Functions and provide or make available to Supplier the Equipment, Software, and other resources that this Agreement expressly states are to be provided by Triple-S or that the Parties otherwise agree in a Change Order, amendment or similar document executed by the Parties after the Effective Date are to be provided or made available to Supplier by Triple-S. |
| (b) | Triple-S will cooperate with Supplier and its Subcontractors, including by making available management decisions, information, approvals and acceptances as reasonably requested by Supplier so that Supplier may accomplish its obligations and responsibilities under this Agreement. |
| (c) | Only personnel as expressly so designated by the Triple-S Program Manager (which Triple-S will communicate to Supplier from time-to-time) will be authorized to make commitments on the part of Triple-S that amend this Agreement or commit resources that are subject to a Charge. To the extent Supplier relies on the apparent authority of any other personnel it does so at its own risk and without obligation on Triple-S’s part. |
|
Triple-S / Supplier Confidential Page 19 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
| 7.3 | Savings Clause |
Triple-S’s delay or failure to perform its responsibilities set forth in this Agreement (or cause them to be performed) will not constitute grounds for termination by Supplier except as provided in Section 16.2 (Termination by Supplier). Supplier’s nonperformance of its obligations under this Agreement will be excused if and to the extent (a) such Supplier nonperformance results directly from the failure or delay by Triple-S to perform (or cause its Service Recipients, agents or third party contractors to perform) Triple-S’s obligations under this Agreement or from Triple-S or its Service Recipients, agents or third party contractors, and (b) Supplier provides Triple-S with reasonable notice of such nonperformance, including details of the impact that the nonperformance has on Supplier’s ability to perform, and uses Commercially Reasonable Efforts to perform notwithstanding the failure to perform. If Supplier’s use of Commercially Reasonable Efforts to perform in such a circumstance would cause Supplier to incur material additional cost and expense, Supplier may so notify Triple-S. If it does, Supplier’s obligation to continue its efforts to work around the failure to perform will be subject to Triple-S agreeing to reimburse Supplier for such material costs and expenses incurred in the course of such efforts.
| 8. | CHARGES |
Schedule C (Charging Methodology) sets forth all of the Charges payable to Supplier for performing the Services and the associated invoicing and payment procedures and terms.
| 9. | USE OF TRIPLE-S RESOURCES |
| 9.1 | Use Rights |
This Section 9 sets forth the terms under which certain resources used by Triple-S prior to the Effective Date will be made available to Supplier for use in providing the Services. RIGHTS OF USE GRANTED BY Triple-S TO SUPPLIER UNDER THIS SECTION 9 ARE GRANTED ON AN “AS IS, WHERE IS” BASIS, WITHOUT WARRANTIES OF ANY KIND, except as otherwise expressly provided in this Agreement. For clarity, the rights granted to Supplier in this Section 9 include use of the resource by Supplier’s Approved Subcontractors.
| 9.2 | Triple-S Equipment |
| (a) | The Triple-S Equipment that Triple-S is obligated to make available to Supplier to provide the Services is listed in Schedule C-3 (Financial Responsibility Matrix). All Triple-S Equipment made available to Supplier shall be subject to the terms of this Section 9.2. |
| (b) | Triple-S grants to Supplier, without sale or assignment, the right to use such Triple-S Equipment that Triple-S is obligated to make available under C-3 (Financial Responsibility Matrix). Such Equipment shall be used solely as necessary to perform the Services. |
| (c) | With respect to any such Equipment that is Triple-S Leased Equipment (i) the foregoing right to use is subject to Triple-S obtaining any Required Consents pursuant to Section 9.7 (Required Consents); and (ii) Supplier will comply with the terms and conditions imposed on Triple-S by the leases for such Equipment that have been provided to Supplier in writing. |
|
Triple-S / Supplier Confidential Page 20 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
| 9.3 | Triple-S Third Party Service Contracts |
| (a) | The Triple-S Third Party Service Contracts, if any, that Triple-S is obligated to make available to Supplier to provide the Services are listed in Schedule X (Source of Truth). All Triple-S Third Party Service Contracts made available to Supplier shall be subject to the terms of this Section 9.3. |
| (b) | Triple-S grants to Supplier, without assignment of such contracts, but subject to Triple-S obtaining any Required Consents pursuant to Section 9.7 (Required Consents), the right to use the services provided to Triple-S under such Triple-S Third Party Service Contracts, if any, until such time as determined pursuant to Section 9.3(d), solely as necessary to perform the Services. Supplier will comply with the terms and conditions imposed on Triple-S by such Triple-S Third Party Services Contracts that are disclosed to Supplier in writing. |
| (c) | For clarity, contracts for maintenance, support, repair and similar services relating to Equipment and Software shall be treated the same as the associated Equipment or Software and therefore governed by Sections 9.2 (Triple-S Equipment) and 9.4 (Triple-S Software and Triple-S Tools) (as applicable), and not as Triple-S Third Party Service Contracts under this Section 9.3. |
| (d) | When any such Triple-S Third Party Service Contract is no longer required for performance of the Services, and in any event upon the earlier of (i) the cessation or termination of the applicable Services, (ii) the expiration of the Term and Disengagement Assistance Period, or (iii) the end of the applicable contract term (as such term may be described in Schedule X (Source of Truth)), Supplier will cease use of such Triple-S Third Party Service Contract. |
| 9.4 | Triple-S Software and Triple-S Tools |
| (a) | The Triple-S Software and Triple-S Tools, if any, that Triple-S is obligated to make available to Supplier to provide the Services are listed in Schedule X (Source of Truth). All Triple-S Software and Triple-S Tools made available to Supplier shall be subject to the terms of this Section 9.4. |
| (b) | Triple-S (and each of its Affiliates) or the applicable licensor retains all of its right, title and interest in and to the Triple-S Software and Triple-S Tools. |
| (c) | Subject to Triple-S having obtained any Required Consents pursuant to Section 9.7 (Required Consents), as of the Effective Date, Triple-S grants to Supplier, without assignment of the license, the right during the Term and any Disengagement Assistance Period (or the applicable license term or as set forth in Section 9.4(e) below, if shorter as Triple S has (or later obtains)) to use such Triple-S Licensed Software and Triple-S Licensed Tools, if any, solely as necessary to perform the Services. Supplier will not seek to modify or otherwise revoke such terms. Supplier will comply with the terms and conditions imposed on Triple-S by the license for such Software and Tools that have been disclosed to Supplier in writing. |
|
Triple-S / Supplier Confidential Page 21 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
| (d) | Supplier is not permitted to use such Triple-S Software and Triple-S Tools for the benefit of any entity other than Triple-S (and other Service Recipients under this Agreement) without the prior written consent of Triple-S, which may be withheld in Triple-S’s discretion. |
| (e) | When Triple-S Software or Triple-S Tools are no longer required for performance of the Services, or in any event upon the earlier of (i) the cessation or termination of the applicable Services, (ii) the expiration of the Term and the Disengagement Assistance Period or (iii) with respect to Triple-S Licensed Software and Triple-S Licensed Tools, the end of the applicable license term (as such term is described in Schedule X(Source of Truth), Supplier will cease use of and return such Triple-S Software and Triple-S Tools to Triple-S in an agreed format or, at Triple-S’s election, destroy them and certify the destruction of all copies in Supplier’s (and any of its Subcontractor’s) possession or control. |
| 9.5 | Triple-S Facilities |
| (a) | Subject to Triple-S having obtained any Required Consents pursuant to Section 9.7, Triple-S grants to Supplier the right, to access the Triple-S Facilities, to the extent permitted by applicable lease agreements, solely to perform the Services. Such space to be made available is described on Schedule C-3 (Financial Responsibility Matrix). |
| (b) | Such facilities shall be provided from the Services Commencement Date until the time period identified in Schedule C-3 (Financial Responsibility Matrix). |
| (c) | Supplier will comply with the duties imposed on Triple-S (or its Affiliate) by each lease for the Triple-S Facilities that are disclosed to Supplier in writing. |
| 9.6 | Terms Applicable to Triple-S Facilities |
| (a) | Except as provided in Section 9.5 above, Supplier is responsible for providing the facilities and facilities-related support it needs to provide the Services. |
| (b) | Supplier’s use of the Triple-S Facilities shall be for the sole and exclusive purpose of providing the Services and shall be subject to the terms set forth in this Section 9.6. Supplier is not permitted to use Triple-S Facilities for the benefit of any entity other than Triple-S (and other Service Recipients under this Agreement) without the prior written consent of Triple-S, which may be withheld in Triple-S’s discretion. |
| (c) | Supplier will use the Triple-S Facilities in an efficient manner and in a manner that does not interfere with Triple-S’s business operations. |
| (d) | Supplier will keep the Triple-S Facilities in good order, not commit or permit waste or damage to them or use them for any unlawful purpose or act. Supplier will comply with the Triple-S Policies and Procedures and with applicable lease terms made available to Supplier in writing, each of the foregoing regarding access to and use of the Triple-S Facilities, including procedures for the physical security of the Triple-S Facilities. Supplier is responsible for any damage to Triple-S Facilities resulting from the acts or |
|
Triple-S / Supplier Confidential Page 22 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
omissions of Supplier during its use of the Triple-S Facilities.
| (e) | Supplier will permit Triple-S and its agents and representatives to enter any portions of the Triple-S Facilities occupied by Supplier Personnel at any time. |
| (f) | Supplier may not make improvements or changes involving structural, mechanical or electrical alterations to the Triple-S Facilities without Triple-S’s prior written approval. Any improvements to the Triple-S Facilities will become the property of Triple-S. |
| (g) | Upon the earlier to occur of (i) the expiration of the time period for which Triple-S agreed to permit Supplier to use the Triple-S Facilities as described in Section 9.5(b), or (ii) when Triple-S Facilities are no longer required for performance of the Services, or (iii) upon expiration or termination of this Agreement (or the applicable lease term (as such term is described in Schedule C-3 (Financial Responsibility Matrix), if shorter), Supplier will return them to Triple-S in substantially the same condition as when Supplier began use of them, subject to reasonable wear and tear. |
| 9.7 | Required Consents |
| (a) | Triple-S, with the reasonable cooperation of Supplier, is responsible for obtaining Required Consents under any of the leases, contracts or licenses referred to in this Section 9 (Use of Triple-S Resources) which Triple-S is making available to Supplier for use in providing the Services (including use by Subcontractors). Triple-S will work diligently to obtain such Required Consents as soon as practicable after the Effective Date. Triple-S will bear the fees and cost (such as transfer or upgrade fees) required to obtain such Required Consents. Unless and until any Required Consent has been obtained, Supplier will, pursuant to the Change Control Process, determine and adopt, subject to Triple-S’s prior approval, such alternative approaches as are necessary and sufficient for Supplier to provide the Services without the Required Consent. |
| (b) | If Triple-S is not able to obtain any such Required Consent, or if Triple-S elects not to obtain a Required Consent because of the cost or other terms required to obtain such Required Consent, the Parties will use Commercially Reasonable Efforts to identify alternative resources through the Change Control Process. |
| (c) | Supplier shall be responsible for obtaining any Required Consents for leases, contracts or licenses relating to Software, Equipment and Third Party Service Contracts that Supplier makes available to Triple-S (which, for clarity, include the TSS Transferred Contracts but do not include Managed Third Parties) during the Term and the Disengagement Assistance Period and thereafter, and will pay any fees required to obtain such Required Consents. Triple-S shall provide reasonable cooperation to Supplier in obtaining Required Consents with respect to TSS Transferred Contracts. |
| 10. | RESPONSIBILITY FOR RESOURCES DURING THE TERM |
This Section 10 describes each Party’s responsibility for providing and operating certain resources required under this Agreement. Supplier shall be compensated for the resources it
|
Triple-S / Supplier Confidential Page 23 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
provides through the Charges provided in Schedule C (Charging Methodology), as they may be adjusted in accordance with the terms of Schedule C (Charging Methodology).
| 10.1 | General Responsibility and Compatibility |
| (a) | Except for (i) any resources which Triple-S has expressly agreed to provide as set forth in Schedule X (Source of Truth), and (ii) items which are shown as Triple-S Retained Expense in the Financial Responsibility Matrix attached as Schedule C-3 (Financial Responsibility Matrix), Supplier is solely responsible (and has Financial Responsibility) for providing, and shall have operational responsibility for, all Equipment, Software, Tools, Third Party Service Contracts, facilities, personnel, third party services and other resources as required for Supplier to properly perform its obligations under and in accordance with this Agreement, including modifications, upgrades, enhancements, additions and replacements of such resources. Supplier’s Financial Responsibility shall include such responsibility as set forth on Schedule C-3 (Financial Responsibility Matrix). |
| (b) | Supplier will conform to and support Triple-S’s architecture, standards, and strategic direction in rendering the Services as set forth in Triple-S Policies and Procedures. Any Equipment and Software provided by or on behalf of Supplier that connects to Triple-S’s IT infrastructure will comply with such architecture, standards, and strategic direction, and any deviation from such will be subject to the prior written approval of Triple-S. Supplier will notify Triple-S if Triple-S’s architecture, standards or strategic direction conflicts or is inconsistent with Supplier’s internal standards that would otherwise enable achievement of efficiencies in providing the Services. |
| 10.2 | Equipment |
Except for items which are shown as Triple-S Retained Expense in the Financial Responsibility Matrix attached as Schedule C-3 (Financial Responsibility Matrix), Supplier is responsible for acquiring, at its expense, the Equipment (including modifications, upgrades, enhancements, additions and replacements of Equipment) as required for Supplier to properly perform its obligations under and in accordance with this Agreement. With respect to such Equipment:
| (a) | Supplier will acquire the Equipment in the name of Supplier; and |
| (b) | Supplier will use Commercially Reasonable Efforts to acquire the right to assign to Triple-S and a Successor Supplier the leases for Equipment exclusively used to provide Services to Triple-S and which were entered into specifically for performance of the Services (“Supplier Leased Equipment”) and applicable maintenance contracts for such Supplier Leased Equipment if Supplier ceases to provide the Services. If Supplier is unable to obtain such right to assign, Supplier shall explore alternatives, and provide information to Triple-S regarding any ramifications to the Services that may arise out of using alternative Equipment. |
| 10.3 | Third Party Services |
Except for (i) third party services which Triple-S has agreed to provide as listed in Schedule X
|
Triple-S / Supplier Confidential Page 24 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
(Source of Truth), and (ii) items which are shown as Triple-S Retained Expense in the Financial Responsibility Matrix attached as Schedule C-3 (Financial Responsibility Matrix), Supplier is responsible for acquiring, at its expense, any third party services as required for Supplier to properly perform its obligations under and in accordance with this Agreement. With respect to such third party services:
| (a) | Supplier will contract for such third party services in its own name; |
| (b) | Supplier will use Commercially Reasonable Efforts to acquire the right to assign to Triple-S and a Successor Supplier any Third Party Service Contract for which Supplier has Financial Responsibility and that is exclusively used to provide Services to Triple-S and which were entered into specifically for performance of the Services (collectively, “Supplier Third Party Service Contracts”) if Supplier ceases to provide the Services. If Supplier is unable to obtain such right to assign, Supplier shall explore alternatives under which other Third Party Service Contracts may be assignable to Triple-S as described above, and provide information to Triple-S regarding any ramifications to the Services that may arise out of using such alternative assignable Third Party Service Contracts; and |
| (c) | Supplier will not procure any such Supplier Third Party Service Contracts for which Supplier would not have the right to assign as described above, without Triple-S’s prior written consent. |
| 10.4 | Supplier Software and Tools |
| (a) | Except for (i) Software and Tools which Triple-S has agreed to provide as listed in Schedule X (Source of Truth), and (ii) items which are shown as Triple-S Retained Expense in the Financial Responsibility Matrix attached as Schedule C-3 (Financial Responsibility Matrix), Supplier is responsible for acquiring, at its expense, the Software and Tools (including modifications, upgrades, enhancements, additions and replacements of Software and Tools) as required for Supplier to properly perform its obligations under and in accordance with this Agreement. With respect to such Software and Tools: |
| (i) | Supplier will acquire such Software and Tools in its own name. |
| (ii) | Supplier shall not, without Triple-S’s prior written consent (including as set forth on Schedule S (Supplier Software and Supplier Tools)), use any Non Commercially Available Supplier Software or Supplier Tools (collectively, “Non Commercially Available Items”) to provide the Services. |
| (iii) | If Supplier uses such a Non Commercially Available Item which requires the consent of Triple-S pursuant to Section 10.4(a)(ii) and Supplier fails to obtain Triple-S’s prior written agreement that Triple-S waives its right to receive a license to such Non Commercially Available Item as hereinafter described, then upon the expiration or termination of this Agreement, any Statement of Work or Task Order (or part thereof), or Services with respect to which such Non Commercially Available Item was used: (i) in the case of Supplier Owned Software or Supplier Owned Tools, Supplier grants to Triple-S and Triple-S Affiliates (and their respective designees and contractors provided that such third |
|
Triple-S / Supplier Confidential Page 25 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
party is subject to a confidentiality agreement with Triple-S with terms substantially similar to Section 21 (Confidentiality) of these General Terms and Conditions and Triple-S is responsible for such third party’s compliance with this Agreement), and (ii) in the case of Supplier Licensed Software or Supplier Licensed Tools, Supplier shall procure for Triple-S and Triple-S Affiliates (and their designees and contractors provided that such third party is subject to a confidentiality agreement with Triple-S with terms substantially similar to Section 21 (Confidentiality) of these General Terms and Conditions and Triple-S is responsible for such third party’s compliance with this Agreement), in each case, for no additional consideration, a perpetual, worldwide, fully paid up, royalty-free, non-exclusive license to Use such Supplier Software or Supplier Tool, as applicable (including Source Code, programmer interfaces, available documentation, manuals, and other materials necessary for the Use thereof), for the sole purpose of providing services to Triple-S and the Service Recipients.
| (iv) | Upon Triple-S’s request, Supplier shall also provide to or procure for Triple-S a commercially reasonable maintenance and support agreement for such Non Commercially Available Item, the charges for which will be Triple-S’s responsibility with respect to the period after the Disengagement Assistance Period. |
| (b) | Without limiting the foregoing, Schedule S (Supplier Software and Supplier Tools) sets forth a list of the Supplier Software and Supplier Tools to be used by Supplier to provide the Services as of the Effective Date. The Parties agree that for the Supplier Software and Supplier Tools set forth in Schedule S (Supplier Software and Supplier Tools) that are designated as “Non Commercially Available,” Triple-S: (i) consents to the use of such Software and Tools by Supplier to provide the Services for the purposes described in Schedule S (Supplier Software and Supplier Tools) (as such consent is contemplated by Section 10.4(a)(ii) above), and (ii) waives its right to receive a license to such Software or Tool as contemplated by Section 10.4(a)(iii) above. |
| (c) | On an annual basis, Supplier shall provide updates to Schedule S (Supplier Software and Supplier Tools) reflecting any additional Supplier Software and Supplier Tools used by Supplier to provide the Services that is not shown on the then-existing Schedule S (Supplier Software and Supplier Tools). (Such Software shall not include any Triple-S Owned Software or Triple-S Licensed Software provided by Triple-S for Supplier’s use under this Agreement.) The updates to such Schedules required under this Section 10.4(c) will separately identify: |
| (i) | Supplier Software that is Commercially Available, |
| (ii) | Supplier Software that is Non-Commercially Available, |
| (iii) | Third Party Software that is Commercially Available, and |
| (iv) | Third Party Software that is Non-Commercially Available. |
|
Triple-S / Supplier Confidential Page 26 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
| 10.5 | License During the Term and Disengagement Assistance Periods |
| (a) | Supplier hereby grants to Triple-S and the Service Recipients (and their respective service providers and contractors provided that Triple-S and such third party are subject to a confidentiality agreement with terms substantially similar to Section 21 (Confidentiality) of these General Terms and Conditions) during the Term and any Disengagement Assistance Period, the right to use Software made available by Supplier to Triple-S and Triple-S Affiliates during the Term (including any updates and upgrades to such Software provided by Supplier), solely for Triple-S (and its Affiliates and Service Recipients) to receive or use the Services. For clarity, this license does not apply to Software used by Supplier in performance of the Services that is not listed in Schedule S (Supplier Software and Tools) and not otherwise made available during the Term for access or use by Triple-S. |
| (b) | Supplier hereby grants to Triple-S, its Affiliates and the Service Recipients (and their respective service providers and contractors provided that such third party is subject to a confidentiality agreement with Triple-S with terms substantially similar to Section 21 (Confidentiality) of these General Terms and Conditions and Triple-S is responsible for such third party’s compliance with this Agreement) during the Term and any Disengagement Assistance Period, the right to access and Use the systems used by Supplier to provide the Services or the systems supported by Supplier as part of the Services (and Triple-S Data stored or processed in such systems) solely for Triple-S, its Affiliates and the Service Recipients (and their respective service providers and contractors provided that such third party is subject to a confidentiality agreement with Triple-S with terms substantially similar to Section 21 (Confidentiality) of these General Terms and Conditions and Triple-S is responsible for such third party’s compliance with this Agreement) to perform their designated roles for Triple-S and its Affiliates as reasonably required to receive and use the Services or otherwise reasonably required to carry on Triple-S’s and its Affiliates business operations and retained responsibilities. By way of example and not limitation, Triple-S’s rights include the right to access (or permit a service provider or contractor to access provided that such third party is subject to a confidentiality agreement with Triple-S with terms substantially similar to Section 21 (Confidentiality) of these General Terms and Conditions and Triple-S is responsible for such third party’s compliance with this Agreement) the systems used by Supplier to provide the Services in order to access Triple-S Data, process claims that are not in the scope of the Services, generate queries, run reports and perform retained Functions. |
| 10.6 | Network Connectivity |
Financially Responsible for providing network connectivity between facilities necessary to provide the Services is allocated in Schedule C-3 (Financial Responsibility Matrix).
| 10.7 | Triple-S Personnel |
The In-Scope Employee Agreement (a form of which is attached as Schedule G) provides obligations of the Parties relating to certain In-Scope Employees (as defined in Schedule G). Supplier remains responsible for all Functions delegated to the In-Scope Employees to the same extent as if such Functions were to be or were performed by Supplier Employees, and for purposes of this Agreement, such Functions will be deemed Functions performed by Supplier. Supplier shall be responsible for all acts and omissions of the In-Scope Employees except to the
|
Triple-S / Supplier Confidential Page 27 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
extent expressly provided otherwise in Schedule G. For purposes of clarity: (a) Supplier’s failure to meet a Service Level or comply with any other obligation under this Agreement shall not be excused under Section 2.5 of Schedule B (Service Level Methodology) or otherwise under this Agreement as a result of an In-Scope Employee’s acts or omissions; and (b) Supplier shall be liable for Security Breaches, indemnification obligations, and other claims Triple-S may have under this Agreement as a result of an In-Scope Employee’s acts or omissions to the same extent Supplier would be liable for them had the acts or omissions been by a Supplier Employee.
| 10.8 | Flow Down Terms |
Triple-S shall comply with the terms and conditions provided in Schedule Y (Subcontractor Flow-Down Terms) regarding Triple-S’s use of Equipment, Third Party Services, Software and Tools provided or made available by Supplier.
| 11. | TRANSITION |
| 11.1 | Transition Overview |
| (a) | This Section 11 (Transition) addresses at a high level the transition of the Functions comprising the Services from Triple-S to Supplier. Each of the Initial SOWs contains an exhibit describing the Transition approach and plans for that Initial SOW. |
| (b) | The Transition approaches, plans and schedules set forth in the Initial SOWs reflect the Parties’ preliminary understanding as to how the Transition will be conducted and will serve as preliminary Transition Documents. Promptly following the execution of this Agreement, Supplier will work diligently with Triple-S’s team leads for each SOW to develop and submit final Transition Documents for Triple-S’s review and approval, and such plans will contain the necessary level of operational detail, as set forth in Section 11.3. |
| 11.2 | Transition Defined and Start of Transition |
| (a) | “Transition” means the process (and associated time period) of migrating performance of the Services from Triple-S or from Triple-S’s then-current service providers to Supplier, completing any contemplated movement of services from onshore locations to alternate onshore locations, near shore locations and offshore locations (each as contemplated by the applicable Transition Documents), making any planned improvements to the process and methods and infrastructure used to perform and deliver the Services that are intended to be made during the period of Transition, and causing any required knowledge transfer from Triple-S personnel to Supplier Personnel. |
| (b) | The Transitions for each of the Initial SOWs (each, an “Initial SOW Transition”) shall commence on the Effective Date or such date set forth in the Statement of Work, if later, and continue through the date that Supplier has assumed all responsibility with respect to the Services covered by the Initial SOWs and completed the transition to the contemplated service delivery model. |
|
Triple-S / Supplier Confidential Page 28 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
| (c) | The Transition for each Future SOW (each, a “Future SOW Transition”) shall commence on the applicable SOW Effective Date or such date set forth in the Statement of Work, if later, and continue through the date that Supplier has assumed all responsibility with respect to the Services covered by such Future SOW and completed the transition to the contemplated service delivery model (if any). |
| 11.3 | Transition Documents |
| (a) | Each Transition shall be conducted in accordance with a written plan and documents (the “Transition Documents”) which shall include: (i) a description of the operations being transitioned; (ii) a general description of the methods and procedures, personnel and organization Supplier will use to perform the Transition; (iii) a schedule of the Transition activities; (iv) a detailed description of the respective roles and responsibilities of Triple-S and Supplier; (v) Transition Milestones, Transition Deliverables and Acceptance Criteria, as described in Section 11.4(b) below, and (vi) such other information and planning as are necessary to conduct the Transition in accordance with the other terms in this Agreement. |
| (b) | A draft of the Transition Documents for the Initial SOWs Transition is attached in each Initial SOW. |
| (c) | A draft of the Transition Documents for any Future SOW Transition shall be included as part of the applicable Future SOWs. |
| (d) | Supplier shall be responsible for revising and finalizing the applicable Transition Documents, provided that: (i) Supplier shall cooperate and work closely with Triple-S in finalizing such Transition Documents (including incorporating Triple-S’s reasonable comments); and (ii) any change to a Transition Document after the Effective Date shall be subject to the prior written approval of Triple-S. |
| (e) | Supplier shall perform the Services necessary to complete the Transition of the initial Services in accordance with the terms set forth in this Agreement, including the Transition Documents (collectively, the “Transition Services”). |
| (f) | Supplier shall be responsible for revising and finalizing the Transition Documents. |
| 11.4 | Transition Deliverables and Transition Milestones |
| (a) | Supplier will carry out and complete each Transition in accordance with the applicable Transition Documents, including any time schedule and deadlines set forth in such documents. Supplier shall complete the Transition by the Transition Completion Date set forth in the Transition Documents. |
| (b) | The Transition Documents will include, as critical components, clear definitions of the waves, stages, and discrete work streams that will comprise the Transition for each Initial SOW and a delineation of the Transition Deliverables (“Transition Deliverables”) and Transition milestones (“Transition Milestones”), and their respective Acceptance Criteria. The Transition Deliverables and Transition Milestones will be used to |
|
Triple-S / Supplier Confidential Page 29 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
determine, at logical stages of each Transition, whether progress has been sufficient to warrant proceeding to the next stage, whether there are any corrective actions that should be taken before proceeding with dependent work, the next stage or related Transition activities, and whether there are any lessons learned from performance of Transition waves that should be documented and communicated to the Transition teams working on other waves in order to minimize the recurrence of problems during Transition.
| (c) | The Transition Deliverables and Transition Milestones for the initial Transitions are set forth in each SOW. |
| (d) | Schedule N-1 (Deliverable and Milestone Acceptance Procedures) details the process by which Triple-S will determine whether the Acceptance Criteria for each Transition Deliverable and Transition Milestone have been met.A Transition Deliverable or Transition Milestone will be deemed to be Accepted at such time as Triple-S agrees that all Acceptance Criteria have been satisfied and completed to Triple-S’s satisfaction and Triple-S issues a written notice to Supplier that the Transition Deliverable or Transition Milestone is complete. |
| 11.5 | Conduct of the Transition |
Except as otherwise expressly provided in this Agreement or the Transition Documents, Supplier’s responsibilities with respect to the Transition include:
| (a) | performing and managing the Transition and activities; |
| (b) | performing the Transition activities without material interruption to any services, and without materially disrupting Triple-S’s business operations; and |
| (c) | otherwise performing such migration tasks as are necessary to enable Supplier to complete the Transition and provide the Services. |
| 11.6 | Triple-S Cooperation and Support |
Triple-S will cooperate with Supplier, and Triple-S shall use Commercially Reasonable Efforts to cause its suppliers (including Managed Third Parties as provided in Section 2.4(e) of Schedule A (Cross Functional Services)) to cooperate with Supplier, in the conduct of the Transition and provide support as described in the Transition Documents or as reasonably required for Supplier to complete the Transition.
| 11.7 | Completion of Transition |
| (a) | Triple-S reserves the right to monitor, test and otherwise observe and participate in the Transition. Supplier will notify Triple-S without delay if any Triple-S monitoring, testing or participation has caused (or Supplier expects it to cause) a problem or delay in the Transition and work with Triple-S to prevent or circumvent the problem or delay. Supplier will not be responsible for any problems or delays caused by any Triple-S monitoring, testing or participation in the Transition (provided Supplier notifies Triple-S that such monitoring, testing or participation may or does cause problems or delays). |
|
Triple-S / Supplier Confidential Page 30 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
| (b) | Triple-S may elect at its reasonable discretion to suspend or delay a Transition activity at any time, including in the event such Transition activity is not proceeding in accordance with the requirements of the approved Transition Project Plan and other Transition Documents or is causing unplanned disruptions or other adverse effects to Triple-S (or its Affiliates). During any suspension or delay period, Supplier, as practicable, will continue to perform the Services as required under this Agreement in the manner the Services were performed prior to the commencement of the applicable Transition activity. Suspension or delay of a Transition activity, where arising out of Supplier’s failure to perform the Transition in accordance with the requirements of the approved Transition Documents or this Agreement, will, except as set forth in Section 11.7(a), be at no additional charge to Triple-S and will continue until Supplier demonstrates, to Triple-S’s reasonable satisfaction, that Supplier is ready to comply with such requirements and/or end any disruptions or adverse effects. Supplier will be responsible, at its own expense, for achieving the Transition schedule notwithstanding the suspension or delay; provided, however, that if Triple-S suspends or delays a Transition activity due to no fault of Supplier, and if the suspension or delay would cause Supplier to incur reasonable additional expenses, the deadlines for Transition will be equitably extended to account for Triple-S’s suspension or delay and Supplier may so notify Triple-S, providing a good faith estimate of such expenses Supplier expects to incur. In such case, Triple-S’s right to continue the suspension or delay will be subject to Triple-S agreeing to reimburse Supplier for such reasonable additional expenses incurred as a result of the suspension or delay. |
| 11.8 | In Flight Projects |
As part of the Transition, Supplier will also assume responsibility for completing the projects listed or described in Schedule P (In-Flight Projects) (to the extent Supplier is assigned responsibility on Schedule P (In-Flight Projects)), which are in progress or planned as of the Effective Date and being performed by resources of Triple-S or a prior service provider which are being replaced by Supplier (the “In-Flight Projects”). After the Effective Date, the Parties will work in good faith to update Schedule P (In-Flight Projects) to describe the Deliverables that are Supplier’s responsibility and the resource requirements for each In-Flight Project.
12. TRANSFORMATION AND CRITICAL MILESTONES
| 12.1 | Transformation |
| (a) | “Transformation” means those activities primarily being performed following completion of the Transitions (although certain Transformation activities will be performed prior to the completion of the Transitions) to be performed by Supplier that are set forth in SOW #2, Exhibit C (IT Solution) that are designed to transform the environments used to deliver Services to Triple-S in accordance with Triple-S requirements, including by further improving the quality, responsiveness, flexibility, efficiency and productivity of Service delivery, by undertaking those activities. |
| (b) | Supplier will carry out and complete Transformation described in and in accordance with SOW #2, Exhibit C (IT Solution) and its associated Schedules, including any time schedules, project plans, deadlines, and other documents set forth in such Schedule |
|
Triple-S / Supplier Confidential Page 31 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
(collectively, “Transformation Documents”). Supplier shall complete Transformation by the dates set forth in the Transformation Documents.
| 12.2 | Critical Milestones |
| (a) | With respect to Transition and Transformation, the Parties shall agree upon a set of Critical Milestones (each, a “Critical Milestone”). Supplier shall complete each Critical Milestone by the applicable date the Parties agree on for completion of such Critical Milestones (each such date, a “Critical Milestone Completion Date”). The Critical Milestones and Critical Milestone Completion Dates are set forth in SOW #1, Exhibit A-3-3 (Critical Milestones) and SOW #2, Exhibit A-3-3 (Critical Transition and Transformation Milestones & Acceptance Criteria). |
| (b) | A Critical Milestone will be deemed to be complete at such time as Triple-S agrees that all Acceptance Criteria have been satisfied and completed to Triple-S’s satisfaction and Triple-S issues a written notice to Supplier that the Critical Milestone is complete. The acceptance procedures described in Schedule N-1 (Deliverable and Milestone Acceptance Procedures) to this Agreement will apply with respect to such milestones. If Supplier fails to complete any Critical Milestone by the applicable Critical Milestone Completion Date, such failure shall be deemed to be a “Critical Milestone Failure”. |
| (c) | If a Critical Milestone Failure occurs, then: |
| (i) | If Supplier’s charges to Triple-S are greater than they would have been if the delayed Transformation project had been completed on schedule, Triple-S will receive a credit against Supplier’s monthly charges on the subsequent invoice(s) in an amount equal to the difference between the actual charges being paid by Triple-S and what Supplier’s charges would have been if the delayed Transformation had been completed on schedule; and |
| (ii) | Supplier will grant Triple-S an additional credit against Supplier’s monthly charges on the subsequent invoice(s) in an amount sufficient to reimburse Triple-S for any documented costs incurred for facilities, personnel, third-party equipment, Software, services, and other operational costs that would not have been incurred if the delayed Transformation had been completed on schedule and in accordance with this Agreement (including costs of internal Triple-S resources and amounts payable to third parties); provided that (A) Triple-S shall use Commercially Reasonable Efforts to mitigate such costs, (B) such costs may not include lost revenue or profits from potential forecasted business benefits, and (C) such credit shall be reduced by the amount of any Critical Transformation Credits paid by Supplier for the same Critical Milestone Failure. |
| (d) | Nothing set forth in Section 12.2 shall limit Triple-S’s right to make a claim for damages relating to a Critical Milestone to the extent such damages exceed the amount of the credits paid by Supplier to Triple-S related to such Critical Milestone described in Section 12.2. |
|
Triple-S / Supplier Confidential Page 32 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
| 13. | COMPLIANCE WITH LAWS |
| 13.1 | Parties’ Compliance Obligations, Generally |
| (a) | Supplier’s Obligations. |
| (i) | Supplier agrees at its cost and expense (subject to Sections 13.1(b) and 18.4(e)(ii)(B)): (x) to comply with its obligations under Schedule W (Regulatory Requirements), and (y) obtain all necessary approvals, licenses (including licensure requirements applicable to Supplier Personnel), and permits required by Law, and to comply with all Laws, in each case as applicable to: |
| (A) | its business (or that of any of its Affiliates); |
| (B) | the performance of any of its obligations under this Agreement; |
| (C) | the Services that Supplier is obligated to provide under this Agreement, including as such obligations may evolve pursuant to this Agreement, including Services provided with respect to any jurisdiction in which Triple-S does business; or |
| (D) | its obligations under this Section 13 (Compliance with Laws). |
| (ii) | Supplier shall provide the Services in a manner that does not cause Triple-S to be non-compliant with any Law relating to the provision or receipt of the Services and to which Triple-S is subject. |
| (iii) | Supplier shall identify, track and report any failure by Supplier to comply with Laws or failure (or suspected failure) to comply with the Regulatory Compliance Adherence Services set forth Schedule A (Cross Functional Services). Such report shall be made to Triple-S in writing and directed to the Triple-S Chief Legal Officer and the Chief Information Officer within five (5) days of Supplier’s learning of same. |
| (b) | Triple-S’s Obligations. |
| (i) | Triple-S agrees at its cost and expense: (x) to comply with its obligations under Schedule W (Regulatory Requirements), and (y) obtain all necessary approvals, licenses and permits required by Law (including licensure requirements applicable to Service Recipients), and to comply with all Laws, in each case as applicable to: |
| (A) | its business (or that of any of its Affiliates); |
| (B) | the performance of any of its obligations under this Agreement; or |
| (C) | its obligations under this Section 13 (Compliance with Laws). |
|
Triple-S / Supplier Confidential Page 33 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
| (ii) | If Triple-S is charged with failing to comply with any such Laws it shall promptly notify Supplier of the charges in writing. |
| (c) | Each Party shall bear the risk of and have financial responsibility for any change in Laws or new Laws for which it is responsible pursuant to Sections 13.1(a) (for Supplier) and 13.1(b) (for Triple-S) except to the extent otherwise expressly provided in Schedule C (Charging Methodology) or Schedule K (Reports). |
| (d) | Changes in Laws and New Laws Applicable to the Services. |
| (i) | The Parties shall be jointly responsible for discovering, identifying, and tracking new Laws and changes in Laws applicable to the Services; provided, however that Triple-S’s responsibility under this Section 13.1(d)(i) shall not relieve Supplier of its obligations under Section 13.1(a) and shall not relieve Triple-S of its obligations under Section 13.1(b). Each Party shall provide written notice to the other Party of any such Law that it identifies. |
| (ii) | In the event there are new Laws or changes in Laws applicable to the Services, Supplier and Triple-S shall jointly interpret such Laws and the extent to which the Services must be changed to comply with such Laws, provided, however, that in the event of a disagreement between the Parties regarding such an interpretation, Triple-S’s interpretation shall govern. |
| (iii) | Triple-S shall be responsible for making any necessary revisions to the Triple-S Policies and Procedures necessary to comply with such new Laws and changes to Laws. Supplier shall comply with such revised Triple-S Policies and Procedures in accordance with Section 4.4 (Triple-S Policies and Procedures). |
| (iv) | Subject to Section 18.4(e)(ii), Supplier shall be solely responsible for making changes to Supplier’s operational processes and procedures required for Supplier to comply with such change in Laws or new Laws. |
| 13.2 | Other Compliance Requirements |
| (a) | Without limiting the generality of the foregoing, Supplier agrees as follows: |
| (i) | FAR Anti-Kickback Requirements. Supplier understands that with respect to any attempt to provide or offer to provide any kickback prohibited by the Anti-Kickback Law of 1986 (41 U.S.C. §§ 51-58), when Triple-S has reasonable grounds to believe that a violation has occurred, Triple-S is obliged to report such to the Federal government in writing and to cooperate fully with any Federal investigation. Supplier further understands that the Federal government may offset the amount of any kickback against any monies owed to the government, or direct Triple-S to withhold that amount from any sums owed Supplier, with notification to the government, and that the government may order that any monies withheld from Supplier be paid to the government, unless already offset. |
|
Triple-S / Supplier Confidential Page 34 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
| (ii) | Supplier Certification. If applicable, the Parties hereby incorporate the requirements of 41 C.F.R. 60-1.4 (a)(7), 41 C.F.R. 60-300.5(a), 41 C.F.R. 60-741.5(a), 48 C.F.R. 19.702, and 48 C.F.R. 19.708. |
| (iii) | Conviction of a Felony Involving Dishonesty or Breach of Trust. Supplier understands that pursuant to 18 U.S.C. §1033, Triple-S is prohibited from employing or contracting with, for any aspect of its business that involves the “business of insurance,” any individual who: (A) (i) has been convicted of a criminal felony or had a civil judgment rendered against it for offenses involving dishonesty or a breach of trust (including the following offenses: any type of fraud; any crime based on false representations; criminal impersonation; fraudulent use of credit or debit charges; violation of a fiduciary relationship; violation of federal or state antitrust statutes; offenses involving the sale or exchange of securities; embezzlement; theft; forgery; bribery; falsification or destruction of records; counterfeiting or passing counterfeit money; money laundering; extortion; perjury and subornation of perjury; knowingly issuing a bad check; theft by deception; knowingly receiving or possessing stolen property; making false statements; tax evasion; or receiving stolen property), or (ii) who has been convicted of an offense under §1033 (any such person under (i) or (ii) a “Prohibited Person”); and (B) has not obtained the prior written consent of the Commissioner of Insurance to engage in the “business of insurance.” Supplier represents that Supplier, its Affiliates and Subcontractors, and their employees, agents and representatives, were not a Prohibited Person at the time hired by Supplier, and, either (1) is not a Prohibited Person or (2) is a Prohibited Person, but has obtained the requisite consent of the Commissioner of Insurance to engage in the business of insurance. Should a Prohibited Person perform duties pursuant to this Agreement on behalf of Supplier, Supplier agrees to so notify Triple-S in writing and provide a copy of the consent of the Commissioner of Insurance within seven (7) days of execution of this Agreement. Supplier certifies that none of Supplier or its Affiliates or subcontractor(s), or its or their employees, agents or representatives, have within a three (3) year period preceding the date of this Agreement, had one or more public transactions (federal, state or local) terminated for cause or default. |
| (iv) | E-Verify. Supplier shall comply with Federal Acquisition Regulation 52.222-54, to verify the employment eligibility of Supplier employees and shall cause all Subcontractors to comply with such regulation. Supplier shall promptly execute an agreement to confirm the foregoing if requested by Triple-S. |
| (v) | Other Federal Requirements. If applicable, Executive Order 11246, 29 C.F.R. Part 471, Appendix A to Subpart A, and 41 C.F.R. Parts 60-1.4, 60-1.7, 60-4.3 are incorporated. Supplier and Subcontractors shall abide by the requirements of 41 C.F.R. 60-300.5(a) and 60-741.5(a). These regulations prohibit discrimination against qualified protected veterans and against qualified individuals on the basis of disability, and require affirmative action by covered prime contractors and subcontractors to employ and advance in employment qualified protected veterans and qualified individuals with disabilities. |
|
Triple-S / Supplier Confidential Page 35 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
| 13.3 | Import/Export Controls |
| (a) | The Parties acknowledge that certain computer hardware, software, technical data, other items (or derivatives of any of the above) exchanged pursuant to this Agreement may be subject to import/export controls under the Laws of the United States and other countries. |
| (b) | Each Party will be responsible for compliance with import/export control Laws with respect to any items it is deemed under such Laws to have imported or exported, including responsibility for preparing and filing all required documentation and obtaining all licenses, permits and authorizations required for compliance. Each Party will reasonably cooperate with the other Party in that Party’s efforts to comply with applicable import/export control Laws. |
| (c) | Neither Party will import, export or re-export any such items, any direct product of those items, or any technical data or permit the shipment of the same (i) in violation of applicable import/export control Laws; (ii) into any country or region with respect to which the United States has imposed comprehensive sanctions (as of the Effective Date, Cuba, North Korea, Iran, Sudan, Syria, and the Crimea region); or (iii) to anyone on the U.S. Treasury Department’s List of Specially Designated Nationals, List of Specially Designated Terrorists or List of Specially Designated Narcotics Traffickers, or the U.S. Commerce Department’s Denied Persons List. |
| (d) | Supplier agrees that Supplier will not utilize any Supplier Personnel who are nationals (citizens or lawful permanent residents) of the countries described in Section 13.3(c)(ii) above or who fall within the criteria set forth in 13.3(c)(iii) above, provided that for clarity, Supplier may utilize any Supplier Personnel who have subsequent dual citizenship in the United States (or another country that is not sanctioned) and one of the countries described in Section 13.3(c)(ii) or who have lawful permanent residency in the United States (or another country that is not sanctioned). |
| (e) | Supplier will include with copies of all Software provided to Supplier by Triple-S on a disc or other similar media and that Supplier will use outside of the United States documentation stating that “These commodities, technology or software were exported from the United States in accordance with Export Administration Regulations. Diversion or re-export contrary to U.S. law is prohibited”. |
| (f) | Supplier agrees that any export by Triple-S to Supplier under this Agreement shall be to Supplier or to Affiliates of Supplier that are a “U.S. subsidiary” as defined in 15 C.F.R. 772.1, such that no export license or other authorization is required to be obtained for its export. |
| 13.4 | Compliance with Data Privacy and Data Protection Laws, Regulations and Policies |
In carrying out its activities under this Agreement, each Party will observe and comply with all applicable data privacy and data protection Laws, including the relevant provisions of HIPAA and the HITECH Act. In addition, when accessing or handling any Triple-S Data that contains Personally Identifiable Information, Supplier will comply with the Triple-S Policies and Procedures and Schedule L (IT Security Addendum) relating to the use and disclosure of such information.
|
Triple-S / Supplier Confidential Page 36 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
| 13.5 | Business Associate Agreement |
The Parties hereby agree to the terms of the Business Associate Agreement attached as Schedule H (Business Associate Agreement), which is hereby incorporated by reference. In the event of any conflict among the terms of this Agreement (excluding Schedule H (Business Associate Agreement)) and the terms and conditions of Schedule H (Business Associate Agreement), the terms and conditions that are more protective of the PHI (as such term is defined in Schedule H) shall govern to the extent of that conflict.
| 14. | DATA SECURITY AND PROTECTION |
| 14.1 | Triple-S Data, Generally |
| (a) | As between the Parties, Triple-S Data will be and remain the property of Triple-S. Supplier may not use Triple-S Data for any purpose other than to render the Services. No Triple-S Data will be sold, assigned, leased or otherwise disposed of to third parties or commercially exploited by or on behalf of Supplier (or any of its Subcontractors). Neither Supplier nor any of its Subcontractors may possess or assert any lien or other right against or to Triple-S Data. Without limiting the generality of the foregoing, (i) Supplier may only use Triple-S Data as strictly necessary to render the Services and must restrict access to such information to Supplier Personnel on a strict need-to-know basis, and (ii) Supplier shall not download, copy, transmit or make available any Triple-S Data to any third party, except as expressly permitted by this Agreement, including (A) to Supplier Affiliates identified on Schedule Q (Supplier Affiliates) or Approved Subcontractors, and then only as strictly necessary for such entities to render the Services and subject to restrictions that such Triple-S Data be made available to their employees on a strict need-to-know basis and subject to the other requirements of this Agreement regarding Triple-S Data, (B) as expressly permitted by this Agreement, or (C) as required by Law. |
| (b) | At Triple-S’s request at any time during the Term and any Disengagement Assistance Period, Suppler shall provide Triple-S with access to and/or copies of (in format reasonably requested by Triple-S and in a reasonable period of time given the circumstances of the request) any Triple-S Data stored on Supplier systems or otherwise under the control of Supplier. |
| 14.2 | Data Security |
| (a) | Supplier shall establish an information security program with respect to Triple-S Data which is designed to: (i) ensure the security and confidentiality of such Triple-S Data; (ii) protect against any anticipated threats or hazards to the security or integrity of such Triple-S Data, and (iii) protect against any unauthorized use of or access to such Triple-S Data. Supplier shall also establish and maintain network and internet security procedures, protocols, security gateways and firewalls with respect to such Triple-S Data. All of the foregoing shall be consistent with the Triple-S Policies and Procedures and |
|
Triple-S / Supplier Confidential Page 37 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
shall be no less rigorous than those maintained by Supplier for its own data and information of a similar nature.
| (b) | When present at Triple-S Facilities or accessing Triple-S Data or Triple-S systems, Supplier will observe and comply with Triple-S’s security procedures that have been communicated to Supplier in writing (which also may be made available to Supplier through other methods mutually agreed by the Parties), and Supplier shall not, without Triple-S’s prior written consent, use any other security procedure that results (or may result) in (i) an adverse operational or other impact on Triple-S’s Facilities, systems or environment, or (ii) additional cost to Triple-S. |
| (c) | Supplier shall comply with the security requirements and standards set forth in Schedule L (IT Security Addendum) as they relate to a vendor performing services for Triple-S, which represent the minimum security requirements and standards with which Supplier must comply. Supplier shall also comply with: |
| (i) | All applicable Laws relating to privacy and information security, as they may evolve during the Term and Disengagement Assistance Period, , the HITRUST Common Security Framework, and as may be required for Triple-S to qualify for the safe harbor exemption for de-identified health information under the HIPAA Privacy Rule (45 C.F.R. 164.502(d)); and |
| (ii) | the Payment Card Industry Data Security Standards (promulgated by the PCI Data Security Standards Council) (“PCI DSS”). |
| (d) | Supplier shall meet with Triple-S not less frequently than once every twelve (12) months to review the continually evolving security threat environment and potential changes to the applicable security standards to address the same. |
| (e) | No Triple-S Data may be stored outside the United States. |
| (f) | Except as permitted in a Statement of Work or Task Order, no Triple-S Data may be accessed from outside the United States without Triple-S’s prior written consent, which may be granted or withheld in Triple-S’s reasonable discretion, except that Supplier may access Triple-S Data from Supplier Facilities shown on Schedule E (Supplier Facilities) that are denoted as Facilities from which Supplier may access Triple-S Data. |
| (g) | Supplier will guard against the unauthorized access, alteration or destruction of Software and Triple-S Data. Such measures will include the installation of Software that: (i) requires all users to enter a user identification and password prior to gaining access to the information systems; (ii) controls and tracks the addition and deletion of users; (iii) controls and tracks user access to areas and features of the information systems; and (iv) encrypts Triple-S Data and Confidential Information that is stored on or sent from Supplier Personnel personal computers. |
| (h) | Triple-S will be provided with backup copies of Triple-S Data from the Supplier upon written request. Supplier must store and transmit backup Triple-S Data in accordance |
|
Triple-S / Supplier Confidential Page 38 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
with Schedule L (IT Security Addendum). Supplier will document such safeguards in the Procedures Manual.
| (i) | Without limiting the generality of the foregoing: |
| (i) | Supplier’s information security policies shall provide for (A) regular assessment and re-assessment of the risks and vulnerabilities to the confidentiality, integrity, and availability of Triple-S Data, including electronic data, and systems acquired or maintained by Supplier and its agents and contractors, including (1) identification of internal and external threats that could result in a Security Breach, (2) assessment of the likelihood and potential damage of such threats, taking into account the sensitivity of such data and systems, and (3) assessment of the sufficiency of policies, procedures, and information systems of Supplier and its agents and subcontractors, and other arrangements in place, to control risks; (B) protection against such risks; and (C) establishment and monitoring of key risk indicators (▇▇▇▇). Supplier shall provide such policies, and, upon thirty (30) days’ advance written request and no greater than twice per twelve (12) month period, and additionally as necessary in connection with a regulatory inquiry, conduct and report on the results of such assessments to Triple-S. |
| (ii) | Supplier shall (A) require all users to enter a user identification and password prior to gaining access to the information systems; (B) control and track the addition and deletion of users; (C) control and track user access to areas and features of Supplier’s information systems, and (D) encrypt Triple-S Data in accordance with Schedule L (IT Security Addendum). |
| (iii) | Supplier Personnel will not attempt to access, or allow access to, any Triple-S Data that they are not permitted to access under this Agreement. |
| (iv) | Except as provided in Section 21 (Confidentiality), Supplier shall (A) remove all Triple-S Data from any media within the scope of the Services that is taken out of service; (B) destroy or securely erase such media in accordance with Triple-S Policies and otherwise in a manner designed to protect against Security Breaches; and (C) provide to Triple-S, within ten (10) Business Days after a receipt of a request from Triple-S, a notification of destruction, which may be provided via an automated solution that creates an auditable record. |
| 14.3 | Security Breach |
| (a) | If Supplier becomes aware of (or if Triple-S notifies Supplier of) any actual, attempted, suspected or threatened Security Breach (but excluding unsuccessful immaterial (1) attempts to breach firewalls, (2) penetrate systems, (3) logon to systems, (4) denial of service attacks, or (5) malware, that do not pose a threat to Triple-S Data), Supplier shall perform clauses (i) and (ii) below, and as requested by Triple-S, clauses (iii) – (vii) below: |
| (i) | as promptly as practicable and, in any case, [***] notify Triple-S’s Chief Compliance Officer, Chief Information Security Officer and Chief Information |
|
Triple-S / Supplier Confidential Page 39 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
Officer of such Security Breach and initiate a root cause analysis thereon, the results of which shall be provided to Triple-S;
| (ii) | investigate such Security Breach and report its findings on a daily basis to Triple-S; |
| (iii) | provide Triple-S with a remediation plan, acceptable to Triple-S, to address such Security Breach and prevent any further incidents; |
| (iv) | execute the approved plan in order to remediate such Security Breach; |
| (v) | conduct a forensic investigation to determine what systems, data and information have been affected by such event, the results of which shall be provided to Triple-S; |
| (vi) | cooperate with Triple-S’s investigation of the Security Breach, including promptly providing any information that Supplier has with respect to the Security Breach; and |
| (vii) | at Triple-S’s request, cooperate with any law enforcement or regulatory officials, credit reporting companies, and credit card associations investigating such Security Breach. |
| (b) | Triple-S shall make the final decision on notifying Triple-S’s members, employees, suppliers and/or the general public of such Security Breach, and the implementation of the remediation plan. |
| 14.4 | Intrusion Detection/Interception |
Upon request, Supplier will, to the extent applicable, provide Triple-S and its representatives with:
| (a) | access to the redacted (to remove other customer information) evidence of alerts, logs and data feeds from Supplier’s network intrusion detection systems, host intrusion detection systems and anti-virus tools to enable Triple-S to have adequate and timely access to system data regarding security incidents impacting Triple-S Data or systems; and |
| (b) | access to Supplier’s policies and procedures relating to intrusion detection and interception with respect to the Supplier systems used to provide the Services for the purpose of examining and assessing those policies and procedures in accordance with Schedule M (Audit and Record Retention Requirements). |
| 14.5 | Litigation and Investigation Requests |
| (a) | Supplier recognizes that (i) Triple-S may, from time to time, ▇▇▇ third parties, be sued by third parties, or have grounds to believe that one or more lawsuits will be filed for or against Triple-S, (ii) Triple-S may be the subject of governmental, regulatory or similar investigations and requests or demands for information from third parties, (iii) Triple-S |
|
Triple-S / Supplier Confidential Page 40 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
may conduct internal investigations or audits at its own prerogative to obtain information necessary to perform an internal audit or monitoring process, obtain information necessary to respond to regulators or other external entities (including commercial groups and sponsors), or otherwise ensure compliance with business and regulatory requirements. Upon any of the foregoing events occurring, Supplier hereby agrees to cooperate with Triple-S and its legal counsel, and to create and implement a process sufficient to comply, in a timely manner, with any requests from Triple-S or its legal counsel to categorize, identify, view, preserve, extract, produce, filter, convert and/or provide to Triple-S, a regulator, or any other Triple-S designee (in the format reasonably requested by Triple-S), any hard copy documents or electronically stored information or data of any type that is associated with the Services, that results from or reflects the Services, that evidences or memorializes Supplier’s efforts on behalf of Triple-S pursuant to this Agreement, or that is required by applicable Law or necessary to evidence compliance with Law (hereinafter, the “Requested Information”). Requested Information may include: claims data, email data, home drive data, server data, common drive data, data stored in cloud repositories, data on smartphones or peripheral devices, and data stored with any third-parties on Supplier’s behalf. Requested Information may include any type of reports or other information received, created or collected as part of the Services, all information created by or for Triple-S or Triple-S’s employees, or at their request, and any information or “metadata,” associated with other types of Requested Information. Requested Information may include any type of information relating to the foregoing within Supplier’s possession, custody or control, including information entrusted to its employees or third parties, or housed in any type of repository or media whatsoever, such as servers, systems, applications, discs, equipment, tapes, or other locations. Supplier shall use Commercially Reasonable Efforts to provide requested information in a timely manner to enable Triple-S to meet regulatory and internal deadlines.
| (b) | Supplier acknowledges and agrees that Supplier may, in some instances, be required by Triple-S to utilize, or be required to involve outside professionals to utilize, forensic extraction methods and techniques to obtain Requested Information. Such methods may include setting-up a new or using an existing non-production environment to retrieve and provide Requested Information. In addition, if requested by Triple-S, Supplier shall provide access to such environment or Requested Information so that Triple-S and/or its designee (provided such designee has a confidentiality agreement in place with Triple-S containing terms comparable to the confidentiality terms set forth in this Agreement) may access, view, download and extract the Requested Information, including reasonable access to third-party litigation support providers selected by Triple-S to facilitate requests for Requested Information. Supplier shall maintain and support an access method for allowing such access and extractions, as determined by Triple-S (e.g., SFTP connections, remote access, on-site access). Supplier will use Commercially Reasonable Efforts to provide all Requested Information within the time period specified by Triple-S or its legal counsel, and, if such deadlines cannot be met, Supplier shall promptly notify Triple-S of the reason and extent of any delay. |
| (c) | Triple-S shall direct any request under this Section 14.5 (Litigation and Investigation Requests) to the Supplier Account Executive. Upon Triple-S’s request, Supplier shall, as appropriate, promptly designate a Supplier attorney or Supplier operations executive to |
|
Triple-S / Supplier Confidential Page 41 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
work with Triple-S and who can facilitate any Triple-S request under this Section. In the event that Triple-S is the target of a governmental inquiry or investigation, Triple-S shall retain all responsibility for directly interacting with such governmental entity regarding such inquiry or investigation. Supplier shall comply with and follow all restrictions and requirements reasonably imposed by Triple-S or its legal counsel to maintain the protections of the attorney-client privilege and attorney work-product doctrine for all efforts and communications connected with requests and efforts made under this Section 14.5.
| 15. | INTELLECTUAL PROPERTY RIGHTS |
This Section 15 sets forth the Parties’ respective rights in Work Product and other materials provided or created pursuant to this Agreement. As between the Parties, the rights apply as set forth in this Section 15 whether the work in question is performed solely by Supplier Personnel or by Supplier Personnel working jointly with others.
| 15.1 | Independent IP |
| (a) | Except as otherwise expressly provided in this Agreement, including in Section 15.2 (Intellectual Property Rights in Work Product): |
| (i) | as between the Parties, each Party will have and retain all of its right, title and interest, including Intellectual Property Rights, in and to its Independent IP and any Derivative Works of its Independent IP, and will be entitled to seek Intellectual Property Rights protection for its Independent IP and any Derivative Works of its Independent IP as it deems appropriate; and |
| (ii) | a Party will not be permitted to use the other Party’s Independent IP or any Derivative Works of the other Party’s Independent IP. |
| (b) | Supplier shall not incorporate any Independent IP of Supplier or a third party into any Deliverable without Triple-S’s prior written approval, which Triple-S may withhold in its discretion. Any such written approval, together with details of the Independent IP that will be incorporated in the Deliverable, shall be documented in the applicable Statement of Work or Task Order. |
| (c) | If Supplier incorporates any Independent IP of Supplier or a third party into a Deliverable without first notifying Triple-S of its nature and entering into with Triple-S, or procuring for Triple-S, a license to Use the Independent IP on terms that are acceptable to Triple-S, then (i) in the case of Supplier Independent IP, Supplier hereby grants to Triple-S and its Affiliates, and (ii) in the case of third party Independent IP, Supplier shall procure for Triple-S and its Affiliates, a perpetual, irrevocable, non-exclusive, worldwide, paid-up right and license to Use such Independent IP (including Source Code, artifacts, programmer interfaces, available Documentation, manuals, and other materials that may assist Triple-S with Use thereof), solely in connection with, and as incorporated into, the Deliverable and solely in their businesses and to authorize others (including Triple-S third party contractors providing services to Triple-S, Triple-S Affiliates, and Service Recipients and not for any such contractor’s own use) to do the same on their behalf, for |
|
Triple-S / Supplier Confidential Page 42 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
no additional charge. Triple-S will require any such third party contractors to comply with the obligations of confidentiality and restrictions limiting use of the Independent IP solely to performance of services on behalf of Triple-S. All representations, warranties, and covenants of Supplier, and any rights of Triple-S under this Agreement, that are applicable to Deliverables shall apply equally to any Independent IP of Supplier incorporated into Deliverables.
| (d) | If Triple-S provides any of its Independent IP to Supplier for use in rendering the Services, Triple-S grants to Supplier a fully paid-up, nonexclusive license during the Term and any Disengagement Assistance Period to Use such Independent IP solely as necessary to perform the Services, and to sublicense Approved Subcontractors to do the same on Supplier’s behalf. Supplier may not Use Triple-S’s Independent IP for the benefit of any entities other than Triple-S (and its Service Recipients under this Agreement) without the prior written consent of Triple-S, which may be withheld at Triple-S’s discretion. |
| 15.2 | Intellectual Property Rights in Work Product |
| (a) | Deliverables and Work Product Owned by Triple-S. |
| (i) | Subject to Section 15.2(a)(iii) below, and subject to the ownership rights of Supplier and any Supplier third party providing Independent IP to Supplier in their respective Independent IP and Derivative Works of their Independent IP which may be incorporated therein pursuant to Section 15.1(a) and 15.1(c), Triple-S will be the sole and exclusive owner of all Intellectual Property Rights in and to the following (collectively, the “Triple-S Work Product”): |
| (A) | Deliverables or portions of Deliverables that are not Derivative Works of Independent IP owned or licensed by a Party or its Affiliates; |
| (B) | Deliverables or portions of Deliverables that are Derivative Works of Independent IP owned or licensed by Triple-S or its Affiliates or Service Recipients; |
| (C) | Work Product that is a Derivative Work of Independent IP owned or licensed by Triple-S or its Affiliates; and |
| (D) | All modifications and enhancements to In-Scope Applications whether they are classified as Deliverables, Work Product or otherwise. |
| (ii) | Subject to Section 15.2(a)(iii), as between the Parties, Triple-S will be the sole and exclusive owner of the Intellectual Property Rights in each Triple-S Work Product from the moment of its creation. Triple-S Work Product will be deemed to be a ‘work made for hire’ under the copyright Laws. To the extent that any such Triple-S Work Product is not deemed to be a ‘work made for hire’ and the property of Triple-S by operation of Law, Supplier (on its own behalf as well as on behalf of its current and future employees, agents and subcontractors) hereby irrevocably conveys and assigns to Triple-S, without further consideration, all |
|
Triple-S / Supplier Confidential Page 43 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
right, title, and interest in and to the Triple-S Work Product. Supplier agrees to execute such other documents or take such other actions as Triple-S may reasonably request to perfect Triple-S’s ownership of any Triple-S Work Product. Triple-S and its assigns will have the right to register and hold in their own name the copyright in and to such Triple-S Work Product.
| (iii) | Triple-S grants to Supplier a fully paid-up, nonexclusive license to Use such Triple-S Work Product during the Term (and the Disengagement Assistance Period) solely as necessary to perform the Services, and to sublicense Approved Subcontractors to do the same on Supplier’s behalf in the performance of the Services. |
| (b) | Ownership of Other Developed Items. |
| (i) | Subject to the rights of Triple-S and any third parties in their respective Independent IP and Derivative Works of their Independent IP and Triple-S’s ownership of Triple-S Work Product pursuant to Section 15.2(a) above, and in addition to Supplier’s rights in Independent IP of Supplier pursuant to Section 15.1(a) above, Supplier shall be the sole and exclusive owner of all Intellectual Property Rights in and to Deliverables and Work Product that are not Triple-S Work Product (collectively, “Other Developed Items”). |
| (ii) | Supplier hereby grants to Triple-S and its Affiliates and Service Recipients, a perpetual, irrevocable, non-exclusive, worldwide, sublicenseable, paid-up right and license to Use in their businesses and to authorize others (including Triple-S contractors) to do the same solely on behalf of Triple-S and its Affiliates and Service Recipients (and only where such other parties are subject to an obligation of confidentiality and limited to services performed for or on behalf of Triple-S, its Affiliates or Service Recipients) for no additional charge, such Other Developed Items, including Source Code, artifacts, programmer interfaces, available Documentation, manuals, and other materials that may assist Triple-S with the Use of such Other Developed Items. For clarity, the foregoing license does not apply to Supplier Software and Supplier Tools denoted as Non-Commercially Available on Schedule S (Supplier Software and Supplier Tools) (including any Other Developed Item denoted as Non-Commercially Available pursuant to the process set forth in Section 10.4(c)), provided the foregoing is not intended to limit the license granted in Section 10.5 (License During the Term and Disengagement Assistance Period). |
| (c) | Residual Knowledge. |
Notwithstanding anything to the contrary in this Agreement, each Party will be free to use the ideas, concepts, methodologies, processes and know-how that are used, developed or created in the course of performing the Services that are retained in the unaided mental impressions of the employees of such Party in intangible form, provided that in doing so they do not use or disclose Confidential Information of the other Party in violation of Section 21 (Confidentiality), or misappropriate or infringe upon the Intellectual Property Rights of the other Party, its Affiliates (including such rights granted pursuant to Section
|
Triple-S / Supplier Confidential Page 44 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
15.1 (Independent IP)) or third parties who have licensed or provided Independent IP to the other Party or its Affiliates.
| 15.3 | Intellectual Property Rights Agreements with Supplier Personnel |
Supplier is responsible for having in place with all Supplier Personnel (either directly or indirectly through their respective employers) such agreements respecting Intellectual Property Rights as are necessary for Supplier to fulfill its obligations under this Section 15 (Intellectual Property Rights). Upon Triple-S’s written request, Supplier shall provide copies of the template which Supplier requires employees and contractors to sign to implement the foregoing agreement with Triple-S (i.e., Supplier’s standard employment contract template).
| 15.4 | Rights on Bankruptcy of Supplier |
All licenses and rights of Use granted under or pursuant to this Agreement shall be deemed to be, for the purposes of Section 365(n) of the United States Bankruptcy Code (the “Bankruptcy Code”), licenses to rights in “intellectual property” as defined under the Bankruptcy Code. Accordingly, the licensee of such rights shall retain and may fully exercise all of its rights and elections under the Bankruptcy Code. Upon the commencement of bankruptcy proceedings by or against either Party under the Bankruptcy Code, the other Party shall be entitled to retain all of its license rights and Use rights granted under this Agreement.
16. TERMINATION
| 16.1 | Termination by Triple-S |
| (a) | Termination for Cause. If Supplier commits (i) a material breach of this Agreement or any Statement of Work or Task Order that is capable of being cured within thirty (30) days after receiving notice of the breach from Triple-S, and fails to cure such breach within such thirty (30) day period; (ii) a material breach of this Agreement that is not capable of being cured within thirty (30) days after receiving notice of breach from Triple-S but is capable of being cured within sixty (60) days, and fails to (A) proceed promptly and diligently to cure the breach, (B) develop within thirty (30) days after receiving such notice a reasonably detailed plan for curing the breach, and (C) cure the breach within sixty (60) days after receiving such notice; or (iii) multiple breaches of this Agreement or any Statement of Work or Task Order, whether material or non-material, that collectively constitute a material breach of this Agreement or any Statement of Work or Task Order; then Triple-S may, by giving written notice to Supplier, terminate (A) in the case of a material breach of the General Terms and Conditions, this Agreement, in whole or in part, and (B) in the case of a material breach of a Statement of Work or any Task Order, terminate the applicable Statement of Work or any Task Order (in whole or in part), without charge or fee (except any outstanding Charges for all Services provided in accordance with this Agreement through the effective date of termination (subject to Triple-S’s right to dispute Charges set forth in Schedule C (Charging Methodology) in good faith)), as of a date specified in the notice of termination. Any termination by Triple-S shall not constitute an election of remedies and shall be without prejudice as to Triple-S’s other rights and remedies. |
|
Triple-S / Supplier Confidential Page 45 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
| (b) | Termination for Convenience. Triple-S may terminate this Agreement (in whole and not in part) at any time for convenience (i.e., for any reason or no reason) by giving Supplier at least one hundred eighty (180) days’ prior written notice (unless the Parties expressly agree otherwise in writing) designating the termination date and paying to Supplier on or before the effective date of termination any (properly invoiced) outstanding Charges for all Services provided in accordance with this Agreement through the effective date of termination (subject to Triple-S’s right to dispute Charges set forth in Schedule C (Charging Methodology) in good faith); provided the effective date of such termination shall not be earlier than the [***] of the Effective Date. Such termination shall be without charge or fee except for any applicable early termination for convenience charges (if any) expressly set forth in Schedule C (Charging Methodology), and except for the amounts described in the preceding sentence. If a purported termination for cause by Triple-S under Section 16.1(a) is found by a competent authority not to be a proper termination for cause, then such termination will be deemed to be a termination for convenience by Triple-S under this paragraph except that the notice requirements of this paragraph will apply. |
| (c) | Termination for certain Service Level Failures. If (i) Supplier fails to meet the same [***] Service Level [***] times in any rolling [***], then Triple-S may, by giving written notice to Supplier, terminate this Agreement or any Statement of Work or Task Order (in whole or in part) without charge or fee (except any outstanding Charges for all Services provided in accordance with this Agreement through the effective date of termination (subject to Triple-S’s right to dispute Charges set forth in Schedule C (Charging Methodology) in good faith)), as of a date specified in the notice of termination. The foregoing rights to terminate shall not be construed as precluding Triple-S from claiming that some other combination of failures to meet Service Levels is a material breach of this Agreement and to exercise any available remedies in connection with such material breach. Triple-S’s termination rights in this Section 16.1(c) shall only apply with respect to each Statement of Work beginning [***] of each Statement of Work. In other words, any Service Level Failure prior to such date will not count as a failure for determining whether Triple-S has the right to terminate pursuant to this Section 16.1(c). |
| (d) | Termination Following a Change of Control of Supplier. “Change of Control of Supplier” means an announcement by Supplier (i) that any other entity, person or “group” (as such term is used in Section 13(d) of the Securities Exchange Act of 1934, as amended) that is not an Affiliate of Supplier will acquire (and eventually does acquire) Control, of all or substantially all of the assets, of Supplier (or any parent company of Supplier), whether directly or indirectly, in a single transaction or series of related transactions, or (ii) that Supplier (or any parent company of Supplier) will consolidate with, or be merged with or into, another entity that is not an Affiliate of Supplier, or will sell, assign, convey, transfer, lease or otherwise dispose of all or substantially all of the assets of Supplier to another person(s) or entity(ies) that is not an Affiliate of Supplier. Notwithstanding the foregoing, Triple-S agrees that a spin-off of Supplier or Optum, Inc. into an independent company will not constitute a Change of Control of Supplier. At any time within one (1) year after the consummation of the transaction described in (i) or (ii) above, Triple-S may terminate this Agreement (in whole and not in part) by giving Supplier at least one hundred eighty (180) days prior written notice designating the |
|
Triple-S / Supplier Confidential Page 46 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
termination date. Such termination shall be [***] Triple-S shall pay to Supplier on or before the effective date of termination any outstanding Charges for all Services (including work in progress) provided in accordance with this Agreement through the effective date of termination (subject to Triple-S’s right to dispute Charges set forth in Schedule C (Charging Methodology) in good faith).
| (e) | Termination in the Event of a Force Majeure. Triple-S may terminate this Agreement or any Statement of Work or Task Order (in whole or in part) [***], as provided in Section 24.4 (Force Majeure). |
| (f) | Termination Due to Change in Laws. |
| (i) | Triple-S may terminate this Agreement or any Statement of Work or Task Order (in whole or in part) by giving Supplier at least ninety (90) days prior written notice specifying the terminated Services and designating the termination date if a Law enacted, created or modified after the Effective Date (including any Laws that increase taxes) (A) has a material adverse effect on Triple-S’s receipt or use of Services or (B) increases Triple-S’s cost of using or receiving the terminated Services by more than [***] and (in either case) the Parties are unable to agree upon equitable adjustment in Charges or the scope of the Affected Services that would address the new or modified Law in a manner that is satisfactory to the Parties. |
| (ii) | Triple-S may exercise the termination right set forth in this Section by sending a written notice to Supplier as described above not later than one hundred eighty (180) days after the effective date of the enacted, created or modified Law. Such termination shall be [***] Triple-S shall pay to Supplier on or before the effective date of termination any outstanding Charges for all Services (including work in progress) provided in accordance with this Agreement through the effective date of termination (subject to Triple-S’s right to dispute Charges set forth in Schedule C (Charging Methodology) in good faith) and any applicable early termination for change in Laws charges expressly set forth in Schedule C (Charging Methodology). |
| (g) | Termination Relating to Supplier’s General Liability Cap. If Supplier pays to or owes to (or some combination thereof) Triple-S aggregate damages in excess of [***] of the General Liability Cap as a result of one or more of the following (i) an agreement by Supplier that it owes Triple-S certain damages, (ii) a settlement agreed to by the Parties, or (iii) an order from a court of competent jurisdiction or an arbitration award, and Supplier does not agree to refresh the General Liability Cap, as applicable, to its original amount (i.e., none of such damages shall, after such refresh, be considered to have applied against the General Liability Cap) within thirty (30) days after a Triple-S request to refresh the General Liability Cap, then Triple-S may terminate for cause this Agreement or any SOW or Task Order (in whole or in part), upon no less than thirty (30) days prior written notice to Supplier. Such termination shall be [***] Triple-S shall pay to Supplier on or before the effective date of termination any outstanding Charges for all Services provided in accordance with this Agreement through the effective date of termination (subject to Triple-S’s right to dispute Charges set forth in Schedule C |
|
Triple-S / Supplier Confidential Page 47 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
(Charging Methodology) in good faith). If Supplier agrees to refresh the General Liability Cap pursuant to this Section, the Parties agree that such amounts added to refresh the General Liability Cap shall not be used to payliabilities described in (i), (ii) or (iii) that caused the [***] threshold to have been exceeded. Triple-S’s termination rights in this Section 16.1(g) shall no longer apply once Supplier refreshes the General Liability Cap [***] during the Term.
| (h) | Termination Relating to Regulatory Approval. |
| (i) | Triple-S may terminate this Agreement or any Statement of Work or Task Order if Triple-S is unable to obtain one or more regulatory approvals as provided in Section 3.3 (Regulatory Approvals) on or prior to December 31, 2017 by giving Supplier prior written notice specifying the terminated Services and designating the termination date, and paying to Supplier on or before the effective date of the termination any outstanding Charges for all Services (including work in progress) provided in accordance with this Agreement through the effective date of termination (subject to Triple-S’s right to dispute Charges set forth in Schedule C (Charging Methodology) in good faith). |
| (ii) | Such termination shall be [***] the amounts described in 16.1(h)(i) above, as applicable, and any applicable early termination for regulatory approval charges expressly set forth in Schedule C (Charging Methodology). |
| (iii) | Before exercising the termination right set forth in this Section, Triple-S and Supplier shall work together in good faith, using the Governance procedure set forth in Schedule F (Governance), for a period acceptable to the regulators (not to exceed ninety (90) days), to seek options to achieve regulatory approval. |
| (i) | Termination related to Business Associate Agreement. Triple-S may terminate this Agreement as provided in Schedule H (Business Associate Agreement). Such termination shall be [***] (except any outstanding Charges for all Services (including work in progress) provided in accordance with this Agreement through the effective date of termination (subject to Triple-S’s right to dispute Charges set forth in Schedule C (Charging Methodology) in good faith)). |
| (j) | Termination Due to Adverse Changes in Supplier’s Financial Circumstances. If Supplier (but not any Subcontractor) (A) files a petition in bankruptcy; (B) has an involuntary petition in bankruptcy filed against it which is not challenged within thirty (30) days and dismissed within sixty (60) days; (C) becomes insolvent; (D) makes a general assignment for the benefit of creditors; (E) admits in writing its inability to pay substantially all of its debts as they mature; (F) has a receiver appointed for its assets; (G) has any significant portion of its assets attached; or (H) experiences a material negative change in its net assets (i.e., total assets minus total liabilities), then Triple-S may by giving thirty (30) day written notice to Supplier, terminate this Agreement as of the date specified in such written notice of termination. Supplier shall notify Triple-S as soon as possible if one of the circumstances in this Section 16.1(j) occurs or is likely to occur. Supplier shall certify within ten (10) Business Days of a written request by Triple-S, that none of the circumstances in this Section 16.1(j) have occurred as of the date of certification or, to |
|
Triple-S / Supplier Confidential Page 48 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
the best of Supplier’s knowledge, are likely to occur within [***] after the date of certification. Such termination shall be [***] (except any outstanding Charges for all Services (including work in progress) provided in accordance with this Agreement through the effective date of termination (subject to Triple-S’s right to dispute Charges set forth in Schedule C (Charging Methodology) in good faith)).
| 16.2 | Termination by Supplier |
| (a) | If Triple-S |
| (i) | fails to pay Supplier when due material Charges under this Agreement, not otherwise disputed in good faith, totaling an amount greater than or equal to the result obtained by [***], and fails to make such payment within [***] after the date Triple-S receives written notice of non-payment from Supplier (a copy of which notice shall also indicate that Supplier may terminate this Agreement if Triple-S fails to pay such unpaid amounts, and shall be sent by Supplier to the Triple-S Chief Financial Officer and General Counsel), or |
| (ii) | materially breaches Section 10.5 (License During the Term and the Disengagement Assistance Periods), Section 13 (Compliance With Laws), Section 15 (Intellectual Property), or Section 21 (Confidentiality) and Triple-S fails to cure such material breach within thirty (30) days after the date Triple-S receives written notice of such material breach from Supplier (a copy of which notice shall also indicate that Supplier may terminate this Agreement if Triple-S fails to cure such material breach, and shall be sent by Supplier to the Triple-S Chief Financial Officer and General Counsel), |
then Supplier may terminate this Agreement by sending written notice to Triple-S terminating this Agreement, in which event this Agreement shall terminate as of the date specified in the notice of termination (but not earlier than thirty (30) days after Triple-S’s receipt of such notice).
| (b) | For clarity and without limiting Triple-S’s rights in Section 17 (Disengagement Assistance) (but subject to Section 17.3(c)), Triple-S shall be entitled to Disengagement Assistance pursuant to Section 17 (Disengagement Assistance) if Supplier terminates this Agreement. |
| 16.3 | Extension of Termination/Expiration Date |
Triple-S may extend the effective date of termination/expiration one or more times as it elects. However, in no event may the total of all such extensions exceed one hundred eighty (180) days following the effective date of termination/expiration in place immediately prior to the initial extension under this Section 16.3. If any extension notice provided to Supplier within ninety (90) days of the then-scheduled date of termination/ expiration would cause Supplier to incur additional costs or expenses, Supplier may so notify Triple-S. In that case, the extension of this Agreement’s Term pursuant to the notice will be subject to Triple-S agreeing to reimburse Supplier for its additional costs and expenses incurred as a result of the extension notice being provided within ninety (90) days of the then scheduled date of termination/ expiration.
|
Triple-S / Supplier Confidential Page 49 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
| 16.4 | Partial Termination |
| (a) | In the event of a termination of this Agreement or Statement of Work or any Task Order in part pursuant to this Section 16: |
| (i) | the scope of the Services shall be reduced to remove the terminated Services; |
| (ii) | the Service Levels and other performance standards for such terminated Services shall cease to apply with respect to the terminated Services; |
| (iii) | if this Agreement (or the applicable SOW) does not otherwise specify the basis for determining Supplier’s charges for the continuing Services that are not terminated, the charges payable under this Agreement (or the applicable SOW) will be equitably adjusted to reflect the Services that have been terminated; |
| (iv) | any minimum revenue commitment shall be adjusted using the methodology provided in Schedule C (Charging Methodology), or otherwise reduced in an equitable manner to the extent such methodology does not apply to the withdrawn portions of the Services; |
| (v) | Supplier shall provide Disengagement Assistance with respect to the terminated Services pursuant to Section 17 (Disengagement Assistance); and |
| (vi) | the following shall be equitably adjusted based on the effect of such partial termination: |
| (A) | the Service Levels for the remaining Services under this Agreement (i.e., if the partial termination affects Supplier’s ability to meet such Service Levels); |
| (B) | applicable affected provisions of this Agreement or other Services; and |
| (C) | the termination-related payments for which Triple-S is responsible will be revised to reflect that some portion of that amount has been paid by Triple-S. |
The Parties shall negotiate such equitable adjustments above in good faith.
| (b) | The Parties shall enter into an amendment to this Agreement or Change Order to reflect the termination in part and the resulting adjustments. |
| (c) | Unless Triple-S provides written notice to Supplier terminating a portion of this Agreement in part pursuant to any applicable provision of Section 16.1 (Termination by Triple-S), a reduction in volumes or scope as contemplated by Section 2.7 (Services Not Exclusive; Variable) or Schedule C (Charging Methodology) shall not constitute a termination in part, and such reduction in volumes or scope shall be subject to the terms of Section 2.7 (Services Not Exclusive; Variable) and/or Schedule C (Charging |
|
Triple-S / Supplier Confidential Page 50 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
Methodology) instead of the provisions of this Section 16.4 (Termination of this Agreement in Part).
| 17. | DISENGAGEMENT ASSISTANCE |
| 17.1 | General |
| (a) | Commencing twelve (12) months prior to expiration of this Agreement, or commencing upon a notice of termination (including notice based upon breach by Triple-S under Section 16.2 (Termination by Supplier)) or of non-renewal of this Agreement or a Statement of Work or Task Order (in whole or in part), and continuing (as requested by Triple-S) for up to [***] following the effective date of expiration or, if applicable, of termination of this Agreement (as such effective date may be extended pursuant to Section 16.3 (Extension of Termination/Expiration Date)), or a portion thereof, Supplier shall provide such Disengagement Assistance to Triple-S as Triple-S requests, including to a Successor Supplier. Triple-S shall provide Supplier with reasonable advance notice (not less than ninety (90) days) before Triple-S removes any material portion of the Services during the Disengagement Assistance Period and the Parties shall work in good faith to establish a plan for the timing of Triple-S’s reduction of Services during the Disengagement Assistance Period. Supplier shall also provide Disengagement Assistance in the context of Triple-S’s reduction or removal of a portion of the Services or volumes or Functions in accordance with this Agreement, although this Agreement is not itself being terminated in whole or in part. Disengagement Assistance includes the assistance described in Schedule I (Disengagement Assistance) and this Section 17. |
| (b) | Supplier shall also provide Disengagement Assistance in the event of any partial termination of this Agreement. |
| (c) | The quality of the Services provided by Supplier, and the Supplier’s performance of the Services, will not be materially degraded during the period Supplier is providing Disengagement Assistance. Supplier shall not make any changes to the number of Supplier Personnel providing Services during the Disengagement Assistance Period or reassign any Supplier Personnel holding Key Supplier Positions away from performing Services under this Agreement during the Disengagement Assistance Period except as mutually agreed to by the Parties in writing or to remove resources for Services that have been reduced or fully wound down. |
| (d) | Supplier shall provide Disengagement Assistance utilizing Supplier Personnel then being regularly utilized to provide the Services, provided, however, that if Supplier believes in good faith that providing such assistance utilizing such Supplier Personnel will prevent Supplier from meeting the Service Levels or otherwise complying with other obligations under this Agreement and gives written notice to such effect to Triple-S, then Supplier shall not be obligated to provide the Disengagement Assistance utilizing only the Supplier Personnel to the extent that utilizing such personnel would cause Supplier to fail to meet the Service Levels or otherwise be unable to comply with other Supplier obligations under this Agreement, provided further, that if Triple-S agrees to waive the Service Level Credits for failure to meet the Service Levels relating to the applicable Service Levels and to excuse nonperformance of other affected obligations of Supplier |
|
Triple-S / Supplier Confidential Page 51 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
(provided that Supplier shall use good faith efforts to continue to meet the Service Levels), then Supplier shall provide Disengagement Assistance utilizing Supplier Personnel then being utilized in performing the Services. If Triple-S does not provide such relief, the Parties shall use the Change Control Process to address the use of additional Supplier Personnel to provide Disengagement Assistance and Section 17.3(b) shall apply.
| (e) | Triple-S and the Successor Supplier shall be permitted to undertake, without interference from Supplier, to hire any Supplier Personnel employed by Supplier or its Affiliates performing the Services (which are expiring or being terminated) as of the date of notice of termination or, in the case of expiration, within the six (6) month period (or longer period reasonably requested by Triple-S) prior to expiration. Supplier and its Affiliates shall waive their rights, if any, under contracts with such personnel restricting the ability of such personnel to be recruited or hired by Triple-S and the Successor Supplier. Triple-S and the Successor Supplier shall have reasonable access to such personnel for interviews and recruitment. This Section 17.1(e) shall not apply to individuals in Key Supplier Positions with respect to the Successor Supplier. |
| (f) | Provided that such third party is subject to a confidentiality agreement with Triple-S with terms substantially similar to Section 21 (Confidentiality) of these General Terms and Conditions and Triple-S is responsible for such third party’s compliance with this Agreement, including Section 15 (Intellectual Property Rights), Supplier shall make available Documentation and information reasonably sufficient for Triple-S or Triple-S’s designated Successor Supplier to assume the provision of such terminated Services and become self-reliant with respect to such terminated Services. In no event shall Triple-S disclose Documentation for Supplier Tools or Supplier Software. Triple-S’s and the Successor Supplier’s use of such Documentation and information that constitutes Supplier Confidential Information shall be subject to the confidentiality obligations herein. Such information shall be stored and provided to Triple-S in an electronic format that is reasonably acceptable to, and in a location and manner that is easily accessible by, Triple-S. Supplier shall provide Triple-S with a copy of any Documentation promptly upon Triple-S’s request, but in any event within ten (10) Business Days of Supplier’s receipt of such request. |
| (g) | With respect to any Software or Tool used by Supplier to provide Services for which Supplier is not obligated to grant or provide a license pursuant to this Agreement, then upon Triple-S’s request, Supplier shall (as designated by Triple-S) assist Triple-S with procuring a license to such Software or Tool (and applicable third party maintenance and support contract) on behalf of Triple-S. |
| (h) | If and to the extent requested by Triple-S, Supplier shall (i) assign to Triple-S or the Successor Supplier leases for some or all of the Supplier Leased Equipment located in Puerto Rico, including applicable maintenance agreements (all as designated by Triple-S) that was used as of the date of termination or expiration of this Agreement or portion thereof exclusively for providing the Services, and Triple-S shall assume the obligations under such leases that relate to periods after such date; provided, however, Supplier shall not be obligated to assign any such leases with respect to which Supplier notified Triple-S that it is unable to obtain the right to assign such lease to Triple-S, and notwithstanding . |
|
Triple-S / Supplier Confidential Page 52 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
such, Triple-S approved the acquisition of such lease pursuant to Section 10.2(a); and (ii) sell to Triple-S or the Successor Supplier, at the lower of fair market value or Supplier’s then current book value, some or all of the Equipment (as designated by Triple-S) owned by Supplier that was used in Puerto Rico as of the date of termination or expiration of this Agreement or portion thereof exclusively used for providing the Services, including applicable maintenance agreements. Supplier shall also provide all user and other Documentation relevant to such Equipment which is in Supplier’s possession. Triple-S or the Successor Supplier (as applicable) will assume responsibility under any such maintenance agreements to the extent such responsibilities relate to periods after the date of termination or expiration of this Agreement or portion thereof
| (i) | If and to the extent requested by Triple-S, Supplier shall assign to Triple-S or the Successor Supplier some or all of the Supplier Third Party Service Contracts (as designated by Triple-S) that were used as of the date of termination or expiration of this Agreement or portion thereof exclusively to provide the Services, and Triple-S shall assume the obligations under such contracts that relate to periods after such date; provided, however, that subject to Section 17.1(j) below, Supplier shall not be required to assign any such contracts with respect to which Supplier notified Triple-S that it is unable to obtain the right to assign such lease to Triple-S, and notwithstanding such, Triple-S approved the acquisition of such lease pursuant to Section 10.3(c). |
| (j) | With respect to any third party services then being exclusively utilized by Supplier in the performance of the Services (other than services under Supplier Third Party Service Contracts Supplier is obligated to assign to Triple-S or the Successor Supplier pursuant to Section 17.1(j)), if permitted by the terms of the applicable contract, if and to the extent requested by Triple-S, Supplier shall make available or assign to Triple-S or the Successor Supplier (as designated by Triple-S) the contract for such third party services, pursuant to reasonable terms and conditions. Supplier shall use Commercially Reasonable Efforts to assign any other third party service contracts used exclusively to provide the Services which Triple-S requests to be assigned to Triple-S. |
| (k) | As requested by Triple-S, Disengagement Assistance shall include Supplier continuing to provide any or all of the Services provided by Supplier prior to the effective date of termination/expiration. Services provided by Supplier under this Section 17 shall be subject to the other provisions of this Agreement. |
| 17.2 | Required Consents |
| (a) | Software/Tools and Associated Maintenance and Support Agreements. Supplier shall have Financial Responsibility and be administratively responsible (with the cooperation of Triple-S) for obtaining the Required Consents for any Software and Tools (and any associated maintenance and support agreements) for which Supplier is obligated to provide a license or access rights to Triple-S pursuant to this Agreement (including Section 10.4(a)(i) (Supplier Software and Tools), Section 10.5 (License During the Term and Disengagement Assistance Period), Section 15.1(c) (Independent IP), Section 15.2(b) (Ownership of Other Developed Items)), and Schedule S (Supplier Software and Supplier Tools). Triple-S shall be financially responsible and Supplier shall be administratively responsible (with the cooperation of Triple-S) for obtaining a Required |
|
Triple-S / Supplier Confidential Page 53 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
Consent necessary to assign to Triple-S or a Successor Supplier a Software or Tool license (and associated maintenance and support agreements) for any Software or Tool not covered by the prior sentence.
| (b) | Equipment Leases and Third Party Service Contracts. If Triple-S requests Supplier to assign any lease for Supplier Leased Equipment in accordance with Section 17.1(h) above, or if Triple-S requests Supplier to assign any Supplier Third Party Service Contract in accordance with Section 17.1(i) above, then the Party which is obligated to procure the Required Consent for such Supplier Leased Equipment lease or such Supplier Third Party Service Contract shall be as follows: |
| (i) | if at the time of acquisition of such Supplier Leased Equipment or Supplier Third Party Service Contract, (A) Supplier had satisfied its obligation in Section 10.2 (Equipment) (with respect to Supplier Leased Equipment) and Section 10.3 (Third Party Services) (with respect to such Supplier Third Party Service Contracts), as applicable, to use Commercially Reasonable Efforts to obtain the right to assign the asset to Triple-S, but (B) despite such efforts Supplier was unable to obtain such rights, and (C) Supplier so notified Triple-S, and (D) Triple-S agreed in writing that Supplier could acquire such asset to utilize in providing the Services notwithstanding not having such right to assign (all as set forth in Section 10.2 (Equipment) and Section 10.3 (Third Party Services) above), then Triple-S shall be financially obligated to procure such Required Consent, and Supplier shall be administratively responsible for procuring such Required Consent (with the cooperation of Triple-S); and |
| (ii) | for any scenario not covered by Section 17.2(b)(i) above with respect to such Supplier Leased Equipment leases and such Supplier Third Party Service Contracts, Supplier shall be financially and administratively obligated to procure such Required Consent (with the cooperation of Triple-S); and |
| (iii) | for clarity, maintenance and support agreements for Software and Tools are covered by Section 17.2(a) above and not this Section 17.2(b). |
| 17.3 | Charges for Disengagement Assistance |
Charges for Disengagement Assistance shall be as follows:
| (a) | For Disengagement Assistance that constitutes a continuation of the Services and for which there is a predetermined Charge in this Agreement (e.g., a charge for maintaining an Application as set forth in this Agreement), such pre-determined Charge shall apply; provided, however, that as Services are reduced the Charges shall be adjusted using the methodology provided in Schedule C (Charging Methodology), or otherwise reduced in an equitable manner to the extent such methodology does not apply to the withdrawn portions of the Services. The Parties shall negotiate such equitable adjustments above in good faith. |
| (b) | For Disengagement Assistance for which (i) there is no predetermined Charges in this Agreement (i.e., for assistance that is not part of the routine Services) and (ii) Supplier is |
|
Triple-S / Supplier Confidential Page 54 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
permitted under Section 17.1(d) to utilize (and does in fact utilize) personnel in addition to the existing Supplier Personnel to provide such Disengagement Assistance, then (subject to Section 17.1(c)) such assistance will be chargeable at the Personnel Rates to the extent performed by Supplier Personnel not otherwise performing Services for Triple-S prior to the effective date of termination or expiration of this Agreement.
| (c) | If Supplier has terminated this Agreement pursuant to Section 16.2 (Termination by Supplier), then the provision of Disengagement Assistance shall be subject to Triple-S paying the estimated charges for Disengagement Assistance monthly in advance. |
| 17.4 | Bid Assistance |
| (a) | In the process of deciding whether to undertake or allow any cessation of Services, or any termination, expiration or renewal of this Agreement, in whole or in part, Triple-S may consider or seek offers for performance of services to replace the Services. As and when reasonably requested by Triple-S for use in any such process, Supplier will provide to Triple-S such information and other cooperation regarding performance of the Services as would be reasonably necessary to enable Triple-S to prepare a request for proposal relating to some or all of such services, and for a third party to conduct due diligence and prepare an informed, non-qualified offer for such services. |
| (b) | Without limiting the generality of Section 17.4(a), the types of information and level of cooperation to be provided by Supplier pursuant to this Section 17.4 will be no less than those initially provided by Triple-S to Supplier prior to the Effective Date, and shall include the following information which Triple-S may distribute to third-party bidders in a request for proposal(s), request for information, specification, or any other solicitation relating to the Services and as necessary to support any related due diligence activities: |
| (i) | General organization charts showing the overall structure of the information technology outsourcing organization supporting Triple-S, and a description of the roles and responsibilities of the various functions described in such organization charts; |
| (ii) | General organization charts showing the overall structure of the organization supporting the Services and a description of the roles and responsibilities of the various Functions described in such organization charts; |
| (iii) | With respect to time and material engagements, the number of personnel at each location used to provide Services classified by job title, skill level, and experience; |
| (iv) | Generic job descriptions of the functions and job classifications within the organization providing Services; |
| (v) | Up-to-date Service Level performance histories, third-party contract lists, then-current work volumes and information relating to projects underway; |
| (vi) | Detailed network topographies; and |
|
Triple-S / Supplier Confidential Page 55 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
| (vii) | List of all Software and Equipment utilized to provide the Services, including details regarding the same such as version, release and the title and similar information related to Software and Equipment as reasonably requested by Triple-S. |
| 18. | GOVERNANCE AND MANAGEMENT |
| 18.1 | Governance Structure and Processes |
| (a) | Supplier acknowledges that it is a key business requirement of Triple-S that Supplier provide the Services in a consistent, integrated manner in accordance with Schedule F (Governance). Schedule F (Governance) contains a description of the committees and governance processes the Parties have formed and will use to govern their relationship and activities under this Agreement. |
| (b) | Notwithstanding anything set forth in this Agreement to the contrary, any term in this Agreement that states that a matter shall be referred to or resolved in accordance with Schedule F (Governance) shall not affect either Party’s right to escalate such matter to the dispute resolution provisions in Section 25. |
| 18.2 | Reports |
The Parties have agreed to certain terms regarding reports as set forth in Schedule K (Reports).
| 18.3 | Procedures Manual |
| (a) | The “Procedures Manual” is a document (or set of documents) to be prepared by Supplier describing how Supplier will perform and deliver the Services under this Agreement, the Equipment and Software used, and the documentation (e.g., operations manuals, user guides, specifications) that provide further details of the activities. The Procedures Manual may also be referred to as “SOPs”. The table of contents of the Procedures Manual as of the Effective Date is set forth in Schedule CC (Procedures Manual TOC). The Procedures Manual will: |
| (i) | describe the activities Supplier shall undertake in order to provide the Services, including those direction, supervision, monitoring, staffing, reporting, planning and oversight activities normally undertaken to provide services of the type Supplier is to provide under this Agreement; |
| (ii) | include Supplier’s escalation procedures and the other standards and procedures of Supplier pertinent to Triple-S’s interactions with Supplier in obtaining the Services; and |
| (iii) | include such other information as would be reasonably necessary to an Auditor when performing audits as permitted by this Agreement. |
| (b) | The Procedures Manual must be reasonably suitable for use by Triple-S to understand the Services. |
|
Triple-S / Supplier Confidential Page 56 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
| (c) | Working in consultation with Triple-S, Supplier will deliver to Triple-S a draft Procedures Manual describing the Services to be transitioned from Triple-S to Supplier within one hundred eighty (180) days after the first Services Commencement Date. Triple-S shall have the opportunity to provide comments and suggestions on the draft Procedures Manual and to identify deficiencies. Supplier will address Triple-S’s reasonable comments and identified deficiencies and will provide a revised Procedures Manual with respect to each wave, within one hundred eighty (180) days after the occurrence of such wave. The final Procedures Manual will be subject to the approval of Triple-S. |
| (d) | The Procedures Manual will be considered an operational document, which Supplier shall revise and periodically, but no more than one time per contract year, update to reflect changes in the operations or procedures described in it. Updates of the Procedures Manual will be provided to Triple-S for review, comment and approval. |
| (e) | Supplier will perform the Services in accordance with the most recent Triple-S-approved version of the Procedures Manual. The Procedures Manual shall not be used to override this Agreement. If there is any conflict between the provisions of this Agreement and the Procedures Manual, the provisions of this Agreement will control. |
| (f) | Any Triple-S Data or Triple-S Confidential Information that is incorporated into the Procedures Manual shall continue to be the property of Triple-S. Any Supplier Confidential Information that is incorporated into the Procedures Manual shall continue to be the property of Supplier. |
| (g) | Triple-S and its Affiliates may retain and Use the Procedures Manual in their businesses and for their benefit both during the Term and the Disengagement Assistance Period and following the expiration or termination of this Agreement (or portion thereof) for any reason. Subject to appropriate non-disclosure agreements for the limited purpose of protecting any Confidential Information or Independent IP of Supplier incorporated into the Procedures Manual, Triple-S and its Affiliates may permit any of their other service providers to use the Procedures Manual during and after the Term, but solely in connection with their provision of services for Triple-S and its Affiliates. |
| 18.4 | Change Control Process |
| (a) | Except as otherwise expressly provided in this Agreement, Triple-S has retained responsibility for establishing the standards and strategic direction of Triple-S (and its Affiliates) with respect to information technology outsourcing. |
| (b) | Supplier will not make any Changes, except in accordance with the Change Control Process and with Triple-S’s prior written approval (which Triple-S may grant or withhold in its discretion). Supplier shall not implement, and shall not be obligated to implement, any proposed Change for which Triple-S has not provided its prior written consent. |
| (c) | In exercising its discretion in determining whether to grant its approval to a Change, Triple-S may consider, among other things, whether implementation of the Change would adversely affect the functionality, performance or resource efficiency of the |
|
Triple-S / Supplier Confidential Page 57 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
Services, increase Triple-S’s internal costs or Supplier’s Charges to Triple-S under this Agreement or charges by other Triple-S suppliers to Triple-S, or if it would otherwise adversely affect Triple-S’s or its Affiliates’ business, operations or security.
| (d) | The Parties agree that a Change may or may not result in additional charges or in an adjustment to the charges. Supplier shall not be entitled to request an additional charge or an adjustment to the charges for a Change unless, and only to the extent, (i) such Change is a Material Change (defined in Schedule C (Charging Methodology), and (A) such Change (1) is not within the scope of the Services or Supplier’s Financial Responsibility under this Agreement, and (2) would increase Supplier’s costs to implement the Change or to deliver the Services in accordance with such Change; and (B) the additional charge requested by Supplier for such Change must be reasonably related to the net additional costs incurred by Supplier arising out of the Change (after taking into account any reductions to Supplier’s costs arising out of the Change). |
| (e) | With respect to any change in a Law, Other Compliance Obligation or Triple-S Policy (or any new Law, Other Compliance Obligation or Triple-S Policy) that either Party determines may require a potential Change to the Services: |
| (i) | The Parties will mutually discuss the potential Change to the Services, and based on such discussions, Supplier shall provide a proposed Change Order addressing such Change, to reflect how the Services would be modified to be in compliance with such changed or new Law, Other Compliance Obligation or Triple-S Policy (as applicable). |
| (ii) | With respect to any Change resulting from (x) a change in or a new Law or Other Compliance Obligation, or (y) a change in or a new Triple-S Policy (but only to the extent such change in or new Triple-S Policy was required in order to comply with an existing Law or Other Compliance Obligation or caused by a change in or a new Law or Other Compliance Obligation): |
| (A) | Supplier shall use Commercially Reasonable Efforts to implement the Change sufficiently in advance of the effective date of compliance with such changed or new Law or Other Compliance Obligation such that Triple-S has a reasonable amount of time to perform testing of any of Triple-S’s equipment, systems, processes or other items that may be impacted by such Change; and |
| (B) | Supplier shall have financial responsibility for any such Change, except (i) to the extent that Triple-S is financially responsible as expressly set forth in Schedule C (Charges); or (ii) as otherwise set forth in Schedule C (Charges) or Schedule K (Reports). |
| (f) | If an approved Change would result in New Services or a change in these General Terms and Conditions or any Schedule, the Change must be authorized via a Change Order or a contract amendment or modification made pursuant to Section 26.3 (Contract Amendments and Modifications). |
|
Triple-S / Supplier Confidential Page 58 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
| 18.5 | Audits and Records |
The rights and obligations of the Parties with respect to audits and record retention are set forth in Schedule M (Audit and Record Retention Requirements).
| 19. | REPRESENTATIONS, WARRANTIES AND COVENANTS |
| 19.1 | Work Standards |
Supplier represents, warrants and covenants that the Services will be rendered with promptness and diligence and be executed in a professional and workmanlike manner in accordance with the practices and standards observed by tier 1 providers of outsourcing services comparable to the Services. Supplier warrants and covenants that it will use adequate numbers of qualified Supplier Personnel with suitable training, education, experience and skill to perform the Services in accordance with timing and other requirements of this Agreement.
| 19.2 | Maintenance |
Supplier represents, warrants and covenants that it will: maintain the Equipment and Software so they operate in accordance with their specifications in all material respects, including: (a) maintaining Equipment in good operating condition, subject to normal wear and tear; (b) undertaking repairs and preventive maintenance on Equipment in accordance with the applicable Equipment manufacturer’s recommendations; and (c) performing Software maintenance in accordance with the applicable Software vendor’s documentation and recommendations (unless otherwise agreed by Triple-S).
| 19.3 | Efficiency and Cost-Effectiveness |
Supplier represents, warrants and covenants that it will use Commercially Reasonable Efforts to use efficiently the resources or services necessary to provide the Services. Supplier warrants and covenants that it will use Commercially Reasonable Efforts to perform the Services in the most cost-effective manner consistent with the required level of quality and performance.
| 19.4 | Deliverable Warranty |
| (a) | Supplier represents, warrants and covenants that each Deliverable produced by Supplier under this Agreement shall not, during the Warranty Period, deviate in any material respect from the Requirements and specifications for such Deliverable set forth in the applicable Statement of Work, or Task Order developed by the Parties pursuant to this Agreement. |
| (b) | If Triple-S notifies Supplier of a breach of the warranty set forth in Section 19.4(a) within the Warranty Period, Supplier will promptly correct and redeliver the affected Deliverable at no additional charge to Triple-S without delay. |
| (c) | “Warranty Period” shall mean the period of time commencing on the earlier to occur of (i) the date of delivery of such Deliverable to Triple-S, and (ii) use of such Deliverable to provide or receive the Services, and continuing for (A)[***]after the start of the |
|
Triple-S / Supplier Confidential Page 59 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
Warranty Period for Deliverables that are provided to Triple-S in such a manner that they are outside of Supplier’s control and support as part of the Services; and (B) the duration of the Term and all Disengagement Assistance Periods for all other Deliverables.
| (d) | Supplier’s obligations under this Section 19.4 do not in any way limit Supplier’s obligation to provide ongoing maintenance and support of the Deliverables as may be specified in a Statement of Work or Task Order. |
| 19.5 | Intentionally Omitted |
| 19.6 | Documentation |
Supplier represents, warrants and covenants that any Software Documentation developed for Triple-S by or on behalf of Supplier will, during the Software Documentation Warranty Period (a) accurately and with reasonable comprehensiveness describe the operation, functionality and use of the applicable Software in all material respects, and (b) accurately describe in terms understandable to a typical End User the material functions and features of the applicable Software and the procedures for exercising such functions and features. “Software Documentation Warranty Period” shall mean the period of time commencing on the date of acceptance of the Software Documentation and continuing until the later of (i) the expiration or termination of the Statement of Work or Task Order under which the Software Documentation was developed and (ii) the expiration or termination of any Disengagement Assistance Period for such Statement of Work or Task Order.
| 19.7 | Compatibility |
Supplier represents, warrants and covenants that any Deliverables and other components of the Services will be compatible and will properly inter-operate and work together in all material respects as components of an integrated system if one would reasonably anticipate that such compatibility and interoperability is necessary to use the Deliverable for its intended purpose.
| 19.8 | Open Source Code |
Supplier represents, warrants and covenants that Supplier shall not incorporate any Open Source Code into any Deliverable unless approved in writing by Triple-S in advance. “Open Source Code” means any Software that requires as a condition of its use, modification or distribution that it be disclosed or distributed in Source Code form or made available at no charge. Open Source Code includes software licensed under the GNU General Public License (GPL) or the GNU Lesser/Library GPL.
| 19.9 | Non-Infringement |
| (a) | Subject to Section 19.9(b), Supplier represents, warrants and covenants as follows: |
| (i) | that Supplier and Supplier Personnel will perform their responsibilities under this Agreement in a manner that does not infringe or constitute an infringement or misappropriation of any Intellectual Property Rights of any third party; |
|
Triple-S / Supplier Confidential Page 60 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
| (ii) | that Supplier has all rights and licenses necessary to convey to Triple-S (and to its Service Recipients, where applicable) the rights of ownership of (or access or license rights to, as applicable and as provided for in, and subject to, this Agreement), all Software, Work Product, Independent IP, Deliverables and other items used by Supplier to deliver the Services or provided by or on the behalf of Supplier pursuant to this Agreement; and |
| (iii) | that no Software, Work Product, Independent IP, Deliverable or other item used by Supplier to deliver the Services or provided by or on behalf of Supplier, nor their use by Triple-S, its Affiliates or other Service Recipients in accordance with this Agreement, will infringe or constitute an infringement or misappropriation of any Intellectual Property Right of any third party. |
| (b) | Supplier will not be considered in breach of the representation, warranty and covenant set forth in Section 19.9(a) to the extent (but only to the extent) any claimed infringement or misappropriation is attributable to any of the following: |
| (i) | A modification made by or on behalf of Triple-S, its Affiliates or any Service Recipient (excluding modifications made by or on behalf of Supplier, Supplier Personnel or any Affiliates of Supplier) of an item used or provided by or on behalf of Supplier unless the modification was recommended, authorized, approved, or made by Supplier; or |
| (ii) | The combination, operation or use of an item by or on behalf of Triple-S, its Affiliates or any Service Recipient (excluding the combination, operation or use by or on behalf of Supplier or Supplier Personnel or any Affiliates of Supplier) used or provided by or on behalf of Supplier with other specific items not furnished by, through or at the specification of Supplier or its Subcontractors; provided, however, that this exception will not be deemed to apply to the combination, operation or use of an item with other commercially available products that could reasonably have been anticipated to be used in combination with the item used or provided by or on behalf of Supplier (e.g., the combination, operation or use of Application Software provided by Supplier with a commercially available computer and operating systems (such as Windows) not provided by Supplier); or |
| (iii) | Developments or modifications made by Supplier in compliance with specific, designs or instructions used or provided by or on behalf of Triple-S, its Affiliates or any Service Recipient, where compliance with such designs or instructions necessarily caused such infringement or misappropriation. |
| 19.10 | Viruses Impacting Triple-S |
| (a) | Supplier represents, warrants and covenants that Supplier Personnel will not knowingly introduce a Virus or knowingly allow a Virus to be introduced into Triple-S’s or any other Service Recipient’s system or any system used to provide the Services. |
|
Triple-S / Supplier Confidential Page 61 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
| (b) | Supplier covenants that it will use Commercially Reasonable Efforts to prevent Supplier Personnel from unknowingly introducing a Virus or allowing a Virus to be introduced into Triple-S’s or any other Service Recipient’s system or any system used to provide the Services. |
| (c) | If a Virus is found to have been introduced into Triple-S’s or other Service Recipients’ systems or the systems used to provide the Services as a result of Supplier’s breach of the foregoing representation, warranty and covenants, Supplier will use Commercially Reasonable Efforts at no additional charge to assist Triple-S in eradicating the Virus and reversing its effects and, if the Virus causes a loss of data or operational efficiency, to assist Triple-S in mitigating and reversing such losses. |
| 19.11 | Disabling Code |
| (a) | Supplier represents, warrants and covenants that in the course of providing the Services it will not knowingly insert into Software or any systems used to provide the Services any code, timer, clock or other design or routine that may cause any Software or data used by it to be erased, become inoperable or inaccessible or accessible by any party other than Triple-S, or any code that would have the effect of disabling or otherwise shutting down all or any portion of the Services (each a “Disabling Device”) without Triple-S’s prior written consent or except for any lockout or similar devices used for the purpose of managing Software or data compliance. |
| (b) | With respect to any Disabling Device that was already part of Software or systems used to provide the Services, Supplier represents, warrants and covenants that it will not at any time without Triple-S’s prior written consent, knowingly invoke such Disabling Device or knowingly permit it to be invoked. |
| (c) | Supplier represents, warrants and covenants that Supplier will not, and will not permit any other party to, invoke Disabling Device at any time without Triple-S’s prior written consent. |
| (d) | For purposes of this Section, programming errors by Supplier or a third party will not be deemed a Disabling Device to the extent Supplier or the third party can demonstrate that such errors were not made with the intention of disabling or otherwise shutting down all or any portion of Triple-S’s or any other Service Recipient’s systems or any system used to provide the Services or causing any of the other negative effects described in Section 19.11(a). |
| 19.12 | Delivery Platforms |
Supplier represents, warrants, and covenants that the Software and Tools identified in Schedule S (Supplier Software and Supplier Tools), at the time such lists are produced, shall constitute, in all material respects, all of the hardware, Software and Tools that comprises or is necessary to operate an instance of the platforms used by Supplier to provide the Services as it is then configured, operated, and used by or for Supplier to perform and deliver services under the Agreement.
|
Triple-S / Supplier Confidential Page 62 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
| 19.13 | Corporate Social Responsibility |
Supplier represents, warrants and covenants to Triple-S that Supplier and Supplier Facilities comply, and during the Term and the Disengagement Assistance Period will comply, with the following:
| (a) | Supplier will not use forced or compulsory labor in any form, including prison, indentured, political, bonded or otherwise. |
| (b) | Supplier will not follow policies promoting or resulting in unacceptable worker treatment such as the exploitation of children, physical punishment, female abuse, involuntary servitude, or other forms of abuse. |
| (c) | Supplier will not discriminate based on race, creed, gender, marital or maternity status, class or caste status, religious or political beliefs, age or sexual orientation. Supplier’s decisions related to hiring, salary, benefits, advancement, termination or retirement will be based solely on the ability of an individual to do the job, Supplier’s business and technical requirements, and those of Supplier’s customers. |
| (d) | Supplier’s management practices will recognize the dignity of the individual employee and the right to a work place free of harassment, abuse or corporal punishment, and will respect Supplier’s employees’ voluntary freedom of association. |
| (e) | Supplier will comply with all applicable Laws concerning the conditions of employment of its employees, including those relating to pay, benefits, and working conditions. |
| (f) | Supplier will maintain on file documentation reasonably necessary to demonstrate compliance with this Section 19.13 (Corporate Social Responsibility) and shall make these documents available for Triple-S and its auditors in accordance with Schedule M (Audit and Record Retention Requirements). Supplier will publicize to its employees and enforce a non-retaliation policy that permits Supplier’s employees to speak with Triple-S and Triple-S’s auditors without fear of retaliation by Supplier’s management. |
| 19.14 | Foreign Corrupt Practices Act |
| (a) | Supplier represents, warrants and covenants that it has not and will not offer, pay, promise to pay, or authorize the payment of any money, or offer, give, promise to give, or authorize the giving of anything of value to a Territory official (as defined in the Foreign Corrupt Practices Act (P.L. 95-213), as amended), to any Territory political party or official thereof or any candidate for Territory political office, or to any person, while knowing or being aware of a high probability that all or a portion of such money or thing of value will be offered, given or promised, directly or indirectly, to any Territory official, to any Territory political party or official thereof, or to any candidate for Territory political office, for the purposes of: |
| (i) | influencing any act or decision of such Territory official, political party, party official, or candidate in his or its official capacity, including a decision to fail to perform his or its official functions; or |
|
Triple-S / Supplier Confidential Page 63 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
| (ii) | inducing such Territory official, political party, party official, or candidate to use his or its influence with the Territory government or instrumentality thereof to affect or influence any act or decision of such government or instrumentality, in order to assist Triple-S or Supplier in obtaining or retaining business for or with, or directing business to Triple-S or Supplier. |
| (b) | Supplier further represents, warrants and covenants that it will not violate the Foreign Corrupt Practices Act or any other applicable anti-corruption laws or regulations. Supplier agrees that if subsequent developments after the Effective Date cause the representations, warranties, covenants and information reported in this Section 19.14 to be no longer accurate or complete, Supplier will immediately furnish Triple-S with a supplementary report detailing such change in circumstances, and will provide updates to Triple-S on the status of such matters. |
| 19.15 | Debarment from Federal Contracts and Termination. |
| (a) | Supplier represents, warrants and covenants that: (i) Supplier and its Affiliates and Subcontractor(s), and its or their employees, agents or representatives, are not subject to any active administrative agreement pertaining to its eligibility for the award of government contracts; (ii) Supplier and its Affiliates and Subcontractor(s), and its or their employees, agents or representatives, have not had any communications with any suspending or debarring official of any governmental entity regarding its eligibility for the award of government contracts; (iii) neither Supplier nor its Affiliates and Subcontractor(s), and its or their employees, agents or representatives, have been debarred, suspended, or similarly disqualified from participation in the award of contracts with the United States Government or any other governmental entity; nor (iv) are there facts or circumstances that would warrant the institution of suspension, debarment, or other disqualification proceedings or the finding of non-responsibility or ineligibility as defined by 48 C.F.R. 2.101, on the part of Supplier or any Affiliate or Subcontractor(s), and its or their employees, agents or representatives. |
| (b) | Supplier represents, warrants and covenants that Supplier shall not employ or contract with, for any aspect of its business that involves government contracts, any individual or entity convicted with a criminal offense involving government business, listed by a federal agency as debarred, or which is suspended or otherwise excluded from federal program participation. Supplier represents that Supplier and its Affiliates and Subcontractor(s), and its or their employees, agents or representatives, do not, fit within any of these categories as of the Effective Date. |
| (c) | Supplier agrees to inform Triple-S promptly if at any time during the effective period of this Agreement if Supplier or any of its employees or Subcontractors becomes so convicted, listed, suspended or excluded. Supplier also agrees not to assign any individual to perform work under this Agreement, insofar as it may involve government contracts, who is so convicted, listed, suspended or excluded, and shall perform screenings of all employees and Subcontractors performing Services under the Agreement against the list of parties excluded from federal contracting available on the System for Award Management, ▇▇▇.▇▇▇, to identify any employees or Subcontractors that have been suspended, excluded or otherwise sanctioned by the federal government. |
|
Triple-S / Supplier Confidential Page 64 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
| 19.16 | Claims Procedures, Appeals and External Review |
Supplier shall ensure that its decisions regarding hiring, compensation, termination, promotion, or other similar matters with respect to Supplier Personnel (such as a claims adjudicator, appeals processor, or medical expert) shall not be made based upon the likelihood or perceived likelihood that the individual will support or tend to support the denial of benefits for Triple-S members and/or customers.
| 19.17 | No Improper Inducements |
Supplier represents, warrants, and covenants to Triple-S that it has not violated any applicable laws or regulations or any Triple-S policies of which Supplier has been given notice in writing, regarding the offering of unlawful or improper inducements in connection with this Agreement.
| 19.18 | Immigration |
Supplier represents, warrants, and covenants to Triple-S that it has not violated and shall comply with any applicable Laws relating to H-1B Visa program and other similar immigration and labor Laws. Supplier shall use best efforts to ensure that Triple-S is not drawn into any investigations or proceedings regarding the immigration status of Supplier Personnel.
| 19.19 | [***] Software |
| (a) | Supplier represents, warrants, and covenants to Triple-S that as of the Effective Date Supplier has executed an agreement with [***] (“[***]”) authorizing Supplier to access the [***] and related software licensed by Triple-S from [***] (“[***] Software”) as necessary to provide the Services (as they exist on the Effective Date) throughout the Term of this Agreement (“[***]/Supplier Agreement”). Supplier shall not terminate the [***]/Supplier Agreement without consulting Triple-S in advance and obtaining Triple-S’ written approval of an alternate solution reasonably acceptable to Triple-S with which Supplier would continue providing the Services. |
| (b) | If Supplier receives any notice from [***] or becomes aware of other circumstance that could lead to [***] terminating the [***]/Supplier Agreement or Supplier otherwise not having the rights it requires to access the [***] Software as necessary to provide the Services (such rights, [***] Access Rights), Supplier shall promptly notify Triple-S of the circumstance and provide periodic updates until the circumstances are resolved. |
| (c) | If Supplier receives a notice of termination of the [***] Access Rights, or otherwise loses or expects to lose the [***] Access Rights, Supplier shall promptly notify Triple-S. Upon receipt of such notice, Triple-S at its option may (i) terminate this Agreement without payment of a termination charge or other liability; or (ii) terminate the portion of the Services that require [***] Access Rights without payment of a termination charge or other liability and Supplier shall work in good faith with Triple-S to equitably adjust the Charges to reflect the remaining Services Supplier will provide. |
| (d) | Except as expressly permitted under the [***]/Supplier Agreement: |
|
Triple-S / Supplier Confidential Page 65 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
| (i) | Supplier shall not host, access or operate the [***] Software, or access any [***] Confidential Information (defined below). |
| (ii) | Supplier shall not request from any In-Scope Employee, and shall instruct such In-Scope Employees not to provide, any access to the [***] Software or to any related documentation, information, data drawings, benchmark tests, specifications, trade secrets, copies of [***] Software code, or other proprietary information marked as confidential information of [***] or its Affiliates (collectively “[***] Confidential Information”). |
| (iii) | Supplier shall develop and maintain written policies, procedures and controls designated to ensure compliance with the terms above in this Section 19.19(d), and shall provide copies to Triple-S upon request. |
| (iv) | If Supplier does obtain access to any [***] Confidential Information other than as permitted under the [***]/Supplier Agreement, Supplier shall promptly (A) notify Triple-S; and (B) take appropriate actions to eliminate such access and prevent such access from occurring again in the future. |
| 19.20 | Non-Infringement |
| (a) | Subject to Section 19.20(b), Triple-S represents, warrants and covenants as follows: |
| (i) | that Triple-S, Triple-S Affiliates and Service Recipients will perform their responsibilities under this Agreement in a manner that does not infringe or constitute an infringement or misappropriation of any Intellectual Property Rights of any third party; |
| (ii) | that Triple-S has all rights and licenses necessary to convey to Supplier (and to its Supplier Personnel and Subcontractors, where applicable) the rights to use (or license rights to, as applicable), all Software, Equipment, Independent IP, Tools and other items provided by or on the behalf of Triple-S pursuant to this Agreement; and |
| (iii) | that no Software, Equipment, Independent IP, Tool or other item provided by or on behalf of Triple-S, nor their use by Supplier, its Affiliates, Supplier Personnel or Subcontractors in accordance with this Agreement, will infringe or constitute an infringement or misappropriation of any Intellectual Property Right of any third party. |
| (b) | Triple-S will not be considered in breach of the representation, warranty and covenant set forth in Section 19.20(a) to the extent (but only to the extent) any claimed infringement or misappropriation is attributable to any of the following: |
| (i) | A modification made by or on behalf of Supplier or its Affiliates (excluding modifications made by or on behalf of Triple-S, Service Recipients or any Affiliates of Triple-S) of an item provided by or on behalf of Triple-S unless the modification was recommended, authorized, approved, or made by Triple-S; or |
|
Triple-S / Supplier Confidential Page 66 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
| (ii) | The combination, operation or use of an item by or on behalf of Supplier or its Affiliates (excluding the combination, operation or use by or on behalf of Triple-S or Service Recipients or any Affiliates of Triple-S) provided by or on behalf of Triple-S with other specific items not furnished by, through or at the specification of Triple-S or a Service Recipient; provided, however, that this exception will not be deemed to apply to the combination, operation or use of an item with other commercially available products that could reasonably have been anticipated to be used in combination with the item provided by or on behalf of Triple-S (e.g., the combination, operation or use of Application Software provided by Triple-S with a commercially available computer and operating systems (such as Windows) not provided by Triple-S); or |
| (iii) | Developments or modifications made by Triple-S in compliance with specific designs or instructions provided by or on behalf of Supplier, where compliance with such designs or instructions necessarily and unavoidably caused such infringement or misappropriation. |
| 19.21 | Viruses Impacting Supplier |
| (a) | Triple-S represents, warrants and covenants that Service Recipients will not knowingly introduce a Virus or knowingly allow a Virus to be introduced into Supplier’s, any Supplier Personnel’s or any Subcontractor’s system or any system used to provide the Services. |
| (b) | Triple-S covenants that it will use Commercially Reasonable Efforts to prevent Service Recipients from unknowingly introducing a Virus or allowing a Virus to be introduced into Supplier’s, any Supplier Personnel’s or any Subcontractor’s system or any system used to provide the Services. |
| (c) | If a Virus is found to have been introduced into Supplier’s, Supplier Personnel’s or any Subcontractor’s systems or the systems used to provide the Services as a result of Triple-S’s breach of the foregoing representation, warranty and covenants, Triple-S will use Commercially Reasonable Efforts at no additional charge to assist Supplier in eradicating the Virus and reversing its effects and, if the Virus causes a loss of data or operational efficiency, to assist Supplier in mitigating and reversing such losses. |
| 20. | MUTUAL REPRESENTATIONS AND WARRANTIES; DISCLAIMER |
| 20.1 | Mutual Representations and Warranties |
Each Party represents, warrants and covenants to the other that:
| (a) | It has the requisite corporate power and authority to enter into this Agreement and to carry out the transactions and activities contemplated by this Agreement; |
| (b) | The execution, delivery and performance of this Agreement and the consummation of the transactions contemplated by this Agreement have been duly authorized by the requisite |
|
Triple-S / Supplier Confidential Page 67 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
corporate action on the part of such Party, are a valid and binding obligation of such Party, and do not constitute a violation of any existing judgment, order or decree;
| (c) | The execution, delivery and performance of this Agreement and the consummation of the transactions contemplated by this Agreement do not constitute a material default under any existing material contract by which it or any of its material assets is bound, or an event that would, with notice or lapse of time or both, constitute such a default; and |
| (d) | There is no proceeding pending or, to the knowledge of the Party, threatened that challenges or could reasonably be expected to have a material adverse effect on this Agreement or the ability of the Party to perform and fulfill its obligations under this Agreement. |
| 20.2 | Disclaimer |
OTHER THAN AS PROVIDED IN THIS AGREEMENT, THERE ARE NO EXPRESS WARRANTIES AND THERE ARE NO IMPLIED WARRANTIES, STATUTORY OR OTHERWISE, INCLUDING THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR USE OR PURPOSE, EXCEPT AS MAY BE REQUIRED BY LAW. FURTHER, SUPPLIER MAKES NO REPRESENTATIONS AND WARRANTIES WITH RESPECT TO MANAGED THIRD PARTIES OR ANY ITEMS OR SERVICES PROVIDED BY MANAGED THIRD PARTIES.
| 21. | CONFIDENTIALITY |
| 21.1 | “Confidential Information” Defined |
| (a) | “Confidential Information” of a Party means any non-public information (or materials) belonging to, concerning or in the possession or control of the Party or any of its Affiliates (the “Furnishing Party”) that is furnished, disclosed or otherwise made available (directly or indirectly) to the other Party (the “Receiving Party”) (or entities or persons acting on the other Party’s behalf) in connection with this Agreement and which is either marked or identified in writing as confidential, proprietary, secret or with another designation sufficient to give notice of its sensitive nature, or is of a type that a reasonable person would recognize it to be confidential. |
| (b) | In the case of Triple-S, “Confidential Information” includes the following, regardless of whether it is marked confidential or how it is marked: |
| (i) | information belonging to, concerning or in the possession or control of Triple-S, its Affiliates, Service Recipients or their respective members, customers, employees, providers, suppliers or contractors (other than information belonging to or concerning Supplier or its Affiliates) to which Supplier has access in Triple-S Facilities or Triple-S systems or through Supplier’s provision of the Services; |
| (ii) | business, technical and financial information of Triple-S, its Affiliates, Service Recipients or their respective members, customers, employees, providers, suppliers or contractors (including past, present and prospective business, current |
|
Triple-S / Supplier Confidential Page 68 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
and future products and services, finances, marketing plans and techniques, price lists);
| (iii) | Triple-S Work Product; |
| (iv) | Deliverables; |
| (v) | Triple-S Data, Triple-S Owned Software, Triple-S Licensed Software, Triple-S Tools, Triple-S Independent IP and systems access codes to such Triple-S Data and such Software and applicable Source Code and Documentation relating to the foregoing; |
| (vi) | information concerning Triple-S’s and/or its Affiliates’ and Service Recipient’s products, marketing strategies, financial affairs, members, customers, employees, providers, suppliers or contractors; |
| (vii) | Personally Identifiable Information, including PHI; and |
| (viii) | All data and information in any form derived from any of the foregoing. |
| (c) | In the case of Supplier, “Confidential Information” includes the following, regardless of whether it is marked confidential or how it is marked: |
| (i) | Business and technical information of Supplier, its Affiliates or Subcontractors (including past, present and prospective business, current and future products and services, marketing plans and techniques); |
| (ii) | cost, pricing, and financial information of Supplier, its Affiliates or Subcontractors; |
| (iii) | Supplier Owned Software, Supplier Licensed Software, Supplier Tools, Supplier Independent IP, Other Developed Items and systems access codes to such Software and applicable Source Code and Documentation relating to the foregoing; |
| (iv) | information about other customers of Supplier, its Affiliates, information about Subcontractors and information about employees of Supplier, its Affiliates and Subcontractors (including employee compensation, benefits, disciplinary records, performance records, and other similar data, regardless of whether or how it is marked); and |
| (v) | all data and information in any form derived from any of the foregoing. |
| (d) | Any notes, memoranda, compilations, derivative works, data files or other materials prepared by or on behalf of the Receiving Party that contain or otherwise reflect or refer to Confidential Information of the Furnishing Party will also be considered Confidential Information of the Furnishing Party. |
|
Triple-S / Supplier Confidential Page 69 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
| (e) | “Confidential Information” does not include any particular information (other than Personally Identifiable Information (including PHI)) that the Receiving Party can demonstrate: |
| (i) | was rightfully in the possession of, or was rightfully known by, the Receiving Party without an obligation to maintain its confidentiality prior to receipt from the Furnishing Party; |
| (ii) | was or has become generally known to the public other than as a result of breach of this Agreement or a wrongful disclosure by the Receiving Party or any of its agents; |
| (iii) | after disclosure to the Receiving Party, was received from a third party who, to the Receiving Party’s knowledge, had a lawful right to disclose such information to the Receiving Party without any obligation to restrict its further use or disclosure; or |
| (iv) | was independently developed by the Receiving Party without use of or reference to any Confidential Information of the Furnishing Party. |
| 21.2 | Obligations of Confidentiality |
| (a) | Each Party acknowledges that it may be furnished, receive or otherwise have access to Confidential Information of the other Party in connection with this Agreement. |
| (b) | The Receiving Party will not use or reproduce Confidential Information of the Furnishing Party except as reasonably required to accomplish the purposes and objectives of this Agreement. The Receiving Party will not disclose the Confidential Information of the Furnishing Party to any person, or appropriate it for the Receiving Party’s own use, or for any other person’s use or benefit, except as specifically permitted by this Agreement or approved in writing by the Furnishing Party. |
| (c) | The Receiving Party will keep the Confidential Information of the Furnishing Party confidential and secure, and will protect it from unauthorized use or disclosure by using at least the same degree of care as the Receiving Party employs to avoid unauthorized use or disclosure of its own Confidential Information, but in no event less than reasonable care. |
| (d) | As necessary to accomplish the purposes of this Agreement, the Receiving Party may disclose Confidential Information of the Furnishing Party to any employee, officer, director, contractor, Service Recipient, agent or representative of the Receiving Party who has a legitimate “need to know” the information in question solely to carry out the responsibilities of the Parties under this Agreement or the purposes and objectives of this Agreement and who is bound in writing to the Receiving Party to protect the confidentiality of the information in a manner at least as stringent as that required of the Receiving Party under this Agreement, and provided that if such party to which such Confidential Information is to be provided is a contractor of the Receiving Party, the requirements of Section 21.2(e) or (f) below (as applicable), shall also apply. The |
|
Triple-S / Supplier Confidential Page 70 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
Receiving Party may also disclose Confidential Information of the Furnishing Party to the Receiving Party’s auditors provided they are made aware of the Receiving Party’s obligations of confidentiality with respect to the Furnishing Party’s Confidential Information, and to the Receiving Party’s attorneys.
| (e) | Supplier may disclose Triple-S Confidential Information only to Approved Subcontractors who have agreed in writing to protect the confidentiality of such Confidential Information in a manner at least as stringent as that required of Supplier under this Agreement and pursuant to written terms requiring such Approved Subcontractors to only permit access to its employees who have a legitimate “need to know” such information in order to provide the subcontracted services approved pursuant to this Agreement. As between the Parties, Supplier shall: (i) cause Supplier Personnel to comply with the confidentiality provisions set forth in this Agreement, and (ii) be responsible for all acts and omissions of Supplier Personnel, Subcontractors and any third party to whom Supplier permits access to Triple-S Data or Triple-S Confidential Information (except to the extent such access is provided by Supplier to a third party (excluding Supplier Affiliates or Subcontractors) at Triple-S’s prior written request). As between the Parties, Triple-S shall: (A) cause Service Recipients to comply with the confidentiality provisions set forth in this Agreement, and (B) be responsible for all acts and omissions of Service Recipients and any third party to whom Triple-S permits access to Supplier Confidential Information (except to the extent such access is provided by Triple-S to a third party (excluding Triple-S Affiliates) at Supplier’s prior written request). |
| (f) | Triple-S may also provide Confidential Information of Supplier to third parties (including outsourcing suppliers and contractors that may replace Supplier under this Agreement) who have a legitimate “need to know” the Confidential Information in question in order to provide services to Triple-S, provided that any such third party is bound to Triple-S to use such Supplier Confidential Information for the sole purpose of providing services to Triple-S, and has agreed to confidentiality obligations at least as stringent to those set forth in this Agreement. |
| (g) | Triple-S and its Affiliates may also disclose Supplier Confidential Information, including this Agreement and the transactions contemplated by this Agreement, in any reports filed or required to be filed with any regulatory agency or body charged with the administration, oversight or enforcement of regulations applicable to any business conducted by Triple-S or any of its Affiliates. |
| (h) | If any unauthorized disclosure, loss of, or inability to account for any Confidential Information of the Furnishing Party occurs, the Receiving Party will promptly so notify the Furnishing Party and will cooperate with the Furnishing Party and take such actions as may be necessary or reasonably requested by the Furnishing Party to minimize the violation and any damage resulting from it. |
| 21.3 | No Implied Rights |
Each Party’s Confidential Information will remain the property of that Party. Nothing contained in this Section 21 (Confidentiality) will be construed as obligating a Party to disclose its
|
Triple-S / Supplier Confidential Page 71 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
Confidential Information to the other Party, or as granting to or conferring on a Party, expressly or by implication, any rights or license to the Confidential Information of the other Party. Any such obligation or grant will only be as provided by other provisions of this Agreement. A Party shall not possess or assert a lien or other similar right against the other Party’s Confidential Information. No Party’s Confidential Information shall be sold, assigned, leased or disposed of to third parties by the other Party or commercially exploited by the other Party.
| 21.4 | Compelled Disclosure |
If the Receiving Party becomes legally compelled to disclose any Confidential Information of the Furnishing Party in a manner not otherwise permitted by this Agreement, the Receiving Party will, to the extent possible, provide the Furnishing Party with prompt notice of the request so that the Furnishing Party may seek a protective order or other appropriate remedy. If a protective order or similar order is not obtained by the date by which the Receiving Party must comply with the request, the Receiving Party may furnish that portion of the Confidential Information that it determines it is legally required to furnish. The Receiving Party will exercise reasonable efforts to obtain assurances that confidential treatment will be accorded to the Confidential Information so disclosed.
| 21.5 | Confidential Treatment of this Agreement |
Each Party may disclose the existence and general nature of this Agreement as permitted by Section 27.6 (Public Disclosures), but otherwise the terms and conditions of this Agreement will be considered the Confidential Information of each Party; provided however, that this Agreement may be disclosed in its entirety by either Party in connection with an actual or good-faith proposed merger, acquisition, or similar transaction or in connection with due diligence conducted for a securities offering, so long as such receiving entity (unless such party is legal counsel to the counterparty in such transaction) first agrees in writing to obligations substantially similar to those described in this Section 21 (Confidentiality); and provided further that Triple-S may disclose in one or more of its filings with the Securities and Exchange Commission such terms of this Agreement as it believes in good faith to be necessary to ensure that its filings under the Securities Exchange Act of 1934, taken as a whole, do not omit to state a material fact necessary in order to make the statements made in the light of the circumstances under which they were made, not misleading. Furthermore, to the extent Triple-S is required, or elects, to file this Agreement (or any portion thereof) with the Securities and Exchange Commission, Triple-S will (i) provide Supplier with advance written notice prior to making such filing; (ii) take all actions reasonably required to request and obtain confidential treatment of commercially sensitive information contained in this Agreement from the Securities and Exchange Commission; and (iii) work in good faith with Supplier to identify for such purpose such commercially sensitive information
| 21.6 | Disclosure of Information Concerning Tax Treatment |
Notwithstanding anything to the contrary in this Section 21 (Confidentiality), each Party (and its Affiliates), and any person acting on their behalf, may disclose to any person or entity the “tax structure” and “tax treatment” (as such terms are defined in the U.S. Internal Revenue Code and regulations under it) of the transactions effected by this Agreement and any materials provided to that Party (or its Affiliates) describing or relating to such tax structure and tax treatment;
|
Triple-S / Supplier Confidential Page 72 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
provided, however, that this disclosure authorization will not be interpreted to permit disclosure of (a) any materials or portions of materials that are not related to the transaction’s tax structure or tax treatment, or (b) any materials or information that the Party (or its Affiliate(s)) must refrain from disclosing to comply with applicable securities Laws.
| 21.7 | Return or Destruction |
Except as may be otherwise provided in Schedule M (Audit and Record Retention Requirements):
| (a) | As requested by the Furnishing Party during the Term and the Disengagement Assistance Period, the Receiving Party will return or provide the Furnishing Party a copy of any designated Confidential Information of the Furnishing Party; |
| (b) | When Confidential Information of the Furnishing Party is no longer required for the Receiving Party’s performance under this Agreement, or in any event upon expiration or termination of this Agreement, the Receiving Party will return all materials in any medium that contain, refer to, or relate to Confidential Information of the Furnishing Party or, at the Furnishing Party’s election, destroy them (which, in the case of Triple-S Confidential Information, will be done in accordance with Section 21.8 (Destruction Obligations) below; |
| (c) | Except with respect to Triple-S Data, which must be returned or destroyed in accordance with Section 21.8 (Destruction Obligations) below, the Receiving Party may, however, keep (i) any Confidential Information of the Furnishing Party that the Receiving Party has a license to continue using, (ii) in the files of its legal department, for record purposes only, one copy of any Confidential Information of the Furnishing Party requested to be returned or destroyed, (iii) archival copies as may be necessary to comply with document retention laws and regulations applicable to such Party’s business operations; and (iv) any Confidential Information that is located in storage media as a result of routine back-up procedures so long as such media is subject to destruction in due course. |
| (d) | Additionally, a Party shall have no obligation to destroy any Confidential Information that is subject to a claim, dispute, lawsuit, or subpoena or in any other circumstances in which such Party reasonably believes that destruction of such Confidential Information would be unethical or unlawful; and |
| (e) | Within ten (10) days of any written request by the Furnishing Party, the Receiving Party will certify in writing signed by an officer of the corporation that it has returned or destroyed all copies of the Furnishing Party’s Confidential Information in the possession or control of the Receiving Party or any of its Affiliates, Subcontractors, or contractors, and if such Confidential Information is required to be destroyed pursuant to Section 21.8 (Destruction Obligations), that all Triple-S Data and other Triple-S Confidential Information has been permanently deleted from Supplier’s systems and all physical files and have been destroyed. The certification shall specify the method and/or tools used to delete the files. |
|
Triple-S / Supplier Confidential Page 73 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
With respect to any situation in which either Party is permitted to retain Confidential Information pursuant to this Section 21.7, it shall keep such information confidential and comply with the requirements of this Section 21.
| 21.8 | Destruction Obligations |
Subject to the last sentence of Section 21.7(c), Section 21.9 (Exceptions to Retention and Destruction Obligations) and Section 5 (Records Retention) of Schedule M (Audit and Record Retention Requirements), in circumstances where Supplier is permitted or directed to destroy Triple-S Data or any other Triple-S Confidential Information, Supplier will:
| (a) | “destroy” all electronic copies of such records in compliance with NIST Special Publication 800-88 (Guidelines for Media Sanitization), using method ‘clearing’ or more thorough; and |
| (b) | destroy all physical copies of such records (including originals, copies and reproductions of electronic copies) by cross-cut shredding, incineration, pulping, or pulverization. |
| 21.9 | Exceptions to Retention and Destruction Obligations |
Upon written notification by Triple-S, whether as a formal legal hold notification pursuant to a legal action against Triple-S, or as a preservation request by Triple-S for any other reason, Supplier will cease destruction, whether automated, scheduled, manual or ad-hoc, of record types specified by Triple-S, and Supplier will preserve specified record types until notified by Triple-S reasonably in advance that preservation is no longer necessary or until the records are handed over to Triple-S (whichever occurs first).
| 21.10 | Duration of Confidentiality Obligations |
The Receiving Party’s obligations under this Section 21 (Confidentiality) apply to Confidential Information of the Furnishing Party disclosed to the Receiving Party before or after the Effective Date and will continue during the Term and survive the expiration or termination of this Agreement as follows:
| (a) | The Receiving Party’s obligations under Section 21.7 (Return or Destruction) and Section 21.8 (Destruction Obligations) will continue in effect until fully performed; |
| (b) | As to any portion of the Furnishing Party’s Confidential Information that constitutes a trade secret under applicable Law, the obligations will continue for as long as the information continues to constitute a trade secret; |
| (c) | As to certain Confidential Information described in Schedule M (Audit and Record Retention Requirements), the obligations will survive for the duration of time set forth therein (e.g., Section 5 (Record Retention) of Schedule M); |
| (d) | As to all other Confidential Information of the Furnishing Party, the obligations will survive for ten (10) years after the Receiving Party’s fulfillment of its obligations under Section 21.7 (Return or Destruction) with respect to the Confidential Information in |
|
Triple-S / Supplier Confidential Page 74 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
question; and
| (e) | With respect to Personally Identifiable Information, the obligations shall survive indefinitely. |
| 22. | INSURANCE |
| 22.1 | General Terms |
Supplier represents that it has, as of the Effective Date, and agrees to maintain in force, throughout the Term and the Disengagement Assistance Period, at least the types and amounts of insurance coverage specified in this Section 22 (Insurance). Supplier will ensure that its Subcontractors obtain the insurance required in Section 22.2(a), and will use Commercially Reasonable Efforts to cause its Approved Subcontractors (other than Non-Key Subcontractors) to obtain reasonable insurance given the services performed by the Approved Subcontractor and where the applicable agreement with the Subcontractor is being entered into specifically for performance of the Services or is up for a negotiated renewal between the parties (i.e., excluding evergreen renewals).
| 22.2 | Types and amounts of coverage |
Supplier agrees that during the Term it will maintain in force, the following types and amounts of insurance:
| (a) | Employer’s Liability Insurance and Statutory Worker’s Compensation Insurance, including coverage for occupational injury, illness and disease, and other similar social insurance in accordance with the laws of the country, state or territory exercising jurisdiction over the employee with limits per employee, per accident and per disease of $1,000,000 or the minimum limit required by law, whichever limit is greater. |
| (b) | Commercial General Liability Insurance, including Products, Completed Operations, Premises Operations, Bodily Injury, Personal and Advertising Injury, Blanket Contractual Liability and Independent Contractors Liability to the extent covered by insurance, and Broad Form Property Damage liability coverages, on an occurrence basis, with a limit per occurrence of $1,000,000 and $2,000,000 in aggregate. Supplier agrees to maintain general liability coverage with the above referenced limits through a DIC/DIL policy for Services provided outside the United States. This coverage will include Triple-S and its Affiliates as additional insureds. |
| (c) | Property Insurance, including Extra Expense and Business Income coverage, for risks of physical loss of or damage to Triple-S buildings, business personal property or other property that is in the care, custody or control of Supplier pursuant to the Agreement that result from such physical loss or damage. Such insurance will have a limit adequate to cover risks on a replacement cost basis. This coverage will include Triple-S and its Affiliates as loss payees for all claims arising out of Triple-S buildings or property for which Supplier has an obligation to provide Property Insurance hereunder. |
|
Triple-S / Supplier Confidential Page 75 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
| (d) | Commercial Automobile Insurance covering use of all owned, non-owned and hired automobiles for bodily injury, property damage liability with a combined single limit per accident of $1,000,000 or similar amount in accordance with the laws of the country, state or territory exercising jurisdiction. This coverage will include Triple-S and its Affiliates as additional insureds. |
| (e) | Umbrella Liability Insurance written on a follow-form basis with a minimum limit of $10,000,000 per occurrence and in the aggregate, providing excess cover for the coverages provided in Sections 22.2(a), 22.2(b), and 22.2(d). |
| (f) | Commercial Crime Insurance, including coverage for employee dishonesty and computer fraud, for loss or damage arising out of or in connection with fraudulent or dishonest acts committed by the employees of Supplier, acting alone or in collusion with others, including Triple-S’s property and funds of others in their care, custody or control, with a limit per event of $10,000,000. This Policy will include forgery or alteration coverage, mysterious disappearance coverage, and coverage for theft of Triple-S or its Affiliates’ property on or off premise, and shall not include a requirement for arrest or conviction. Supplier will maintain a separate third party crime policy that will include Triple-S and its Affiliates as loss payees for all claims arising out of Supplier’s services under this Agreement. |
| (g) | Managed Care Errors and Omissions Insurance appropriate to the Supplier’s profession, covering liability for loss or damage due to an act, error, omission or negligence arising out of the scope of Services under this Agreement, with a limit per claim and annual aggregate of $30,000,000. |
| (h) | Professional Liability, Privacy Liability and Network Security Insurance with a limit per claim and annual aggregate of $30,000,000 covering Supplier’s legal liability for expenses incurred as a result of acts, errors and omissions in connection with performance of the Services under this Agreement. Such insurance shall, at a minimum, cover legal liability to others for: |
| (i) | data security breaches (including, without limitation, unauthorized access, use, loss or theft of Personally Identifiable Information or Triple-S Confidential Information); |
| (ii) | violation of Laws relating to the care, custody, control or use of Personally Identifiable Information or Triple-S Confidential Information or the privacy or security of such information; |
| (iii) | data damage, destruction, or corruption; |
| (iv) | any act, omission or failure to act that results in a failure of network security (including unauthorized access to, unauthorized use of, a denial of service attack by a third party against, or transmission of a Virus or other type of malicious code to Triple-S’s computer systems) or the security of any other information asset; |
|
Triple-S / Supplier Confidential Page 76 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
| (v) | Internet Media liability (slander, defamation, libel, invasion of privacy) or Intellectual property infringement (such as copyrights, trademarks, service marks and trade dress); |
| (vi) | Cyber Extortion; |
| (vii) | Business Interruption coverage with no more than twelve (12) hour waiting period post Network Security event; and |
| (viii) | Crisis Management expense coverage (including notification, call center, credit monitoring, identity theft repair, public relations and legal expenses). |
The insurance of this subsection (h) shall cover Supplier’s liability for expenses (including legal expenses) that Triple-S and/or its Affiliates incur as a result of any such actual or alleged event, including costs of defending, settling and paying judgments resulting from claims, costs of responding to regulatory or administrative investigations, regulatory fines, and costs of computer forensic analysis and investigation, notification of impacted individuals, public relations, call center services, fraud consulting services, credit monitoring and protection services, and identity restoration services. The foregoing insurance shall address all of the foregoing without limitation if caused by an employee of Supplier or an independent contractor working on behalf of Supplier in connection with the Agreement, and will provide coverage for wrongful acts, claims, and lawsuits anywhere in the world where legally permissible. Supplier will maintain the foregoing policy in force during the Term of the Agreement and for a period of three (3) years after the termination or expiration of this Agreement (either as a policy in force or extended reporting period).
| 22.3 | Terms of coverage |
| (a) | The insurance coverages described above, will be primary, and all coverage will be non-contributing with respect to any other insurance or self-insurance that may be maintained by Triple-S. Supplier will be responsible for all deductibles and retentions with regard to such insurance. The General Liability, Auto Liability, Workers Compensation and Umbrella Liability coverages described above will include a waiver of subrogation. To the extent any of the coverages set forth in Section 22.2 is written on a claims-made basis, (i) such coverage shall have a retroactive date no later than the Effective Date; and (ii) such coverage shall continue for three (3) years after the termination or expiration of the Agreement, and if the policy is terminated, then it will allow for an extended reporting period of at least three (3) years. |
| (b) | Supplier will cause its insurance representatives to issue certificates of insurance evidencing that the coverages required under this Agreement are maintained in force. With the exception of any wholly owned captive, the insurers selected by Supplier will have an A.M. Best rating of A-, Financial Size Category (FSC) X or better, or, if such ratings are no longer available, with a comparable rating from a recognized insurance rating agency. Supplier shall provide Triple-S with at least thirty (30) days’ notice of any cancellation or material changes to any of the insurance coverages set forth in this Section 22 (Insurance). |
|
Triple-S / Supplier Confidential Page 77 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
| (c) | In the case of loss or damage or other event that requires notice or other action under the terms of any insurance coverage described above, Supplier will be solely responsible for taking such action. Supplier will use Commercially Reasonable Efforts to notify Triple-S of any claim submitted to Supplier’s insurers regarding a loss, damage or other event resulting from the Services. |
| (d) | The Parties do not intend to shift all risk of loss to insurance. Supplier’s obligation to maintain insurance coverage in specified amounts will not act as a limitation on any other liability or obligation which Supplier would otherwise have under this Agreement. Similarly, the including of Triple-S and its Affiliates as additional insureds is not intended to be a limitation of Supplier’s liability under this Agreement and will in no event be deemed to, or serve to, limit Supplier’s liability to Triple-S to available insurance coverage or to the policy limits specified in this Section 22, nor to limit Triple-S’s rights to exercise any and all remedies available to Triple-S under this Agreement, at law or in equity. |
| 23. | INDEMNIFICATION |
| 23.1 | Indemnification by Supplier |
Supplier will at its expense indemnify, defend and hold harmless Triple-S and its Affiliates, and their respective officers, directors, employees, customers, agents, representatives, successors and assigns (collectively, “Triple-S Indemnitees”) from and against any and all Losses suffered or incurred by any of them arising from, in connection with, or based on any of the following, whenever made:
| (a) | Hiring Process. Any Claim by, on behalf of or relating to any individual arising out of Supplier’s employee selection, communications, recruitment or hiring process, excluding Claims for which Triple-S is required to indemnify under Section 23.3; |
| (b) | Subcontractor Claims. Any Claim by Subcontractors arising out of Supplier’s breach or violation of Supplier’s subcontracting arrangements; |
| (c) | Supplier Personnel Claims. Any Claim by a Subcontractor or by other Supplier Personnel that Triple-S is liable to such personnel for employee benefits or as the employer or joint employer of such personnel; but excluding claims for which Triple-S is required to indemnify under Section 23.3(a) or Schedule G (Form of In-Scope Employee Agreement). |
| (d) | Confidentiality, Data Security and HIPAA. Any Claim arising out of an alleged breach of Supplier’s obligations under (i) Section 14 (Data Security and Protection); (ii) Section 21 (Confidentiality); or (iii) Schedule H (Business Associate Agreement); |
| (e) | Security Breach. Any Claim arising out of a Security Breach; |
| (f) | Infringement. Any Claim arising out of an alleged breach of Section 19.9(a) (Non-Infringement), but subject in all respects to Section 19.9(b) (Non-Infringement); |
| (g) | Compliance. Any Claim relating to: |
|
Triple-S / Supplier Confidential Page 78 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
| (i) | an alleged breach of Supplier’s obligations under Section 13 (Compliance with Laws); or |
| (ii) | an alleged breach of Supplier’s obligations under this Agreement, or Supplier’s negligence or willful misconduct, to the extent such breach, negligence or willful misconduct results in (A) assessment of a Regulatory or Contract Assessment; or (B) Triple-S not complying with any applicable Law or Other Compliance Obligation. |
| (h) | Bodily Injury and Property Damage. Any Claim for death or bodily injury, or the damage, loss, loss of use or destruction of real or tangible personal property of any third party (including employees of Triple-S or Supplier or their respective subcontractors) brought against a Triple-S Indemnitee alleged to have been caused by the negligence or willful misconduct of Supplier, Supplier Personnel or anyone else for whose acts Supplier is responsible; |
| (i) | Transferred Third Party Contracts. Supplier’s failure to observe or perform any duties or obligations to be observed or performed after the date of assignment or transfer to Supplier under any of the TSS Transferred Contracts that are assigned or otherwise transferred to Supplier under this Agreement by Triple-S. |
| (j) | Retained Third Party Equipment, Software and Third Party Service Contracts. Any Claim arising out of Supplier’s use of any Triple-S Leased Equipment, Triple-S Licensed Software or services under any Triple-S Third Party Services Contracts made available by Triple-S to Supplier or Supplier’s Subcontractors to the extent the Claim results from a breach by Supplier or Supplier Subcontractors of, or an act or omission of Supplier which creates liability for Triple-S relating to, (i) the applicable third party Software license agreement, lease agreement or Triple-S Third Party Services Contract, or certain provisions thereof, all of the foregoing that have been provided to Supplier in writing, including obligations to comply with the requirements regarding members and types of licenses under any such agreement, (ii) the [***]/Optum Agreement; (iii) Supplier’s obligations with respect to Managed Third Party Contracts as set forth in this Agreement, or (iv) any other reasonable restrictions required by Triple-S relating to Triple-S Leased Equipment, Triple-S Licensed Software or Triple-S Third Party Services Contracts, which restrictions are provided in writing to Supplier; |
| (k) | Cessation of Services. Any Claim arising out of Supplier’s (i) improper or wrongful termination of this Agreement, or (ii) abandonment of any Services in breach of this Agreement (including a failure to provide Disengagement Assistance as required by this Agreement); |
| (l) | Mutual Representations and Warranties. Any Claim arising out of any breach of any of Supplier’s representations or warranties set forth in Section 20.1 (Mutual Representations and Warranties); |
| (m) | Viruses. Any Claim arising out of any breach of any of Supplier’s representations, warranties or obligations under Section 19.10(a) (Viruses); |
|
Triple-S / Supplier Confidential Page 79 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
| (n) | Disabling Device. Any Claim arising out of any breach of any of Supplier’s obligations under Section 19.11 (Disabling Device); |
| (o) | CAP. Any Claim arising out of any breach of the CAP by Triple-S or its Affiliates to the extent it results from Supplier’s breach of this Agreement, negligence or willful misconduct; |
| (p) | Misconduct and Negligence. Any Claim arising out of any criminal misconduct, willful misconduct or negligence by Supplier; and |
| (q) | Insurance. Any Claim arising out of risks, losses, or damages Supplier is required to insure against under this Agreement, but only to the extent that such insurance would have provided defense and/or indemnity coverage for the insured loss but for Supplier’s failure to procure such insurance. |
Any act or omission of a Subcontractor or In-Scope Employee shall be deemed to be an act or omission of Supplier for purposes of determining Supplier’s indemnification obligations pursuant to this Section 23.1.
| 23.2 | Infringement Claims |
If any item used by Supplier to provide the Services or which is provided by Supplier to Triple-S under this Agreement, including any Software, Work Product, Independent IP, Deliverables or Services (collectively, the “Indemnified Items”) becomes, or in Supplier’s reasonable opinion is likely to become, the subject of a Claim which is indemnifiable pursuant to Section 23.1(f) (Infringement), Supplier will, in addition to indemnifying Triple-S Indemnitees as provided in this Section 23 (Indemnification) and to the other rights Triple-S may have under this Agreement, and at law or equity, at Supplier’s expense: (a) promptly secure the right to continue using the Indemnified Item, or (b) if this cannot be accomplished with Commercially Reasonable Efforts, then at Supplier’s expense replace or modify the Indemnified Item to make it non-infringing or without misappropriation, while not materially degrading performance, functionality, or quality, increasing Triple-S costs, or materially disrupting Triple-S’s business operations, or (c) if neither of the foregoing can be accomplished by Supplier with Commercially Reasonable Efforts, and only in such event, then upon at least 180 days’ prior written notice to Triple-S, (i) with respect to Indemnified Items other than Deliverables, Supplier may remove the item from use in performing the Services, in which case Supplier’s Charges for the affected Services will be equitably adjusted to reflect such removal, and (ii) in the case of Deliverables, Supplier may recall the Deliverable and (if the Deliverable was subject to a specific Charge) shall refund to Triple-S Charges and fees paid by Triple-S for such Deliverable. If removal of the Indemnified Item from use in performing Services or recall of a Deliverable causes the loss or degradation of the Services or any portion of the Services that is material to Triple-S or has a material impact on Triple-S, such loss, degradation or material impact will constitute a material breach of this Agreement by Supplier in respect of which Triple-S may exercise its termination and other rights and remedies under this Agreement or at law or equity.
| 23.3 | Indemnification by Triple-S |
Triple-S will at its expense indemnify, defend and hold harmless Supplier and its Affiliates, and
|
Triple-S / Supplier Confidential Page 80 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
their respective officers, directors, employees, agents, representatives, successors and assigns (collectively, “Supplier Indemnitees”) from and against any and all Losses suffered or incurred by any of them arising from, in connection with or based on any of the following, whenever made:
| (a) | Former Triple-S Employees. Any Claim by, on behalf of or relating to any of the Former Triple-S Claims Employees (and/or by their collective bargaining representative and/or union, where applicable), with respect to matters arising out of the acts or omissions of Triple-S and/or any of its agents or representatives, and/or with respect to the employment relationship between these employees and Triple-S, the ending of such employment relationship, and the decision by Triple-S to outsource Claims processing, but excluding Claims for which Supplier is required to indemnify under Section 23.1. For purposes of this Section 23.3(a): (i) “Former Triple-S Claims Employees” means individuals who were employed by Triple-S to perform Claims processing or related services at any time between the Effective Date and the Employee Separation Date ; and (ii) “Employee Separation Date” means the date the employment relationship between a Former Triple-S Claims Employee and Triple-S ends. For clarification, the Former Triple-S Claims Employees do not include any personnel designated as “In-Scope Employees” under Schedule G (In-Scope Employee Agreement). |
| (b) | Confidentiality, Data Security and HIPAA. Any Claim arising out of an alleged breach of Triple-S’s obligations under (i) Section 21 (Confidentiality); or (ii) Schedule H (Business Associate Agreement); |
| (c) | Transferred Third Party Contracts. Triple-S’ failure to observe or perform any duties or obligations to be observed or performed prior to the date of assignment or transfer by Triple-S, under any of the TSS Transferred Contracts that are assigned or otherwise transferred to Supplier under this Agreement by Triple-S; |
| (d) | Infringement. Any Claim arising out of an alleged breach of Section 19.20(a) (Non-Infringement), but subject in all respects to Section 19.20(b) (Non-Infringement). |
| (e) | Compliance with Laws. Any Claim arising out of an alleged breach of Triple-S’s obligations under Section 13 (Compliance with Laws); |
| (f) | Bodily Injury and Property Damage. Any Claim for death or bodily injury, or the damage, loss, loss of use or destruction of real or tangible personal property of any third party (including employees of Triple-S or Supplier or their respective subcontractors) brought against a Supplier Indemnitee alleged to have been caused by the negligence or willful misconduct of Triple-S, Triple-S personnel or anyone else for whose acts Triple-S is responsible; |
| (g) | Misconduct and Negligence. Any Claim arising out of any criminal misconduct, willful misconduct or negligence by Triple-S or Triple-S employees; |
| (h) | Viruses. Any Indemnity Claim arising out of any breach of any of Triple-S’s obligations under Section 19.21(a) (Viruses); |
|
Triple-S / Supplier Confidential Page 81 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
| (i) | CAP. Any Claim arising out of any breach of the CAP, except to the extent it results from Supplier’s breach of Section 4.4(a) of this Agreement, negligence or willful misconduct; and |
| (j) | Mutual Representations and Warranties. Any Claim arising out of any breach of any of Triple-S’s representations or warranties set forth in Section 20.1 (Mutual Representations and Warranties). |
Any act or omission of a Service Recipient or any Triple-S contractor engaged to perform Triple-S responsibilities under this Agreement shall be deemed to be an act or omission of Triple-S for purposes of determining Triple-S’s indemnification obligations pursuant to this Section 23.3.
| 23.4 | Indemnification Procedures |
The following procedures will apply to Claims for which a Party seeks to be indemnified pursuant this Agreement:
| (a) | Notice. Promptly after an indemnitee receives notice of any Claim for which it will seek indemnification pursuant to this Agreement, the indemnitee will notify the indemnitor of the Claim in writing. No failure to so notify the indemnitor will abrogate or diminish the indemnitor’s obligations under this Section 23 (Indemnification) if the indemnitor has or receives knowledge of the Claim by other means or if the failure to notify does not materially prejudice its ability to defend the Claim. Within fifteen (15) days after receiving an indemnitee’s notice of a Claim, the indemnitor will notify the indemnitee in writing (a “Notice of Election”) as to whether: |
| (i) | the indemnitor acknowledges its indemnification obligation to indemnify and hold harmless the indemnitee with respect to such Claim; and |
| (ii) | the indemnitor elects to assume control of the defense and settlement of such Claim. |
In addition, the indemnitor shall provide the Notice of Election no later than fifteen (15) days before the date on which any response to the complaint or Claim is due.
| (b) | Procedure Following Notice of Election. |
| (i) | Procedure for Non-Governmental Claims. |
With respect to any Claim that is not a Governmental Claim, if the indemnitor timely delivers a Notice of Election to the address set forth in Section 27.3 (Notices) that both (x) acknowledges indemnitor’s obligation to indemnify and hold the indemnitee harmless with respect to such Claim, and (y) includes an express election to assume control of the defense and settlement of such Claim, then:
| (A) | the indemnitor will be entitled to have sole control over the defense and settlement of such Claim, provided that the indemnitee shall be entitled |
|
Triple-S / Supplier Confidential Page 82 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
to participate in the defense of such Claim on a monitoring, non-controlling basis and to employ counsel at its own expense to assist in the handling of such Claim;
| (B) | the indemnitor will not be liable to the indemnitee for any legal expenses incurred by the indemnitee in defending or settling the Claim incurred after the date that indemnitee receives such indemnitor’s Notice of Election; |
| (C) | the indemnitor will not be required to reimburse the indemnitee for any amount paid or payable by the indemnitee in settlement of the Claim if the settlement was agreed to without the written consent of the indemnitor; and |
| (D) | the indemnitor shall not, without the prior written consent of the indemnitee, (1) consent to the entry of any judgment or enter into any settlement that provides for injunctive or other non-monetary relief affecting the indemnitee (or the Indemnitees of the indemnitee), nor (2) consent to the entry of any judgment or enter into any settlement unless such judgment or settlement provides for the unconditional and full release of the indemnitee (and the Indemnitees of the indemnitee) in respect of such Claim and does not diminish the indemnitee’s rights under this Agreement or result in additional fees, charges or costs to the indemnitee. |
| (ii) | Procedure for Governmental Claims. |
| (A) | A “Governmental Claim” means a Claim made against a Party (or an Indemnitee of such Party) by a regulator, federal or state Attorney General or other governmental entity with respect to which such Party elects to retain control of the defense and settlement of such Claim in its notice to the other Party pursuant to Section 23.4(a) above and for which such Party indicates in such notice that it will seek indemnification from the other Party pursuant to this Agreement. |
| (B) | With respect to any Governmental Claim, if the indemnitor timely delivers a Notice of Election to the address set forth in Section 27.3 (Notices) acknowledging its obligation to indemnify and hold harmless the indemnitee with respect to such Claim, then the indemnitee will be entitled to have sole control over the defense and settlement of such Claim at the cost and expense of the indemnitor, subject to Section 23.4(b)(ii)(B)(4) below, which amount shall include payment of any settlement, judgment or award in the cost of defending or settling such Claim; provided that: |
| (1) | the indemnitee will (i) keep the indemnitor informed about the status of the proceedings with the entity that made the Governmental Claim (including providing copies of documents |
|
Triple-S / Supplier Confidential Page 83 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
received by the indemnitee from such governmental entity and copies of documents provided by the indemnitee to such governmental entity), (ii) allow the indemnitor to participate in settlement discussions with the applicable governmental entity unless such participation is prohibited (in which case Triple-S will use reasonable efforts to obtain written notice of such prohibition and the grounds for such prohibition from the government entity), (iii) consult with indemnitor and its counsel regarding the Government Claim on a regular basis regarding strategy and all significant case developments, and (iv) consider any input that the indemnitor provides regarding the defense or settlement of the Government Claim, provided that the indemnitee is not required to follow the advice or suggestions of the indemnitor or its counsel;
| (2) | the indemnitor shall be entitled to retain its own legal counsel, at its cost and expense, and participate fully and cooperatively in all respects with the indemnitee in such defense, including the investigation, litigation, settlement, and trial of such Claim and any appeal arising therefrom; |
| (3) | subject to Section 23.4(b)(ii)(B)(4), the indemnitor will promptly reimburse the indemnitee upon demand for all Losses suffered or incurred by the indemnitee as result of or in connection with such Claim; and |
| (4) | where the amount payable to settle a Government Claim is in excess of [***], the indemnitee shall obtain the indemnitor’s written consent to such amount in excess of [***]. Indemnitor’s consent shall not be unreasonably withheld (it being understood that the indemnitor is responsible for reimbursing the indemnitee for all reasonable amounts paid or payable by the indemnitee in its defense and settlement of such Claim, subject to any applicable limitations of liability provided in Section 24). “Reasonability” for purposes of this Section 23.4(b)(ii)(B)(4) shall be determined by taking into consideration all of the facts and circumstances relating to such Claim, including reputational risks to the indemnitee, the potential for the Claim to cause adverse impacts to the indemnitee’s business or operations, and cost incurred by the indemnitee as result of or in connection with such Claim. If indemnitor does not provide consent for amounts indemnitee incurs in its defense and settlement of such Claim in excess of [***], any disputes regarding the reasonability of indemnitor’s withholding consent (and subsequently indemnitor’s obligation to fund any such excess incurred by indemnitee) shall be settled pursuant to Section 23.4(b)(ii)(B)(5) below. |
|
Triple-S / Supplier Confidential Page 84 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
| (5) | in the event of a dispute between the Parties as to the reasonableness of the amount of any cost, expense, settlement, judgement or other financial liability that the indemnitee approves or otherwise incurs above [***] without obtaining indemnitor’s consent under Section 23.4(b)(ii)(B)(4), the Parties shall use the dispute process provided in Section 25 to resolve such dispute. |
| (c) | Procedure Where No Notice of Election Is Delivered. If the indemnitor does not deliver a timely (i.e., in accordance with Section 23.4(a)) Notice of Election for a Claim that both (i) acknowledges its indemnification obligation to indemnify and hold the indemnitee harmless with respect to such Claim, and (ii) in the case of a Claim that is not a Governmental Claim, includes an express election by the indemnitor to assume control of the defense and settlement of the Claim, then the indemnitee may defend and/or settle the Claim in such manner as it may deem reasonably appropriate, at the cost and expense of the indemnitor, including payment of any settlement, judgment or award and the costs of defending or settling the Claim. The indemnitor will promptly reimburse the indemnitee upon demand for (A) all Losses suffered or incurred by the indemnitee as a result of or in connection with the Claim; and (B) any reasonable attorneys fees and related expenses incurred to collect such Losses from the indemnitor. |
| (d) | Cooperation regarding Claims. The indemnitor and the indemnitee shall provide reasonable cooperation with one another in connection with the resolution of any Claim, provided that, if such cooperation was at the request of indemnitor, any costs incurred by the indemnitee in connection with such cooperation shall be borne by the indemnitor, and shall be promptly reimbursed by the indemnitor upon demand from the indemnitee. |
| 23.5 | Subrogation |
Upon fulfilling all of its obligations under this Section 23 (Indemnification) with respect to a Claim, including making payment in full of all amounts due pursuant to its indemnification obligations, the indemnitor will be subrogated to the rights of the indemnitee(s) with respect to that Claim.
| 24. | LIABILITY |
| 24.1 | General Intent |
Subject to the specific provisions of this Section 24 (Liability), it is the intent of the Parties that if a Party fails to perform its obligations in the manner required by this Agreement, that Party will be liable to the other Party for any actual damages suffered or incurred by the other Party as a result.
| 24.2 | Limitations of Liability |
| (a) | Consequential Damages. Except as provided in Section 24.3 (Exceptions to Limitations of Liability), in no event, whether in contract or in tort (including breach of warranty, |
|
Triple-S / Supplier Confidential Page 85 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
negligence and strict liability in tort or otherwise), will a Party be liable to the other Party under this Agreement for indirect, consequential, exemplary, punitive or special damages of any kind or nature whatsoever (including lost revenues, profits, savings or business), even if such Party has been advised of the possibility of such damages in advance.
| (b) | General Liability Cap. Except as provided in Section 24.3(a) (Exceptions to Limitations of Liability), each Party’s total liability to the other under this Agreement, whether in contract or in tort (including breach of warranty, negligence and strict liability in tort) will be limited, in the aggregate, to an amount equal to the greater of the following (the “General Liability Cap”): |
| (i) | $20,000,000.00; or |
| (ii) | the total Charges paid or payable by Triple-S to Supplier pursuant to this Agreement for proper performance of the Services for the twelve (12) months prior to the month in which the most recent event giving rise to liability occurred, provided that if the most recent event giving rise to liability occurs during the first [***] months after the Effective Date, the amount of this clause (ii) shall equal [***] times the result obtained by dividing the total Charges paid or payable by Triple-S to Supplier pursuant to this Agreement for proper performance of the Services from the Effective Date through the date on which such event occurred, by the number of months from the Effective Date through such date. |
| 24.3 | Exceptions to Limitations of Liability |
| (a) | Exceptions to Consequential Damages Exclusion and General Liability Cap. The limitations and exclusions of liability set forth in Sections 24.2(a) (Consequential Damages) and 24.2(b) (General Liability Cap) shall not apply to any of the following: |
| (i) | damages attributable to the gross negligence or intentional or criminal misconduct of a Party; |
| (ii) | Claims and Losses that are the subject of indemnification pursuant to Section 23 (Indemnification); |
| (iii) | Damages relating to a Security Breach; |
| (iv) | damages attributable to a Party’s breach of the Business Associate Agreement or a breach of its obligations under this Agreement with respect to Triple-S Data, Personally Identifiable Information, HIPAA or Confidential Information of the other Party; |
| (v) | damages attributable to the improper or wrongful termination of this Agreement or abandonment of any Services by Supplier in breach of this Agreement; |
| (vi) | damages arising from a Party’s breach of its obligations under this Agreement (including as set forth in Section 13) to comply with applicable Laws; |
|
Triple-S / Supplier Confidential Page 86 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
| (vii) | damages arising from Supplier’s breach of this Agreement, negligence, or willful misconduct, to the extent such breach, negligence, or willful misconduct results in Triple-S (A) incurring a Regulatory or Contract Assessment; or (B) Triple-S not complying with any applicable Law or Other Compliance Obligation; or |
| (viii) | amounts described in Section 12.2(c) (Transformation). |
| (b) | Stipulated Direct Damages. Without limiting (1) each Party’s responsibility for direct damages under this Agreement, and (2) each Party’s right to claim other direct damages, the Parties agree that the following shall be considered direct damages under this Agreement, notwithstanding anything set forth in Section 24.2 (Limitations of Liability) to the contrary: |
| (i) | Costs of recreating, restoring or reloading any of Triple-S’s information lost or damaged as a direct result of a failure by Supplier to perform the Services at all or in accordance with Supplier’s obligations under this Agreement. Such recreation, restoration and reloading costs shall include all reasonable activities and efforts that an IT group of a health insurance company may undertake to recreate, restore or reload such lost or damaged information, using efforts that are proportionate to the importance to Triple-S of the information to be recreated, restored or reloaded and the volume of such lost or damaged information; |
| (ii) | Identity-Related Costs incurred by Triple-S relating to any Security Breach; |
| (iii) | Costs of implementing a workaround with respect to a failure by Supplier to perform the Services at all or in accordance with Supplier’s obligations under this Agreement; |
| (iv) | Costs and expenses incurred by Triple-S to acquire and have performed substitute services conforming to this Agreement in place of any Services Supplier fails to provide at all or in accordance with Supplier’s obligations under this Agreement; or |
| (v) | Straight time, overtime, or related expenses reasonably incurred by Triple-S or its Affiliates, including wages and salaries of additional personnel, travel, expenses, telecommunication and similar charges, incurred due to the failure of Supplier to perform the Services at all or in accordance with Supplier’s obligations under this Agreement. |
Nothing in this Section 24.3(b) shall limit Supplier’s obligations or liability under Section 23 (Indemnification), including Section 23.1(d) (Confidentiality, Data Security and HIPAA), Section 23.1(e) (Security Breach), and Section 23.1(g) (Compliance with Laws), nor Triple-S’s right to claim damages for other items not set forth in this Section.
| (c) | Service Level Credits, milestone credits and transition-related reimbursements (including Critical Transition Milestones and Critical Milestones) described in this Agreement, as well as any other credits as may be agreed between the Parties for particular projects, shall not limit or otherwise reduce (i) the foregoing liability caps or (ii) any other rights |
|
Triple-S / Supplier Confidential Page 87 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
or remedies that Triple-S may have available to it under this Agreement, including termination rights and rights to recover damages; provided, however, that the amount of damages recoverable by Triple-S with respect to a failure for which credits are payable shall equal (A) the total amount of damages then recoverable under this Agreement and incurred by Triple-S with respect to such failure, without consideration of whether any credits resulting from such failure had been provided to Triple-S; less (B) any amounts received by Triple-S as credits that result from such failure.
| (d) | Each Party has a duty to mitigate the damages suffered by it for which the other Party is or may be liable. |
| (e) | The limitations specified in this Section 24 will survive and apply even if any limited remedy specified in this Agreement is found to have failed of its essential purpose. |
| 24.4 | Force Majeure |
| (a) | No Party will be liable for any default or delay in the performance of its obligations under this Agreement (i) if and to the extent such default or delay is caused, directly or indirectly (including any default or delay that affects a Subcontractor), by fire, flood, pestilence, earthquake, elements of nature or acts of God, riots, or civil disorders, and (ii) provided the non-performing Party is without fault in causing such default or delay, and such default or delay could not have been prevented by reasonable precautions and could not reasonably be circumvented by the non-performing Party through the use of alternate sources, workaround plans or other means (including with respect to Supplier by Supplier meeting its obligations for performing Disaster Recovery and business continuity services as described in this Agreement) (each such event a “Force Majeure Event”). For avoidance of doubt (A) failures of Subcontractors to perform a Supplier obligation under this Agreement will not be a Force Majeure Event for Supplier, and failure of Triple-S contractors to perform a Triple-S obligation under this Agreement shall not be a Force Majeure Event for Triple-S, unless the Subcontractor or contractor (as applicable) is precluded from performing due to an event that satisfies the requirements above with respect to such Subcontractor or contractor, and (B) strikes or other labor unrest involving the non-performing Party’s own workers shall not constitute a Force Majeure Event. |
| (b) | In such event the non-performing Party will be excused from further performance or observance of the obligations so affected for as long as such circumstances prevail and such Party continues to use Commercially Reasonable Efforts to recommence performance or observance without delay. Any Party so delayed in its performance will immediately notify the Party to whom performance is due by telephone (to be confirmed in writing as soon as possible after the inception of such delay) and describe at a reasonable level of detail the circumstances causing such delay. To the extent the provision of the Services or any part thereof is prevented or materially affected by a Force Majeure Event, Triple-S’s obligation to pay Charges hereunder shall accordingly be reduced by an equitable amount (which in the case of total suspension of the Services would be an amount equal to the total charges hereunder for the period of suspension). |
| (c) | If any event under Section 24.4(a) substantially prevents, hinders or delays performance |
|
Triple-S / Supplier Confidential Page 88 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
of the Services, then Supplier shall use Commercially Reasonable Efforts to identify another Supplier location from which it might provide the Services without interference from such event, and if Triple-S requests, Supplier shall assist Triple-S in identifying an alternate source that may be able to provide the Services to Triple-S during the time of such Force Majeure Event. If any event under Section 24.4(a) substantially prevents, hinders or delays performance of Services which are reasonably necessary for the continuity of Triple-S’s business, for more than the Force Majeure Time Period (as hereinafter defined), then at Triple-S’s option:
| (i) | Triple-S may procure such Services from an alternate source, and in such event Supplier will reimburse Triple-S for one-half of the difference between (1) the amount Triple-S is obligated to pay the alternate source for such Services, and (2) the amount that Triple-S would have paid Supplier for such Services under this Agreement, for a period not to exceed one hundred eighty (180) days; |
| (ii) | if such Services cannot be substantially restored within three (3) Business Days after the occurrence of the Force Majeure Event, Triple-S may terminate any portion of this Agreement so affected without charge or fee (except as set forth in Section 24.4(e) below) or liability to Supplier, and the Charges payable under this Agreement will be equitably adjusted to reflect those terminated Services; or |
| (iii) | if such Services cannot be substantially restored within fifteen (15) Business Days and such Services constitute a material portion of this Agreement or any Statement of Work, Triple-S may terminate this Agreement or such Statement of Work, without charge or fee to Triple-S (except as set forth in Section 24.4(e) below) or liability to Supplier, as of a date specified by Triple-S in a written notice of termination to Supplier. |
| (d) | “Force Majeure Time Period” shall mean ten (10) consecutive days. |
| (e) | Triple-S shall not be obligated to pay Supplier for Services that Supplier is not providing due to a Force Majeure Event. Supplier will not have the right to any additional payments from Triple-S for costs or expenses incurred by Supplier as a result of any Force Majeure Event. In the event that Triple-S exercises an option to terminate pursuant to this Section, Triple-S shall pay any outstanding Charges for all Services (including work in progress) provided in accordance with this Agreement through to the effective date of termination (subject to Triple-S’s right to dispute Charges set forth in Schedule C (Charging Methodology) in good faith). |
| (f) | A Force Majeure Event will not relieve Supplier of its obligations to implement successfully all of the Services relating to Disaster Recovery services that are included in this Agreement within the time period described in this Agreement. |
| 24.5 | Disaster Recovery and Business Continuity |
Supplier will at all times maintain Disaster Recovery and business continuity plans, procedures and capabilities, described in Schedule A (Cross Functional Services).
|
Triple-S / Supplier Confidential Page 89 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
| 25. | DISPUTE RESOLUTION |
Any dispute between the Parties arising out of or relating to this Agreement, including with respect to the interpretation of any provision of this Agreement or with respect to performance by Supplier or Triple-S, will be resolved as provided in this Section 25 (Dispute Resolution).
| 25.1 | Informal Dispute Resolution |
| (a) | Subject to Section 25.1(b), the Parties initially will attempt to resolve any dispute arising out of or relating to this Agreement informally in accordance with the following: |
| (i) | Within ten (10) Business Days after a Party receives notice of a dispute from the other Party (“Dispute Date”), it will designate a senior representative (i.e., a person whose rank within the company is superior to, in the case of Supplier, the Supplier Account Executive, and in the case of Triple-S, the Triple-S Program Manager) who does not devote substantially all of his time to performance under this Agreement, who will offer to meet with the designated senior representative of the other Party for the purpose of attempting to resolve the dispute amicably. |
| (ii) | The appointed representatives will meet promptly to discuss the dispute and attempt to resolve it without the necessity of any formal proceeding. They will meet as often as the Parties deem necessary in order that each Party may be fully advised of the other’s position. During the course of discussion, all reasonable requests made by one Party to the other for non-privileged information reasonably related to the matters in dispute will be honored promptly. |
| (iii) | The specific format for the discussions will be left to the reasonable discretion of the appointed representatives. |
| (b) | Formal dispute resolution may be commenced by a Party upon the first to occur of any of the following: |
| (i) | the appointed representatives conclude in good faith that amicable resolution of the dispute through continued negotiation does not appear likely; |
| (ii) | thirty-five (35) days have passed from the Dispute Date (this period will be deemed to run notwithstanding any claim that the process described in this Section 25.1 (Informal Dispute Resolution) was not followed or completed); or |
| (iii) | commencement of formal dispute resolution is deemed appropriate by a Party to avoid the expiration of an applicable limitations period or to preserve a superior position with respect to other creditors, or a Party makes a good faith determination, including as provided in Section 25.4 (Equitable Remedies), that a breach of this Agreement by the other Party is such that a temporary restraining order or other injunctive or conservatory relief is necessary. |
|
Triple-S / Supplier Confidential Page 90 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
| 25.2 | Litigation |
For all litigation which may arise with respect to this Agreement, the Parties irrevocably and unconditionally submit (a) to the exclusive jurisdiction and venue (and waive any claim of forum non conveniens and any objections as to laying of venue) of the Southern District of New York, or (b) if such court does not have subject matter jurisdiction, to the state courts located in New York, New York, in connection with any action, suit or proceeding arising out of or relating to this Agreement. The Parties further consent to the jurisdiction of any state court located within a district that encompasses assets of a Party against which a judgment has been rendered for the enforcement of such judgment or award against the assets of such Party.
| 25.3 | Continued Performance |
Each Party agrees (a) to continue performing its obligations under this Agreement while a dispute is being resolved except (and then only) to the extent performance is prevented by the other Party or the issue in dispute precludes performance, and (b) not to take any action that intentionally obstructs, delays, or reduces in any way the performance of such obligations. For the avoidance of doubt, a good faith dispute regarding invoiced charges and Triple-S’s exercise of rights with respect to such disputed charges as permitted under Schedule C (Charging Methodology) will not be considered to prevent Supplier from performing the Services or preclude performance by Supplier, nor will this Section 25.3 be interpreted to limit either Party’s right to terminate this Agreement as provided in Section 16 (Termination).
| 25.4 | Equitable Remedies |
| (a) | Each Party acknowledges that a breach of any of its obligations under the Sections of this Agreement listed in Section 25.4(c), or its infringement or misappropriation of any Intellectual Property Rights of the other Party, may irreparably harm the other Party in a way that could not be adequately compensated by money damages. |
| (b) | In such a circumstance, the aggrieved Party may (in addition to all other remedies and rights) proceed directly to court notwithstanding the other provisions of this Section 25 (Dispute Resolution). |
| (c) | Sections 25.4(a) and 25.4(b) apply to Sections 14 (Data Security and Protection), 15 (Intellectual Property Rights), 17 (Disengagement Assistance), 21 (Confidentiality) and 23 (Indemnification). |
| 25.5 | Disclaimer of Uniform Computer Information Transactions Act |
TO THE MAXIMUM EXTENT PERMITTED UNDER APPLICABLE LAW, THE PARTIES DISCLAIM AND NONE OF THIS AGREEMENT SHALL BE SUBJECT TO THE UNIFORM COMPUTER INFORMATION TRANSACTIONS ACT (“UCITA”) (PREPARED BY THE NATIONAL CONFERENCE OF COMMISSIONERS ON UNIFORM STATE LAWS) AS CURRENTLY ENACTED OR AS MAY BE ENACTED, CODIFIED OR AMENDED FROM TIME TO TIME BY ANY JURISDICTION. TO THE EXTENT THAT ANY ASPECT OF THIS AGREEMENT OR ANY LICENSE GRANTED UNDER THIS AGREEMENT IS UNCLEAR OR DISPUTED BY THE PARTIES AND UCITA, IF APPLIED, WOULD CLARIFY SUCH LICENSE OR RESOLVE SUCH DISPUTE, THE PARTIES AGREE TO CLARIFY SUCH LICENSE OR RESOLVE SUCH DISPUTE INDEPENDENTLY OF UCITA
|
Triple-S / Supplier Confidential Page 91 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
BY APPLYING THE INTENT OF THE PARTIES AT THE TIME THAT THEY ENTERED THIS AGREEMENT.
| 26. | RULES OF CONSTRUCTION |
| 26.1 | Entire Agreement |
This Agreement – consisting of the signature page, these General Terms and Conditions and the attached Schedules and Exhibits and attachments, and each Statement of Work (and its respective Exhibits and attachments) and Task Order – constitutes the entire agreement between the Parties with respect to its subject matter and merges, integrates and supersedes all prior and contemporaneous agreements and understandings between the Parties, whether written or oral, concerning its subject matter.
| 26.2 | Contracting Parties; No Third Party Beneficiaries |
This Agreement is entered into solely between, and may be enforced only by, Triple-S and Supplier. This Agreement does not create any legally enforceable rights in third parties, including suppliers, subcontractors and customers of a Party, except as provided in this paragraph and Section 23 (Indemnification).
| 26.3 | Contract Amendments and Modifications |
Any terms and conditions varying from this Agreement on any order or written notification from either Party will not be effective or binding on the other Party. Subject to regulatory approval as set forth in Schedule W (Regulatory Requirements), this Agreement may be amended or modified solely in a writing signed by an authorized representative of each Party.
| 26.4 | Governing Law |
This Agreement and performance under it shall be governed by and construed in accordance with the laws of the Commonwealth of Puerto Rico without regard to its choice of law principles.
| 26.5 | Relationship of the Parties |
Supplier, in furnishing the Services, is acting as an independent contractor. Supplier has the sole right and obligation to supervise, manage, contract, direct, procure, perform or cause to be performed, all work to be performed by Supplier under this Agreement. Supplier is not an agent or partner of Triple-S and has no authority to represent or bind Triple-S as to any matters, except as expressly authorized in this Agreement. Except as set forth in Section 2.7, this Agreement establishes a nonexclusive relationship between the Parties.
| 26.6 | Consents and Approvals |
Where approval, acceptance, consent, determination or similar action by either Party is required under this Agreement, such action will not be unreasonably delayed, conditioned or withheld unless this Agreement expressly provides that it is in the discretion or reasonable discretion of the Party, provided that this shall not be construed to force Triple-S to accept any Deliverable or
|
Triple-S / Supplier Confidential Page 92 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
Milestone that does not meet applicable Acceptance Criteria in all material respects. No approval or consent given by a Party under this Agreement will relieve the other Party from responsibility for complying with the requirements of this Agreement, nor will it be construed as a waiver of any rights under this Agreement (except to the extent, if any, expressly provided in such approval or consent). Each Party will, at the request of the other Party, perform those actions, including executing additional documents and instruments, reasonably necessary to give full effect to this Agreement.
| 26.7 | Waiver |
No failure or delay by a Party in exercising any right, power or remedy will operate as a waiver of that right, power or remedy, and no waiver will be effective unless it is in writing and signed by an authorized representative of the waiving Party. If a Party waives any right, power or remedy, the waiver will not waive any successive or other right, power or remedy that Party may have.
| 26.8 | Remedies Cumulative |
Except as otherwise expressly provided in this Agreement, all remedies provided in this Agreement are cumulative and in addition to and not in lieu of any other remedies available to a Party under this Agreement, at law, or in equity.
| 26.9 | References |
| (a) | The section headings and the table of contents used in this Agreement are for convenience of reference only and will not enter into the interpretation of this Agreement. |
| (b) | Unless otherwise indicated, section references are to sections of the document in which the reference is contained. For example, section references in these General Terms and Conditions are to sections of the General Terms and Conditions and, likewise, section references in a Schedule to this Agreement are to sections of that Schedule. |
| (c) | References to numbered (or lettered) sections of this Agreement also refer to and include all subsections of the referenced section. |
| (d) | Unless otherwise indicated, references to Schedules to this Agreement also refer to and include all Exhibits to the referenced Schedule. |
| 26.10 | Rules of Interpretation |
| (a) | Unless the context requires otherwise, (i) ”including” (and any of its derivative forms) means including but not limited to, (ii) ”may” means has the right, but not the obligation to do something and “may not” means does not have the right to do something, (iii) ”will” and “shall” are expressions of command, not merely expressions of future intent or expectation, (iv) ”written” or “in writing” is used for emphasis in certain circumstances, but that will not derogate from the general application of the notice requirements set forth in Section 27.3 (Notices) in those and other circumstances, (v) use of the singular imports the plural and vice versa, and (vi) use of a specific gender imports the other gender(s). |
|
Triple-S / Supplier Confidential Page 93 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
| (b) | References in this Agreement to “days” that do not specifically refer to Business Days are references to calendar days, unless otherwise provided. |
| 26.11 | Order of Precedence |
If there is any conflict within this Agreement between these General Terms and Conditions and any document incorporated by reference into this Agreement, the Parties shall attempt to read any such conflicting provisions consistently, however, in the event such a consistent reading cannot be accomplished, the order of precedence will be as follows (subject to Section 13.5 above): (i) the General Terms and Conditions and any amendments thereto, (ii) the Schedules, (iii) other attachments to this Agreement, (iv) other documents incorporated by reference, (v) subject to Section 2.3(d), Statements of Work and Task Orders (including the Exhibits attached thereto).
| 26.12 | Severability |
If any provision of this Agreement conflicts with the Law under which this Agreement is to be construed or if any provision of this Agreement is held invalid, illegal, or otherwise unenforceable by a competent authority, such provision will, if possible, be deemed to be restated to reflect as nearly as possible the original intentions of the Parties in accordance with applicable Law. In any event, the remainder of this Agreement will remain in full force and effect.
| 26.13 | Counterparts |
This Agreement may be executed in several counterparts and by facsimile or PDF signature, all of which taken together constitute a single agreement between the Parties. Each signed counter-part, including a signed counterpart reproduced by reliable means (including facsimile and PDF), will be considered as legally effective as an original signature.
| 26.14 | Reading Down |
If a provision of this Agreement is reasonably capable of an interpretation which would make that provision valid, lawful and enforceable and an alternative interpretation that would make it unenforceable, illegal, invalid or void then, so far as is possible, that provision will be interpreted or construed to be limited and read down to the extent necessary to make it valid and enforceable.
| 27. | GENERAL PROVISIONS |
| 27.1 | Survival |
Any provision of this Agreement that contemplates or governs performance or observance subsequent to termination or expiration of this Agreement will survive the expiration or termination of this Agreement for any reason, including Sections 8 (Charges), 14 (Data Security and Protection), including Schedule L (IT Security Addendum), 15 (Intellectual Property Rights), 17 (Disengagement Assistance), including Schedule I (Disengagement Assistance), 18.5 (Audits and Records), including Schedule M (Audit and Record Retention Requirements), 19.4 and 19.5 (Representations, Warranties and Covenants), but solely to the extent that any Warranty Period or Software Documentation Warranty Period, as applicable, extends beyond the termination or expiration of this Agreement, 19.9 (Non-Infringement), 19.19 (Non-Infringement), 20.2
|
Triple-S / Supplier Confidential Page 94 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
(Disclaimer), 21 (Confidentiality), 23 (Indemnification), 24 (Liability), 25 (Dispute Resolution), 26.4 (Governing Law), 27.1 (Survival), 27.4 (Non-Solicitation of Employees), Schedule H (Business Associate Agreement) and Schedule S (Supplier Software and Supplier Tools).
| 27.2 | Binding Nature and Assignment |
This Agreement is binding upon, and inures to the benefit of, the Parties hereto and their respective successors and permitted assigns. Supplier acknowledges that the Services are personal in nature and that, as a result, Supplier may not assign this Agreement or delegate its rights or obligations under this Agreement (except as set forth in Section 6.6 (Subcontracting)), whether by operation of law or otherwise, without the prior written consent of Triple-S. Triple-S may not assign this Agreement without the prior written consent of Supplier except to a Triple-S Affiliate or to the successor in a merger or reorganization of Triple-S or an entity that acquires Control of Triple-S or acquires all or substantially all of Triple-S’s business or assets provided that such assignee agrees in writing to assume and be bound by all obligations of Triple-S under this Agreement. Any attempted assignment or delegation in violation of this Section 0 will be void and will constitute a material breach of this Agreement by the Party attempting the assignment.
| 27.3 | Notices |
| (a) | All notices, requests, demands and determinations under this Agreement (other than routine operational communications), shall be in writing and shall be deemed duly given (i) when delivered by hand, and (ii) on the designated day of delivery after being timely given to an express overnight courier with a reliable system for tracking delivery,: |
In the case of Triple-S:
Triple-S Salud, Inc.
▇▇ ▇▇▇ ▇▇▇▇▇▇
▇▇▇ ▇▇▇▇, ▇▇▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇-▇▇▇▇
Attention: President
With a copy to:
Triple-S Salud, Inc.
▇▇ ▇▇▇ ▇▇▇▇▇▇
▇▇▇ ▇▇▇▇, ▇▇▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇-▇▇▇▇
Attention: Chief Legal Counsel
and, in the case of notices of renewal, default, or termination:
Pillsbury ▇▇▇▇▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇▇ LLP
▇▇▇ ▇▇▇▇▇▇▇▇ ▇▇▇▇▇▇, ▇▇▇▇▇ ▇▇▇▇
▇▇▇▇▇▇, ▇▇ ▇▇▇▇▇-▇▇▇▇
Attention: ▇▇▇▇ ▇▇▇▇▇▇
In the case of Supplier:
|
Triple-S / Supplier Confidential Page 95 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
OptumInsight, Inc.
▇▇▇▇▇ ▇▇▇▇▇ ▇▇▇▇▇▇
▇▇▇▇ ▇▇▇▇▇▇▇, ▇▇ ▇▇▇▇▇
Attn: General Counsel
| (b) | A Party may from time to time change its address or designee for notification purposes by giving the other prior written notice of the new address or designee and the date upon which it will become effective. |
| 27.4 | Non-solicitation of Employees |
| (a) | Except as set forth in Section 17.1(e), each Party agrees not to directly or indirectly solicit (i) in the case of Triple-S, the employment of Supplier’s employees engaged in the provision of the Services during the period they are so engaged and for six (6) months thereafter, and (ii) in the case of Supplier, Triple-S’ employees working in functions related to information technology or business process services (e.g., claims, contact center, member and provider servicing) during the period they are so engaged and for six (6) months thereafter without the first Party’s prior written consent. |
| (b) | The restriction set forth in Section 27.4(a) shall not bar either Party from soliciting, hiring or receiving services provided by any of the other Party’s personnel whose employment has been terminated by the other Party or who have previously voluntarily resigned from the other Party to accept an offer of employment from a third party, including as contemplated in Schedule G (In-Scope Employee Agreement). |
| (c) | The restriction set forth in Section 27.4(a) shall not apply to solicitation, hiring or receipt of services provided by personnel engaged via general advertising that is not targeted at the other Party’s personnel. |
| 27.5 | Covenant of Good Faith |
Each Party, in its respective dealings with the other Party under or in connection with this Agreement, will act reasonably and in good faith.
| 27.6 | Public Disclosures |
Neither Party shall make any media releases, public announcements or public disclosures relating to this Agreement or the subject matter of this Agreement, including promotional or marketing material, but not including disclosures to the extent required to meet legal or regulatory requirements beyond the reasonable control of the disclosing Party without the prior written consent of the other Party.
| 27.7 | Service Marks |
Each party will not, without the other Party’s consent, use the name, service names or marks, derivative names or marks, or trademarks of the other Party in any advertising or promotional materials prepared by or on behalf of the first Party.
|
Triple-S / Supplier Confidential Page 96 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Master Services Agreement
General Terms and Conditions
| 27.8 | Mutually Negotiated |
No rule of construction will apply in the interpretation of this Agreement to the disadvantage of one Party on the basis that such Party put forward or drafted this Agreement or any provision of this Agreement.
IN WITNESS WHEREOF, Triple-S and Supplier have each caused this Agreement to be signed and delivered by its duly authorized officer, all as of the date first set forth above.
| TRIPLE-S SALUD, INC. | OPTUMINSIGHT, INC. | |||
| By: |
/s/ ▇▇▇▇▇▇▇▇ ▇▇▇▇▇▇▇▇▇-▇▇▇▇▇▇▇ |
By: |
/s/ ▇▇▇▇ ▇▇▇▇▇▇ |
|
| Print Name: |
▇▇▇▇▇▇▇▇ ▇▇▇▇▇▇▇▇▇-▇▇▇▇▇▇▇ |
Print Name: |
▇▇▇▇ ▇▇▇▇▇▇ |
|
| Title: |
President |
Title: |
CEO, OptumInsight |
|
| Date: |
August 29, 2017 |
Date: |
8/29/2017 |
|
|
Triple-S / Supplier Confidential Page 97 |
MSA Schedule A
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
SCHEDULE A
CROSS FUNCTIONAL SERVICES
| Schedule A | Triple-S / Supplier Confidential |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule A
Cross-Functional Services
TABLE OF CONTENTS
| 1 | INTRODUCTION | 1 | |
| 1.1 | General | 1 | |
| 1.2 | Hours of Coverage | 1 | |
| 1.3 | Definitions | 1 | |
| 2 | CROSS-FUNCTIONAL SERVICES | 2 | |
| 2.1 | Training Services | 2 | |
| 2.2 | Documentation | 2 | |
| 2.3 | Regulatory Compliance Adherence Services | 3 | |
| 2.4 | Managed Third Party Contract Services | 4 | |
| 2.5 | Issue and Error Resolution Services | 8 | |
| 2.6 | Knowledge Base Services | 8 | |
| 2.7 | Triple-S Policy Support Services | 9 | |
| 2.8 | Business Continuity & Disaster Recovery Services | 10 | |
| 3 | EMBEDDED PROCESSES | 14 | |
| 3.1 | General | 14 | |
| 3.2 | Embedded Processes | 14 | |
| 4 | RETAINED TRIPLE-S RESPONSIBILITIES | 15 | |
|
Triple-S / Supplier Confidential Page i |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
SCHEDULE A
CROSS FUNCTIONAL SERVICES
| 1 | INTRODUCTION |
| 1.1 | General |
| (a) | This Schedule A (Cross Functional Services) describes, among other things, those Cross Functional Services and Embedded Processes to be performed and delivered by Supplier, which are applicable to all of the Services performed by Supplier under this Agreement. |
| (b) | References to specific resources (e.g., tools, systems) in this Schedule A (Cross Functional Services), any SOW, or elsewhere in the Agreement that are used by Supplier in performing the Services shall be deemed to include successor or replacement resources. |
| 1.2 | Hours of Coverage |
| (a) | The minimum hours of coverage for each of the Services are set forth in SOW #1 (Claims Services) and SOW #2 (IT Services). Supplier acknowledges and agrees that performance of the Cross Functional Services may require Supplier Personnel to perform additional/overtime work outside regular operating hours, and that such additional/overtime work is within the scope of the Cross Functional Services. |
| (b) | Subject to any adjustments to charges expressly set forth in Schedule C (Charging Methodology), Supplier will extend its hours of operations (for example, through overtime, weekend and holiday work) from time to time as needed to meet regulatory requirements, compliance and Service Level Metrics and other requirements of the Agreement. Supplier’s work during such extended hours of operations is within the scope of the Cross Functional Services. |
| 1.3 | Definitions |
Capitalized terms not defined in this Schedule A (Cross Functional Services) shall have the meanings given them in Schedule AA (Glossary) or elsewhere in this Agreement.
| (a) | “Plan” means a health insurance plan offered by Triple-S. |
| (b) | “Provider” means a facility, physician, physician organization, independent practice association, health care provider, supplier, or other organization that may provide covered services. |
|
Triple-S / Supplier Confidential Page 1 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule A
Cross-Functional Services
| 2 | CROSS-FUNCTIONAL SERVICES |
Supplier shall provide the following cross-functional services (the “Cross Functional Services”) as part of the Services. If Triple-S terminates the provision of any part of the Services pursuant to this Agreement, Supplier shall continue to provide the Cross Functional Services set forth in this Section 2 as such Cross Functional Services relate to the remaining Services.
| 2.1 | Training Services |
“Training Services” are those Functions associated with the curriculum development, planning, scheduling and delivery of trainings in compliance with Laws and Triple-S Policies and Procedures for all Supplier Personnel performing the Services including the following activities:
| (a) | Developing training curriculum needed to deliver the Services including training scenarios and knowledge checks; |
| (b) | Developing training, including computer based training that comply with regulatory requirements; |
| (c) | Maintaining training calendar and inventory; |
| (d) | Documenting training attendance, course completion and other training related details; |
| (e) | Managing and maintaining intake process and system for new and adjusted training requests; |
| (f) | Regularly reviewing training technology, methodologies, courses, and approach; |
| (g) | Performing needs assessment and training validation for any new training requests; |
| (h) | Reviewing audit findings and making recommendations to business areas for policy and procedure creation/updates, additional training, process automation tools, and/or process change/improvement; and |
| (i) | Providing regulatory training support including ad hoc training requests relating to Supplier’s performance of the Services and reporting. |
| 2.2 | Documentation |
“Documentation Services” means those Functions associated with maintaining, archiving, offsite storage, retrieval, and destruction of documentation as related to the Services in hard copy and/or electronic form, including the following activities:
| (a) | Recommending documentation requirements, location, and formats; |
| (b) | Reviewing and approving documentation requirements, location and formats as appropriate; |
|
Triple-S / Supplier Confidential Page 2 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule A
Cross-Functional Services
| (c) | Maintaining, retrieving and archiving documentation in agreed format in support of the Services; |
| (d) | Identifying documentation for archival per Triple-S retention policies and coordinating with Triple-S to prepare documents for delivery to offsite storage; |
| (e) | Providing additional information as requested to support Triple-S documentation requirements and Triple-S proposal efforts; |
| (f) | Enabling Triple-S direct electronic access to documentation retained in accordance with the documentation requirements; |
| (g) | Following record destruction processes set forth in Section 21.7 of the General Terms and Conditions; |
| (h) | Storing business continuity documentation separate from standard retention documents; |
| (i) | Maintaining documentation per legal hold requirements per regulatory and Triple-S policies; and |
| (j) | Providing, as requested by Triple-S, documentation related to the training services, including assistance reports and training material. |
| 2.3 | Regulatory Compliance Adherence Services |
“Regulatory Compliance Adherence Services” are the Functions necessary to manage compliance of the Services, including managing the compliance of all Subcontractors, in accordance with Law. The Regulatory Compliance Adherence Services include the activities required under Section 14.5 of the General Terms and Conditions and the following:
| (a) | Develop and distribute content for, and monitor evidence of completion of, compliance training for Supplier Personnel; |
| (b) | Monitor Supplier’s compliance with Laws with which Supplier is responsible for complying pursuant to Section 13 (Compliance with Laws) of the General Terms and Conditions; |
| (c) | Identify, track, report, and escalate issues of non-compliance (or suspected non-compliance) to Triple-S within required timeframes; |
| (d) | Implement, monitor and report on normal course of business controls; and |
| (e) | Notify Subcontractors of compliance requirements, monitor Subcontractor compliance, and report to Triple-S on the compliance of Subcontractors. |
|
Triple-S / Supplier Confidential Page 3 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule A
Cross-Functional Services
| 2.4 | Managed Third Party Contract Services |
Supplier shall provide the Managed Third Party Contract Services with respect to Managed Third Party Contracts.
“Managed Third Party Contract” means the contracts in the name of Triple-S or a Triple-S Affiliate used in support of the Services or complimentary to the Services and identified as Managed Third Party Contracts in Schedule X (Source of Truth) or as otherwise agreed by the Parties in writing (e.g., in a Statement or Work or project plan).
“Managed Third Party Contract Services” means the Functions described below associated with managing the Managed Third Party Contracts in place as of the Effective Date and entered into by Triple-S after the Effective Date and that the Parties agree will be Managed Third Party Contracts.
“Managed Third Party” means the third party that is a party to the Managed Third Party Contract with Triple-S or a Triple-S Affiliate.
The Managed Third Party Contract Services consist of the following activities:
| (a) | Commercial Oversight and Management. Supplier will manage the Managed Third Party Contracts on behalf of Triple-S. This responsibility includes establishing resources within Supplier that are responsible for proactively managing contract, performance, change, financial, transition and other issues that arise under the Managed Third Party Contracts, including: |
| (i) | Understanding contractual commitments in the Managed Third Party Contracts. |
| (ii) | Serving as primary point of contact with Triple-S for interpretation and modification of contracts with the applicable Managed Third Party. |
| (iii) | Authorizing, managing, and testing scope changes and project work under each Managed Third Party Contract (e.g., when Triple-S requires custom changes to software provided by a Managed Third Party, Supplier is responsible for communicating those changes and associated requirements provided by Triple-S, working with the Managed Third Party refine and document them in a statement of work or task order for Triple-S approval, overseeing and managing the work performed by the Managed Third Party, and conducting testing and advising Triple-S whether the work meets applicable user acceptance testing requirements). Supplier shall obtain and document all requisite approvals to establish an appropriate audit trail, within Triple-S guidelines for Managed Third Party Contracts as such guidelines are provided to Supplier in writing. Any such scope changes as well as exceptions to Triple-S guidelines will require Triple-S’s prior written approval before any work is performed. If no guidelines are established for a specific Managed Third Party Contract, Supplier will consult with Triple-S regarding any such scope change. With respect to [***], Supplier will (1) communicate with Triple-S personnel in connection with such |
|
Triple-S / Supplier Confidential Page 4 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule A
Cross-Functional Services
personnel’s interactions with [***]; and (2) reasonably cooperate in providing information to support such interactions, in each case subject to Section 19.19 of the General Terms and Conditions.
| (iv) | Revising Managed Third Party Contracts to reflect changes in scope, new services, service levels and other conditions upon prior approval by Triple-S, including those related to formal change requests. |
| (v) | Performing general administrative tasks associated with Managed Third Party Contracts, including maintaining records and documentation related to Managed Third Party Contracts, recording decisions in contract files. |
| (vi) | Monitoring license usage and maintaining compliance with the terms of third party licenses (i.e., the number of licenses and scope of licenses). |
| (vii) | Maintaining Triple-S-provided copies of all Managed Third Party Contracts (or a Triple-S-provided summary of the pertinent information contained in each Managed Third Party Contract), including such contracts that expire during the Term, in a secure, online location accessible to designated individuals at both Triple-S and Supplier. |
| (viii) | Escalating and working to resolve issues and disputes (pursuant to the governance process agreed to by the Parties) related to the Managed Third Party Contracts, and referring matters to Triple-S legal where appropriate. |
| (ix) | Overseeing the performance of Managed Third Party Contracts, striving to (i) maximize the operational and financial performance of such contracts (from Triple-S's perspective) and (ii) minimize risk to Triple-S from the performance of such contracts. Supplier's responsibilities consist of: |
| (A) | Monitoring Managed Third Party Contract performance with respect to all material contractual requirements directly related to the provision of products or services and tracking and reporting on service levels or similar performance metrics included in the applicable contract (as such reports are set forth in Schedule K (Reports)); |
| (B) | Monitoring Managed Third Party Contract technical performance with respect to the exchange of data between Supplier and the Managed Third Party including: |
| (1) | Validating incoming and outgoing file transmissions to confirm what is transmitted is received and processed correctly and in accordance with scheduled frequencies; |
| (2) | Validating file transmission contents are processed upon receipt of transmission; |
|
Triple-S / Supplier Confidential Page 5 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule A
Cross-Functional Services
| (3) | Validating file transmission contents are processed correctly and result in system records that match to the information in the initiator’s source system; |
| (4) | Validating/resolving that receiver systems’ impacted records are accurately reconciled; |
| (5) | Confirming compliance with applicable privacy requirements and regulations; |
| (6) | Resolving issues with delegated entities/outside vendors related to discrepancies with respect to risk determination in writing, and documenting and logging related actions; |
| (C) | Integrating work performed under the Managed Third Party Contracts among Supplier and Supplier’s Subcontractor(s), Triple-S and its Affiliates, and other Managed Third Parties; |
| (D) | Validating assessments, calculations, and if Triple-S elects to receive credits related to service level failures, the timely payment of such credits and other similar types of credits and rebates under Managed Third Party Contracts; provided, however, that execution and escalation on service level failures, or application of credits and rebates, will be in cooperation with Triple-S; |
| (E) | Monitoring the compliance with any service levels contained in the applicable Managed Third Party Contract; |
| (F) | Notifying Triple-S of material failure to perform in accordance with the provisions of its Managed Third Party Contract; |
| (G) | Notifying Triple-S promptly if (i) there are performance failures or other issues regarding contractual responsibilities related to any Managed Third Party Contract, or (ii) there are issues with a Managed Third Party Contract adversely affecting the Services or Triple-S (or its Affiliates); |
| (H) | Evaluating and recommending retention, modification, or termination of a Managed Third Party Contract based on the performance or cost benefits to Triple-S as tracked by Supplier; and |
| (I) | Monitoring Managed Third Party Contract adherence to compliance activities, including auditing and training; and |
| (x) | Providing assistance with Managed Third Party Contract negotiations as reasonably required. |
|
Triple-S / Supplier Confidential Page 6 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule A
Cross-Functional Services
| (b) | Financial Contract Management Support. Supplier will support Triple-S financial contract management Functions by: |
| (i) | Managing contract (including formal, short form, and annual contracts) drafting, evaluation, negotiation, execution and order pricing; |
| (ii) | Reviewing Managed Third Party invoices to confirm validity and accuracy; |
| (iii) | Assigning applicable financial coding; |
| (iv) | Managing invoice discrepancies and disputes and handle on-going issue and change management; |
| (v) | Submitting processed invoices for payment to Triple-S in a timely manner to allow assistance to Triple-S to comply with third party payment terms; and |
| (vi) | Obtaining Triple-S’s prior written approval prior to taking any action that may affect amounts payable or other obligations Triple-S may have under the Managed Third Party Contracts. |
| (c) | Service Levels Performance. If a Managed Third Party fails to meet a service level under a Managed Third Party Contract as a direct result of acts or omissions of Supplier, Supplier shall pay Triple-S an amount equal to the service level credit that would have been payable under the Managed Third Party Contract had the Managed Third Party’s failure resulted from the Managed Third Party’s acts or omissions, less any amounts actually paid by the Managed Third Party. |
| (d) | Contract Compliance. Triple-S and Supplier will comply with the terms of the Managed Third Party Contracts to the extent they are related to their respective obligations and will not violate, or cause Triple-S to violate, the terms of such Managed Third Party Contracts. Triple-S will also keep Supplier informed of any pertinent communications Triple-S has with any Managed Third Party. |
| (e) | Objections to Managed Services. If a Managed Third Party objects to Supplier’s responsibilities as set forth in this Schedule or otherwise objects to Supplier acting under such Managed Third Party Contracts as provided herein, Triple-S and Supplier will, and will cause their respective Affiliates to, cooperate and use their respective commercially reasonable efforts so that the portion of such Managed Third Party Contract that relates to the Services can be performed by Supplier and the objection, if any, of the Managed Third Party can be resolved. If a Managed Third Party requires evidence of the rights set forth in this Schedule, Triple-S will provide reasonable documentation to evidence such rights. |
| (f) | Transition Away from the Managed Third Party Contracts. Supplier shall lead efforts required to transition services from Managed Third Party Contracts to Supplier that the Parties agree will be transitioned to Supplier. Supplier’s responsibilities in this regard include: |
|
Triple-S / Supplier Confidential Page 7 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule A
Cross-Functional Services
| (i) | Preparing and negotiating transition plans with Managed Third Parties; |
| (ii) | Tracking and managing performance against transition plans; |
| (iii) | Escalating problems that may arise with Managed Third Parties’ performance that Supplier is unable to resolve to Triple-S; |
| (iv) | Negotiating statements of work or other appropriate documentation required to support the transition away from the Managed Third Party Contract. Supplier must obtain Triple-S’s approval prior to authorizing any Managed Third Party to perform any work that may be chargeable to Triple-S; and |
| (v) | Identifying and drafting all notices and other communications to Managed Third Parties that are required to conduct the transition (e.g., notices to remove services or to terminate or extend portions of the Agreement). |
| 2.5 | Issue and Error Resolution Services |
“Issue and Error Resolution” means the Functions associated with resolving all issues related to the Services including issues identified by Triple-S’ internal audit, customer complaints, any errors identified by regulators, or through any other Triple-S or Supplier quality assurance activities, including the following:
| (a) | Reviewing requests to correct errors; |
| (b) | Correcting all errors in the systems used by Supplier and its Subcontractors; and |
| (c) | Timely reporting to Triple-S on the Issue and Error Resolution. |
| 2.6 | Knowledge Base Services |
“Knowledge Base Services” are the Functions associated with managing and maintaining the knowledge base (“KB”) system and content. The KB will be used to store all content and procedures applicable to the Services. All documents in the KB must be reviewed within one year of the previous review or after delivering training. Knowledge Base Services include:
| (a) | Create, validate and approve (as appropriate) all KB content; |
| (b) | Performing annual review of content and update accordingly except where content is identified to be updated on a more frequent basis; and |
| (c) | Timely updating Supplier staff of any revised content applicable to their role. |
|
Triple-S / Supplier Confidential Page 8 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule A
Cross-Functional Services
| 2.7 | Triple-S Policy Support Services |
“Triple-S Policy Support Services” means those Functions associated with supporting Triple-S in its development and implementation of Triple-S Policies and Procedures, that govern or pertain to the Services. Supplier’s role in providing Triple-S Policy Support Services includes:
| (a) | Generally, providing operational input and subject matter expertise with respect to Triple-S Policies and Procedures; |
| (b) | As reasonably requested, participating in meetings with Triple-S and Supplier stakeholders having responsibility for the development, implementation, monitoring and enforcement of Triple-S Policies and Procedures; |
| (c) | Following any Triple-S Policies and Procedures review timelines requirements as reasonably specified by Triple-S; |
| (d) | In response to changes in Laws, regulations, guidelines, policies, contracts or requests from Triple-S’ or Supplier’s compliance organization: |
| (i) | Participate in Triple-S EPCO Steering Committee meetings to review new legal and regulatory changes and assessment of business impact; |
| (ii) | Participate in Triple-S EPCO regulatory implementation change teams; |
| (iii) | Project manage the operational implementation and/or affected system changes of legal and regulatory changes that affect IT Services and participate in operational implementation and/or affected system changes of legal and regulatory changes that span multiple functions/departments, including tracking the progress of deliverables and communicating status to Triple-S’ EPCO and/or compliance organization; and |
| (iv) | Based on the aforementioned meetings and guidance from the EPCO, prepare initial drafts of revised or new Triple-S Policies and submit them to the relevant Triple-S and Supplier stakeholders for review and comment. |
To the extent the Services described in Sections 2.7(d)(iii) or (iv) require Supplier to perform Application Support Services, they shall be counted against the Applications Support Pool defined in Section 6 of Schedule C (Charging Methodology). To the extent they require Supplier to perform Infrastructure Projects that require changes to the Infrastructure used to host In-Scope Applications, any Charges for those Infrastructure Projects will be determined pursuant to Section 7 of Schedule C (Charging Methodology).
| (e) | As directed by Triple-S, prepare updated versions of Triple-S Policies and Procedures to address input provided by relevant Triple-S and Supplier stakeholder groups; |
|
Triple-S / Supplier Confidential Page 9 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule A
Cross-Functional Services
| (f) | Provide communications and training to Supplier personnel regarding revised and new Triple-S Policies and Procedures and access to Triple-S personnel to such communications and training; and |
| (g) | Implement new Triple-S-approved Triple-S Policies and Procedures related to the performance of the Services in accordance with Section 4.4 (Triple-S Policies and Procedures) of the General Terms and Conditions. |
| 2.8 | Business Continuity & Disaster Recovery Services |
| (a) | General. Supplier will provide the following Functions associated with planning, documenting, implementing, maintaining and periodically testing Supplier’s business continuity plan and related process documentation (including emergency management and site emergency response plans), as may be amended from time to time during the Term, that are designed to provide Services in a sustained and appropriate level during any business continuity / disaster recovery event (a “BC/DR Event”). Supplier shall maintain a plan describing the way in which it will provide the business continuity and disaster recovery Functions (the “Business Continuity and Disaster Recovery Plan” or “BC/DR Plan”). The BC/DR Plan includes the Legacy BC/DR Plan and New BC/DR Plan defined below. |
| (b) | Commencement. Supplier shall initially maintain and follow the existing Triple-S business continuity plan for all operations that remain at facilities used by Triple-S to provide the Services prior to the Services Commencement Date (“Legacy BC/DR Plan”). As Supplier conducts the Transition and Transformation, Supplier will develop, test and implement a new BC/DR Plan for the Services that meets the requirements in this Section 2.8 (“New BC/DR Plan”). |
| (c) | Policies and Access. Supplier will maintain the Services in compliance with the BC/DR Plan. Supplier will store the BC/DR Plan in readily accessible locations for access in the event of a BC/DR Event, and will provide Triple-S ongoing access to the Triple-S BC/DR Plan during the Term (Supplier may redact portions of the BC/DR Plan that are not applicable to Triple-S). |
| (d) | New BC/DR Plan. The New BC/DR Plan shall meet the following requirements: |
| (i) | Compliance with the requirements of the General Terms and Conditions; |
| (ii) | Recovery time objectives (RTOs) of not more than four (4) hours for all In-Scope Applications and Services, with recovery point objectives (RPOs) of not more than four (4) hours; |
| (iii) | A brief description of processes and procedures used to recover the Services, and associated RTO time frames for the recovery of such Services, including a prioritized listing of Services aligning with Triple-S’s reasonable input; |
|
Triple-S / Supplier Confidential Page 10 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule A
Cross-Functional Services
| (iv) | Notification procedures to alert Triple-S of Service disruptions including off-hour and weekend coverage; |
| (v) | Supplier’s and Triple-S’s respective recovery responsibilities; |
| (vi) | Clearly defined structure, roles, responsibilities, names and tasks of a team of Supplier Personnel (including appropriate deputies and delegates and dedicated liaisons to Supplier) to implement, manage and execute the New BC/DR Plan in accordance with its terms and the Agreement; |
| (vii) | Description of how Supplier will implement, test, maintain (with relevant updates/improvements) and manage the New BC/DR Plan; |
| (viii) | Escalation and resolution procedures for BC/DR Events; |
| (ix) | Identification and links to key emergency organizations (such as fire, police and ambulance) and to applicable governmental agencies and authorities; |
| (x) | Processes for performing post-event analysis (and identifying any need for improvements) of a BC/DR Event following restoration of Services and technology; |
| (xi) | Strategy or strategies for restoration of the affected processes, Services and technology; |
| (xii) | Provisions for recovery of operations related to Services delivery and as needed to relocate Supplier Personnel to Recovery Sites; |
| (xiii) | Contact listings of key Supplier Personnel associated with recovery of operations with respect to the New BC/DR Plan; |
| (xiv) | A list of the rimary ites and Recovery Sites for each Supplier Facility that delivers Services to Triple-S; |
| (xv) | Procedures for evacuation of Supplier Facilities and emergency notification; |
| (xvi) | Criteria for BC/DR Event declaration, recovery and testing; and |
| (xvii) | Names and titles of those individuals who are authorized by Supplier to declare a BC/DR Event. |
| (e) | Notice of Deficiencies. Supplier will promptly alert Triple-S of any deficiencies discovered in the BC/DR Plan that may reasonably be expected to adversely affect the provision of Services to Triple-S. |
| (f) | Updates. Supplier shall review and update, the BC/DR Plan on an annual basis or as otherwise warranted by: (i) business or technical Changes (or both) made through |
|
Triple-S / Supplier Confidential Page 11 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule A
Cross-Functional Services
the Change Control Process, (ii) requirements of applicable Laws, and (iii) in the case of the New BC/DR Plan only, otherwise as necessary to maintain compatibility with the applicable terms of this Agreement. Supplier will take Triple-S business direction and requirements into consideration when making updates. Supplier shall not make any changes to a BC/DR Plan that increase RTOs or RPOs or that may otherwise reduce the effectiveness or timeliness of the recovery of Services following a BC/DR Event without Triple-S’s prior written consent.
| (g) | Performance of Business Continuity and Disaster Recovery Services. As part of the Business Continuity and Disaster Recovery Functions, Supplier will: |
| (i) | Fully execute the BC/DR Plan following a BC/DR Event; |
| (ii) | Perform any other unimpacted Services during a BC/DR Event; |
| (iii) | Use Commercially Reasonable Efforts to continue to perform any Services in accordance with the minimum acceptable levels of operation specified in the BC/DR Plan; |
| (iv) | Assess and define functional, performance, availability, maintainability and disaster recovery needs (e.g., support processes and procedures); |
| (v) | Propose functional, performance, availability, maintainability and disaster recovery requirements and establish standards (e.g., support processes and procedures); |
| (vi) | Perform education and awareness training related to the New BC/DR Plan for all Supplier Personnel; |
| (vii) | Upon cessation of the BC/DR Event, implement the activities necessary to restore the affected Services at the affected locations with the capabilities to meet the RTO and RPO requirements and other turnaround times set forth in this Schedule A and the BC/DR Plan; and |
| (viii) | Integrate Supplier’s disaster recovery and business continuity plans, procedures and capabilities with Triple-S's disaster recovery and business continuity plans, processes and procedures. |
| (h) | BC/DR Plan Testing. Supplier shall test the BC/DR Plan annually, and as otherwise reasonably necessary to comply with requirements of applicable Laws. Each business continuity and disaster recovery test (each such test a “BC/DR Drill”) shall comply with the following requirements: |
| (i) | Test the site emergency response plan in accordance with the BC/DR Plan; |
|
Triple-S / Supplier Confidential Page 12 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule A
Cross-Functional Services
| (ii) | If requested by Triple-S upon reasonable notice, reasonably integrate Supplier testing with Triple-S’s disaster recovery and business continuity testing for Triple-S customers and business partners, including by coordinating with third parties as such third parties relate to the Services; |
| (iii) | Provide a summary report of the BC/DR Drill results to Triple-S within thirty (30) days of the Drill’s completion. The report shall be no less detailed than similar information that Supplier provides to other customers similar to Triple-S for similar services; |
| (iv) | If material deficiencies are identified during the BC/DR Drill that may reasonably be expected to have a material adverse impact to the performance of Services, Supplier shall (A) include them in the summary report described above; (B) promptly provide a plan and timeline to correct them; (C) execute the plan and track and report progress against it to Triple-S; and (D) retest the BC/DR Plan (or New BC/DR Plan if the remediation involves accelerating migration to a new environment covered by the New BC/DR Plan) to determine if the deficiencies have been remediated; and |
| (v) | Notify Triple-S of a scheduled BC/DR Drill with respect to the BC/DR Plan via email at least thirty (30) days prior to the scheduled date, reasonably allowing Triple-S to observe or participate as applicable. In the event Supplier changes any such scheduled testing date, Supplier will send prompt notification of the change. |
| (i) | BC/DR Event Management. If Supplier experiences a BC/DR Event, Supplier shall provide the Services and other business continuity Functions in accordance with the BC/DR Plan. Supplier’s Functions shall include the following: |
| (i) | Promptly notifying the primary Triple-S contacts under the Agreement and other Triple-S personnel designated in the BC/DR Plan; |
| (ii) | Providing a single 24 hour per day, 365 day per year (24/365) point-of-contact with an alternative back-up point-of-contact with 24/365 availability for business continuity related communications and activities; |
| (iii) | If a BC/DR Event occurs at a primary site, promptly providing Triple-S with an initial assessment of the impact of the BC/DR Event and an estimated forecast of the time it will take to bring Supplier’s recovery site to operational status; |
| (iv) | Paying all travel and living expenses incurred by Supplier Personnel in the performance of Supplier’s responsibilities described in this Section 2.8; |
| (v) | Providing an assessment of the state of the Services periodically as outlined in the BC/DR Plan during the recovery process until Services are restored; |
|
Triple-S / Supplier Confidential Page 13 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule A
Cross-Functional Services
| (vi) | Meeting service levels and recovery timelines as established in the approved BC/DR Plan required during the BC/DR Event with relief from consequences (financial impact or otherwise) outside of Supplier control and within scope of services provided by third parties contracted directly to Triple-S and as set forth in Schedule B (Service Level Methodology); |
| (vii) | Performing a Root Cause Analysis of Incidents identified during a BC/DR Event; and |
| (viii) | Validating that the Services are functioning properly after recovering from a BC/DR Event. |
| 3 | EMBEDDED PROCESSES |
| 3.1 | General |
To the extent Supplier is responsible for performing a particular Function (either as identified in Section 2 of this Schedule A (Cross Functional Services) or in any SOW, then Supplier is responsible not only for performing the indicated Function, but also for providing the resources necessary to perform such Function and any other Functions and responsibilities described in this Section 3.1 as they may relate to such Function (the “Embedded Processes”).
| 3.2 | Embedded Processes |
The Embedded Processes include:
| (a) | Developing the procedures underlying the Function, subject to and in compliance with Triple-S regulatory requirements and in alignment with Triple-S Policies and Procedures as defined in Schedule J (Triple-S Policies and Procedures) and the requirements of this Agreement so as to enable the Services to function cohesively and in a coordinated manner; |
| (b) | Performing the required activities necessary to manage the Function, including (i) supervising and reporting, including reporting to other personnel within the Function, (ii) measuring and reporting on the performance of the Function in accordance with Schedule K (Reports); |
| (c) | Managing documents and data (including data acquisition, data entry, data recording and data distribution) related to the Function; |
| (d) | Coordinating with Triple-S business units as necessary to perform the Services; |
| (e) | Performing “self audits” of the Function, including testing the (i) accuracy, reliability and quality of work, (ii) compliance with approved policies and procedures, and (iii) performance and correction of any issues identified during such audits and reporting of self audit results; |
|
Triple-S / Supplier Confidential Page 14 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule A
Cross-Functional Services
| (f) | Participating in internal and external audits pursuant to Schedule M (Audit and Record Retention Requirements); |
| (g) | Engineering the Function, including performing those actions necessary to maintain or improve the underlying activities based on (i) then-current best practices, and (ii) how it is intended to interact with other activities performed by Supplier or by Triple-S; |
| (h) | Responding to reasonable queries and requests concerning activities associated with the performance of the Function, including making the applicable subject matter experts, documentation and other relevant content available as reasonably necessary to be responsive; |
| (i) | Interacting and coordinating as needed with Triple-S, including (i) integrating the Function with the activities of Triple-S such that the overall delivery of services is optimized (i.e., not sub-optimized within the confines of the Function), and (ii) monitoring the activities performed by Triple-S to mitigate negative impact on the Function; and |
| (j) | Providing reasonable support to Triple-S’s sales and marketing processes by responding to prospective or existing customer requests for proposals (RFPs), providing reasonable access to Supplier Facilities and Supplier Personnel as part of any prospective or existing customer requests (subject to Supplier Facility and Security Polices), and providing Triple-S with information concerning the Services or delivery of the Services as (i) reasonably requested by the prospective or existing customer, (ii) reasonably required by Triple-S for the purpose of responding to an RFP, or (iii) reasonably necessary to support the Triple-S sales and marketing process (e.g., sales pitches). Triple-S disclosure of any Supplier Confidential Information remains subject to Section 21.2(d) of the General Terms and Conditions. |
| 4 | RETAINED TRIPLE-S RESPONSIBILITIES |
Triple-S shall retain the following responsibilities:
| (a) | Information Sharing: |
| (i) | Provide access to operational reports applicable to Supplier’s performance of the Services from Triple-S Systems. |
| (b) | Procedures Manuals: |
| (i) | Assist with development of and provide input to the Procedures Manual; and |
| (ii) | Provide available Triple-S documents, policies and processes as reasonably requested by Supplier to assist in completion of the Procedures Manual. |
|
Triple-S / Supplier Confidential Page 15 |
MSA Schedule B
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
MASTER SERVICES AGREEMENT
SCHEDULE B
SERVICE LEVEL METHODOLOGY
| Schedule B | Triple-S / Supplier Confidential |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule B
Service Level Methodology
TABLE OF CONTENTS
| 1 | GENERAL PROVISIONS | 1 | |
| 1.1 | Definitions | 1 | |
| 1.2 | General | 2 | |
| 1.3 | Reporting of Performance Measures | 3 | |
| 2 | SERVICE LEVEL OBLIGATIONS | 4 | |
| 2.1 | Service Level Obligations | 4 | |
| 2.2 | Commencement of Service Level Obligations | 5 | |
| 2.3 | Interim Period | 5 | |
| 2.4 | Service Level Failures | 5 | |
| 2.5 | Excused Performance | 6 | |
| 3 | CHANGES TO SERVICE LEVELS | 7 | |
| 3.1 | Changes to Service Points | 7 | |
| 3.2 | Deletion of Service Levels | 8 | |
| 3.3 | Additions of Service Levels | 8 | |
| 3.4 | Minimum and Maximum Number of CPIs | 8 | |
| 3.5 | Initial Baselined Service Levels | 8 | |
| 3.6 | Additions of Regulatory Service Levels | 9 | |
| 3.7 | [***] Service Levels | 10 | |
| 4 | SERVICE LEVEL CREDITS | 11 | |
| 4.1 | Service Points | 11 | |
| 4.2 | Service Level Credit Calculation | 11 | |
| 4.3 | Service Credit Multipliers | 12 | |
| 4.4 | Service Level Credit Earn Back | 12 | |
| 4.5 | Notice and Payment of Service Level Credits | 13 | |
| 4.6 | Cumulative Remedies and Waivers | 13 | |
| 5 | CONTINUOUS IMPROVEMENT OF SERVICE LEVELS | 13 | |
| 6 | QUARTERLY REVIEW | 14 | |
|
Triple-S / Supplier Confidential Page i |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
SCHEDULE B
SERVICE LEVELS METHODOLOGY
This Schedule B (Service Level Methodology) to the Agreement provides the methodology by which Supplier’s performance of the Services will be monitored and measured in relation to certain quantitative Service Levels. This Schedule B also (a) defines such quantitative Service Levels that shall be provided in Exhibit(s) to each SOW (collectively, the “Service Level Metrics Documents”), (b) describes what constitutes a Service Level Failure, (c) describes the methodology for calculating Service Level Credits that Supplier will provide to Triple-S upon the occurrence of a Service Level Failure and such Service Level Failure is not excused pursuant to this Schedule B, and (d) describes the procedure for adding new Service Levels.
| 1. | General Provisions |
| 1.1 | Definitions |
The following capitalized terms when used in this Schedule shall have the meanings given below. Any capitalized terms used but not defined in this Schedule B (Service Level Methodology) will have meaning provided in Schedule AA (Glossary) or elsewhere in the Agreement.
| (a) | “At Risk Amount” means, for any month during the Term, [***] of the total Monthly Charges under the Agreement (excluding any taxes, reimbursements and pass through expenses) for such month. |
| (b) | “Baselined” means that the Service Level will be established using the process set forth in Section 3.5. |
| (c) | “Compliance Date” has the meaning given in Section 2.2. |
| (d) | “Escalator Credit” has the meaning given in Section 4.3. |
| (e) | “Interim Period” means the period of time beginning on the Compliance Date during which Supplier will be held to the Interim SLA. |
| (f) | “Interim SLA” means the Service Level effective during the Interim Period. |
| (g) | “Long Term SLA” means the Service Level effective upon expiration of the Interim Period. |
|
Triple-S / Supplier Confidential Page 1 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule B
Service Level Methodology
| (h) | “Measurement Window” means the periodic evaluation and reporting frequency for each individual Service Level as specified in the Service Level Metrics Documents (e.g., monthly, quarterly, semi-annually, annually). |
| (i) | “Root Cause Analysis” means the problem analysis process undertaken to identify and enumerate the underlying cause(s) of a Service Level Failure or some other failure, and to document the necessary corrective actions to be taken to prevent recurring problems or trends which could result in problems. |
| (j) | “Service Commencement Date” has the meaning given in Schedule AA (Glossary). |
| (k) | “Service Level” has the meaning given in Schedule AA (Glossary). |
| (l) | “Service Level Credit” means a monetary credit to Triple-S by Supplier upon the occurrence of a Service Level Failure of a Service Level after the Compliance Date for such Service Level and calculated in accordance with Section 4.2 of this Schedule B (Service Level Methodology). |
| (m) | “Service Level Failure” means Supplier’s failure after the applicable Compliance Date to meet a Service Level during the applicable Measurement Window pursuant to this Schedule B (Service Level Methodology) and the applicable Service Level Metrics Documents. |
| (n) | “Service Level Metric” shall mean the measurement value of Supplier’s required level of performance for the applicable Service Level. The Service Level Metrics are described in the Service Level Metrics Documents. |
| (o) | “Service Level Metrics Documents” has the meaning given in the Preamble to this Schedule B. |
| (p) | “Service Level Performance Report” has the meaning given in Section 1.3(a). |
| (q) | “Service Point” means a percentage point that is equal to one percent (1%) of the At Risk Amount and that is assigned in accordance with Sections 4.1 and 3.1. |
| (r) | “SLA Pool” has the meaning given in Section 4.1(a). |
| (s) | “[***] Service Level” means those Service Levels designated in Section 3.7 of this Schedule B for which Triple-S can terminate the Agreement pursuant to Section 16.1(d) of the General Terms and Conditions. |
| 1.2 | General |
| (a) | This Schedule B (Service Level Methodology) provides certain Service Levels against which Supplier’s performance of the Services shall be measured. Supplier shall perform the Services at or above the levels of performance indicated for the applicable Service |
|
Triple-S / Supplier Confidential Page 2 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule B
Service Level Methodology
Level as set forth in this Schedule B (Service Level Methodology) and the Service Level Metrics Documents.
| (b) | Supplier will provide and maintain all of the tools, processes, and capabilities that are necessary for measuring, monitoring and reporting Supplier’s performance with respect to the Service Levels. |
| (c) | Except as otherwise provided in the Service Level Metrics Documents, the Measurement Window for each Service Level will be a calendar month. Except as otherwise provided in the Service Level Metrics Documents, all references to “hour” or “hours” shall mean clock hours; all references to “day” or “days” shall mean calendar days (except where Business Days are expressly stated); all references to “month” shall mean calendar month; and all references to “year” shall mean calendar year. |
| 1.3 | Reporting of Performance Measures |
On or before each applicable Service Commencement Date, Supplier shall implement mutually agreed standard reporting procedures to report Supplier’s performance of the Services at a level of detail sufficient to verify Supplier’s compliance with the Service Levels. Triple-S has the right to audit all such reporting procedures in accordance with Schedule M (Audit and Record Retention Requirements).
| (a) | Throughout the Term of the Agreement and for the duration of any Disengagement Assistance Period, Supplier shall track its performance with respect to each Service Level and report the results to Triple-S in a monthly report the format, structure, and level of detail of which shall be agreed to by the Parties (the “Service Level Performance Report”). Without limiting the generality of the foregoing, the Service Level Performance Report shall include: |
| (i) | summary reporting for each Service Level; |
| (ii) | a comparison of Supplier’s performance during the Measurement Window being reported against Supplier’s performance during each of the Measurement Windows over the previous twelve (12) months (or if a Service Level has been measured for less than twelve (12) months, such time that the Service Level has been measured) with respect to each Service Level; |
| (iii) | with respect to each Service Level Failure: (A) a summary and description of each Service Level Failure; and the Root Cause Analysis with respect to each Service Level Failure; (B) associated trend analyses with respect to such Service Level Failures; (C) to the extent not already included in the Root Cause Analysis, a description of remedial and/or preventative measures taken or planned to be taken by Supplier in connection with such Service Level Failures and if remedial and/or preventative measures were taken in the past but the same Service Level Failure persists, the alternative measures to be taken; and (D) a |
|
Triple-S / Supplier Confidential Page 3 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule B
Service Level Methodology
calculation of the amount of the corresponding Service Level Credit Triple-S is entitled to receive in connection with each such Service Level Failure.
| (b) | Supplier shall deliver the Service Level Performance Report within thirty (30) days after the last day of each month. The Service Level Performance Report shall be in electronic form suitable for use on a personal computer in a MS Office format. Supplier shall provide a hard copy of the Service Level Performance Report to Triple-S upon request. |
| (c) | If any Service Level Performance Report does not contain a level of detail sufficient to allow Triple-S to reasonably determine whether Supplier has met or failed to meet a Service Level in the immediately preceding Measurement Window, Triple-S will notify Supplier of such failure and Supplier will provide such detail within ten (10) Business Days of such notice. If such additional detail does not sufficiently allow Triple-S to reasonably determine whether Supplier has met or failed to meet the applicable Service Level (including where Supplier fails to report upon its performance for a Service Level), a Service Level Failure shall be deemed to have occurred for such Service Level during the applicable Measurement Period. |
| (d) | Supplier shall provide reasonably detailed supporting information in connection with any Service Level Performance Report to Triple-S in electronic copy form suitable for use on a personal computer in a MS Office format accessible upon reasonable request by Triple-S. Supplier shall also provide Triple-S with on-line access to up-to-date problem management data and other data regarding the status of service problems, service requests, and user inquiries. |
| (e) | Supplier shall provide Triple-S with reasonable access to the data used by Supplier to calculate its performance against the Service Levels and the measurement and monitoring tools and procedures utilized by Supplier to generate such data for purposes of audit and verification. To ensure the ability to audit Service Level reporting, Supplier shall retain for the duration of the Term, and on request provide Triple-S with access (in accordance with Schedule M (Audit and Record Retention Requirements)) to, underlying data used for Service Level reporting and reasonably necessary for such verification, including manually created and machine generated data, together with records of all calculations or adjustments applied to such data as part of the reporting process. Triple-S shall not be required to pay any amount in addition to the Charges for access to Supplier’s measurement and monitoring tools or the resource utilization associated with their use. The Service Level Performance Reports, and any supporting data and information, will be considered the Confidential Information of each Party. |
| 2. | Service Level Obligations |
| 2.1 | Service Level Obligations |
The metrics, measurement standards, and other pertinent features for Service Levels are described in the Service Level Metrics Documents.
|
Triple-S / Supplier Confidential Page 4 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule B
Service Level Methodology
| 2.2 | Commencement of Service Level Obligations |
The “Compliance Date” for any Service Level means the date that Supplier first becomes obligated to meet or exceed the Service Level Metric for such Service Level. The Compliance Date for each Service Level shall be the later of (a) the applicable Service Commencement Date for SOW #1 (Claims Services) and SOW #2 (IT Services) or (b) if applicable, the date set forth in the Service Level Metrics Documents, subject to Section 3.5.
Claims within the Day One Backlog (as defined in Section 4.5 of Schedule B (Service Level Methodology) will be excluded from Service Level calculations under SOW #1 (Claims Services) for the first 60 days following completion of the Claims Transition.
Supplier will not be responsible for Service Level Credits prior to July 1, 2018 (notwithstanding that the Service Commencement Date is earlier than such date) with respect to Service Level Failures under SOW #1, except for [***] Service Levels [***] for which Service Level compliance will begin on the Service Commencement Date [***] Service Levels, the “Key Claims Transition SLAs”).
| 2.3 | Interim Period |
| (a) | The Service Level Metrics Documents may describe certain Service Levels for which there will be an Interim SLA. Supplier will be required to meet or exceed each such Interim SLA for the Interim Period (as measured from the Service Commencement Date) designated in the applicable Service Level Metrics Document, subject to Section 3.5. |
| (b) | If there is an Interim SLA specified, upon the conclusion of the applicable Interim Period, Supplier will be required to meet or exceed the corresponding Long-Term SLA designated in the applicable Service Level Metrics Document. |
| 2.4 | Service Level Failures |
Upon the occurrence of a Service Level Failure with respect to a Service Level, the following will apply:
| (a) | Supplier shall grant to Triple-S a Service Level Credit, calculated in accordance with Section 4.2, as applicable, |
| (b) | The Service Level Failure will be escalated to the Program Manager or his or her designee and the Governance Committee in accordance with Schedule F (Governance). |
| (c) | Supplier will promptly: |
| (i) | conduct a Root Cause Analysis to determine why such failure occurred (in not more than 48 hours); |
| (ii) | provide copies of the Root Cause Analysis to Triple-S, upon its request; |
|
Triple-S / Supplier Confidential Page 5 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule B
Service Level Methodology
| (iii) | prepare a formal written recovery plan designed to prevent the reoccurrence of such Service Level Failure; and |
| (iv) | once such recovery plan has been approved by Triple-S, implement such plan at Supplier’s sole cost and expense and in a mutually agreed timeframe. |
| 2.5 | Excused Performance |
| (a) | Supplier will not be excused from a failure to achieve a Service Level other than as provided in this Section 2.5. |
| (b) | Supplier shall be excused from a failure to meet a Service Level only if and to the extent |
| (i) | such failure was: |
| (A) | due to changes made by Triple-S, for which it has not provided reasonable notice to Supplier, in or to systems, technology, or data transmissions; |
| (B) | due to failure of third party systems or network connectivity that Triple-S is required to provide under this Agreement and that Supplier requires to provide the Services; provided (1) this excuse shall not apply to any Supplier Affiliates or Subcontractors; and (2) this excuse shall not apply to Managed Third Parties to the extent such failure is attributable to Supplier not performing is vendor management responsibilities under Schedule A (Cross Functional Services); |
| (C) | due to Supplier’s compliance with Triple-S’s written direction to perform the Services in a manner inconsistent with Supplier’s obligations (provided Supplier has notified Triple-S of such inconsistency and related impact on the Service Levels), including for Projects or Changes where the Parties have agreed to a Change Order or Task Order that noted that the Change or Project will likely or possibly result in a failure to meet a Service Level; |
| (D) | with respect to those Service Levels denoted as Volume-Sensitive Service Levels in the Service Level Metrics Documents, due to the volume to be processed by Supplier exceeding [***] (as defined in any applicable SOW), provided Supplier’s acts or omissions did not cause the volume to exceed such forecast (it being understood that omissions shall not include Supplier’s failure to process excess volumes if Triple-S determines not to pay additional Charges pursuant to Schedule C (Charging Methodology); |
| (E) | caused by circumstances that constitute a Force Majeure Event; provided, that Supplier has met its obligations for performing Disaster |
|
Triple-S / Supplier Confidential Page 6 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule B
Service Level Methodology
Recovery and business continuity services as described in this Agreement; or
| (F) | caused by circumstances described in Section 7.3 (Savings Clause) of the General Terms and Conditions; and |
| (ii) | Supplier: |
| (A) | promptly notified Triple-S of the applicable circumstances referenced in Section 2.5(b)(i); |
| (B) | used Commercially Reasonable Efforts to prevent, overcome, or mitigate the adverse effects of such failure and to perform its obligations notwithstanding such failure; and |
| (C) | complied with Section 2.5(c). |
| (c) | If Supplier wishes to avail itself of one of the clauses referenced in Section 2.5(b), then Supplier shall indicate in the Service Level Performance Report the following: |
| (i) | Each applicable Service Level that is subject to the Service Level Failure; |
| (ii) | For each applicable Service Level, the circumstances claimed by Supplier under Section 2.5(b); |
| (iii) | The calculation of the affected Service Level value, both with and without taking into account the effect of the clause concerned; and |
| (iv) | The circumstances and background data giving rise to the excuse, in reasonably sufficient detail to permit Triple-S to evaluate whether Supplier’s claim of excuse is valid. |
| (d) | Supplier will at all times bear the burden of proof as to the existence of an excuse and the applicability of the excuse to the Service Level Failure at issue, including during dispute resolution proceedings. |
| 3. | Changes to Service Levels |
| 3.1 | Changes to Service Points |
| (a) | Not more than [***], Triple-S has the right to provide written notice to Supplier to increase or decrease the then-current Service Points among one or more Service Levels; provided the total Service Points do not exceed the SLA Pool and all such changes remain subject to Section 4.1(a). |
|
Triple-S / Supplier Confidential Page 7 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule B
Service Level Methodology
| (b) | The changes will become effective 90 days after the agreement of the Parties (or on the first day of the next Measurement Window if the 90th day after such notice does not fall on the first day of the Measurement Window). |
| (c) | Certain Service Levels are designated as “Critical Performance Indicators” (or “CPIs”) and others as “Key Performance Indicators” (or “KPIs”). Triple-S may not allocate Service Points to any KPIs without Supplier’s consent. |
| 3.2 | Deletion of Service Levels |
Triple-S has the right to delete a Service Level by sending written notice to Supplier; provided, however, that Triple-S shall not be entitled to reallocate any Service Points except as set forth in Section 3.1 and all deletions remain subject to Section 3.4. A deletion of any Service Level shall be documented through the Change Control Process (but no Supplier consent shall be required).
| 3.3 | Additions of Service Levels |
Except as provided below in Section 3.6, the addition of new Service Levels will be subject to mutual agreement of the Parties.
| 3.4 | Minimum and Maximum Number of CPIs |
Notwithstanding anything in this Schedule B (Service Level Methodology) and except as mutually agreed by the Parties, there will be no fewer [***] CPIs at any time during the Term of the Agreement. If the Parties add new Services to this Agreement (e.g., a new SOW for call center services), the maximum number of CPIs shall be reasonably increased to accommodate the new Service Levels required for such new Services.
| 3.5 | Initial Baselined Service Levels |
For Service Levels that the Parties have designated in the Service Level Metrics Documents as Service Levels to be “baselined”, the Service Level will be established using the process set forth below. The Parties may, however, agree to extend the baselining period to account for seasonality and other factors.
Where historical data exists and reporting is available as of the Effective Date (“Existing Service Level”), the Interim SLAs will be established or validated (as applicable) prior to the Service Commencement Date using the process provided in Section 3.5(a). Where historical data exists and reporting is not available (“Newly Reported Service Level”), Supplier will develop the required reporting, and the Interim SLAs will be established or validated (as applicable) using the process provided in 3.5(a), prior to the Service Commencement Date. Where historical data does not exist for a Service Level (“New Service Level”), the Interim SLAs will be established or validated using the process provided in Section 3.5(b), with the baselining period commencing as soon as the Parties are able to begin measuring performance against the applicable New Service Levels. For clarification, the Long-Term Service Levels reflect levels negotiated by the Parties and are not subject to baselining under this Section 3.5 or otherwise. If Triple-S determines it has
|
Triple-S / Supplier Confidential Page 8 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule B
Service Level Methodology
historical data for a Service Level being baselined, the Parties will agree on the Service Level Metric and when to end the baselining period.
| (a) | For each Service Level for which there is at least six (6) months of historical data within the past nine (9) months and such data indicates performance that is acceptable to Triple-S, then the Service Level metric shall be the arithmetic mean of the most recent six (6) months of historical data, after excluding the highest and lowest monthly actual results during such period . For example, if the six (6) months of historical data are 99.85, 99.90%, 99.91, 99.92%, 99.93% and 99.95%, then the Service Level would be the arithmetic mean, after excluding the highest and lowest and monthly actual results during such period (99.915%) (calculated as ((99.90 + 99.91% + 99.92% + 99.93%) / 4). Such Service Level shall become effective as soon as the calculations above have been performed. |
| (b) | If the Parties agree to add a new Service Level for which at least six (6) months of historical data within the past nine (9) months does not exist, then such Service Level shall be baselined to determine the initial Service Level value in accordance with the following: |
| (i) | Supplier and Triple-S shall promptly meet to agree upon the tools and procedures to be used to measure such new Service Level. Upon such agreement, Supplier or Triple-S, as applicable, shall promptly implement such agreed upon tools and/or procedures and begin measuring the new Service Level. |
| (ii) | The “Baselining Period” for each such Service Level shall begin on the first day of the calendar month following the date upon which Supplier or Triple-S, as applicable, is capable of beginning to measure such Service Level using the agreed upon tools and procedures, and continue for six (6) months. The Parties may agree to extend the Baselining Period at any time. |
| (iii) | Supplier shall begin to measure its performance against each such Service Level commencing on the start date of the relevant Baselining Period, and shall report on its performance with respect to each such Service Level as provided in Section 1.3 or as otherwise agreed by the Parties. The Service Level level will be set using the formula provided in Section 3.5(a). |
| (iv) | Each such Service Level shall become effective (i.e., the Compliance Date will be) as soon as the calculations above have been completed. |
| 3.6 | Additions of Regulatory Service Levels |
Upon reasonable notice to Supplier (not less than [***] days or such shorter period as may be required by applicable Law), Triple-S may supplement or modify the Service Levels (provided that the Compliance Date for any such supplemented or modified Service Level will be [***] after the date of the change to enable Supplier to implement any required changes within such
|
Triple-S / Supplier Confidential Page 9 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule B
Service Level Methodology
period or (ii) such shorter period as may be required by applicable Law):
| (a) | To the extent there is a change to existing Laws or new Laws with which the Services are required to comply; |
| (b) | To the extent there is an updated interpretation of a Law with which the Services are required to comply; or |
| (c) | At the direction by a Regulator, or if there is a change in the enforcement or threshold by a Regulator. |
| 3.7 | [***] Service Levels |
Below are the [***] Service Levels as of the Effeictive Date. There will be no more than [***] Service Levels at any time. Any changes to the [***] Service Levels will be subject to mutual agreement of the Parties; provided that any change to the [***] Service Levels will only be effective [***] after the Parties agree to the change. Any Service Level with a Service Level Metric of 100% will not be a [***] Service Level. Any Service Level Failure of a Key Claims Transition SLA prior to July 1, 2018 will not count as a failure for determining whether Triple-S has the right to terminate pursuant to Section 16.1(c) of the General Terms and Conditions.
| SOW | Service Level # | Category | Service Level Name |
| SOW #1 - Claims | |||
| Claims | 1 | Claims | End to End Timeliness of Clean Claim Adjudication Process |
| Claims | 3 | Claims | Timeliness of Unclean Claim Adjudication (provided, performance must be below 99.5% in order for the failure to be counted for purposes of the termination right provided in Section 16.1(c)) |
| SOW #2 - IT | |||
| IT | 1 | Application Availability | Availability of Criticality 1 Applications |
| IT | 2 | Application Availability | Availability of Criticality 2 Applications |
| IT | 8 | Business to Business | Timely B2B File Execution - Criticality 1 |
|
Triple-S / Supplier Confidential Page 10 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule B
Service Level Methodology
| SOW | Service Level # | Category | Service Level Name |
| IT | 10 | IT Infrastructure | Production Server (OS Instance) Availability |
| IT | 13 | Network Availability | IT Network (Data Center and Triple-S Primary Facilities) |
| 4. | Service Level Credits |
| 4.1 | Service Points |
For the purposes of calculating Service Level Credits, Triple-S may apportion Service Points to the Service Levels, subject to the following:
| (a) | Subject to Section 3.1, Triple-S may apportion [***] Service Points (collectively, the “SLA Pool”) across the collection of all Service Levels included in the Service Level Metrics Documents; provided that (i) the maximum number of Service Points for any Service Level with a Service Level Metric of 100% shall not exceed [***] Service Points; and (ii) the maximum number of Service Points for any other particular Service Level shall not exceed [***] Service Points. |
| (b) | For clarity, each Service Point in the SLA Pool represents [***] of the At Risk Amount; provided, however, the aggregate amount in Service Level Credits recovered by Triple-S for any given month may not exceed the At Risk Amount in such month. |
| 4.2 | Service Level Credit Calculation |
With respect to a Service Level Failure, the applicable Service Level Credit will be computed in accordance with the following formula:
Service Level Credit = A x B
Where A is the At Risk Amount; and
Where B is the allocation of Service Points for the applicable Service Level;
For example only, assume that Supplier fails to meet the Service Level for a Service Level, the At Risk Amount is [***] of the Monthly Charges, and the Monthly Charges for the month in which the Service Level Failure occurred were [***]. Additionally, assume that the allocation of Service Points for such Service Level is [***]. The Service Level Credit due to Triple-S for such Service Level Failure would be computed as follows:
A (the At Risk Amount) is [***] which is [***];
|
Triple-S / Supplier Confidential Page 11 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule B
Service Level Methodology
Multiplied by B (the allocation of Service Points for such Service Level), which is [***] Service Points (or [***]);
Yields a Service Level Credit = [***]
In the event of multiple Service Level Failures due to a single incident occurring in a month, only the highest Service Level Credit resulting from such Service Level Failures will apply in such month.
| 4.3 | Service Credit Multipliers |
| (a) | If Supplier’s performance results in a Service Level Failure for the same Service Level [***], then upon the occurrence of the [***] and any additional Service Level Failure in the rolling six month period, the Service Level Credit [***] by [***] (an “Escalator Credit”). |
| (b) | For example, assume an At Risk Amount of [***] and that the applicable Service Level has [***] Service Points. If Supplier fails to meet or exceed such Service Level [***] times in a [***], then upon the occurrence of the [***] such Service Level Failure, the Escalator Credit shall be [***]. |
| 4.4 | Service Level Credit Earn Back |
| (a) | If, during the [***] period immediately following the Measurement Window of a Service Level Failure that generated a Service Level Credit, Supplier’s performance is greater than or equal to the applicable Service Level metric for each of such [***], then Supplier will earn back [***] of the applicable Service Level Credit associated with, and previously credited for, the Service Level Failure (a “Earn Back”), subject to the following: |
| (i) | A Earn Back shall not apply to the same Service Level more than [***]; and |
| (ii) | Supplier shall not be eligible for Earn Back for a Service Level Failure that involves performance that is more than [***] the required Service Level level. For example, if a Service Level requires 99.5% availability or 99.5% of claims to be processed within 1 hour, if availability is less than [***] of such claims are processed within 1 hour, Supplier would not be eligible to Earn-Back the Service Level Credit payable for the failure). |
| (b) | If Supplier fails to satisfy the requirements in Section 4.4(a), then Supplier shall not be capable of generating a Earn Back for that Service Level Credit. Earn Backs will be provided as set forth in Section 4.5 below. |
|
Triple-S / Supplier Confidential Page 12 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule B
Service Level Methodology
| 4.5 | Notice and Payment of Service Level Credits |
Supplier shall notify Triple-S in the Service Level Performance Report if Triple-S becomes entitled to a Service Level Credit. For each Service Level Credit that Triple-S is entitled to pursuant to this Schedule B (Service Level Methodology), Supplier will provide such Service Level Credit to Triple-S (less any Earn Backs for prior Service Level Failures) on the invoice following the applicable Service Level Performance Report at the end of the applicable Measurement Window. If there will be no further invoices, Supplier will pay the amount of the Service Level Credit (less any Earn Backs for prior Service Level Failures) to Triple-S within thirty (30) calendar days after the date of the last invoice.
| 4.6 | Cumulative Remedies and Waivers |
The exercise by Triple-S of its rights under this Schedule B (Service Level Methodology), including the right to receive Service Level Credits and receive payments for or interests, shall be without prejudice to its other rights or remedies under the Agreement or at law or equity, including Triple-S’s right to claim and collect damages and Triple-S’s right to terminate the Agreement in whole or in part in accordance with the Agreement. If Triple-S elects to waive in writing a Service Level Credit, such waiver will not be considered a waiver of the application of the Service Level Failure toward any termination rights set forth in the Agreement, unless otherwise expressly stated in such writing.
| 5. | Continuous Improvement of Service Levels |
The Service Levels designated by the Parties as being subject to continuous improvement in the Service Level Metrics Documents will be subject to a continuous improvement process that results in the adjustment of the Service Level Metrics. Such adjustment will be conducted on an [***] basis commencing [***] after each applicable Compliance Date. Such adjustments to the Service Levels will be formalized by making updates to the relevant Service Level Metrics Documents and will take effect [***] after the end of each measured year (“Service Level Improvement Date”) and be calculated as follows:
| (a) | Following each Service Level Improvement Date, each applicable Service Level Metric shall be reset to a value equal the outcome of the formula set forth in Section 5(b) below (as may be modified by Section 5(c)), provided that the result is better than the current Service Level standard. |
| (b) | The formula referenced in Section 5(a) shall calculate the output of the average of the [***] from the previous year. The Service Level will be reset by taking the [***], and dividing the sum of the results by [***]. For example, if the monthly results for the previous year were [***] the new Service Level would be [***] provided the existing Service Level is lower than [***]. |
| (c) | Notwithstanding Section 5(b) above, in no event shall any single improvement in a Service Level pursuant to Section 5(b) above exceed [***] and the then-current Service |
|
Triple-S / Supplier Confidential Page 13 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule B
Service Level Methodology
Level. (For example, if the Service Level being adjusted were [***], the maximum increase for that reset would be [***].
| (d) | The process described in this Section 5 will be performed utilizing the data collected over the immediately preceding [***] month period. |
| 6. | QUarterly Review |
During the first six (6) months following each Service Commencement Date and every calendar quarter thereafter, or at either Party’s request, Supplier and Triple-S will review the Service Levels and any proposed adjustments to them as appropriate pursuant to the Change Control Process to reflect any improved performance capabilities associated with advances in the technology and methods used to perform the Services or material changes in volumes and metrics used to determine the Service Levels. The Parties will also review any other considerations relating to the Service Levels raised by either Party. As part of this review process, the Parties may: (a) jointly determine and agree on the addition and/or removal of Service Levels, (b) jointly determine and agree to revisions to the results of the automatic continuous improvement adjustment developed for a particular Service Level pursuant to Section 5 above or jointly determine and agree to improve a particular Service Level not subject to the automatic continuous improvement adjustments of Section 5 above.
|
Triple-S / Supplier Confidential Page 14 |
Schedule C (Charging Methodology) (FEV)
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
MASTER SERVICES AGREEMENT
SCHEDULE C
CHARGING METHODOLOGY
| Schedule C | Triple-S / Supplier Confidential |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule C
Charging Methodology
TABLE OF CONTENTS
| 1. INTRODUCTION | 1 |
| 1.1 Overview of Charges | 1 |
| 1.2 General Terms | 1 |
| 2. DEFINITIONS | 1 |
| 2.1 Certain Definitions | 1 |
| 2.2 Other Terms | 5 |
| 3. TRANSITION AND TRANSFORMATION | 5 |
| 3.1 [***] Charges | 5 |
| 3.2 In-Flight Projects | 6 |
| 4. HEALTH PLAN CHARGES | 6 |
| 4.1 Membership Reports | 6 |
| 4.2 Charges | 7 |
| 4.3 Non-Restricted Members | 8 |
| 4.4 Member Categories and Mix | 8 |
| 4.5 Other Adjustments | 9 |
| 5. NON-HEALTH PLAN HOSTING SERVICES | 12 |
| 5.1 Fixed Charges | 12 |
| 6. APPLICATION SUPPORT SERVICES | 13 |
| 6.1 Application Support Pool | 13 |
| 6.2 Ongoing Operational Costs | 15 |
| 7. INFRASTRUCTURE PROJECTS | 15 |
| 7.1 Definitions | 15 |
| 7.2 Charges for BAU Activity | 16 |
| 7.3 Charges for Special Infrastructure Projects | 16 |
| 7.4 Infrastructure Project Management | 18 |
| 8. MATERIAL CHANGES | 18 |
| 8.1 Material Scope Change | 19 |
| 8.2 Triple-S Efficiency Initiatives | 20 |
| 8.3 Additional Terms | 21 |
| 9. TRANSFERRED CONTRACTS | 21 |
| 9.1 Transferred Contracts | 21 |
| 10. T&M RATES | 22 |
| 10.1 Rates | 22 |
| 10.2 Additional Terms | 22 |
| 11. ADDITIONAL TERMS RELATING FIXED FEES FOR HEALTH PLAN CHARGES | 23 |
| 12. TERMINATION CHARGES | 23 |
| 12.1 Termination Charges | 24 |
| 12.2 Mitigation of Charges | 24 |
| 13. RESERVED | 24 |
Triple-S / Supplier Confidential
Page i
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule C
Charging Methodology
| 14. OTHER CHARGES, CREDITS AND TERMS | 24 |
| 14.1 Financial Responsibility Matrix | 24 |
| 14.2 Inflation Adjustments for T&M Rates | 24 |
| 14.3 Inflation Adjustments for All Charges | 25 |
| 14.4 End User Support | 26 |
| 14.5 Pass-Through Expenses | 26 |
| 14.6 Incidental Expenses | 27 |
| 14.7 Taxes | 27 |
| 14.8 Benchmarking | 29 |
| 14.9 Currency | 30 |
| 14.10 New Services | 30 |
| 14.11 Remedial Services | 30 |
| 14.12 Disengagement Services | 30 |
| 14.13 Travel | 30 |
| 14.14 Service Level Credits | 31 |
| 14.15 [***] Pricing for Certain New Charges and Adjustments | 31 |
| 14.16 IT Inventory and Configuration | 31 |
| 15. INVOICING AND PAYMENT | 31 |
| 15.1 Invoicing | 31 |
| 15.2 Payment Due | 32 |
| 15.3 Accountability | 32 |
| 15.4 Proration | 32 |
| 15.5 Refundable Items | 32 |
| 15.6 Deductions | 32 |
| 15.7 Disputed Charges | 32 |
TABLE OF SCHEDULES
| Schedule C-1 | Charges |
| Schedule C-2 | T&M Rates |
| Schedule C-3 | Financial Responsibility Matrix |
| Schedule C-4 | Termination Charges |
| Schedule C-5 | TSS Transferred Contracts |
Triple-S / Supplier Confidential
Page ii
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
SCHEDULE C
CHARGING METHODOLOGY
| 1. | INTRODUCTION |
| 1.1 | Overview of Charges |
This Schedule C (Charging Methodology) describes the methodology for calculating the charges for the Services provided by Supplier to Triple-S under this Agreement. The charges consist of the following (collectively, the “Charges”):
| (a) | the charges for health plan Services in Section 4; |
| (b) | the charges for non-health plan hosting Services in Section 5; |
| (c) | the charges for Application Support Services in Section 6; |
| (d) | the charges for Infrastructure Projects in Section 7; |
| (e) | any Termination Charges payable under Section 12; |
| (f) | any Pass-Through Expenses payable under Section 14.3; and |
| (g) | any other charges, fees or other amounts or adjustments expressly set forth in this Schedule C (Charging Methodology), a Change Order, Future SOW, or Task Order executed by the Parties. |
| 1.2 | General Terms |
| (a) | There are no amounts other than the Charges defined in Section 1.1 payable by Triple-S under this Agreement. |
| (b) | If any service or offering that Supplier is obligated to provide under this Agreement is not measured by a specific Charge, the cost to Supplier of providing that service or offering is subsumed in the Charges hereunder and there shall be no separate charge for such service or offering. |
| (c) | Supplier was given an opportunity to perform due diligence on the Services prior to the Effective Date. Accordingly, except where expressly permitted under this Agreement, in no event will information or changes in circumstances discovered after the Effective Date serve as the basis for Supplier to adjust Charges or terms of this Agreement. |
| 2. | DEFINITIONS |
| 2.1 | Certain Definitions |
| (a) | “Application Development Project” means a Project to develop new applications and enhancements to existing applications and systems. |
Triple-S / Supplier Confidential
Page 1
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule C
Charging Methodology
| (b) | “Application Support Pool” has the meaning given in Section 6. |
| (c) | “Applications Support Services” means the following IT Processes (each of which is defined in Exhibit A-1-1 (Process Definitions) of SOW #2 (IT Services) when performed by Supplier on an In-Scope Application within the Health Plan Portfolio: |
| (i) | 1.4.1 - Delivery Strategy Development; |
| (ii) | 2.3.2 – Application Architecture Development; |
| (iii) | 2.6.3 – Solution Integration; |
| (iv) | 2.92 – Project Management; |
| (v) | 3.1.1 – Technical Requirements Definition; |
| (vi) | 3.1.3 – Solution Development; |
| (vii) | 3.1.4 – Resource Estimation; |
| (viii) | 3.3.1 – Software Design; |
| (ix) | 3.3.2 – Software Development; |
| (x) | 3.3.3 – Software Integration; |
| (xi) | 3.3.5 – Peer Review; |
| (xii) | 3.3.6 – Testing; |
| (xiii) | 3.4.2 – Environmental Integration Testing; |
| (xiv) | 3.5.3 – Business Systems (Functional) Support; |
| (xv) | 3.71. – Configuration; |
| (xvi) | 3.7.2 – Implementation; |
| (xvii) | 3.91. – Corrective Maintenance; |
| (xviii) | 3.9.2 – Adaptive Maintenance; |
| (xix) | 3.9.3 – Perfective Maintenance; |
| (xx) | 3.9.4 – Preventive Maintenance; |
| (xxi) | 3.11.2 – Problem Identification and Resolution; |
Triple-S / Supplier Confidential
Page 2
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule C
Charging Methodology
| (xxii) | 3.11.3 – Configuration Management Execution; |
| (xxiii) | 3.11.4 – Change Management Execution; and |
| (xxiv) | 3.11.5 – Release Management Execution. |
| (d) | “Contract Year” means each twelve (12) month period beginning on the first Service Commencement Date and each anniversary of such date. |
| (e) | “Change Control Process” has the meaning given in Schedule AA (Glossary). |
| (f) | “Change Order” has the meaning given in Section 3(a) of Schedule O (Change Control Process). |
| (g) | “Charges” has the meaning given in Section 1. |
| (h) | “Effective Date” has the meaning given in the first paragraph of the General Terms and Conditions. |
| (i) | “Financial Responsibility Matrix” has the meaning given in Section 14.1. |
| (j) | “Fixed Monthly Fee” means the fixed monthly fee provided in Schedule C-1 (Charges). |
| (k) | “Fixed PC & Life Charge” has the meaning given in Section 5.1(a). |
| (l) | “Fixed TSM Charge” has the meaning given in Section 5.1(b). |
| (m) | “Health Plan Charges” has the meaning given in Section 4. |
| (n) | “Health Plan Portfolio” means the In-Scope Applications designated to be part of the Health Plan Portfolio in Schedule X (Source of Truth) (as it may be updated by the Parties pursuant to Section 4.5(d)). |
| (o) | “Infrastructure” means the Equipment, network connectivity, and system software used or required (as applicable) to provide Services. |
| (p) | “Infrastructure Project” has the meaning given in Section 7. |
| (q) | “In-Scope Application” means a Triple-S application for which Supplier provides IT Services requested by Triple-S. The In-Scope Applications existing as of the Effective Date are listed in Schedule X (Source of Truth) and each designated to be part of the Health Plan Portfolio, PC & Life Portfolio or TSM Portfolio. |
| (r) | “In-Scope Member” means a Non-Restricted Member or a Restricted Member. |
| (s) | “Labor Costs” means the cost of Supplier Personnel required to provide Services. Labor Costs shall be determined using the T&M Rates. |
Triple-S / Supplier Confidential
Page 3
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule C
Charging Methodology
| (t) | “Law” has the meaning given in Schedule AA (Glossary). |
| (u) | “Material Change” has the meaning given in Section 5. |
| (v) | “Material Functionality”, as it relates to an In-Scope Application, means: |
| (i) | new end user functionality that (A) is added to an In-Scope Application through an applications development project requested by Triple-S; (B) is designated in advance as “Material Functionality” in the applicable Task Order for the Project; and (C) requires Supplier to purchase and maintain a substantial amount of additional ongoing compute capacity in order support the new functionality; or |
| (ii) | end user functionality that (A) is decommissioned or removed from an In-Scope Application; and (B) enables Supplier to reduce a substantial amount of existing compute capacity as a result of the decommissioning or removal. |
| (w) | “Material Scope Change” has the meaning given in Section 8.1(a). |
| (x) | “Member” means a person, enrollee, subscriber, dependent or other individual who is enrolled in and is eligible to receive services under a health care plan offered or administered by Triple-S or its Affiliates or other Service Recipient. |
| (y) | “Monthly Minimum Fixed Fee” has the meaning given in Section 11. |
| (z) | “Non-Restricted Member” means a Member for which Supplier provides Claims Services from outside of the United States or its territories, including Puerto Rico. |
| (aa) | “PC & Life Portfolio” means the In-Scope Applications designated to be part of the PC & Life Portfolio in Schedule X (Source of Truth) (as it may be updated by the Parties pursuant to Section 5.1(c). |
| (bb) | “PMPM Rates” means the per member per month rates provided in Schedule C-1 (Charges). |
| (cc) | “Productive Application Hour” means an hour of Productive Work performed by Supplier on Application Support Services authorized by Triple-S. |
| (dd) | “Productive Work” means productive work performed specifically for Triple-S or a Service Recipient, as appropriately recorded under a labor tracking system or other system acceptable to both Parties. Nonproductive time, including holidays, vacation time, sick leave or other personal time off, education, training, travel, administrative, expense accounting, and management time (e.g., Supplier’s internal meetings, internal reporting, expense accounting), internal Supplier process implementation work, and idle time between projects shall not be counted as Productive Work. Further, except as agreed to as part of a Project, any time spent by personnel in Supplier’s program management office or by any other personnel that perform administrative or account level management functions shall not be considered Productive Work. |
Triple-S / Supplier Confidential
Page 4
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule C
Charging Methodology
| (ee) | “Project” has the meaning given in Schedule N (Project Framework). |
| (ff) | “Restricted Member” means a Member, other than a Non-Restricted Member, whose Claims are processed using Triple-S’s [***] or HealthSuite claims processing platform hosted by Supplier under this Agreement. |
| (gg) | “Service Recipient” has the meaning given in Section 2.6 of the General Terms and Conditions. |
| (hh) | “Services” has the meaning given in Section 2.1(a) of the General Terms and Conditions. |
| (ii) | “T&M Rates” means the T&M Rates provided in Schedule C-2 (T&M Rates). |
| (jj) | “Transformation” has the meaning given in Section 12 of the General Terms and Conditions. |
| (kk) | “Transition” has the meaning given in Section 11 of the General Terms and Conditions. |
| (ll) | “TSM Portfolio” means the In-Scope Applications designated to be part of the TSM Portfolio in Schedule X (Source of Truth) (as it may be updated by the Parties pursuant to Section 5.1(c). |
| (mm) | “TSS Membership Report has the meaning given in Section 3. |
| 2.2 | Other Terms |
Capitalized terms used in this Schedule C (Charging Methodology) but not defined herein have the meanings given in the Glossary attached as Schedule AA (Glossary) or elsewhere in this Agreement.
| 3. | TRANSITION AND TRANSFORMATION |
| 3.1 | [***] Charges |
| (a) | General Rule. There are [***] payable by Triple-S for the Transition or Transformation. Supplier [***]. |
| (b) | Clarification. The IT Solution provided in Exhibit A-2 (IT Solution) provides for an Assessment of the Triple-S environment and for Supplier to make certain recommendations for improvements and other details about the final Solution to be implemented by Supplier. Where Supplier is required to “recommend” particular solutions to Triple-S, Supplier’s obligation includes making a reasonable recommendation to achieve the objectives of SOW #2, work in good faith with Triple-S to agree on the details of the recommended solution, [***]. |
| (c) | Shift of Financial Responsibility. Schedule X (Source of Truth) identifies the date by which each In-Scope Application is expected to transition from the Triple-S data center |
Triple-S / Supplier Confidential
Page 5
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule C
Charging Methodology
to a Supplier Facility (“Assumed Migration Date”). Without limiting Supplier’s obligations under Section 12.2 of the General Terms and Conditions, if one or more of these In-Scope Applications is not migrated to a Supplier Facility by the Assumed Migration Date (subject to Section 7.3 of the General Terms and Conditions), then beginning on such date, Supplier shall: (i) continue to provide Services in support of the In-Scope Application from the Triple-S data center or other facility agreed by the Parties; (ii) provide Triple-S with a payment in an amount equal to Triple-S’ documented costs (including internal costs, external out-of-pocket costs and depreciation of remaining NBV) for facilities, personnel, third party Equipment, Software, services and other operational costs that would not have been incurred if the In-Scope Application had been migrated to a Supplier Facility prior to the applicable Assumed Migration Date. If such Equipment or Software needs to be refreshed, or if additional Equipment or Software is required, in order to provide the Services and meet the Service Levels for such In-Scope Applications, then Supplier will purchase or license such Equipment or Software directly.
| 3.2 | In-Flight Projects |
Supplier shall assume responsibility for the In-flight Projects denoted as being Supplier’s responsibility (as defined in Schedule P (In-Flight Projects)) beginning on the Effective Date and shall complete them. Services that are Applications Support Services will count against the Application Support Pool. Services that are Special Infrastructure Projects will count against the Special Infrastructure Project Pool. Services for other Services necessary to complete the In-Flight Projects (including Infrastructure Projects that are not designated in Schedule P as Special Infrastructure Projects) will be performed by Supplier as BAU Activity.
| 4. | HEALTH PLAN CHARGES |
This Section 4 describes certain charges that shall be determined based on the number of Members (“Health Plan Charges”). The Health Plan Charges shall compensate Supplier for providing (a) Claims Services for Non-Restricted Members; (b) hosting and other Infrastructure support for the Health Plan Portfolio; (c) the Application Support Pool; and (d) all other IT Services not expressly covered by another charging methodology described in this Schedule C (Charges).
| 4.1 | Membership Reports |
The Health Plan Charges shall be determined each month as follows:
| (a) | Triple-S will provide Supplier with a report that specifies the number of In-Scope Members (with detail showing the volume of Non-Restricted Members and Restricted Members) that were receiving the benefit of the Services as of the 10th day of each month (“TSS Membership Report”) by the 15th day of such month. In addition, with each TSS Membership Report, Triple-S shall provide an update to the data reported on the TSS Membership Report from three months prior that reflects any retroactive additions or removals of In-Scope Members by Triple-S (“True-Up TSS Membership Report”). For example, by the 15th day of April, Triple-S will provide the volume of In- |
Triple-S / Supplier Confidential
Page 6
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule C
Charging Methodology
Scope Members existing on April 10 for the TSS Membership Report and the volume of In-Scope Members existing on January 10 (after retroactive adds/removals are made) for the True-Up TSS Membership Report). The TSS Membership Report will be used to determine monthly charges under Section 4.1(b); the True-Up TSS Membership Report will be used to “true-up” those Charges under Section 4.1(c).
| (b) | At the end of each month, the Health Plan Charges provided in Schedule C-1 (Charges) will be applied based on the volume of Restricted Members and Non-Restricted Members for the month in the TSS Membership Report, as further described in this Section 4. |
| (c) | At the end of each quarter, the Health Plan Charges that were determined in each of the months that were four, five and six months prior will be recalculated based on the In-Scope Membership in the True-Up TSS Membership Reports, and an additional charge or credit will be applied to the current months’ Charges to reflect such recalculated Charges. |
Example: By the end of January, Triple-S will provide the In-Scope Membership as it existed on January 10. Supplier will invoice Triple-S for the Health Plan Charges in early February based on such report. The same reporting and invoicing process will occur in each subsequent month. At the end of June, the Health Plan Charges will be recalculated for (i) January using the True-Up TSS Membership Report provided in April (i.e., to reflect the number of In-Scope Members for January as reported in April after retroactive adds and removals are made); (ii) February using the True-Up TSS Membership Report provided in May; and (iii) March using the True-Up TSS Membership Report provided in June. Any additional Charges or credits required as a result of the true-up above will be applied on the July invoice. At the end of September, the same true-up process would occur for the Health Plan Charges invoiced in April, May and June.
| 4.2 | Charges |
The Health Plan Charges consist of the following:
| Number of In-Scope Members | Charges |
| [***] | [***] |
| [***] | [***] |
| [***] | [***] |
| [***] | [***] |
| [***] | [***] |
For clarification, except where variable incremental fees are noted above, the Fixed Monthly Fees are not subject to adjustment [***].
Triple-S / Supplier Confidential
Page 7
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule C
Charging Methodology
| 4.3 | Non-Restricted Members |
The volume tiers and corresponding Charges in Section 4.2 count and include both Restricted Members and Non-Restricted Members, subject to the following:
| (a) | Each month, for purposes of determining Charges payable under Section 4.2: |
| (i) | The first [***] Restricted Members shall count as “In-Scope Members”; |
| (ii) | The next [***]Restricted Members shall not count as “In-Scope Members” (i.e., Supplier will provide IT Services in support of them but they will be excluded from In-Scope Member counts when determining Charges); and |
| (iii) | Each Restricted Member above [***] shall count as an “In-Scope Member”. |
| (b) | Additionally, if Triple-S acquires new In-Scope Members through a merger or acquisition, including acquisition of a new Triple-S Affiliate that becomes a Service Recipient: |
| (i) | Such new Members that meet the definition of Non-Restricted Member will be counted for purposes of determining Charges payable under Section 4.2 as soon as they meet such definition. |
| (ii) | For such new Members that meet the definition of Restricted Member, Supplier will provide IT Services in support of them but they will be excluded from the “In-Scope Member” counts for purposes of determining the Charges payable under Section 4.2 until the earlier of (A) [***] following the date they become Restricted Members under this Agreement; and (B) the date they become Non-Restricted Members. |
| (iii) | For clarification, new Members that do not meet the definition of Restricted Members or Non-Restricted Members (e.g., Members that receive processing on a platform not supported by Supplier) are not counted as In-Scope Members for purposes of determining Charges under Section 4.2. |
| 4.4 | Member Categories and Mix |
The Fixed Monthly Fees and the PMPM Rates shall compensate Supplier for providing the Services for all types of existing and new Non-Restricted Members for which Triple-S may request Services during the Term. The addition or removal of Members within any Triple-S line of business through organic growth, merger or acquisition or otherwise (e.g., Medicaid, Medicare, Commercial) shall not result in a change to the Health Plan Charges other than through the adjustments described in this Section 4.
Triple-S / Supplier Confidential
Page 8
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule C
Charging Methodology
| 4.5 | Other Adjustments |
| (a) | Claims Volumes in Excess of Forecast. If the volume of Claims to be processed by Supplier pursuant to SOW #1 exceeds [***] of a Binding 2 Month Forecast (as defined in SOW #1) in a month (such amount in excess of this [***] threshold, a “Monthly Claims Backlog”), at Triple-S’ option (i) Supplier will use Commercially Reasonable Efforts to process the Monthly Claims Backlog using available Supplier Personnel capacity and no additional Charges shall apply (at a minimum this shall include using any capacity below the [***] threshold in subsequent months – e.g., if the actual volume of Claims in a subsequent month is at 100% of forecast, Supplier will use the remaining [***] of capacity below the [***] threshold to process backlog from prior months); or (ii) Supplier will add supplemental Supplier Personnel on a temporary basis to process the Monthly Claims Backlog more quickly and the Charges for such supplemental Supplier Personnel will be determined using the T&M Rates. Any Claims that require reprocessing as a result of Supplier’s acts or omissions shall be excluded from Claims volumes used to determine if there is a Monthly Claims Backlog. |
| (b) | Day One Claims Backlog. The Health Plan Charges include Supplier processing up to [***] Claims within the Day One Backlog within [***] of Supplier’s completion of the Claims Transition. “Day One Backlog” means Triple-S’s backlog of Claims that have not been processed by or on behalf of Triple-S prior to completion of the Claims Transition. If Triple-S desires, at its option, for Supplier to process additional Claims in the Day One Backlog, Supplier will add supplemental Supplier Personnel on a temporary basis to process the Day One Backlog more quickly and the Charges for such supplemental Supplier Personnel will be determined using the T&M Rates. |
| (c) | MCPM. |
| (i) | Supplier has established a baseline calculation of manual Claims per member per month using Triple-S information as of the Effective Date, calculated based on total Claims, auto-adjudication rates, and Claims re-work rates according to the methodology set forth in Section 4.5(c)(ii) below (“MCPM”). For purposes of calculating MCPM, Supplier will use (A) [***]. |
| (ii) | As of the Effective Date, the MCPM is: |
| Key Stats (LTM): | Reference | ||
| 1 | Average Membership | [***] | From Data |
| 2 | Claims per member per month | [***] | From Data |
| 3 | Avg. Monthly Claims | [***] | (1)*(2) |
| 4 | Blended Auto Adjudication Rate | [***] | From Data |
| 5 | Avg. Manual Claims per Month | [***] | (3)*[100%-(4)] |
| 6 | Adjustment Rate per Member | [***] | From Data |
| 7 | Avg. Adjustments per Month | [***] | (1)*(6) |
| 8 | Avg. Manual Monthly Claims | [***] | (5)+(7) |
| 9 | Manual claims per member per month | [***] | (8)/(1) |
| 10 | [***] | [***] | (9)*[***] |
| 11 | [***] | [***] | (9)*[***] |
Triple-S / Supplier Confidential
Page 9
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule C
Charging Methodology
| (iii) | Based on the MCPM calculated as of the Effective Date, Supplier will establish a [***]. At the end of each quarter during the Term, Supplier will calculate [***] in each of the three months of such quarter. Any “Manual Monthly Claims” resulting from Supplier’s acts or omissions shall be excluded from the MCPM calculation (e.g., if an adjustment is required as a result of a Supplier processing error, that adjustment shall be excluded from the MCPM calculation). If [***], then, Supplier will calculate and apply an additional charge or a credit to Triple-S as follows: |
| (A) | Step 1: Determine the [***]. |
| (B) | Step 2: Determine the [***]: |
[***]
C = the applicable Cost per Claim (as defined below).
| (C) | Supplier will apply the [***] the quarter. |
| (D) | For purposes of calculating any change, [***] during such quarter. (i) [***]. |
| (E) | At the end of each month, Supplier shall provide reporting to enable Triple-S to validate the MCPM calculations, including a report of each of the “Key Stats” listed in Section 4.5(b)(ii) above. At the end of each month [***], Supplier shall also provide a report showing information used in calculating the Average Manual Claims Processed per Hour (including total manual Claims processed and total Productive Hours for Claims Agents used by Supplier to perform Services in the month). |
| (iv) | Example: |
[***]:
[***]
| (v) | Long-Term Trends: If there [***], the Parties agree to renegotiate the Fixed Monthly Fees and PMPM Rates to reflect such long-term trend. Any such renegotiation will require agreement by both Parties and will be “cost neutral” – meaning the renegotiated Fixed Monthly Fees and PMPM Rates should in the aggregate be equal to the existing fees and rates as adjusted above for [***] (which calculation will be based on (i) the membership mid-point for each tier, and (ii) [***] membership for the minimum membership tier). |
Triple-S / Supplier Confidential
Page 10
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule C
Charging Methodology
| (d) | Adjustments to Health Plan Portfolio. |
| (i) | Except for changes that relate to a change to (or addition of) an In-Scope Application agreed to by the Parties in the Schedule X (Source of Truth), if Triple-S (1) adds a new Application to the Health Plan Portfolio, or (2) adds Material Functionality to an existing Application in the Health Plan Portfolio that requires a material change in the Infrastructure required to support such Application, which Triple-S must do pursuant to the Change Control Process, then: |
| (A) | Supplier shall propose a staffing and Infrastructure plan showing the incremental Supplier Personnel and Infrastructure required to support the new or modified Application. |
| (B) | Supplier will categorize charges associated with the new or modified Application as one-time charges or ongoing charges (which will be further categorized as fixed or variable). |
| (C) | After the incremental staffing and Infrastructure is determined and the charges are categorized: |
| (a) | Triple-S shall pay for one-time charges using the Special Infrastructure Projects Pool (if available) or using the T&M Rates; |
| (b) | Triple-S shall pay for fixed ongoing charges as a separate line item on the invoices; and |
| (c) | For ongoing charges that are variable, the Parties shall equitably adjust the Health Plan Charges to reflect the additional staffing and Infrastructure, which adjustment shall not exceed an amount equal to [***]. |
| (ii) | Except for changes that relate to a change to an In-Scope Application agreed to by the Parties in the Schedule X (Source of Truth), if Triple-S (1) removes an existing Application from the Health Plan Portfolio, or (2) removes Material Functionality from an existing Application in the Health Plan Portfolio that allows for a material reduction in the Infrastructure required to support such Application, which Triple-S must do pursuant to the Change Control Process, then: |
| (A) | Supplier shall propose a revised staffing and Infrastructure plan showing the reduction in Supplier Personnel and Infrastructure required to support the reduced workload. |
| (B) | After the revised staffing and Infrastructure is determined, the Parties shall equitably adjust the Health Plan Charges to reflect the revised staffing, which adjustment shall equal [***]. |
Triple-S / Supplier Confidential
Page 11
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule C
Charging Methodology
| (iii) | Patches, enhancements and other modifications to the existing Applications in the Health Plan Portfolio shall [***] in connection with the addition or removal of Material Functionality. |
| (iv) | Upon request in connection with the processes in Sections 4.5(d)(i) through 4.5(d)(ii), Supplier shall provide Triple-S with reasonable supporting detail from Supplier’s estimating tools to allow Triple-S to understand and validate Supplier’s proposed changes. |
| 5. | NON-HEALTH PLAN HOSTING SERVICES |
This Section 5 provides the Charges payable for Services Supplier provides in support of the PC & Life Portfolio and TSM Portfolio.
| 5.1 | Fixed Charges |
| (a) | Fixed PC & Life Portfolio Charge. Schedule C-1 (Charges) provides a fixed monthly charge payable by Triple-S for all Services provided in support of the PC & Life Portfolio (“Fixed PC & Life Charge”). |
| (b) | Fixed TSM Hosting Portfolio Charge. Schedule C-1 (Charges) provides a fixed monthly charge payable by Triple-S for all Services provided in support of the TSM Portfolio (“Fixed TSM Charge”). |
| (c) | Adjustments to Fixed Charges. |
| (i) | If Triple-S (1) adds a new Application to the PC & Life Portfolio or the TSM Portfolio, or (2) adds Material Functionality to an existing Application in the PC & Life Portfolio or the TSM Portfolio that requires a material change in the Infrastructure required to support such Application, which Triple-S must do pursuant to the Change Control Process, then: |
| (A) | Supplier shall propose a staffing and Infrastructure plan showing the incremental Supplier Personnel and Infrastructure required to support the new or modified Application. |
| (B) | After the incremental staffing and Infrastructure is determined, the Parties shall equitably adjust the Fixed PC & Life Charge or Fixed TSM Charge (as applicable) to reflect the additional staffing and Infrastructure, which adjustment shall not exceed an amount equal to (i) the number of incremental FTEs in the revised staffing multiplied by the applicable T&M Rates provided in Schedule C-2 (T&M Rates); and (ii) Supplier’s reasonable cost of providing such additional Infrastructure. |
| (ii) | If Triple-S (1) removes an existing Application from the PC & Life Portfolio or the TSM Portfolio, or (2) removes Material Functionality from an existing Application in the PC & Life Portfolio or the TSM Portfolio that allows for a |
Triple-S / Supplier Confidential
Page 12
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule C
Charging Methodology
material reduction in the Infrastructure required to support such Application, which Triple-S must do pursuant to the Change Control Process, then:
| (A) | Supplier shall propose a revised staffing and Infrastructure plan showing the reduction in Supplier Personnel and Infrastructure required to support the reduced workload. |
| (B) | After the revised staffing and Infrastructure is determined, the Parties shall equitably adjust the Fixed PC & Life Charge or Fixed TSM Charge (as applicable) to reflect the revised staffing, which adjustment shall equal (i) the FTEs reduced multiplied by the applicable T&M Rates provided in Schedule C-2 (T&M Rates) unless the Parties agree otherwise; and (ii) reductions in Supplier’s cost as a result of the removal of such Infrastructure. |
| (iii) | Patches, enhancements and other modifications to the existing Applications in the PC & Life Portfolio and TSM Portfolio shall [***] connection with the addition or removal of Material Functionality. |
| (iv) | Upon request in connection with the processes in Sections 5.1(c)(i) through 5.1(c)(ii), Supplier shall provide Triple-S with reasonable supporting detail from Supplier’s estimating tools to allow Triple-S to understand and validate Supplier’s proposed changes. |
| 6. | APPLICATION SUPPORT SERVICES |
This Section 6 describes how the Charges for Applications Support Services shall be determined.
| 6.1 | Application Support Pool |
| (a) | Pool Hours. The Health Plan Charges include the provision of the following pool of Productive Application Hours that shall be used by Supplier to perform Applications Support Services (“Application Support Pool”): |
| Application Support Pool | |
| Contract Year 1 | [***] hours |
| Contract Year 2 | [***] hours |
| Contract Year 3 | [***] hours |
| Contract Year 4 and each Contract Year thereafter | [***] hours |
| (b) | Use of Hours. |
| (i) | The hours in the Application Support Pool shall be applied against all Productive Application Hours worked by Supplier in a Contract Year (regardless of location or skill-set required) until the Application Support Pool is reduced to zero. |
Triple-S / Supplier Confidential
Page 13
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule C
Charging Methodology
| (ii) | The Parties expect that Supplier will perform application maintenance Services such that Triple-S has at least [***] available for discretionary applications development projects. |
| (c) | Reporting. Supplier shall provide monthly reports showing: |
| (i) | the number of Productive Application Hours worked each month (“Monthly Hours Report”), including: |
| (A) | identification of all individual timekeepers that charge hours against the Application Support Pool (including location and position); |
| (B) | number of hours charged by each such timekeeper; |
| (C) | reasonably detailed descriptions of the Applications Support Services performed by each timekeeper; |
| (D) | number of hours allocated to application maintenance (vs. discretionary development projects); |
| (E) | number of hours charged against each Applications Development Project; and |
| (ii) | a rolling three-month forecast of how Productive Application Hours are estimated to be allocated going forward. |
| (d) | Hours in Excess of Pool. If Productive Application Hours in excess of the Application Support Pool are required to perform the Application Support Services: |
| (i) | Supplier shall provide Triple-S with reasonable advance notice of the additional hours required, including the information required in the Monthly Hours Report defined above and the T&M Rates applicable to each individual identified in the Monthly Hours Report; and |
| (ii) | Supplier may charge Triple-S for additional Productive Application Hours approved by Triple-S in advance and in writing on a time and materials basis using the T&M Rates. |
| (e) | Forecasting and Carry-Forward of Application Support Pool Hours. |
| (i) | Sixty (60) days prior to the start of each Contract Year, Triple-S will allocate the Application Support Pool for the Contract Year between the first and second six (6) month periods. Triple-S may update its forecast to move hours allocated to the second six (6) month period into the first six (6) month period by providing ninety (90) days’ notice to Supplier. Triple-S’ initial allocation of hours (as it may be adjusted as provided above) may not result in an allocation of more than [***]. |
Triple-S / Supplier Confidential
Page 14
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule C
Charging Methodology
| (ii) | If Triple-S does not use [***] of the Application Support Pool hours in a [***] period forecast (as it may be adjusted above), the unused portion of the Application Support Pool for such period will be added to the Application Support Pool in the following [***] period; provided, no more than [***] of the original baseline amount (i.e., excluding any hours carried forward from a prior period) of Application Support Pool hours from the immediately preceding[***] period may be carried forward to the next [***] period under this Section 6.1(e) unless Triple-S was unable to use Application Support Pool dollars due to Supplier’s failure to make sufficient Supplier Personnel with appropriate skill sets available to perform Projects requested by Triple-S. |
| (f) | Project Management. All Applications Development Projects shall be initiated, defined, approved in writing by Triple-S, performed and accepted in accordance with the process described in Schedule N (Project Framework). Triple-S shall not be responsible for Charges (and dollars shall not be debited from the Application Support Pool) for Applications Development Projects that are not approved by Triple-S in writing in accordance with such process. |
| (g) | Additional Terms. Supplier shall not charge (or count against the Application Support Pool): |
| (i) | any hours worked to perform Services required by the Transition or Transformation; or |
| (ii) | any hours worked on an Infrastructure Project or other Services that are not Applications Support Services; or |
| (iii) | any hours to correct errors or other issues caused by Supplier Personnel. |
| 6.2 | Ongoing Operational Costs |
Each Party shall be responsible for implementing and providing on an ongoing basis all additional Equipment, Software, network connectivity, and facilities that may be required to support Applications Projects in the manner set forth in the Financial Responsibility Matrix. Supplier is fully compensated for the resources it provides in this regard through the Health Plan Charges, Fixed PC & Life Charge and Fixed TSM Charge, as they may be adjusted as expressly provided in this Schedule C.
| 7. | INFRASTRUCTURE PROJECTS |
This Section 7 describes how the charges for Projects (other than Application Development Projects) (“Infrastructure Projects”) shall be determined.
| 7.1 | Definitions |
| (a) | “Special Infrastructure Project” means an Infrastructure Project that (i) is requested by Triple-S; and (ii) is intended to (A) implement new technologies, business functions, software, tools, business processes or to change the IT architecture or (B) modify the |
Triple-S / Supplier Confidential
Page 15
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule C
Charging Methodology
Infrastructure used to support the In-Scope Applications to enable Triple-S to comply with a change in Applicable Law enacted after the Effective Date, in each case excluding all BAU Activities that may be required in connection with the Infrastructure Project.
| (b) | “BAU Activity” means: |
| (i) | any Services that do not meet the definition of “Project”; |
| (ii) | any Services or related activities required for Supplier to execute the Transition or Transformation, and otherwise implement the Infrastructure, solution and functionality described in the scope and solution documents attached to the IT SOW; |
| (iii) | any Services that Supplier is required to perform under SOW #1 (Claims Services) or SOW #2 (IT Services) |
| (iv) | any IMACs (including end user IMACs and network IMACs); |
| (v) | any Services covered by a Service Level or required to meet Service Levels (e.g., performing break-fix, capacity management, database index maintenance); |
| (vi) | labor required to provision new Equipment and Software or to refresh existing Equipment and Software; |
| (vii) | labor required to manage project work to be performed by Managed Third Parties (e.g., projects performed by Managed Third Parties requiring modifications or upgrades to software); and |
| (viii) | any Services that Supplier is required to perform under this Agreement in the absence of a specific request from Triple-S for Supplier to perform them (i.e., only ad hoc work specifically requested by Triple-S can be a Special Infrastructure Project). |
| 7.2 | Charges for BAU Activity |
There are no additional amounts payable for Projects that include BAU Activity. Supplier is compensated for these Projects through the Fixed Fees and Health Plan Charges, Fixed PC & Life Fee and Fixed TSM Fee.
| 7.3 | Charges for Special Infrastructure Projects |
| (a) | Pool Hours. The Health Plan Charges include the provision of the following pool of Productive Hours that shall be used by Supplier to perform Special Infrastructure Projects (“Special Infrastructure Projects Pool”): |
Triple-S / Supplier Confidential
Page 16
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule C
Charging Methodology
| Special Infrastructure Project Pool (Hours) | |
| Contract Year 1 (first 6 months) | [***] |
| Contract Year 1 (second 6 months) | [***] |
| Contract Year 2 (first 6 months) | [***] |
| Contract Year 2 (second 6 months) | [***] |
| Contract Year 3 (first 6 months) | [***] |
| Contract Year 3 (second 6 months) | [***] |
| Contract Year 4 (first 6 months) | [***] |
| Contract Year 4 (second 6 months) | [***] |
| Contract Year 5 and each year thereafter during the Term (first 6 months) | [***] |
| Contract Year 5 and each year thereafter during the Term (first 6 months) | [***] |
| (b) | Use of Hours. The hours in the Special Infrastructure Project Pool shall be applied against Productive Hours worked by Supplier on Special Infrastructure Projects in a Contract Year (regardless of location or skill-set required) until the Special Infrastructure Project Pool is reduced to zero. |
| (c) | Reporting. Supplier shall provide monthly reports showing: |
| (i) | the number of Productive Hours worked each month on Special Infrastructure Projects (“Monthly Infrastructure Hours Report”), including: |
| (A) | identification of all individual timekeepers that charge hours against the Special Infrastructure Project Pool (including location and position); |
| (B) | number of hours charged by each such timekeeper; |
| (C) | reasonably detailed descriptions of the work performed by each timekeeper; and |
| (D) | number of hours charged against each Special Infrastructure Project; and |
| (ii) | a rolling three-month forecast of how Productive Hours are estimated to be allocated going forward for Special Infrastructure Projects. |
| (d) | Hours in Excess of Pool. If Productive Hours in excess of the Special Infrastructure Project Pool are required to perform Special Infrastructure Projects: |
| (i) | Supplier shall provide Triple-S with reasonable advance notice of the additional hours required, including the information required in the Monthly Infrastructure Hours Report defined above and the T&M Rates applicable to each individual identified in the Monthly Infrastructure Hours Report; and |
Triple-S / Supplier Confidential
Page 17
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule C
Charging Methodology
| (ii) | Supplier may charge Triple-S for additional Productive Hours approved by Triple-S in advance and in writing on a time and materials basis using the T&M Rates. |
| (e) | Carry-Forward. If Triple-S does not use [***] of the Special Infrastructure Projects Pool hours in a [***] period, the unused portion of the pool for such period will be added to the Special Infrastructure Projects Pool in the following[***] period; provided, no more than [***] of the original baseline amount (i.e., excluding any hours carried forward from a prior period) of pool hours from the immediately preceding [***] period may be carried forward to the next [***] period under this Section unless Triple-S was unable to use Special Infrastructure Project Pool dollars due to Supplier’s failure to make sufficient Supplier Personnel with appropriate skill sets available to perform Projects requested by Triple-S. |
| (f) | Project Management. All Special Infrastructure Projects shall be initiated, defined, approved in writing by Triple-S, performed and accepted in accordance with the process described in Schedule N (Project Framework). Triple-S shall not be responsible for Charges (and dollars shall not be debited from the Special Infrastructure Projects Pool)) for Projects that are not approved by Triple-S in writing in accordance with such process. |
| (g) | Charges for Equipment and Software. For Special Infrastructure Projects that (i) constitute Material Scope Changes; and (ii) require Supplier to purchase additional Equipment and Software, the charges for that Equipment and Software shall be determined under Section 14.15. |
| 7.4 | Infrastructure Project Management |
| (a) | Supplier shall use trained project managers and project management tools and methodologies to manage all Infrastructure Projects under the Agreement, including those that are included in BAU Activities. |
| (b) | All Special Infrastructure Projects shall be initiated, defined, approved in writing by Triple-S, performed and accepted in accordance with the process described in Schedule N (Project Framework). Triple-S shall not be responsible for Charges for Special Infrastructure Projects not approved by Triple-S in writing in accordance with such process. |
| 8. | MATERIAL CHANGES |
The Health Plan Charges (together with the other Charges provided in this Schedule C (Charging Methodology)) shall compensate Supplier for all Services provided to Triple-S, including substantial variability in the volume of such Services that may be required from month-to-month. Accordingly, except as expressly required elsewhere in this Schedule C (Charging Methodology), the Charges are subject to adjustment only in the following circumstances (each a “Material Change”):
Triple-S / Supplier Confidential
Page 18
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule C
Charging Methodology
| 8.1 | Material Scope Change |
| (a) | Definition. “Material Scope Change” means a change that Triple-S requires to the scope of the Services that: |
| (i) | causes a material increase or enables a material decrease in the recurring labor or Infrastructure Supplier requires to provide the Services, where “material” means [***]; |
| (ii) | is approved by Triple-S in writing through the Change Control Process; and |
| (iii) | does not involve the following: |
| (A) | changes in Member or Claims volumes (which are to be addressed through the pricing methodologies provided in Section 4); |
| (B) | changes involving Application Support Services (which are to be addressed through the pricing methodology provided in Section 6.1); |
| (C) | changes to the Health Plan Portfolio, PC & Life Portfolio or TSM Portfolio (which are to be addressed through the pricing methodologies provided in Sections 4.5(d) and 5); |
| (D) | Infrastructure Projects (which are to be addressed through the pricing methodologies provided in Section 7); |
| (E) | changes assumed to occur as part of the Transition or Transformation; or |
| (F) | change that is assumed as part of the Services described in Schedule A (Cross Functional Services) or an SOW executed under this Agreement (for example, annual updates to Claims processes and procedures; refresh of Triple-S Software). |
| (b) | Process and Pricing Adjustment. If Triple-S requests a change to the Services that either Party believes is a Material Scope Change, such Party shall notify the other of its determination and the following shall apply: |
| (i) | the Parties will evaluate the impact of the change requested by Triple-S through the Change Control Process; and |
| (ii) | if the change is a Material Scope Change, they shall (A) determine the extent to which Supplier’s Labor Costs or Infrastructure costs will increase or decrease after implementing the Material Scope Change; and (B) negotiate appropriate adjustments to the Health Plan Charges to reflect such increase or decrease. Any changes to Health Plan Charges must be agreed in writing by the Parties and will apply on a going-forward basis only. Unless agreed otherwise by the Parties, adjustments based on Supplier Labor Costs shall be made using the T&M Rates and adjustments to Infrastructure shall be made pursuant to Section 14.15. |
Triple-S / Supplier Confidential
Page 19
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule C
Charging Methodology
If the change is not a “Material Scope Change”, Supplier will, subject to Section 8.1(c) below, perform the change as part of the Services at no additional charge.
| (c) | With respect to changes described in Section 18.4(e)(ii) of the General Terms and Conditions that are enacted after the Effective Date (each, a “Change in Law”): |
| (i) | Application Changes. Changes to In-Scope Applications that require Application Support Services shall be performed using hours from the Application Support Pool. Supplier shall be required to make any changes required to Supplier Software at Supplier’s expense. If any work product charged against the Application Support Pool can be leveraged for the benefit of Supplier or a Supplier Affiliate or their respective provider, the hours spent on such work product shall be [***]. |
| (ii) | Infrastructure Changes. Changes to Infrastructure shall be reviewed under the Material Scope Change provisions above. If the change is a Material Scope Change, (A) charges for the one-time Infrastructure Project work will be determined under Section 7; and (B) incremental Equipment and Software will be charged under Section 14.15. |
| (iii) | Labor Changes. Supplier shall be responsible for adding Supplier Personnel as necessary to comply with a Change in Law; provided if Changes in Law require, without regard to whether any such change is a Material Scope Change, Supplier to add more than [***] in the aggregate over the Term of the Agreement (net of any reductions Supplier makes in Supplier Personnel as a result of Changes in Law) (“Labor Threshold”), (A) Supplier shall notify Triple-S of the Change in Law and provide supporting detail for the increase in FTEs; and (B) the Parties will negotiate an equitable increase to the Charges to compensate Supplier for the FTEs required above the Labor Threshold. |
| 8.2 | Triple-S Efficiency Initiatives |
| (a) | Definition. “Triple-S Efficiency Initiative” means a material change that does not relate to a change to an In-Scope Application agreed to by the Parties in Schedule X (Source of Truth) and (i) Triple-S makes to Triple-S systems or operations; or (ii) Supplier makes as part of Application Support Services, that enables Supplier to materially reduce Supplier’s recurring Labor Charges, Infrastructure costs or other costs of providing the Services. |
| (b) | Process and Pricing Adjustment. Triple-S shall notify Supplier of any change that it believes is a Triple-S Efficiency Initiative and the following shall apply: |
| (i) | the Parties will evaluate the impact of the change requested by Triple-S through the Change Control Process; and |
| (ii) | if the Parties agree the change is a Triple-S Efficiency Initiative, the Parties shall (A) determine the extent to which Supplier’s Labor Charges, Infrastructure or other costs are reasonably expected to decrease in connection with the Triple-S |
Triple-S / Supplier Confidential
Page 20
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule C
Charging Methodology
Efficiency Initiative; and (B) negotiate equitable adjustments to the Charges to reflect such decrease, taking into consideration each Party’s investment in the Triple-S Efficiency Initiative. Any changes to Charges must be agreed in writing by the Parties and will apply on a going-forward basis only.
| 8.3 | Additional Terms |
| (a) | The pricing adjustments contemplated in this Section 8 in connection with Material Changes [***]. |
| (b) | Supplier shall provide Triple-S with reasonably detailed information about Supplier’s existing environment (including personnel and Infrastructure solution) and any changes required or made possible with respect to personnel, Infrastructure and other resources as a result of a Material Change. This information shall be sufficient for Triple-S to understand and assess the net impact of the Material Change and the need to increase (or opportunity to decrease) Labor Charges, including (i) identification of affected Supplier Personnel by individual, rate category and location; and (ii) a list of affected Infrastructure by component and location. |
| 9. | TRANSFERRED CONTRACTS |
| 9.1 | Transferred Contracts |
Schedule C-5 (TSS Transferred Contracts) designates third party service contracts and licenses for Equipment, Software, services and other resources (“TSS Transferred Contracts”) that Supplier will assume as of the Service Commencement Date for IT Services, subject to the terms in this Section 9.
| (a) | The parties will work in good faith to assign, novate or otherwise transfer all of the TSS Transferred Contracts to Supplier prior to the Service Commencement Date for IT Services. |
| (b) | If the parties are unable to transfer a Transferred Contract to Supplier prior to the Service Commencement Date for IT Services: |
| (i) | Subject to the Parties obtaining any additional Required Consents, Triple-S will use Commercially Reasonable Efforts to continue to make the Transferred Contract available to Supplier for up to an additional 24 months. If Supplier requests an extension beyond such 24 month period, Triple-S may agree to or reject the request in its sole discretion. |
| (ii) | If it is not possible using Commercially Reasonable Efforts for Triple-S to continue making the Transferred Contract available to Supplier for the period described above, Supplier will replace the TSS Transferred Contract with a new contract or alternative solution approved in writing by Triple-S. |
Triple-S / Supplier Confidential
Page 21
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule C
Charging Methodology
| (iii) | Supplier will be responsible for [***] of the costs incurred by Triple-S under each TSS Transferred Contract and payable to the counterparty to such TSS Transferred Contract after the Service Commencement Date for IT Services whether it is transferred to Supplier or retained by Triple-S. |
| (c) | If Triple-S has prepaid any amounts under a TSS Transferred Contract (e.g., software maintenance) prior to the Service Commencement Date, Supplier shall provide Triple-S with a payment for the prepaid amounts attributable to periods after the Service Commencement Date for IT Services (e.g., if Triple-S prepaid $1,200 in maintenance fees for January through December 2017 and the Service Commencement Date is September 1, Supplier would provide a payment equal to $400). The Parties will reconcile the Triple-S spend for TSS Transferred Contracts to identify such payments within ninety (90) days of the Effective Date and Supplier will pay Triple-S such amounts within forty-five (45) days after such date. |
| 10. | T&M RATES |
| 10.1 | Rates |
| (a) | T&M Rates. Schedule C-2 (T&M Rates) provides time and materials rates that shall apply for purposes of calculating: |
| (i) | any Applications Support Services charges payable by Triple-S on a time and materials basis under this Agreement; |
| (ii) | Labor Costs; |
| (iii) | adjustments to the Health Plan Charges required in connection with a Material Change under Section 8; and |
| (iv) | any other Services for which this Agreement expressly permits Supplier to charge on a time and materials basis. |
| 10.2 | Additional Terms |
| (a) | All T&M Rates are fully loaded, meaning they include the following costs and expenses: |
| (i) | all corporate and administrative overhead; |
| (ii) | charges or fees for visas for Supplier Personnel; |
| (iii) | office space, Equipment and other Infrastructure expenses for Supplier Personnel working outside of Triple-S facilities (including those working remotely); |
| (iv) | management activities by Supplier Personnel that are not dedicated to performing Services for Triple-S; |
Triple-S / Supplier Confidential
Page 22
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule C
Charging Methodology
| (v) | personal computers for Supplier Personnel and related office Software and tools (excluding Software and tools purchased specifically for performance of Services for Triple-S that Supplier does not generally use in provision of Services), except to the extent expressly provided otherwise in the Financial Responsibility Matrix; and |
| (vi) | all other costs associated with providing the Services, unless or to the extent explicitly authorized in advance by Triple-S. |
| (b) | Only Productive Work is chargeable to Triple-S in connection with a Project or counted against the Application Support Pool. Supplier shall not charge for or count any work for the purposes referenced above that does not meet the definition of Productive Work. |
| 11. | ADDITIONAL TERMS RELATING FIXED FEES FOR HEALTH PLAN CHARGES |
Section 4.2 provides for a Monthly Fixed Fee payable for In-Scope Members at the [***] volume tier (“Minimum Monthly Fixed Fee”).
| (a) | The Minimum Monthly Fixed Fee shall be adjusted in connection with a Termination Event as required under Section 12. |
| (b) | If the volume of Non-Restricted Members in a month is reduced below [***] as a result of: |
| (i) | Supplier’s acts or omission (e.g., a Regulator suspends Triple-S’ right to enroll new Members due to Supplier’s failure to meet Service Levels); |
| (ii) | Triple-S’ removal of Services from this Agreement due to Supplier’s negligence or failure to perform in accordance with this Agreement; |
| (iii) | Any delay in completion of the Transition or Transformation (to the extent the delay results from Supplier’s acts or omissions), or |
| (iv) | During the Disengagement Assistance Period; then |
the Monthly Minimum Fixed Fees for the period of the Non-Restricted Member reduction caused by one of the foregoing events will be reduced by an amount equal to (A) the volume of Non-Restricted Members reduced as a result of such circumstance, multiplied by (B) the PMPM Rate payable for In-Scope Members in the first tier above [***].
| 12. | TERMINATION CHARGES |
This Section 12 describes the Termination Charges that are payable in connection with certain termination events defined in Section 16 (Termination) of the General Terms and Conditions (each, a “Termination Event”).
Triple-S / Supplier Confidential
Page 23
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule C
Charging Methodology
| 12.1 | Termination Charges |
Schedule C-4 (Termination Charges) sets forth the Termination Charges that Triple-S will pay to Supplier in connection with the termination of the entire Agreement (including all SOWs executed under the Agreement) under Sections 16.1(b), 16,1(f) or 16.1(h) of the General Terms and Conditions.
| 12.2 | Mitigation of Charges |
The Termination Charges in Schedule C-4 (Termination Charges) assume Supplier will be responsible for severance for all Supplier Personnel and stranded asset costs for all Equipment and Software used by Supplier to provide the Services.
| (a) | If Triple-S elects to hire Supplier Personnel, the Termination Charges shall be reduced by an amount equal to the severance that would otherwise be payable to those Supplier Personnel had they been terminated on the date Triple-S hired them. |
| (b) | If Triple-S assumes facility leases, data center contracts or other obligations that reduce Supplier’s wind-down obligations to third parties, the Termination Charges shall be equitably reduced to reflect the associated savings realized by Supplier. |
| 13. | RESERVED |
| 14. | OTHER CHARGES, CREDITS AND TERMS |
| 14.1 | Financial Responsibility Matrix |
Schedule C-3 (Financial Responsibility Matrix) contains a financial responsibilities matrix (“Financial Responsibilities Matrix” or “FRM”) identifying which Party has financial responsibility for the various resources used in performing the Services under the Agreement, including personnel resources, Equipment, Software and facilities. With respect to those items for which Supplier has financial responsibility, the Charges are deemed to compensate Supplier for supplying the item and/or providing associated services as specified in the FRM. Accordingly, Triple-S will not be required to pay Supplier any amounts with respect to such items other than the Charges.
| 14.2 | Inflation Adjustments for T&M Rates |
This Section 14.2 sets forth the cost of living adjustment that Supplier may make solely to the T&M Rates each year beginning in Contract Year 2, in addition to any adjustments set forth in Section 14.3 below.
| (a) | On [***], Supplier shall increase the T&M Rates by multiplying such rates by the applicable Inflation Factor defined below (each adjustment, a “COLA”). |
| (b) | The “Inflation Factor” for T&M Rates in the United States shall equal [***]. “US CPI” means All Items Consumer Price Index for All Urban Consumers (CPI-U) for the U.S. City Average, 1982-84 = 100 CPI. |
Triple-S / Supplier Confidential
Page 24
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule C
Charging Methodology
| (c) | The Inflation Factors for T&M Rates in India shall be determined as provided above in Section 14.2(b), except the US CPI shall be replaced by the Consumer Price Index “Numbers for Industrial Workers - CPI(IW) – All India Index”, published by the Labour Bureau, Government of India for rates for Supplier Personnel in India (“India CPI”). |
| (d) | Notwithstanding the calculations above, the Inflation Factor in the United States and India shall not exceed [***] in any year. |
| (e) | Supplier shall give Triple-S notice of the applicable COLA for each Contract Year and corresponding adjustments required under this Section 14.2 within thirty (30) days after [***], including detailed calculations and supporting documentation as to the determination of the Inflation Factor and the resulting changes to the T&M Rates for such year. |
| 14.3 | Inflation Adjustments for All Charges |
In addition to the adjustments to T&M Rates under Section 14.2, this Section 14.3 sets forth the cost of living adjustment that Supplier may make to the T&M Rates, Health Plan Charges, PMPM Rates, PC & Life Fixed Fee and TSM Fixed Fee each year beginning in Contract Year 2.
| (a) | Certain Definitions. |
| (i) | “Base Growth” means [***] on [***] growth per year thereafter. |
| (ii) | [***] means [***] on [***] growth per year thereafter. |
| (iii) | [***] |
| (b) | [***]: |
| (i) | [***] |
[***].
| (c) | [***]: |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
Triple-S / Supplier Confidential
Page 25
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule C
Charging Methodology
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | ||||||||||
| [***] | ||||||||||
| [***] | ||||||||||
| [***] | ||||||||||
| [***] | ||||||||||
| [***] | ||||||||||
[***].
| (d) | Supplier shall give Triple-S notice of any such adjustments for each Contract Year and corresponding adjustments required under this Section 14.3 within thirty (30) days of September 1 of such year, including detailed calculations and supporting documentation as to the determination of the resulting changes to the Charges for such year. |
| 14.4 | End User Support |
The Health Plan Charges shall fully compensate Supplier for all service desk functions, information technology support for all existing and future employees of Triple-S and its Affiliates (and contractors working at Triple-S and its Affiliates’ facilities) and support of their personal computers, peripherals, printers and other end user devices.
| 14.5 | Pass-Through Expenses |
| (a) | As of the Effective Date, there are no Pass-Through Expenses payable by Triple-S. If the Parties agree to add Pass-Through Expenses to this Agreement after the Effective Date, they will do so through the Change Control Process. |
| (b) | “Pass-Through Expenses” means third party charges that are to be both (i) paid by Triple-S (either (A) directly to the third party or (B) to Supplier, which, in turn, pays the third party) on an Out-of-Pocket Expenses basis, and (ii) administered by Supplier. Any Pass-Through Expenses shall be agreed upon in accordance with this Section. Supplier shall arrange for delivery by third parties to Supplier of invoices for Pass-Through Expenses, and Supplier promptly shall review such invoices and provide Triple-S with the original invoice together with a statement identifying which charges are proper and valid and should be paid by Triple-S. |
| (c) | Supplier shall use Commercially Reasonable Efforts to minimize the amount of Pass-Through Expenses. With respect to services or materials paid for on a Pass-Through Expenses basis, Triple-S reserves the right to: (i) obtain such services or materials directly from a third party; (ii) designate the third party source for such services or materials; (iii) designate the particular services or materials (e.g., equipment make and |
Triple-S / Supplier Confidential
Page 26
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule C
Charging Methodology
model) Supplier shall obtain; (iv) designate the terms for obtaining such services or materials (e.g., purchase or lease and lump sum payment or payment over time); (v) require Supplier to identify and consider multiple sources for such services or materials or to conduct a competitive procurement; and (vi) review and approve the applicable Pass-Through Expenses before entering into a contract for particular services or materials.
| 14.6 | Incidental Expenses |
Supplier acknowledges that, except as may be otherwise provided in this Agreement, expenses that Supplier expects to incur in performing the Services (including travel and lodging, document reproduction and shipping, and long-distance telephone) are included in Supplier’s Charges and rates set forth in this Agreement. Accordingly, such Supplier expenses are not separately reimbursable by Triple-S unless, on a case-by-case basis for unusual expenses, Triple-S has agreed in advance and in writing to reimburse Supplier for the expense.
| 14.7 | Taxes |
The Parties’ respective responsibilities for taxes arising under or in connection with this Agreement shall be as follows:
| (a) | Each Party shall be responsible for any personal property taxes on property it owns or leases, for franchise and privilege taxes on its business, and for taxes based on its net income or gross receipts. |
| (b) | Supplier shall be responsible for any sales, use, excise, value-added, services, consumption and other taxes and duties payable by Supplier on the goods or services used or consumed by Supplier in providing the Services where the tax is imposed on Supplier’s acquisition or use of such goods or services and the amount of tax is measured by Supplier’s costs in acquiring such goods or services. |
| (c) | Triple-S shall be responsible for any applicable sales, use, excise, value-added, services, consumption or other tax that is assessed on the provision of the Services as a whole, or on any particular Service by any governmental or taxing authority within the United States; provided, however, that (i) Supplier invoices reflect on a current basis the amount of any such tax in each jurisdiction and the taxable Services to which such tax relates, (ii) if Supplier fails to reflect on its invoice any such tax on a current basis, Supplier shall be financially responsible for any penalties and interest assessed by the taxing authority with respect to such tax, and (iii) if Supplier fails to reflect any such tax on a Supplier invoice within twelve (12) months after the date that such tax is due and payable, Supplier shall be financially responsible for the full amount of such tax, including any penalties and interest. |
| (d) | Supplier shall be responsible for any sales, use, excise, value-added, services, consumption or other tax that is assessed on the provision of the Services as a whole, or on any particular Service, by any governmental or taxing authority outside the United States as of the Effective Date or during the Term, except (i) where the Parties agree in writing that a Supplier Affiliate located in a jurisdiction outside of the United States may |
Triple-S / Supplier Confidential
Page 27
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule C
Charging Methodology
invoice Triple-S or a Triple-S Affiliate directly or (ii) where the Parties agree in writing including email that Supplier will provide centralized billing, wherein a Triple-S Affiliate located in a jurisdiction outside of the United States will receive Services from a Supplier Affiliate located in a jurisdiction outside of the United States and invoicing for such Services is between a Triple-S Affiliate located in the United States and a Supplier Affiliate located in the United States.
| (e) | Supplier shall be responsible for any payments required to compensate Supplier Personnel for compensatory tax treatment resulting from Supplier Personnel traveling to perform services. |
| (f) | If a sales, use, excise, value added, services, consumption or other tax is assessed on the provision of any of the Services, the Parties shall work together to segregate the payments under this Agreement into three (3) payment streams: |
| (i) | those for taxable Services; |
| (ii) | those for which Supplier functions merely as a payment agent for Triple-S in receiving goods, supplies, or services (including leasing and licensing arrangements); and |
| (iii) | those for other nontaxable Services. |
| (g) | The Parties agree to reasonably cooperate with each other to enable each to more accurately determine its own tax liability and to minimize such liability to the extent legally permissible. Supplier’s invoices shall separately state the amounts of any taxes Supplier is collecting from Triple-S, or otherwise a tax-compliant invoice, and Supplier shall remit such taxes to the appropriate authorities. Each Party shall provide and make available to the other any resale certificates, information regarding out-of-state or out-of-country sales or use of equipment, materials or services, and other exemption certificates or information reasonably requested by the other Party. |
| (h) | Supplier shall promptly notify Triple-S of, and coordinate with Triple-S the response to and settlement of, any claim for taxes asserted by applicable taxing authorities for which Triple-S is responsible hereunder, it being understood that with respect to any claim arising out of a form or return signed by a Party to this Agreement, such Party shall have the right to elect to control the response to and settlement of the claim, but the other Party shall have all rights, at its sole cost and expense, to participate in the responses and settlements that are appropriate to its potential responsibilities or liabilities. If Triple-S requests Supplier to challenge the imposition of any tax, Supplier shall do so in a timely manner and Triple-S shall reimburse Supplier for the reasonable legal fees and expenses it incurs. Triple-S shall be entitled to any tax refunds or rebates granted to the extent such refunds or rebates are of taxes that were paid by Triple-S. |
Triple-S / Supplier Confidential
Page 28
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule C
Charging Methodology
| 14.8 | Benchmarking |
| (a) | [***] during the Term commencing [***] (with intent to complete the benchmark and make any adjustments resulting from the benchmark effective at the beginning of [***], Triple-S may benchmark the Charges for the Services under this Agreement in accordance with this Section 14.8. |
| (b) | A benchmarking under this Section shall be conducted by an independent industry-recognized benchmarking service provider designated by Triple-S and reasonably approved by Supplier (‘Benchmarker’). Supplier agrees that [***] is acceptable as a Benchmarker. If Supplier rejects any other Benchmarker suggested by Triple-S, Supplier shall also provide Triple-S with the names of three (3) other Benchmarkers that would be acceptable to Supplier. [***]. The Parties shall cooperate with the Benchmarker, including, as appropriate, making available knowledgeable personnel and pertinent documents and records. |
| (c) | The Benchmarker shall perform the benchmarking in accordance with the Benchmarker’s documented procedures that shall be provided to the Parties prior to the start of the benchmarking process and as part of the Benchmarker selection process. The Benchmarker shall compare the Charges for the Services under this Agreement being benchmarked to the costs being incurred in a representative sample of similar services. The Benchmarker shall select the representative sample from entities (i) identified by the Benchmarker and approved by the Parties, or (ii) identified by agreement of the Parties and approved by the Benchmarker. The representative sample shall include at least [***]. |
| (d) | The Benchmarker shall conduct a benchmarking as promptly as is prudent in the circumstances. In conducting the benchmarking, the Benchmarker shall normalize the data used to perform the benchmarking to accommodate, as appropriate, differences in volume of service, scope of services, service levels, service delivery locations and other pertinent factors. Supplier will provide to the Benchmarker reasonably detailed information about the component elements of Supplier’s charges and pricing methods under this Agreement (although if Supplier fails to do so the Benchmarker shall proceed with such assumptions as it determines are reasonable under the circumstances), and the Benchmarker shall gather and utilize reasonably detailed information with respect to the representative samples being used for comparison. At the appropriate stage early in the process; but, in any event, prior to completing its report, the Benchmarker will meet with the Parties and describe in reasonable detail the steps that the Benchmarker proposes to take to normalize the data for comparison. The Parties shall have a reasonable opportunity to comment on those steps, and the Benchmarker shall incorporate into its normalization process the reasonable suggestions made by either Party; provided that if those suggestions are in conflict, the Benchmarker’s have the discretion to make the final determination. After the Benchmarker issues its preliminary report, each Party shall be provided a reasonable opportunity to review, comment on, and request changes in the Benchmarker’s preliminary report. Following such review and comment, the Benchmarker shall issue a final report of its findings and conclusions, indicating what it believes all the Charges would be at the[***] (viewed from the |
Triple-S / Supplier Confidential
Page 29
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule C
Charging Methodology
perspective of most beneficial to Triple-S (e.g., lowest charges shall be the “best” charges)). In doing so, the Benchmarker will set [***].
| (e) | If in the final report of the Benchmarker, the Charges to Triple-S for the benchmarked Services are greater than the [***] of the representative sample, (i) the Parties shall meet and work in good faith to adjust the Charges in an attempt to achieve such [***]; and (ii) if the Parties are unable to agree on and document in an amendment such adjustment within [***] after the Benchmarker publishes its final report, Triple-S shall have the right to terminate this Agreement (including the SOWs executed under this Agreement) [***] notice to Supplier. If in the final report of the Benchmarker, the Charges are within the [***] of the representative sample, there shall not be an adjustment to the Charges. In no case will the Charges be [***]. |
| 14.9 | Currency |
All Charges in this Agreement are stated in U.S. Dollars, and shall be invoiced by Supplier and paid by Triple-S in U.S. Dollars. There are no adjustments permitted for changes in foreign exchange rates.
| 14.10 | New Services |
The Charges for any New Services performed by Supplier at Triple-S’ request shall be determined in accordance with Section 2.2 (New Services) of the General Terms and Conditions.
| 14.11 | Remedial Services |
Supplier shall not be entitled to charge Triple-S for any rework or other Services required as a result of Supplier’s failure to perform in accordance with this Agreement.
| 14.12 | Disengagement Services |
Supplier shall invoice Triple-S for Disengagement Services payable by Triple-S as provided in Section 17 (Disengagement Assistance) of the General Terms and Conditions.
| 14.13 | Travel |
| (a) | Except as provided in Section 14.13(b), Supplier shall be responsible for all expenses for travel and lodging required to provide the Services, including with respect to the Transition, training for Supplier Personnel, management oversight, and any internal Supplier meetings. |
| (b) | Triple-S shall reimburse Supplier for actual expenses for travel within the United States requested by Triple-S only in connection with discretionary Applications Development Projects; provided such expenses are (i) approved in advance by Triple-S and documented in advance and in writing; and (ii) incurred in accordance with Triple-S’ travel and expense policy. |
Triple-S / Supplier Confidential
Page 30
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule C
Charging Methodology
| 14.14 | Service Level Credits |
Supplier shall credit any Service Level Credits (less any Claw Backs) earned in a month against the subsequent month’s Charges.
| 14.15 | [***] Pricing for Certain New Charges and Adjustments |
Where this Schedule C (Charging Methodology) provides for a new Charge or an increase to an existing Charge (including under Sections 4.5(d), 5.1(c), 7 and 8), the components of the new Charge or increase that involve the purchase of additional Infrastructure and related services from a third party shall not exceed an amount equal to [***]. This [***] shall compensate Supplier for all procurement, vendor management, oversight and audit, financing, and Supplier expertise in defining and documenting requirements. Supplier shall provide detail to substantiate any third party costs that are the basis for a new Charge or increase to an existing Charge under this Agreement.
| 14.16 | IT Inventory and Configuration |
On a quarterly basis, and as otherwise reasonably requested by Triple-S, Supplier shall provide Triple-S with a detailed inventory of Infrastructure components hosted by Supplier or its Subcontractors (including number of servers and related capacity, GB of storage, system software and tools installed, and any other component for which a third party charges a separate fee). At Triple-S’ request, Supplier will meet with Triple-S to review Supplier’s report and provide additional detail about the hosting environment as reasonably requested by Triple-S.
| 15. | INVOICING AND PAYMENT |
| 15.1 | Invoicing |
| (a) | Supplier shall invoice Triple-S for all amounts due under this Agreement on a monthly basis in arrears (i.e., Charges for Services delivered in August will be invoiced on the invoice delivered to Triple-S in September), or as otherwise agreed by the Parties in writing. Each invoice shall provide, for each Charge, information regarding the Services to which such Charge relate which is sufficient to enable Triple-S to determine the contractual basis for such Charge. Supplier shall include the calculations utilized to establish the Charges. |
| (b) | To the extent a credit may be due Triple-S pursuant to this Agreement, Supplier shall provide Triple-S with an appropriate credit against amounts then due and owing against the next month’s invoice. If no further payments are due to Supplier, Supplier shall pay such amounts to Triple-S within [***] of the date of request for such credit by Triple-S. |
| (c) | Supplier shall render a single consolidated invoice for each month’s Charges showing such details as reasonably specified by Triple-S, including as necessary to satisfy Triple-S’ internal accounting and chargeback requirements (such as allocating Charges among Service components, locations and departments). The form of invoice shall be mutually agreed by the Parties during Transition and any changes to such form invoice during the Term must be approved by Triple-S. |
Triple-S / Supplier Confidential
Page 31
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule C
Charging Methodology
| (d) | Supplier shall use good faith efforts to submit complete invoices that include all Charges incurred in the applicable month, and may include additional Charges on a later invoice, provided that in no event shall Charges [***]. |
| 15.2 | Payment Due |
Subject to the other provisions of this Section 15, invoices provided under Section 15.1 and properly submitted to Triple-S pursuant to this Agreement shall be paid by Triple-S within [***] after receipt thereof.
| 15.3 | Accountability |
Supplier shall maintain complete and accurate records of and supporting documentation for the amounts billable to and payments made by Triple-S hereunder in accordance with generally accepted accounting principles applied on a consistent basis. Supplier agrees to provide Triple-S with documentation and other information with respect to each invoice as may be reasonably requested by Triple-S to verify accuracy and compliance with the provisions of this Agreement.
| 15.4 | Proration |
Except as may be otherwise provided in this Agreement, periodic Charges under this Agreement are to be computed on a calendar month basis, and shall be prorated for any partial month.
| 15.5 | Refundable Items |
| (a) | Prepaid Amounts. Where Triple-S has prepaid for a service or function for which Supplier is assuming financial responsibility under this Agreement, Supplier shall refund to Triple-S, upon either Party identifying the prepayment, that portion of such prepaid expense which is attributable to periods on and after the Effective Date. |
| (b) | Refunds and Credits. If Supplier should receive a refund, credit or other rebate for Pass-Through Expenses previously paid for by Triple-S or for amounts paid by Triple-S under a TSS Transferred Contract prior to the date the contract is transferred to Supplier, Supplier shall promptly notify Triple-S of such refund, credit or rebate and shall promptly pay the full amount of such refund, credit or rebate, as the case may be, to Triple-S. |
| 15.6 | Deductions |
With respect to any amount to be paid by Triple-S hereunder, Triple-S may deduct from such amount any amount that Supplier is obligated to pay Triple-S hereunder.
| 15.7 | Disputed Charges |
Subject to Section 15.6, Triple-S shall pay undisputed Charges when such payments are due under this Section 15.7. Triple-S may withhold and/or set off payment of particular Charges that Triple-S disputes in good faith, and may set off amounts due and owing to Triple-S as credits against Charges payable to Supplier under this Agreement. If any such disputed Charges have already been paid, Triple-S may deduct such disputed Charges or amounts due from future amounts owed by Triple-S to Supplier.
Triple-S / Supplier Confidential
Page 32
MSA Schedule C1
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
MASTER SERVICES AGREEMENT
SCHEDULE C-1
CHARGES
| Schedule C-1 | Triple-S / Supplier Confidential |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
Schedule C-1 Charges
| Final Pricing | Fee Schedule | ||||||||||||
| Year 1 (a) | Year 2 | Year 3 | Year 4 | Year 5 | Year 6 | Year 7 | Year 8 | Year 9 | Year 10 | ||||
| Health Fees | Basis | ||||||||||||
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | ||
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | ||
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | ||
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | ||
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | ||
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | ||
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | ||
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | ||
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | ||
| Year 1 Fee Schedule | ||||||||||||||
| Final Year 1 Fee Schedule | ||||||||||||||
| Mo. 1 | Mo. 2 | Mo. 3 | Mo. 4 | Mo. 5 | Mo. 6 | Mo. 7 | Mo. 8 | Mo. 9 | Mo. 10 | Mo. 11 | Mo. 12 | |||
| Health Fees | Basis | |||||||||||||
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | |
M = Millions
(a) Optum has provided Year 1 fees broken out by month. Year 1 column in this analysis represents the average.
| Schedule C-1 | Page 1 | Triple-S / Supplier Confidential |
MSA Schedule C2
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
MASTER SERVICES AGREEMENT
SCHEDULE C-2
T&M RATES
| Schedule C-2 | Triple-S / Supplier Confidential |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
Schedule C-2 T&M Rates
| Role No. | Role Type | Key Skill | Onshore (Landed) Hourly Rate - Long Term (USD) |
Offshore Hourly Rate (USD) | |||||
| Level | Level | ||||||||
| Intermediate | Senior | Associate | Intermediate | Senior | |||||
| 1 | Technology Architect | Enterprise/Solution Architect , Data Architect, Compliance Architect, QA Architect | [***] | [***] | [***] | ||||
| Network Architect (LAN, WAN, Networking), Data Center | [***] | [***] | [***] | ||||||
| 2 | Database Administrator | SQL, Oracle, DB2, and Sybase | [***] | [***] | [***] | [***] | [***] | ||
| 3 | Developer | Developer - Java & Web Programming, ASP, VB, C++ Developer, BizTalk Developer/ HIPAA EDI, JCL Developer, PrintNet, OnBase |
[***] | [***] | [***] | [***] | [***] | ||
| .Net Framework Developer | [***] | [***] | [***] | [***] | [***] | ||||
| Edifecs Programmer | [***] | [***] | [***] | [***] | [***] | ||||
| DW/ETL IBM Infosphere, ESP/ IBM Websphere, BI Cognos, Informatica |
[***] | [***] | [***] | [***] | [***] | ||||
| 4 | Production Support Engineer |
Service Desk Technican, Command Center Specialist, Data Network Engineering, Windows Server Engineer, Storage Engineer, Messaging Engineer, Cloud/Virtualization Specialist, ESB (Middleware) Infrastructure Engineer, Mobile Technology Specialist |
[***] | [***] | [***] | [***] | [***] | ||
| Workplace Services Specialist, Network & Telecom (Voice) Specialist |
[***] | [***] | [***] | [***] | [***] | ||||
| UNIX Engineer, Backup Engineer | [***] | [***] | [***] | [***] | [***] | ||||
| Release Manager | [***] | [***] | |||||||
| ▇▇▇▇▇ ▇ Distributed Ops/Engineering | [***] | [***] | [***] | [***] | [***] | ||||
| 5 | QA Tester | Manual and Automated Software Tester |
[***] | [***] | [***] | [***] | [***] | ||
| Test Designer | [***] | [***] | |||||||
| 6 | Security Engineer |
Enterprise Security Solution Engineer |
[***] | [***] | [***] | [***] | [***] | ||
|
Triple-S / Supplier Confidential Page 1 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule C-2
T&M Rates
Schedule C-2 T&M Rates (continued)
| Role No. | Role Type | Key Skill | Onshore (Landed) Hourly Rate - Long Term (USD) |
Offshore Hourly Rate (USD) | |||||
| Level | Level | ||||||||
| Intermediate | Senior | Associate | Intermediate | Senior | |||||
| 7 | Analysts | Business / Technology Analysts | [***] | [***] | |||||
| Business Application Configuration Architect, Workstream Lead |
[***] | [***] | |||||||
| 8 | BPO | Claims Adjudication Processor | [***] | ||||||
| Claims Audit Processor | [***] | ||||||||
| Performance Management Analyst | [***] | ||||||||
| Trainer | [***] | ||||||||
| UAT Tester | [***] | ||||||||
| Business Process Analyst | [***] | ||||||||
| Project Lead | [***] | ||||||||
| Project Manager | [***] | ||||||||
| Role No. | Role Type | Key Skill | Onshore (US Based) Hourly Rate - (USD) |
||
| Level | |||||
| Intermediate | Senior | ||||
| 9 | Program Management1 | Business/ Technology Analyst | [***] | [***] | |
| Business and Technology-enabled Business PM | [***] | [***] | |||
______________________
| 1 | These roles will be provided with U.S. based resources. |
|
Triple-S / Supplier Confidential Page 2 |
MSA Schedule C3
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
MASTER SERVICES AGREEMENT
SCHEDULE C-3
FINANCIAL RESPONSIBILITY MATRIX
| Schedule C-3 | Triple-S / Supplier Confidential |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
Schedule C-3
Financial Responsibility Matrix
| 1. | EQUIPMENT |
| Financial Responsibility | |
|
Equipment located in Triple-S data centers*
|
[***]
|
|
Equipment located in Supplier Facilities (including third party cloud and other Subcontractor facilities)*
|
[***]
|
|
End user equipment (including personal computers and peripherals, printers, mobile phones) for Triple-S employees and contracts
|
[***]
|
|
End user equipment (including personal computers and peripherals, printers, mobile phones) for Supplier employees and contracts
|
[***]
|
* Including servers, storage, network infrastructure as production and disaster recovery data centers. All In-Scope Applications are assumed to migrate to Supplier Facilities within the timelines set forth in Schedule X (Source of Truth) and the transition documents attached in SOW #2 (IT Services). Triple-S will retain Financial Responsibility for the Equipment and facilities required to host the [***] Software.
| 2. | NETWORK CONNECTIVITY |
| Financial Responsibility | |
|
Network connectivity between Triple-S facilities
|
[***]
|
|
Network connectivity between Triple-S facilities and Supplier data centers in the United States
|
[***]
|
| Network connectivity between Supplier facilities (including all connectivity required between the United States and India) |
[***]
|
|
Triple-S / Supplier Confidential Page 1 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule C-3
Financial Responsibility Matrix
| 3. | FACILITIES |
| 3.1 | Facilities |
Supplier shall provide and have Financial Responsibility for the facilities required to provide the Services, except as follows:
| Supplier Use of Triple-S Space To Deliver Buzz Services | |||
| Locations | Initial Take-Over Period* | Transition to Cloud* |
Managed IT Services
(Post Data Center)*
|
| 9/12017 – 12/31/2017 | 1/1/2018 - 6/30/2019 | 7/1/2019 – End of Term | |
| Data Center | [***] (Existing Employees) | [***] | [***] |
| Other Triple-S Locations | [***] (Existing Employees)** | [***] | [***] |
| Workplace services | [***] | [***] | [***] |
| Supplier KA / KT & Mgmt Staff | [***] | [***] | [***] |
* Triple-S shall provide facilities for the In-Scope Employees designated in Schedule G (In-Scope Employee Agreement) so long as they retain employees of Interactive Systems.
The timelines above assume Supplier move of majority of existing resources into Supplier temporary space.
**Supplier is also assuming [***] open requisitions. Open requisitions will be hired direct to Supplier locations & Triple-S real estate is not required.
| 3.2 | Reimbursements |
| (a) | The reimbursements Supplier is required to make under the In-Scope Employee Agreement include certain allocations for use of the space above. |
| (b) | Supplier will not be required to reimburse Triple-S for real estate costs for the personnel noted above, except as provided in the In-Scope Employee Agreement. |
|
Triple-S / Supplier Confidential Page 2 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule C-3
Financial Responsibility Matrix
| 4. | SOFTWARE |
| Financial Responsibility | |
|
Suppler-provided Software (including as listed in Schedules, S, X and C-5) and any other Software required to implement the IT Solution
|
[***]
|
|
Triple-S-provided Software listed in Schedule X
|
[***]
|
| 5. | ADDITIONAL TERMS |
| (a) | Triple-S Financial Responsibility in this Schedule C-3 is subject to Sections 12.2 of the General Terms and Conditions and Section 3.1(c) of Schedule C (Charging Methodology). |
| (b) | If there is an express conflict between the general allocation of responsibility in Sections 1 through 4 of this Schedule C-3, and the terms of Schedule S (Supplier Software), X (Source of Truth) or C-5 (TSS Transferred Contracts), the terms of Schedule S, X or C-5 (as applicable) shall control. |
| (c) | Supplier shall have Financial Responsibility for all Equipment and Software maintenance contracts (including where Triple-S has Financial Responsibility for the underlying Equipment or Software), except as provided otherwise in Schedule X (Source of Truth). |
|
Triple-S / Supplier Confidential Page 3 |
MSA Schedule C4
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
MASTER SERVICES AGREEMENT
SCHEDULE C-4
TERMINATION CHARGES
| Schedule C-4 | Triple-S / Supplier Confidential |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
Schedule C-4 Termination Charges
Termination Fee for termination pursuant to Section 16.1(b) of the General Terms and Conditions:
| Termination Schedule | Termination Fee | ||||||||||
| Basis | Year 1 | Year 2 | Year 3 | Year 4 | Year 5 | Year 6 | Year 7 | Year 8 | Year 9 | Year 10 | |
| Termination for Convenience | Annual | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
Termination Fee for termination pursuant to Section 16.1(f) of the General Terms and Conditions:
| Termination Schedule | Termination Fee | ||||||||||
| Basis | Year 1 | Year 2 | Year 3 | Year 4 | Year 5 | Year 6 | Year 7 | Year 8 | Year 9 | Year 10 | |
| Termination due to change in laws | Annual | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
Termination Fee for termination pursuant to Section 16.1(h) of the General Terms and Conditions:
| Termination Fee - Contract Year 1 Only | |||||
| Month 1 | Month 2 | Month 3 | Month 4 | ||
| Termination - No regulatory approval | [***] | [***] | [***] | [***] | |
The Termination Fees above state the Termination Fee payable for a termination that is effective in the first month of each Contract Year. If the effective date of termination is later in the year, the Termination Fee will be pro-rated based on the number of months remaining in the year. For example, assume each Contract Year is from 9/1 through 8/31 and that the Termination Fee for year 1 is $1,000 and for year 2 is $2,000. If the effective date of termination is in the middle of year 1, the Termination Fee would be $1,500.
|
Triple-S / Supplier Confidential Page 1 |
MSA Schedule C5
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
MASTER SERVICES AGREEMENT
SCHEDULE C-5
TSS TRANSFERRED CONTRACTS
| Schedule C-5 | Triple-S / Supplier Confidential |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule C-5
TSS Transferred Contracts
Schedule C-5 – TSS Transferred Contracts
| Seq # | Vendor | Description | Long Description |
Agreement Name/Date
|
Contract File Reference | Annual Baseline Spend Amount - In Scope |
Legal Name |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
Triple-S / Supplier Confidential
Page 1
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule C-5
TSS Transferred Contracts
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
Triple-S / Supplier Confidential
Page 2
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule C-5
TSS Transferred Contracts
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
Triple-S / Supplier Confidential
Page 3
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule C-5
TSS Transferred Contracts
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
Triple-S / Supplier Confidential
Page 4
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule C-5
TSS Transferred Contracts
[***][***]
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
| [***] | [***] | [***] | [***] | [***] | [***] | [***] | [***] |
Triple-S / Supplier Confidential
Page 5
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule C-5
TSS Transferred Contracts
| [***] | [***] | [***] | [***] | [***] | [***] | ||
| [***] | [***] | [***] | [***] | [***] | [***] | ||
| [***] | [***] | [***] | [***] | [***] | [***] | ||
| [***] |
Triple-S / Supplier Confidential
Page 6
Schedule D
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
SCHEDULE D
KEY SUPPLIER POSITIONS
| Schedule D | Triple-S/Supplier Confidential |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
SCHEDULE D
KEY SUPPLIER POSITIONS
| I. | INTRODUCTION |
With reference to Section 6.3 (Key Supplier Positions and Other Requirements) of the General Terms and Conditions, this Schedule D (Key Supplier Positions) identifies the Key Supplier Positions that are approved as of the Effective Date. All Key Supplier Positions will be identified, interviewed and on-boarded within thirty (30) days of the Effective Date.
| II. | KEY SUPPLIER POSITIONS |
| Ref # | Key Supplier Position | Summary of Role/ Responsibilities | Physical Location |
| 1 | Client Account Executive | The Client Account Executive is a Senior Executive who has full authority to make decisions across all services. The Supplier Account Executive will have extensive experience in managing strategic client relationships across a complex set of service delivery and performance standards. This position will be available to travel to attend meetings in Puerto Rico. The Supplier Account Executive will be authorized to act as Supplier’s primary contact with respect to each Party’s obligations under this Agreement, and will have day-to-day authority to assess Triple-S satisfaction, including a strong cultural fit. The Supplier Account Executive will have day-to-day responsibility for managing the delivery of the Services and coordinating with Triple-S executives. The Client Account Executive will have primary responsibility for governance obligations across all services for a smooth transition and a high level of satisfaction with Triple-S personnel. The Account Executive will be the single point of escalation for all contract deliverables. | Puerto Rico 75% for first 2 years then 50% or as determined need for onsite presence after implementation milestones have been completed. |
Triple-S/Supplier Confidential
Page 1
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule D
Key Supplier Positions – Account Level
| Ref # | Key Supplier Position | Summary of Role/ Responsibilities | Physical Location |
| 2 | IT Implementation Lead |
The IT Implementation Lead will be responsible for managing the transition phase cloud implementation of services to steady state for IT services.
Once steady state is achieved across the IT services, ongoing Transition Services will be provided on an as-needed basis and resource will no longer be dedicated.
· Mobilize the IT Implementation Team, progress tracking, communications, and status reporting.
· Manage and provide guidance and direction on the development of the Transition Plans and Transition Work Plans.
· Coordinate to produce a consolidated status report that conveys program status, accomplishments, key next steps, risks and issues for the transition.
· Develop and maintain a matrix summarizing the progress of contractual deliverables through the development, submission, review and approval activities.
Implement a risk and issue management process for the program that includes mitigation and contingency planning. |
Puerto Rico 75% for first 2 years (or longer if necessary, to complete the Transition and Transformation) then 50% or as determined need for onsite presence after implementation milestones have been completed |
Triple-S/Supplier Confidential
Page 2
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
| Ref # | Key Supplier Position | Summary of Role/ Responsibilities | Physical Location |
| 3 | Program Delivery Lead / VP of Program Operations | The Program Delivery Lead will provide program oversight, contract compliance, change control functions and financial management. This position has oversight to day-to-day responsibility for ensuring contract adherence and management in areas such as reporting, compliance, invoicing, finance and other contract relevant management functions. The Program Delivery Lead will be responsible for coordinating the delivery of contractually specified reports and manages the contract changes through the Change Control and Governance process in partnership with the Triple-S executives. The Program Delivery Lead will be the key responsible party for the overall program deliverables including SLAs, program deliverables, client expectations, and all program milestones. The Program Delivery Lead is accountable for reporting the performance of all programs to the client on a recurrent basis. The Program Delivery Lead will also be responsible for managing the transition of Claims Services to steady state. | Puerto Rico 75% for first 2 years then 50% or as determined need for onsite presence after implementation milestones have been completed |
| 4 | Claims Operations Lead |
The Claims Operations Lead will provide oversight and management of claims staff and day to day operations focusing on quality. The Claims Operations Lead will be responsible for Triple-S operational commitments and service delivery capability. The Claims Operations Lead will conduct internal performance management meetings. The Claims Operations Lead will manage operational performance, SLA metrics and communicate status to Triple-S as required through performance reporting. |
Hyderabad, India Eau Claire, WI
|
| 5 | IT Delivery Lead |
The IT Delivery Lead will provide oversight and management of IT staff and day to day operations focusing on quality. The IT Delivery Lead will be responsible for Triple-S operational commitments and service delivery capability. The IT Delivery Lead will conduct internal performance management meetings. The IT Delivery Lead will manage operational performance, SLA metrics and communicate status to Triple-S as required through performance reporting. |
Puerto Rico 75% for first 2 years then 50% or as determined need for onsite presence after implementation milestones have been completed |
Triple-S/Supplier Confidential
Page 3
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule D
Key Supplier Positions – Account Level
| Ref # | Key Supplier Position | Summary of Role/ Responsibilities | Physical Location |
| 6 | PMO |
The Program Management Lead is a Director level or higher resource with extensive experience in leading large scale program management teams during the transition of services to steady state. This resource reports into the Program Delivery Lead and will be a dedicated resource during the transition. During transition the PMO will perform the following functions:
· Mobilize the Program Management Office (PMO) program management processes including day-to-day program governance, progress tracking, communications, and status reporting.
· Establish and manage the program change management process, including logging changes and shepherding them through the review, approval, and reporting activities.
· Coordinate across the transition services to produce a consolidated status report that conveys program status, accomplishments, key next steps, risks and issues for the transition.
· Implement a risk and issue management process for the program that includes mitigation and contingency planning.
Once steady state is achieved across the services, ongoing Transition Services will be provided on an as-needed basis. |
Puerto Rico 75% for first 2 years then 50% or as determined need for onsite presence after implementation milestones have been completed |
Triple-S/Supplier Confidential
Page 4
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule D
Key Supplier Positions – Account Level
| Ref # | Key Supplier Position | Summary of Role/ Responsibilities | Physical Location |
| 7 | Director of IT Operations |
The Director of IT Operations is a direct support role of the IT Delivery Lead role and will provide oversight and management of IT staff and day to day operations focusing on quality. The Director of IT Operations will be responsible for Triple-S operational commitments and service delivery capability. The IT Delivery Lead will conduct internal performance management meetings. The Director of IT Operations will manage operational performance, SLA metrics and communicate status to Triple-S as required through performance reporting. |
Puerto Rico 75% for first 2 years then 50% or as determined need for onsite presence after implementation milestones have been completed |
| 8 | Director of Program Operations | The Director of Program Operations is a direct support role of the Program Delivery Lead/VP of Program Operations role and support all functions and responsibilities of that role. | Puerto Rico 75% for first 2 years then 50% or as determined need for onsite presence after implementation milestones have been completed |
| 9 | Claims Delivery Liaison | The Claims Delivery Liaison is a claims expert that will be responsible for day to day management of the transition of the Claims Services from Triple-S to Supplier. This will include managing the knowledge transfer process and information and document requests from Triple-S. The Claims Delivery Liaison will also coordinate with the Claims Operations Lead for any follow-ups from Supplier and will communicate regularly with Triple-S personnel regarding the status of the transition and Supplier’s launch of the Claims Services on a production basis. Claims Delivery Liaison will also be available to participate and contribute in meetings with providers, clients, actuaries, regulators as required by Triple S | Puerto Rico 75% for first 2 years then 50% or as determined need for onsite presence after implementation milestones have been completed. |
Triple-S/Supplier Confidential
Page 5
Schedule E
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
SCHEDULE E
SUPPLIER FACILITIES
| Schedule E | Triple-S / Supplier Confidential |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
SCHEDULE E
SUPPLIER FACILITIES
| I. | INTRODUCTION |
With reference to Section 4.2 (Place of Performance) of the General Terms and Conditions, this Schedule E (Supplier Facilities) describes the facilities at which Supplier will perform the Services.
| II. | SUPPLIER FACILITIES |
| Primary Location | Location Address |
Triple-S Data Accessed? (Y/N) |
Authorized Service(s) | Backup Location(s) |
| Optum Headquarters |
11000 Optum Circle (Bldgs. 1, 2 and 3) ▇▇▇▇ ▇▇▇▇▇▇▇, ▇▇ ▇▇▇▇▇ ▇▇▇
|
Y |
Process design Architecture support Claims process support Data analysis support Project management support Leadership support Executive management |
[***] |
Triple-S/Supplier Confidential
Page 1
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule E
Supplier Facilities
| Primary Location | Location Address |
Triple-S Data Accessed? (Y/N) |
Authorized Service(s) | Backup Location(s) |
|
Optum Elk River, MN
Data Center
|
[***] | Y |
End User Help Desk Support Application Support 24/7 Monitoring & Alerting War Room Services (priority 1&2 kickoff) |
[***] |
| Gurgaon, India |
[***] |
Y | Claims processing | [***] |
| Noida, India | [***] | Y | Claims processing | [***] |
| Chaska, Minnesota | [***] | Y |
End User Help Desk Support Application Support 24/7 Monitoring & Alerting War Room Services (priority 1&2 kickoff) |
[***] |
Triple-S/Supplier Confidential
Page 2
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule E
Supplier Facilities
Primary Location |
Location Address |
Triple-S Data Accessed?
(Y/N)
|
Authorized Service(s) | Backup Location(s) |
| Gurgaon, India | [***] | Y | Application M&O | [***] |
| Gurgaon, India | [***] | Y | IT engineering, implementation and support services | [***] |
| East US 2 (Virginia) | [***] | Y | Microsoft Data Center | [***] |
Triple-S/Supplier Confidential
Page 3
Schedule F
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
SCHEDULE F
GOVERNANCE
| Schedule F | Triple-S / Optum Confidential |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule F
Governance
SCHEDULE F
GOVERNANCE
Table of Contents
| 1. INTRODUCTION | 1 |
| 2. CONTRACT GOVERNANCE PLAN | 1 |
| 2.1 Contract Governance Plan Development | 1 |
| 2.2 Contract Governance Responsibilities | 2 |
| 2.3 Relationship Management Structure | 3 |
| 2.4 Meetings | 6 |
| 3. ANNUAL TECHNOLOGY PLAN | 6 |
| 4. VENDOR GOVERNANCE | 7 |
| 5. COORDINATION AMONGST KEY THIRD PARTIES | 8 |
Triple-S / Supplier Confidential
Page 1
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule F
Governance
SCHEDULE F
GOVERNANCE
| 1. | INTRODUCTION |
| (a) | With reference to Section 18 (Governance and Management) of the General Terms and Conditions, this Schedule F (Governance) sets forth an integrated set of business office governance processes, plans and tools relating to this Agreement (“Contract Governance”). The purpose of this Contract Governance is to monitor and control aspects of the Services in order to promote smooth operation of the Services in accordance with this Agreement. This Schedule F (Governance) describes the Contract Governance plan, Triple-S’s and Supplier’s roles and responsibilities, the relationship management structure, and the decision-making processes related to the Services. |
| (b) | In the event of a conflict between the provisions of this Schedule and other parts of this Agreement, the provisions of Section 26.11 (Order of Precedence) of the General Terms and Conditions shall apply. |
| (c) | All references in this Schedule to Sections and Exhibits shall be to the Sections and Exhibits to this Schedule, unless otherwise specified. |
| (d) | Capitalized terms are defined in Schedule AA (Glossary) to the Agreement or in the place where they are used. |
| 2. | CONTRACT GOVERNANCE PLAN |
| 2.1 | Contract Governance Plan Development |
Triple-S and Supplier will jointly develop, approve and begin implementing a plan for governance of the Agreement (the “Contract Governance Plan”) within ninety (90) days following the Effective Date. The Contract Governance Plan will:
| (a) | Be consistent with the Relationship Management Structure described in Section 2.3 below, specify the formal organizations, processes, and practices for managing Triple-S’s and Supplier’s relationship under the Agreement and the Parties’ governance and integration of third party systems and processes that are applicable to the Services; |
| (b) | Establish organizational interfaces for management and operation of this Agreement including: |
| (i) | Provide a high level overview of the business office governance processes requiring Triple-S’s involvement; |
| (ii) | Establish a strategy for communicating and planning for major organization changes (i.e., people, processes, functions); and |
Triple-S / Supplier Confidential
Page 1
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule F
Governance
| (iii) | Enhance and facilitate effective operating protocols and resolution of certain disputes in accordance with Section 25 (Dispute Resolution) of the General Terms and Conditions. |
| 2.2 | Contract Governance Responsibilities |
| (a) | Supplier will: |
| (i) | Assign an individual to be the single point of contact to Triple-S for the Contract Governance Plan development and maintenance; |
| (ii) | Provide, update and maintain a description of the Supplier’s leadership organization as part of the organization charts to be provided by Supplier pursuant to Section 6.3(f) of the General Terms and Conditions; |
| (iii) | Draft the initial Contract Governance Plan and provide such to Triple-S within sixty (60) days after the Effective Date; |
| (iv) | Identify Service process inhibitors, if any, and propose process improvements to Triple-S; |
| (v) | Jointly review the Contract Governance Plan on an annual basis or more frequently as may be agreed by the Parties, and update and maintain the Contract Governance Plan accordingly; and |
| (vi) | Provide appropriate Supplier Personnel access to the Contract Governance Plan, as needed. |
| (b) | Triple-S will: |
| (i) | Assign an individual to be the single point of contact to Supplier for the Contract Governance Plan development and maintenance; |
| (ii) | Provide, update and maintain the Triple-S leadership organization; |
| (iii) | Review and provide to Supplier, in writing, Triple-S’s comments, questions and proposed changes to the draft Contract Governance Plan within thirty (30) days following Triple-S’s receipt of the draft Contract Governance Plan; |
| (iv) | Acknowledge Triple-S’s receipt and approval of the final version of the Contract Governance Plan; |
| (v) | Identify Service process inhibitors, if any, and propose process improvements to Supplier; |
Triple-S / Supplier Confidential
Page 2
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule F
Governance
| (vi) | Jointly review and update the Contract Governance Plan on an annual basis or more frequently as may be agreed by the Parties; and |
| (vii) | Provide the Contract Governance Plan to appropriate Triple-S employees, as appropriate. |
| 2.3 | Relationship Management Structure |
| (a) | On the Effective Date, the Parties will each identify an Executive Sponsor (who will focus on Triple-S’ and Supplier’s long-term strategic relationship and the mission, vision and innovation as they relate to the Services) and Delivery Executives (the Triple-S Program Manager a described in Section 7.1 of the General Terms and Conditions and the Supplier Account Executive as described in Section 6.3(e) of the General Terms and Conditions). (who will have responsibility for the execution of Contract Governance and who will be responsible for the day-to-day operations and delivery of the Services). These positions will function as the initial Relationship Management Structure until the long term Relationship Management Structure is implemented as described below. During such period, each Party will cause its representatives to participate in contract governance related discussions and work together to establish agendas and agreed upon tasks. These roles will continue within the Relationship Management Structure. |
| (b) | Within thirty (30) days after the Effective Date, the Parties will identify the titles of (i) the initial members of the committees set forth below in this Section 2.3 (Relationship Management Structure) and (ii) the initial representatives who will attend the meetings identified in Section 2.4 (Meetings) below, and will agree upon a process for replacement of committee members and meeting attendees, as applicable, during the Term. |
| (c) | Joint Steering Committee. |
| (i) | Triple-S and Supplier will jointly create a committee consisting of three (3) management employees from Triple-S and its Affiliates and three (3) management employees from Supplier who will focus on Triple-S’s and Supplier’s long-term strategic plans as they relate to the Services (“Joint Steering Committee”). |
| (ii) | The Joint Steering Committee will: |
| (A) | Meet at least monthly within the first six (6) months after the Effective Date, quarterly for the next six (6) months and then semi-annually thereafter, to discuss the evolving business agenda and strategic alignment of Triple-S and Supplier as it relates to the Services, including key Triple-S priorities; |
| (B) | Facilitate the goals of this Agreement; |
| (C) | Review performance against goals and revise such goals, as appropriate; |
Triple-S / Supplier Confidential
Page 3
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule F
Governance
| (D) | Approve and/or propose Changes to this Agreement, as appropriate; |
| (E) | Identify major Triple-S organization changes (i.e., people, processes, functions) or proposed changes affecting this Agreement; |
| (F) | Review industry and business trends and the impact of technology on the Services; |
| (G) | Evaluate Supplier industry initiatives for potential applicability to the Services; |
| (H) | Discuss future Triple-S service needs, including opportunities for additional collaboration and/or Supplier’s performance of additional services for Triple-S; |
| (I) | Upon Triple-S’s or Supplier’s request, assist in resolving issues arising under this Agreement; and |
| (J) | Participate in the dispute resolution process set forth in Section 26 (Dispute Resolution) of the General Terms and Conditions, as necessary. |
| (d) | Joint Management Committee. |
| (i) | Triple-S and Supplier will jointly create a committee consisting of three (3) management employees from Triple-S and its Affiliates and three (3) management employees from Supplier who will focus on management of the Triple-S and Supplier relationship and delivery of the Services (“Joint Management Committee”). |
| (ii) | The Joint Management Committee will: |
| (A) | Meet at least monthly within the first twelve (12) months after the Effective Date, and quarterly thereafter, to review tactical alignment, promote effective relationship management, and validate progress under this Agreement; |
| (B) | Develop and implement plans to meet the goals of this Agreement; |
| (C) | Review performance against the established Service Levels and address contractual or management problems and issues, as appropriate; |
| (D) | Assess the quality of Triple-S’s and Supplier’s working relationship and develop and implement action plans to strengthen such relationship, as appropriate; |
Triple-S / Supplier Confidential
Page 4
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule F
Governance
| (E) | Identify, manage and address issues affecting performance of the Services; |
| (F) | Identify and manage impending change; and |
| (G) | When appropriate, propose changes to the Joint Steering Committee regarding the Triple-S and Supplier relationship, and/or this Agreement. |
| (e) | Joint Operations Committee. |
| (i) | Within sixty (60) days after the Effective Date, Triple-S and Supplier will jointly create a committee (as agreed to by the Parties) comprised of employees of Triple-S and its Affiliates and employees of Supplier and its Affiliates (“Joint Operations Committee”) who will focus on the day-to-day operations and delivery of the Services. As part of the Joint Operations Committee, the Parties will work together to share information and reporting as reasonably necessary for the Joint Operations Committee, including such information from Triple-S Vendors. The Parties will also work together to consider whether a Managed Third Party or other Triple-S Vendor should be invited to participate in Joint Operations Committee and will work together to obtain such participation. Sub-committees will be established and meet as required to ensure IT (both Supplier and Triple-S) are connected to and listening to the needs of the business. Committees to be established may include Sales and Marketing Operations, Product Development, Claims, Service, Enrollment and Revenue Management, Pharmacy, PCPs/IPAs/Alliances, NW Management, Compliance, Ethics and Audits, STARS & Quality, Appeals’ & Grievances, BIA, Configuration, Medial Management, SALUS, TSP, TSV, and Finance. |
| (ii) | The Joint Operations Committee shall: |
| (A) | Meet at least every two (2) weeks within the first twelve (12) months after the Effective Date, and monthly thereafter, to review operational performance status and plans; |
| (B) | Review contract performance; |
| (C) | Review operational trends and analysis and take corrective action, as required; |
| (D) | Identify and address potential operational issues; |
| (E) | Identify and manage operational change; and |
| (F) | Make recommendations, as appropriate, to the Joint Management Committee. |
Triple-S / Supplier Confidential
Page 5
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule F
Governance
| (f) | Day-to-Day Operations. |
| (i) | Within the same timeframe in which the Committees are established, Triple-S and Supplier will identify interaction points for which each party will designate a primary and alternate point of contact. These interaction points are necessary to monitor day-to-day operations and act as necessary to address issues or ensure smooth execution of processes. |
| (ii) | The designations of those points of contact will be documented and maintained up to date by the Joint Operations Committee(s). |
| 2.4 | Meetings |
Within thirty (30) days after the Effective Date, the Parties will determine an appropriate set of meetings to be held between their representatives, which will include at least the following:
| (a) | Joint Steering Committee meetings, to be held not less than semi-annually (unless the Parties otherwise agree); |
| (b) | Joint Management Committee meetings, to be held not less than quarterly (unless the Parties otherwise agree); and |
| (c) | Joint Operations Committee meetings, to be held not less than monthly (unless the Parties otherwise agree). |
| 3. | ANNUAL TECHNOLOGY PLAN |
| (a) | As part of the governance process, Supplier will prepare an annual technology plan in accordance with the provisions of this Section 3 (Annual Technology Plan) (the “Technology Plan”). Each Technology Plan will include a review and assessment of the immediately preceding Technology Plan. The Technology Plan will consist of a three-year plan and an annual implementation plan as described below. |
| (b) | Contents of the Technology Plan. |
| (i) | The Technology Plan will include an assessment and strategic analysis of Triple-S’s then-current and future technology environments that are in-scope hereunder for the next three (3) years, including an assessment of the recommended direction for Triple-S’s systems and services in light of Triple-S’s business priorities and strategies and competitive market forces (to the extent such business information is available or provided to Supplier), including additional opportunities for the Parties to collaborate. The Technology Plan will include an identification of proposed Software and Equipment strategies and direction, a cost projection, a costs-vs.-benefits analysis of any proposed Changes, a description of the types of personnel skills and abilities needed to respond to any recommended Changes or upgrades in technology, a general plan and a projected time schedule |
Triple-S / Supplier Confidential
Page 6
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule F
Governance
for developing and achieving the recommendations made, and references to appropriate operating platforms that support Service Level requirements, exploit industry trends in production capabilities and provide potential price-performance improvement opportunities.
| (ii) | As necessary to support the overall objectives and directions of the three (3)-year plan, the annual implementation plan will provide guidance as to the information services requirements, projects and plans for the upcoming year, including information on operations, maintenance backlog and development activities. Supplier will prepare an annual implementation plan for each year of the Term. |
| (c) | Process for Developing the Technology Plan. |
| (i) | As part of the process of preparing the annual implementation plan, the Parties (working through the committees described above) will review the overall operation of this Agreement to ensure that the Services continue to be aligned with Triple-S’s strategic business and IT requirements. |
| (ii) | Supplier will submit the draft of the first Technology Plan (for the second Contract Year) within six (6) months after the Effective Date. Triple-S will review and provide comments on the draft. Supplier will review such comments and submit the final Technology Plan to Triple-S within thirty (30) days after receiving Triple-S’s comments on the draft. |
| (iii) | Supplier will submit the draft of the Technology Plan for the third and subsequent Contract Years not later than three months (3) months prior to the commencement of such Contract Year. The Parties may agree to make changes to the dates that the draft Technology Plan must be submitted by Supplier to Triple-S to coordinate it with and to support Triple-S’s annual business planning cycle and/or the timing of Joint Steering Committee meetings. Triple-S will review and provide comments on the draft. Supplier will review such comments and submit the final Technology Plan to Triple-S within thirty (30) days after receiving Triple-S’s comments on the draft. |
| (iv) | Supplier will update the Technology Plan during the year as necessary to reflect changes to Triple-S’s and its Affiliates’ businesses that materially affect the validity of the then-current Technology Plan. Supplier will recommend modifications to the Technology Plan as it deems appropriate, and will revise the Technology Plan as requested by Triple-S. |
| 4. | VENDOR GOVERNANCE |
Supplier will provide oversight and management of Managed Third Parties through its performance of the Managed Third Party Contract Services (see Section 2.4 of Schedule A).
Triple-S / Supplier Confidential
Page 7
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule F
Governance
| 5. | [***] |
Without limiting Supplier’s obligations under the Agreement, with respect to [***], Supplier will perform the following:
| (a) | Regularly communicate, and follow up on communications as needed, with designated Triple-S personnel who interface with [***] to facilitate delivery of the Services and completion of Projects relating to the [***] Software, as applicable; |
| (b) | Provide support to Triple-S in connection with Triple-S negotiations with [***] as they relate to the Services; |
| (c) | Coordinate and regularly communicate with Triple-S and [***] regarding issues arising during the performance of Projects or other Functions performed by [***] as they relate to the Services, including performance issues and any errors in deliverables provided by [***]. |
Triple-S / Supplier Confidential
Page 8
Schedule G
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
SCHEDULE G
In-scope employee agreement
| Schedule G | Triple-S / Supplier Confidential |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule G
In-Scope Employment Agreement
SCHEDULE G
IN-SCOPE EMPLOYEE AGREEMENT
IN-SCOPE EMPLOYEE AGREEMENT (this “Agreement”), executed on August 29, 2017, by and between INTERACTIVE SYSTEMS, INC., and a corporation organized and existing under the laws of the Commonwealth of Puerto Rico (“Interactive Systems”) and OPTUMINSIGHT, INC., a corporation organized and existing under the laws of Delaware (“Optum”).
WITNESSETH:
WHEREAS, Triple-S Salud, Inc. a company under common control with Interactive Systems, and Optum executed a Master Services Agreement dated August 29, 2017 (the “Master Services Agreement”), pursuant to which Optum agreed to provide infrastructure, application development, maintenance, business process, hosting and consulting services to Interactive Systems (the “Services”).
WHEREAS, Optum desires to leverage certain employees of Interactive Systems to assist Optum with the process of migrating and/or the ongoing performing the Services.
NOW, THEREFORE, in consideration of the mutual covenants and conditions set forth below, and other good and valuable considerations, the receipt and sufficiency of which are mutually acknowledged by Interactive Systems and Optum, the parties hereto hereby agree as follows:
| 1. | Provision of In-Scope Employees |
Subject to the terms and conditions of this Agreement, on August 31, 2017 (the “Effective Date”) Interactive Systems will make available to Optum the employees listed in Appendix A (the “In-Scope IT Employee(s))” or also interchangeably referred to as “In-Scope Employee(s)”, described below) to assist Optum in the process of performing the Services.
| (a) | In-Scope IT Employee(s) or In-Scope Employee(s) means individuals who are employed by Triple-S Salud or Interactive Systems as information technology employees who Triple-S Salud and Interactive Systems will make available for Optum to leverage in order to perform the Services. These employees will be identified in Appendix A, the list of which may include any addition, removal or replacement of employees during the Term of this Agreement. |
| (b) | In-Scope Employee Period (“Transition Period”), for each In-Scope Employee, means the period commencing on the Effective Date of this Agreement and continuing until the date Optum is required to make an offer of employment under Section 5 below. |
Triple-S / Supplier Confidential
Page 1
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule G
In-Scope Employment Agreement
| 2. | Term of the Agreement. |
This Agreement shall commence as of the Effective Date and shall remain in force so long as the Master Services Agreement remains in effect (the “Term”), unless sooner terminated as provided in Section 6 of this Agreement.
| 3. | Status of In-Scope Employee(s). |
| (a) | Employee Payroll and Benefits: Subject to the terms of this Section (including Optum’s obligations set forth in Section 3(b) below), In-Scope Employee(s) providing services to Optum under this Agreement shall at all times during the Term remain employees of Interactive Systems. Interactive Systems shall provide payroll, employment taxes, employee benefits, and workers compensation with respect to the In-Scope Employees. |
| (b) | Control and Supervision: All In-Scope Employees shall be subject to supervision, direction and control by Optum. Optum shall have full and exclusive responsibility to evaluate, train, supervise, promote, discipline and control the In-Scope Employees, and to determine which In-Scope Employees shall be designated to perform required tasks. Certain In-Scope Employees may hold supervisory positions and, in such capacity (unless otherwise determined by Optum), shall control and determine the procedures to be followed by other In-Scope Employees regarding the time, place and manner of performance of work for Optum by the In-Scope Employees, including determination of hours of work, rest periods, lunch periods and the delegation and assignment of work; provided, however, that such In-Scope Employees having supervisory responsibilities shall adhere to all of Interactive System’s policies, practices and contractual obligations if any, concerning days of vacation, sick time, leave and all other terms and conditions of employment. |
| (c) | Employee Removal: Optum shall have the right to have Interactive Systems remove any In-Scope Employee, specifically, as service provider to Optum for just cause. In this event, the removal of any In-Scope Employee for just cause shall not constitute a termination of employment by Interactive Systems. Just cause for purposes of this section shall generally mean if, among other things, any In-Scope Employee: fails to perform his/her duties satisfactorily; and/or violates Optum or Interactive Systems rules, regulations or policies. |
| (d) | Employee Replacement and Recruiting: Upon death, resignation or removal of any In-Scope Employee, Optum may elect to replace such In-Scope Employee. In the event Optum makes such election, it shall recruit qualified individuals as potential replacements for such In-Scope Employees. Upon Optum’s written notice to Interactive Systems of such recruitment, Interactive Systems shall hire (pursuant to Optum’s hiring decision-making process) such individuals and shall |
Triple-S / Supplier Confidential
Page 2
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule G
In-Scope Employment Agreement
commence to exert its functions of payroll, employment taxes, employee benefits, and workers compensation of such hired individual(s).
| (e) | Representations to Third Parties: In-Scope Employee(s) shall not be treated as agents or representatives of Optum and shall not have any authority or responsibility to enter into any contract or otherwise take any action in the name of or on behalf of Optum. |
| (f) | [***] Confidential Information: Optum shall exercise control and supervision of the In-Scope Employees and perform its other obligations under this Agreement strictly in accordance with the terms of in Section 10.7 and 19.19 of the Master Services Agreement. |
| 4. | Service Fees. |
| (a) | Reimbursement for Services and Other Reasonable Expenses: In exchange for exerting the functions of payroll, employment taxes, employee benefits, and workers compensation during the Term, Interactive Systems will be reimbursed by Optum for the salary, benefits and other reasonable overhead costs directly incurred in providing the In-Scope Employee(s) in accordance with the terms set forth in Appendix B. In addition, Optum shall reimburse Interactive Systems for reasonable expenses incurred by the In-Scope Employee(s) in the performance of services, provided that such expenses are supported by original receipts and the In-Scope Employee(s) obtain the prior authorization of Optum before incurring any such expenses. |
| (b) | Invoice Dispute: In case of a disputable invoice, Optum shall make a payment with the total amount of the invoice minus the disputed amount, along with a detailed schedule of the fees being disputed and the reason for the dispute. |
| (c) | Invoice due: All payments of amounts due under this Agreement will be made to Interactive Systems within [***] days upon delivery of invoice. Invoices will be generated at the end of every payroll period according to Interactive Systems’ payroll policies. |
| 5. | Offering of Employment to In-Scope Employees. |
From time-to-time during the Term, Interactive Systems may identify In-Scope Employees that Optum shall offer employment to (such employees, the “Transitioning Employees”), with the goal of Optum making an initial set of employment offers to certain Employees by December 31, 2017 and in any case prior to March 31, 2018 (such date, the “Initial Offer Date”). Optum represents and warrants that it will provide the Transitioning Employees it offers employment to with comparable compensation and benefits as required by applicable law, including Act 80. In all cases Optum shall offer employment to Transitioning Employees by the later of (a) the Initial Offer Date; and (b)
Triple-S / Supplier Confidential
Page 3
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule G
In-Scope Employment Agreement
sixty (60) days after Interactive Systems designates them as Transitioning Employees in writing to Optum.
| 6. | Termination of Agreement. |
This Agreement will automatically terminate if (i) the Master Services Agreement is terminated; or (ii) the parties mutually agree in writing to terminate this Agreement. For clarification, a material breach of this In-Scope Employee Agreement will be considered a material breach of the Master Services Agreement.
| 7. | Indemnification. |
| (a) | Interactive Systems will at its expense indemnify, defend and hold harmless Optum and its affiliates, and their respective officers, directors, employees, agents, representatives, successors and assigns, from and against any and all Losses (as defined in the Master Services Agreement) suffered or incurred by any of them arising from, in connection with or based on any claims by, or on behalf of the In-Scope Employees) (and/or by their collective bargaining representative and/or union, where applicable), with respect to matters arising out of the acts or omissions of Interactive Systems and/or Triple-S Salud’s agents or representatives occurring prior to the termination or expiration date of this Agreement, and/or with respect to the employment relationship between the In-Scope Employees and Interactive Systems and/or Triple-S Salud for acts or omissions attributable to any other Interactive System’s or Triple-S Salud’s employee not defined as an In-Scope Employee, but excluding claims for which Optum is required to indemnify Interactive Systems pursuant to Section 7(b) below. |
| (b) | Optum will at its expense indemnify, defend and hold harmless Interactive Systems and its affiliates, and their respective officers, directors, employees, agents, representatives, successors and assigns, from and against any and all Losses (as defined in the Master Services Agreement) suffered or incurred by any of them arising from, in connection with or based on (i) any claims from In-Scope Employees arising out of the acts and/or omissions of Optum after the Effective Date of this Agreement; (ii) any claims directly arising out of the termination of any In-Scope Employee(s) as a consequence of Optum choosing not to hire them upon the end of the applicable Transition Period, pursuant to Section 5 of this Agreement; (iii) any claims directly arising out of the termination of any In-Scope Employee(s) as consequence of Optum’s breach of Section 5 of this Agreement; and (iv) any claims arising out of the acts or omissions of the In-Scope Employees, agents or representatives towards any employee, agent or representative of Triple-S and its affiliates directly arising out of Optum’s breach of Section 3(b) of this Agreement, but excluding claims for which Interactive Systems is required to indemnify Optum pursuant to Section 7(a) above. |
Triple-S / Supplier Confidential
Page 4
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule G
In-Scope Employment Agreement
| 8. | Incorporation by Reference. |
All terms, provisions and agreements set forth in the Master Services Agreement with respect to confidentiality, non-solicitation, data-security protection, intellectual property rights, indemnification and dispute resolutions obligations are hereby made part of this Agreement to the same extent and with the same force as if they were fully set forth herein.
| 9. | Amendments. |
This Agreement may only be amended in writing and signed by all of the parties to this Agreement.
| 10. | Notices. |
All notices and communications shall be given in the manner, and shall be effective, as provided in Master Services Agreement.
| 11. | Binding Effect. |
This Agreement shall inure to the benefit of and be binding upon the parties hereto and their respective heirs, successors, representatives and assign. Neither party to this Agreement may assign its rights or delegate its duties hereunder without the express written consent of the other party, which consent shall not be unreasonably withheld.
| 12. | Execution in Counterpart. |
This Agreement may be executed in any number of counterparts and by different parties hereto in separate counterparts, each of which when so executed shall be deemed to be an original and all of which taken together shall constitute one and the same agreement. Delivery of an executed counterpart of a signature page to this Agreement by electronic means shall be effective as delivery of a manually executed counterpart of this Agreement.
| 13. | Headings. |
Section and other headings contained in this Agreement are for reference purposes only and shall not affect in any way the meaning or interpretation of this Agreement.
| 14. | Severability. |
If any part or condition of this Agreement is held to be void, invalid or inoperative, such shall not affect any other provision hereof, which shall continue to be effective as though such void, invalid or inoperative part, clause or condition had not been made.
Triple-S / Supplier Confidential
Page 5
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule G
In-Scope Employment Agreement
| 15. | Governing Law. |
This Agreement shall be governed by, and construed in accordance with, the laws of the Commonwealth of Puerto Rico without regard to its conflict of laws principles.
[Signature Page Follows]
Triple-S / Supplier Confidential
Page 6
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule G
In-Scope Employment Agreement
IN WITNESS WHEREOF, the parties hereto have caused this Agreement to be executed and delivered as of the date first above written.
INTERACTIVE SYSTEMS, INC.
| By: | /s/ ▇▇▇▇ ▇. ▇▇▇▇ | |
| Name: | ▇▇▇▇ ▇. ▇▇▇▇ | |
| Title: | President |
OPTUMINSIGHT, INC.
| By: | /s/ ▇▇▇▇ ▇▇▇▇▇▇ | |
| Name: | ▇▇▇▇ ▇▇▇▇▇▇ | |
| Title: | CEO, OptumInsight |
Triple-S / Supplier Confidential
Page 7
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule G
In-Scope Employment Agreement
Appendix A
In-Scope Employees
Interactive Systems provided Optum with an initial list of In-Scope Employees prior to the Effective Date, and will provide updates during the Term as necessary to keep the list current.
Triple-S / Supplier Confidential
Page 8
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule G
In-Scope Employment Agreement
Appendix B
Service Fees and Additional Compensation
| Charge per In-Scope Employee* | ||||
| Annual | Monthly | |||
| Overhead | [***] | [***] | ||
| Real Estate | [***] | [***] | ||
| Total | [***] | [***] | ||
[***]
Notwithstanding the calculations above, the adjustment shall not exceed [***] percent ([***]%) in any year. Triple S shall give Supplier notice of the applicable adjustment for each year during this Agreement within thirty (30) days after April 1 of such year, including detailed calculations and supporting documentation as to the determination of the adjustment and the resulting changes to the fees for such year.
Overhead and real estate charges will be paid monthly based on the number of In-Scope Employees during each month. For In-Scope Employees who cease to become an In-Scope Employee during a month, the monthly charges will be pro-rated for any partial month.
Triple-S / Supplier Confidential
Page 9
Schedule H
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
SCHEDULE H
BUSINESS ASSOCIATE AGREEMENT
This Business Associate Agreement is an addendum to the Agreement entered into to be effective as of August 31, 2017, by and between Triple-S Salud, Inc., a Puerto Rico corporation, with principal offices located at #1441 ▇.▇. ▇▇▇▇▇▇▇▇▇ ▇▇▇▇▇▇, ▇▇▇ ▇▇▇▇, ▇▇▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇ (hereafter, the Covered Entity) and OptumInsight, Inc., a Delaware corporation, having a primary place of business at ▇▇▇▇▇ ▇▇▇▇▇ ▇▇▇▇▇▇, ▇▇▇▇ ▇▇▇▇▇▇▇, ▇▇ ▇▇▇▇▇ (hereafter, the Business Associate).
WHEREAS, the Health Insurance Portability and Accountability Act of 1996 (“HIPAA”) and its implementing regulations (45 Code of Federal Regulations Parts 160-164) impose on Covered Entity and its Business Associates rules relating to the use, storage, transmission, and disclosure of protected health information pertaining to participants and beneficiaries in order to standardize communications and protect the privacy and security of individual health, insurance and financial information; and
WHEREAS, Business Associate requires access to Protected Health Information of participants and beneficiaries of Covered Entity to perform its obligations under the Underlying Agreement. The purpose of this Business Associate Agreement is to satisfy certain standards and requirements of HIPAA including, but not limited to, 45 C.F.R. §§164.308(b), 164.314(a), 164.502(e) and 164.504(e).
In consideration of the mutual promises below and the exchange of information pursuant to this Business Associate Agreement, intending to be legally bound hereby, Covered Entity and Business Associate agree as follows:
Section 1. Definitions
“Breach” shall have the same meaning given to the term in 45 CFR §164.402, as the impermissible acquisition, access, use, or disclosure of protected health information that compromises the security or privacy of the protected health information.
“Designated Record Set” shall have the same meaning as set forth in 45 C.F.R. §164.501.
“Disclosure” shall mean the release, transfer, and provision of access to or divulgation in any manner of information outside the entity holding the information, as set forth in 45 C.F.R. §160.103.
“IT Functions” shall refer to services related to business continuity, information system data integrity, and information confidentiality, security, storage, maintenance, and destruction.
Triple-S / Supplier Confidential
Page 1
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH "[***]". AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule H
Business Associate Agreement
“Business Continuity” shall mean the strategic and tactical capability of the organization to plan for and respond to incidents and business disruptions in order to continue business operations at an acceptable predefined level.
“System Data Integrity” shall refer to the processes and controls established by the organization to maintain and assure the accuracy and consistency of data over its entire life-cycle, and is a critical aspect to the design, implementation and usage of any system which stores, processes, or retrieves data.
“Effective date” shall mean the day and year first above written.
“HITECH Act” The Health Information Technology for Economic and Clinical Health Act, signed on February 17, 2009, promotes the adoption and meaningful use of health information technology. The HITECH Act also addresses what is a security breach and provides general guidelines on how Covered entities and Business Associates should handle security incidents in which unsecured PHI is exposed.
“Individual” shall have the meaning given to such term under the Privacy Rule, including, but not limited to, 45 C.F.R. §160.103 and shall include a person who qualifies as a personal representative in accordance with 45 CFR 164.502(g).
“Privacy Rules” shall mean the Standards for Privacy of Individually Identifiable Health Information as set forth under 45 CFR Part 160 and Part 164, Subparts A and E, as amended.
“Protected Health Information (PHI and E-PHI)” shall have the meaning given to the term at 45 C.F.R. §160.103 limited to the information created or received by Business Associate from or on behalf of Covered Entity.
“Required By Law” shall have the same meaning set forth in 45 C.F.R. §164.103.
“Secretary” shall mean the Secretary of the U.S. Department of Health and Human Services or his/her designee.
“Security Rules” shall mean the Security Standards for the Protection of Electronic Protected Health Information at 45 C.F.R. Part 160 and Part 164, Subparts A and C.
“Unsecured Protected Health Information” shall have the same meaning provided to the term at 45 C.F.R. §164.402.
Triple-S / Supplier Confidential
Page 2
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH "[***]". AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule H
Business Associate Agreement
Other terms used in this Business Associate Agreement, but not otherwise defined shall have the same meaning as those terms in HIPAA.
Section 2. Obligations of Business Associate
| a. | Functions and activities on behalf of Covered Entity. Business Associate may use or disclose Protected Health Information for the purpose of providing the Services or as otherwise permitted or required under this Business Associate Agreement or the Agreement, provided that such use or disclosure would not violate the Privacy Rules and Security Rules if done by Covered Entity. To the extent Business Associate is to carry out Covered Entity’s obligations under the Privacy Rule, Business Associate will comply with the requirements of the Privacy Rule that apply to Covered Entity in the performance of those obligations. |
| b. | Limited use and disclosure. Business Associate shall not use or further disclose PHI other than as permitted or required by this BAA, or as required by law or as otherwise authorized by Covered Entity. |
| c. | Proper handling of PHI. Business Associate shall have in place and have its workforce, agents and subcontractors trained on formalized policies, procedures, protocols and mechanisms to handle PHI in a responsible manner in order to prevent unauthorized access, uses, disclosures or acquisition of PHI. |
| d. | Prohibition on sale of PHI. Business Associate shall not directly or indirectly receive remuneration in exchange for any PHI of an individual unless the Covered Entity obtains from the individual a valid authorization that includes a specification of whether the PHI can be exchanged for remuneration by the entity receiving PHI of that individual. |
| e. | Prohibition on requesting information related to medical services or procedures paid in its entirety by the individual. The Business Associate will not require information related to medical services and procedures paid in its entirety by the individual, unless that information is necessary to take a determination and the authorization of the individual is obtained. |
| f. | De-identified information. Business Associate may use or disclose protected health information that has been de-identified in accordance with the standards set forth at 45 C.F.R. §164.514(a), (b), and (c ). |
| g. | Minimum necessary. Business Associate shall limit its uses, disclosures and requests for PHI to that which is reasonably necessary to accomplish the intended purposes of such use, disclosure and/or request consistent with the minimum necessary requirements under HIPAA. Moreover, Business Associate shall disclose the minimum necessary PHI to perform its obligations to the Covered Entity only (i) to its employees, |
Triple-S / Supplier Confidential
Page 3
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH "[***]". AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule H
Business Associate Agreement
subcontractors, and agents (ii) as directed by Covered Entity; or (iii) as otherwise permitted by the terms of this Business Associate Agreement.
| h. | Transfer of data. Transfer, exchange or sharing of data information between the Business Associate, the Covered entity and its agents or subcontractors shall be conducted using secure means to protect PHI against the access or intrusion of third unauthorized parties. Business Associate and Covered Entity will agree on the best methodology to exchange data in a safely and secure manner as stated in the Security Rule, including all repositories that may contain PHI/ IIHI. |
| i. | [Reserved] |
| j. | Security and annual risk assessments. Business Associate shall use and maintain technical, administrative and physical safeguards as set forth in 45 C.F.R. §§164.308, 164.310, and 164.312 that reasonably and appropriately protect the confidentiality, integrity, and availability of e-PHI. Business Associate shall conduct a security risk assessment at least on an annual basis. |
| k. | Subcontractors. Business Associate shall ensure that any subcontractor or agent that create, receive, maintain, or transmit PHI on behalf of Business Associate agree to the same restrictions and conditions that apply to Business Associate with respect to such information. If Business Associate becomes aware of a pattern of activity or practice of a Subcontractor that would constitute a material breach or violation of the written agreement between Business Associate and Subcontractor, Business Associate shall (1) take reasonable steps to cure such breach or end the violation, if any and as applicable, or, if feasible, terminate such written agreement with such Subcontractor if such steps were unsuccessful. |
| l. | Except as otherwise limited in this Business Associate Agreement, Business Associate may: |
| (a) | Use PHI in its possession, but only to the minimum extent necessary, for the proper management and administration of Business Associate or to carry out the legal responsibilities of Business Associate if such uses are permitted under applicable state and federal confidentiality laws. |
| (b) | Disclose PHI to third parties, but only to the minimum extent necessary, for the proper management and administration of Business Associate or to carry out the legal responsibilities of Business Associate, provided that (i) the disclosures are Required By Law, as provided under 45 C.F.R. Section 164.501, or (ii) Business Associate obtains reasonable written assurances from the third party to whom the information is disclosed that such information shall be held confidentially in accordance with the Privacy Rules and shall be used or further disclosed only as required by law or for the purpose for which it was disclosed |
Triple-S / Supplier Confidential
Page 4
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH "[***]". AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule H
Business Associate Agreement
to such third party, and such third party notifies Business Associate of any instance of which the confidentiality of the information has been breached.
| (c) | Use for reporting of violations of law to appropriate Federal and State authorities, consistent with 45 C.F.R. §164.502(j) (1). |
| (d) | Use for data aggregation services. Use the information to provide data agregation services related to the health care operations (as such term is defined in 45 C.F.R. §164.501) of Covered Entity, as permitted by 45 C.F.R. §164.504(e)(2)(i)(B), if requested by Covered Entity in writing. |
| m. | Reporting of any unauthorized use or disclosure. Report to Covered Entity, as promptly as practicable and, in any case, within forty-eight (48) hours , any use or disclosure of PHI of which Business Associate becomes aware that is not provided for in this Business Associate Agreement or the Agreement. The report shall include the identification of each individual whose Unsecured PHI has been or is reasonably believed by the Business Associate to have been accessed, acquired, or disclosed during such Breach. |
| n. | Unsuccessful Security Incidents. The parties acknowledge that this paragraph constitutes notice by Business Associate to Covered Entity of the ongoing existence and occurrence or attempts of Unsuccessful Security Incidents for which no additional notice to Covered entity shall be required. “Unsuccessful Security Incident” means, without limitation, pings and other broadcast attacks on Business Associate’s firewall, port scans, unsuccessful log-on attempts, denial of service attacks, and any combination of the above, so long as no such incident (i) results in unauthorized access to, use, or disclosure of PHI or (ii) adversely affects the ability of Business Associate to maintain, process or safeguard PHI of Covered Entity. This paragraph reflects the parties’ determination under 45 C.F.R. §164.306(b) that the effort and expense required for Business Associate’s accurate reporting of Unsuccessful Security Incidents to Covered Entity would significantly outweigh any benefit that might be achieved through such reporting and, accordingly, that requiring reporting of Unsuccessful Security Incidents would not be reasonable or appropriate. |
| o. | Mitigation and corrective actions. Establish procedures to mitigate and correct, to the extent practicable, any harmful effect that is known to Business Associate of a use or disclosure of PHI by Business Associate or any of its agents in violation of the requirements of this Business Associate Agreement, including the duty to notify affected individuals due to a Breach of Unsecured PHI pursuant to §§13401-13402 of the American Recovery and Reinvestment Act of 2009, Public Law 111-5. |
| p. | Breach notification. Following the discovery of a Breach of Unsecured PHI, Business Associate: |
Triple-S / Supplier Confidential
Page 5
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH "[***]". AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule H
Business Associate Agreement
| 1) | Shall provide written notice to Covered Entity of such Breach as promptly as practicable and, in any case, within forty-eight (48) hours following Business Associate’s discovery of the same. Business Associate shall furnish subsequent reports with additional information as reasonably required by Covered Entity. A Breach shall be treated as discovered by Business Associate as of the first day on which such Breach is known to Business Associate or, through the exercise of reasonable diligence, would have been known to Business Associate. Notwithstanding the foregoing, if a law enforcement official states to Business Associate that notification of a Breach would impede a criminal investigation or cause damage to national security, then Business Associate shall delay such notification for the time period specified by the official. |
| 2) | The Breach notification provided to Covered Entity shall include, to the extent possible: (i) the identification of each individual whose Unsecured PHI has been, or is reasonably believed by Business Associate to have been accessed, acquired, used or disclosed during the Breach; (ii) a brief description of the incident, including the date of the Breach and the date of discovery of the Breach, if known; (iii) a description of the types of Unsecured PHI that were involved in the Breach (such as whether full name, Social Security number, date of birth, home address, account number, diagnosis, medical procedures, or other types of information were involved); (iv) any steps individuals should take to protect themselves from potential harm resulting from the Breach; (v) a description of what Business Associate is doing to investigate the Breach, to mitigate harm to individuals, and to protect against any further Breach; and (vi) contact procedures for individuals to ask questions or learn additional information, which shall include a toll-free telephone number, an e-mail address, Website or postal address. |
| q. | Corrective Measures. Business Associate shall adopt corrective measures if any violation to the terms of this Business Associate Agreement is detected. |
| r. | Access to the Secretary. Business Associate shall make available its internal practices, books and records relating to the use and disclosure of PHI hereunder to the United States Secretary of Health or its designees for purposes of determining Covered Entity’s compliance with the Privacy and Security Rules. |
| s. | Amendments to Protected Health Information. Within ten (10) business days following Business Associate’s receipt of a written request from the Covered Entity, Business Associate shall incorporate any amendments or corrections to PHI in Designated Record Sets when notified and as required by Covered Entity, the beneficiary or his representative that the information is inaccurate or incomplete or as otherwise required by Covered Entity, all in compliance with the standards set forth in 45 C.F.R. §164.526. |
| t. | Access to PHI. Within ten (10) business days following Business Associate’s receipt of a written request from the Covered Entity, Business Associate shall make available PHI contained in a Designated Record Set to Covered Entity or, if directed to do so in |
Triple-S / Supplier Confidential
Page 6
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH "[***]". AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule H
Business Associate Agreement
specifications and limitations included in the Privacy Rule or other applicable legal requirements.
| u. | Accounting of Disclosures. Business Associate shall maintain and, within ten (10) business days following Business Associate’s receipt of a written request from the Covered Entity, make available PHI requested by Covered Entity or an individual as required to provide an Accounting of disclosures in accordance with 45 C.F.R.§164.528. Such information shall be provided to Covered Entity, unless Covered Entity directs Business Associate in writing to make the Accounting directly to the individual. |
| v. | Requests for restrictions. Business Associate shall comply with any requests for restrictions on certain disclosures of PHI to which Covered Entity has agreed in accordance with 45 C.F.R. §164.522 and of which Business Associate has been notified by Covered Entity. |
| w. | Authentication of individuals. Institute and maintain procedures that meet the requirements of the Privacy Rule to reasonably verify the identity of an individual requesting access to, or requesting an amendment or accounting of PHI in a Designated Record Set. |
| x. | Disclosures for Legal Orders and administrative proceedings. Business Associate may disclose PHI in the course of any judicial or administrative proceeding in accordance with 45 C.F.R. §164.512(e ). If legally permissible, following receipt of any order from a court or administrative tribunal or a subpoena, discovery request, or other lawful process that is not accompanied by an order of a court or administrative tribunal, Business Associate shall provide Covered Entity with prompt notice of such order or process. If possible, Business Associate shall provide such notice to Covered Entity prior to the disclosure of any PHI. Business Associate shall cooperate with reasonable requests of Covered entity in responding to such order or process. |
| y. | Shredding, Destruction or Storage of PHI. Business Associate will comply with ensuring the most appropriate secure measures, as stated under the Security Rule for the shredding, destruction and/or storage of documents containing PHI, including the onsite repositories, and if deemed necessary securing offsite transportation of the information. |
| z. | Compliance with IT Functions. Business Associate will comply with maintaining appropriate policies and procedures for securing all data containing PHI with their business continuity plan, where their contingency for operations shall have established and implemented procedures, as needed, that allow facility access in support of restoration of lost data under the disaster recovery plan and/or emergency mode operations plan in the event of an emergency. |
| · | Business Associate will implement policies and procedures to limit physical access to its electronic information systems and the facility or facilities in which |
Triple-S / Supplier Confidential
Page 7
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH "[***]". AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule H
Business Associate Agreement
they are housed, while ensuring that properly authorized access is allowed for the receipt and removal of hardware and electronic media that contain electronic PHI into and out of a facility, and the movement of these items within the facility.
| · | Business Associate will implement security measures to ensure that electronically transmitted electronic protected health information is not improperly modified without detection until disposed of, therefore securing appropriate system data integrity procedures to ensure statistical accuracy. |
| aa. | Compliance with Standard Transactions. Business Associate shall comply and require its agents or subcontractors to comply with each applicable requirement for standard transactions established in 45 CFR Part 162 when conducting all or any part of a Standard Transaction, electronically for, or on behalf of, Covered Entity, if applicable. |
| bb. | Other representations. Business Associate represents and warrants to Covered Entity: |
| (a) | that all of its employees, agents, representatives and members of its workforce whose services may be used to fulfill obligations under this Business Associate Agreement are or shall be appropriately trained as required by the Privacy Rule, and are under legal obligation to Business Associate, by contract or otherwise, sufficient to enable Business Associate to fully comply with all provisions of this Business Associate Agreement with respect to the Privacy Rule. |
| (b) | that it will reasonably cooperate with Covered Entity in the performance of the mutual obligations under this Business Associate Agreement with respect to the Privacy Rules. |
| (c) | that it will notify Covered Entity immediately upon becoming aware that any of the foregoing representations and warranties may be inaccurate or may become inaccurate. |
Section 3. Obligations of Covered Entity
Covered Entity shall:
| (a) | Notify Business Associate of any limitations in its Notice of Privacy Practices to the extent that such restriction may affect Business Associate’s use or disclosure of PHI. |
| (b) | Notify Business Associate of any changes in, or revocation of, permission by an individual to use or disclose PHI, to the extent that such changes may affect Business Associate’s use or disclosure of PHI. |
Triple-S / Supplier Confidential
Page 8
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH "[***]". AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule H
Business Associate Agreement
| (c) | Notify Business Associate of any restriction to the use or disclosure of PHI to which Covered Entity has agreed, to the extent that such restriction may affect Business Associate’s use or disclosure of PHI. |
| (d) | Covered Entity shall not request Business Associate to use or disclose PHI in any manner that would not be permissible under the Privacy and Security Rules if done by Covered Entity. |
Section 4. Term and Termination.
| a. | Term. The Term of this Business Associate Agreement shall be effective as of the Effective Date, and shall terminate on the later of (i) the effective date of termination or expiration of the Agreement; and (ii) when all of the PHI provided by Covered Entity to Business Associate, or created or received by Business Associate on behalf of Covered Entity, is destroyed or returned to Covered Entity after the expiration date of the underlying agreement, or if it is unfeasible to return or destroy PHI, protections are extended to such information, in accordance with the termination provisions in this section. |
| b. | Termination for Cause by Covered Entity. If Covered Entity determines that Business Associate has committed a material breach of this Business Associate Agreement, Covered Entity shall (i) provide Business Associate with written notice of the breach within ten (10) days after discovering the alleged breach (“Notice of Breach”); and (ii) afford Business Associate an opportunity to cure such breach within thirty (30) days of the Notice of Breach. Failure to cure in the manner set forth under this Section shall constitute grounds for immediate termination of this Business Associate Agreement and the Agreement. Further, Triple-S may terminate this Business Associate Agreement upon notice to Supplier if Supplier commits a material breach of this Business Associate Agreement and Triple-S is required to terminate in order to comply with Applicable Law or direction from a Regulator. |
| c. | Effect of Termination. Within thirty (30) days termination of this Business Associate Agreement for any reason. |
| (a) | Business Associate shall, if feasible, return or destroy all Protected Health Information received from Covered Entity, or created or received by Business Associate on behalf of Covered Entity. This provision shall also apply to PHI that is in the possession of subcontractors or agents of Business Associate. Business Associate shall retain no copies of the PHI, except where return or destruction is infeasible. |
Triple-S / Supplier Confidential
Page 9
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH "[***]". AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule H
Business Associate Agreement
| (b) | In the event that Business Associate determines that returning or destroying the PHI is infeasible, Business Associate shall provide Covered Entity notification in writing, and Business Associate, its agents and subcontractors shall extend the protections of this Business Associate Agreement to such PHI and limit further uses and disclosures of such PHI to those purposes that make the return or destruction infeasible, for so long as Business Associate, its agents and subcontractors maintain such PHI. |
Survival. All the obligations of Business Associate to protect Protected Health Information shall survive the termination of this Business Associate Agreement, and the Agreement, for as long as Business Associate maintains such Protected Health Information.
Transition Assistance. Following the termination of this Agreement for any reason, Business Associate agrees to provide transition services as described in Section 17 of the Agreement
Section 5. Miscellaneous provisions
Notices. All notices, demands, claims, requests, and other communications which may be or are required to be given hereunder or with respect hereto shall be in writing, will either be given by personal delivery, by mail or overnight courier, or by fax, and shall be deemed to have been given or made when personally delivered, and otherwise when received, addressed to the respective Parties as follows:
TO COVERED ENTITY:
| Attn: Dallila ▇▇▇▇▇▇▇ ▇▇▇▇ | |||
| Corporate Ethics and Compliance Director – Office of Legal Affairs | |||
| Triple-S | |||
| Telephone: | |||
| Fax: | |||
| ▇▇ ▇▇▇ ▇▇▇▇▇▇ | |||
| ▇▇▇ ▇▇▇▇, ▇▇, ▇▇▇▇▇-▇▇▇▇ | |||
TO BUSINESS ASSOCIATE:
|
Name: General Counsel, OptumInsight, Inc. |
|||
| Telephone: | |||
| Fax: | |||
| Postal Address: ▇▇▇▇▇ ▇▇▇▇▇ ▇▇▇▇▇▇ | |||
| ▇▇▇▇ ▇▇▇▇▇▇▇, ▇▇ ▇▇▇▇▇ | |||
Triple-S / Supplier Confidential
Page 10
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH "[***]". AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule H
Business Associate Agreement
Interpretation. Any ambiguity in this Business Associate Agreement shall be resolved in favor of a meaning that permits the Parties to comply with the Privacy Rule, federal and local rules or statutes regarding the confidentiality and security of PHI. A reference in this Business Associate Agreement to a section of the Privacy Rule means the section as in effect or as amended.
Amendments required by law. If HIPAA, the HITECH Act or other legal requirements relating to the protection of Protected Health Information are instituted mandating an amendment of certain provisions within this Business Associate Agreement, the Parties agree that this Agreement is amended pursuant to said mandate without further consent of the parties.
Audit and Records Retention. Schedule M (Audit and Record Retention) contains audit and record retention terms applicable to this Business Associate Agreement.
Disputes. If any controversy, dispute or claim arises between the Parties with respect to this Business Associate Agreement, the Parties shall resolve it pursuant to the dispute resolution terms provided in the General Terms and Conditions of the Agreement.
Injunction. Business Associate hereby agrees that Covered Entity may suffer irreparable damage upon Business Associate’s breach of the provisions of this Agreement and that such damages may be difficult to quantify. Business Associate hereby agrees that Covered Entity may file an action for an injunction to enforce the terms of this Business Associate Agreement against Business Associate, in addition to any other remedy Covered Entity may have.
Severability. If any provision of this Business Associate Agreement is held by a court of competent jurisdiction to be illegal, invalid, or unenforceable under present or future laws effective during the term of this Business Associate Agreement, the legality, validity, and enforceability of the remaining provisions of this Business Associate Agreement shall not be affected thereby.
IN WITNESS WHEREOF, each of the following undersigned has caused this Business Associate Agreement to be duly executed.
| Triple-S Salud, Inc., | OptumInsight, Inc. | |
|
/s/ ▇▇▇▇▇▇▇▇ ▇▇▇▇▇▇▇▇▇-▇▇▇▇▇▇▇ |
/s/ ▇▇▇▇ ▇▇▇▇▇▇▇▇ |
|
| Name: ▇▇▇▇▇▇▇▇ ▇▇▇▇▇▇▇▇▇-▇▇▇▇▇▇▇ | Name: ▇▇▇▇▇▇▇▇ ▇▇▇▇▇▇▇▇▇-▇▇▇▇▇▇▇ | |
| Title: President | Title: Deputy General Counsel |
Triple-S / Supplier Confidential
Page 11
Schedule I
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
SCHEDULE I
DISENGAGEMENT ASSISTANCE
| Schedule I | Triple-S / Supplier Confidential |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule I
Disengagement Assistance
SCHEDULE I
Disengagement Assistance
TABLE OF CONTENTS
| 1. Introduction | 1 |
| 2. Definitions | 1 |
| 3. General Terms | 2 |
| 3.1 Overview of Disengagement Assistance | 2 |
| 3.2 Compensation for Disengagement Assistance | 3 |
| 3.3 Audit Rights | 3 |
| 4. Disengagement Assistance Planning | 3 |
| 4.1 Disengagement Assistance Plan | 3 |
| 4.2 Supplier Responsibilities Under the Disengagement Assistance Plan | 4 |
| 5. Resource Transition | 5 |
| 5.1 General Terms | 5 |
| 5.2 Supplier Equipment | 6 |
| 5.3 Supplier Third Party Service Contracts | 7 |
| 5.4 Software and Tools | 7 |
| 5.5 Telephone Numbers | 8 |
| 5.6 Unidentified Assets | 8 |
| 5.7 Human Resources | 9 |
| 6. Supplier Disengagement Assistance Team | 10 |
| 7. Operational Transition | 10 |
| 8. Organizational Transition | 14 |
| 9. Business Continuity and Disaster Recovery Transition | 15 |
| 10. Knowledge Transfer | 15 |
| 11. Financial Transition | 16 |
| 12. Risk Mitigation | 17 |
Triple-S/Supplier Confidential
Page ii
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
SCHEDULE I
Disengagement Assistance
| 1. | Introduction |
| (a) | With reference to (and without limiting) Section 17 (Disengagement Assistance) of the General Terms and Conditions, this Schedule I (Disengagement Assistance) sets forth terms relating to the provision of Disengagement Assistance by Supplier. |
| (b) | The primary purpose of Disengagement Assistance, and Supplier’s goal in providing it, shall be to: |
| (i) | assist in enabling Triple-S to obtain from a Successor Supplier, or to provide for itself and other Service Recipients, each in an efficient manner without adverse effect on the continuity of operations or otherwise, services to substitute for or replace the Services; and |
| (ii) | minimize any adverse effect of transferring responsibility for providing the Services to Triple-S or to a Successor Supplier. |
| (c) | In the event of a conflict between the provisions of this Schedule I and other parts of this Agreement, the provisions of Section 27.11 (Order of Precedence) of the General Terms and Conditions shall apply. |
| 2. | Definitions |
Capitalized terms are defined in Schedule AA (Glossary) to this Agreement, in the place where they are used, or have the meanings set forth below:
| (a) | “Affected Services” means the Services for which Disengagement Assistance is requested by Triple-S to be provided by Supplier pursuant to and in accordance with Section 17 (Disengagement Assistance) of the General Terms and Conditions. |
| (b) | “Affected Supplier Third Party Service Contracts” has the meaning given in Section 5.3(a). |
| (c) | “Affected Supplier Personnel” has the meaning given in Section 5.7(a)(i). |
| (d) | “Cutover Date” means, for any Affected Services, the corresponding effective date of the cessation of, or the termination or expiration (as applicable) of, Supplier’s obligation under this Agreement to provide such Affected Services (as such effective date may be extended pursuant to this Agreement). |
| (e) | “Discovery Notice” has the meaning given in Section 5.6. |
| (f) | “Disengagement Assistance Plan” has the meaning given in Section 4.1(a). |
Triple-S/Supplier Confidential
Page 1
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule I
Disengagement Assistance
| (g) | “Disengagement Event” means any event (e.g., withdrawal of Services, notice of termination, Agreement expiration) that gives Triple-S the right to request Disengagement Assistance pursuant to Section 17 (Disengagement Assistance) of the General Terms and Conditions. |
| (h) | “Financial Reconciliation Period” has the meaning given in Section 11. |
| (i) | “Knowledge Transfer Plan” has the meaning given in Section 10(b). |
| (j) | “Resources” has the meaning given in Section 5.1(a). |
| (k) | “Supplier Disengagement Assistance Lead” has the meaning given in Section 6. |
| (l) | “Supplier Leased Equipment” has the meaning given in Section 10.2(b) (Equipment) of the General Terms and Conditions. |
| (m) | “Supplier Non-Personnel Resource Obligations” has the meaning given in Section 5.1(c). |
| (n) | “Supplier Owned Equipment” has the meaning given in Section 5.2. |
| (o) | “Supplier Personnel Information” has the meaning given in Section 5.7(a). |
| (p) | “Supplier Personnel Resource Obligations” has the meaning given in Section 5.1(c). |
| (q) | “Unidentified Asset” has the meaning given in Section 5.6. |
| 3. | General Terms |
| 3.1 | Overview of Disengagement Assistance |
| (a) | Supplier shall, upon Triple-S’s request in accordance with Section 17 (Disengagement Assistance) of the General Terms and Conditions, provide Disengagement Assistance with respect to the Affected Services in accordance with Section 17 (Disengagement Assistance) of the General Terms and Conditions. Supplier shall continue to perform the Affected Services in accordance with the Agreement until the applicable Cutover Dates, but no longer than the periods set forth in the General Terms and Conditions. |
| (b) | Supplier shall provide Disengagement Assistance pursuant to a Disengagement Assistance Plan (as set forth in Section 4). |
| (c) | To the extent that Supplier has used a Subcontractor to provide any part of the Affected Services, Supplier shall cause such Subcontractor to comply with Supplier’s obligations set forth in this Schedule I with respect to such Affected Services. |
Triple-S/Supplier Confidential
Page 2
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule I
Disengagement Assistance
| (d) | Supplier shall use Commercially Reasonable Efforts to minimize Triple-S’s costs and management time resulting from the cessation of the Affected Services and to minimize the implementation time for the transfer of the Affected Services to Triple-S and/or its Successor Supplier(s). |
| 3.2 | Compensation for Disengagement Assistance |
| (a) | Triple-S shall fully compensation Supplier for the provision of Disengagement Assistance as set forth in Section 17.3 (Charges for Disengagement Assistance) of the General Terms and Conditions. The provision of Disengagement Assistance shall not be subject to any other charges by Supplier. |
| (b) | As Services are transitioned from Supplier during the Disengagement Assistance Period, Supplier shall reduce the Charges to Triple-S as, and to the extent that, the resource utilization volumes specified in the applicable Statement of Work or Task Order decline, and the resources otherwise used by Supplier in performing the Services are reduced as a result of such transition in accordance with the agreed Disengagement Assistance Plan. |
| 3.3 | Audit Rights |
Triple-S may audit the accuracy of information provided by Supplier under this Schedule I in accordance with Schedule M (Audit and Record Retention Requirements).
| 4. | Disengagement Assistance Planning |
| 4.1 | Disengagement Assistance Plan |
| (a) | As part of its obligations to provide Disengagement Assistance, Supplier shall assist Triple-S and the Successor Supplier in preparing and subsequently revising a disengagement plan for the transition of any Affected Services (which may include major transition activities, schedules, and milestones) and, if applicable, the transfer of corresponding assets to Triple-S or the Successor Supplier (any such plan, a “Disengagement Assistance Plan”). Without limiting the generality of the foregoing, such assistance shall include: |
| (i) | prior to the fifth anniversary of the Effective Date, preparing an initial draft Disengagement Assistance Plan that includes the information necessary for Supplier to perform the Disengagement Assistance described in this Schedule I; |
| (ii) | preparing input for the Disengagement Assistance Plan detailing how Supplier shall perform, during the Disengagement Assistance Period, its responsibilities to provide (A) the Affected Services before the corresponding Cutover Dates for each Affected Service, and (B) Disengagement Assistance with respect to the Affected Services; |
Triple-S/Supplier Confidential
Page 3
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule I
Disengagement Assistance
| (iii) | reviewing draft versions of the Disengagement Assistance Plan and subsequent revisions, and identifying to Triple-S (A) material risks associated with Triple-S’s proposed plans for Disengagement Assistance (including any potential disruption in the Affected Services before the corresponding Cutover Dates, disruption to the other Services being provided by Supplier, and disruption to Triple-S’s business or other third party services), and suggested means by which such risks may be mitigated, and (B) operational constraints that may impact Triple-S’s proposed plans; and |
| (iv) | Subject to Section 17 (Disengagement Assistance) of the General Terms and Conditions, providing other information regarding the Affected Services or Supplier’s performance of Disengagement Assistance with respect to the Affected Services that may be reasonably requested by Triple-S in connection with the preparation or subsequent revision of the Disengagement Assistance Plan. |
| (b) | Triple-S or the Successor Supplier shall be responsible for finalizing and managing the overall Disengagement Assistance Plan. |
| 4.2 | Supplier Responsibilities Under the Disengagement Assistance Plan |
| (a) | Supplier Performance. Supplier shall manage and perform its responsibilities under the Disengagement Assistance Plan. |
| (b) | Handover of Records. The Disengagement Assistance Plan shall set forth a detailed plan for Supplier to deliver to Triple-S the Triple-S Data required by Triple-S, including the records described in Section 5 (Records Retention) of Schedule M (Audit and Record Retention Requirements) and in this Schedule I. This plan shall describe the migration of such data and records from Supplier to Triple-S, including the applicable schedule, file formats, medium of transmission, and applicable criteria for acceptance of delivered data and records. |
| (c) | Modification of Supplier Responsibilities. Triple-S may, from time to time and subject to the Change Control Process, modify Supplier’s responsibilities under the Disengagement Assistance Plan in order to meet the evolving dynamics of implementing the goals of the plan; provided, however, that Triple-S shall consult with Supplier in defining or modifying Supplier’s responsibilities, and shall consider, and use reasonable efforts to accommodate, Supplier’s reasonable input. |
| (d) | Risk Assessment. Within thirty (30) days after commencement of the Disengagement Assistance Services, Supplier shall perform and provide a risk assessment, identify any material additional risk factors relating to the migration of the Services to Triple-S and any Successor Supplier, and recommend activities to mitigate such risks. |
Triple-S/Supplier Confidential
Page 4
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule I
Disengagement Assistance
| 5. | Resource Transition |
| 5.1 | General Terms |
| (a) | Access to Resources. During the Disengagement Assistance Period, Supplier shall provide to Triple-S and any Successor Supplier reasonable and timely access to and use of information regarding the Equipment, Software, Tools, third parties (including Subcontractors), third party contracts (including leases, licenses and contracts), Documentation and other materials or information about the resources that are used to provide the Affected Services (collectively the “Resources”) and Supplier Personnel, in each case, consistent with Section 17.1(f) (Disengagement Assistance) of the General Terms and Conditions and other applicable restrictions set forth in the Agreement, for the purpose of transitioning responsibility for the Affected Services to Triple-S or the Successor Supplier. |
| (b) | Management of Resources. During the Disengagement Assistance Period, Supplier shall obtain Triple-S’s prior written approval before (i) taking any action or actions with respect to the removal, reassignment, transfer or disposal of any Resources used to provide the Services, which Triple-S is entitled to acquire as part of Disengagement Assistance, or (ii) proposing, amending or extending the terms of (or entering into new) agreements governing such Resources used to provide the Services, which Triple-S is entitled to acquire as part of Disengagement Assistance. |
| (c) | Transfer of Resources. |
| (i) | Section 17.2 (Required Consents) of the General Terms and Conditions sets forth certain Supplier obligations relating to obtaining Required Consents with respect to Resources. |
| (ii) | Supplier shall provide reasonable assistance required for, and take reasonable actions (including by executing documents) necessary to affect, the transfer of Resources as contemplated in this Section 5 and Section 17 (Disengagement Assistance) of the General Terms and Conditions (to the extent Triple-S requests such transfers). Supplier shall use Commercially Reasonable Efforts to minimize the costs associated with the transfer of, or assumption of responsibility for, Resources pursuant to this Section 5 and Section 17 (Disengagement Assistance) of the General Terms and Conditions. |
(iii) Unless otherwise agreed by the Parties, the effective date of any transfer of Resources pursuant to this Section 5 shall be the Cutover Date for the corresponding Affected Services; provided, however, that any such transfer shall not take place before the Cutover Date for the corresponding Affected Services unless mutually agreed by the Parties in writing.
| (iv) | Triple-S shall not assume, and shall not be liable for, any of Supplier’s or any of its Subcontractor’s obligations to any third party with respect to any non- |
Triple-S/Supplier Confidential
Page 5
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule I
Disengagement Assistance
personnel Resource owned, leased, licensed, or contracted for by Supplier or any of its Subcontractors (such obligations collectively the “Supplier Non-Personnel Resource Obligations”), and Supplier shall be responsible for performing such Supplier Non-Personnel Resource Obligations. Triple-S shall only be responsible for any of such obligations that arise after the date that the underlying Resource is transferred to Triple-S.
| (v) | Triple-S shall not assume, and shall not be liable for, any claims, obligations, or liabilities of any kind or nature with respect to any personnel Resource that arise out of (A) Supplier’s relationship as the employer of such person, or (B) a contractual arrangement with such person (such obligations collectively “Supplier Personnel Resource Obligations”), and Supplier shall be responsible for performing such Supplier Personnel Resource Obligations. |
| 5.2 | Supplier Equipment |
| (a) | Subject to Section 5.1(a), Supplier shall provide information to Triple-S or the Successor Supplier concerning: (i) the Equipment owned by Supplier (and its Subcontractors) that is used to perform the Affected Services (collectively, the “Supplier Owned Equipment”); and (ii) Supplier Leased Equipment. All such information shall include a complete inventory of such Supplier Owned Equipment and Supplier Leased Equipment (in Microsoft Excel format) specifying make, model, location, the corresponding Services such Supplier Owned Equipment and Supplier Leased Equipment are used to provide, whether such Equipment is dedicated to providing the Services or whether Supplier utilizes such Equipment for other customers, and such other information as Triple-S may reasonably request. With respect to Supplier Owned Equipment or Supplier Leased Equipment for which Triple-S has a right to purchase or receive through assignment (as applicable) under Section 17.1(i) (Disengagement Assistance) of the General Terms and Conditions, Supplier shall also provide the serial number, purchase or lease date (as applicable), depreciation cycle, fair market value or copy of the lease (as applicable), and other reasonable information requested by Triple-S. |
| (b) | With respect to Supplier Owned Equipment to be sold to Triple-S pursuant to Section 17.1(i) (Disengagement Assistance) of the General Terms and Conditions, as directed by Triple-S and upon Supplier’s receipt of payment in full, Supplier shall convey such Supplier Owned Equipment to Triple-S or the Successor Supplier, along with any associated warranties that Supplier is permitted to pass on to a purchaser and with all available user and other Documentation, free of any liens, claims or encumbrances (excluding any such liens, claims or encumbrances created by Triple-S), and shall execute a ▇▇▇▇ of sale in a mutually agreed form to evidence the conveyance. |
| (c) | With respect to Supplier Leased Equipment to be assigned to Triple-S pursuant to Section 17.1(i) (Disengagement Assistance) of the General Terms and Conditions, as directed by Triple-S, Supplier shall (i) provide to Triple-S a copy of the current leases pertaining to the Supplier Leased Equipment, and (ii) assign to Triple-S or the Successor Supplier the leases for such Supplier Leased Equipment. |
Triple-S/Supplier Confidential
Page 6
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule I
Disengagement Assistance
| (d) | If requested by Triple-S, a conveyance to Triple-S of any Supplier Owned Equipment under Section 5.2(b) or Supplier Leased Equipment under Section 5.2(c) shall include Supplier’s assignment to Triple-S of all associated Equipment maintenance agreements to the extent that Supplier has such rights to assign under the applicable maintenance agreements. |
| 5.3 | Supplier Third Party Service Contracts |
| (a) | Subject to Section 5.1(a), Supplier shall provide information to Triple-S concerning any Supplier Third Party Service Contracts held by Supplier (and any of its Subcontractors) that are used to perform the Affected Services (collectively, the “Affected Supplier Third Party Service Contracts”) (other than Equipment leases, which are governed by Section 5.2 above), which shall include a complete inventory of such contracts (in Microsoft Excel format) specifying the third party, the nature of the contract (e.g., support agreement, equipment maintenance contract), the corresponding Services such contract is used to provide, and other reasonable information requested by Triple-S. |
| (b) | With respect to Supplier Third Party Service Contracts to be assigned to Triple-S pursuant to Section 17.1(j) (Disengagement Assistance) of the General Terms and Conditions, as directed by Triple-S, Supplier shall (i) provide, or use Commercially Reasonable Efforts to cause the corresponding Subcontractor to provide, to Triple-S or the Successor Supplier a copy of the Supplier Third Party Service Contracts, and (ii) assign, or use Commercially Reasonable Efforts to cause the corresponding Subcontractor to assign, to Triple-S or the Successor Supplier such Supplier Third Party Service Contracts, which such assignee shall assume the assigning party’s obligations under any such contract assigned relating to periods after the date of assignment. |
| 5.4 | Software and Tools |
| (a) | Subject to Section 5.1(a), Supplier shall provide information to Triple-S or the Successor Supplier concerning any Supplier Software or Supplier Tools that are used for the provision of the Affected Services (including those for tracking Projects and service information requests, and those used for knowledge transfer), which shall include a complete inventory of such Supplier Software and Supplier Tools, the corresponding licensor of such Supplier Software and Supplier Tools, the nature of such Supplier Software and Supplier Tools (e.g., Software, process), the corresponding Services each Supplier Software or Supplier Tool is used to provide, all Documentation related to Supplier Software and Supplier Tools required to be made available under Section 17.1(f) (Disengagement Assistance) of the General Terms and Conditions, and other information reasonably requested by Triple-S. |
| (b) | As part of Disengagement Assistance, Supplier shall procure any license that Supplier has not previously provided to Triple-S that Supplier is expressly obligated to provide to Triple-S pursuant to Section 10.4 (Supplier Software and Tools), Section 10.5 (License During the Term and Disengagement Assistance Periods), Section 10.6 (Post Term License Option), Section 15.1(c) (Independent IP), Section 15.2(b) (Ownership of Other |
Triple-S/Supplier Confidential
Page 7
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule I
Disengagement Assistance
Developed Items) of the General Terms and Conditions and Schedule S (Supplier Software and Tools). With respect to any third party Software or Tool for which Supplier is not obligated to procure such a license, Section 17.1(h) (Disengagement Assistance) of the General Terms and Conditions shall govern. For clarity, Triple-S’s rights with respect to Supplier Owned Software and Supplier Owned Tools are set forth in the General Terms and Conditions and Schedule S (Supplier Software and Tools).
| 5.5 | Telephone Numbers |
| (a) | Supplier shall provide information to Triple-S or its designee concerning any telephone numbers (i) for which Supplier or a Subcontractor is the customer of record, and (ii) that are used for the provision of the Affected Services (e.g., help desk numbers), which shall include a complete inventory of such numbers (in Microsoft Excel format), the corresponding Services each of such numbers is used to provide, the corresponding network provider and country of origin, and other reasonable information requested by Triple-S. Triple-S may audit the accuracy of such information in accordance with Section 18.6 (Audits and Records) of the General Terms and Conditions and Schedule M (Audit and Record Retention Requirements). For avoidance of doubt, this Section 5.5(a) shall not require Supplier to provide the individual telephone number for any specific Supplier employee (personal or otherwise), or the personal telephone number of any Subcontractor. |
| (b) | Supplier shall cause each of the telephone numbers described in Section 5.5(a) that are used exclusively for the provision of the Affected Services to be ported to Triple-S or its designee as of the corresponding Cutover Date(s), thereby making Triple-S or its designee the customer of record for such numbers. |
| 5.6 | Unidentified Assets |
| (a) | For any Affected Services, if after the corresponding Cutover Date, any Resources are discovered that were not identified by Supplier pursuant to Sections 5.2 through 5.5 (each, an “Unidentified Asset”), Supplier shall provide Triple-S or the Successor Supplier with notice of such discovery (such notice for any such Unidentified Asset, a “Discovery Notice” for such asset), which Discovery Notice shall provide a description of the corresponding Unidentified Asset that includes the information described in Sections 5.2 through 5.5, as applicable. |
| (b) | As of the Cutover Date, Supplier hereby grants to Triple-S and its designees, at no additional charge, to the greatest extent possible given Supplier’s existing rights, perpetual, irrevocable rights of access to, and use of the Unidentified Assets; provided, however, that with respect to any Unidentified Asset that is Leased Equipment or a Third Party Agreement, Supplier may terminate the lease or agreement corresponding to such Unidentified Asset at Supplier’s expense, but only after: (i) Supplier has provided Triple-S with a Discovery Notice for such Unidentified Asset, (ii) Supplier has presented Triple-S with a complete copy of the corresponding agreement and has provided Triple-S with the opportunity to exercise its rights pursuant to Sections 5.2(c) and 5.3(b); and (iii) |
Triple-S/Supplier Confidential
Page 8
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule I
Disengagement Assistance
Triple-S has notified Supplier that it does not wish to exercise its rights pursuant to Sections 5.2(c) or 5.3(b). For any such Unidentified Asset that is Leased Equipment or a Third Party Agreement, Triple-S shall provide the notification as to whether it wishes to accept assignment of the corresponding lease or agreement within thirty (30) days after Supplier’s delivery of the corresponding agreement to Triple-S pursuant to clause (ii) of this Section 5.6(b).
| 5.7 | Human Resources |
| (a) | Supplier Personnel Information. |
| (i) | Supplier shall, within ten (10) Business Days following either Triple-S’s request made during the Disengagement Assistance Period or a Disengagement Event, and subject to any applicable Law governing the use, disclosure or processing of personal data, provide Triple-S with information and copies of records concerning Supplier Personnel (such information collectively, the “Supplier Personnel Information”). If requested by Triple-S, Supplier Personnel Information shall be provided in electronic format (including in Microsoft Excel format). Supplier Personnel Information shall include a current organizational chart that identifies all Supplier Personnel performing the Affected Services (“Affected Supplier Personnel”), and summarizes their organizational relationship among one another (e.g., solid-line versus dotted-line reporting from one person to another), and which specifically distinguishes the Affected Supplier Personnel from other Supplier Personnel. For the Affected Supplier Personnel, such chart shall include roles, responsibilities, level of effort (i.e., dedicated to Triple-S or % of time dedicated to Triple-S) and authority of such personnel. |
| (ii) | With respect to Supplier Personnel who are eligible to be hired by Triple-S pursuant to Section 17.1(e) (Disengagement Assistance) of the General Terms and Conditions, as and to the extent reasonably requested by Triple-S, Supplier shall provide a list of the Supplier Personnel performing the Affected Services (“Affected Supplier Personnel”) by individual, and the following information (both on an aggregated basis and by individual person, each broken down by function): (A) name; (B) position and job title; (C) job responsibilities; and (D) whether such person is a heritage Triple-S employee, heritage Supplier employee, or independent contractor personnel. |
| (iii) | Where Supplier Personnel Information has been provided pursuant to this Section 5.7(a), Supplier shall: (A) inform Triple-S of any material change to the same; (B) clarify any matter on which clarification is reasonably requested by Triple-S; and (C) cooperate with any other reasonable requests made by Triple-S concerning Supplier Personnel Information. Supplier shall perform such obligations as soon as practicable, but in any event within ten (10) Business Days of any material change described in clause (A) of this paragraph, or of any Triple-S request pursuant to clauses (B) and (C) of this paragraph. |
Triple-S/Supplier Confidential
Page 9
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule I
Disengagement Assistance
| (b) | Hiring of Supplier Personnel. |
| (i) | Following a Disengagement Event, Triple-S and the Successor Supplier shall have the right to make offers of employment to all Supplier Personnel pursuant to Section 17.1(e) of the General Terms and Conditions; however, nothing shall be construed to require acceptance of employment offers by any such Supplier Personnel. Triple-S and the Successor Supplier shall have reasonable access to such Supplier Personnel for interviews and recruitment. |
| (ii) | Supplier shall fully and promptly cooperate in good faith with all reasonable requests of Triple-S to procure the smooth and lawful transfer to Triple-S or the Successor Supplier of the Supplier Personnel who accept offers to transfer to Triple-S or a Successor Supplier. |
| (c) | Satisfaction of Obligations. To the extent Triple-S hires any Supplier Personnel pursuant to the Agreement, as of the date of such hire, Supplier shall satisfy all of its obligations with respect to all outgoing and accrued liabilities incurred as Employer of such hired personnel, including wages, contractual bonuses, commission, holiday remuneration, tax, social security and national insurance contributions or other relevant national statutory deductions governed by the Laws of any jurisdiction governing the employment of such personnel. |
| 5.8 | Transfer of Services Operating Environment. |
As part of the Disengagement Plan and upon termination of the Agreement, Triple-S shall have the right to take over the existing instances of the Triple-S operating environment contained within the data center(s) of Supplier’s applicable Subcontractors (“Existing Instances”). Supplier shall not restrict or otherwise hinder Triple-S’ ability to acquire rights to the software and supporting systems and access such Existing Instances.
| 6. | Supplier Disengagement Assistance Team |
Until the completion of the Disengagement Assistance Plan, Supplier shall assign an individual to service on a dedicated basis to manage and oversee Supplier’s support of Disengagement Assistance activities (such position, the “Supplier Disengagement Assistance Lead”). The individual serving as the Supplier Disengagement Assistance lead shall be subject to Triple-S’ prior written approval. The Supplier Disengagement Assistance Lead shall meet with his or her Triple-S counterparts on a weekly basis (or more frequently if reasonably requested by Triple-S), and shall serve as an escalation point for issues relating to the Disengagement Assistance.
| 7. | Operational Transition |
Pursuant to this Schedule I, Section 17 (Disengagement Assistance) of the General Terms and Conditions, and the Disengagement Assistance Plan, the Disengagement Assistance to be provided to Triple-S by Supplier shall include the following activities, as directed by Triple-S:
Triple-S/Supplier Confidential
Page 10
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule I
Disengagement Assistance
| (a) | Providing Source Code and object code, database, file, record layouts and field descriptions, where available with respect to the Triple-S Software (and other Software, to the extent Triple-S is entitled to a license to Source Code pursuant to the General Terms and Conditions), along with the Documentation and associated program execution statements if available, and other similar information necessary for the designee to execute such Software for Triple-S’s benefit, in the form reasonably specified by Triple-S; |
| (b) | To the extent Supplier is obligated to grant or procure a license for Triple-S that includes a right to Source Code under the General Terms and Conditions, providing the available object code, database, file, record layouts and field descriptions with respect to such Source Code, along with the Documentation and associated program execution statements, and other similar information in a form reasonably specified by Triple-S; |
| (c) | To the extent Supplier is obligated to grant or procure a license for Triple-S that includes a right to Source Code under the General Terms and Conditions, documenting and delivering the available program materials, including source and object libraries, reference files, interface definitions, specifications, implementation procedures relative to Triple-S’s technical environment, and embedded software; |
| (d) | In accordance with Section 21.7 (Return or Destruction) of the General Terms and Conditions and Section 5 (Records Retention) of Schedule M (Audit and Record Retention Requirements), delivering or destroying all Triple-S Data and Triple-S Confidential Information, in the manner and format specified by Triple-S (including electronic copies on storage devices in, and electronic transmission to, a new environment) with a complete content listing; |
| (e) | Delivering then-existing systems support profiles, change logs including enhancement and maintenance, history, problem tracking/resolution documentation, functional and complexity assessment analyses, and status reports associated with the Services; |
| (f) | Providing work volumes, then-current staffing requirements, demand backlog and information on historical performance for the Service Levels, to the extent available for the Affected Services, over the preceding twelve (12) months; |
| (g) | Identifying and documenting the demarcation points for each portion of the Affected Services, including any operating level agreements with other Triple-S or Supplier groups at those demarcation points, and information regarding the physical and virtual locations affected by the Disengagement Assistance Plan; |
| (h) | Identifying work and Projects expected to be in progress as of the corresponding Cutover Dates for the Affected Services, and with respect to such work, documenting current status (including Project budget information), stabilizing for continuity during transition, and providing any reasonably required training to qualified personnel to achieve transfer of responsibility for such work and Projects; |
Triple-S/Supplier Confidential
Page 11
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule I
Disengagement Assistance
| (i) | Before the corresponding Cutover Dates, providing the following Services: |
| (i) | Subject to Section 17.1(f) of the General Terms and Conditions, provide Documentation used by Supplier to provide the Affected Services and reasonably necessary to provide continuity of service during transition, in an electronic format that is reasonably acceptable to, and in a location and manner that is easily accessible by, Triple-S; |
| (ii) | Identify, record and provide change control records with respect to Projects and provide release management with respect to application changes; |
| (iii) | Provide and coordinate assistance in notifying Subcontractors of the procedures to be followed in connection with the Disengagement Assistance Plan; |
| (iv) | Collaboratively with Triple-S, coordinate with [***] and other similar third parties regarding the procedures to be followed in connection with the Disengagement Assistance Plan; |
| (v) | Review the organization, structure use and contents of all Software libraries, databases and repositories including those utilized for test, staging and production with Triple-S’s or the Successor Supplier’s operations staff; |
| (vi) | Provide reasonable assistance to Triple-S or the Successor Supplier in establishing or transferring operational standards including naming and addressing conventions; |
| (vii) | Make arrangements for any physical de-installation, transportation, and relocation of Equipment and physical assets to be performed as part of the Disengagement Assistance; |
| (viii) | Reasonably cooperate and assist Triple-S and the Successor Supplier in achieving a state of operational readiness before the applicable Cutover Dates; |
| (ix) | Provide Triple-S with any help desk or service request tickets and problem logs it does not already have, reporting back at least two (2) years prior to the Cutover Date (but no earlier than the Effective Date); |
| (x) | After consultation with Triple-S, discontinue all discretionary Software changes, other than with respect to the Services or other modifications necessary to address processing problems; |
| (xi) | Assist Triple-S or its designee in the analysis of the direct access storage capacity required to accommodate Software libraries and Triple-S’s data files; |
Triple-S/Supplier Confidential
Page 12
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule I
Disengagement Assistance
| (xii) | Deliver in a usable format, all databases and associated content used to provide the Services including those for tracking projects and service information requests, and those used for knowledge transfer; |
| (xiii) | As provided in Sections 10.4 (Supplier Software and Tools) and 15 (Intellectual Property Rights) of the General Terms and Conditions or expressly provided in any other section of the Agreement, generate and provide the Source Code for the Software to which Triple-S has a license under Sections 10.4 (Supplier Software and Tools) and 15 (Intellectual Property Rights) of the General Terms and Conditions or such other express provision of the Agreement in a form reasonably requested, and deliver such Source Code, technical specifications and materials, and user documentation for the Software to Triple-S or its designee, as and to the extent provided for in Sections 10.4 (Supplier Software and Tools) and 15 (Intellectual Property Rights) of the General Terms and Conditions or such other express provision of the Agreement; |
| (xiv) | Provide documentation and diagrams for the voice, data, video, and other communications capabilities, asset information and configuration settings (including configurations, router tables, IP addressing schema, managed device thresholds) for all configurable items used by Supplier to perform the Services (including media access, media, routing, bridging and switching devices and other equipment and software providing communications service delivery and management functions); and |
| (xv) | Provide interim Triple-S Data, in such format and on such media as reasonably requested by Triple-S. |
| (j) | On or before the corresponding Cutover Dates, providing the following Services: |
| (i) | In conjunction with Triple-S or the Successor Supplier, conduct a rehearsal of any migration that is part of the Disengagement Assistance Plan prior to the Cutover Date and as scheduled by Triple-S and reasonably agreed to by Supplier, and provide any required corrective action identified during the rehearsal; |
| (ii) | Provide reasonable assistance to Triple-S or its designee in making Triple-S Data files available on the storage devices of the new environment; |
| (iii) | Provide reasonable assistance to Triple-S or its designee with the transmission or movement of data from then-existing databases to the new environment; |
| (iv) | Provide an image copy (and mirrored DASD volumes if available) of each operating system environment (in dump/restore or image mode, as applicable to the operating system platform); |
Triple-S/Supplier Confidential
Page 13
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule I
Disengagement Assistance
| (v) | Provide reasonable assistance to Triple-S or the Successor Supplier with the turnover of operations and the execution of parallel testing and parallel operations; |
| (vi) | Assist Triple-S or the Successor Supplier in the identification and removal of security access credentials for Supplier Personnel from any computing communications devices and associated Software transferred to Triple-S or the Successor Supplier; and |
| (vii) | Transfer responsibility to Triple-S or the Successor Supplier for off-site media and document storage. |
| (k) | On or before the corresponding Cutover Dates, providing additional assistance reasonably requested by Triple-S, including: |
| (i) | Returning to Triple-S (or, if requested by Triple-S, destroying) at no additional charge any remaining Triple-S property in Supplier’s possession or control, including remaining reports, data and Triple-S Data or Triple-S Confidential Information; and |
| (ii) | Vacating Triple-S Facilities in a timely manner. |
| 8. | Organizational Transition |
Supplier shall provide reasonable assistance required to adequately transfer, in accordance with the Disengagement Assistance Plan, the organizational information developed during the Term to support the delivery of the Affected Services. Supplier’s responsibilities shall include, as requested by Triple-S:
| (a) | Providing, to the extent Supplier has created such items, functional organization charts, operating level agreements with third-party contractors, phone trees, contact lists, and standard operating procedures; |
| (b) | Transferring physical and logical security processes and tools, including cataloguing and tendering all badges and keys, documenting ownership and access levels for all passwords, and instructing Triple-S or its designee in the use and operation of security controls; and |
| (c) | Protecting against security breaches of Supplier Personnel during the Disengagement Assistance Period by revoking Supplier Personnel access to Triple-S Facilities (or secure locations within such facilities), Triple-S Data, Triple-S Confidential Information, Equipment, Software and other systems, processes and tools, as such Supplier Personnel are transitioned away from Triple-S’s account or as the functions performed by such Supplier Personnel are transitioned away from Supplier, and accordingly, corresponding access to such items is no longer required. |
Triple-S/Supplier Confidential
Page 14
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule I
Disengagement Assistance
| 9. | Business Continuity and Disaster Recovery Transition |
During the Disengagement Assistance Period Supplier shall:
| (a) | Supply the BC/DR Plan to Triple-S; |
| (b) | To the extent Triple-S Data corresponding to the Affected Services is replicated to another facility, transfer such data to Triple-S or its designee, and upon Triple-S’s request, provide reasonable assistance to Triple-S in developing equipment and other requirements for relocating such data; and |
| (c) | Participate in business continuity and Disaster recovery testing in connection with the Disengagement Assistance Plan until a successful test of the recovery arrangements is accomplished. |
| 10. | Knowledge Transfer |
| (a) | As reasonably requested by Triple-S, Supplier shall provide for a transfer of knowledge regarding its performance of the Affected Services, scope, processes, and related topics, so as to facilitate the provision of the Affected Services by Triple-S or the Successor Supplier. Supplier’s responsibilities shall include: |
| (i) | Providing the Documentation and information described in, and subject to the restrictions set forth in, Section 17.1(f) (Disengagement Assistance) of the General Terms and Conditions, including: (A) relevant Documentation; (B) the Procedures Manual; (C) schedules, frequencies, Work Product owned by Triple-S or to which it has a license and related information for activities and Deliverables as reasonably requested by Triple-S; (D) security plans and procedures; and (E) key support contacts (names and phone numbers) of Triple-S personnel, third party personnel, and Supplier Personnel during the Disengagement Assistance Period; |
| (ii) | Providing reasonable training to Triple-S’s or the Successor Supplier’s personnel in the performance of those Services that are to be transferred, including in the management of the third party vendors of goods and services used to perform the Affected Services; |
| (iii) | Explaining the particular Supplier implementation of the processes used to provide the Services, and the human, procedural and technical interfaces to and interactions with Triple-S (including the Procedures Manual) to Triple-S or the Successor Supplier’s operations staff; |
| (iv) | Responding to inquiries from Triple-S regarding the Affected Services, including by providing reasonable access (e.g., by telephone) during the Disengagement Assistance Period; and |
Triple-S/Supplier Confidential
Page 15
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule I
Disengagement Assistance
| (v) | Providing contact listings of potential alternate sources of resources, including skilled labor and spare Equipment parts. |
| (b) | Supplier’s performance of the obligations described in Section 10(a) shall be in accordance with a knowledge transfer plan for the Affected Services (each such plan a “Knowledge Transfer Plan”). Each Knowledge Transfer Plan shall be aligned with the Disengagement Assistance Plan, and shall, at a minimum, describe the overall knowledge transfer process, including, without disclosing Supplier Confidential Information: (i) Supplier’s overall approach; (ii) major activities and schedules for the knowledge transfer; (iii) the Supplier Personnel who shall participate in the knowledge transfer; (iv) a description of the documentation that Supplier shall provide in connection with the knowledge transfer; and (v) designation of resources needed from Triple-S and associated schedules. Each Knowledge Transfer Plan shall be provided to Triple-S for its review, comment and approval. The reasonable comments or suggestions of Triple-S shall be incorporated as applicable into each such Knowledge Transfer Plan and Triple-S’s final approval shall be obtained prior to implementation of the Knowledge Transfer Plan. |
| 11. | Financial Transition |
As of the Cutover Date for any Affected Services, and continuing for a period of six (6) months thereafter (each such period a “Financial Reconciliation Period”), Supplier shall reasonably cooperate with and support Triple-S, at no additional charge, to achieve a final reconciliation with respect to the areas identified in this Section 11.
| (a) | Supplier Invoicing. Supplier shall submit its invoice for all charges and credits applicable to the Affected Services through the corresponding Cutover Date, which shall be payable in accordance with Schedule C (Charging Methodology). Effective as of the Cutover Date for any Affected Services, each Party shall submit to the other Party reconciliation information (including as reasonably requested by the other Party) to reconcile any outstanding charges or credits, and each Party shall work diligently and in good faith to achieve a final reconciliation of such charges and credits by the end of the Financial Reconciliation Period. |
| (i) | The Parties acknowledge the possibility that invoices for third-party contracts (e.g., Third Party Service Contracts or Equipment leases) used to provide the Affected Services and transferred to Triple-S or its designees pursuant to Section 5 may be misdirected by third-party vendors after the effective date of transfer, and provided to Supplier instead of Triple-S or its designee. Supplier shall provide any such invoices in their original form to Triple-S in a timely manner. |
| (ii) | Supplier shall reimburse Triple-S for third party products or services, if any, for which Supplier is financially responsible, and that are used to provide the Affected Services before the Cutover Date, but that are invoiced to Triple-S or its designee. |
Triple-S/Supplier Confidential
Page 16
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule I
Disengagement Assistance
| (iii) | On or before the Cutover Date, Supplier shall provide Triple-S with information regarding any third party contracts used to provide the Affected Services such that Triple-S can reasonably validate that the corresponding third party vendor has invoiced, and Supplier has paid, any charges arising under such contracts before the Cutover Date. |
| (b) | Asset Acquisitions. Sections 5.2 through 5.4 describe terms pursuant to which Triple-S or its designee may acquire certain resources used to provide the Affected Services. Each Party shall work diligently and in good faith to achieve, by the end of the Financial Reconciliation Period, a final reconciliation of the financial issues arising from any transfer of such resources to Triple-S or its designee under such provisions. |
| 12. | Risk Mitigation |
The Parties shall at all times work together in good faith during the Disengagement Assistance Period to minimize any risk to or interference with the Services (including the Service Levels).
Triple-S/Supplier Confidential
Page 17
Schedule J
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
SCHEDULE J
TRIPLE-S POLICIES AND PROCEDURES
| Schedule J | Triple-S / Supplier Confidential |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
SCHEDULE J
TRIPLE-S POLICIES AND PROCEDURES
| No. | Policy Name |
| 1 | Claims Department Medicare Secondary Payer COB |
| 2 | Claims Payment Dispute Process for Non Contracted Provider |
| 3 | Claims Universe Request |
| 4 | Code of Business Conduct and Ethics |
| 5 | Compliance Program |
| 6 | Contracting and Monitoring of Delegated Entities |
| 7 | Manual de Politicas Corporativas – Empleo de Familiares |
| 8 | Manual de Politicas Corporativas – Co▇▇▇▇▇▇▇▇▇▇ ▇▇ ▇▇▇▇▇▇▇▇ – ▇▇▇▇▇▇▇▇▇▇ ▇ ▇▇▇▇▇▇▇▇▇▇▇▇▇ |
| ▇ | ▇▇ ▇nd Information Security Policies |
| 10 | IT Controls Questionnaire for Service Providers |
| 11 | Manual de Politicas Corporativas – Politica Antifraude y Abuso |
| 12 | Manual de Politicas Corporativas – Contratacion de Terceros |
| 13 | Manual de Politicas Corporativas – Retencion de Documentos |
| 14 | Protocolo Para el Cumplimiento Con Law FCPA |
Triple-S / Supplier Confidential
Page 1
Schedule J1
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
| TSA P&P #: CL-009 | Page 1 of 10 |
 |
Policy and Procedure
|
| Title: Part C-Medicare Secondary Payer |
| Department: Claims Department | Additional Areas of Impact: Enrollment , Finance Legal and Pharmacy Department |
| Effective Date: 1/1/2015 | Date Last Amended: 8/26/2016 |
| Reference: | |
| · | Medicare Manage Care Manual - Chapter 4 Benefits and Beneficiary Protections (Rev. 121, 4-22-2016) |
| · | 42 CFR 422.108 Medicare as Secondary Payer (MSP) Procedures |
|
Approved by: ▇▇▇▇▇▇▇ ▇▇▇▇▇▇ ▇▇▇▇▇▇▇▇, Claims Director
|
Date: 9/14/2016 |
Policy Statement
Triple S Advantage does not pay for services to the extent that there is a third party that is required to be the primary payer, after identifying payers that are primary to Medicare, the amounts payable by those payers and coordinate its benefits to Medicare enrollees with the benefits of the primary payers in compliance with the "Omnibus Budget Reconciliation Act of 1980" that turned Medicare into a secondary payer under specifics conditions.
Purpose
To guarantee that Triple-S Advantage will apply the Medicare Secondary Payer rules when receiving a claim of a member with other health insurance or a liability insurance policy; to prevent payments of medical services when there is another health plan as primary payer.
Definitions
| 1. | Coordination of Benefits (COB): is a program which determines which plan or insurance policy will issue primary payment when two insurance companies cover the same benefits. If one of the plans is a Medicare Health Plan, Federal Law establishes which plan is the Primary Payer. It is the process of determining the respective |
2016 TSA Policy and Procedure Template. Hardcopies of this document are considered uncontrolled, for the latest version
please refer to Compliance 360 or contact Compliance Department through: ▇▇▇▇▇▇▇▇▇▇▇▇▇@▇▇▇▇▇▇▇▇▇▇▇▇.▇▇▇
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
| TSA P&P #: CL-009 | Page 2 of 10 |
responsibilities of two or more health care insurance plans that have financial responsibility over a medical claim.
| 2. | Electronic Correspondence Referral System (ECRS): allows authorized users at Medicare contractor sites and authorized CMS Regional Offices (ROs) to fill out various online forms and electronically transmit requests for changes to existing CWF MSP information, and inquiries concerning possible MSP coverage. Transactions are automatically stored on the Coordination of Benefits (COB) contractor’s system. Each evening, a batch process reads the transactions and processes the requests. The status of each transaction is updated as it moves through the system. |
| 3. | Explanation of Benefits (EOB): is a document issued by the Insurance Plan that describes services rendered to a member and billed to the plan. The EOB is issued to notify him/her of the results of the claim’s payment or denial evaluation process. The Medicare Advantage Plan must issue the Appeals Language in the EOB when services are denied to the member. |
| 4. | Group Health Plan (GHP): is a health plan which provides coverage to employees, retired employees and their families; and is financially supported by an employer or employee organization. The determination for application of Medicare Secondary rules is based on the number of employees of the plan. |
| 5. | Liability Insurance: is an insurance (includes self-insurance plan) that provides a payment based on legal liability, illness or damages to property. It includes but is not limited to: automobile insurance, uninsured and under-insure motorist insurance, homeowner’s liability, malpractice insurance, product liability, insurance and general casualty insurance. And also includes payments under State wrongful death statutes that provide payment for medical damages. |
| 6. | Medicare Secondary Payer (MSP): is the term generally used when the Medicare program does not have primary payment responsibility - that is, when another entity has the responsibility for paying before Medicare. Medicare is secondary payer in the following situations: |
| a. | Working Aged |
| · | Beneficiaries over 65 years. |
| · | If the beneficiary has an Employer Group Health Plan (EGHP) coverage by virtue of the individual’s current employment status or the current employment status of the individual spouse. |
2016 TSA Policy and Procedure Template. Hardcopies of this document are considered uncontrolled, for the latest version
please refer to Compliance 360 or contact Compliance Department through: ▇▇▇▇▇▇▇▇▇▇▇▇▇@▇▇▇▇▇▇▇▇▇▇▇▇.▇▇▇
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
| TSA P&P #: CL-009 | Page 3 of 10 |
| · | The employer should have 20 or more employees. |
| b. | Disabled |
| c. | Beneficiaries under 65 years. |
| · | That received Medicare benefit based on disability. |
| · | Whose large group health plan (LGHP) coverage is based on the individual’s current employment status of the spouse or a family member. |
| · | The employer should have 100 or more employees. |
| d. | Worker’s Compensation |
| · | Medicare is secondary payer for medical services that were related to a work injury. |
| e. | Auto No-Fault / Liability |
| · | Medicare is secondary payer for those medical services that were related to a car injury covered by the ACAA or services payable under no-fault or liability insurance. |
| f. | ESRD (End Stage Renal Disease) |
| · | Medicare is secondary payer to GHP’s for individual eligible for or entitled to Medicare benefits based on ESRD during a coordination period of 30 months. |
| 7. | Primary Payer: An insurance policy, plan, or program that pays first on a claim for medical care. This could be Medicare or other health insurance. Medicare is primary payer in the following situations: |
| a. | Individual has ESRD, is covered by COBRA and is after the first 30 months of eligibility or entitlement to Medicare |
| b. | Individual is disabled and covered by Medicare & COBRA |
| 8. | Subrogation: is the substitution of one person or entity for another. |
Procedure
| A. | Claims Department receives the UB04 and CMS1500 claim forms and enters the claim data in the HealthSuite System. Claims Analyst will verify the following in the UB04 and 1500 Health Insurance Claim Form: |
| 1. | System reason codes with possible additional payers |
| 2. | Membership information on the system |
| 3. | Trauma and occupational illness diagnosis codes |
| 4. | MSP data on the claim |
| 5. | Claim indicators that the services were related to an accident |
| 6. | Patient history showing claims for ambulance or trauma related services |
| 7. | Claims documents that may include an Explanation of Benefits (EOB) from other insurance |
2016 TSA Policy and Procedure Template. Hardcopies of this document are considered uncontrolled, for the latest version
please refer to Compliance 360 or contact Compliance Department through: ▇▇▇▇▇▇▇▇▇▇▇▇▇@▇▇▇▇▇▇▇▇▇▇▇▇.▇▇▇
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
| TSA P&P #: CL-009 | Page 4 of 10 |
| B. | A rule was created with the clearing house to detect if a claim has any item in the item #10 (Is Patient’s Condition Related To) of the 1500 Claim Form that indicates “yes”: employment, B: auto accident or C: other accident. The provider will receive a Remittance Advice (277 form) with the Status Code Related Causes Code (Accident, auto accident, employment). |
| 1. | The provider must submit the claim to the primary insurance. |
| C. | In the UB04 claim form other insurance that may be the Primary Payer to Medicare is identified as follows: |
| 1. | A trauma related ICD-9/ICD-10-CM code is shown; or |
| 2. | A Value Code (VC) in items 39-41: |
| Code | Description |
| 12 | Working aged beneficiary/spouse with an EGHP (beneficiary over 65). Beneficiary must have Medicare Part A entitlement (enrolled in Part A) for this provision to apply. Primary Payer Code = A. |
| 13 | ESRD beneficiary with EGHP in MSP/ESRD 30-month coordination period. Primary Payer Code = B. |
| 14 | No-Fault including automobile/other. Examples: Personal injury protection (PIP) and medical payment coverage. Requires Occurrence Code-OC 01 or 02 with date of accident/injury. Primary Payer Code = D. If filing for a Conditional Payment, report with Occurrence Code 24. |
| 15 | Workers Compensation (WC). Requires Condition Code-CC 02 and OC 04 with date of accident/injury. Primary Payer Code = E. If filing for a Conditional Payment, report with Occurrence Code 24. |
| 16 | Public health services (PHS) or other federal agency. Conditional billing does not apply. Primary Payer Code = F. |
| 41 | Federal Black Lung (BL) Program. Primary Payer Code = H. |
| 42 | Veterans Administration (VA). Conditional billing does not apply. Primary Payer |
2016 TSA Policy and Procedure Template. Hardcopies of this document are considered uncontrolled, for the latest version
please refer to Compliance 360 or contact Compliance Department through: ▇▇▇▇▇▇▇▇▇▇▇▇▇@▇▇▇▇▇▇▇▇▇▇▇▇.▇▇▇
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
| TSA P&P #: CL-009 | Page 5 of 10 |
| Code = I. | |
| 43 | Disabled beneficiary under age 65 with an LGHP. Beneficiary must have Medicare Part A entitlement (enrolled in Part A) for this provision to apply. Primary Payer Code = G. |
| 44 | Amount provider was obligated/required to accept from a primary payer as payment in full due to contract/law when that amount is less than charges but higher than amount actually received. An MSP payment may be due. Note: When applicable, this Value Code is reported in addition to MSP Value Code. |
| 47 | Any Liability Insurance. Requires Occurrence Code-OC 02 with date of accident/injury. Primary Payer Code = L. If filing for a Conditional Payment, report with Occurrence Code 24. |
| 3. | An Occurrence Code (OC) in items 31 to 34: |
| Code | Description |
| 01 | Accident/Medical Payment Coverage – Date of accident/injury for which there is medical payment coverage. Reported with Value Code-VC 14 or VC 47. If filing for a Conditional Payment, report with Occurrence Code 24. |
| 02 | No-Fault Insurance (including automobile and other accidents) – Date of accident/injury for which the state has applicable No-Fault laws. Reported with Value Code-VC 14 or 47. If filing for a Conditional Payment, report with Occurrence Code 24. |
| 03 | Accident/Tort Liability - Date of an accident/injury resulting from a third party's action that may involve a civil court action in an attempt to require payment by third party, other than No-Fault. Reported with Value Code-VC 47. |
| 04 | Accident/Employment-Related - Date of an accident/injury related to beneficiary's employment. Reported with Value Code-VC 15 or VC 41. If filing for a Conditional |
2016 TSA Policy and Procedure Template. Hardcopies of this document are considered uncontrolled, for the latest version
please refer to Compliance 360 or contact Compliance Department through: ▇▇▇▇▇▇▇▇▇▇▇▇▇@▇▇▇▇▇▇▇▇▇▇▇▇.▇▇▇
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
| TSA P&P #: CL-009 | Page 6 of 10 |
| Payment, report with Occurrence Code 24. | |
| 05 | Accident/No Medical Payment, No-Fault or Liability Coverage – Date of accident/injury for which there is no Medical Payment or other third-party liability coverage |
| 06 | Crime victim - Date on which a medical condition resulted from alleged criminal action committed by one or more parties |
| 18 | Date of retirement (beneficiary) |
| 19 | Date of retirement (spouse) |
| 24* | Date Insurance denied - Date of receipt of a denial of coverage by a higher priority payer. This could be date of primary payer's Explanation of Benefit (EOB) statement, letter or other documentation. Date is required on all Conditional Payment claims. |
| 25 | Date Coverage No Longer Available – Date on which coverage, including Workers' Compensation benefits or No-Fault coverage, is no longer available to beneficiary |
| 33 | First day of MSP ESRD coordination period for ESRD beneficiaries covered by an EGHP |
| 4. | A Condition Code (CC) in items 18 to 28: |
| Code | Description |
| 02 | Condition is employment related |
| 06 | End-stage renal disease (ESRD) beneficiary in first 30 months of eligibility/entitlement covered by an employer group health plan (EGHP) |
| 08 | Beneficiary refused to provide information concerning other insurance coverage |
2016 TSA Policy and Procedure Template. Hardcopies of this document are considered uncontrolled, for the latest version
please refer to Compliance 360 or contact Compliance Department through: ▇▇▇▇▇▇▇▇▇▇▇▇▇@▇▇▇▇▇▇▇▇▇▇▇▇.▇▇▇
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
| TSA P&P #: CL-009 | Page 7 of 10 |
| 09 | Neither the beneficiary nor spouse is employed |
| 10 | Beneficiary and/or spouse is employed but no Employer Group Health Plan (EGHP) |
| 11 | Disabled beneficiary and/or family member is employed but no Large Group Health Plan (LGHP) |
| 28 |
Beneficiary's and/or spouse's Employer Group Health Plan (EGHP) is secondary to Medicare. Beneficiary and/or spouse are employed and there is an EGHP that covers beneficiary but either:
1. EGHP is a single employer plan and employer has fewer than 20 full- and/or part-time employees
2. EGHP is a multi- or multiple-employer plan that elects to pay secondary to Medicare for employees and spouses aged 65 and older for those participating employers who have fewer than 20 employees |
| 29 |
Disabled beneficiary and/or family member's Large Group Health Plan (LGHP) is secondary to Medicare. Beneficiary and/or family member(s) are employed and there is a LGHP that covers beneficiary but either:
1. LGHP is a single employer plan and employer has fewer than 100 full- and/or part-time employees
2. LGHP is a multi-or multiple employer plan and all employers participating in plan have fewer than 100 full- and/or part-time employees |
| 63 | Services rendered to beneficiary in state or local custody (prisoner) meets requirements of 42 CFR 411.4(b) for payment |
| 77 | Provider accepts or is obligated/required, due to a contractual arrangement/law, to accept payment by primary payer as payment in full (and that amount has been received and no Medicare payment is due). MSP claim is being filed because claim is an inpatient claim or claim is an outpatient claim and the beneficiary has not yet met his/her annual Medicare Part B deductible. |
| D7 | Change to make Medicare the secondary payer (report on adjustment when original |
2016 TSA Policy and Procedure Template. Hardcopies of this document are considered uncontrolled, for the latest version
please refer to Compliance 360 or contact Compliance Department through: ▇▇▇▇▇▇▇▇▇▇▇▇▇@▇▇▇▇▇▇▇▇▇▇▇▇.▇▇▇
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
| TSA P&P #: CL-009 | Page 8 of 10 |
| claim was processed as a Medicare primary claim, conditional claim or was rejected for MSP). | |
| D8 | Change to make Medicare the primary payer (report on adjustment when original claim was processed as an MSP claim or as a conditional claim). |
| D9 | Any other change (report on adjustment claim when original claim was rejected for MSP but Medicare is primary or when original claim was processed as an MSP or conditional claim and a change needs to be made to the claim such as a change in the MSP Value Code amount). |
| D. | If item 50-Payer Name of the UB04 is completed with another payer and the information needed for payment is on the claim, the Claim Analyst will pay the lowest of: |
| 1. | The gross amount payable by TSA less any deductible or coinsurance amount; or, |
| 2. | The gross amount payable by TSA minus the amount paid by the primary payer for TSA covered services; or, |
| 3. | The provider's charges, minus the amount paid by the primary payer for TSA covered services; or |
| 4. | The provider's charges minus the applicable TSA deductible and/or coinsurance amounts. |
| 5. | Condition Code-CC 08 is shown on the claim; |
| 6. | Claim with primary insurer identification, no primary payer amounts, and nothing indicated in remarks item; |
| 7. | MSP claim filed with very low primary payment (investigate for possible keying error with provider to ensure accurate payment amount); |
| 8. | Trauma diagnosis, and claim does not show Occurrence Code-OC 05 and date nor remarks; |
| 9. | Retirement dates same as dates of service (i.e., improper use of Occurrence Codes-OC18 and 19); |
| 10. | Occurrence Codes-OC 01-04 used, but not MSP claim. No Occurrence Code-OC 24 or remarks |
| E. | If item 50-Payer Name of the UB04 is completed with another payer but the claim lacks of information TSA will deny the claim requesting the missing data. |
| 1. | When the information is received the Claim Analyst completes the adjudication of the claim. |
| 2. | No primary payment will be made where a GHP denies payment for particular services because: |
| a. | The services are not covered by the plan, and there is reason to believe the plan does cover the services; |
2016 TSA Policy and Procedure Template. Hardcopies of this document are considered uncontrolled, for the latest version
please refer to Compliance 360 or contact Compliance Department through: ▇▇▇▇▇▇▇▇▇▇▇▇▇@▇▇▇▇▇▇▇▇▇▇▇▇.▇▇▇
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
| TSA P&P #: CL-009 | Page 9 of 10 |
| b. | The plan offers only secondary coverage of services covered by Medicare. Primary benefits may not be paid in this situation even if the GHP has only collected premiums for secondary rather than primary coverage. Where a GHP has denied the claim because the plan provides only secondary coverage, TSA will deny the claim. |
| c. | The plan limits its payments when the individual is entitled to Medicare; |
| d. | The services are covered under the EGHP for younger employees and spouses but not for employees and spouses age 65 or over; |
| e. | The provider fails to file a proper claim for any reason |
| F. | If a primary payer is detected after the claim was paid, the claim will be adjusted to offset future payments to the provider by a recurrent recovery process and the provider will be authorized to ▇▇▇▇ the primary payer. This process will be performed weekly by the Recovery Unit. |
| G. | Recovery Unit will generate a weekly report through Reporting Services which combines members with MSP - TPL indicator from the Electronic Correspondence Referral System (ECRS) and Health Suite eligibility. This report will match the claims paid with TPL accident related diagnosis during the same period. |
| H. | Once the Recovery Examiner identifies possible cases to be recover, the Analytics Unit will perform a proper investigation following the coordination of benefits investigation guidelines set forth by CMS. This investigation includes contact with the member, communication with the Third Party Liability Insurance (TPL) and evaluation of Medical Records, among others. |
| I. | Once the Analytics Unit confirms the information of the MSP-TPL report was correct, including the period and the condition; Recovery Unit will recoup the claims that applies to the TPL and cases will be referred to: |
| 1. | Pharmacy Department for their TPL recoup process with the PBM |
| 2. | Legal Department for the subrogation process |
| 3. | Finance Department for the re-adjudication, evaluation and impact of the cases in the Risk Adjustment Processing System (RAPS), Encounter Data System (EDS) and Prescription Drug Event (PDE). |
| J. | TSA will include Third Party Liability and Coordination of Benefits information in the eligibility report sent monthly to all delegated entities to prevent overpayments. Delegated entity will perform recoveries of the overpayments and re-adjudications. |
| 1. | FDR’s will submit the results to Claims Manager in no more than 45 days after they are performed. |
| 2. | Claims Department will performed quarterly monitoring to the FDR’s of the MSP-TPL and Coordination of Benefits process. |
2016 TSA Policy and Procedure Template. Hardcopies of this document are considered uncontrolled, for the latest version
please refer to Compliance 360 or contact Compliance Department through: ▇▇▇▇▇▇▇▇▇▇▇▇▇@▇▇▇▇▇▇▇▇▇▇▇▇.▇▇▇
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
| TSA P&P #: CL-009 | Page 10 of 10 |
Supporting Documents
| · | N/A |
Review and Revision History
| Date | Sections Affected | Reason for Change | Reviewer |
| 8/26/2016 | Policy name and procedure | New process | ▇▇▇▇▇▇▇ ▇▇▇▇▇ |
▇▇▇▇ ▇▇▇ Policy and Procedure Template. Hardcopies of this document are considered uncontrolled, for the latest version
please refer to Compliance 360 or contact Compliance Department through: ▇▇▇▇▇▇▇▇▇▇▇▇▇@▇▇▇▇▇▇▇▇▇▇▇▇.▇▇▇
Schedule J2
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
| TSA P&P #: CL-033 | Page 1 of 4 |
|
|
Policy and Procedure |
|
| Title: Payment Dispute Process for Non Contracted Provider | ||
| Department: Claims | Additional Areas of Impact: Customer Service, Contracting, Provider Relations, Medical Management, Network Management | |
| Effective Date: 5/9/2016 | Date Last Amended: 5/9/2016 | |
|
Reference: Providers Payment Dispute Resolution Contractor(PDRC), CMS Memo of April 15, 2015 – MA Payment Guide for Out of Network Payments Policy # CL-023: Payment Process of Non-Contracted Non Clean Claims and CL-033: Payment Dispute Process |
||
| Approved by: ▇▇▇▇▇▇▇ ▇▇▇▇▇▇ ▇▇▇▇▇▇▇▇, Claims Director | Date: 5/9/2016 | |
Policy Statement
TSA has a process to review non-contracted providers payment disputes for instances non- contracted provider contends that the amount paid for covered services is less than the amount that would have been paid under original (traditional) Medicare or where a non-contracted provider disagrees with TSA decision to pay for a different service than billed, often referred to as down-coding of a claim.
Purpose
To establish a procedure for claim payment dispute requested by non-contracted providers.
Definitions
| 1. | Non – Contracted-Provider: A provider for whom/which there is no signed contract agreement between the provider and Triple S Advantage. |
| 1. | Payment Dispute: Any decision where a non-contracted Medicare health plan provider contends that the amount paid by the Medicare health plan for a Medicare covered service is less than the amount that would have been paid under Original Medicare. Non- contracted provider claim payment disputes also include instances where there is a disagreement between a non-contracted Medicare health plan provider and the Medicare health plan about the plan’s decision to pay for a different service or level than that billed. The dispute process does not include: |
| · | Payment denials that result in zero payments |
| · | Payment disputes for contracted providers |
| · | Local and National Coverage Determinations |
| · | Medical necessity determinations |
| · | A non-contracting provider requesting payment in full |
| · | Claims denied for timely filing |
| · | Claims denied as not prior authorized |
| · | Misdirected claim submissions |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
| TSA P&P #: CL-033 | Page 2 of 4 |
Procedure
| A. | Request a Payment Dispute |
| 1. | The non-contracted provider’s payment dispute received by mail, hand delivery to: |
Triple-S Advantage, Inc.
Claims Department
Re: Provider Payment Dispute
▇▇ ▇▇▇ ▇▇▇▇▇
▇▇▇ ▇▇▇▇, ▇▇▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇
| 2. | The Payment Dispute request must be filed within a minimum of 120 calendar days following the notice of initial determination and must include any related documentation including but not limited to: |
| a. | Non Contracted Provider Payment Dispute Form (see attachment 1) |
| b. | Explanation of Payment (EOP) |
| c. | 1500/Ub-04 Form |
| d. | Waiver or the Liability Letter, if available (see attachment 2) |
| e. | Any support document that help to resolve the provider dispute |
| B. | Registration of dispute payment request |
| 1. | The Payment Dispute request are registered by the Claims Clerk in a Dispute Log (see Attachment 3) storage in the Claims Department Folder: J:\Claims Dispute Non Contracted Provider and stamped according to received date. |
| a. | As part of the registration the Claims Clerk has to identify if it is a First Level Payment Dispute or a Payment Dispute Committee Review Request. |
| 2. | Once the Claims Clerk register the dispute in the log, scan all documentation and create an electronic file in the share folder of the Unit and send an email to the Claims Supervisor to communicate the dispute received. |
| a. | If it is a First Level Dispute the Claims Supervisor is responsible to assign the dispute to the Claims Analyst (that was not involved in the initial determination) refer to Section (C) of this policy and procedure. |
| b. | If it is a Payment Dispute Committee Review Request, refer to Section (D) of this policy and procedure. |
| 3. | The Claims Supervisor is responsible to monitor the log weekly to ensure the turnaround time in order to guarantee compliance. |
| C. | First Level Payment Dispute |
| 1. | The Claims Analyst assigned, reviews all the documentation and identifies if the Payment Dispute request needs additional information for determination. |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
| TSA P&P #: CL-033 | Page 3 of 4 |
| a. | The Claims Analyst must contact via phone call or in writing (see attachment 4) the non-contracted provider in order to request the missing information. |
| b. | The non-contracted provider have 14-calendar days to submit the requested information. |
| c. | Any attempts to contact the non-contracted provider is documented in the claims Dispute Log. |
| 2. | Once the Claims Analyst has all the required documentation, he/she has 30 calendar days to make a determination with regards to the Payment Dispute. |
| a. | If the decision is favorable the Claims Analyst process the Payment Dispute and notify the non-contracted provider orally or in writing about the decision and document the resolution and the notification date in the Dispute Log. |
| b. | If the decision is adverse the Claims Analyst send a letter (see attachment 5) to the non-contracted provider to communicate the decision including the reason and the rights to request a Payment Dispute Committee Review and document the resolution and the notification date in the Dispute Log. |
| D. | Payment Dispute Committee Review Request |
| 1. | The non-contracted provider has 120 calendar days from the First Level determination date to request a Payment Dispute Committee Review. |
| 2. | The Claims Supervisor has 30 calendar days to present the case to the Providers Committee to make a determination. |
| a. | Upon the determination the Claims Supervisor assigned to the Claims Analyst the Payment Dispute in order to: |
| i. | If it is favorable: process and notify the non-contracted provider by phone and document the resolution and date of completion in the Dispute Log. |
| ii. | If it is adverse: send a letter (see attachment 6) to the non-contracted provider to communicate the decision including the reason and the rights to request a Second Level Payment Dispute and document the resolution and notification date in the Dispute Log. |
| E. | Second Level Payment Dispute: |
| 1. | If the non-contracted provider disagrees with the Payment Dispute Committee Review determination, she/he may file a complaint with 1-800-MEDICARE. |
| 2. | TSA must process the CMS determination in accordance with CMS requirements. |
Supporting Documents:
Attachment 1: Non Contracted Provider Payment Dispute Form
Attachment 2: Waiver or the Liability Letter
Attachment 3: Dispute Log
Attachment 4: Request to Additional Information Letter Attachment 5: Adverse First Level Payment Letter Attachment 6: Adverse Second Level Payment Letter
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
| TSA P&P #: CL-033 | Page 4 of 4 |
Review and Revision History
| Date | Sections Affected | Reason for Change | Reviewer |
| 05/04/2016 | All policy and procedure | Reorganization of the process | ▇▇▇▇▇▇▇ ▇▇▇▇▇ |
Schedule J3
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
| TSA P&P #: CL-034 | Page 1 of 5 |
 |
Policy and Procedure | |
| Title: Claims Universe Request | ||
| Department: Claims Department | Additional Areas of Impact: Delegated Entities (APS, Net Claim, TNPR) | |
| Effective Date: 7/5/2016 | Date Last Amended: | |
|
Reference:
· CMS Part C Organization Determinations, Appeals and Grievances (ODAG) Audit Process and Data Request (2015-2016 v.100815)
· Prescription Drug Benefit Manual, Chapter 9 and Medicare Managed Care Manual Chapter 21 – Compliance Program Guidelines; Section 50.6 Element VI: Effective System for Routine Monitoring, Auditing and Identification of Compliance Risks Rev. 01-11-2013
|
||
| Approved by: ▇▇▇▇▇▇▇ ▇▇▇▇▇▇ ▇▇▇▇▇▇▇▇, Claims Director | Date: 8/22/2016 | |
Policy Statement
TSA Claims Department implements a validation and monitoring process to ascertain, test and confirm that universes data from Triple-Advantage and the Delegated Entities are accurate and in compliance with Medicare regulations, as well as internal policies and procedures regarding the universe submission per CMS Audit protocols.
Purpose
Establish a formal procedure to generate the universe for claims in TSA and the Delegated Entities (APS, Net Claim and TNPR) in order to assure the compliance of the requirements and guidelines established in the CMS Part C Organization Determinations, Appeals, and Grievances (ODAG) Audit Process and Data request in order to produce and submit appropriate universe records.
Definitions
| 1. | Center for Medicare and Medicaid Services (CMS): The agency within the U.S. Department of Health and Human Services responsible for the Medicare, Medicaid and the Children’s Health Insurance Programs. |
| 2. | Delegated entity: entity that assumes, by contract, the performance of an activity covered under these standards for which the organization is responsible of. The delegated entities are commercial entities, not individuals. |
| 3. | FDRs: First Tier, Downstream and Related Entities. |
2016 TSA Policy and Procedure Template. Hardcopies of this document are considered uncontrolled, for the latest version
please refer to Compliance 360 or contact Compliance Department through: mailto: ▇▇▇▇▇▇▇▇▇▇▇▇▇@▇▇▇▇▇▇▇▇▇▇▇▇.▇▇▇
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
| TSA P&P #: CL-034 | Page 2 of 5 |
| a. | First Tier Entity: Any part compliant with local, federal regulations (including CMS, and ASES) that enters into a written arrangement Triple S, to provide administrative of health care services to a member. |
| b. | Downstream Entity: Any part compliant with local, federal regulations (including CMS, and ASES) that enters into a written arrangement with persons or entities involved with Triple S below the level of the arrangement between the Plan and a first tier entity. These written arrangements continue down to the level of the ultimate provider of both health and administrative services. |
| c. | Related Entity: means any entity compliant with local, federal regulations (including CMS, and ASES) that is related to Triple S by common ownership or control and |
| i. | Performs some of the Plan’s management functions under contract or delegation; |
| ii. | Furnishes services to enrollees under an oral or written agreement; or |
| iii. | Leases real property or sells materials to Plan at a cost of more than $2,500 during a contract period. |
| 4. | Monitoring Activities are regular reviews performed as part of normal operations to confirm ongoing compliance and to ensure that corrective actions are undertaken and effective. |
| 5. | Protocols: Guidelines to ensure universe submission accuracy. |
| 6. | Universe: Report of organizational determination processed on a determined timeframe. |
Procedure
| 1. | Claims Department certifies and guarantee through a validation process that each Delegated Entity and TSA are following the guidelines and requirements established by CMS in the protocols, and includes methods in which data will be gathered and compiled from delegated entities. |
| 2. | Universe validation process will be performed by the Claims Auditor and/or Claims Manager in coordination with the delegated entities; on a monthly basis to assure that each delegated entity and Claims Department has their processes to generate the universe up to date with CMS changes as well ensure the compliance, completeness and accuracy of the data included. |
| a. | The validation procedures will be performed on a monthly basis for three (3) months period or until 100% threshold is reached, whichever occurs later. |
| b. | By the end of this period, the monitoring efforts will be performed every six (6) months. |
2016 TSA Policy and Procedure Template. Hardcopies of this document are considered uncontrolled, for the latest version
please refer to Compliance 360 or contact Compliance Department through: mailto: ▇▇▇▇▇▇▇▇▇▇▇▇▇@▇▇▇▇▇▇▇▇▇▇▇▇.▇▇▇
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
| TSA P&P #: CL-034 | Page 3 of 5 |
| c. | TSA Claims universe will be generated by Claims Coordinator using Reporting Service Portal and request for universe submission will be sent to the Delegated Entities. Delegated Entities will have one week to submit the Universe. |
| d. | A sample of 25 random cases will be selected for validation purposes of each universe layout in order to validate that the universes are accurate. Delegated Entities (TNPR and APS) will be required to submit print screen of the claims in their system, letters and checks sent to members and providers in a timeframe of 72 hours. |
| 3. | The validation process will consist of the following analysis: |
| a. | Includes denied claims for both contracted and non-contracted providers |
| b. | Partially paid claims are considered denied |
| c. | Includes approved claims for non-contracted providers |
| d. | Exclusion of all direct member reimbursement (DMR), duplicate claims, adjustments, claims denied for billing errors, eligibility and recoupments |
| e. | Claims submitted correspond to the period requested |
| f. | If a claim has more than one line, all items should be included with a maximum length |
| g. | The name, length and description of the fields in accord with the protocol |
| h. | If the rationale of one column with another is correct |
| i. | Timeliness of the determination and or mailing date |
| j. | Accuracy in appeal member and provider language |
| 4. | Claims processing validation will consist of the following: |
| a. | If the claims were processed within Medicare timeframes (non-contracted providers should be determined in less than 60 days) |
| b. | If the determination is adverse, was the letter with appeal rights sent to members and providers? |
| c. | If the determination is favorable, did the provider receive the correct amount of reimbursement? |
| d. | If adverse, was the non-contracted provider development process followed? |
| 5. | Claims Auditor will have a week to validate the information submitted and share the results and findings to the responsible parties of the delegated entities (Refer to Attachment #1). |
| a. | If the audit results in any finding the Delegated Entity will have to correct the issue in a timeframe determined by TSA. |
| b. | This document will be sent to Compliance Department for their records. |
2016 TSA Policy and Procedure Template. Hardcopies of this document are considered uncontrolled, for the latest version
please refer to Compliance 360 or contact Compliance Department through: mailto: ▇▇▇▇▇▇▇▇▇▇▇▇▇@▇▇▇▇▇▇▇▇▇▇▇▇.▇▇▇
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
| TSA P&P #: CL-034 | Page 4 of 5 |
Supporting Documents
P&P Attachments:
| · | Attachment 1: TSA Delegated Entity Audit Results Notification Template |
Claims Department P&P’s:
| · | CL-002: Professional Claims Adjudication |
| · | CL-003: Institutional Claims Adjudication |
| · | CL-015: Claims Payments and Denials |
| · | CL-025: Claims Quality Audit Process |
Compliance Department P&P’s:
| · | COMP-006: Internal Compliance Audit and Monitoring Process |
Review and Revision History
| Date | Sections Affected | Reason for Change | Reviewer |
| 7/7/2016 | All policy and procedure | New Policy & Procedure | ▇▇▇▇▇▇▇ ▇▇▇▇▇ |
▇▇▇▇ ▇▇▇ Policy and Procedure Template. Hardcopies of this document are considered uncontrolled, for the latest version
please refer to Compliance 360 or contact Compliance Department through: mailto: ▇▇▇▇▇▇▇▇▇▇▇▇▇@▇▇▇▇▇▇▇▇▇▇▇▇.▇▇▇
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
| TSA P&P #: CL-034 | Page 5 of 5 |
Attachment 1: TSA Delegated Entity Audit Results Notification Template

2016 TSA Policy and Procedure Template. Hardcopies of this document are considered uncontrolled, for the latest version
please refer to Compliance 360 or contact Compliance Department through: mailto: ▇▇▇▇▇▇▇▇▇▇▇▇▇@▇▇▇▇▇▇▇▇▇▇▇▇.▇▇▇
Schedule J4
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
MESSAGE FROM THE CHAIRMAN OF THE BOARD OF DIRECTORS AND THE PRESIDENT AND CEO OF TRIPLE-S MANAGEMENT CORPORATION
dEAR COLLEAGUE:
our success as a Corporation is founded on the decisions we make. Every day, we face challenges that need to be addressed with the highest ethical standards. Ethical behavior is more than safeguarding our reputation or avoiding legal issues. We must do what is right. This Code of Business Conduct and Ethics, together with our policies and corporate guidelines, sets our standards for appropriate conduct. Read the Code in its entirety and refer to it often. Look in it for guidance whenever you are uncertain about any decision you are about to make. We are committed to integrity. We value our Corporation, customers and shareholders. By translating the principles of this Code into actions we will continue to achieve our goals. Thank you for joining us in this effort!
| ▇▇▇▇ ▇. ▇▇▇▇▇▇▇ ▇▇▇▇▇▇▇▇▇, MD | ▇▇▇▇▇ ▇▇▇▇-▇▇▇▇▇ |
| Chairman | President and CEO |
| Board of Directors | Triple-S Management Corporation |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
Code of Business Conduct and Ethics
OUR values
We RESPECT people and APPRECIATE their involvement.
We contribute to the DEVELOPMENT and WELL –BEING of our employees.
We value TEAM WORK.
We believe in INTEGRITY and ETHICAL BEHAVIOR in all our actions.
We believe PROACTIVITY, CREATIVITY and INNOVATION give us a competitive edge.
We believe in EXCELLENCE when serving our constituents.
We encourage EFFICIENCY and EFFECTIVENESS.
We promote the QUALITY OF LIFE in the communities we serve.
NOTE: This Code is part of the Corporation’s Compliance Program and is an important part of its internal control structure.
2
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
Code of Business Conduct and Ethics
OVERVIEW
Triple-S Management Corporation
Triple-S Management Corporation and its subsidiaries (collectively referred to as the “Corporation”) are committed to integrity, ethical behavior and professionalism in all areas. All employees, agents, officers, directors, consultants and independent contractors must respect and comply with all laws, rules and regulations applicable to the Corporation. This Code of Business Conduct and Ethics (“Code”) is intended to help us prevent and detect any illegal, improper and unethical conduct within the Corporation and to promote effective business controls. This Code is part of the corporation’s Compliance Program and is an important part of its internal control structure.
Who must follow the Code
This Code applies to all directors, officers, employees, agents, consultants and independent contractors of the Corporation at all times, anywhere throughout the world. Each one of us should read the Code in conjunction with any other policy, manual or handbook that applies to our respective jobs. Independent contractors are not employees of the Corporation, but their adherence to this Code is important because integrity, ethical behavior and respect to every individual shall permeate every activity in which we are involved.
Violations of this Code are subject to disciplinary, civil or legal action, including but not limited to termination of employment. In some cases, civil and criminal penalties may apply. Because of the significant legal and ethical consequences of noncompliance with the Code, disciplinary action may be taken with respect to not only those who violate the Code, but also those who – through lack of diligence or supervision – fail to prevent or report violations. This Code does not summarize all the laws, rules and regulations applicable to the Corporation, but it sets forth the behavioral expectations and guidelines for how we should conduct business.
Please consult with the Legal Affairs Office of TSM (hereinafter referred to as the “Legal Affairs Office”) if you have any questions related to this Code. Also, refer to the various corporate policies and guidelines which the Corporation has prepared regarding specific laws, rules and regulations.
3
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
Code of Business Conduct and Ethics
OUR RESPONSIBILITY
We are all responsible for knowing, understanding and complying with this Code as well as with all the corporation’s policies and procedures. The guidelines set forth in the Code should be used in conjunction with the policies and procedures of the Corporation including the Corporate Policies Manual, the Employee Handbook and other departmental or administrative procedures. While there may be some overlap, the Code does not replace or supersede any portion of the Employee Handbook not addressed by the Code. The detailed Corporate Policies Manual is available in its entirety to all employees on the Intranet. Any questions regarding specific employment related policies may be directed to your manager or the Human Resources Division staff. Consultants and independent contractors may request a copy of any applicable policy to its respective contact within the Corporation.
NOTE: We are all responsible for knowing, understanding and complying with this Code as well as with all the Corporation’s policies and procedures.
4
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
Code of Business Conduct and Ethics
ETHICAL CULTURE
This Code cannot possibly address every potential situation or issue we may face, so it’s important to understand the principles behind the Code and how to apply them. We must act honestly and ethically to safeguard the Corporation’s integrity.
If you have questions, you are encouraged to discuss the issue with your supervisor, speak with your designated Human Resources Representative, your Compliance Officer or contact the Legal Affairs Office for help and advice.
You should never engage in dishonest or illegal act, even if directed to do so by a supervisor, other employee, consultant or independent contractor. You should immediately report any request to engage in a dishonest or illegal act to your supervisor, your Compliance Officer or the Legal Affairs Office of TSM.
Compliance to our Code and other policies is subject to audit. The Vice-President of the Office of Internal Audit will periodically report to the Audit Committee of the Board of Directors of Triple-S Management Corporation in compliance with the Code.
Consider your actions and ask for guidance. If you are uncertain about a course of conduct, ask yourself:
| Ø | Is it consistent with the Code? |
| Ø | Is it ethical? |
| Ø | Is it legal? |
| Ø | Will it reflect well on me and the Corporation? |
| Ø | Would I want to read about it in the newspaper? |
If the answer is “NO” to any on these questions, do not do it.
5
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
Code of Business Conduct and Ethics
Directors’, Officers’ and Managers’ Responsibility
The managerial personnel (which include managers, directors, Vice-presidents, officers and directors of the Corporation) play a key role in implementing the Code and creating and sustaining a strong ethical work environment. This includes:
| · | Understanding, accepting and enforcing the Code. |
| · | Projecting an image of an ethical leader and maintaining a workplace environment supportive of the Code. |
| · | Educating employees in the meaning and application of the Code. Considering conduct in relation to the Code and policies when evaluating employees or independent contractors. |
Reporting Violations
We have the duty to report any known or suspected violation of this Code. Reporting a known or suspected violation shows responsibility and fairness and helps protect the Corporation’s reputation and assets. It is about sustaining a place where we all are proud to work in. We are all encouraged to speak to our supervisor , manager, compliance officer or other appropriate officer regarding any illegal or unethical behavior observed, any suspected violation of the Code or questions about the best course of action to follow when a particular situation whose legal or ethical nature is unclear. If you are aware of any violations to this Code, or other illegal or unethical conducts that may have occurred, we urge you to contact your supervisor, the Compliance Officer, the Vice-president of the Office of Internal Audit, The Legal Affairs Office of TSM. The Vice-President of the Office of Internal Audit and the General Counsel of Triple-S Management Corporation or their designees will investigate any alleged violations of our Code.
To report acts or suspicions of non-compliance with the Code or illegal activities you may contact the following persons at Triple-S Management Corporation:
| Office of Internal Audit |
|
Attention: Vice-President of Internal Audit Address: ▇.▇. ▇▇▇ ▇▇▇▇▇▇, ▇▇▇ ▇▇▇▇, ▇▇ ▇▇▇▇▇-▇▇▇▇ Fax: (▇▇▇) ▇▇▇-▇▇▇▇ E-mail: ▇▇▇▇▇▇▇@▇▇▇▇▇.▇▇▇ |
| Legal Affairs Office |
|
Attention: Corporate Compliance and Ethics Director Address: ▇.▇. ▇▇▇ ▇▇▇▇▇▇, ▇▇▇ ▇▇▇▇, ▇▇ ▇▇▇▇▇-▇▇▇▇ Fax: (▇▇▇) ▇▇▇-▇▇▇▇ E-mail: ▇▇▇▇▇▇▇▇@▇▇▇▇▇.▇▇▇ |
6
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
Code of Business Conduct and Ethics
An ethics helpline and website are available for those people that seek guidance or wish to report any known or suspected violation of the Code, in complete confidentiality and without fear of retaliation. These resources are intended to supplement existing internal communication channels and are not intended to replace the management team.
Ethics and Compliance Help Line: (▇▇▇) ▇▇▇-▇▇▇▇ (Toll free)
EthicsPoint Website: ▇▇▇.▇▇▇▇▇▇▇▇▇▇▇.▇▇▇
The Ethics Point Helpline is available 24 hours a day, seven days a week. After reporting a violation, you can expect that:
| Ø | A report will be filed and forwarded to the Audit Committee and the Office of Internal Audit for follow up. |
| Ø | The concern will be addressed by the appropriate personnel, which may include representatives from Compliance and Ethics, Human Resources, Legal Affairs, Security or Internal Audit. Each concern will be carefully evaluated before it is referred for investigation or resolution. |
| Ø | The concern will be handled promptly, discreetly and professionally. |
| Ø | Certain follow-up information about how the concern was addressed may be obtained upon request. |
DUTY TO COOPERATE WITH INVESTIGATIONS
The Corporation expects the full cooperation of all employees, officers, directors, agents and independent contractors during and after internal or external investigations. This duty includes providing truthful and honest information, giving verifiable facts and supporting documentation, and being available to be questioned by internal or external investigating officers.
REPORTING ACCOUNTING, AUDITING AND INTERNAL CONTROL IRREGULARITIES
We are committed to complying with all rules and regulations regarding financial and accounting reports that apply to the Corporation. If you have any concerns or complaints regarding questionable corporate accounting, auditing practices or internal control irregularities, you should submit those concerns or complaints (anonymously or confidentially if desired) to the Audit Committee of the Board of Directors, to any member of the Audit Committee or make a confidential report to EthicsPoint, as identified in REPORTING VIOLATIONS, on pages 10 and 11.
7
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
Code of Business Conduct and Ethics
NOTE: If you have any concerns or complaints regarding questionable corporate accounting, auditing practices or internal control irregularities, you should report them.
| Example: Two employees on a business trip eat dinner at a restaurant. One of them pays for the meal and is reimbursed by the Corporation for the expense. The other employee takes a duplicate receipt and submits an expense report for money he didn’t spend. The second employee is disciplined because he submitted a false expense report. |
OBLIGATION OF LEGAL ADVISORS
All of the Corporation’s legal advisors should inform the General Counsel of Triple-S Management Corporation and the Audit Committee regarding any violation to the Securities and Exchange Commission (“SEC”) regulations. If that person or entity does not act upon the evidence presented (adopting, as necessary, the corresponding preventive measures or sanctions), the legal advisor could present said evidence to the President and CEO of the Corporation or to the Audit Committee.
WHAT TO DO IF YOU HAVE EXHAUSTED AVAILABLE REPORTING CHANNELS
You should report known or suspected violations to the Audit Committee when you have exhausted available management channels or you are uncomfortable about bringing an issue to your supervisor.
|
FAX; (▇▇▇) ▇▇▇-▇▇▇▇
WEBSITE: ▇▇▇.▇▇▇▇▇▇▇▇▇▇▇.▇▇▇
POSTAL ADDRESS: ▇.▇. ▇▇▇ ▇▇▇▇▇▇, ▇▇▇ ▇▇▇▇, ▇▇ ▇▇▇▇▇-▇▇▇▇ |
NO DISCRIMINATION, NO RETALIATION
The Corporation will not discriminate or allow any retaliation against you from or on behalf of the Corporation or any other persons because of reports or complaints made in good faith or for participation in an investigation of violations to this Code, any internal policies or procedures, or of any other unethical or illegal behavior.
8
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
Code of Business Conduct and Ethics
MAKING FALSE ACCUSATIONS
The Corporation will protect any employee or independent contractor who raises a concern in good faith and honesty, but it is a violation of our Code to knowingly make a false accusation.
CONFIDENTIALITY
Confidentiality, including maintaining the informant’s identity anonymous, will be protected, subject to applicable laws, regulations and/or legal proceedings. You are expected to fully cooperate during an internal, external and/or government investigation.
CONSEQUENCES OF NON-COMPLIANCE
Any person who violates this Code or other internal policies and procedures of the Corporation is subject to corrective actions, up to and including termination of employment or contract. The degree of the corrective action will depend on the nature and circumstances of the violation. Some violations, such as those listed below, may be so serious that they warrant immediate notification to government authorities before, or simultaneously with, the beginning of an internal investigation:
| Ø | The incident is a clear violation of civil or criminal law. |
| Ø | It has a significant adverse effect on the quality of care provided to participants and beneficiaries. |
| Ø | It presents a pattern of a systematic failure to comply with applicable laws or contractual obligations. |
9
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
Code of Business Conduct and Ethics
REPORTS TO THE SECURITIES AND EXCHANGE COMMISSION (SEC)
As a Corporation that files reports with the SEC, it is important that reports submitted to the SEC be accurate and timely. Depending on your position within the Corporation, you may be called upon to provide necessary information to ensure that the Corporation’s public reports are complete, fair, accurate, timely and understandable. The Corporation expects you to take this responsibility very seriously, providing correct and rapid responses to questions regarding the Corporation’s public disclosure requirements.
10
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
Code of Business Conduct and Ethics
WORK ENVIRONMENT
OPEN DOOR POLICY
You are encouraged to communicate any idea or concern directly to management. It is important that you speak up promptly, so your ideas or concerns can be addressed. You can contact your Human Resources representative or the Legal Affairs Office of TSM for guidance if you think your supervisor cannot address your idea or concern or if you think your supervisor is part of the problem.
EQUAL EMPLOYEMENT OPPORTUNITY, NON-DISCRIMINATION AND HARASSMENT
It is our policy to ▇▇▇▇▇▇ a positive, productive work environment that promotes equal employment opportunity and prohibits discriminatory practices.
The Corporation is an equal opportunity employer. The Corporation forbids all forms of discrimination and employment decisions based upon an individual's qualifications, skills, and performance, without regard to race, color, sex, age, disability, veteran status, religion, national origin, ancestry, sexual orientation, or any characteristic protected by applicable law. Retaliation based on your report or complaint of discrimination is prohibited. You should promptly report perceived retaliation to your Human Resources representative. The Corporation will take appropriate disciplinary action against any individual who is proven to have taken adverse action against you on your complaint or report of alleged discrimination.
It is the Corporation’s policy that you, our customers, vendors, and visitors enjoy a positive, productive, and respectful environment that is free from harassment. Harassment, whether verbal, physical or related to the work environment, is unacceptable. The Corporation encourages the reporting of all incidents of harassment, regardless of who the offender may be. Retaliation against you, a customer, vendor, or visitor who in good faith alleges harassment will not be tolerated. All complaints of harassment or retaliation will be investigated and appropriate disciplinary or corrective actions will be taken.
| EXAMPLE: Today Mario has been telling racial jokes that are inappropriate for the workplace and offend me and other coworkers. What an I do? You should tell Mario that his jokes offend you. If you’re not comfortable doing so, talk to your supervisor or contact your human resources representative. Mario’s behavior is creating a hostile environment for you, and that could therefore constitute harassment. |
11
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
Code of Business Conduct and Ethics
Alcohol and Drug-Free Workplace
We are committed to providing an alcohol and drug-free workplace, which helps facilitate a safe and healthy work environment. None of us shall report to work under the influence of alcohol and/or illegal drugs. Additionally, you shall not manufacture, distribute, sell or be in possession of illegal drugs or prohibited substances. Unlawful substances are not to be stored in your vehicle while at the premises owned or controlled by the Corporation.
Searches of property owned or controlled by the Corporation may be conducted at any time, including those used or in possession of any employee, agent, officer, director, consultant and independent contractor. The Corporation may also take all legal and reasonable steps to search employees, agents, officers, directors, consultants and independent contractors and their property within the premises owned and controlled by the Corporation.
| EXAMPLE: ▇▇▇▇ notices that ▇▇▇▇▇ is acting strangely after her lunch. She does not express her ideas in an understandable and coherent manner and is staggering when she walks. When ▇▇▇▇ confronts her, she tells him she has the flu but he smells alcohol on her breath. What should he do? ▇▇▇▇ should report ▇▇▇▇▇ to her supervisor. If ▇▇▇▇▇ is under the influence of alcohol, she is creating a safety hazard for herself and for those around her in the workplace. This behavior cannot be tolerated because it violates our Corporation’s policy. |
CORPORATE OPPORTUNITY
You are forbidden to:
| Ø | Make personal use of opportunities that in truth belong to the Corporation, or which are discovered through corporate property, information, or position. |
| Ø | Using corporate property, information or position for personal benefit. |
| Ø | Competing with the Corporation. |
You must promote the Corporation’s legitimate interests when the opportunity to do so arises.
WORKPLACE HEALTH AND SAFETY
The health and safety of our people are of utmost importance to the Corporation, which is committed to protecting the health and well-being of each employee. We srive to
12
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
Code of Business Conduct and Ethics
protect our people, customers and the public from injury and illness through our Health and Safety Program.
You are required to advise the Corporation of any work-related vehicle accident, workplace injury, instance of non-compliance, or any situation which may represent a risk of injury. When an unsafe condition, practice, or non-compliant action is identified, prompt and appropriate action must be taken to correct the condition and prevent it from happening again.
Workplace or domestic Violence
The Corporation will not tolerate acts of violence, threats, harassment, intimidation, intentional or reckless destruction of property or other disruptive behavior in its workplace, its premises or any other place at which an event conducted or sponsored by the Corporation takes place.
If you witness, are the subject of, or have knowledge of a threatening behavior, you should immediately report it to your supervisor, Compliance Officer, Office of Corporate Security or the Human Resources Division.
Weapons
The Corporation prohibits any individual from keeping weapons on property owned or controlled by the Corporation. In addition, weapons may not be kept in vehicles parked at company owned or controlled parking lots. Weapons include, but are not limited to, guns, knives and/or ammunition.
ENVIRONMENTAL PROTECTION
We are committed to conducting our business in a manner that protects the environment. Our commitment includes the advancement of programs that promote improvement of the environment, such as recycling. Everyone who is part of the Corporation is expected to support our effort to maintain a leadership role in protecting the environment.
13
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
Code of Business Conduct and Ethics
ANTI-FRAUD POLICY
The Corporation has zero tolerance for fraudulent or illegal acts. Fraud is any intentional conduct performed with the intent to misrepresent facts in order to obtain a benefit to which the individuals not entitled. Fraud can be committed by internal or external individuals. The Corporation is firmly committed to complying with federal and local anti-fraud statutes. Consequently, it has an adequate infrastructure to monitor, detect, investigate and refer to public enforcement agencies any fraudulent or illegal activity.
Keep in mind that illegal acts or improper conduct may represent severe financial losses and may expose the Corporation to administrative, civil and criminal penalties, including large fines and being barred from certain types of business. Therefore, you must report any illegal activity or violations of the Code to the appropriate personnel, as identified I REPORTING VIOLATIONS on pages 10 and 11.
NOTE: The Corporation has zero tolerance for fraudulent or illegal acts and is firmly committed to comply with federal and local anti-fraud statutes.
MONEY LAUNDERING
It is the process by which individuals or entities try to conceal illegal funds or otherwise enter into transactions to make these funds appear legitimate. The Corporation does not condone, facilitate or support money laundering. Few of us will ever personally be in the position to violate money laundering laws, but we all need to be alert to irregularities in the way payments are made, including large cash payments and unusual transactions. Furthermore, we have the responsibility to conduct due diligence on our customers, intermediaries and business partners, and to report any suspicious behavior.
| EXAMPLE: A customer visits our offices and tells you he wants to buy an insurance product. He gives you $12,000 in cash to pay the premium of the whole year in advance. What you should do? Transactions over $10,000 must be reported. Follow the corporate procedures implemented to handle these cases, including the filing of various forms to document the transaction. Be sure to contact your Compliance Officer if you have any questions. |
14
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
Code of Business Conduct and Ethics
Fair Dealing
You should endeavor to deal fairly with the Corporation’s clients, suppliers, competitors, officers, and directors. No one should take unfair advantage through manipulation, cover-up, concealment or the abuse of privileged information, misrepresentation of material facts, or any other unfair business practice. To preserve our relationships: 1) we do not misrepresent our services or products in any sales or promotional efforts; 2) we communicate clearly, so that our customers and contractors understand the terms of our business relationships, including contracts performance criteria, schedules, prices and responsibilities and 3) we only make promises to customers that we believe we will be able to keep.
| EXAMPLE: While attending a customer meeting with another corporate employee, the other employee made what I believe to be an intentionally false statement about our capabilities in order to retain the account. What should I do? Correct the error during the meeting if possible. If that is not possible, raise the issue with the employee, your manager or other responsible corporate personnel after the meeting, and ensure that the Corporation corrects any customer misrepresentation. If you are correct that the other employee intentionally lied to a customer, the other employee has violated the Code. |
15
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
Code of Business Conduct and Ethics
Conflicts of Interest
You must be scrupulous in avoiding a conflict of interest regarding the Corporation’s interests. A “conflict of interest” exists whenever an individual’s private interests interfere or diverge or diverge in any way (or even appear to interfere or diverge) with those of the Corporation.
It is the Corporation’s policy to avoid any situation that involves, or appears to involve, a conflict between the interests of the Corporation and your interests. Conflicts of interest are prohibited as a matter of corporate policy.
Conflicts of interest can arise when you are directly or indirectly connected with a present or potential supplier, competitor, or customer.
Outside financial or business involvement by members of your immediate family, or by persons with whom you have a close personal relationship, may create a possible conflict of interest, and are subject to the requirements of this policy.
Moreover, it is our policy to prohibit anyone from: taking personal opportunities that are discovered through the use of corporate property, information or position; using corporate property, information or position for personal gain; or competing against the Corporation.
A conflictive situation can arise when any of us undertake some action or have interests that adversely affect the objective and effective performance of our duties in the Corporation. Another possible conflict could emerge if you, or some member of their family, receive improper personal benefits as a result of your position in the Corporation, whether the benefit is received from the Corporation or from a third party. You should also avoid outside activities that interfere with your working hours or your regular duties, adversely affect the quality of the work performed or negatively impact the Corporation.
Personal loans to, or guarantees of obligations by the Corporation may also create conflicts of interest and are subject to the requirements of this Code. Loans to its directors and/or executive officers are prohibited by law and the Corporation.
Such conflicts may not always be clear-cut; therefore, any question should be consulted with the highest managerial levels or with the Legal Affairs Office of TSM. If you observe, encounter or discover a conflict or a potential conflict you should inform a supervisor, manager, or consult and/or follow the procedures described in this Code.
16
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
| EXAMPLE: It is my job to select a supplier for the Corporation. One of the suppliers being considered is a company owned by my spouse. Do I need to take any precautions? Yes. In this situation your interest in your spouse’s business conflicts – or at least appears to conflict – with your responsibility to select the best supplier for the Corporation. The best course of action is either for you not to be involved in the selection process and disclose the conflict of interest immediately or for your spouse’s business to be eliminated from consideration. |
17
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
Code of Business Conduct and Ethics
Confidentiality
We cannot disclose confidential information entrusted to us by the Corporation, its suppliers, clients, or any other person, except when disclosure is authorized by the Legal Affairs Office or required by law, regulations, or legal proceedings. If you understand there is a legal obligation to disclose such information, you must consult with the Legal Affairs Office.
It is the Corporation’s policy to protect the privacy of past, present and prospective customers, members, plan participants, policyholders, insureds, and its employees and other similar parties, consistent with applicable law. All individually identifiable personal information will be collected only as reasonably necessary for the conduct of the Corporation’s business.
It is also the Corporation’s policy to protect its information assets from accidental or unauthorized modification, destruction and/or disclosure. We must protect corporate information assets and must follow the requirements provided by the Corporation. Safeguarding confidential information requires our compliance with all related policies and procedures, protect paper documents and individual workstations; manage passwords properly, secure software, back up critical data; and use the Corporation’s networks safely and responsibly.
It is expected that in the event a consultant, agent or independent contractor experiences a security breach in which confidential information is exposed, a process is implemented to mitigate, to the extent practicable, any harmful effect. This includes the duty to promptly notify the Corporation and each affected individual, and cover all the costs incurred by the Corporation if it has to notifyits customers of such exposure.
| EXAMPLE: You went out to work with a coworker. At the restaurant, the two of you discussed a project – on which you are both working- with a lot of detail, including several of your secret business strategies. When leaving the restaurant, you notice that in the table next to yours were seated employees from a rival company. What should you do? Notify your supervisor of the potential disclosure so he/she can work with legal counsel to avoid or minimize damage. We must protect our Corporation’s confidential information and exercise caution when discussing such information in public spaces, like restaurants. |
18
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
Code of Business Conduct and Ethics
Reporting and Public Disclosures of Corporate Information
The Corporation is committed to provide full, fair, accurate, timely and understandable disclosure in its public communications and in the reports and documents that it files with regulatory authorities, including the SEC. Strict compliance with both the spirit and the letter of the laws governing public disclosures and reporting to SEC is required. The Corporation’s disclosures will enable its stockholders to understand (i) the key business opportunities it seeks, (ii) the issues and risks it manages, (iii) the critical accounting policies it employs and (iv) the important judgments it makes in preparing its financial statements.
Certain employees are authorized to release information about the Corporation as part of their duties, subject to corporate procedures. Other than those employees, no one should release information concerning the Corporation or its business activities without prior, written approval from the Legal Affairs Office of TSM.
Confidential Information About Employees
Confidential information must not be revealed to anyone, except when necessary for legitimate business purposes or as permitted by law. Confidential information includes, but is not limited to wage and salary data, employment agreements, social security numbers, information on leaves, financial/banking information and claims/medical information.
| EXAMPLE: I have just received an e-mail by accident with a file containing the salaries of several other employees. May I share it with other people at work? No. if you and your colleagues have no business reason to have this information, you should delete the e-mail and bring the error to the attention of the sender immediately. Disclosing the information to other employees is a code violation. |
Confidential Information About insureds and other customers
Numerous federal and state laws govern the use and disclosure of health and financial information relating to the Corporation’s members. The Health Insurance Portability and Accountability Act of 1996 (“HIPAA”) prohibits unauthorized disclosure of the Corporations members’ protected health information (“PHI”).
19
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
Code of Business Conduct and Ethics
The Corporation’s policies and procedures include HIPAA requirements, which must be followed when dealing with PHI. Accessing or sharing confidential member information, except as necessary to do the assigned job is inappropriate. We must uphold the trust that the Corporation’s customers have placed in the Corporation and keep their information confidential.
| EXAMPLE: I know that an employee in my work area accessed and viewed PHI about his neighbor without any business cause, in order to harm his heighbor’s reputation. Do I have to report this? Yes. The other employee committed a violation of the Code that is subject to disciplinary action and is reportable to federal agencies. |
Material Nonpublic or Inside Information About Our Corporation
The communication, release and use of material nonpublic or inside information for personal financial benefit or financial benefit of family, friends or closely related persons is strictly prohibited. You must not buy or sell securities of the Corporation securities, based on knowledge of material nonpublic or inside information.
In addition, you must not share or disclose material nonpublic or inside information with co-workers, family, friends or others unless the other party is considered an “insider,” has signed a non-disclosure or confidentiality agreement with the Corporation, or the information is required as part of doing business and the appropriate functional approval has been obtained from the Legal Affairs Office.
The use of material nonpublic or inside information about other publicly traded companies is also prohibited. You must not buy or sell securities of other companies about which they have knowledge or any other material inside information.
Information is material if it is likely to be a consideration to an investor in determining whether to buy, sell, or hold the particular company’s securities. Information is nonpublic if it has not yet been fully disclosed to the public.
Any inappropriate use or disclosure of inside information may expose you, the company, and any person to whom the inside information is communicated, to severe penalties, both criminal and civil, under applicable law.
20
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
Code of Business Conduct and Ethics
Before trading in the Corporation’s securities, company officers, members of the Board of Directors and other designated associates should consult and must pre-clear any transactions with the General Counsel or the Chief Financial Officer of Triple-S Management Corporation.
NOTE: You must not share or disclose material non-public or inside information with co-workers, family, friends or others.
| EXAMPLE: I have learned that the Corporation is considering the acquisition of a small, publicly traded company. May I acquire the stock of this company in anticipation of the acquisition? No. Trading on material non-public information is illegal and a violation of the Code. |
PROTECTION AND PROPER USE OF THE CORPORATION’S ASSETS
The Corporation’s assets include property such as materials, facilities, furniture, supplies, office equipment of all kinds, telephone and mail systems, voice mail and e-mail systems, computers, computer networks, software, and information relating to the company, the products and services it provides, and its customers. Assets also include any documents or records that have financial value such as currency, checks, vouchers, credit or other charge cards, receivables, payables, records of time worked, expense reimbursements or invoices.
It is our policy that its assets be adequately protected from loss, damage or misuse. We must protect the Corporation’s assets and ensure their efficient use. Theft, carelessness, waste and alterations, all have a direct impact on the Corporation’s assets. All such assets must be only used for corporate business or any legitimate purpose determined by the Corporation.
We must not use, sell, loan, give away or dispose of corporate assets regardless of condition or value, except when properly authorized by corporate policy. We are expected to use corporate assets in a professional, productive, ethical and lawful manner consistent with our corporate policies.
|
EXAMPLES:
Personal favor. An employee used corporate computer and equipment, as well as time at work to design and print a school project for the daughter/son of another employee. The employee misused corporate assets.
Personal assistance. A manager persistently asked an administrative assistant to take |
21
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
Code of Business Conduct and Ethics
| care of the manager’s personal matters on corporate time, such as picking up laundry, medical appointments, balancing a personal checkbook or shopping for personal gifts. The manager is misusing the assistant’s work time, which is a corporate asset.
Teaching. As marketing manager, I have volunteered to teach a course on marketing at a local college. I believe that my students would benefit from a discussion of how the Corporation developed marketing campaigns. Can I discuss this work in class? No. You can only do this with the prior approval from the President of your company. The development of marketing campaigns is a corporate work product and a corporate asset. Much of this work may be proprietary, and may not be appropriate to reveal outside the Corporation. |
NOTE: We must protect the Corporation’s assets and ensure their efficient use.
NAMES, LOGOS AND INTELLECTUAL PROPERTY
All names and logos to be used by the Corporation and all of us must be the approved names and logos of the Corporation. The Advertising and Public Relations Office is responsible for developing and managing brand positioning standards for all references to the Corporation in advertising, promotional materials, stationery, and other forms of communications media used externally.
The Corporation owns all innovations, ideas, inventions, discoveries and improvements conceived, created, made or discovered by its employees while employed by the Corporation, if they relate or pertain in any way to the Corporation’s business. This includes innovations made by employees working alone or with others. All innovations conceived of or made by an employee will be deemed to have been made in the course of employment unless the innovations: 1) were developed on the employee's own time; 2) outside the employee's regular or assigned duties for the Corporation; and 3) no equipment, facility, or proprietary information of the Corporation was used.
It is the Corporation’s policy is to take necessary steps to secure and protect its rights in its intellectual property and to protect it from illegal use or other misuse by ensuring it is affixed with or identified by "Confidential" notices, trademark, service ▇▇▇▇ or copyright symbols and by avoiding any inappropriate or unauthorized disclosures.
ANTITRUST AND OTHER COMPETITION LAWS
Antitrust laws are designed to ensure a fair and competitive free market system where no single company has a monopoly on providing a service or a product. While the
22
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
Code of Business Conduct and Ethics
Corporation competes vigorously in the marketplace, it complies with the applicable antitrust and competition laws wherever it does business.
This means that the Corporation competes on the merits of its services, prices and customer loyalty. The Corporation independently determines the pricing structure of its products and providers contracts, subject to applicable regulatory review. Our actions in the marketplace define who we are as a Corporation.
Some of the most serious antitrust offenses occur between competitors, such as agreements to fix prices or to divide customers, territories or markets. It is therefore very important for us to avoid discussions with competitors regarding customers, pricing policies, bids, discounts, promotions, terms and conditions of sale and any other proprietary or confidential information.
Competition laws also prohibit entering into formal or informal agreements with suppliers, distributors or clients that may restrict competition. Such agreements include tying products, or refusing to sell to particular clients or buy from particular suppliers.
We must remember that unlawful agreements need not be written or even consist of express commitments. Agreements can be inferred based on “loose talk,” informal discussions, or the mere exchange of certain information. If a conversation with a competitor enters an inappropriate area, we should end the conversation at once and report the matter immediately to the Legal Affairs Office.
Please note that violating these laws may subject both the individuals involved and our corporation to severe consequences.
TRANSACTIONS WITH GOVERNMENT OFFICERS
Transactions with governments are covered by special legal rules and are not the same as conducting business with private parties. In general, do not offer anything to an agent of public service – directly or indirectly – in return for favorable treatment. To be responsible members of our business community, we must follow the law wherever we do business, regardless of local law or custom.
Bribes are prohibited. A bribe is giving or offering anything of value to an agent of public service to influence a discretionary decision. Examples of a bribe include the payment to an agent of public service to encourage a decision to award or continue a business relation, to influence the outcome of a government audit or inspection or to influence on tax ruling or any other legislation. Obtain prior approval before providing anything of value to an agent of public service.
23
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
Code of Business Conduct and Ethics
We shall be completely honest in all dealings with government agencies and representatives. No misrepresentations shall be made, and no false bills or requests for payment shall be submitted to government agencies. Personnel certifying the correctness of records submitted to government agencies, including bills or requests for payment, shall have knowledge that the information is accurate and complete before giving such certification. Personnel who participate in government interviews shall always give truthful, complete and unambiguous answers.
NOTE: We shall be completely honest in all dealings with government agencies and representatives.
HIRING AN AGENT OF PUBLIC SERVICE
The Corporation may hire public officers to perform services that have a legitimate business purpose and do not conflict with the public officer’s duties, such as hiring an off-duty police officer to provide security at a corporate event. All such hiring decisions must have the prior approval of an officer of the Corporation.
IMPROPER PAYMENTS BY THIRD PARTIES
The Corporation may be held liable for bribes paid by a third party agent, consultant or independent contractor acting on behalf of the Corporation. You must not engage a third-party agent, consultant or independent contractor if there is any reason to believe that such third-party may attempt to bribe an agent of public service.
COOPERATION WITH GOVERNMENT INQUIRIES
From time to time, the Corporation may be asked to cooperate with a government investigation or to respond to a request for information from the government about how we conduct our business. The request may come through official channels from the government to the Corporation’s management or you could be contacted individually by a member of a law enforcement agency, such as the Department of Justice, the Federal Bureau of Investigations (FBI) or the Office of the Inspector General.
It is the Corporation’s policy to cooperate fully and truthfully on all such matters. To ensure that this process is conducted efficiently, immediately notify the General Counsel of Triple-S Management Corporation and inform that you have been contacted by a government representative. The decision of whether or not to cooperate with their inquiry is up to you alone and you will not be disciplined, punished or otherwise retaliated against if you decide to do so. Although you are free to cooperate individually with the government investigators, you may not provide documents or data that belong to the Corporation or are in its custody and control in response to a government request for information without first obtaining authorization from the Corporation’s legal counsel.
24
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
Code of Business Conduct and Ethics
POLITICAL ACTIVITIES AND CONTRIBUTIONS
Local and federal laws restrict the use of corporate funds and assets in connection with elections and other political activities. Consequently, we may not make any political contribution to any candidate, office holder or political organization for or on the behalf of the Corporation.
The term “political contribution” includes payments, provision of services, purchasing tickets or furnishing supplies on behalf of a candidate running for political office. The covered persons may not use any corporate property, facilities or time of any other employee for any political activity.
The Corporation recognizes your right as a citizen to participate in the political process. When engaged in political activities, you shall let it be known that the views expressed are yours as an individual and not those of the Corporation.
NOTE: We may not make any political contribution to any candidate, officeholder or political organization for or on the behalf of the Corporation.
| EXAMPLE: My friend is running for political office, and I would like to help with the campaign. Is this allowed? Yes. Your personal political activity in your leisure time is your own concern. Just make sure that you do not use corporate resources, including corporate time, e-mail, equipment or supplies or the corporate name to advance the campaign. |
CHARITABLE CONTRIBUTIONS
The President of the Corporation and the Presidents of each of its subsidiaries are the only persons authorized to make charitable contributions on behalf of their respective company. Requests for charitable contributions should be referred to the President of each particular company. Under no circumstances you should use the Corporation’s funds to make charitable contributions on behalf of the Corporation.
gifts and entertainment
The Corporation recognizes that business gifts and entertainment can create goodwill and sound working relationships. However, the use of business gifts and entertainment for gaining special advantage or unduly influencing employees, customers, suppliers or others doing business with the Corporation is strictly prohibited. Gifts over $200, in value, in total over a one year period, have to be reported and approved by the President of the particular company.
25
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
Code of Business Conduct and Ethics
Do not accept gifts in exchange for doing or promising to do anything for a customer or supplier. Do not ask for gifts. Gifts or discounts offered to a large group of corporate employees as part of an agreement between the Corporation and a customer or supplier may be accepted and used as intended by the customer and supplier.
Purchase of goods and services on behalf of the Corporation must not benefit you or your family in the form of kickbacks or rebates. Kickbacks or rebates can take many forms and are not limited to direct cash payments or credits. In general, if you or your family benefit personally from the transaction, it is prohibited.
Such practices are not only unethical but, in many cases, they are illegal. It is strictly prohibited by this Code to accept cash, bank issued gift/debit cards, gift certificates redeemable for cash, checks or similar items.
| EXAMPLE: Last year, an independent contractor sent you a box of fine chocolates for the Holidays. This year, the same contractor sends you an expensive watch, valued at $500.00 with your name engraved on it. May you keep the watch? No. The chocolates were within the bounds of a reasonable gift, but the personalized watch goes beyond our Corporation’s monetary limit. You should politely decline the gift. |
Amendments, Modifications and Waiver
This Code may be amended, modified or suspended by the Board of Directors, who can also grant suspensions or waivers, subject to disclosure and other applicable provisions of the Securities and Exchange Act of 1934, as amended, and other applicable regulations.
The policies contained in this Code apply to all the Corporation’s controlled entities, regardless of geographic location.
This Code is posted on the Corporation’s website: ▇▇▇.▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇.▇▇▇
If you want to make a contribution to ▇▇▇▇▇▇ our commitment to ethical behavior, please send your comments to:
| ATTENTION: Corporate Compliance and Ethics Director |
|
FAX: (▇▇▇) ▇▇▇-▇▇▇▇ E-MAIL: dallende @▇▇▇▇▇.▇▇▇ POSTAL ADDRESS: ▇.▇. ▇▇▇ ▇▇▇▇▇▇ ▇▇▇ ▇▇▇▇, ▇▇ ▇▇▇▇▇-▇▇▇▇ |
26
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
Code of Business Conduct and Ethics
This Code of Business Conduct and Ethics was approved by the Board of Directors of Triple-S Management Corporation on October 5, 2010.
27
Schedule J5
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
 |
 |
Compliance Program
Effective Lines of Communication
Compliance Officer:▇▇▇▇▇ ▇▇▇▇▇▇▇▇ ▇▇▇▇▇▇▇
Privacy Officer: ▇▇▇▇ ▇▇▇▇▇▇▇ ▇▇▇▇▇▇
 1-866-384-4277
1-866-384-4277
 ▇▇▇.▇▇▇▇▇▇▇▇▇▇▇.▇▇▇
▇▇▇.▇▇▇▇▇▇▇▇▇▇▇.▇▇▇
Compliance Department Email:
▇▇▇▇▇▇▇▇▇▇▇▇▇@▇▇▇▇▇▇▇▇▇▇▇▇.▇▇▇
Effective Lines of Communications
Anonymous • Confidential • No retaliation • No discrimination • No intimidation
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Compliance Program
Approved by the Board of Directors on March 29, 2016
Last Review Date: August 15, 2017
2| Compliance Program
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Table of Contents
| Organization Overview | 4 |
| Commitment to Compliance | 5 |
| general overview | 6 |
| Element 1: Written Policies, Procedures and Standard of Conduct | 7 |
| Element 2: Compliance Officer, Compliance Committee and High Level Oversight | 8 |
| Element 3: Effective Training and Education | 15 |
| Element 4: Effective Lines of Communication | 18 |
| Element 5: Well Publicized Standards | 21 |
| Element 6: Effective System for Routine and Monitoring and Identification of Compliance Risk | 23 |
| Element 7: Procedures and System for Prompt Reponses to Compliance Issues | 28 |
| Laws and regulations | 32 |
| DEFINITIONS | 33 |
| Contact us | 37 |
3| Compliance Program
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Organization Overview
Triple-S was founded in 1959 by doctors and dentists who were concerned with the need to provide better access to healthcare. Triple-S Management (TSM) was created 1999 as part of a corporate reorganization and to serve as holding company for its health, life and property insurance businesses. TSM became a public company on December 7, 2007. Its shares are traded in the New York Stock Exchange, under the symbol GTS.
The TSM family of companies includes: Triple-S Salud (health insurance), Triple-S Advantage (Medicare Advantage health insurance), Triple-S Vida (life insurance), and Triple-S Propiedad (property and casualty insurance). Other affiliates operate in Costa Rica and the US Virgin Islands.
Triple-S Salud (TSS), Triple-S Advantage (TSA) and Triple-S Blue are Blue Cross Blue Shield licensees and have the exclusive right to use the BCBS name and logo throughout Puerto Rico, the U.S. Virgin Islands, Costa Rica, the British Virgin Islands and Anguilla.
TSS has a contract with Puerto Rico Health Insurance Administration, “PRHIA”for Medicare Platino and Mediciad Programs and TSA, Inc. is licensed to conduct managed care business in Puerto Rico, and has a contract with Centers for Medicare and Medicaid Services (CMS) for Medicare Advantage Prescription Drug (MAPD) programs.
| ü | Vision |
Be recognized as market leader in the health industry in the communities we serve.
4| Compliance Program
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
| ü | Mission |
We take better care of your health, wellbeing and peace of mind during life’s expected and unexpected events.
Commitment to Compliance
Statement from the Chairman of the Board of Directors and
CEO, Triple –S Management Corporation
Dear Colleague
Our success as a Company is founded on the decisions we make. Every day, we face challenges that need to be addressed with the highest ethical standards. Ethical behavior and a compliance culture are more than safeguarding our reputation or avoiding legal issues. We must do what is right.
This Compliance Program (“Program”) and compliance policies and procedures together with our Code of Business Conduct and Ethics, sets our standards for expected conduct. Read this Compliance Program in its entirety and refer to it often. Look in it for guidance whenever you are uncertain about any decision you are about to make.
Our commitment to comply with all applicable Federal and Commonwealth of Puerto Rico laws, regulations and guidelines and doing our jobs with ACCOUNTAIBLITY, INTEGRITY, RESPECT, EXCELLLENCE, INNOVATION and COMMITMENT, support our mission to take better care of the member’s health, well-being and peace of mind during life’s expected and unexpected events.
By translating the elements of this Program into actions we continue to achieve our goals. We count on you to take our Compliance initiatives to the next level!
Thank you,

5| Compliance Program
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
General Overview
The Compliance Program reflects our interpretation of CMS Compliance Program requirements. In order to be effective, this Program is tailored to the Triple-S Salud (TSS) and Triple – S Advantage (TSA) unique operations and circumstances. TSS and TSA has devoted adequate resources to this Program to promote and enforce the Code of Business Conduct and Ethics and this Program, train and educate our Board of Directors members, employees, as well as consultants and FDRs, establish effective lines of communication within our self and between our FDRs, overseeing FDRs compliance with this Program and Medicaid, Commercial, Medicare Part C and D requirements, establishing and implementing an effective system for routine auditing and monitoring and identifying and promptly responding to risks and findings. TSS and TSA conducts its quality management functions in accord with applicable laws, regulations and current URAC accreditation standards.
This Program includes the following core elements:
| 1. | Written Policies, Procedures and Standard of Conduct; |
| 2. | Compliance Officer, Privacy Officer, Compliance Committees and High Level Oversight; |
| 3. | Effective Training and Education; |
| 4. | Effective Lines of Communication; |
| 5. | Well Publicized Disciplinary Standards; |
6| Compliance Program
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
| 6. | Effective System for Routine Monitoring and Identification of Compliance Risks; and |
| 7. | Procedures and System for Prompt Response to Compliance Issues. |
This Program is subject to change as policy, technology and Medicaid, Commercial, and Medicare business practices continue to evolve.
Element 1: Written Policies and Procedures and Standard of Conduct
TSS and TSA adopts the Code of Business Conduct and Ethics and Employee Handbook of TSM and has implemented the Code of Business Conduct and Ethics, Compliance Program and policies and procedures. The Code of Business Conduct and Ethics and policies and procedures:
| ü | Articulate our commitment to comply with all applicable Federal and State standards; |
| ü | Describe compliance expectations as embodied in the Code of Business Conduct and Ethics; |
| ü | Implement the operation of the compliance program; |
| ü | Provide guidance to employees and others on dealing with suspected, detected or reported compliance issues; |
| ü | Identify how to communicate compliance issues using the effective lines of communications; |
| ü | Describe how suspected, detected or reported compliance issues are investigated and resolved by Triple-S ; and |
| ü | Include a policy of non-intimidation, non-discrimination and non-retaliation for good faith participation in this Program, including, but not limited to, reporting potential |
7| Compliance Program
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
issues, investigating issues, conducting self-evaluations, audits and remedial actions, and reporting to appropriate officials.
TSS and TSA compliance policies and procedures are detailed and specific, describe the operation of this Program, and are updated to incorporate changes in applicable laws, regulations, other program requirements and accreditation standards.
The Code of Business Conduct and Ethics, this Program, as well as compliance policies and procedures are distributed to all the employees and FDRs within ninety (90) days of initial hire or contract, when there are updates and annually thereafter. For more information refer to the policy and procedure COMP-001 Development, Review, Approval and Distribution of the Code of Business Conduct and Ethics, Compliance Program and Policies and Procedures.
Element 2: Compliance Officer, Compliance Committee and High Level Oversight
The President of Triple-S Salud, Inc. (TSS) and Triple-S Advantage, Inc. (TSA) designates a Compliance Officer and a Privacy Officer. Similarly, the Board of Directors of TSS and TSA delegates the Compliance Program oversight to the Executive Compliance Committee. Furthermore, the President designates the members of the Vendor Management Oversight Committee (VMOC). Those components, together, shall oversee the performance of the Compliance Program.
The Compliance Officer have express authority to provide unfiltered, in-person reports to the Board of Directors and is responsible for the implementation of the Compliance Program, the definition of the program structure, educational requirements, reporting and complaint mechanisms, response and correction procedures, and compliance expectations of all personnel and FDRs. Additional duties of the Compliance Officer include, but are not limited to:
| þ | Chair the Executive Compliance Committee. |
8| Compliance Program
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
| þ | Ensuring that compliance reports are provided regularly to the Executive Compliance Committee, Board of Directors, and President. Reports includes the status of the Compliance Program implementation, the identification and resolution of suspected, detected or reported instances of noncompliance, and compliance oversight and audit activities; |
| þ | Being aware of daily business activity by interacting with the operational units; |
| þ | Creating and coordinating educational training programs to ensure that Board of Directors, employees, FDRs, and other individuals working in the Medicare program are knowledgeable about the Compliance Program, its written Code of Business Conduct and Ethics, compliance policies and procedures, and all applicable statutory and regulatory requirements; |
| þ | Developing and implementing methods and programs that encourage managers and employees to report Medicare program noncompliance and potential FWA without fear of retaliation, discrimination or intimidation; |
| þ | Maintaining the compliance reporting mechanism and closely coordinating with the internal audit department and the Audit and Investigation Unit (SIU), where applicable; |
| þ | Responding to reports of potential FWA, the development of appropriate corrective or disciplinary actions and coordinate internal investigations. |
| þ | Ensuring that the DHHS OIG and Government Services Administration (“GSA”) exclusion lists have been checked with respect to all employees, Board of Directors members, and FDRs monthly and coordinating any resulting personnel issues with the Triple S Management (TSM) Human Resources, Security, Legal or other departments as appropriate; |
| þ | Maintaining documentation for each report of potential noncompliance or potential FWA received from any source, through any reporting method (e.g., helpline, Compliance email, or in-person); |
| þ | Overseeing the development and monitoring of corrective action plans implementation; |
| þ | Coordinating potential fraud investigations/referrals and the appropriate NBI MEDIC. This includes facilitating any documentation or procedural requests that |
9| Compliance Program
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
the NBI MEDIC makes of Triple-S.
| þ | Review contracts and other documents pertinent to the Medicare and other government programs; |
| þ | Report potential FWA to CMS, ASES, OCI its designee or law enforcement. |
| þ | Overseeing the FDRs performance thru the active participation of VMOC. |
To assist the senior management in observing its responsibilities related to the TSA/TSS operational compliance with applicable legal requirements and comprehensive ethical standards, senior management has established an Executive Compliance Committee, which will provide oversight of and direction to the Compliance Officer and receive report from the Compliance Officer no less frequently than every quarter.
The Executive Compliance Committee will undertake the following responsibilities and duties and any other activities related to the Compliance Program as delegated by the Board of Directors and established in the Compliance Program.
| þ | Development, implementation and annual review and approval of the compliance policies and procedures; |
| þ | Development of strategies to promote compliance and the detection of any potential violation; |
| þ | Review and approval of compliance and FWA training, and ensuring that training and education are effective and appropriately completed; |
| þ | Assist with the creation, approval and implementation of the compliance risk assessment and of the compliance monitoring and auditing work plan and audit results; |
| þ | Assist in the creation, implementation and monitoring of effective corrective actions; |
| þ | Development of innovative ways to implement appropriate corrective and preventative action; |
| þ | Review and approval of corrective action plans resulting from audits; |
10| Compliance Program
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
| þ | Review the effectiveness of the system of internal controls designed to ensure compliance with Medicare regulations and other applicable federal and local laws in daily operations; |
| þ | Support the compliance officer’s needs for sufficient staff and resources to carry out his/her duties; |
| þ | Oversee that TSS/TSA has appropriate, up-to-date compliance policies and procedures; |
| þ | Oversee that TSS/TSA has a system for employees and FDRs to ask compliance questions and report potential instances of Commercial/ Medicare/Medicaid programs noncompliance and potential FWA confidentially or anonymously (if desired) without fear of retaliation; |
| þ | Oversee that the sponsor has a method for enrollees to report potential FWA; |
| þ | Review and address reports of monitoring and auditing of areas in which TSS/TSA are at risk for program noncompliance or potential FWA and ensuring that corrective action plans are implemented and monitored for effectiveness and; |
| þ | Review of Compliance Officer ad hoc reports on the status of compliance with recommendations to the Board of Directors; |
| þ | Review of dashboard, scorecard, and self-assessment tools that reveal compliance issues; |
| þ | Review of internal and external oversight activities results and government compliance enforcement activities. |
The Privacy Officer respond to the Compliance Officer and reports to the Executive Compliance Committee. The responsibilities includes, but is not limited to:
| þ | Provides guidance and assists in the identification, development, , maintenance of information privacy policies and procedures and implementation; |
| þ | Performs annual privacy risk assessment and conducts relevant privacy monitoring activities; |
| þ | Oversees the development and monitoring of corrective action plans implementation. |
11| Compliance Program
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
| þ | Manages external audits related to privacy requirements. |
| þ | Ensures that the organization maintains appropriate privacy and confidentiality forms, notices and materials reflecting current organization and legal practices and requirements; |
| þ | Creates and coordinates privacy educational trainings to ensure that Board of Directors, employees, FDRs, and other individuals as applicable about the privacy policies and procedures, notice of privacy practices and other applicable statutory and regulatory requirements; |
| þ | Participates in the development, implementation, and ongoing compliance monitoring of business associate to ensure all privacy concerns, requirements and responsibilities are addressed; |
| þ | Works cooperatively with appropriate senior staff to review, amend and restrict access to protected health information as appropriate; |
| þ | Generate quality reports regarding privacy initiatives; |
| þ | Establishes and administers a process for receiving, documenting, tracking, investigating and taking action on all complaints concerning the organization’s privacy P&Ps; |
| þ | Ensures compliance with privacy practices and consistent application of sanctions for failure to comply with privacy policies for all individuals in the workforce, extended workforce and for business associates, in cooperation with Human Resources, Security Officer and Legal Counsel; |
| þ | Initiates, facilitates and promotes activities to ▇▇▇▇▇▇ information privacy awareness within the organization and business associates; |
| þ | Works with all personnel involved with any aspect of release of protected health information (PHI) to ensure full coordination and compliance; |
| þ | Maintains current knowledge of federal, state and local privacy laws and accreditation standards, and monitors advancements in information privacy technologies to ensure adaptation and compliance; |
| þ | Develop and implement methods and programs that encourage managers and employees to report noncompliance issues without fear of retaliation, discrimination or intimidation; |
12| Compliance Program
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
| þ | Maintaining documentation for each report of potential noncompliance received from any source, through any reporting method (e.g., helpline, Compliance email, or in-person); |
| þ | Review Business Associate Agreements and other documents to ensure compliance with privacy requirements. |
| þ | Report privacy and security breaches to CMS, ASES, OCR its designee or law enforcement. |
The Board of Directors members of TSS/TSA exercise reasonable oversight with respect to the implementation and effectiveness of the Compliance Program. The oversight by the Board of Directors members includes, but is not limited to:
| þ | Approving the Code of Business Conduct and Ethics; |
| þ | Understanding the compliance program structure; |
| þ | Remaining informed about the Compliance Program outcomes, including results of internal and external audits; |
| þ | Remaining informed about governmental compliance enforcement activity such as Notices of Non-Compliance, Warning Letters and/or more formal sanctions; |
| þ | Receiving regularly scheduled, periodic updates from the compliance officer and compliance committee; and |
| þ | Reviewing the results of performance and effectiveness assessments of the compliance program. |
| þ | Provide regular and ad hoc reports on the status of FDR compliance with recommendations to the Executive Compliance Committee. |
The Vendors Management and Oversight Committee (VMOC) undertakes the following responsibilities and duties to support the Compliance Officer and Executive Compliance Committee in their duties of appropriate oversight, including but not limited to:
| þ | Assist with the creation, approval and implementation of the FDR compliance risk |
13| Compliance Program
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
assessment and of the FDR monitoring and auditing work plan and audit results;
| þ | Review of FDR oversight activities results; |
| þ | Review of the FDRs corrective action plans resulting from audits; |
| þ | Assist in the monitoring of the effective implementation of the corrective actions from the FDRs; |
| þ | Ensure that the FDRs has a method for their employees to report potential FWA; |
| þ | Review and address reports of monitoring and auditing of areas in which the FDRs are at risk for program noncompliance or potential FWA and ensuring that corrective action plans are implemented and monitored for effectiveness; and |
| þ | Provide regular and ad hoc reports on the status of FDR compliance with recommendations to the Executive Compliance Committee. |
The following diagram summarize the previous structure:
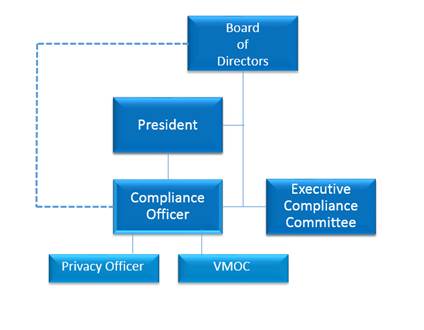
Related to URAC Accreditation, the Board of Directors delegated the Quality Council for oversees the Quality Improvement Program for the Commercial and Medicaid Line of Business. The responsibilities include, but are not limited to:
14| Compliance Program
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
| þ | Oversees physical and mental health care, risk management, enrollee’s access to services, provider services, and complaint and appeal processes, satisfaction with services provided, among others, |
| þ | Provide guidance on quality management priorities and projects, |
| þ | Approves the quality improvement projects to undertake, |
| þ | Allocate resources for quality initiatives, |
| þ | Receive all issues and concerns about the quality of the care of the services rendered by the health plan, |
| þ | Monitors progress in meeting quality improvement goals, |
| þ | Report to the Board of Directors on an annual basis. |
| þ | Review and approval policies and procedures related to URAC Accreditation. |
15| Compliance Program
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Element 3: Effective Training and Education
TSS and TSA establish, implement and provide effective training and education for its employees, (including all senior management, and members of the Board of Directors) as well as contractorsand FDRs.
The training and education occurs at least annually and is part of the orientation for new employees, including Board of Directors members, contractorsand FDRs.
General/Specialized Compliance Trainings
TSS/TSA’s employees, and Board of Directors members and contractors receive General Compliance Training before entering the work area or within 30 days of initial hiring, contracting or appointment, depending of business needs, and annually thereafter.
TSS/TSA provides specialized compliance trainings to ensure that employees are aware of the regulatory requirements (Medicare, Medicaid, Commercial, etc.) related to their job function.
TSS/TSA review and update the compliance trainings as necessary, whenever there are material changes in regulations, policy or guidance, and at least annually. The following are examples of topics the general compliance training program communicate:
| þ | A description of the Compliance Program, including a review of compliance policies and procedures, the Code of Business Conduct and Ethics, and our commitment to business ethics, confidentiality and compliance with all Commercial/Medicare/Medicaid and other regulatory requirements; |
| þ | An overview of how to ask compliance questions, request compliance clarification or report suspected or detected noncompliance. Trainings emphasize confidentiality, anonymity, and non-retaliation for compliance related questions or reports of suspected or detected noncompliance or potential Fraud, Waste and Abuse (FWA); |
16| Compliance Program
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
| þ | The requirement to report to the sponsor actual or suspected Commercial/Medicare/Medicaid or other program noncompliance or potential FWA; |
| þ | Examples of reportable noncompliance that an employee might observe; |
| þ | A review of the disciplinary guidelines for non-compliant or fraudulent behavior and communicate how such behavior can result in mandatory retraining and may result in disciplinary action, including possible termination when such behavior is serious or repeated or when knowledge of a possible violation is not reported; |
| þ | Attendance and participation in compliance and FWA training programs as a condition of continued employment and a criterion to be included in employee evaluations; |
| þ | A review of policies related to contracting with the government, such as the laws addressing gifts and gratuities for Government employees; |
| þ | A review of potential conflicts of interest and the sponsor’s system for disclosure of conflicts of interest; |
| þ | An overview of HIPAA/HITECH, the CMS Data Use Agreement (if applicable), and the importance of maintaining the confidentiality of personal health information; |
| þ | An overview of the monitoring and auditing process; and |
| þ | A review of the laws that govern employee conduct in the Commercial/Medicare/Medicaid programs. |
| þ | Mental Health Parity Addiction and Equity Act |
Additional, specialized or refresher training may be provided on issues posing FWA risks and URAC Accreditation standards, based on the individual’s job function.
Training may be provided upon appointment to a new job function; when requirements change; when employees are found to be noncompliant; as a corrective action to address a noncompliance issue; and when an employee works in an area implicated in past FWA.
FWA training include, but not limited to, the following topics:
| þ | Laws and regulations related to MA and Part D FWA (i.e., False Claims Act, Anti-Kickback statute, HIPAA/HITECH, etc.); |
| þ | Obligations of FDRs to have appropriate policies and procedures to address FWA; |
17| Compliance Program
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
| þ | Processes for TSA employees and FDR employees to report suspected FWA to TSA (or, as to FDR employees, either to the sponsor directly or to their employers who then must report it to TSA); |
| þ | Protections for TSA and FDR employees who report suspected FWA; and |
| þ | Types of FWA that can occur in the TSA settings and FDR employees work. |
For more information, related to employees training and education refer to the policy and procedure: COMP-003 Effective Training and Education.
TSS/TSA communicates general compliance information to FDRs. TSA distributes the Code of Business Conduct and Ethics and compliance policies and procedures to FDRs’ and have oversight processed implemented to ensure its distribution to the FDRs employees.
TSS/TSA maintains training records for a period of 10 years of the time, attendance, topic, certificates of completion (if applicable), and test scores. TSS/TSA requires the FDRs to maintain records of the training of the FDRs’ employees. For more information, related to FDRs training and education refer to the policy and procedure: COMP-003-1 FDRs Effective Training and Education.
18| Compliance Program
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Element 4: Effective Lines of Communication
Triple-S establishes and implements effective lines of communication, ensuring confidentiality between the compliance officer, members of the Executive Compliance Committee, our employees, Board of Directors, and FDRs. The lines of communication are accessible to all and allow compliance issues to be reported including a method for anonymous and confidential good faith reporting of potential compliance issues as they are identified.
TSS/TSA implemented an effective way to communicate information from the Compliance Officer to others, including the Compliance Officer’s name, office location and contact information; laws, regulations and guidance for employees, Board of Directors and FDRs. Communications from the Compliance Officer include but is not limited to, statutory, regulatory, and sub-regulatory changes (e.g., HPMS memos); and changes to policies and procedures and Code of Business Conduct and Ethics. TSS/TSA use different methods to timely communicate information to others, including physical postings of information, e-mail distributions, internal websites, and individual and group meetings with the Compliance Officer.
TSS/TSA requires to all employees, members of the Board, and FDR’s to report compliance concerns and suspected or actual violations related to the Compliance Program through the following effective lines of communication:
| ü | Immediate supervisor or manager |
| ü | Compliance Officer, Privacy Officer, or any member of the Compliance Department |
19| Compliance Program
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
| · | Compliance Officer: ▇▇▇▇▇▇▇▇@▇▇▇▇▇▇▇▇▇▇▇▇.▇▇▇ |
| · | Privacy Officer: ▇▇▇▇▇▇▇▇@▇▇▇▇▇▇▇▇▇▇▇▇.▇▇▇ |
| · | Compliance Department Email: ▇▇▇▇▇▇▇▇▇▇▇▇▇@▇▇▇▇▇▇▇▇▇▇▇▇.▇▇▇ |
| ü | Ethics Point (available 24 hours/7 days): Helpline: 1.866.384.4277 / ▇▇▇.▇▇▇▇▇▇▇▇▇▇▇.▇▇▇ |
| ü | The Human Resources Department |
| ü | Vice-President of the Office of Internal Audit and the General Counsel of Triple-S Management Corporation or their designees. |
| · | Office of Internal Audit:▇▇▇▇▇▇▇@▇▇▇▇▇.▇▇▇ |
| · | Corporate Ethics and Compliance Director: ▇▇▇▇▇▇▇▇@▇▇▇▇▇.▇▇▇ |
Triple-S have a system in place to receive, record, respond to and track compliance questions or reports of suspected or detected noncompliance or potential FWA from employees, members of the Board of Directors, enrollees and FDRs and their employees. Reporting systems maintain confidentiality, to the greatest extent possible, allow anonymity if desired and emphasize Triple-S policy of non-intimidation, non-discrimination and non-retaliation for good faith reporting of compliance concerns and participation in the compliance program. TSS/TSA allows their FDRs to have their own reporting mechanism with an important emphasis that reports related or that impacts TSS/TSA must be informed to TSS/TSA.
Triple-S have a no-tolerance policy for retaliation or retribution against any employee or FDR who in good faith reports suspected FWA. This no-tolerance policy is widely publicized, and enforced. Employees and FDRs are notified that they are protected from retaliation for False Claims Act complaints, as well as any other applicable anti-retaliation protections. The methods available for reporting compliance or FWA concerns and the non-retaliation policy are publicized throughout the TSS/TSA or FDR’s facilities. TSS/TSA may use different mechanisms to publicize this information such use of posters, table tents, mouse pads, key cards and other prominent displays.
20| Compliance Program
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
When a suspected compliance issue is reported, TSS/TSA provide the complainant with information regarding expectations of a timely response, confidentiality, non-retaliation, non-intimidation, and non-discrimination and progress reports.
TSS/TSA educate their enrollees and providers about identification and reporting of potential FWA. Education methods may include flyers, letters, pamphlets that can be included in mailings to enrollees, such as enrollment packages, Explanation of Benefits (“EOB”), and information published on the TSS/TSA’s website. For more information, refer to the policy and procedure COMP-004 Effective Lines of Communication.
Element 5: Disciplinary Standards
TSS and TSA has well-publicized disciplinary standards through the implementation of the Code of Business Conduct and Ethics and compliance policies and procedures, which encourage good faith participation in the Compliance Program. These standards must include policies that articulate expectations for reporting actual or potential, fraud, waste and abuse, HIPAA and compliance issues and assist in their resolution; identify noncompliance or unethical behavior; and provide for timely, consistent, and effective enforcement of the standards when non-compliance or unethical behavior is determined.
TSS and TSA establishes and implements disciplinary policies and procedures that reflect clear and specific disciplinary standards. The disciplinary policies describe expectations for the reporting of compliance issues including noncompliant, unethical or illegal behavior, that employees participate in required training, and the expectations for assisting in the resolution of reported compliance issues. In addition, the disciplinary policies identify noncompliant, unethical or illegal behavior, through examples of misconduct that employees might encounter in their jobs. Further, the policies provide for timely, consistent and effective enforcement of the standards when noncompliant or unethical behavior is found. Finally, the disciplinary actions are appropriate to the seriousness of the violation.
21| Compliance Program
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
To encourage good faith participation in this Program, TSS and TSA publicize disciplinary standards for employees, providers, enrollees, contractors and FDRs (as applicable). The standards include the duty and expectation to report issues or concerns. The following are examples of the types of publication mechanisms that TSS and TSA could use:
| ü | Newsletters; |
| ü | Regular presentations at department staff meetings; |
| ü | Communications with FDRs; |
| ü | General compliance training; |
| ü | Intranet site; |
| ü | TSA and TSS Internet site; |
| ü | Provider Portal; |
| ü | Annual compliance awareness campaign |
| ü | Posters prominently displayed throughout employee work and break areas; and |
| ü | Lunch room table tents. |
Triple-S applies disciplinary actions on a timely manner and consistent with the seriousness of the violation. The Compliance Officer or his/her designated and Human Resources Department work in collaboration with the appropriate supervisor or manager in determining disciplinary action related to an instances of regulatory noncompliance. Example of disciplinary action that may be taken in accordance with the measure and scope of the noncompliance event include, but are not limited to:
| · | Retraining |
| · | Verbal memorandum |
| · | Written memorandum |
| · | Suspension |
| · | Termination |
Disciplinary actions records are maintained for a period of 10 years for all compliance
22| Compliance Program
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
violation disciplinary actions, capturing the date the violation was reported, a description of the violation, date of investigation, summary of findings, disciplinary action taken and the date it was taken. TSS/TSA reviews these records on a periodic basis to ensure that disciplinary actions are appropriate to the seriousness of the violation, fairly and consistently administered and imposed within a reasonable timeframe. Compliance in one of the competences on the employee’s performance evaluation. Disciplinary Action taken are reported to the Executive Compliance Committee on a quarterly basis. For more information, refer to the policy and procedure COMP-005 Well-Publicized Disciplinary Standards.
Element 6: Effective System for Routine Monitoring and Identification of Compliance Risks
TSS and TSA establishes and implements an effective system for routine monitoring and identification of compliance risks. The system include internal monitoring and audits and, as appropriate, external audits, to evaluate the TSS/TSA’s operations, including FDRs’, compliance with regulatory requirements and the overall effectiveness of this Program.
TSS/TSA conducts monitoring and auditing to test and confirm compliance with Centers for Medicare and Medicaid Services (CMS), Office of Personnel Management (OPM), Office of Insurance Commissioner (OIC) and ASES regulations, sub-regulatory guidance, contractual agreements, and applicable Federal and State laws, including Mental Health Parity Law, as pertains specifically for our mental health and substance use disorder services, accreditation requirements, as well as internal policies and procedures to protect against program noncompliance and potential FWA.
23| Compliance Program
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
TSS/TSA develops a monitoring and auditing work plan that addresses the risks associated with the Commercial, Medicaid and Medicare Parts C and D benefits. The monitoring and auditing work plan is coordinated, overseen and/or executed by the Compliance Officer, assisted if desired by the Compliance Department staff and/or the Executive Compliance Committee. The Compliance Officer or his/her designee provide updates on monitoring and auditing results to the Executive Compliance Committee, the President, Senior Leadership and the Board of Directors. For more information refer to the policies and procedures COMP-006 Internal Compliance Audit and Monitoring Process; COMP-006-1 Delegation Oversight and COMP-006-3 Compliance with Mental Health Parity Law.
TSS/TSA establishes and implements policies and procedures to conduct the annual compliance and FWA risk assessments. The risk assessments takes into account all business operational areas and First tiers. Each operational area and/or first tier are assessed for the types and levels of risks they presents to the Commercial, Medicaid and Medicare program and to TSS/TSA. The factors that may be considered in determining the risks associated with each department or First Tiers include, but are not limited to:
| ü | Size of the department / Size of the first-tier entity; |
| ü | Complexity of transactions / Complexity of process delegated and decision making authority; |
| ü | Background experience of personnel |
| ü | Implementation of policies, procedures and internal controls |
| ü | Adequacy of equipment, software or applications |
| ü | Amount of training that has taken place; |
| ü | Past Compliance issues and budget. |
Risks identified by the risk assessment are ranked to determine which risk areas/entities have the greatest impact on TSS/TSA, and to prioritize the monitoring and auditing strategy accordingly. Ongoing review of potential risks of noncompliance
24| Compliance Program
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
and FWA and a periodic re-evaluation of the accuracy of the TSS/TSA risk assessment is conducted as risks change and evolve with changes in the law, regulations, ASES and CMS, OIG requirements and operational matters. Risk areas identified through CMS audits and oversight, as well as through the TSA’s monitoring, audits and investigations are priority risks. The results of the risk assessment inform the development of the monitoring and audit work plans. For more information, refer to the policy and procedure COMP-006-2 Risk Assessment.
Once the risk assessment is completed, a monitoring and auditing work plan is developed based. The work plans includes a process for responding to all monitoring and auditing results and for conducting follow-up reviews of areas found to be non-compliant to determine if the implemented corrective actions have fully addressed the underlying problems. The work plans include a schedule that lists all of the monitoring and auditing activities for the calendar year for departments and first tiers.
Corrective action and follow-up are overseen by the Compliance Officer and assisted by the compliance department staff and include actions such as reporting findings to ASES, CMS or to the NBI MEDICs, if necessary.
TSS/TSA uses a variety of audit approaches, including but not limited to: desk and/or on-site audits, including, as appropriate and as permitted by contractual agreements, unannounced audits or “spot checks” when developing the work plans. TSS/TSA prepares a standard audit report that includes items such as:
| ü | Audit Objectives; |
| ü | Scope and Methodology; |
| ü | Findings: |
| · | Condition; |
| · | Criteria; |
| · | Cause; |
| · | Effect; and |
| ü | Recommendations |
25| Compliance Program
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
The effectiveness of this Program is measured through an annual audit and results are shared with the Board of Directors.
TSS/TSA conducts monitoring and auditing activities of the first tier entities to ensure that they are in compliance with all applicable laws and regulations, and to ensure that the first tier entities are monitoring the compliance of the entities with which they contract (the sponsors’ “downstream” entities). Monitoring activities are also conducted to related entities to ensure they are compliant with all applicable laws and regulations.
When corrective action is needed, TSS/TSA conduct validation procedures to ensure that corrective actions are taken by the entity. TSS/TSA track and document compliance efforts. In addition to formal audits and monitoring, TSS/TSA uses the Compliance Scorecard and self-assessments that show the extent to which operational areas and FDRs are meeting compliance goals. Results are shared with employees, Senior Management, Executive Compliance Committee and Board of Directors members, as applicable.
Triple-S reviews the DHHS OIG List of Excluded Individuals and Entities (LEIE list) and the GSA Excluded Parties Lists System (EPLS) prior to the hiring or contracting of any new employee, temporary employee, volunteer, consultant, Board of Directors members, or FDR, and monthly thereafter, to ensure that none of these persons or entities are excluded or become excluded from participation in federal programs. Monthly screening is essential to prevent inappropriate payment to providers, pharmacies, and other entities that have been added to exclusions lists since the last time the list was checked. After entities are initially screened against the entire LEIE and EPLS at the time of hire or contracting, Triple-S only review the LEIE supplement file provided each month, which lists the entities added to the list that month, and review the EPLS updates provided during the specified monthly time frame.
26| Compliance Program
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
TSS/TSA performs effective monitoring in order to prevent and detect FWA including data analysis. Baselines data are established to recognize unusual trends, changes in drug utilization over time, physician referral or prescription patterns, and plan formulary composition over time. This activities are designed to:
| ü | Reduce or eliminate Medicaid and Medicare Parts C and D benefit costs due to FWA; |
| ü | Reduce or eliminate fraudulent or abusive claims paid for with federal dollars; |
| ü | Prevent illegal activities; |
| ü | Identify enrollees with overutilization issues; |
| ü | Identify and recommend providers for exclusion, including those who have defrauded or abused the system to the NBI MEDIC and/or law enforcement; |
| ü | Refer suspected, detected or reported cases of illegal drug activity, including drug diversion, to the NBI MEDIC and/or law enforcement and conducting case development and support activities for NBI MEDIC and law enforcement investigations; and |
| ü | Assist law enforcement by providing information needed to develop successful prosecutions. |
TSS/TSA allow access to any auditor acting on behalf of the state and federal government or CMS to conduct an on-site audit. On-site audits require a thorough review of required documentation as well as interviews of the staff. TSS/TSA and the FDRs provide records to ASES, CMS or its designee. TSS/TSA and the FDRs are committed to cooperate with regulatory agencies and contractors, such as the NBI MEDICs. This cooperation includes providing CMS and/or the NBI MEDICs or other contractor’s access to all requested records associated in any manner with the Medicare Parts C or D program.
27| Compliance Program
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Element 7: System for Prompt Response to Compliance Issues
TSS/TSA establishes and implements procedures and a system to promptly respond to compliance issues as they are raised, investigates potential compliance problems as identified in the course of self-evaluations and audits, corrects such problems promptly
28| Compliance Program
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
and thoroughly to reduce the potential for recurrence, and ensures ongoing compliance with agencies regulatory requirements.
The Compliance Department conducts a timely and well-documented reasonable inquiry into any compliance incident or issue involving potential Medicare, Medicaid and Commercial noncompliance or potential FWA.
Noncompliance and FWA may be discovered through the lines of communication, enrollee complaint, during routine monitoring or self-evaluation, an audit, or by regulatory authorities. Regardless of how the noncompliance or FWA is identified, the Compliance Department initiates an inquiry as quickly as possible, but not later than two (2) weeks after the date the potential noncompliance or potential FWA incident was identified.
The inquiry includes a preliminary investigation of the matter by the Compliance Officer or his/her delegated. If the issue appears to involve potential FWA and the Compliance Department does not have either the time or the resources to investigate the potential FWA in a timely manner, it should refer the matter to the NBI-MEDIC within thirty (30) days of the date the potential fraud or abuse is identified so that the potentially fraudulent or abusive activity does not continue.
The Compliance Department monitors FWA and Medicare, Medicaid and Commercial noncompliance. When serious noncompliance or waste occurs, the Compliance Officer or his/her designee refers the matter to the applicable regulatory agencies. When potential fraudulent or abusive activity is identified for Medicare Advantage line of business, the Compliance Officer or his/her designee refers the matter to NBI MEDIC.
Corrective actions are implemented by the operational areas of TSS/TSA and the FDRs in response to potential noncompliance or potential FWA and are designed to correct the underlying problem that results in program violations and to prevent future noncompliance. As part of the evaluation of the potential noncompliance or potential FWA, a root cause analysis is performed to determine what caused or allowed the
29| Compliance Program
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FWA, noncompliance or deficiency to occur. The corrective actions are tailored to address the particular FWA, noncompliance or deficiency identified, and includes timeframes for specific achievements.
Failure of the FDRs to effectively implement appropriate corrective actions may result in contract termination. The Compliance Department conducts monitoring activities during and after the implementation of the corrective actions to ensure that they are effective. The Compliance Department performs a thorough documentation of all the elements, including ramifications of the corrective actions that address noncompliance or FWA committed by the TSS’s/TSA’s employees or the FDRs. Enforcement of correction are implemented through disciplinary measures, including employment or contract termination, if warranted.
The Compliance Department conducts self-report of potential FWA discovered at the plan level, and potential fraud and abuse by FDRs, as well as significant waste and significant incidents of Commercial, Medicare/Medicaid program noncompliance.
The Compliance Department conducts investigation of potential FWA activity to make a determination whether potential FWA has occurred. Investigations of potential FWA are concluded within a reasonable time period after the activity is discovered. If after conducting a reasonable inquiry, the Audit and Investigation Unit determines that potential FWA related to the Medicaid and Medicare Parts C or D programs has occurred, the matter is referred to the NBI MEDIC promptly. The Audit and Investigation Unit also refer potential FWA at the FDR levels to the NBI MEDIC so that the NBI MEDIC can help identify and address any scams or schemes.
The Compliance Officer or his/her designee reports potentially fraudulent conduct to government authorities such as the Office of Inspector General (through the OIG’s Provider Self-Disclosure Protocol) or the Department of Justice.
30| Compliance Program
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
When the Compliance Officer discovers an incident of significant Medicare program noncompliance, it reports the incident to CMS as soon as possible after its discovery. The Compliance Officer or his/her designee refers cases involving potential fraud or abuse that meet any of the following criteria to the NBI MEDIC:
| · | Suspected, detected or reported criminal, civil, or administrative law violations; |
| · | Allegations that extend beyond the Parts C and D plans, involving multiple health plans, multiple states, or widespread schemes; |
| · | Allegations involving known patterns of fraud; |
| · | Pattern of fraud or abuse threatening the life or wellbeing of beneficiaries; and |
| · | Scheme with large financial risk to the Medicare Program or beneficiaries. |
When a Fraud Alert is received, TSS/TSA and the corresponding FDR conduct a review of its contractual agreements with the identified parties. Review of past paid claims from entities identified in a fraud alert is conducted to identify claims that may be or may have been part of an alleged fraud scheme and remove them from their sets of prescription drug event data submissions.
TSS/TSA maintains files for a period of 10 years on both in-network and out-of-network providers who have been the subject of complaints, investigations, violations, and prosecutions. This includes enrollee complaints, NBI MEDIC investigations, OIG and/or DOJ investigations, US Attorney prosecution, and any other civil, criminal, or administrative action for violations of Federal health care program requirements. Files that contain documented warnings (i.e., fraud alerts) and educational contacts, the results of previous investigations, and copies of complaints resulting in investigations are maintained. Triple -S comply with requests by law enforcement, CMS and CMS’ designee regarding monitoring of providers within the Triple -S network that CMS has identified as potentially abusive or fraudulent.
31| Compliance Program
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Laws and Regulations
The following are laws and regulation that was consider in this Program:
| · | Title XVIII of the Social Security Act |
| · | Medicare regulations governing Parts C and D found at 42 C.F.R. §§ 422 and 423 respectively |
| · | Patient Protection and Affordable Care Act (Pub. L. ▇▇. ▇▇▇ -▇▇▇, ▇▇▇ ▇▇▇▇. 119) |
| · | Health Insurance Portability and Accountability Act (HIPAA) (Public Law 104-191) |
| · | False Claims Acts (31 U.S.C. §§ 3729-3733) |
| · | Federal Criminal False Claims Statutes (18 U.S.C. §§ 287,1001) |
| · | Anti-Kickback Statute (42 U.S.C. § 1320a-7b(b)) |
| · | The Beneficiary Inducement Statute (42 U.S.C. § 1320a-7a(a)(5)) |
| · | Civil monetary penalties of the Social Security Act (42 U.S.C. § 1395w-27 (g)) |
| · | Physician Self-Referral (“▇▇▇▇▇”) Statute (42 U.S.C. § 1395nn) |
| · | Fraud and Abuse, Privacy and Security Provisions of the Health Insurance Portability and Accountability Act, as modified by HITECH Act |
| · | Prohibitions against employing or contracting with persons or entities that have been excluded from doing business with the Federal Government (42 U.S.C.§1395w-27(g)(1)(G) |
| · | Fraud Enforcement and Recovery Act of 2009 |
| · | All sub-regulatory guidance produced by CMS and HHS such as manuals, training materials, HPMS memos, and guides |
| · | Final Rule of the Section 1557 of the Patient Protection and Affordable Care Act (ACA) of 2010 (45 CFR § 92.1) |
| · | Mental Health Parity and Addiction Equity Act |
| · | URAC Health Plan Accreditation Guideline Version 7.2: |
| o | Core 3 - |
| o | Core 4 – Regulatory Compliance |
32| Compliance Program
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
| o | Core 6 thru 9 – Oversight of Delegated Activities [P-QM 1] [P-QM 3(a)] [P-QM 3(e)] [P-QM 3(d)] |
| o | Core 16 – Confidentiality of Individually-Identifiable Health Information |
| o | Core 27 – Staff Training Program |
| o | P-CP 1 – Compliance Program: Internal Controls |
Definitions
ASES: Administración de Seguros de Salud de Puerto Rico (the Puerto Rico Health Insurance Administration, “PRHIA”, in its English acronym), the entity of the Government of Puerto Rico responsible for oversight of the Government Health Plan (GHP) Program and the Medicare Platino Program, or its Agent.
DHHS is the Department of Health and Human Services. CMS is the agency within DHHS that administers the Medicare program.
FDRs: First Tier, Downstream and Related Entities
| a) | First Tier Entity: Is an independent entity that enters into a written contract with the Corporation, acceptable for CMS, to provide administrative services or health care services to a beneficiary. |
| b) | Downstream Entity: It is a party who enters into a written agreement with the Delegated Entity, which is acceptable for CMS to provide services. The agreement falls below the level of agreement that reaches Triple-S with a Delegated Entity (First Tear Entity). |
| c) | Related Entity: Any entity that is affiliated with the Corporation under a same common control, in addition: 1) performs some of the activities of the Corporation by contract or delegation; (2) it provides services to the beneficiaries through a written contract; or (3) rents real property or sell materials to the Corporation at a cost that exceeds $2,500 for the contract period. |
| d) | Delegated Entity: Entity to which an activity is transferred through a contract. A Delegated Entity may be a first tear entity (contractor), a downstream entity (subcontractor) or a related entity. Delegated entities are commercial entities, not individuals. |
33| Compliance Program
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Fraud, Waste and Abuse (FWA):
| a) | Fraud: is knowingly and willfully executing, or attempting to execute, a scheme or artifice to defraud any health care benefit program or to obtain (by means of false or fraudulent pretenses, representations, or promises) any of the money or property owned by, or under the custody or control of, any health care benefit program. 18 U.S.C. §1347. |
| b) | Waste: is the overutilization of services, or other practices that, directly or indirectly, result in unnecessary costs to the Medicare program. Waste is generally not considered to be caused by criminally negligent actions but rather the misuse of resources. |
| c) | Abuse: includes actions that may, directly or indirectly, result in: unnecessary costs to the Medicare/Medicaid Program, improper payment, payment for services that fail to meet professionally recognized standards of care, or services that are medically unnecessary. Abuse involves payment for items or services when there is no legal entitlement to that payment and the provider has not knowingly and/or intentionally misrepresented facts to obtain payment. Abuse cannot be differentiated categorically from fraud, because the distinction between “fraud” and “abuse” depends on specific facts and circumstances, intent and prior knowledge, and available evidence, among other factors. |
GSA: General Services Administration is an independent agency of the United States government, established in 1949 to help manage and support the basic functioning of federal agencies. The GSA supplies products and communications for U.S. government offices, provides transportation and office space to federal employees, and develops government-wide cost-minimizing policies, among other management tasks.
HIPAA: (Public Law 104-191, as amended) The Health Insurance Portability and Accountability Act of 1996, is federal legislation approved by Congress regulating the continuity and portability of health plans, mandating the adoption and implementation of administrative simplification standards to prevents, fraud, waste and/or abuse, improve
34| Compliance Program
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
health plan overall operations and guarantee the privacy, confidentiality and security of individually identifiable health information, among others requirements.
HITECH: The Health Information Technology for Economic and Clinical Health Act (2009). Provisions of this act expanded HIPAA regulations to include mandatory data breach notifications, heightened enforcement, increased penalties and expanded patient rights.
HHS-OIG: is the Office of Inspector General within the U.S Department of Health and Human Services (DHHS). The HHS OIG is dedicated to combating fraud, waste and abuse and to improving the efficiency of HHS programs. A majority of OIG's resources goes toward the oversight of Medicare and Medicaid programs.
Health Plan Management System (HPMS): is a CMS web-enabled information system that serves a critical role in the ongoing operations of the Medicare Advantage (MA), Part D, and Accountable Care Organization (ACO) programs.
NBI-MEDIC: Health Integrity is the Medicare Part C and Part D program integrity contractor for the Centers for Medicare & Medicaid Services (CMS) under the National Benefit Integrity Medicare Drug Integrity Contract (NBI MEDIC). The purpose of the NBI MEDIC is to detect and prevent fraud, waste and abuse in the Part C (Medicare Advantage) and Part D (Prescription Drug Coverage) programs on a national level.
Office of the Commissioner of Insurance of Puerto Rico (OCI): Regulator of the insurance business in the Commonwealth of Puerto Rico. The Office of the Commissioner of Insurance is an entity that reports directly to the Governor of Puerto Rico.
OIG: is the Office of the Inspector General within DHHS. The Inspector General is responsible for audits, evaluations, investigations, and law enforcement efforts relating to DHHS programs and operations, including the Medicare program.
35| Compliance Program
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Office of Personnel Management (OPM): The Office of Personnel Management manages the civil service of the federal government, coordinates recruiting of new government employees, and manages their health insurance and retirement benefits programs.
Protected Health Information (PHI): Information transmitted through any means of communication (paper, electronic or verbal) that identifies a specific individual. The elements that identify and represent an individual's protected health information are:
| a) | Name |
| b) | Any reference to a geographical division smaller than a State, including street address, city, county, precinct, zip code or their equivalents. |
| c) | Any information on dates directly related to the individual, including birth date, subscription or start date in the plan, discharge date or cancellation, date of death, any over 89 years reference to age, and any information or reference to the indicative dates of that age. |
| d) | Phone number, fax, e-mail addresses |
| e) | Social Security Number |
| f) | Medical Record Number |
| g) | Beneficiary health plan number |
| h) | Account numbers |
| i) | License number, license plate, permits, tags |
| j) | Identification or medical equipment serial number |
| k) | Biometric identifiers, including voice tests or fingerprints |
| l) | Images of the individual face photographs |
| m) | Any other number, code or characteristic that is unique in the identification of the individual or that could lead to the identification of the individual |
The Centers for Medicare and Medicaid Services (CMS): The federal agency that runs the Medicare program. In addition, CMS works with the States to run the Medicaid program. CMS works to make sure that the beneficiaries in these programs are able to get high quality health care.
36| Compliance Program
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Contact Us
This Compliance Program is published in Compliance 360, if you have any questions or concerns related to this Program and/or if you want to report any situation of noncompliance, fraud, waste and/or abuse, you can contact our Compliance Department through:

▇▇▇▇▇▇▇▇▇▇▇▇▇@▇▇▇▇▇▇▇▇▇▇▇▇.▇▇▇
37| Compliance Program
Schedule J6
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
| I. | Purpose: |
The purpose of this policy is to establish processes to ensure the organization: 1) develops criteria to perform an assessment of potential contractors prior to delegation of functions, 2) follows such criteria to approve contractors, 3) enters into written agreements that includes all URAC and other regulatory agencies requirements, and 4) establishes and implements an oversight mechanism for delegated functions.
| II. | Scope: |
Regular employees, temporary personnel and contractors.
| III. | Policy: |
Delegated Entities are independent contractors to whom we assign by contract certain operational activities in which they have developed expertise and have achieved operational efficiencies. Even if we delegate certain activities of our operation to these entities, we are responsible to policyholders and regulators regarding compliance with laws and regulations applicable to the functions delegated to such entities, as well as the continuity and quality of the services that they provide. For this reason, we have the duty to continually ensure the integrity and competence of the Delegated Entities and their compliance with the laws and regulations applicable to the functions that were delegated to them. Triple-S as an insurer has the final responsibility for compliance with the terms and conditions of its contract with the Center for Medicare and Medicaid Services (CMS), the Office of Personnel Management (OPM); the Puerto Rico Health Insurance Administration (ASES), the Office of the Insurance Commissioner (OCS) and any other regulator.
Therefore, for each Delegated Entity, the Corporation has appointed a contract administrator so as to maintain a continuous monitoring to the Delegated Entity throughout the year. This monitoring consists of periodic interactions with Delegated Entities, as well as review and follow-up of performance indicators, their policies and operational procedures, meetings, phone calls, emails, educational workshops, audit reports, among others.
2017 Triple - S Policy and Procedure Template. Hardcopies of this document are considered uncontrolled, for the latest version please refer to Compliance 360 or contact Compliance Department
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
 |
Policy No.: TSS-CE-001 | Page 2 of 11 |
| Effective Date:09/01/2016 | ||
| Approval Date:09/07/2017 | ||
| Department: Compliance | ||
| Policy Name: Contracting and monitoring of Delegated Entities | ||
The delegation oversight authority shall conduct a documented review, no less frequently than annually, of the contractor’s written policies and documented procedures to assure continued compliance and capacity to comply with the terms of the delegation agreement.
Note: All the delegations are subject to approved policies, the resolutions of the Board of Directors, business strategy plans and current budget.
This policy/procedure will govern everything related to the contracting and monitoring of the Delegated Entities.
| IV. | Definitions: |
| 1. | Criteria: A set of standards, guidelines or protocols used by the Corporation to govern its processes. The criteria should: be in writing, be based on professional practice and the applicable literature, to be applied consistently; and subject to review at least once a year. |
| 2. | Delegation: The process by which an organization contracts with or otherwise arranges for another entity to perform functions and to assume certain responsibilities on behalf of the organization, while the organization retains final authority to provide oversight to the delegate. The Corporation has to be specific as to the parts of the function that are subject to delegation. |
| 3. | Delegated Entity: Entity to which an activity is transferred through a contract. A Delegated Entity may be a first tear entity (contractor), a downstream entity (subcontractor) or a related entity. Delegated entities are commercial entities, not individuals. |
| 4. | Downstream Entity (Subcontractor): It is a party who enters into a written agreement with the Delegated Entity, which is acceptable for CMS to provide services. The agreement falls below the level of agreement that reaches Triple-S with a Delegated Entity (First Tear Entity). |
| 5. | Related Entity: Any entity that is affiliated with the Corporation under a same common control, in addition: 1) performs some of the activities of the Corporation by contract or delegation; (2) it provides services to the beneficiaries through a written contract; or (3) rents real property or sell materials to the Corporation at a cost that exceeds $2,500 for the contract period. FDR: means First Tier, Downstream or Related Entity. |
| 6. | First Tear Entity (Delegated Entity): Is an independent entity that enters into a written contract with the Corporation, acceptable for CMS, to provide administrative services or health services to a beneficiary. |
| 7. | Off-shore: refers to businesses that have operations in any foreign country (not the United States of America, or its Territories, including Puerto Rico) delegated entities have to notify and request the prior written authorization from the Corporation in they have off-shore |
Triple - S Policy and Procedure Template. Hardcopies of this document are considered uncontrolled, for the latest version please refer to Compliance 360 or contact Compliance Department.
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
 |
Policy No.: TSS-CE-001 | Page 3 of 11 |
| Effective Date:09/01/2016 | ||
| Approval Date:09/07/2017 | ||
| Department: Compliance | ||
| Policy Name: Contracting and monitoring of Delegated Entities | ||
operations before the pre-delegation audit or 90 days before the effective date in which they plan to perform a delegated activity off-shore.
| V. | Responsibilities: |
The responsibilities of the Contract Administrator include, but are not limited to, keep a copy of the contract with the Delegated Entity, establish and maintain good relations with the Delegated Entity for which he/she is responsible, act as contact for the solution of problems, monitor the contractor to carry out activities in compliance with the contractual and regulatory standards, corporate policies and procedures, regulatory and accreditation agencies, and best practices as well as producing reports for management related to compliance with the contract. For this, the Administrator must perform the initial pre-delegation assessment and subsequent compliance assessments, at least once a year. The Administrator must keep a record for each contract that he/she administers. Also, the Contract Administrator will monitor financial incentives, if any, to ensure that the quality of the services is not adversely affected.
| VI. | Procedure: |
The contract administrator will work closely with the subject matter experts. These are knowledgeable/experts in a particular area, process or topic subject to delegation. The primary responsibilities of the subject matter experts are:
| 1) | Evaluate reports produced and/or submitted by the delegated entity. |
| 2) | Review policies and procedures related to their areas of expertise from an operational perspective. |
| 3) | Collaborate in the monitoring of the implementation of regulatory changes. |
| 4) | Participate in the performance of pre-delegation, delegation audits and monitoring activities. |
| 5) | Oversee the implementation of corrective actions required based on the monitoring activities and audits. |
The Compliance and Privacy Offices of the various business units will collaborate with the Contract Administrators in those tasks that are understood to be relevant, including but not limited to those related to the requested trainings, regulatory monitoring and follow-up of corrective action plans.
The Vendor Management Oversight Committee (VMOC) will receive quarterly written reports from the Contract Administrators who are responsible for the selected Delegated Entities.
| A. | Activities than can be Delegated |
Below, for illustrative purposes, we present a list of related activities with contracts that we currently have with regulators and that can be delegated:
Triple - S Policy and Procedure Template. Hardcopies of this document are considered uncontrolled, for the latest version please refer to Compliance 360 or contact Compliance Department.
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
 |
Policy No.: TSS-CE-001 | Page 4 of 11 |
| Effective Date:09/01/2016 | ||
| Approval Date:09/07/2017 | ||
| Department: Compliance | ||
| Policy Name: Contracting and monitoring of Delegated Entities | ||
| Affiliations, non-affiliations and membership management | Pharmacy Benefits Manager (PBM) | Applications Processing |
| Clinical quality | Provider Network Management (Mental health, dental and vision) | Grievances, Complaints and Appeals |
| Coordination of benefits | Utilization Management | Claims, processing and adjudication of coverage |
| Licensing and credentials | Rebates negotiation and other price concessions for prescribed medications | Customer Service |
| Confidence Line | Bid preparation | Sales and marketing |
| Affiliation verification |
| B. | Factors to Consider to determine if we have a Delegated Entity |
There are several factors to consider. If you answer in the affirmative all questions below, we are probably facing a Delegated Entity:
| 1) | What function does the entity perform? Refer to the list of activities that can be delegated. |
| 2) | Is the function one that Triple-S must perform in the ordinary course of the business of an insurer, according to the Law, the contract, rules or guidelines of the regulator or accrediting entity? |
| 3) | Does the function that it performs impact policyholders directly? |
| 4) | Is the interaction with the insured, verbal, written or face-to-face? |
| 5) | Does it have access to confidential information of the insured? |
| 6) | Does it have discretion to make decisions in relation to the service that it offers? |
| C. | Criteria for the Selection of a Delegated Entity [Core 6] |
Triple S carefully monitors the activities performed and any responsibilities assumed by another entity whenever those activities are covered under accreditation standards and/or other applicable laws or regulations.
Triple S adheres to the following criteria for approving delegation of activities to a contractor: [Core 6]
Triple - S Policy and Procedure Template. Hardcopies of this document are considered uncontrolled, for the latest version please refer to Compliance 360 or contact Compliance Department.
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
 |
Policy No.: TSS-CE-001 | Page 5 of 11 |
| Effective Date:09/01/2016 | ||
| Approval Date:09/07/2017 | ||
| Department: Compliance | ||
| Policy Name: Contracting and monitoring of Delegated Entities | ||
| 1) | Potential Delegate must demonstrate ability to adhere/comply with URAC Standards (if applicable) and local and federal laws and regulations relevant to the functions that they are being contracted to perform (if applicable). [Core 6] |
| 2) | Potential Delegate must demonstrate that it has adequate resources (e.g., Information Technology/Information Management, Equipment, and Staffing) to implement the functions that they are being contracted to perform. [Core 6] |
| 3) | Potential Delegate must be willing and capable of complying with Triple S delegation oversight activities including Pre-assessment Evaluation, Annual Delegation Reviews and Performance Reporting as delineated in the Triple S Delegation Agreement. [Core 6 & Core 7(b)] |
In addition, the Delegated Entities must comply with the following criteria: [Core 6]
| i. | Good standing with regulatory agencies [Core 6] |
| ii. | Compliance with federal, local and accrediting agencies statutory requirements [Core 6] |
| iii. | Fiscal solvency [Core 6] |
| iv. | Preferably, it should be a company that has an existing accreditation with URAC, NCQA or another entity with national recognition. [Core 6] |
| v. | Approval of the pre-delegation evaluation by the Contract Administrator and the Compliance Officer. [Core 6] |
Note that for purposes of this policy, those business functions covered under the "Health Plan Accreditation" program of URAC that are carried out off-shore are subject to these standards and we have to monitor contractor’s compliance with URAC requirements. Certifications for off-shore activities must be submitted by the contract administrator to the Compliance Officer as part of the pre-delegation process.
| D. | Pre - Evaluation of the Delegated Entity [Core 7(a) & Core 7(b)] |
In order to evaluate a potential delegate’s capacity to meet Triple S delegation approval criteria, a formal review is performed. The pre- assessment includes a review of the potential delegate’s applicable written policies and procedures and other documents to confirm compliance with the delegation criteria, applicable URAC standards (if applicable), and any applicable laws and regulations. [Core 7(a)] The previous evaluation of the capabilities of a possible delegated entity contributes to promote a good working relationship and ensure a quality service to customers. Prior to the
Triple - S Policy and Procedure Template. Hardcopies of this document are considered uncontrolled, for the latest version please refer to Compliance 360 or contact Compliance Department.
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
 |
Policy No.: TSS-CE-001 | Page 6 of 11 |
| Effective Date:09/01/2016 | ||
| Approval Date:09/07/2017 | ||
| Department: Compliance | ||
| Policy Name: Contracting and monitoring of Delegated Entities | ||
contract, the entity shall be evaluated using, at the discretion of the Corporation, one or more of the methods below: [Core 7(b)]
| 1) | Review of written policies and procedures applicable to the delegated function. Once the Delegated Entity is contracted, the Contract Administrator shall perform, as a minimum, an annual review of these policies and procedures and documentation of the way in which the Delegated Entity monitors the quality of the services provided to the Corporation and our customers for related delegated functions. [Core 7(b)] |
| 2) | Validation and documentation of status to operate with primary sources such as the Office of the Inspector General, the System for Awards Merit, Department of State, local Department of Health, Office of Foreign Assets Control, among others. [Core 7(b)] |
| 3) | Evaluation as to the sufficiency, appropriateness and expertise of staff to perform delegated functions [Core 7(b)] |
| 4) | Selection of sample of cases to confirm the capacity of the Delegated Entity to carry out the function [Core 7(b)] |
| 5) | Perform satisfaction surveys [Core 7(b)] |
| 6) | Site visit - An onsite review may be performed if there is indication that further information is necessary to determine appropriateness of delegation. In the case of Delegated Entities who receive insured in their facilities to provide services, this is to ensure that the facilities meet minimum requirements for accessibility, hygiene, number of professionals, signs required by law, waiting times, among others. [Core 7(b)] |
| 7) | Interviews (telephonic or on-site) and exchange of information with potential Delegate’s staff [Core 7(b)] |
| 8) | Screen Prints of potential Delegate’s electronic documentation/record system [Core 7(b)] |
If the potential Delegate is URAC accredited the pre-assessment is not required. Current URAC accreditation will be verified via URAC web site ▇▇▇.▇▇▇▇.▇▇▇.
The result of the assessment must be in writing and signed by the person(s) who performed it.
| E. | Delegation Oversight [Core 9] |
Triple - S Policy and Procedure Template. Hardcopies of this document are considered uncontrolled, for the latest version please refer to Compliance 360 or contact Compliance Department.
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
 |
Policy No.: TSS-CE-001 | Page 7 of 11 |
| Effective Date:09/01/2016 | ||
| Approval Date:09/07/2017 | ||
| Department: Compliance | ||
| Policy Name: Contracting and monitoring of Delegated Entities | ||
After contracting, the Contract Administrator will evaluate the Delegated Entity with the regularity that at his/her own discretion, or the Vendor Management Oversight Committee, deems necessary, but it must be at least an annual assessment. For the annual evaluation the administrator can use the Pre-Delegation Uniform Audit Form.
Triple S will require its delegated vendors to submit periodic reports to the organization regarding the performance of its delegated responsibilities. [Core 9(a) & Core 9(b)] In addition it may include specific reports related to individual incidents. As part of the periodic monitoring, the Corporation shall review, no less frequently than annually, the contractor’s written policies and procedures to assure continued compliance with applicable company standards, contractual agreements, URAC standards, other applicable accrediting organizations standards, and any applicable laws and regulations. [Core 9(a) & Core 9(b)] The contract administrator shall conduct a documented review of the Delegated Entity quality activities related to the delegated functions in order to assure continued compliance with the applicable quality standards of TSS regarding the quality of services provided. [Core 9(a) & Core 9(b)] In cases in which the Delegated Entity does not comply with the quality requirements, the Contract Administrator must request a corrective action plan to improve the level of quality of the services provided under the contract.
In addition, as a part of the annual review, the contract administrator will query the Delegated Entity as to the existence of any financial incentives, either in the agreement between Triple-S and the contractor or within the contractor’s relationships to its staff. Should such financial incentives exist, the contract administrator, after consultation with the medical director if necessary, will document whether such financial incentives compromise the quality of care and service provided to Triple-S members. If the incentives are found to compromise members’ quality of care and service, the medical director shall be alerted and shall work with staff to either terminate the agreement or require the contractor to take steps appropriate to address the risk to members. [Core 9(c)]
| F. | Contracting with the Delegated Entity [Core 8] |
Contracts with the Delegated Entities must comply with Third-Party Contracting Policy parameters. The contract with the Delegated Entity, just like any other contract, must be in writing, signed by the parties and be prospective. In addition, it will specify:
| 1) | The responsibilities delegated to the contractor and the responsibilities held by the Corporation; [Core 8(a)] |
| 2) | The requirement that the services are provided according to the requirements of the Corporation, URAC standards, guidelines of ASES, OPM and CMS; [Core 8(b)] |
Triple - S Policy and Procedure Template. Hardcopies of this document are considered uncontrolled, for the latest version please refer to Compliance 360 or contact Compliance Department.
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
 |
Policy No.: TSS-CE-001 | Page 8 of 11 |
| Effective Date:09/01/2016 | ||
| Approval Date:09/07/2017 | ||
| Department: Compliance | ||
| Policy Name: Contracting and monitoring of Delegated Entities | ||
| 3) | Process that it has implemented to monitor the quality of the services it provides; |
| 4) | The obligation that the Delegated Entity notifies the Corporation any material changes in its ability to perform delegated functions. Examples of material change may include prolonged interruption of services and loss or replacement of senior clinical person. [Core 8(c)] |
| 5) | The discretion of the Corporation to carry out interviews, polls or surveys on the Delegated Entity, as it may consider necessary; [Core 8(d)] |
| 6) | Process by which Triple S evaluates the Delegate’s performance including at least annual Delegation Reviews and semi-annual Performance Reporting. The Delegated Entity has an obligation to submit periodic reports to the Corporation on its performance of the delegated responsibilities; [Core 8(e)] |
| 7) | Remedies or penalties applicable if the Delegated Entity does not fulfill its obligations or does not correct the problems identified within a specific period as required; [Core 8(f)] |
| 8) | The requirement to sign a business associate agreement if as part of the delegated functions there will be exchange of personal insurance, health or financial information of the customers. |
| 9) | Services during transition periods. |
| 10) | The circumstances in which a contractor may subcontract, including the requirement to obtain prior authorization from the Corporation, provided that in the case of subcontracting, it corresponds to the Delegated Entity to submit to the contract administrator periodic reports on the performance of the subcontractor; and [Core 8(g)] |
| 11) | Services sub-delegated by Delegate shall be subject to all terms and conditions of the written delegation agreement between Delegate and Triple S and shall be provided in accordance with URAC standards and other national accrediting standards that the organization is required to meet. [Core 8(h)] |
| 12) | Delegated Entities that are accredited by local or national organizations (URAC, NCQA) must notify the Corporation of any changes in their accreditation. |
| 13) | If the Delegated Entity is accredited by URAC, the Corporation must perform a primary verification in the directory of corporations accredited by URAC provided |
Triple - S Policy and Procedure Template. Hardcopies of this document are considered uncontrolled, for the latest version please refer to Compliance 360 or contact Compliance Department.
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
 |
Policy No.: TSS-CE-001 | Page 9 of 11 |
| Effective Date:09/01/2016 | ||
| Approval Date:09/07/2017 | ||
| Department: Compliance | ||
| Policy Name: Contracting and monitoring of Delegated Entities | ||
in the Internet (▇▇▇.▇▇▇▇.▇▇▇) and provide a copy to demonstrate that the Delegated Entity is accredited.
| 14) | The duty of the Delegated Entity is to keep records of the trainings taken by its employees as a requirement of the contract. As a minimum it should retain copy of the material taught, information of the resource that provided the training, attendance sheets or certifications, mechanism used to assess the effectiveness of the training. |
| 15) | If applicable, include with the Medicare Advantage attachment. |
| G. | Non-Compliance in Performance |
If from the continuous monitoring and reviews came indications that the Delegated Entity cannot meet the contractual requirements of the Corporation, its policies, accreditations and standards, the Contract Administrator should report it to senior management and to the Vendor Management Oversight Committee (VMOC) within a period which shall not exceed 3 working days. In this report the Contract Administrator will indicate the measures required to make the Delegated Entity rectify the deficiencies. The deficiencies associated with regulatory non-compliance should be informed immediately to the Compliance Officers of the different business units, in order to formally request a corrective action plan.
The results of the reviews, monitoring and management determinations will be communicated to the Delegated Entity in writing. Triple SSS will work with the Delegate to address and correct any concerns in its effort to continuously improve processes and provide services. The Delegated Entity shall have ten (10) calendar days to respond to any finding through a corrective action plan indicating:
| o | Plans taken to immediately correct deficiencies that impact Consumer health and safety; |
| o | Plans to correct/revise policies and/or processes that fail to meet other contractual and/or accreditation requirements |
Actions to correct deficiencies will be assessed on a case by case basis and on its merits. As a general rule the corrective action plans must be completed within a period of thirty
(30) days. It is at the discretion of senior management to provide longer periods to those provided in this section. Unjustified failure to comply with these deadlines will be sufficient cause for the Contract Administrator to recommend the termination of the contract to senior management and report it to the VMOC. Reviews or re-audits are conducted as needed to assure corrective actions have been effective in improving previously identified deficiencies.
Triple - S Policy and Procedure Template. Hardcopies of this document are considered uncontrolled, for the latest version please refer to Compliance 360 or contact Compliance Department.
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
 |
Policy No.: TSS-CE-001 | Page 10 of 11 |
| Effective Date:09/01/2016 | ||
| Approval Date:09/07/2017 | ||
| Department: Compliance | ||
| Policy Name: Contracting and monitoring of Delegated Entities | ||
| H. | Management Reports |
Contract Administrators who have Delegated Entities in charge must submit to the VMOC a quarterly report which details the evaluation of the performance of the contractor (may include corrective action plans, and their update, audits results, among others). Quarterly reports will be submitted through this address ▇▇▇▇@▇▇▇▇▇.▇▇▇ on the following dates:
| 1) | First quarter: April 10 |
| 2) | Second quarter: July 10 |
| 3) | Third quarter: October 10 |
| 4) | Fourth quarter: January 10 |
If any of these dates falls on a holiday or weekend, the report will be presented the next working day.
| I. | Document Retention |
Documentation related to the delegation of functions will be retained by the Contract Administrator of the contracting unit while the contract with the Delegated Entity is in force. This documentation shall be recorded in the contractor’s file (paper or electronic) which will contain:
| 1) | Copy of the contract |
| 2) | Copy of the Non-Disclosure Agreement or Business Associate Agreement, if applicable. |
| 3) | Copy of policies and procedures and any other documentation submitted by the Delegated Entity. |
| 4) | Copies of Delegate’s Performance Reports |
| 5) | Copy of the pre-evaluation results and annual delegation review of performance and contractual compliance. |
| 6) | Copy of corrective action plans and follow-up revisions |
| 7) | Written communications between the Corporation and the Delegated Entity |
| 8) | Primary source verification of the status of URAC accreditation certification, if applicable |
Vendor Agreements Quasi-Delegation Involving Protected Health Information
Triple - S Policy and Procedure Template. Hardcopies of this document are considered uncontrolled, for the latest version please refer to Compliance 360 or contact Compliance Department.
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
 |
Policy No.: TSS-CE-001 | Page 11 of 11 |
| Effective Date:09/01/2016 | ||
| Approval Date:09/07/2017 | ||
| Department: Compliance | ||
| Policy Name: Contracting and monitoring of Delegated Entities | ||
For URAC compliance, services provided by a contractor that are not within the scope of URAC Health Plan Accreditation Program, but the relationship between Triple-S and such contractor involves contact by the vendor with protected health information (“PHI”) or individually identifiable health information (“IIHI”) of members of Triple-S, is considered to be Limited Delegation.
Examples of such vendor relationships include document storage and/or shredding and the operation of member translator telephone services, among others.
The requirements for this type of delegation are:
| o | Delegation agreement |
| o | Business Associate Agreement that address the following elements: |
| o | Breach |
| o | Breach notification/remediation/mitigation |
| o | Transferring of data, |
| o | Requirements of training for the BA’s workforce, and |
| o | Proper handling of the PHI |
| VII. | Attachments: None |
| VIII. | References: |
URAC accreditation standards
| Version Control | Effective Date | Approved By (include position name) | Amendment |
| 1 | 09/01/2016 | ▇▇▇▇▇▇ ▇▇▇▇▇▇▇, Compliance and Ethics Director | New document |
| 2 | 09/07/2017 | ▇▇▇▇▇▇ ▇▇▇▇▇▇▇, Compliance and Ethics Director | Annual review, no changes |
Triple - S Policy and Procedure Template. Hardcopies of this document are considered uncontrolled, for the latest version please refer to Compliance 360 or contact Compliance Department.
Schedule J9
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.

IT and Information Security Policies
Approved by and Date
|
Issued by: ▇▇▇▇▇▇ ▇. ▇▇▇▇▇▇▇, Cyber & Information Security Director |
Effective Date: Sep 1, 2016 | |
| Revised by: ▇▇▇▇▇▇ ▇. ▇▇▇▇▇▇▇ | Date Revised: Aug. 11, 2016 | Version: 1.2 |
|
Approved by: ▇▇▇▇ ▇▇▇▇ ▇▇▇▇, Chief Information Officer (CIO) |
||
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Table of Contents
| Acceptable Use | 1 |
| Anti-virus and Anti-Spyware | 10 |
| Asset Management Policy | 14 |
| Backup & Retention | 18 |
| Change Management | 23 |
| Clear Desk & Clear Screen | 27 |
| Data Classification | 30 |
| Data Integrity and Interoperability | 35 |
| Encryption and Cryptographic ▇▇▇▇▇▇▇▇▇▇ | ▇▇ |
| General Information Security | 45 |
| Information Exchange | 49 |
| IT Compliance Management | 54 |
| Network Security | 61 |
| Password Management | 66 |
| Physical and Environmental Security | 70 |
| Remote Access | 75 |
| Removable Device Management | 79 |
| Retention and Disposal | 83 |
| Security Awareness and Training | 88 |
| Security Monitoring Policy | 91 |
| Technical Vulnerability Management Policy | 97 |
| Teleworking | 100 |
| Third Party Services Risk Management | 105 |
| User Access | 107 |
| Information Security Risk Analysis | 113 |
| Business Continuity Management | 117 |
| Patch and Vulnerability Management Policy | 121 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#1 | Page 1 | |||
| Effective Date: 09/01/2016 | |||||
| Approval Date: 09/01/2016 | |||||
| Department: Information Security | Last Review Date: 08/11/2016 | ||||
| Policy Name: | Acceptable Use | ||||
|
Drafted by: ▇▇▇▇ ▇▇▇▇▇▇, IT Compliance Supervisor
|
Reviewed by: ▇▇▇▇▇▇ ▇. ▇▇▇▇▇▇▇, Information & Cyber Security Director |
Approved by: ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, Chief Information Officer
|
|||
| I. | Purpose: |
The purpose of this policy is to establish what is considered acceptable (and also unacceptable) use of computer and related media in TSM in order to reduce unauthorized access to sensible information (i.e. corporate, personnel and EPHI information), security breaches and of course avoid legal issues associated with such breaches.
| II. | Scope: |
This policy applies to all TSM and its subsidiaries employees, temporary workers, contractors, business partners, third party vendors and physical facilities where TSM provides services to its customers.
| III. | Policy: |
This policy help the organization prevent confidentiality and security breaches. The policy also help identify how individually-identifiable health information should be used.
Triple-S Management Corporation (TSM) has developed and adopted the Acceptable Use Policy to provide management with direction, support and protection for inappropriate, unauthorized, and even illegal actions performed by users, whether the action is performed knowingly (intentionally) or by ignorance.
Internet systems that includes: desktop computers, laptops and other mobile media (tablets, smartphones), file transfer protocols, operating systems, network accounts, electronic mail, all electronic storage media, are the property to TSM. All of these resources are to be used only for business, never for personal use.
TSM shall ensure that all the in scope parties are formal communicated of TSM Information Security Policies. TSM has implemented training programs to guide users on the importance of properly using the information of TSM, and at the same time raise awareness of existing regulations and corporate policies and procedures to ensure full compliance with all the requirements.
Access to the TSM information systems and applications will be provided to users to support business activities and only on a need-to-know basis to perform their jobs responsibilities.
| IV. | Definitions: |
| 1. | Blogging: The activity of adding new entries to a blog or website usually designed to present the owner’s thoughts and ideas, observations, opinions and experiences. |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#1 | Page 2 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Acceptable Use | ||
| 2. | Honeypot: A location in network that is expressly set up to attract and study malware that attempts to penetrate the network or computer system. |
| 3. | Honeynets: Contains one or more honey pots, which are computer systems on the Internet expressly set up to attract and "trap" people who attempt to penetrate other people's computer systems. |
| 4. | Proprietary Information: The information that is not considered public. This may include: corporate, financial and system information. |
| 5. | Spam: Any electronic junk mail received by users and most unsolicited e-mail. |
| 6. | Cloud Platform: A system where applications or systems may be run in an environment composed of utility services in an abstract environment, such as the Internet. Internet- based computing, where shared resources, data and information are provided to computers and other devices on-demand. |
| 7. | Cloud Storage: A popular method used for data storage on the Internet. This could be free or paid. |
| 8. | Mobile device: Any portable equipment used in technology. |
| 9. | BYOD: An acronym for Bring Your Own Device. A custom on the corporate culture where the employer approves the use of employee personal devices such as phones and tablets for the daily job function. |
| 10. | Jail Break: Term used to unlock the operating system of a smartphone, tablet or any portable device without its default security system. |
| 11. | Root: Rooting gives the user administrator rights to alter the OS, tweak the hardware and unlock the phone from its carrier. |
| V. | Responsibilities: |
| 1. | All Triple-S Management Corporation (TSM) and its subsidiaries employees, temporary workers, contractors, business partners and third party vendors, without exception, must comply with the information security policies. Any employee found to have violated such Policies may be subject to disciplinary actions, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated. Triple-S Management Corporation (TSM) reserves the right to audit networks, systems, or procedures on a periodic basis to ensure compliance with this policy. |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#1 | Page 3 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Acceptable Use | ||
In addition, all TSM personnel shall not interfere with federal or state investigations or disciplinary proceedings by willful misrepresentation or omission of facts or by the use of threats or harassment against any person.
| 2. | Exceptions |
The Information & Cyber Security Director or Triple-S Management must approve any exception to the policy in advance.
| 3. | Non-Compliance |
An employee found to have violated this policy may be subject to disciplinary action, up to and including termination of employment.
| VI. | Procedure: |
| 1. | The following General Use and Ownership practices help the organization prevent confidentiality and security breaches: |
| a) | All users should know that all generated information through TSM networks and systems is property of TSM. |
| b) | A physical inventory of all TSM devices and the authorized personnel to use the devices (e.g. Laptops, Desktops Computers, and Corporate Cellphones among others) shall exist and be updated frequently. All devices shall be labeled with either a TSM inventory number, or logo for proper identification. |
| c) | Authorized users may access, use or share TSM proprietary information only to the extent it is authorized and necessary to fulfill the user assigned job duties (e.g. minimum necessary).[Core-16(a)] [Core 15(b)] |
| d) | All users shall be liable for the protecting the information stored on systems, applications, directories and network devices belonging to TSM and shall exercise good judgment regarding the reasonableness of the use of the equipment and the information. [Core- 15(b)] |
| e) | For security and network maintenance purposes, TSM, authorized individuals shall supervise and monitor equipment, system and network traffic. [Core-15(a)(b)(c)] |
| f) | TSM reserves the right to audit network and systems if necessary on a periodic basis to ensure compliance with this policy. [Core-15(a)(c)] |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#1 | Page 4 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Acceptable Use | ||
| g) | All system accesses will be disabled and/or deleted upon termination of employee, completion of contract, end of service of non-employee, or disciplinary action arising from violation of this policy. In the case of a change in job function and/or transfer the original access will be discontinued, and only reissued if necessary and a new request for access is approved. [Core-15(b)] |
| 2. | Security and Proprietary Information: |
The following Security and Proprietary Information protection practices help the organization prevent confidentiality and security breaches [Core-15(b)].
| a) | Providing access to another individual, either deliberately or through failure to secure its access is prohibited. |
| b) | All computing devices must be secured with a password-protected screensaver with the automatic activation feature set at 10 minutes or less. The user must lock the screen or log off when the device is unattended. |
| c) | Posting by employees from a TSM email address or systems on blogs or social networking sites is prohibited unless posting is in the course of business duties. |
| 3. | Unacceptable Use: |
The following activities are not considered an acceptable use of the organization information and information assets. Not following these recommendations could place individually- identified health information and company information at risk. Note that some users may be exempted from some of the restrictions during the course of their legitimate job responsibilities (e.g., system administrator staff may have a need to disable the network access of a host if that host is disrupting production services).
| a) | Under no circumstances an employee of TSM is authorized to engage in any activity that is illegal under local, state, federal or international law while utilizing TSM owned resources. [Core-15(b)] |
| b) | Violations of the rights of any person or company protected by copyright, trade secret, patent or other intellectual property, or similar laws or regulations, including, but not limited to, the installation or distribution of "pirated" or other software products that are not appropriately licensed for use by TSM. [Core-15(b)] |
| c) | Unauthorized copying of copyrighted material including, but not limited to, digitization and distribution of photographs from magazines, books or other copyrighted sources, |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#1 | Page 5 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Acceptable Use | ||
copyrighted music, and the installation of any copyrighted software for which TSM or the end user does not have an active license is strictly prohibited. [Core-15(b)]
| d) | The use or installation of unauthorized software, including obtaining data and/or software from external networks is prohibited. [Core-15(b)] |
| e) | Accessing data, a server or an account for any purpose other than conducting TSM business, even if you have authorized access, is prohibited. [Core-16(a)] |
| f) | Exporting software, technical information, encryption software or technology, in violation of international or regional export control laws, is illegal. The appropriate management should be consulted prior the export of any material that is in question.[Core-15(b)] |
| g) | Introduction of malicious programs into TSM network environment (e.g., viruses, worms, Trojan horses, e-mail bombs, ransomware, etc.). [Core-15(b)] |
| h) | Revealing your account password to others or allowing use of your account by others. This includes family and other household members when work is being done at home. [Core-15(b)] |
| i) | Using a TSM information technology asset to actively engage in procuring or transmitting material that is in violation of sexual harassment or hostile workplace laws in the user's local jurisdiction. |
| j) | Making fraudulent offers of products, items, or services originating from any TSM account. |
| k) | Making statements about warranty, expressly or implied, unless it is a part of normal job duties. |
| l) | Effecting security breaches or disruptions of network communication. Security breaches include, but are not limited to, accessing data of which the employee is not an intended recipient or logging into a server or account that the employee is not expressly authorized to access, unless these duties are within the scope of regular duties. For purposes of this section, "disruption" includes, but is not limited to, network sniffing, pinged floods, packet spoofing, denial of service, and forged routing information for malicious purposes. [Core- 15(b)] |
| m) | Port scanning or security scanning is expressly prohibited unless prior notification to the Information Security Group is made. [Core-15(b)] |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#1 | Page 6 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Acceptable Use | ||
| n) | Executing any form of network monitoring which will intercept data not intended for the employee's host, unless this activity is a part of the employee's normal job/duty. [Core- 15(b)] |
| o) | Circumventing user authentication or security of any host, network or account. [Core- 15(b)] |
| p) | Introducing honeypots, honeynets, or similar technology on the TSM networks. [Core- 15(b)] |
| q) | Using any program/script/command, or sending messages of any kind, with the intent to interfere with, or disable, a user's terminal session, via any means, locally or via the Internet/Intranet/Extranet. [Core-15(b)] |
| r) | Providing confidential information about TSM employees to parties outside TSM. [Core- 15(b)] |
| 4. | Email and Communication Activities: |
The following practices help the organization prevent confidentiality and security breaches and therefore are prohibited [Core-15(b)]:
| a) | Sending unsolicited email messages, including the sending of "junk mail" or other advertising material to individuals who did not specifically request such material (email spam). |
| b) | Any form of harassment via email, telephone or texting, whether through language, frequency, or size of messages. |
| c) | Unauthorized use, or forging, of email header information. |
| d) | Creating or forwarding "chain letters", "Ponzi" or other "pyramid" fraudulent schemes of any type. |
| e) | Use of unsolicited email originating from within TSM networks or other information technology service providers on behalf of, or to advertise, any service hosted by TSM or connected via TSM network unless this activity is part of normal business activity. |
| f) | Posting the same or similar non-business-related messages to large numbers of Usenet newsgroups (newsgroup spam). |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#1 | Page 7 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Acceptable Use | ||
| g) | Employees should never open e-mails received from unknown senders as these e-mails may contain malware. |
| 5. | Blogging and Social Media: |
The following practices help the organization prevent confidentiality and security breaches [Core-15(b)]:
| a) | Blogging by employees, whether using Triple-S Management Corporation (TSM) property and systems or personal computer systems, is also subject to the terms and restrictions set forth in this Policy. Blogging from TSM systems is also subject to monitoring. |
| b) | Users shall also carefully control what information they post on social media accounts and to whom this information is available. This particularly applies to users who actively participate on social media sites as part of their company job function, in order to network with customers and promote brand awareness. |
| c) | TSM Confidential Information policy also applies to blogging. As such, Employees are prohibited from revealing any TSM confidential or proprietary information, trade secrets or any other material covered by TSM Confidential Information policy when engaged in blogging. |
| d) | Employees shall not engage in any blogging that may harm or tarnish the image, reputation and/or goodwill of TSM and/or any of its employees. Employees are also prohibited from making any discriminatory, disparaging, defamatory or harassing comments when blogging or otherwise engaging in any conduct prohibited by TSM Non- Discrimination and Anti-Harassment policy. |
| e) | Employees shall also not attribute personal statements, opinions or beliefs to TSM when engaged in blogging. If an employee is expressing his or her beliefs and/or opinions in blogs, the employee shall not, expressly or implicitly, represent itself as an employee or representative of TSM. Employees shall assume any and all risk associated with blogging. |
| f) | Apart from following all laws pertaining to the handling and disclosure of copyrighted or export controlled materials, TSM trademarks, logos and any other TSM intellectual property shall also not be used in connection with any blogging activity. |
| 6. | Cloud Base Storage Sites: |
The following practices help the organization prevent confidentiality and security breaches [Core-15(b)]:
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#1 | Page 8 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Acceptable Use | ||
Triple-S Management Corporation (TSM) has contracted the services of “Box” (cloud platform). This is the TSM authorized cloud platform for the secure online storage of TSM files.
| a) | User access to “Box” shall be authorized by the Information & Cyber Security Director to support business activities, only in a need-to-know basis to allow the authorized users to perform their jobs functions and responsibilities. |
| b) | All files, data and information with PHI, PII, ePHI or any other sensitive information property of TSM store using the cloud platform (Box) shall be encrypted with PGP or other mechanisms. |
| c) | The use of cloud base store sites such as (Dropbox, OneDrive, Google Drive, Amazon, Copy, and iCloud) are not considered an acceptable use. The Users shall not storage any type of TSM data and/or information. All users shall maintain and protect the confidentiality of all TSM data and information systems. |
| d) | Users shall not use the designated TSM “Box” account for personal use. The storage of files, music, pictures or other data not related to TSM business purposes is prohibited. |
| 7. | Mobile Devices: |
The following practices help the organization prevent confidentiality and security breaches [Core-15(b)]:
This policy establishes the rules for the proper used of mobile devices (BYOD/Corporate Owned) whenever it is use to access to Triple-S Management Corporation (TSM) networks or corporate email, in order to protect the confidentiality of sensitive data, the integrity of data and applications, and the availability of services at TSM, as well as corporate assets (confidentiality and integrity) and continuity of the business (availability).
TSM reserves the right to disconnect any device or disable the access to TSM networks or application services without notification. The users shall use his or her devices always in an ethical manner and agrees to adhere to the TSM applicable policies and procedures.
| a) | Mobile devices must be passwords/PIN protected. |
| b) | Users shall maintain the original device operating system and keep the device current with security patches and updates, as released by the manufacturer. |
| c) | Users shall not “Jail Break” nor “Root” the device (installing software that allows the user to bypass standard built-in security features and controls). |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#1 | Page 9 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Acceptable Use | ||
| d) | Users agree to delete any sensitive business files that may be inadvertently downloaded and stored on the device, and that is not going to be used anymore. |
| e) | Users are responsible for security and backing up all personal information on their mobile devices. |
| f) | Users must take appropriate precautions to prevent others from obtaining access to their mobile device(s). |
| g) | Mobile devices user credentials (User-ID, PIN, and Password) shall not be share with other personnel. |
| h) | Employees are responsible for immediately notifying to TSM in case of device loss or theft. |
| i) | Selected TSM mobile device activities can be tracked and monitored. |
| VII. | Attachments: |
N/A
| Version Control |
Effective Date
|
Approved By (include position name)
|
Amendment
|
| 1 | 09/01/2016 | ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, CIO | 1 |
| 2 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#2 | Page 10 | |||
| Effective Date: 09/01/2016 | |||||
| Approval Date: 09/01/2016 | |||||
| Department: Information Security | Last Review Date: 08/11/2016 | ||||
| Policy Name: | Anti-virus and Anti-Spyware | ||||
|
Drafted by: ▇▇▇▇ ▇▇▇▇▇▇, IT Compliance Supervisor
|
Reviewed by: ▇▇▇▇▇▇ ▇. ▇▇▇▇▇▇▇, Information & Cyber Security Director |
Approved by: ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, Chief Information Officer
|
|||
| I. | Purpose: |
The purpose of this policy is to establish requirements which must be followed by all users of the organization and be met by all computers connected to the TSM network. The adoption and enforcement of the policy help reduce the organization risk against malicious programs such as malware, botnets and computer viruses.
Computer viruses, malware, botnets and spyware are some of the most significant threats against computer environment connected to the Internet. The Internet has made the propagation of malicious programs part of the global cyber-crime industry. This industry today counts with computer viruses, malware, botnets and spyware program developers as well as formal distribution and harvesting channels. One of the main goals of the cyber-crime industry is to steal customer sensitive information and promote fraud and cyber-espionage against individuals and corporations. The channel is highly effective due to the following factors:
| 1. | Easy and rapid access to the internet by cyber criminals. |
| 2. | Cyber-criminals leverage the very low cost of the internet channel. |
| 3. | Billions of users connected to the internet provide a great incentive to cyber-criminals to harvest this channel for committing fraud. |
| 4. | Most internet users have a very low level of awareness cyber-crime and cyber-crime techniques. |
| 5. | Global nature of the internet makes criminal prosecution harder. |
For these reasons proper maintenance and operation of the anti-virus and anti-spyware system is one of the primary security layers used by TSM to protect its IT assets against malware and other types of attacks. The anti-virus and antispyware system is designed to detect and protect the IT assets based on the Windows operating system used by TSM.
| II. | Scope: |
This policy applies to TSM and its subsidiaries employees, temporary workers, contractors, business partners, third party vendors and physical facilities where TSM provides services to its customers.
| III. | Policy: |
This policy help the organization prevent confidentiality and security breaches [Core-15(b)].
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#2 | Page 11 |
| Effective Date: 09/01/2016 | ||
| Approval Date: 09/01/2016 | ||
| Department: Information Security | Last Review Date: 08/11/2016 | |
| Policy Name: Anti-virus and Anti-Spyware | ||
Triple-S Management Corporation (TSM) has developed and adopted the Anti-Virus and Anti- Spyware Policy to provide management with direction and support for the implementation of safeguards to detect, prevent and recover, against malicious programs such as malware, botnets and computer viruses.
| IV. | Definitions: |
| 1. | Virus: A program that enters a computer usually without the knowledge of the operator. Some viruses are mild and only cause messages to appear on the screen, but others are destructive and can wipe out the computer's memory or cause more severe damage. |
| 2. | Botnet: A network of computers created by malware and controlled remotely, without the knowledge of the users of those computers. |
| 3. | Malware: Software that is intended to damage or disable computers and computer systems. Including computer viruses, worms, trojan horses, ▇▇▇▇▇▇ ▇▇▇▇, spyware, adware and other malicious programs. |
| 4. | Spyware: Software that aims to gather information about a person or organization without their knowledge and that may send such information to another entity. |
| V. | Responsibilities: |
All Triple-S Management Corporation (TSM) and its subsidiaries employees, temporary workers, contractors, business partners and third party vendors, without exception, must comply with the information security policies. Any employee found to have violated such Policies may be subject to disciplinary actions, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated.
TSM reserves the right to audit networks, systems, or procedures on a periodic basis to ensure compliance with this policy.
In addition, all TSM personnel shall not interfere with federal or state investigations or disciplinary proceedings by willful misrepresentation or omission of facts or by the use of threats or harassment against any person.
| 1. | Exceptions |
Any exception to the policy must be approved by the Information & Cyber Security Director or Triple-S Management in advance.
| 2. | Non-Compliance |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#2 | Page 12 |
| Effective Date: 09/01/2016 | ||
| Approval Date: 09/01/2016 | ||
| Department: Information Security | Last Review Date: 08/11/2016 | |
| Policy Name: Anti-virus and Anti-Spyware | ||
Any employee found to have violated the policy may be subject to disciplinary actions, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated.
| VI. | Procedure: |
| 1. | TSM Microsoft based Windows servers, workstations and laptop computers must have TSM's approved and supported anti-virus and anti-spyware agent installed and scheduled to run at regular intervals. [Core-15 (b)] |
| 2. | The anti-virus and anti-spyware agent and its virus and spyware signature database must be configured for performing automatic updates of the system malicious program database. [Core-15 (b)] |
| 3. | All new software and files downloaded from the internet must be subject to screening by the anti-virus and anti-spyware system before being allowed in the internal network. [Core- 15(c)] |
| 4. | The Desktop Management Group (DMG) is responsible for removing from the TSM network virus-infected computers until they are verified as virus-free. Confirmation of the verification shall be send to the Information Security Group. [Core-15(c)] |
| 5. | The Infrastructure Management Group (IMG) is responsible for removing from the TSM network virus-infected servers until they are verified as virus-free. Confirmation of the verification shall be send to the Information Security Group. [Core-15(c)] |
| 6. | The Information Security Group is responsible for creating procedures to ensure that anti- virus and anti-spyware software is run at regular intervals, to confirm that computers are verified as virus-free. [Core-15 (b)] |
| 7. | Audit logs shall be generated and be maintained of the checks performed by the anti-virus software. Audit logs of the anti-virus and anti-spyware system will be managed by the Information Security group. [Core-15(c)] |
| 8. | Employees, temporary personnel, contractors and Service providers granted access to the TMS network are prohibited from performing any activities with the intention to create and/or distribute malicious programs into TSM's networks (e.g., viruses, spyware, malware, worms, Trojan horses, e-mail bombs, etc.) are prohibited, in accordance with the TSM Acceptable Use Policy. [Core-15(b)] |
| 9. | Machines with operating systems other than those based on Microsoft Operating System are exempted from this policy. [Core-15 (b)] |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#2 | Page 13 |
| Effective Date: 09/01/2016 | ||
| Approval Date: 09/01/2016 | ||
| Department: Information Security | Last Review Date: 08/11/2016 | |
| Policy Name: Anti-virus and Anti-Spyware | ||
| VII. | Attachments: |
N/A
| Version Control |
Effective Date
|
Approved By (include position name)
|
Amendment
|
| 1 | 09/01/2016 | ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, CIO | 1 |
| 2 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#3 | Page 14 | |||
| Effective Date: 09/01/2016 | |||||
| Review Date: 06/05/2016 | |||||
| Department: Information Security | |||||
| Policy Name: | Asset Management Policy | ||||
|
Drafted by: ▇▇▇▇ ▇▇▇▇▇▇, IT Compliance Supervisor
|
Reviewed by: ▇▇▇▇▇▇ ▇. ▇▇▇▇▇▇▇, Information & Cyber Security Director |
Approved by: ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, Chief Information Officer
|
|||
| I. | Purpose: |
The purpose of this policy is to define requirements to ensure that IT assets are clearly identified and that an inventory of all IT assets is maintained and updated ton ensure accountability and protection of the electronic information stored in the asset. [Core-15(b)]
| II. | Scope: |
This policy applies to TSM and its subsidiaries employees, temporary workers, contractors, business partners, third party vendors and physical facilities where TSM provides services to its customers.
| III. | Policy: |
Triple-S Management Corporation (TSM) has developed and adopted the IT Asset Management Policy to provide management with direction and support to ensure that management requires ownership, defines responsibilities and maintains accountability for the protection of the organization computing assets. [Core-15(b)]
| IV. | Definitions: |
None
| V. | Responsibilities: |
| 1. | All Triple-S Management Corporation (TSM) and its subsidiaries employees, temporary workers, contractors, business partners and third party vendors, without exception, must comply with the information security policies. Any employee found to have violated such Policies may be subject to disciplinary actions, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated. |
| 2. | TSM reserves the right to audit networks, systems, or procedures on a periodic basis to ensure compliance with this policy. |
In addition, all TSM personnel shall not interfere with federal or state investigations or disciplinary proceedings by willful misrepresentation or omission of facts or by the use of threats or harassment against any person.
| 3. | Exceptions |
Any exception to the policy must be approved by the Information & Cyber Security Director or Triple-S Management in advance.
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#3 | Page 15 |
| Effective Date: 09/01/2016 | ||
| Review Date: 06/05/2016 | ||
| Department: Information Security | ||
| Policy Name: Asset Management Policy | ||
| 4. | Non-Compliance |
An employee found to have violated this policy may be subject to disciplinary action, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated.
| VI. | Procedure: |
| 1. | IT Asset Lifecycle Program |
TSM shall implement an IT Asset Lifecycle Program, monitor its effectiveness making changes as needed. TSM shall implement six (6) stages for the lifecycle of an IT asset. The following activities for each stage must include: [Core-15(b)]
| a) | Planning: Defining supporting processes, setting standards for configuration and retention, aligning purchase plans to business goals, collecting aggregate information on intended purchases, and negotiating volume discounts. |
| b) | Procurement: Requisitioning, approving, ordering, receiving and validating orders. |
| c) | Deployment: Tagging assets, entering asset information in a repository, configuring and installing assets including: |
| o | Disabling unnecessary or insecure services or protocols |
| o | Limiting servers to one primary function |
| o | Defining system security parameters to prevent misuse |
| d) | Management: Inventory / counting, monitoring usage, managing contracts for maintenance and support, and monitoring configuration. |
| e) | Support: Adding and changing configurations, repairing devices, and relocating equipment and software. |
| f) | Disposition: Removing assets from service, deleting storage contents, disassembling components for reuse, disposing of equipment, terminating contracts, disposing of equipment, and removing or eliminating assets from the active inventory. |
The inventory of IT assets shall include capital and non-capital assets. Capital assets are considered property, plant and equipment (assets that are usually capitalized). For capital assets an annual inventory must be performed at least once a year. [Core-15(b)]
Non-capital assets are those that are usually, due to the lower cost considered as a supply expense (i.e. pen drives, etc.). [Core-15(b)]
| 2. | Inventory of IT assets |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#3 | Page 16 |
| Effective Date: 09/01/2016 | ||
| Review Date: 06/05/2016 | ||
| Department: Information Security | ||
| Policy Name: Asset Management Policy | ||
The organization shall identify, tag and inventory all IT assets including information (e.g. ePHI, PII) and document the importance of these assets. The IT asset inventory shall include the information necessary to uniquely identify the IT asset. [Core-15(b)]
The inventory of IT assets shall include the following information elements (where applicable): [Core-15(b)]
| o | Equipment serial number. |
| o | Equipment or machine name. |
| o | Information system of which the component is a part. |
| o | Type of information system component (i.e. server, desktop, laptop, application, database, etc.). |
| o | Operating System (OS) type and version. |
| o | Service Pack (SP) level. |
| o | Presence of virtual machines |
| o | Application or database software version/license information (i.e. [***], MS SQL Server). |
| o | Physical location (i.e. building/room number). |
| o | Logical location (i.e. IP address, position with the IS architecture). |
| o | Media access control (MAC) address. |
| o | Ownership by position and role. |
| o | Operational status (i.e. Active/Inactive). |
| o | Primary and secondary system administrators. |
| o | Primary and secondary application administrators. |
| o | Primary business application owner. |
| o | Asset classification level based on data classification criteria (i.e. CONFIDENTIAL). |
| 3. | Equipment assigned to employees, temporary employees or contractors |
Records of property assigned to employees of the organization, temporary employees or contractors (laptops, tablets, cell phones, external drives, and similar peripherals) shall be maintained. [Core-15(b)]
The equipment record shall be used to ensure that all the assigned property is returned to the organization upon the employee termination or transfer out of the department or upon termination of the temporary employee contract or upon termination of the contractor contract. [Core-15(b)]
The manager of the employee or of the contractor is responsible for ensuring that during the employee exit process or the contractor termination process the assigned equipment is returned and that the IT asset inventory is updated. In case of laptops and notebooks the IT
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#3 | Page 17 |
| Effective Date: 09/01/2016 | ||
| Review Date: 06/05/2016 | ||
| Department: Information Security | ||
| Policy Name: Asset Management Policy | ||
asset shall be returned to the Desktop Management Group (DMG) for updating of the IT asset inventory. [Core-15(b)]
Laptops and any other equipment assigned to employees, temporary employees and contractors must be reviewed and updated annually. [Core-15(b)]
| 4. | IT Asset inventory |
TSM shall employ automated mechanisms to scan the network at least on a weekly basis to detect the presence of unauthorized components or devices (including hardware, firmware and software) into the information system. TSM shall disable network access by such components. [Core-15(b)]
| 5. | Inventory of Wireless Access Points (WAP) |
TSM shall maintain an inventory of Wireless Access Points (WAP). This inventory shall also be updated on an annual basis or when WAP are removed or added. [Core-15(b)]
| 6. | Ownership of IT Assets |
All IT assets must be assigned a System Owner who will be responsible for the asset (protection, storage, transfer protocols, destruction). Although property might be assigned to contractors or volunteers for business purposes, ownership will remain in TSM to the officer assigned such ownership. [Core-15(b)]
| 7. | Accepted use of IT Assets |
Refer to Acceptable Use Policy for details.
| 8. | Sensitive System Isolation |
Sensitive systems shall have a dedicated and isolated computing environment. [Core-15(b)]
| VII. | Attachments: |
N/A
| Version Control |
Effective Date
|
Approved By (include position name)
|
Amendment
|
| 1 | 09/01/2016 | ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, CIO | 1 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#4 | Page 18 | |||
| Effective Date: 09/01/2016 | |||||
| Approval Date: 09/01/2016 | |||||
| Department: Information Security | Last Review Date: 08/11/2016 | ||||
| Policy Name: | Backup & Retention | ||||
|
Drafted by: ▇▇▇▇ ▇▇▇▇▇▇, IT Compliance Supervisor
|
Reviewed by: ▇▇▇▇▇▇ ▇. ▇▇▇▇▇▇▇, Information & Cyber Security Director |
Approved by: ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, Chief Information Officer |
|||
| I. | Purpose: |
The purpose of this policy is to establish the organization backup and retention policy in order to protect the confidentiality, integrity and availability of critical data required to support TSM business operations.
| II. | Scope: |
This policy applies to all TSM and its subsidiaries equipment (e.g. laptops, desktops, servers etc.), data and systems, owned or operated by TSM where the organization provides services to its customers. In order to safeguard the information assets of TSM and to prevent the loss of data in the case of an accidental deletion or corruption of data, system failure, or a disaster.
| III. | Policy: |
This policy supports the organization plan for storage, maintenance and destruction information [Core-13b].
Triple-S Management Corporation (TSM) has developed and adopted the Backup and Retention Policy to provide management with direction and support for the implementation of secured and protected backup processes in order to ensure the availability of the critical business information in case of major disaster or system interruption. The implementation of robust backup and retention procedures also help minimize potential loss or corruption of critical data reducing the organization level of risk against unexpected interruptions and events.
| IV. | Definitions: |
| 1. | Backup: The activity of storing data, files or databases in a secured environment (equipment, cloud) in case of catastrophe or hardware failure. |
| 2. | Full Backup: A backup of a set of specified files, often the entire contents of a disk, regardless of when they were last modified. |
| 3. | Incremental Backup: Incremental backups only backup the files that have been modified since the last backup. If dump levels are used, incremental backup’s only backup files changed since last backup of a lower dump level. |
| 4. | Restore: The process of copying files forms a backup location to a hard drive or other acceptable media. A restore can be performed when backup data is needed and as part of a testing process. |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#4 | Page 19 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Backup & Retention | ||
| 5. | Encryption: Cryptographic transformation of data (called "plaintext") into a form (called "cipher text") that conceals the data's original meaning to prevent it from being known or used. |
| 6. | Retention: The period established to keep backup media. This period must be in compliance with local and Federal regulations. |
| V. | Responsibilities: |
| 1. | All Triple-S Management Corporation (TSM) and its subsidiaries employees, temporary workers, contractors, business partners and third party vendors, without exception, must comply with the information security policies. Any employee found to have violated such Policies may be subject to disciplinary actions, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated. |
| 2. | TSM reserves the right to audit networks, systems, or procedures on a periodic basis to ensure compliance with this policy. |
In addition, all TSM personnel shall not interfere with federal or state investigations or disciplinary proceedings by willful misrepresentation or omission of facts or by the use of threats or harassment against any person.
| 3. | Exceptions |
Any exception to the policy must be approved by the Information & Cyber Security Director or Triple-S Management in advance.
| 4. | Non-Compliance |
Any employee found to have violated the policy may be subject to disciplinary actions, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated.
| VI. | Procedure: |
This procedure supports the organization process for storage, maintenance and destruction information [Core-13b].
| 1. | Scheduling and Retention: |
| a) | TSM shall implement backup and retention schedules to ensure that application and system data are safeguarded against destruction and lost. |
| b) | TSM is committed to retain and preserve the application and system data for the period of time required by federal and local laws and with the requirements of the Record Retention policy. |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#4 | Page 20 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Backup & Retention | ||
| c) | Full and incremental backups shall be performed and verified on a daily, weekly, and monthly basis for Mainframe, Unix, Windows and VM ▇▇▇▇ base systems. |
| d) | A full backup shall be made at least once a month and will be retained for a minimum of one year. |
| e) | A full backup shall be made at least once a year and will be retained for a minimum of ten years. |
| f) | Full and incremental backups shall be performed for all business applications and databases. |
| g) | All backups shall be subject to verification on a daily, weekly, and monthly basis and backup error conditions should be monitored, log and notified to management for investigation and executions of the backup process. |
| h) | Automatic backup verification process shall be performed, to ensure backups are completed successfully and without error. |
| i) | Backups shall be monitored and problem management procedures shall be followed if error conditions are generated that could impact the integrity and completeness of the backup process. |
| j) | Procedures for retention, and storage of backup media shall be designed, implemented and documented. Backup tapes will be rotated on a daily, weekly, and monthly basis to a secured off-site storage facility (International Safe Deposit) and maintained according to a predefined retention schedule. |
| k) | Tape media inventory shall be performed on a monthly and quarterly basis for mainframe and distributed systems, respectively. |
| l) | Controls must be in place to ensure backup tapes data are not reuse until retention period expires. |
| 2. | Onsite and Offsite Storage: |
| a) | Depending on the criticality of the data, TSM shall ensure its preservation by moving the data to the contracted offsite backup storage facility using a data encryption mechanism. |
| b) | Data considered critical for the business continuity must be moved to an offsite storage at least once a week. |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#4 | Page 21 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Backup & Retention | ||
| c) | Network infrastructure backups, and system critical files must be moved to an offsite storage at least once a month. |
| d) | When the backup service is delivered by the third party, the service level agreement shall include the detailed protections to control confidentiality, integrity, and availability of the back-up information. |
| 3. | Storage Access and Security: |
| a) | All backup media must be stored in a secure area that is accessible only to authorized personnel. |
| b) | Physical and environmental controls shall be in place to protect the backup tapes. |
| 4. | Restorations: |
| a) | All restorations require approval from the designated Data Owner and/or Application Owner. The requestor must fill out a "Restore and Recovery Data" form. |
| 5. | Verification: |
| a) | The backup system shall be tested periodically by restoring a single random file from a random equipment, and manually inspecting it for accurate recovery. The recovery tests will be stored into secured temporary areas so that current "real" user copies of the files will not be overwritten. |
| b) | Backup verification processes must be enabled to facilitate the automatic backup verification purposes and adequate exception notification configured. |
| c) | Failed backups will be re-started twice automatically by the backup tools implemented at TriServe. |
| 6. | Documentation: |
| a) | Backup procedure must be documented. Procedure should describe how to execute backup process and the data restoration process. The procedure must include a list of all the systems and files that are backed up as well as frequency, retention and in-site / off-site backup details. |
| 7. | Responsibilities and other important consideration: |
| a) | Information that it is stored in the "My Documents" folder of the user (e.g. Desktop) will not be backed-up, it is the responsibility of the employee to store all important and critical TSM information in the "My Documents” folder. |
| VII. | Attachments: |
ATTACHMENT A - Backup & Retention Procedure [Core-13b]
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#4 | Page 22 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Backup & Retention | ||
| Version Control |
Effective Date
|
Approved By (include position name)
|
Amendment
|
| 1 | 09/01/2016 | ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, CIO | 1 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#5 | Page 23 | |||
| Effective Date: 09/01/2016 | |||||
| Approval Date: 09/01/2016 | |||||
| Department: Information Security | Last Review Date: 08/11/2016 | ||||
| Policy Name: | Change Management | ||||
|
Drafted by: ▇▇▇▇ ▇▇▇▇▇▇, IT Compliance Supervisor
|
Reviewed by: ▇▇▇▇▇▇ ▇. ▇▇▇▇▇▇▇, Information & Cyber Security Director |
Approved by: ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, Chief Information Officer
|
|||
| I. | Purpose: |
The purpose of this policy is to establish the requirements of the change management process required to control the request, approval and implementation of changes to TSM systems, applications and IT infrastructure. The objective of the policy if to help to minimize the risk of impact to TSM IT services and customers as well as resulting in the introduction of significant vulnerabilities in the TSM IT systems.
| II. | Scope: |
This policy applies to TSM and its subsidiaries employees, temporary workers, contractors, business partners, third party vendors and physical facilities where TSM provides services to its customers and host its IT systems, applications and IT infrastructure components.
| III. | Policy: |
This policy supports the organization data integrity process of electronic information [Core- 13(a)].
Triple-S Management Corporation (TSM) has adopted a Change Management Policy to provide management with direction and support for the implementation of processes and controls to effectively manage risks associated with changes to IT systems and the organization IT infrastructure. As a standard practice changes should be documented, approved, tested and validated. This policy is designed to ensure the organization designs and implement procedures and controls for management of the change management process. These processes and controls are required to meet operational and compliance requirements as well as reduce the level of risk for the organization by ensuring that changes are subject to an approval process before being deployed to the production environment.
| IV. | Definitions: |
| 1. | Change Management: A systematic approach to managing all changes made to a product or system. |
| 2. | Fallback: Actions to revert software implemented changes that failed and therefore it is requiring going back to the original state. |
| 3. | Outsourced software development: Software made by a third party contracted by an organization with specific requirements. |
| V. | Responsibilities: |
| 1. | All Triple-S Management Corporation (TSM) and its subsidiaries employees, temporary workers, contractors, business partners and third party vendors, without exception, must |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#5 | Page 24 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Change Management | ||
comply with the information security policies. Any employee found to have violated such Policies may be subject to disciplinary actions, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated.
TSM reserves the right to audit networks, systems, or procedures on a periodic basis to ensure compliance with this policy.
| 2. | In addition, all TSM personnel shall not interfere with federal or state investigations or disciplinary proceedings by willful misrepresentation or omission of facts or by the use of threats or harassment against any person. |
| 3. | Exceptions |
Any exception to the policy must be approved by the Information & Cyber Security Director in advance.
| 4. | Non-Compliance |
An employee found to have violated this policy may be subject to disciplinary action, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated.
| VI. | Procedure: |
This procedure supports the organization data integrity process of electronic information [Core-13(a)].
| 1. | Changes to Information Technology (IT) assets and systems, such as operating system, hardware, software, application, and network component shall follow the organization change management process. This process shall ensure that changes are documented, authorized, tested, approved and properly implemented. |
| 2. | For custom developed applications and the implementation of package applications, TSM shall ensure that data input validation controls are tested to ensure that the data is correct and appropriate. |
| 3. | The following activities shall be adopted within the change management process: |
| a) | Change Request Form (CR Form): Documentation of the change shall be completed explaining the purpose, details and consequences of the proposed change. All change requests shall be prioritized in terms of benefits, urgency, effort required and potential impact on TSM operations. The CR Form shall include Risk and Impact considerations about the proposed change. |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#5 | Page 25 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Change Management | ||
| b) | Version Control: Change requests and/or updates shall be controlled with version control numbers. Access to system files and program source code shall be restricted to authorized personnel and only authorized personnel shall have access to the version control system. |
| c) | Testing: Changes to TSM systems and IT infrastructure (i.e. servers, databases, applications, system access level and end-user access level) shall be tested in an isolated, controlled environment (where feasible) prior to implementation. The testing process shall verify that intended changes will meet the stated objectives and not cause operational problems, service interruptions or introduce security risks to the organization. |
| d) | Approval: All changes shall be approved prior to implementation. Approval of changes shall be based on the documented acceptance criteria (i.e. a change request form is completed and approved by TSM personnel, an impact assessment was performed and proposed changes were tested). All users, significantly affected by a change, shall be notified. The user representative such as the Application Owner shall sign-off on the change request form. |
| e) | Implementation: Implementation shall only be undertaken after appropriate testing and approval by the designated TSM stakeholders. Implementation of changes to the production environment shall be performed only by authorized TSM systems administrator or by the designated IT personnel such as Database administrator or the Application Administrator. Production systems shall only hold approved programs and required executable code. No development code or compilers shall reside in production systems. Any decision to upgrade (software) to a new release shall take into account the business requirements for the change, and the security and privacy impacts of the release. |
| f) | Fallback: Fallback procedures shall be defined and implemented. This includes defining procedures and roles and responsibilities for aborting/cancelling and recovering from unsuccessful changes and unforeseen events. |
| g) | Post Implementation: All changes shall be monitored once they have been implemented to check for unexpected behavior or incidents. |
| 4. | Emergency Changes shall follow documented procedures to ensure the proper control and authorization. |
| 5. | Outsourced software development shall be reviewed to ensure that the contracts shall have considerations for: code ownership, intellectual property rights, escrow arrangements, right to audit, requirements for quality of code, and technical support. |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#5 | Page 26 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Change Management | ||
| 6. | All internally developed software and all changes to internally developed software that will be accessible via the internet must be subject to a code verification process. The Quality Assurance Group to reduced risks associated with potential vulnerabilities at the application level establish a subscription to use the Code Scanning service to facilitated and conduct this verification process. |
| VII. | Attachments: |
ATTACHMENT B - Change Management process [Core-13(a)]
|
|
Policy No.: ISP#6 | Page 27 | |||
| Effective Date: 09/01/2016 | |||||
| Approval Date: 09/01/2016 | |||||
| Department: Information Security | Last Review Date: 08/11/2016 | ||||
| Policy Name: | Clear Desk & Clear Screen | ||||
|
Drafted by: ▇▇▇▇ ▇▇▇▇▇▇, IT Compliance Supervisor
|
Reviewed by: ▇▇▇▇▇▇ ▇. ▇▇▇▇▇▇▇, Information & Cyber Security Director |
Approved by: ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, Chief Information Officer
|
|||
| I. | Purpose: |
The purpose of this policy is to establish requirements for maintaining a “Clear Desk” & “Clear Screen” procedures where sensitive/confidential information about our employees, our intellectual property, our customers and our vendors is secure in locked areas and out of site.
This Policy is not only about security, but it is also part of the TSM Privacy Policies and it has the purpose to reduce the risk of security breaches in the workplace.
| II. | Scope: |
This policy applies to all TSM and its subsidiaries employees, temporary workers, contractors, business partners, third party vendors and physical facilities where TSM provides services to its customers.
| III. | Policy: |
This policy help the organization prevent confidentiality and security breaches [Core-15(b)] and provide guidance to employees on how to shred and destroy paper documents [CORE-13(b)].
Triple-S Management Corporation (TSM) has developed and adopted a Clear Desk & Clear Screen policy to ensure that sensitive/confidential information (on paper or electronic media) are removed from the end user workspace, locked away when the items are not in use or an employee leaves his/her workstation and clear screen for information assets. This Policy shall take into account the information classification, legal and contractual requirements, and the corresponding risks and cultural aspects of TSM.
| IV. | Definitions: |
None
| V. | Responsibilities: |
| 1. | All Triple-S Management Corporation (TSM) and its subsidiaries employees, temporary workers, contractors, business partners and third party vendors, without exception, must |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#6 | Page 28 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Clear Desk & Clear Screen | ||
comply with the information security policies. Any employee found to have violated such Policies may be subject to disciplinary actions, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated.
| 2. | TSM reserves the right to audit networks, systems, or procedures on a periodic basis to ensure compliance with this policy. |
In addition, all TSM personnel shall not interfere with federal or state investigations or disciplinary proceedings by willful misrepresentation or omission of facts or by the use of threats or harassment against any person.
| 3. | Exceptions |
Any exception to the policy must be approved by the Information & Cyber Security Director in advance.
| 4. | Non-Compliance |
An employee found to have violated this policy may be subject to disciplinary action, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated.
| VI. | Procedure: |
The following practices help the organization prevent confidentiality and security breaches [Core-15(b)]:
| 1. | Sensitive/Confidential business information in paper or electronic storage media shall be locked away in secure cabinets when not required, especially when the office is vacated for a short or extended period of time. |
| 2. | File cabinets containing business sensitive/confidential information shall be kept closed and locked when not in use or when not attended. |
| 3. | Keys used for access to confidential information shall not be left at an unattended desk and they shall be kept in a secure place. |
| 4. | Computer and terminals shall be logged off or protected with a screen and keyword locking mechanism controlled by a password (e.g., (“Ctrl+Alt+Del”) in Windows systems), token or similar user authentication mechanism that conceals information previously visible on the display when unattended and shall be protected by key locks, passwords, or other controls when not in use. |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#6 | Page 29 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Clear Desk & Clear Screen | ||
| 5. | Unattended portable computing devices such as laptops and tablets shall be either locked with a locking cable, locked away in a drawer or kept in a restricted area where only authorized employees are authorized to access. |
| 6. | Employee shall treat mass storage devices such as CD-ROM, DVD or USB drives as sensitive and secure them in a locked drawer when not in use. |
| 7. | Passwords shall not be written on sticky notes or posted on under a computer, nor shall they be left written down in accessible locations. |
| 8. | Incoming and outgoing mail points and unattended facsimile machines shall be protected and unauthorized use of photocopiers shall be prevented. |
| 9. | All printers, copiers and facsimile machines shall be cleared of documents as soon as they are printed to ensure that sensitive printouts are not left in printer trays for the wrong person to pick up. |
| 10. | When transporting documents with Sensitive/Confidential within facilities and through inter- office mail, information shall not be visible through envelope windows and envelopes shall be marked according its classification level (e.g., “Confidential”). |
| 11. | Sensitive/Confidential documents shall be placed in the official shredder bins/recycling bins or placed in the locked secured disposal recycling bins contracted by the organization for the secured destruction of the documents. [CORE-13(b)] |
| 12. | Whiteboard containing sensitive/confidential information shall be erased. [CORE-13(b)] |
| VII. | Attachments: |
N/A
| Version Control |
Effective Date
|
Approved By (include position name)
|
Amendment
|
| 1 | 09/01/2016 | ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, CIO | 1 |
| 2 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#7 | Page 30 | |||
| Effective Date: 09/01/2016 | |||||
| Approval Date: 09/01/2016 | |||||
| Department: Information Security | Last Review Date: 08/11/2016 | ||||
| Policy Name: | Data Classification | ||||
|
Drafted by: ▇▇▇▇ ▇▇▇▇▇▇, IT Compliance Supervisor
|
Reviewed by: ▇▇▇▇▇▇ ▇. ▇▇▇▇▇▇▇, Information & Cyber Security Director |
Approved by: ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, Chief Information Officer
|
|||
| I. | Purpose: |
The purpose of the Data Classification Policy is to ensure that TSM IT assets receive an appropriate level of protection based on the type of information stored and managed. As such the policy required a data centric and risk base focus for the design and implementation safeguard for protection of the most sensitive data including ePHI. [Core-15(b)]
| II. | Scope: |
This policy applies to TSM and its subsidiaries employees, temporary workers, contractors, business partners, third party vendors and physical facilities where TSM provides services to its customers.
| III. | Policy: |
Triple-S Management Corporation (TSM) has defined and documented a Data Classification Policy to provide management with direction and support for the proper handling of information considering the sensitivity and risk of such data. In order to ensure proper management, information must be first classified according to its level of risk and sensitivity considering local and federal regulations. The higher the sensitivity and risk, the higher the classification to be assigned and therefore more controls will be needed to ensure only authorized personnel can access such information. [Core-15(b)]
Users shall be made aware of their responsibilities for proper handling of information received, created, processed, stored, distributed and destroyed by TSM according to its sensitivity and assigned data classification level. [Core-15(b)]
| IV. | Definitions: |
| 1. | Information Owner: Responsible for determining who has access to the information he/she owns. Usually senior management or department head. |
| 2. | Information Custodian: Responsible for assigning the access to the information according to the instructions of the information owner. |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#7 | Page 31 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Data Classification | ||
| 3. | Information User: Responsible for the application of this policy in his/her daily activities in TSM and its subsidiaries. |
| V. | Responsibilities: |
| 1. | All Triple-S Management Corporation (TSM) and its subsidiaries employees, temporary workers, contractors, business partners and third party vendors, without exception, must comply with the information security policies. Any employee found to have violated such Policies may be subject to disciplinary actions, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated. |
| 2. | TSM reserves the right to audit networks, systems, or procedures on a periodic basis to ensure compliance with this policy. |
In addition, all TSM personnel shall not interfere with federal or state investigations or disciplinary proceedings by willful misrepresentation or omission of facts or by the use of threats or harassment against any person.
| 3. | Exceptions |
Any exception to the policy must be approved by the Information & Cyber Security Director in advance.
| 4. | Non-Compliance |
An employee found to have violated this policy may be subject to disciplinary action, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated.
| VI. | Procedure: |
| 1. | Classification Levels |
Four levels of data classification have been defined: [Core-15(b)]
| Level | Description | Examples |
|
PUBLIC
|
Information officially released by TSM for widespread public disclosure. | Press releases, public marketing materials, employment advertising, annual reports, product brochures, the public web site, etc. |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#7 | Page 32 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Data Classification | ||
|
INTERNAL
|
All forms of proprietary information originated or owned by TSM, or entrusted to it by others that is not considered sensitive or confidential. | General organization charts (with no names, only positions), policies, procedures, phone directories (excluding client contact information), some types of training materials. |
|
CONFIDENTIAL
|
Information for which the unauthorized disclosure or compromise would likely have an adverse impact on the company's competitive or financial position, or compromise regulatory compliance of local and Federal laws for protecting personal information. | Trade secrets & marketing, PHI or EPHI, operational, financial, employee user ID’s, passwords, PINs, or other personal identification devices, source code, and technical information integral to the success of our company. |
|
HIGHLY RESTRICTIVE
|
Includes information that is so sensitive that disclosure or usage would have a definite impact on the TSM’s business and future.
Significant restrictions and controls need to be applied.
|
Merger and acquisition information, reorganization documents, security protocol information, legal actions, strategic or tactical information of the organization and its subsidiaries, etc. |
| a) | All information generated by or for TSM, no matter the format: written, verbal, or electronic, is to be treated according to its classification level. [Core-15(b)] |
| b) | If the information is not labeled, personnel must assume it’s confidential. [Core-15(b)] |
| c) | Information that is labeled as public or internal use, but is in draft form or has not been formally approved, it should also be considered confidential. [Core-15(b)] |
| d) | All employees should familiarize themselves with the information labeling and handling guidelines included in the procedures document. [Core-15(b)] |
| e) | It should be noted that the sensitivity level classifications were created as guidelines and to emphasize appropriate measures that users have to take to protect TSM and third Party Confidential information. [Core-15(b)] |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#7 | Page 33 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Data Classification | ||
| f) | Nothing in this policy is, however, intended to prevent employees from engaging in concerted activity protected by law. [Core-15(b)] |
| 2. | Information Owner |
The Information Owner also known as the Application Owner is the leader of a business area or service who is directly responsible for the proper use of the area’s information under his/her management. Such use must be performed, based on the objectives of TSM business. The information owner is responsible for classifying the information, deciding who must have access to it and validating that the security is commensurate according to its assigned classification and that controls are implemented in consistency with such classification. The owner must also periodically review the classification, ensure it is kept up to date and ensure the classification is correct. [Core-15(b)]
Documentation that a physical inventory has been taken, for all locations, shall be retained in the organization’s central accounting office. [Core-15(b)]
| 3. | Information Custodian |
The Information Custodian also known as the Data Custodian is responsible for ensuring that access to TSM information is consistent with the information owner’s requirements and updating such access as personnel changes his responsibilities, is transferred to another unit (and therefore another information owner) and eliminating access if personnel is terminated. [Core-15(b)]
| 4. | Considerations |
The data classification process must consider: [Core-15(b)]
| a) | Business needs for sharing or restricting information. |
| b) | The business impacts associated with such needs. |
| c) | The aggregation effect in the classification process (consider groups of similar information assets and how their individual classification may impact the group or conglomerate of such assets: i.e. if similar information assets have been assigned different classifications, re-consider the classification of each one). |
| 5. | Information asset life cycle |
Information assets should be protected in all phases of their life cycle: received/created, processed, storing, transmittal and destruction. The protection must be according to the classification assigned. Details of how to protect the information asset will be presented in a procedure document. [Core-15(b)]
| 6. | Third Party Confidential Information |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#7 | Page 34 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Data Classification | ||
A subset of TSM Confidential information is "TSM Third Party Confidential" information. This is information that belongs to another corporation which has been entrusted to TSM by that company under non-disclosure agreements (NDA’s) and other contracts as part of the business agreement between both parties. Examples of this type of information include everything from joint business activities to vendor lists, customer orders, and supplier information. Information in this category ranges from extremely sensitive to information about the fact that we’ve connected a supplier / vendor into TSM network to support our operations. [Core-15(b)]
| VII. | Attachments: |
N/A
| Version Control |
Effective Date
|
Approved By (include position name)
|
Amendment
|
| 1 | 09/01/2016 | ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, CIO | 1 |
| 2 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#8 | Page 35 | |||
| Effective Date: 09/01/2016 | |||||
| Approval Date: 09/01/2016 | |||||
| Department: Information Security | Last Review Date: 08/11/2016 | ||||
| Policy Name: | Data Integrity and Interoperability | ||||
|
Drafted by: ▇▇▇▇ ▇▇▇▇▇▇, IT Compliance Supervisor
|
Reviewed by: ▇▇▇▇▇▇ ▇. ▇▇▇▇▇▇▇, Information & Cyber Security Director |
Approved by: ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, Chief Information Officer |
|||
| I. | Purpose: |
This policy provides direction for management of the information as a valuable and strategic resource through establishment of the required processes and controls to ensure the accuracy and integrity of the information managed by the organization.
| II. | Scope: |
This policy applies to TSM and its subsidiaries employees, temporary workers, contractors, business partners, third party vendors and physical facilities where TSM provides services to its customers.
| III. | Policy: |
This policy supports the organization data integrity process of electronic information [Core- 13(a)].
Information has most value when it is complete, accurate, relevant, accessible and timely (CARAT). This policy describes the commitment of Triple-S Management for designing, implementing, and maintaining procedures and controls for proper management of its information. This includes ensuring the accuracy and interoperability of the information managed by the core systems of the organization.
| IV. | Definitions: |
| 1. | Data: numbers, words or images that have yet to be organized or analyzed to answer a specific question. It is often interchangeable with the word ‘information’. |
| 2. | Data Quality: ensuring data is ‘fit for purpose’ and ‘right first time’, which includes the relevance, correctness, completeness and timeliness of all data held in all Trust systems |
| 3. | Document: smallest complete unit of recorded material which is accumulated to form a file. |
| 4. | Information: Produced through processing, manipulating and organizing data to answer questions, adding to the knowledge of the receiver. It is often interchangeable with the word data. |
| 5. | Information Management: a collection and management of information from one or more sources and the distribution of that information to one or more audiences. Management means the organization of and control over the planning, structure and organization, controlling, processing evaluating and reporting of information activities in order to meet the Trust’s objectives and to enable corporate functions in the delivery of information. |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#8 | Page 36 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Data Integrity and Interoperability | ||
| 6. | Software Life Cycle Development: The systems development life cycle (SDLC), also referred to as the application development life-cycle, is a term used in systems engineering, information systems and software engineering to describe a process for planning, creating, testing, and deploying an information system. |
| 7. | Change Management Process: Change Management (CM) refers to any approach to transitioning individuals, teams, and organizations using methods intended to re-direct the use of resources, business process, budget allocations, or other modes of operation that significantly reshape a company or organization. |
| 8. | Referential Integrity: Referential integrity is a relational database concept, which states that table relationships must always be consistent. In other words, any foreign key field must agree with the primary key that is referenced by the foreign key. |
| 9. | Data Purging: Data purging is a term that is commonly used to describe methods that permanently erase and remove data from a storage space. There are many different strategies and techniques for data purging, which is often contrasted with data deletion. Deletion is often seen as a temporary preference, whereas purging removes the data permanently and opens up memory or storage space for other uses |
| 10. | Sensitive Information: Sensitive information is defined as information that is protected against unwarranted disclosure. |
| V. | Responsibilities: |
| 1. | All Triple-S Management Corporation (TSM) and its subsidiaries employees, temporary workers, contractors, business partners and third party vendors, without exception, must comply with the information security policies. Any employee found to have violated such Policies may be subject to disciplinary actions, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated. Triple-S Management Corporation (TSM) reserves the right to audit networks, systems, or procedures on a periodic basis to ensure compliance with this policy. |
In addition, all TSM personnel shall not interfere with federal or state investigations or disciplinary proceedings by willful misrepresentation or omission of facts or by the use of threats or harassment against any person.
| 2. | Exceptions |
The Information & Cyber Security Director or Triple-S Management must approve any exception to the policy in advance.
| 3. | Non-Compliance |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#8 | Page 37 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Data Integrity and Interoperability | ||
An employee found to have violated this policy may be subject to disciplinary action, up to and including termination of employment.
| VI. | Procedure: |
This procedure supports the organization data integrity process of electronic information [Core-13(a)].
| 1. | Data Accuracy and Trace-Ability: |
| a) | The organization will follow the System Development Life Cycle (SDLC) process for all internal system development activities. The SDLC provides a structured methodology for the design, development, testing and implementation of new systems and reduces the risk associated with errors that could be generated by the introduction of new programs. |
| b) | To promote data accuracy the organization promotes the adoption of relational databases structures for its core systems (e.g. [***]). In a relational database framework referral integrity between tables will be enforced by the definition of primary and secondary keys. Maintaining referential integrity ensures the consistency of the data stored by avoiding duplicate records and records with invalid information. |
| c) | To promote data accuracy new systems must be subject to user testing and certification steps. Test results must be documented and retained as part of the project documentation. |
| d) | To promote data accuracy system and applications must be designed to validate data fields registered by end users. For online systems data entry errors must notify the user by generating an error message. |
| e) | To promote data accuracy files received will be subject to a data validation process prior to processing. Records with errors will be reported and will require investigation and be subject to a clearance process in order to continue processing. |
| f) | To promote data accuracy reconciliation reports will be developed and provided to the business owners for tracking and monitoring as part of their daily work activities. |
| g) | To promote data accuracy users will be trained on the proper use and management of new applications. |
| h) | To promote data accuracy administration access to production data will be restricted to authorized personnel (e.g. Database Administrator). |
| i) | To promote data integrity users access will be granted based on the employee job function. User access will require the approval of the business unit manager. |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#8 | Page 38 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Data Integrity and Interoperability | ||
| j) | To verify data accuracy database consistency checks must be run at least annually. |
| k) | To promote trace-ability applications will maintain and audit trail of the most recent changes performed by the users. |
| l) | To promote data accuracy and trace-ability changes to applications and systems must follow the organization change control and release management procedures. Following these procedures is will the organization ensure the consistency, continuity and integrity of the data through software, application and system upgrades. |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#8 | Page 39 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Data Integrity and Interoperability | ||
| m) | To promote data accuracy and confidently two factor authentication will be enforced for authorized telecommute users (e.g. Working from home users). |
| n) | To verify data accuracy end users will participate in the annual Disaster Recovery test to confirm the successful restoration of the system and the system data. Results will be documented and retained. |
| 2. | Interoperability: |
| a) | System and data Interoperability will be promoted by the adoption of open based technology standards and protocols and adherence to each information system interface. |
| 3. | Quality: |
| a) | Data quality will be ensured by the manager in the business area having responsibility over the data, with support from the information technology specialists. |
| 4. | Telecommuters, Remote Users, Delegated Entities and Vendors changes: |
| a) | Authorized telecommuters, remote users, delegated entities and vendors authorized to work and support the systems and business applications used by the organization will be subject to the system development and change management controls established. Following these processes and controls to production systems and environments as defined in the Change Management Policy help reduce the risk of data corruption and system or application errors. |
| VII. | Attachments: |
N/A
| Version Control |
Effective Date
|
Approved By (include position name)
|
Amendment
|
| 1 | 09/01/2016 | ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, CIO | 1 |
| 2 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#9 | Page 40 | |||
| Effective Date: 09/01/2016 | |||||
| Approval Date: 09/01/2016 | |||||
| Department: Information Security | Last Review Date: 08/11/2016 | ||||
| Policy Name: | Encryption and Cryptographic Algorithms | ||||
|
Drafted by: ▇▇▇▇ ▇▇▇▇▇▇, IT Compliance Supervisor
|
Reviewed by: ▇▇▇▇▇▇ ▇. ▇▇▇▇▇▇▇, Information & Cyber Security Director |
Approved by: ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, Chief Information Officer
|
|||
| I. | Purpose: |
TSM has established a formal policy concerning cryptographic and key-management methods that limit the use of encryption to those algorithms that complies with industry-accepted standards and have been proven to work securely and effectively. Additionally, this policy provides direction to ensure that required Federal Regulations and sound industry practices are followed, and legal authority is granted for the dissemination and use of encryption technologies outside Puerto Rico and the United States.
| II. | Scope: |
This policy applies to all TSM and its subsidiaries employees, temporary workers, contractors, business partners, third party vendors and physical facilities where TSM provides services to its customers.
| III. | Policy: |
This policy help the organization prevent confidentiality and security breaches [Core-15(b)].
Triple-S Management Corporation (TSM) has developed and adopted the Encryption Policy to provide management with direction and support to protect the confidentiality, authenticity and integrity of the information by cryptographic means.
| IV. | Definitions: |
| 1. | Proprietary Encryption: An algorithm that has not been made public and/or has not withstood public scrutiny. The developer of the algorithm could be a vendor, an individual, or the government. |
| 2. | Symmetric Cryptosystem: A method of encryption in which the same key is used for both encryption and decryption of the data. |
| 3. | Asymmetric Cryptosystem: A method of encryption in which two different keys are used: one for encrypting and one for decrypting the data (e.g., public-key encryption). |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#9 | Page 41 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Encryption and Cryptographic Algorithms | ||
| V. | Responsibilities: |
| 1. | All Triple-S Management Corporation (TSM) and its subsidiaries employees, temporary workers, contractors, business partners and third party vendors, without exception, must comply with the information security policies. Any employee found to have violated such Policies may be subject to disciplinary actions, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated. |
| 2. | TSM reserves the right to audit networks, systems, or procedures on a periodic basis to ensure compliance with this policy. |
In addition, all TSM personnel shall not interfere with federal or state investigations or disciplinary proceedings by willful misrepresentation or omission of facts or by the use of threats or harassment against any person.
| 3. | Exceptions |
Any exception to the policy must be approved by the Information & Cyber Security Director in advance.
| 4. | Non-Compliance |
An employee found to have violated this policy may be subject to disciplinary action, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated.
| VI. | Procedure: |
TSM shall ensure that the Encryption and Cryptographic Algorithms Policy adheres to the following conditions for purposes of complying with sound industry practices and regulatory requirements. These practices help the organization prevent confidentiality and security breaches [Core-15(b)]:
| 1. | Whenever encryption is used, workers must not delete the sole readable version of the information unless they have demonstrated that the decryption process is able to reestablish a readable version of the information. |
| 2. | It shall not be allowed: |
| o | The use of proprietary encryption algorithms for any purpose. |
| o | The use of any deprecated cryptographic algorithms as reported in the NIST Special Publication 800-131A Revision 1 |
| o | The use of insecure In-Trasit protocols such as SSL versions 1, 2, 3 or TLS v1.0. |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#9 | Page 42 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Encryption and Cryptographic Algorithms | ||
| o | The use of weak key lengths and weak Random Number Generators in accordance to the NIST Special Publication 800-131A Revision 1 |
| 3. | Types of Encryption Algorithms: |
Proven, standard algorithms such as AES256 and Three-Key Triple DES should be used as the basis for protecting the confidentiality of the corporate information. These algorithms represent the actual cipher used for an approved application. Symmetric cryptosystem key lengths must be at least 128 bits. Asymmetric crypto-system keys must be of a length that yields equivalent strength.
Cipher Suites must be used in order of their encryption algorithm key strength and length (e.g.):
| o | AES256 |
| o | AES192 |
| o | AES128 |
| o | Three-Key 3DES |
Special concessions and exceptions could be made for applications transitioning from deprecated algorithms into acceptable ones. These exceptions must be documented and approved by Information & Cyber Security Director.
| 4. | Types of HASH Algorithms: |
Proven, standard algorithms such as ▇▇▇-▇▇▇, ▇▇▇-▇▇▇, ▇▇▇-▇▇▇ and SHA-512 should be used as the basis for protecting the corporate information. These algorithms represent the actual hash used for an approved application. MD5 and SHA-1 are deprecated and MUST NOT be used to protect the corporate information in accordance to the NIST Special Publication 800-131A Revision 1. Acceptable hash functions are:
| o | SHA-224 |
| o | SHA-256 |
| o | SHA-384 |
| o | SHA-512 |
Special concessions and exceptions could be made for applications transitioning from deprecated algorithms into acceptable ones. These exceptions MUST be documented and approved by Information & Cyber Security Director.
| 5. | Types of Digital Signatures: |
Digital signatures are used to provide assurance of origin authentication and data integrity. The generation of a digital signature on data requires the use of 1) a cryptographic hash
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#9 | Page 43 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Encryption and Cryptographic Algorithms | ||
algorithm that operates on the data to be signed, and 2) the use of a cryptographic key and a signing algorithm to generate a signature on the output of the hash function (and, by extension, the data that is intended to be signed) Proven, standard algorithms such as DSA, ECDSA and RSA should be used as the basis for protecting the corporate information in accordance with the NIST Special Publication 800-131A Revision 1. For digital signature, generation Key lengths providing at least 112 bits of security are acceptable. For digital signature verification, Key lengths providing at least 112 bits of security using approved digital signature algorithms are acceptable.
Special concessions and exceptions could be made for applications transitioning from deprecated algorithms into acceptable ones. These exceptions MUST be documented and approved by Information & Cyber Security Director.
| 6. | Protocols for Protecting Data while IN-Transit: |
TSM shall ensure that all confidential data (including encryption keys) is protected while in transit. Proven, standard protocols such as IPsec and TLS should be used as the basis for protecting the corporate information while in-transit. The use of SSL in all its versions 1-3 and TLS v1.0 is prohibited. TLS v1.2 and above is allowed in accordance to NIST Special Publication 800-52 Revision 1. IPsec MUST BE used ONLY with approved cryptographic algorithms. Additionally, proven, standard security protocols such as Secured FTP (SFTP) and Secured Shell (SSHv2) MAY be used as the basis for protecting the corporate sensitive data during transmission over open, public networks.
Special concessions and exceptions could be made for applications transitioning from deprecated algorithms into acceptable ones. These exceptions MUST be documented and approved by Information & Cyber Security Director.
| 7. | Key Management Procedures: |
TSM shall ensure to have documented and implemented all key-management procedures for cryptographic keys to address the following considerations:
| o | Generate strong keys |
| o | Securely distribute keys |
| o | Securely store keys |
| o | Conduct cryptographic key changes for keys that have expired |
| o | Replacement of known or suspected compromised keys |
| o | Prevent unauthorized substitution of keys |
| o | Prevent the use of keys that were retired or replaced |
Key Agreement schemes with keys of 2048 bits or larger are acceptable in accordance to NIST SP 800-56B. Key transport schemes with keys of 2048 bits or larger are acceptable in accordance to NIST SP 800-56B.
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#9 | Page 44 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Encryption and Cryptographic Algorithms | ||
| 8. | Key Access and Security: |
Encryption keys used for TSM information are always classified as confidential information. Access to such keys must be limited authorized personnel and based upon job responsibilities.
TSM will ensure to require approval from the Information & Cyber Security Director or authorized representative prior revealing encryption keys to consultants, contractors, or other this parties.
Certificates must be signed in accordance to the above mentioned digital signature requirements of this policy.
9. Portable Devices:
TSM shall ensure that all portable approved devices such as laptops, and general mobile devices, must be encrypted through TSM approved tools including but not limited to:
| o | Symantec End Point Protection system |
| o | Airwatch for mobile devices |
| o | PGP and Pkzip for end user file encryption capabilities |
| o | FTP secured for file transmission |
| o | HTTPS for encrypted web sessions. Using TLSv1.2 |
Provided that the applications meet the above-mentioned requirements specified in this policy.
| 10. | Review: |
TSM’s key length requirements shall be reviewed annually and upgraded as technology allows.
| VII. | Attachments: |
N/A
| Version Control |
Effective Date
|
Approved By (include position name)
|
Amendment
|
| 1 | 09/01/2016 | ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, CIO | 1 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#10 | Page 45 | |||
| Effective Date: 09/01/2016 | |||||
| Approval Date: 09/01/2016 | |||||
| Department: Information Security | Last Review Date: 08/11/2016 | ||||
| Policy Name: | General Information Security | ||||
|
Drafted by: ▇▇▇▇ ▇▇▇▇▇▇, IT Compliance Supervisor
|
Reviewed by: ▇▇▇▇▇▇ ▇. ▇▇▇▇▇▇▇, Information & Cyber Security Director |
Approved by: ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, Chief Information Officer
|
|||
| I. | Purpose: |
The purpose of this policy is to define requirements for maintaining the Information Security Policies, the organization Information Security Management Program and establish the direction of TSM by aligning the documentation with information security sound practices, laws, and regulatory requirement. [Core-15(b)]
| II. | Scope: |
This policy applies to TSM, its subsidiaries, employees, temporary workers, contractors, business partners and third party vendors contracted by TSM to provide services to its customers.
| III. | Policy: |
Triple-S Management Corporation (TSM) has developed and adopted a General Information Security Policy to provide management clear direction in line with business objectives and relevant laws and regulations. The policy also demonstrates the support and commitment of the organization, its Senior Management and the Board of Directors to maintaining a robust Information Security Management Program (ISMP) in compliance with regulatory requirements across TSM, subsidiaries and its direct and indirect affiliates. [Core-15(b)]
Information security policies are an organizational tool that help its members to be aware of the importance for protecting the organization information assets from threats such as cyber- attacks, internal theft and malicious programs among others as these could result in the unauthorized disclosure of sensitive or protected information and significant regulatory fines. [Core-15(b)]
Therefore, this policy focuses on defining general information security requirements, based on industry standards and information security practices. Adoption of these information security requirements allows TSM to mitigate or reduce risks associated with threats that could expose critical information assets of the organization. [Core-15(b)]
| IV. | Definitions: |
| 1. | Information Security: The practice of protecting data or information from unauthorized access for viewing, modification, recording or destruction. |
| V. | Responsibilities: |
| 1. | All TSM and its subsidiaries employees, temporary workers, contractors, business partners and third party vendors, without exception, must comply with the information security policies. |
| 2. | TSM reserves the right to audit networks, systems, or procedures on a periodic basis to ensure compliance with this policy. |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#10 | Page 46 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | General Information Security | ||
| 3. | In addition, all TSM personnel shall not interfere with federal or state investigations or disciplinary proceedings by willful misrepresentation or omission of facts or by the use of threats or harassment against any person. |
| 4. | Exceptions |
Any exception to the policy must be approved by the Information & Cyber Security Director in advance.
| 5. | Non-Compliance |
Any employee found to have violated such Policies may be subject to disciplinary actions, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated.
| VI. | Procedure: |
| 1. | Information Security Management Program |
An Information Security Management Program (ISMP) shall be formally established, implemented, operated and maintained. [Core-15(b)]
The ISMP shall be reviewed and updated at least annually considering the needs of the organization and changes on existing business requirements, technologies, threats and risk facing the organization. [Core-15(b)]
TSM Senior Management support for the ISMP shall be demonstrated through signed acceptance or approval by management of the program. [Core-15(b)]
The ISMP shall include the relevant security domains for proper management of the program as required by HITRUST. [Core-15(b)]
Personnel assigned with formal responsibilities in the ISMP must be competent in information security tasks. [Core-15(b)]
| 2. | Information Security Policy |
The Information Security Policy shall be approved by Senior Management (e.g. CEO, CFO, COO), published and communicated to all employees and required external service providers. The Information Security Policy shall be supported by a strategic plan and a ISMP with well-defined roles and responsibilities for leadership and officer roles. The policy shall consider: [Core-15(b)]
| o | Definition of information security; |
| o | Overall objectives and scope and the importance of security; |
| o | Statement of management intent, supporting the goals and principles of information security in line with the business strategy and objectives; |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#10 | Page 47 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | General Information Security | ||
| o | A framework for setting control objectives including risk management; |
| o | The need and goals for information security; |
| o | Compliance scope; |
| o | Applicable laws and regulatory requirements; |
| o | Arrangement for notification of security incidents and breaches; |
| o | Definition of roles and responsibilities for information security management. |
The Information Security Policy, the ISMP and related documents shall have a designated owner was approved by management responsibility for accountability purposes. [Core- 15(b)]
The Information Security Policies shall be reviewed and updated at least annually to ensure its continuing adequacy and effectiveness. [Core-15(b)]
| 3. | Organization of Information Security |
The Board of Director and TSM Senior Management shall demonstrate commitment and clear direction to support the Information Security Policy and the organization ISMP. [Core- 15(b)]
An Information & Cyber Security Director must be appointed to ensure that the required components of the Information Security Policy and the ISMP are effectively implemented, maintained and are communicated to all stakeholders. [Core-15(b)]
Information security activities shall be coordinated with a designated person in the division. As such the Business Unit Manager has the responsibility to designate a role for an Information Security Coordinator (ISC) to facilitate the communication and coordination process in the implementation and maintenance of the organization ISMP. [Core-15(b)]
TSM shall ensure to keep continuous contact with relevant regulatory requirements to ensure that information security practices are in alignment with current requirements. Additionally, contact with special interest groups, security forums and professional associations shall be maintained. [Core-15(b)]
Independent review of the ISMP shall be periodically planned and conducted such as independent assessments and audits to ensure continuing adequacy and effectiveness of the security policies and procedures. [Core-15(b)]
| VII. | Attachments: |
N/A
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#10 | Page 48 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | General Information Security | ||
| Version Control |
Effective Date
|
Approved By (include position name)
|
Amendment
|
| 1 | 09/01/2016 | ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, CIO | 1 |
| 2 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#11 | Page 49 | |||
| Effective Date: 09/01/2016 | |||||
| Approval Date: 09/01/2016 | |||||
| Department: Information Security | Last Review Date: 08/11/2016 | ||||
| Policy Name: | Information Exchange | ||||
|
Drafted by: ▇▇▇▇ ▇▇▇▇▇▇, IT Compliance Supervisor
|
Reviewed by: ▇▇▇▇▇▇ ▇. ▇▇▇▇▇▇▇, Information & Cyber Security Director |
Approved by: ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, Chief Information Officer |
|||
| I. | Purpose: |
The purpose of this policy is to ensure the exchange of information within TSM and with external business partners, business associates and covered entities is secured and protected, and carried out in compliance with relevant laws, regulations and exchange agreements.
| II. | Scope: |
This policy applies to all TSM and its subsidiaries employees, temporary workers, contractors, business partners, third party vendors and physical facilities where TSM provides services to its customers.
| III. | Policy: |
This policy supports the organization plan for interoperability [CORE-13(c)]. The policy also addresses electronic communication and records that are transmitted or stored by the organization [CORE-16(d)].
Triple-S Management Corporation (TSM) has adopted and implemented safeguards and countermeasures to secure confidential and sensitive information exchanges. This safeguards and controls are required to protect the confidentiality and integrity of the information that is processed, stored, and transmitted by TSM networks and systems.
| IV. | Definitions: |
| 1. | Encryption: Cryptographic transformation of data (called "plaintext") into a form (called "cipher text") that conceals the data's original meaning to prevent it from being known or used. Also, Virtual Private Network (VPN) is a method employing encryption to provide secure access to a remote computer over the Internet. |
| 2. | Information Exchange: The act of people, companies, and organizations passing information from one to another, especially electronically, or a system that allows them to do this. |
| 3. | Sensitive Information: Defined as information that is protected against unwarranted disclosure. |
| 4. | Wiretapping: The practice of connecting a listening device to a telephone line to secretly monitor a conversation. |
| 5. | Eavesdropping: Secretly listening to the private conversation of others without their consent. |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#11 | Page 50 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Information Exchange | ||
| 6. | Cache: A computer memory with very short access time used for storage of frequently or recently used instructions or data. |
| V. | Responsibilities: |
| 1. | All Triple-S Management Corporation (TSM) and its subsidiaries employees, temporary workers, contractors, business partners and third party vendors, without exception, must comply with the information security policies. Any employee found to have violated such Policies may be subject to disciplinary actions, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated. |
| 2. | TSM reserves the right to audit networks, systems, or procedures on a periodic basis to ensure compliance with this policy. |
In addition, all TSM personnel shall not interfere with federal or state investigations or disciplinary proceedings by willful misrepresentation or omission of facts or by the use of threats or harassment against any person.
| 3. | Exceptions |
Any exception to the policy must be approved by the Information & Cyber Security Director in advance.
| 4. | Non-Compliance |
An employee found to have violated this policy may be subject to disciplinary action, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated.
| VI. | Procedure: |
This procedure supports the organization plan for interoperability [CORE-13(c)]. The procedure also addresses electronic communication and records that are transmitted or stored by the organization [CORE-16(d)]. Attachment A includes the list of systems within the scope of the URAC accreditation that provide support for the internal and external interoperability standards. Attachment B includes a High Level Architecture diagram for the [***] core system which provides support for internal and external interoperability requirements.
The diagram below is a high level representation of TSS core [***] application architecture. The architecture is based on open system standards and the use of SQL databases and web based systems.
TSM shall ensure that the exchange of information within TSM networks and systems and with authorized external business partners, business associates and covered entities is secured and protected.
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#11 | Page 51 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Information Exchange | ||
Procedures shall be defined and documented to ensure that communication protection requirements, including the security of exchanges of information include the following considerations as well as confidentiality and privacy requirements:
1. B2B Information Exchange Requirements:
| a) | Information exchanges including the transmission of sensitive and confidential information including ePHI must be controlled and managed by the Data Center Operation B2B group. |
| b) | The Data Center Operation B2B group shall document, establish and maintain formal data exchange policies, procedures, and controls to protect the exchange of ePHI and company confidential information through the use of corporate approved of communication methods managed by the B2B group. |
| c) | ePHI information shall only be transmitted to business associates and covered entities who have a demonstrated need to receive the information and which have a Business Associate Agreement (BAA) duly signed and approved by the Legal Division. |
| d) | All ePHI transmissions must be performed via approved encrypted telecommunication channels. |
| e) | All ePHI files to be transmitted must be fully encrypted prior to transmission over the secured telecommunication channel. |
| 2. | Electronic Communication: |
| a) | When using electronic communication applications or systems for information exchanges of sensitive and ePHI information, the following procedures and guidelines shall be defined: |
| o | Acceptable use of electronic communication applications or systems. |
| o | Anti-malware for the detection of and protection against malicious code that may be transmitted through the use of electronic communications. |
| o | Secure wireless communications including an appropriate level of encryption. |
| o | Cryptographic techniques shall be implemented to protect the confidentiality, integrity and authenticity of TSM sensitive information (e.g., ePHI). |
| o | Retention and disposal guidelines shall be defined and followed. |
| 3. | Personnel Awareness: |
TSM personnel shall be appropriately educated and periodically reminded of the precautions that TSM employees need to consider when sharing TSM sensitive and ePHI with authorized third parties.
| 4. | Exchange Agreements: |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#11 | Page 52 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Information Exchange | ||
Exchange agreements shall be defined and implemented for the exchange of information between TSM and external parties. The agreements shall specify security controls on responsibility, procedures and technical solutions.
5. Encryption:
TSM shall define and implement standard encryption algorithms for transmission of private or confidential information over public networks protected by industry standard protocols. Refer to the Encryption Policy.
| 6. | Physical Media in Transit: |
Media containing sensitive, confidential and ePHI information shall be protected against unauthorized access, misuse or corruption during transportation beyond TSM physical boundaries. The following requirements shall be implemented for protection of physical storage media to be transported (i.e. backup tapes):
| o | Transportation shall be conducted by authorized couriers who have valid and current contracts with TSM. |
| o | Contracted transport or courier company must be able to track the status of the backup media being transported. |
| o | Procedures to check the identification of couriers shall be followed. |
| o | Packaging shall be sufficient to protect the content from physical damage. |
| o | Transportation of the media shall be conducted using locked containers. |
| o | Delivery of the media shall be conducted by hand and confirmation of receipt shall be maintained. |
| o | Tamper-evident packaging (which reveals any attempt to gain access) shall be used. |
| o | Use of approved encryption methods for data being physically transported in the |
| o | storage media is required. |
| o | Procedures for proper inventory and accountability of backup tapes shall be defined, implemented and followed. |
| o | Procedure for maintaining proper inventory of backup media shall define and followed. |
| 7. | Interconnected Business Information Systems: |
| a) | TSM shall define and implement procedures and guidelines to protect information associated with the interconnection of business information systems between TSM and third parties’ networks. |
| b) | Security controls such as a firewall and network segmentation shall be in place to manage the exchange of information with third parties when using public networks. The firewall shall restrict connections between untrusted networks and systems storing, processing or transmitting sensitive (e.g., ePHI) information. |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#11 | Page 53 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Information Exchange | ||
| c) | Third parties that shall not meet TSM Information Security Policies, shall not be trusted and interconnected until TSM receives the assurance that the third party meets the security controls. |
| VII. | Attachments: |
ATTACHMENT C- Internal and External Interoperability [CORE-13(c)]
ATTACHMENT D- High Level Architecture for Internal and External Interoperability [CORE- 13(c)]
| Version Control |
Effective Date
|
Approved By (include position name)
|
Amendment
|
| 1 | 09/01/2016 | ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, CIO | 1 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#12 | Page 54 | |||
| Effective Date: 09/01/2016 | |||||
| Approval Date: 09/01/2016 | |||||
| Department: Information Security | Last Review Date: 08/11/2016 | ||||
| Policy Name: | IT Compliance Management | ||||
|
Drafted by: ▇▇▇▇ ▇▇▇▇▇▇, IT Compliance Supervisor
|
Reviewed by: ▇▇▇▇▇▇ ▇. ▇▇▇▇▇▇▇, Information & Cyber Security Director |
Approved by: ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, Chief Information Officer
|
|||
| I. | Purpose: |
The purpose of this policy is to define requirements to ensure that the design, operation, use, and management of information systems complies with industry laws, regulations and contractual obligations, including security requirements.
| II. | Scope: |
This policy applies to TSM and its subsidiaries employees, temporary workers, contractors, business partners, third party vendors and physical facilities where TSM provides services to its customers.
| III. | Policy: |
Triple-S Management Corporation (TSM) has developed and adopted the IT Compliance Policy to provide management with direction and support for the implementation of appropriate security measures for the identification of applicable local and federal legislation, intellectual property rights of TSM over its products and services, protection of organizational records, and other related subjects related to legal and regulatory compliance that are expected of organizations in the insurance and healthcare industry. [Core-13(b) & Core-15(c)]
| IV. | Definitions: |
None
| V. | Responsibilities: |
| 1. | All Triple-S Management Corporation (TSM) and its subsidiaries employees, temporary workers, contractors, business partners and third party vendors, without exception, must comply with the information security policies. Any employee found to have violated such Policies may be subject to disciplinary actions, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated. |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#12 | Page 55 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | IT Compliance Management | ||
| 2. | TSM reserves the right to audit networks, systems, or procedures on a periodic basis to ensure compliance with this policy. |
In addition, all TSM personnel shall not interfere with federal or state investigations or disciplinary proceedings by willful misrepresentation or omission of facts or by the use of threats or harassment against any person.
| 3. | Exceptions |
Any exception to the policy must be approved by the Information & Cyber Security Director in advance.
4. Non-Compliance
An employee found to have violated this policy may be subject to disciplinary action, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated.
| VI. | Procedure: |
This section is composed of different sections which detail the policies required for TSM to ensure effective compliance efforts.
| 1. | Identification of Applicable Legislation: |
TSM must ensure that applicable local (i.e. Puerto Rico Insurance Commissioner Officer) and Federal (i.e. HHS, OCR, HIPAA, HITECH) Information Security regulatory requirements are addressed, implemented and maintained. ).
TSM must be a member of a recognized industry trade associations including thought leadership and similar organizations (i.e. Asociacion de Compañias de Seguros de PuertoRico – ACODESE) in order to stay abreast of industry’s legal, regulatory, and technology environmental trends (and threats) that could have an impact on TSM operations including but not limited to TSM information security policies and procedures which, might need to be updated accordingly to consider those new trends and threats.
| 2. | Intellectual Property Rights: |
Preparation of a detailed procedures is required for compliance intellectual property rights and on the use of proprietary software products. The procedures to be developed must include the following elements:
| a) | Acquisition of software only through known and reputable sources to avoid copyright violations. |
| b) | Keep in a safe place all formal and documented evidence of license ownership, master disks, owner’s manuals, and any other documented evidence. |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#12 | Page 56 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | IT Compliance Management | ||
| c) | Implementing controls to avoid exceeding the number of authorized users allowed by the purchased license. |
| d) | Establish controls to avoid copying software and any other illegal approach to increase users. |
| e) | Implementing a license tracking mechanism (manual or automated) to ensure proper control of the software. |
| f) | At least on a yearly basis, perform an audit in the employee’s computers to identify any unauthorized software installation. |
| g) | The information regarding software purchase must be kept in an asset registry or inventory (refer to Asset Management policy for details). |
| 3. | Protection of Electronic Records: [Core-13(b)] |
TSM is responsible to ensure that sensitive data like member or patient medical electronic records, legal contracts or agreements, financial information, employee records and other sensitive information is protected from loss, accidental destruction (i.e. fire, earthquake, flood, etc.) and from unauthorized access.
TSM will issue guidelines that will include ownership, classification, retention, storage, handling and disposal of electronic records and information. A designated member of the business shall be designated as the Data Owner and will be responsible of assigning the corresponding data classification level (i.e. confidential). The ISG will ensure that security controls are applied based on the assigned data classification level (i.e. encryption).
| 4. | Retention of Electronic Records: [Core-13(b)] |
Part of the protection efforts includes that electronic and physical information needs to be retained for the minimum period as established by regulation.
| No. | Documentation | Retention Period |
| 1 | TSM must comply with local and Federal document retention regulations for both physical and electronic information: formal policies and procedures, risk assessment evaluation results and disclosures of protected health information. | 6 years |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#12 | Page 57 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | IT Compliance Management | ||
| 2 | For notice requirements, TSM (as a covered entity as defined by HIPAA) must comply with the minimum requirement period. This requirement includes any written acknowledgements of receipt of such notice or documentation of good faith to obtain such written acknowledgement. | 6 years |
| 3 | For electronic Protected Health Information (ePHI), TSM must retain records of disclosures needed to perform treatment, payment and health care operations. | 3 years |
| 4 | TSM must document restrictions in disclosure and formally keep such files or an electronic copy. | 6 years |
| 5 | Accounting of disclosures, including the information required for disclosure, the information provided to the individual, and the positions and titles of the person (including unit) that received and processed the request for accounting of such request. | 6 years |
| 6 | Minimum period of retention of PHI for deceased plan members. | 50 years |
| 7 | Federal Tax Information (FTI) | 5 years |
| 8 | Audit information | 7 years |
| 5. | Electronic Record Retention Program: [Core-13(b)] |
TSM must develop and update a formal electronic record retention program that includes:
| o | Secure disposal of information (physical and electronic) when no longer needed and is no longer required as per documented retention requirements. |
TSM must develop procedures for secured storage, access, retention and disposal that shall include the following controls as minimum:
| o | Retention schedule to identify record types and the time period that must be retained according to such type. |
| o | Inventory of sources of key information. |
| o | To facilitate decryption, all encryption key material (including digital signatures), programs and documentation should be stored securely. |
| 6. | Data Protection and Privacy of Covered Information: |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#12 | Page 58 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | IT Compliance Management | ||
| a) | A data protection and privacy policy (refer to Data Classification Policy) must be developed to ensure security of sensitive TSM data including EPHI. The policy must be distributed and communicated to all relevant parties. The policy must be updated with latest regulatory requirements and the necessary technical security controls according to classification of assets on an annual basis. |
| b) | A data protection officer should be appointed that will be in charge of assigning responsibilities as presented in the data classification policy. Refer to the Data Classification policy for data ownership and the responsibility according to the role. |
| c) | Covered information must be rendered unreadable anywhere it is stored (i.e. PC’s, portable digital media, backup media, servers, databases, or in logs using the following approach: (for details refer to encryption policy): [Core-13(b)] |
| o | Full disk encryption |
| o | Virtual disk encryption |
| o | Volume disk encryption |
| o | File and folder encryption |
| d) | The encryption approach shall be performed using one or combination of the following: [Core-13(b)] |
| o | One-way hashes based on strong cryptography |
| o | Truncation |
| o | Strong cryptography with associated key-management processes and procedures |
| e) | Protection of information assets must be according to its assigned data classification level (i.e. applying encryption control to PHI/PII). [Core-13(b)]). |
| f) | The implementation of security and privacy protections include transfers of TSM records and even extracts of such records (i.e. spreadsheet information, PDF images of documents, electronic copies, and any other format including .TXT). [Core-13(b)] |
| 7. | Prevention of Misuse of Information Assets: |
Controls must be established to avoid unauthorized use of sensitive information including ePHI/ePII. The following controls must be established:
| a) | Notification to employees, contractors and service providers that their actions may be monitored and are subject to, depending on the event, disciplinary actions (employees) and in contractors and service providers (penalties and even contract termination). |
| b) | All employees contracted personnel (professional services) and service providers (i.e. consultants, auditors) must sign an acceptable use |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#12 | Page 59 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | IT Compliance Management | ||
agreement (refer to acceptable use policy for details). The agreement must establish that they have read, understand and agree to abide by the rules of behavior before TSM management authorizes access to any database and information system of TSM. This must be performed on a yearly basis as this document is updated accordingly.
| c) | TSM must render the Primary Account Number (PAN) and PHI and PII information unreadable via encryption wherever it is stored including portable media. |
| d) | The criteria of what is considered acceptable use of sensitive information should be reviewed every year to update as needed due to regulatory requirements or because of new technologies and threats. |
| 8. | Regulation of Cryptographic Controls: [Core-13(b)] |
Refer to encryption policy for details however, all cryptographic controls need to be reviewed annually for minimum standards established by local and Federal Regulations.
| 9. | Compliance with Security Policies and Standards: [Core-15(c)] |
Reviews of the compliance of systems with security policies, standards applicable (i.e. HIPAA, local and Federal regulations, etc.) should be conducted by the ISG team.
Compliance reviews should be formally documented including all relevant evidence. If noncompliance is found, TSM management must:
| a) | Determine the cause for non-compliance (intentional, lack of training, lack of resources, etc.) |
| b) | Evaluate the need for actions to ensure remediation effort is effective |
| c) | Select and implement a remediation action |
| d) | Perform a re-testing effort to ensure corrective action was effective |
Develop a continuous monitoring strategy that includes security metrics.
| 10. | Technical Compliance Checking: [Core-15(c)] |
TSM must check the technical security configuration of its systems at least annually. In the case where services are provided by a third party, the agreement must allow TSM to verify compliance with processing and security requirements required by TSM.
| 11. | Information Systems Audit Controls: [Core-13(b)] |
TSM must require an annual audit of its information systems to ensure protection data received, stored and transmitted through the systems.
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#12 | Page 60 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | IT Compliance Management | ||
In the case of service providers that manage PHI and PII information, the requirement of an audit must be included in their contracts: either TSM is allowed to audit or a SSAE 16 SOC 1 and/or SOC 2 will be required from the service provider depending on the service provided or information processed.
| 12. | Protection of Information Systems Audit Tools: [Core-15(c)] |
Access to audit applications and the databases generated from those applications should have access controls which limit such access to authorize personnel and they type of access should be according to role in the audit and oversight of such audit.
| VII. | Attachments: |
N/A
| Version Control |
Effective Date
|
Approved By (include position name)
|
Amendment
|
| 1 | 09/01/2016 | ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, | 1 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#13 | Page 61 | |||
| Effective Date: 09/01/2016 | |||||
| Approval Date: 09/01/2016 | |||||
| Department: Information Security | Last Review Date: 08/11/2016 | ||||
| Policy Name: | Network Security | ||||
|
Drafted by: ▇▇▇▇ ▇▇▇▇▇▇, IT Compliance Supervisor |
Reviewed by: ▇▇▇▇▇▇ ▇. ▇▇▇▇▇▇▇, Information & Cyber Security Director |
Approved by: ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, Chief Information Officer
|
|||
| I. | Purpose: |
The purpose of this policy is to define the security requirements for the implementation and management of telecommunication networks. The security requirements are required to protect the organization IT assets from internal and external threats and to maintain the security of the systems and applications using the telecommunication network to support the organization and our internal and external client’s business objectives. [Core-15(b)]
| II. | Scope: |
This policy applies to TSM and its subsidiaries employees, temporary workers, contractors, business partners, third party vendors and physical facilities where TSM provides services to its customers.
| III. | Policy: |
Triple-S Management Corporation (TSM) has adopted and implemented safeguards and countermeasures to secure TSM telecommunication network and systems, in order to protect the confidentiality, integrity, and availability of information that is processed, stored, and transmitted by TSM networks and systems. These controls are implemented to support the business objectives of the organization and to comply with applicable laws and regulations. [Core-15(b)]
| IV. | Definitions: |
| 1. | Encryption: Cryptographic transformation of data (called "plaintext") into a form (called "cipher text") that conceals the data's original meaning to prevent it from being known or used. Also, Virtual Private Network (VPN) is a method employing encryption to provide secure access to a remote computer over the Internet. |
| 2. | Router: Device that interconnect logical networks by forwarding information to other networks based upon IP addresses. |
| 3. | Switch: Networking device that keeps track of MAC addresses attached to each of its ports so that data is only transmitted on the ports that are the intended recipient of the data. |
| 4. | Network Diagram: Unique kind of diagram that represents a cluster or small structure of computers or other networking devices. Generally, is made up of interconnected devices and systems. |
| 5. | Wireless Access Point (WAP): A networking hardware device that allows wireless devices to connect to a wired network using Wi-Fi, or related standards. |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#13 | Page 62 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Network Security | ||
| 6. | Simple Network Management Protocol (SNMP): Protocol governing network management and the monitoring of network devices and their functions. A set of protocols for managing complex networks. |
| V. | Responsibilities: |
| 1. | All TSM and its subsidiaries employees, temporary workers, contractors, business partners and third party vendors, without exception, must comply with the information security policies. |
| 2. | TSM reserves the right to audit networks, systems, or procedures on a periodic basis to ensure compliance with this policy. |
In addition, all TSM personnel shall not interfere with federal or state investigations or disciplinary proceedings by willful misrepresentation or omission of facts or by the use of threats or harassment against any
| 3. | Exceptions |
Any exception to the policy must be approved by the Information & Cyber Security Director in advance.
| 4. | Non-Compliance |
Any employee found to have violated the policy may be subject to disciplinary actions, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated.
| VI. | Procedure: |
Telecommunication networks controls shall be managed and implemented to protect TSM IT assets, systems and information and to maintain the security, integrity and availability of the systems and applications. Telecommunication networks controls are also required to avoid the unauthorized access, use, disclosure, disruption, modification, or destruction of TSM IT assets and electronic information. [Core-15(b)]
| 1. | Network Controls |
A current telecommunication network diagram shall be maintained. The telecommunication network diagram shall document all internal and external connections to TSM systems storing, processing or transmitting information (e.g., PII, ePHI). The diagram shall also include authorized wireless networks and Wireless Access Points (WAP). [Core-15(b)]
The telecommunications network diagram shall be reviewed and updated based on the changes in the environment and no less than every 6 months. [Core-15(b)]
TSM management shall implement telecommunications network controls to ensure the security of the IT assets and the protection of connected systems and active services from
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#13 | Page 63 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Network Security | ||
unauthorized access as well as to ensure the availability of the required telecommunication network services in order to support the organization Business Continuity and Disaster Recovery strategy. [Core-15(b)]
| 2. | Segregation of Networks |
Firewalls shall be used to segregate and control traffic between the TSM internal network and external networks (Internet and authorized 3rd party networks), and any Demilitarized Zone (DMZ). [Core-15(b) & Core-15(c)]
An internal network perimeter shall be implemented by installing firewalls and implementing the required virtual networks to control access and information flow between TSM domains to authorized traffic. The firewall shall be capable of enforcing security policies, be configured to filter traffic between TSM domains, and block unauthorized access in accordance with TSM User Access Policy. [Core-15(b) & Core-15(c)]
Wireless Access Points (WAP) shall be segregated from the internal and private TSM networks. A firewall shall be implemented between any wireless network and TSM information systems environment. [Core-15(b) & Core-15(c)]
| 3. | Network Connection Controls |
Managed interfaces and network traffic shall be denied by default and allowed by exception (i.e., deny all, permit by exception). [Core-15(b)]
Access controls shall restrict the ability of users to connect to TSM internal network(s), in accordance with the User Access Policy and the requirements of TSM business applications and services. [Core-15(b)]
| 4. | Router & Switch Configuration |
Every router, switch and firewall connecting to a TSM production telecommunication network must meet the following configuration controls: [Core-15(b)]
| a) | Local or default user accounts shall not be configured on the router or switch. |
| b) | All default passwords of the equipment must be changed. |
| c) | Access to the administrator password shall be provided only to authorize personnel based on their job function and role. |
| d) | Unnecessary user or equipment accounts shall be disabled. |
| e) | The following services or features must be disabled unless a business justification is provided: |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#13 | Page 64 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Network Security | ||
| o | IP directed broadcasts. |
| o | Incoming packets at the router/switch sourced with invalid addresses such as RFC1918 addresses. |
| o | TCP small services. |
| o | UDP small services. |
| o | All source routing and switching. |
| o | All web services running on router. |
| o | Discovery protocol on Internet connected interfaces. |
| o | Telnet, FTP, and HTTP services. |
| o | Auto-configuration. o Discovery protocols. o Dynamic trunking. |
| o | Scripting environments, such as the TCL shell. |
| f) | Restricted access statement banner shall be presented for all forms of login whether remote or local. |
| g) | Access must be restricted to only TSM authorized personnel. |
| h) | All device updates shall be done using secure routing updates and shall adhere to the TSM Change Management process. |
| 5. | Wireless Security |
When configuring Wireless Access Points (WAP) and devices, the organization shall change the following: [Core-15(b)]
| o | Equipment administrator default password. |
| o | Vendor default encryption keys. |
| o | Encryption keys anytime anyone with knowledge of the keys leaves TSM or changes positions. |
| o | Default SNMP community strings on wireless devices. |
| o | Default passwords/passphrases on access points. |
| o | Other security-related wireless vendor defaults, if applicable. |
TSM shall monitor all authorized and unauthorized Wireless Access Points (WAP) to TSM information systems and networks. The installation of Wireless Access Points (WAP) is prohibited, unless explicitly authorized, in writing, by the Infrastructure Manager and the Information & Cyber Security Director. [Core-15(b) & Core-15(c)]
Approved Wireless Access Points (WAP) and devices shall have appropriate encryption enabled for authentication and transmission and shall be placed in secure areas. [Core- 15(b)]
| 6. | Security of Network Services |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#13 | Page 65 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Network Security | ||
Security features, service levels, and management requirements of all network services shall be identified, documented and included in any network services agreement, whether these services are provided in-house or outsourced. [Core-15(b)]
Agreed services shall be determined and regularly monitored, and the right to audit shall be agreed by management. [Core-15(b)]
| VII. | Attachments: |
N/A
| Version Control |
Effective Date
|
Approved By (include position name)
|
Amendment
|
| 1 | 09/01/2016 | ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, | 1 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#14 | Page 66 | |||
| Effective Date: 09/01/2016 | |||||
| Approval Date: 09/01/2016 | |||||
| Department: Information Security | Last Review Date: 08/11/2016 | ||||
| Policy Name: | Password Management | ||||
|
Drafted by: ▇▇▇▇ ▇▇▇▇▇▇, IT Compliance Supervisor
|
Reviewed by: ▇▇▇▇▇▇ ▇. ▇▇▇▇▇▇▇, Information & Cyber Security Director |
Approved by: ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, Chief Information Officer
|
|||
| I. | Purpose: |
The purpose of this policy is to establish the standard for creation of strong passwords, the protection of those passwords, and the frequency of change.
| II. | Scope: |
This policy applies to TSM and its subsidiaries employees, temporary workers, contractors, business partners, third party vendors and physical facilities where TSM provides services to its customers.
| III. | Policy: |
This policy help the organization prevent confidentiality and security breaches [Core-15(b)].
Triple-S Management Corporation (TSM) has developed and adopted the Password Management Policy to provide management with direction and support for the implementation strong password practices. Password are an important aspect of information security and they are designed to protect user accounts. Weak passwords may result in the compromise of TSM information systems. All TSM users are responsible for taking the steps to select a strong password and secure their passwords.
Users shall be made aware of their responsibilities for maintaining effective access controls and shall be required to follow good security practices in the selection and use of passwords and security of equipment. It is the employee's, temporary, contractors and vendor’s responsibility to protect at the maximum, that third parties have no knowledge of any of the passwords to access TSM databases, networks, applications and systems.
| IV. | Definitions: |
None
| V. | Responsibilities: |
| 1. | All Triple-S Management Corporation (TSM) and its subsidiaries employees, temporary workers, contractors, business partners and third party vendors, without exception, must comply with the information security policies. Any employee found to have violated such Policies may be subject to disciplinary actions, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated. |
| 2. | TSM reserves the right to audit networks, systems, or procedures on a periodic basis to ensure compliance with this policy. |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#14 | Page 67 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Password Management | ||
In addition, all TSM personnel shall not interfere with federal or state investigations or disciplinary proceedings by willful misrepresentation or omission of facts or by the use of threats or harassment against any person.
| 3. | Exceptions |
Any exception to the policy must be approved by the Information & Cyber Security Director or Triple-S Management in advance.
| 4. | Non-Compliance |
An employee found to have violated this policy may be subject to disciplinary action, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated.
| VI. | Procedure: |
The following practices help the organization prevent confidentiality and security breaches [Core-15(b)]:
| 1. | General Requirements: |
The following practices shall be communicated to all TSM users and followed by all employees:
| a) | Keep passwords confidential. |
| b) | Passwords shall not be displayed when entered. |
| c) | Avoid keeping a record (e.g., paper, file in the computer) of passwords. |
| d) | Change passwords whenever there is any indication of a possible system or password compromise. |
| e) | Do not share your user account or password. |
| f) | Do not provide the password to anyone for any reason. |
| g) | The use of the same password for business and non-business purposes shall be avoided. |
| h) | Select strong passwords that meet TSM Password Management Guidelines. |
| i) | Default vendor passwords shall be modified following installation of any system, software or application. |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#14 | Page 68 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Password Management | ||
| j) | The allocation of passwords shall be controlled through a formal management process. The use of third parties or unprotected (clear text) electronic mail messages shall be avoided. |
| 2. | Password Creation: |
| a) | All user-level and system-level passwords must conform to TSM strong password guidelines. |
| b) | Users must not use the same password for TSM accounts as for other non-TSM access accounts (i.e. personal ISP account, etc.). |
| c) | User accounts that have system-level privileges granted through group memberships or programs such as “sudo” (temporary privilege elevation) must have a unique password from all other accounts held by that user to access TSM systems. |
| d) | Where Simple Network Management Protocol (SNMP) is used, the community strings must be defined as something other than the standard defaults of public, private, and system and must be different from the passwords used to log in interactively. |
| 3. | Password Change and Parameters: |
This Policy specifies the minimum requirements and passwords parameters among all the system environments (network, operating system, applications and data repository, if applicable).
| a) | Lan Passwords shall be changed at least every 90 days. |
| b) | Passwords for privileged accounts (i.e. system administrators) shall be changed at least every 60 days. |
| c) | Password length must be a minimum of eight (8) characters. |
| d) | Passwords shall be easy to remember but not easily to guess, free of words included in dictionaries, free of consecutive identical characters and require a combination of alphabetic, upper and lower case characters, numbers, and special characters (combination of any three (3) of the above four (4) listed is acceptable). |
| e) | Passwords shall be prohibited from being reused for at least four (4) generations for users or six (6) generations for privileged users and at least four (4) changed characters are changed when new passwords are created. |
| f) | Temporary passwords shall be unique to an individual and shall not be guessable. |
| g) | User identity shall be verified before performing password reset process. |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#14 | Page 69 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Password Management | ||
| h) | Temporary passwords shall be changed at the first log-on. |
| i) | Temporary passwords shall be given to users in a secure manner. |
| j) | Allow a minimum of three (3) failed login attempts before disabling the accounts. |
| 4. | Password Protection: |
| a) | Passwords must not be shared with anyone. All passwords are to be treated as sensitive, Confidential TSM information. |
| b) | Users shall not reveal his/her passwords over the phone to anyone. |
| c) | Do not write passwords down or store them anywhere in your office. |
| d) | Do not store passwords in a file on a computer system without encryption. |
| e) | Do not use the "Remember Password" feature of applications (for example, web browsers). |
| f) | Any user suspecting that his/her password may have been compromised must report the incident to the ISG and change all passwords. |
| 5. | Application Development: |
Application developers must ensure that their programs contain the following security precautions:
| a) | Support authentication of individual users, not groups. |
| b) | Applications must not store passwords in clear text or in any easily reversible form. |
| c) | Shall not transmit passwords in clear text over the network. (For further information see Minimum Security Requirements Baseline). |
| VII. | Attachments: |
N/A
| Version Control |
Effective Date
|
Approved By (include position name)
|
Amendment
|
| 1 | 09/01/2016 | ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, CIO | 1 |
| 2 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#15 | Page 70 | |||
| Effective Date: 09/01/2016 | |||||
| Approval Date: 09/01/2016 | |||||
| Department: Information Security | Last Review Date: 08/11/2016 | ||||
| Policy Name: | Physical and Environmental Security | ||||
|
Drafted by: ▇▇▇▇ ▇▇▇▇▇▇, IT Compliance Supervisor
|
Reviewed by: ▇▇▇▇▇▇ ▇. ▇▇▇▇▇▇▇, Information & Cyber Security Director |
Approved by: ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, Chief Information Officer |
|||
| I. | Purpose: |
TSM has established a formal policy and supporting procedures concerning physical and environmental security to prevent loss, damage, theft or compromise of IT assets and interruption to TSM IT business functions.
| II. | Scope: |
This policy applies to TSM and its subsidiaries employees, temporary workers, contractors, business partners, third party vendors and physical facilities where TSM provides services to its customers.
| III. | Policy: |
This policy help the organization prevent confidentiality and security breaches [Core-15(b)].
Triple-S Management Corporation (TSM) has developed and adopted the Physical and Environmental Security Policy to provide management with direction and support to prevent unauthorized physical access, damage, and interference to TSM’s IT asset storage locations such as the primary data center and information.
| IV. | Definitions: |
None
| V. | Responsibilities: |
| 1. | All Triple-S Management Corporation (TSM) and its subsidiaries employees, temporary workers, contractors, business partners and third party vendors, without exception, must comply with the information security policies. Any employee found to have violated such Policies may be subject to disciplinary actions, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated. |
| 2. | TSM reserves the right to audit networks, systems, or procedures on a periodic basis to ensure compliance with this policy. |
In addition, all TSM personnel shall not interfere with federal or state investigations or disciplinary proceedings by willful misrepresentation or omission of facts or by the use of threats or harassment against any person.
| 3. | Exceptions |
Any exception to the policy must be approved by the Information & Cyber Security Director or the Corporate Security Director responsible for physical security.
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#15 | Page 71 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Physical and Environmental Security | ||
4. Non-Compliance
An employee found to have violated this policy may be subject to disciplinary action, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated.
| VI. | Procedure: |
The following practices help the organization prevent confidentiality and security breaches [Core-15(b)]:
| 1. | Physical Security Perimeter: |
| a) | Computers and IT assets that store or process sensitive and confidential business or ePHI information shall not be located in areas that are unattended or have unrestricted access by public or visitors to the facilities. |
| b) | At the data center access to a delivery and loading area from outside of the building shall be restricted to identified and authorized personnel. |
| c) | All physical security for the TSM buildings will be managed and monitored by the Real Estate & Facilities Division of TSS who have designated a Corporate Security Director to manage the physical security program for offices and facilities. |
| 2. | Physical Entry Controls to Data Center: |
Adequate physical security measures must be in implemented to protect TSM computer and communications equipment, and data from unauthorized access, disclosure, modification, destruction, lost, and misuse whether accidental or intentional.
| a) | Authorized credentials shall be issued for all personnel with access to TSM facilities. |
| b) | A list of authorized personnel with access to the Data Center shall be develop and approve. This list shall be reviewed at least quarterly. Personnel that access is no longer required shall be removed from the list. |
| c) | Access to areas where sensitive, confidential and PHI information is processed or stored shall be controlled and restricted to authorized persons only. |
| d) | Servers and communication devices should be kept in secured physical areas. Access to these areas should be restricted to authorized personnel and contractors working for TSM and who have a demonstrated need to access the area. |
| e) | Access to TSM offices should be protected and subject to monitoring (e.g. video surveillance). This may include, but not limited to, protection by PIN, card swipe devices, biometric devices, door locks and video surveillance systems. |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#15 | Page 72 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Physical and Environmental Security | ||
| f) | Access to the data center server room shall require the authorized employee to use of the assigned ID card as well as a biometric authentication method. |
| g) | Access to the data center shall restricted to authorized personnel and be subject to video surveillance. |
| h) | A visitor log shall be maintained to record all authorized visits to the data center. |
| i) | Third party support service personnel shall be granted restricted access to secure areas or covered information processing facilities only when required. This access shall be authorized and monitored. |
| j) | For the data center maintain physical access audit logs for at least two years and review the visitor records periodically but no less than monthly. |
| k) | The security access PIN number should be changed every 180 days or when an employee with knowledge of the PIN is terminated. |
| 3. | Visitors to Data Center: |
| a) | A visitor log to the data center shall be maintained. The visitor’s log records shall contain the following information: |
| o | Name and organization of the person visiting. |
| o | Signature of the visitor. o Form of identification. o Date of access. |
| o | Time of entry and departure. |
| o | Purpose of visit. |
| o | Name and organization of person visited. |
| b) | All visitors must be identified prior to gaining access to restricted areas controlled by TSM. |
| c) | All visitors must be admitted to TSM premises only for specific authorized purposes. |
| d) | All physical access shall be granted with the minimum required access needed to perform the personnel duties and job responsibilities. |
| e) | Visitors to TSM offices and the data center must be escorted and supervised at all times by an authorized TSM employee, consultant, or contractor. |
| f) | Individuals, who are neither TSM employees, nor authorized contractors, nor authorized consultants, shall not be provided access to areas where containing sensitive, confidential or PHI information. |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#15 | Page 73 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Physical and Environmental Security | ||
| g) | Entrance to the TriServe Tech, Data Center by external personnel (non-regular employees) must be pre-notified in advance to the Data Center supervisor. |
| 4. | Physical Environmental Controls: |
| a) | Physical protection measures against damage from fire, flood, earthquake, explosion, civil unrest, and others forms of natural or man-made disaster shall be designated and implemented, to protect and maintain the availability of Triple-S Management Corporation (TSM) assets like computer, communications equipment, and data from lost and/or destruction accidental or intentional. |
| b) | TSM shall develop, disseminate and review/update annually: |
| o | Formal, documented physical and environmental protection policies that addresses purpose, scope, roles, responsibilities, management commitment, coordination among organizational entities, and compliance. For further information, (refer to GTS Business Continuity Plan (BCP) and the Security Awareness & Training policy). |
| o | Formal, documented procedures to facilitate the implementation of the physical and environmental protection policy and the associated protection controls. |
| c) | The following controls shall be implemented to avoid damage from fire, flood, earthquake, explosion, civil unrest, and other forms of natural or man-made disasters: |
| o | Appropriate fire extinguishers shall be located throughout the facility. |
| o | The fire extinguishers shall be no more than 50 feet away from critical electrical components. |
| o | Fire detectors (e.g., smoke or heat activated) shall be installed on and in ceilings and floors. |
| o | Fire authorities shall be automatically notified when a fire alarm is activated. |
| 5. | Maintenance Personnel: |
All maintenance personnel access shall be authorized, monitored and validated periodically.
| 6. | Inventory of Hardware: |
| a) | TSM will ensure to maintain an up to date inventory of computer and communications equipment, removable storage media, and software under its control. At a minimum the inventory of information system components shall include manufacturer, type, serial number, and physical location. |
| b) | Procedures shall be developed, documented and implemented effectively to control the flow of equipment into and out of the organization. Business Managers shall authorize the delivery or removal of TSM information system equipment. |
| 7. | Secure Disposal or Re-Use of Equipment: |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#15 | Page 74 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Physical and Environmental Security | ||
Equipment containing storage media shall be checked to ensure that any sensitive business information and licensed software is physical destroyed or completely removed/erased using industry standard secured methods of destruction prior to disposal or re-use.
| VII. | Attachments: |
N/A
| Version Control |
Effective Date
|
Approved By (include position name)
|
Amendment
|
| 1 | 09/01/2016 | ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, CIO | 1 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#16 | Page 75 | |||
| Effective Date: 09/01/2016 | |||||
| Approval Date: 09/01/2016 | |||||
| Department: Information Security | Last Review Date: 08/11/2016 | ||||
| Policy Name: | Remote Access | ||||
|
Drafted by: ▇▇▇▇ ▇▇▇▇▇▇, IT Compliance Supervisor
|
Reviewed by: ▇▇▇▇▇▇ ▇. ▇▇▇▇▇▇▇, Information & Cyber Security Director |
Approved by: ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, Chief Information Officer
|
|||
| I. | Purpose: |
The purpose of this policy is to define requirements for connecting to TSM network from a remote location by authorized users. These requirements are designed to minimize the potential risk associated with remote connections and protect from exposure TSM IT assets.
| II. | Scope: |
This policy applies to TSM and its subsidiaries employees, temporary workers, contractors, business partners, third party vendors and physical facilities where TSM provides services to its customers.
| III. | Policy: |
This policy help the organization prevent confidentiality and security breaches [Core-15(b)].
Triple-S Management Corporation (TSM) has developed and adopted the Remote Access Policy to provide management with direction and support for the implementation of appropriate authentication methods to control access to the TSM IT assets by remote users.
| IV. | Definitions: |
| 1. | Remote Access: Any Connection to TSM network(s) or information systems that originates from a computer or device located outside of TSM network. |
| 2. | Encryption: Cryptographic transformation of data (called "plaintext") into a form (called "cipher text") that conceals the data's original meaning to prevent it from being known or used. Also, Virtual Private Network (VPN) is a method employing encryption to provide secure access to a remote computer over the Internet. |
| 3. | Authentication: Authentication is the process of confirming the correctness of the claimed identity. |
| 4. | Authorization: To allow access only to those resources which are appropriate to that entity's identity. |
| 5. | Strong password: Consists of at least eight characters (and the more characters, the stronger the password) that are a combination of letters, numbers and symbols (@, #, $, %, etc.) |
| 6. | Accountability: The quality or state of being accountable; especially: an obligation or willingness to accept responsibility or to account for one's actions. |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#16 | Page 76 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Remote Access | ||
| V. | Responsibilities: |
| 1. | All Triple-S Management Corporation (TSM) and its subsidiaries employees, temporary workers, contractors, business partners and third party vendors, without exception, must comply with the information security policies. Any employee found to have violated such Policies may be subject to disciplinary actions, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated. |
| 2. | TSM reserves the right to audit networks, systems, or procedures on a periodic basis to ensure compliance with this policy. |
In addition, all TSM personnel shall not interfere with federal or state investigations or disciplinary proceedings by willful misrepresentation or omission of facts or by the use of threats or harassment against any person.
| 3. | Exceptions |
Any exception to the policy must be approved by the Information & Cyber Security Director or Triple-S Management in advance.
| 4. | Non-Compliance |
An employee found to have violated this policy may be subject to disciplinary action, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated.
| VI. | Procedure: |
The following practices help the organization prevent confidentiality and security breaches [Core-15(b)].
Remote connections represent a high risk access method if adequate controls and management procedures are not implemented and followed. For this reason TSM have established a remote access policy and procedures to protect the organization IT assets from unauthorized access. The primary objective of this policy is to protect the confidentiality, integrity and availability of the IT assets in accordance with TSM established business objectives and regulatory requirements.
The following requirements were defined in order to access from a remote (external) location TSM’s network and IT assets. This includes connections performed to support remote working from home activities or establishing remote connections to the TSM corporate network to perform system monitoring activities, provide system support or conduct maintenance to production systems among other activities.
| 1. | General Requirements: |
| a) | Authorization to grant remote access permission will require manager approval. |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#16 | Page 77 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Remote Access | ||
| b) | The managers are responsible for recertifying on a quarterly basis the list of authorized remote access users. |
| c) | Managers must ensure that remote access is limited only to authorized users and that this type of access shall be kept to the minimum number of employees. |
| d) | All users shall have a unique identifier (user-id) to ensure proper identification and authentication. |
| e) | A stronger user authentication method must be implemented and use to authenticate remote users. Two of the following factors shall be used to conduct the remote user authentication process: |
| o | Something you know (e.g. User ID & Password) |
| o | Something you have (e.g. Symantec VIP two factor authentication token, Azure two factor authentication token) |
| o | Something you are (e.g. biometric technology) |
| f) | All remote access sessions must be monitored and audit logs of remote connections shall be protected and retained. Remote access logs shall be retained for a period of 1 year online and 3 years on backup tapes. |
| g) | Authorized users shall protect their assigned user id, password and the assigned second factor authentication method at all times and not shared with others. |
| h) | The Information Security Group (ISG) shall ensure that redundant or duplicate user IDs and second factor authentication methods are not issued. |
| i) | Regular user activities shall not be performed from privileged accounts. |
| j) | All computer devices that are connected to TSM network(s) remotely must have: |
| o | Updated anti-virus and anti-spyware software installed and active. |
| o | Updated operating system patches. |
| o | Updated application level patches (e.g. Acrobat, Flash) |
| k) | Remote access by vendors and business partners (e.g., maintenance, reports or other data access) shall be maintained in a disabled stated unless specifically authorized by management. |
| l) | Remote access by vendors and business partner shall also be immediately deactivated after use. |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#16 | Page 78 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Remote Access | ||
| m) | The remote connection shall be automatically disconnected from TSM network after 30 minutes of inactivity. |
| 2. | Access Request: |
An approved Access Request Form shall be submitted to the Information Security Group (ISG) to establish and grant remote access permission for authorized employees (Regulars and/or Temporary), prior to connecting to TSM information systems. The following practices shall be established:
| a) | The access request shall indicate a predefined date, profile based on job responsibilities or assignments to specific functions and/or resources. |
| b) | Remote access shall be restricted to authorized personnel and must be requested and be authorized by the user manager or supervisor. |
| c) | Remote user’s access rights and privileges shall be restricted to the minimum services and functions as is necessary to carry out their job role or function. |
| d) | The activity of each account can be monitored at any time and may be terminated by the ISG at any time. |
| e) | Access to Confidential, Restricted and Protected information will be limited to authorized personnel whose job responsibilities require this type of information or as determined by the Application Owner. |
| 3. | Emergency Access: |
In case of any situation where an emergency access is needed, the request will follow the established process stated on the User Access Policy.
| 4. | Access Review: |
A formal process shall be conducted at regular intervals by system owners and application owners in conjunction with ISG to confirm that remote users’ access rights remains appropriate. The review shall be documented and sign off by the applicable responsible.
Managers are responsible for recertifying on a quarterly basis the list of authorized remote access users.
| VII. | Attachments: |
ATTACHMENT E - Remote Access Procedure
| Version Control |
Effective Date
|
Approved By (include position name)
|
Amendment
|
| 1 | 09/01/2016 | ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, CIO | 1 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#17 | Page 79 | |||
| Effective Date: 09/01/2016 | |||||
| Approval Date: 09/01/2016 | |||||
| Department: Information Security | Last Review Date: 08/11/2016 | ||||
| Policy Name: | Removable Device Management | ||||
|
Drafted by: ▇▇▇▇ ▇▇▇▇▇▇, IT Compliance Supervisor
|
Reviewed by: ▇▇▇▇▇▇ ▇. ▇▇▇▇▇▇▇, Information & Cyber Security Director |
Approved by: ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, Chief Information Officer
|
|||
| I. | Purpose: |
The purpose of this policy is to establish the requirements for the use of removable devices on TSM information systems and equipment, to minimize the risk associated with loss or exposure of sensitive information such as PII, PHI and ePHI managed by TSM. The policy is also design to reduce the risk associated with malware infections, computer viruses and botnet that can be propagated on computers operated by TSM by this type of device.
| II. | Scope: |
This policy applies to TSM and its subsidiaries employees, temporary workers, contractors, business partners, third party vendors and physical facilities with access to TSM information, information systems or IT equipment (i.e. computer, server, laptop and mobile devices) and intends to store any information on removable media devices.
| III. | Policy: |
This policy help the organization prevent confidentiality and security breaches [Core-15(b)].
Triple-S Management Corporation (TSM) has developed and adopted the Removable Device Management policy, to provide management with direction and support for the implementation of safeguards to ensure the proper use of removable media devices used to store and transfer information by users who have been authorized access by TSM management to use this type of equipment for the purpose of conducting official TSM business.
| IV. | Definitions: |
| 1. | Encryption: The process of encoding a message so that it can be read only by the sender and the intended recipient. |
| 2. | Malware: Is defined as software of malicious intent/impact such as viruses, worms, and spyware. |
| 3. | Removable Media: Any type of device that can be removed from a computer while the system is running. |
| 4. | Sensitive Information: Information that is protected against unwarranted disclosure. Access to sensitive information should be safeguarded. |
| 5. | USB Flash Drive: A memory data storage device integrated with a USB (universal serial bus) interface. They are typically small, lightweight, removable and rewritable. |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#17 | Page 80 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Removable Device Management | ||
| 6. | Personal Identification information (PII): An individual’s name together with Social Security number, drivers’ license number, or certain bank or credit account information. |
| 7. | Protected Health Information (PHI): Protected health information, generally refer to demographic information, medical history, test and laboratory results, insurance information and other data that a healthcare professional collects to identify an individual and determine appropriate care. |
| 8. | Electronic Protected Health Information (ePHI): Refers to any protected health information (PHI) that is covered under Health Insurance Portability and Accountability Act of 1996 (HIPAA) security regulations and is produced, saved, transferred or received in an electronic form. |
| V. | Responsibilities: |
| 1. | All Triple-S Management Corporation (TSM) and its subsidiaries employees, temporary workers, contractors, business partners and third party vendors, without exception, must comply with the information security policies. Any employee found to have violated such Policies may be subject to disciplinary actions, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated. |
| 2. | TSM reserves the right to audit networks, systems, or procedures on a periodic basis to ensure compliance with this policy. |
In addition, all TSM personnel shall not interfere with federal or state investigations or disciplinary proceedings by willful misrepresentation or omission of facts or by the use of threats or harassment against any person.
| 3. | Exceptions |
Any exception to the policy must be approved by the Information & Cyber Security Director in advance.
| 4. | Non-Compliance |
An employee found to have violated this policy may be subject to disciplinary action, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated.
| VI. | Procedure: |
The following practices help the organization prevent confidentiality and security breaches [Core-15(b)]:
| 1. | General Requirements: |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#17 | Page 81 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Removable Device Management | ||
| a) | TSM shall implement safeguards and procedures for the proper management of removable media. |
| b) | Procedures and controls shall be designed and implemented to prevent the unauthorized use of removable media storage devices such as: |
| o | USB Memory Sticks (also known as pen drives or flash drives). |
| o | External Hard Drives. |
| o | Media Card Readers. |
| o | CDs. |
| o | DVDs. |
| o | Embedded Microchips (including Smart Cards and Mobile Phone SIM Cards). |
| o | Smart and Cellular Phones. |
| o | MP3 Players. |
| o | Digital Cameras. |
| o | Backup tapes. |
| c) | All PII or PHI data stored on removable media devices must be encrypted by the TSM approved removable media encryption tool. |
| d) | Authorized users are responsible for the appropriate use and protection of the removable media from theft or lost. |
| e) | Authorized users must be aware that TSM can audit the transfer of data files to and from all removable media devices and TSM IT equipment by using the approved Data Loss Prevention (DLP) tool |
| f) | Confidential, PII, PHI or ePHI information should be stored on removable media only when required in for the performance of TSM personnel assigned duties. |
| g) | All Confidential, PII, PHI or ePHI information to be stored on removable media, must be encrypted in accordance with the TSM Encryption Policy. |
| h) | Media containing confidential, PII, PHI or ePHI information shall be physically secured until the media is destroyed and/or sanitized. |
| i) | Virus and malware checking software must be used when the removable media device is connected to TSM equipment and systems. |
| j) | Only data that is authorized and necessary to be transferred should be saved on to the removable media device. |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#17 | Page 82 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Removable Device Management | ||
| k) | Removable media devices must not to be used for archiving or storing records as an alternative to the approved computer systems such used by TSM. |
| l) | Special care must be taken to physically protect the removable media device and stored data from loss, theft or damage. |
| 2. | Restricted Access to Removable Media: |
The use of removable media devices shall be approved by the department manager and by the Information & Cyber Security Director of TriServe.
The Department Manager must document the user access request by using the Removable Device Access Form.
The Department Managers are responsible for re-certifying the list of authorized users to access removal media storage devices on an annual basis.
| 3. | Preventing Information Security Incidents: |
The data in transit, storage or held on any removable media devices must be given appropriate security according to the type of data and its sensitivity. Encryption and password control must be applied for PII and PHI information.
PII, PHI and/or TSM confidential or sensitive data must not be transmitted or stored on Bluetooth enabled devices.
TSM users are require to immediately report any loss or theft of TSM information or equipment to the ISG and/or IT Service Desk.
| 4. | Bluetooth Enabled Device’s: |
All Bluetooth devices must use Secure Simple Pairing with encryption enabled. Bluetooth users must only access TSM information systems using approved Bluetooth device hardware, software, solutions, and connections.
| 5. | Disposal of Removable Media Devices: |
Removable media devices that are no longer required, or have become damaged, must be disposed securely to avoid data leakage.
| VII. | Attachments: |
N/A
| Version Control |
Effective Date
|
Approved By (include position name)
|
Amendment
|
| 1 | 09/01/2016 | ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, CIO | 1 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#18 | Page 83 | |||
| Effective Date: 09/01/2016 | |||||
| Approval Date: 09/01/2016 | |||||
| Department: Information Security | Last Review Date: 08/11/2016 | ||||
| Policy Name: | Retention and Disposal | ||||
|
Drafted by: ▇▇▇▇ ▇▇▇▇▇▇, IT Compliance Supervisor
|
Reviewed by: ▇▇▇▇▇▇ ▇. ▇▇▇▇▇▇▇, Information & Cyber Security Director |
Approved by: ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, Chief Information Officer
|
|||
| I. | Purpose: |
The purpose of this policy is to define requirements for data retention and disposal of technology equipment and records. These requirements are designed to minimize the potential exposure to TSM from damages which may result from unauthorized access, disclosure and use of TSM records containing sensitive, confidential, and ePHI information.
| II. | Scope: |
This policy applies to all TSM and its subsidiaries employees, temporary workers, contractors, business partners, third party vendors and physical facilities where TSM provides services to its customers.
| III. | Policy: |
This policy supports the organization plan for storage, maintenance and destruction information [Core-13(b)].
Triple-S Management Corporation (TSM) has developed and adopted the Retention and Disposal Policy to provide management with direction and support to protect important records containing sensitive, confidential, and ePHI information from loss, destruction, and falsification, in accordance with business requirements, laws and regulations.
| IV. | Definitions: |
| 1. | Record: Any type of record created or received in the course of TSM business, including, but not limited to, paper, e-mail, any type of electronic file or data, plans, and audio/ video recordings, etc. |
| 2. | Disk wiping: Is a software-based method of overwriting the data that aims to completely destroy all electronic data residing on a hard disk drive or other digital media. |
| 3. | Degaussing: Is a technique for destroying data on magnetic storage tapes. Can also be used to erase the contents of a hard drive, USB thumb drive or a smart phone. |
| 4. | Active Record: Any record that is currently in use by TSM and is required to support the business operational functions and client’s services. |
| 5. | Archival Record: A record that is not required to be retained on premise and which can be moved to a long term archival method. |
| 6. | Electronic Record: A record kept in an electronic format, such as a word processing document, a spreadsheet, a database, a scanned or imaged document, and any other type of |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#18 | Page 84 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Retention and Disposal | ||
file stored on a computer, server or mainframe storage device or medium, or on any external or off-site storage medium.
| 7. | Inactive Record: A record that is no longer an Active Record but must be maintained pursuant to the Records Retention Program requirements. |
| 8. | Personal Identifiable Information (PII), Personal Health Information (PHI) and Electronic Personal Health Information (ePHI) records: PII, PHI and ePHI are considered highly sensitive and confidential and must be safeguarded and secured at all times. |
| 9. | Hard Copy Record: Any physical representation of information, most often associated with paper printouts. |
| 10. | Electronic Record: Information captured and managed through electronic means, and which may or may not have a paper record to back it up. Also called machine readable record. Electronic records can be stored throughout an organization in a variety of ways such as databases, directories, file systems, applications, hard drives, and email accounts. |
| V. | Responsibilities: |
| 1. | All Triple-S Management Corporation (TSM) and its subsidiaries employees, temporary workers, contractors, business partners and third party vendors, without exception, must comply with the information security policies. Any employee found to have violated such Policies may be subject to disciplinary actions, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated. Triple-S Management Corporation (TSM) reserves the right to audit networks, systems, or procedures on a periodic basis to ensure compliance with this policy. |
In addition, all TSM personnel shall not interfere with federal or state investigations or disciplinary proceedings by willful misrepresentation or omission of facts or by the use of threats or harassment against any person.
| 2. | Exceptions |
The Information & Cyber Security Director or Triple-S Management must approve any exception to the policy in advance.
| 3. | Non-Compliance |
An employee found to have violated this policy may be subject to disciplinary action, up to and including termination of employment.
| VI. | Procedure: |
This procedure supports the organization process for storage, maintenance and destruction information [Core-13(b)].
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#18 | Page 85 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Retention and Disposal | ||
| 1. | General Requirements: |
| a) | TSM shall establish documented procedures for the retention and disposal of data, technological equipment and resources of electronic data storage media. This includes, but are not limited to hard disks, tapes, cartridges, CDs, and USB drives. |
| b) | TSM shall establish a formal record retention program that addresses, record storage, access, retention, and destruction. The program shall also specify the retention period for electronic storage media (i.e. backup tapes). |
| c) | Procedures shall be implemented meeting the requirements of the define retention schedule by identifying essential records types and periods of retention, an inventory of sources of key information, a disposal of information that exceeds the retention period and secure disposal of equipment. |
| 2. | Record Retention: |
| a) | Electronic Communication (Email): Email communications shall be retained for a period of 6 months. E-mail messages containing approvals or representing TSM agreements with outside entities, shall be retained by TSM departments according to the retention guidelines set in this policy (either electronic or paper). For further information on retention periods refer to the Backup and Retention Policy. |
| b) | Document Retention Periods: For further information on document retention periods refer to the Documents Retention Policy #V-14. |
| 3. | Disposal: |
| a) | All media shall be disposed of securely and safely when is no longer required by TSM business or legal requirements, using formal documented procedures. All information shall be rendered unusable, unreadable, or indecipherable on system media, both digital and non-digital, prior to disposal or release for reuse. Media containing sensitive information that cannot be sanitized shall be destroyed. |
| 4. | Secure Disposal Techniques: |
| a) | The following are appropriate techniques to securely remove information: |
| o | Disk Wiping |
| o | Degaussing |
| b) | The following are appropriate techniques to securely destroy electronic and hard copy media: |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#18 | Page 86 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Retention and Disposal | ||
| o | Shredding disk platters |
| o | Disintegration |
| o | Grinding surfaces |
| o | Incineration |
| o | Pulverization |
| o | Melting |
| 5. | Document Disposal: |
| a) | Paper documents may be disposed (destroyed) after being digitized as long as it is verified that the document to be printed is clear, legible, integrity remains intact and is a true and exact copy of the original. |
| b) | All documents may be destroyed after fulfilling the corresponding period of conservation and if there are not legal hold periods related to the document content. |
| c) | A log of the destroyed documents shall be keep to maintain a documented process and tracking of all destroyed documents covered by this policy. All document destruction for in scope legal cases or investigations shall be halted, after receiving notification of the Legal Division for hold notification. |
| d) | All paper sensitive/confidential documents shall be placed in the official shredder bins/recycling bins or placed in the locked secured disposal recycling bins contracted by the organization for the secured destruction of the documents. |
| 6. | Secure Equipment Disposal: |
| a) | Surplus equipment shall be stored securely while not in use, and shall be disposed of or sanitized when no longer required. |
| b) | Sanitization of desktop computers and portable media will be managed by Desktop Management Group (DMG). |
| c) | All items of equipment containing storage media shall be checked to ensure that any covered information and licensed software has been removed or securely overwritten prior to disposal. |
| d) | Devices containing covered information shall be physically destroyed or the information shall be destroyed, deleted or overwritten using techniques to make the original information non-retrievable rather than using the standard delete or format function. |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#18 | Page 87 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Retention and Disposal | ||
| e) | Disposal without sanitization shall be considered only if information disclosure would have no impact on TSM business, would not result in damage to TSM assets, and would not result in financial loss or harm to any customer, employees and business associates. |
| 7. | Equipment Donation and/or Transfers |
| a) | TSM personnel shall sanitized or destroyed information system digital media before its disposal or release for reuse outside of TSM premises, to prevent unauthorized individuals from gaining access to and using the information contained on the media. |
| VII. | Attachments: |
ATTACHMENT F - Retention & Disposal Procedure [Core-13(b)]
| Version Control |
Effective Date
|
Approved By (include position name)
|
Amendment
|
| 1 | 09/01/2016 | ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, CIO | 1 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#19 | Page 88 | |||
| Effective Date: 09/01/2016 | |||||
| Approval Date: 09/01/2016 | |||||
| Department: Information Security | Last Review Date: 08/11/2016 | ||||
| Policy Name: | Security Awareness and Training | ||||
|
Drafted by: ▇▇▇▇ ▇▇▇▇▇▇, IT Compliance Supervisor
|
Reviewed by: ▇▇▇▇▇▇ ▇. ▇▇▇▇▇▇▇, Information & Cyber Security Director |
Approved by: ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, Chief Information Officer
|
|||
| I. | Purpose: |
The purpose of this policy is to define the requirements to ensure that users of TSM systems and third party contractors receive appropriate awareness and training to ensure the protection of TSM’s IT assets and information. [Core-15(b)]
| II. | Scope: |
This policy applies to TSM and its subsidiaries employees, temporary workers, contractors, business partners, third party vendors and physical facilities where TSM provides services to its customers.
| III. | Policy: |
Triple-S Management Corporation (TSM) has developed and adopted the Security Awareness and Training Policy to provide management with direction and support for the implementation of a security awareness training program including providing regular updates of TSM information security policies and procedures required to protect the organization IT assets. [Core-15(b)]
| IV. | Definitions: |
None
| V. | Responsibilities: |
| 1. | All Triple-S Management Corporation (TSM) and its subsidiaries employees, temporary workers, contractors, business partners and third party vendors, without exception, must comply with the information security policies. Any employee found to have violated such Policies may be subject to disciplinary actions, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated. |
| 2. | TSM reserves the right to audit networks, systems, or procedures on a periodic basis to ensure compliance with this policy. |
In addition, all TSM personnel shall not interfere with federal or state investigations or disciplinary proceedings by willful misrepresentation or omission of facts or by the use of threats or harassment against any person.
| 3. | Exceptions |
Any exception to the policy must be approved by the Information & Cyber Security Director in advance.
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#19 | Page 89 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Security Awareness and Training | ||
| 4. | Non-Compliance |
An employee found to have violated this policy may be subject to disciplinary action, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated.
| VI. | Procedure: |
TSM shall define and implement security awareness, training, and education programs for internal use as well as with applicable third parties to ensure that all users are appropriately trained in the organization Information Security Policies periodically. The following requirements shall be considered: [Core-15(b)]
| 1. | All employees of TSM, contractors and third party users shall receive appropriate Information Security training. [Core-15(b)] |
| 2. | The Information Security Group (ISG) shall provide regular updates in the organization Information Security policies and procedures as considered relevant for the employee job functions and responsibilities in TSM and its subsidiaries. [Core-15(b)] |
| 3. | ISG shall develop an Information Security Training and Awareness program to support the employee onboarding process of TSM and its subsidiaries and affiliates. [Core-15(b)] |
| 4. | ISG shall review and update the Information Security Training and Awareness program on an annual basis to ensure compliance with local and federal regulations. [Core-15(b)] |
| 5. | The Information Security Training and Awareness, which must be part of the onboarding process, will include employees as well as contractors, and third party service providers that may come into contact with sensitive information. [Core-15(b)] |
| 6. | TSM must maintain record of each individual who completes the on-boarding process and the Information Security Training module. The training records must be filed for at least five years thereafter. [Core-15(b)] |
| 7. | The ISG in coordination with the Human Resources training center will coordinate providing the employee with a refresher training at least every year. [Core-15(b)] |
| 8. | The organization training center will keep track of the employees who completed the training. [Core-15(b)] |
| 9. | Employees, contractors and any other third party, must acknowledge that they received the training and that they are responsible to comply with it through a formal and documented signoff. [Core-15(b)] |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#19 | Page 90 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Security Awareness and Training | ||
| 10. | TSM security personnel shall receive specialized security education and training appropriate to their role/responsibilities. [Core-15(b)]. |
| 11. | Personnel from the Information Security Group (ISG) shall be required to participate in information system security training for the following functions: [Core-15(b)] |
| o | Before engaging in user provisioning activities. |
| o | When required due to new threats. |
| o | Changes in role, employee transfers to the information security unit will require a training before officially starting his/her position. |
| 12. | At least, on an annual basis, refresher training to all security personnel will be conducted to ensure knowledge keeps relevant considering new threats and changes. [Core-15(b)] |
| 13. | TSM shall incorporate simulated events into incident response training to ensure effective response in critical events. [Core-15(b)] |
| 14. | All third parties that provide and/or manage critical applications (i.e. for handling claims – [***]) must provide training or training materials on the correct use and operation of security functions and controls of the applications or systems. [Core-15(b)] |
| 15. | Awareness training shall include a formal introduction to the organizations security and privacy policies, state and federal laws. [Core-15(b)] |
| VII. | Attachments: |
N/A
| Version Control |
Effective Date
|
Approved By (include position name)
|
Amendment
|
| 1 | 09/01/2016 | ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, | 1 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#20 | Page 91 | |||
| Effective Date: 09/01/2016 | |||||
| Approval Date: 09/01/2016 | |||||
| Department: Information Security | Last Review Date: 08/11/2016 | ||||
| Policy Name: | Security Monitoring Policy | ||||
|
Drafted by: ▇▇▇▇ ▇▇▇▇▇▇, IT Compliance Supervisor
|
Reviewed by: ▇▇▇▇▇▇ ▇. ▇▇▇▇▇▇▇, Information & Cyber Security Director |
Approved by: ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, CIO |
|||
| I. | Purpose: |
The purpose of this policy is to ensure that information security events are recorded and monitored to detect unauthorized system activities in compliance with applicable laws and regulations.
| II. | Scope: |
This policy applies to TSM and its subsidiaries employees, temporary workers, contractors, business partners, third party vendors and physical facilities where TSM provides services to its customers.
| III. | Policy: |
This policy help the organization detect, contain and correct confidentiality and security violations [Core-15(c)].
Triple-S Management Corporation (TSM) has developed and adopted the Security Monitoring Policy to provide management with direction and support to ensure that information security events are recorded and monitored to detect unauthorized system activities in compliance with applicable laws and regulations.
Procedures for monitoring the use of IT assets shall be established to check for use and effectiveness of implemented controls. The results of the monitoring activities shall be reviewed regularly.
| IV. | Definitions: |
| 1. | Event: Something that occurs within a system or network. |
| 2. | Log: A record of the events occurring within an organization’s systems and networks. |
| 3. | Log Archival: Retaining logs for an extended period of time, typically on removable media. |
| 4. | IPS: A proactive protection technology that provides security at the network level. |
| 5. | Clock Synchronization: Process of precisely coordinating or matching two or more activities, devices, or processes in time. |
| V. | Responsibilities: |
| 1. | All Triple-S Management Corporation (TSM) and its subsidiaries employees, temporary workers, contractors, business partners and third party vendors, without exception, must comply with the information security policies. Any employee found to have violated such |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#20 | Page 92 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Security Monitoring Policy | ||
Policies may be subject to disciplinary actions, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated. Triple-S Management Corporation (TSM) reserves the right to audit networks, systems, or procedures on a periodic basis to ensure compliance with this policy.
In addition, all TSM personnel shall not interfere with federal or state investigations or disciplinary proceedings by willful misrepresentation or omission of facts or by the use of threats or harassment against any person.
| 2. | Exceptions |
The Information & Cyber Security Director or Triple-S Management must approve any exception to the policy in advance.
| 3. | Non-Compliance |
An employee found to have violated this policy may be subject to disciplinary action, up to and including termination of employment.
| VI. | Procedure: |
This procedure help the organization detect, contain and correct confidentiality and security violations [Core-15(c)].
| 1. | General Requirements: |
| a) | All users should know that all generated information through TSM networks and systems is property of TSM. |
| b) | Telecommunication networks, computers, internet and email traffic shall be monitored by members of the Information Security Group (ISG), or third parties contracted in support of the Information Security Group monitoring function. |
| c) | All systems, applications and databases shall be configured with audit logs enabled at each of the following levels: |
| a. | Operation system and admin activities audit log |
| b. | Application event level audit log |
| c. | Database event level audit log |
| d) | All audit logs shall be kept secure and be protected from unauthorized deletion or alteration. |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#20 | Page 93 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Security Monitoring Policy | ||
| e) | Audit logs shall be protected against tampering and unauthorized access. |
| f) | Audit logs shall be accessible to authorized personnel of the ISG. |
| g) | Audit logs must be backup and retained in accordance with the retention periods defined by the Retention Officer. |
| h) | Security event logging and monitoring of TSM systems shall be carried out in order to detect suspicious activities that could impact the confidentiality, integrity and availability of the IT assets and the data stored. |
| i) | Authorized access and unauthorized access attempts in systems that manage PHI and/or PII information and/or company financial information shall be logged. |
| j) | System administrator and system operator activities shall be logged and regularly reviewed. |
| k) | Suspicious events shall be evaluated and categorized appropriately. If an event is determined to be an attack or is categorized as a security incident, it shall be investigated and reported to affected parties according to the IT & Cyber Security Incident Response Plan. |
| l) | The results of the monitoring activities shall be reviewed periodically. |
| m) | The clocks of all relevant information processing systems within TSM or security domain shall be synchronized with an agreed accurate time source to support tracing and reconstitution of activity timelines. |
| 2. | Monitoring: |
| a) | TSM shall implement the following safeguards and mechanisms to ensure the confidentiality, integrity and availability of TSM networks and information systems. Specific network perimeter controls include: |
| a. | Network Firewalls: Firewalls are frequently used to prevent unauthorized Internet users from accessing private networks connected to the Internet, especially intranets. All messages entering or leaving the intranet pass through the firewall, which examines each message and blocks those that do not meet the TSM security criteria. |
| b. | Application Level Firewall: An application firewall is a form of firewall that controls input, output, and/or access from, to, or by an application or service. It operates |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#20 | Page 94 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Security Monitoring Policy | ||
by monitoring and potentially blocking the input, output, or system service calls that do not meet the configured policy of the firewall.
| c. | Intrusion Detection System (IDS) and Intrusion Prevention Systems (IPS): To provide automated real-time identification of unauthorized use, misuse, and abuse of computer assets by internal or external network users. Logs alarms, alerts and functions shall be monitored and reviewed on a regular basis and anomalies/trends shall be identified, analyzed and reported. |
| d. | Network Traffic Monitoring: Firewall logs, alerts and network traffic shall be monitored to ensure identified issues are reviewed and resolved on time. Firewall rules shall be documented and reviewed on a quarterly basis. |
| e. | Endpoints: Detection and prevention controls to protect the endpoints with anti- virus protection. |
| f. | Internet Browsing: The Internet use shall be monitored from all computers and devices connected to the TSM network and Web Content Filter technologies shall be used to protect users. |
| g. | Email: Emails shall be monitored from all users to ensure that sensitive information is kept confidential and technology is in place to protect from malware. |
| b) | The following monitoring frequencies have been implemented are followed: |
| Security Device | Monitoring Frequency |
| Network Firewalls | 7x24x365 |
| Application Level Firewall | 7x24x365 |
| Intrusion Detection System (IDS) and Intrusion Prevention Systems (IPS) |
7x24x365
|
| Network Traffic Monitoring | 7x24x365 |
| Endpoints | Daily for anti-virus status |
| Internet Browsing | On demand for internal investigations |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#20 | Page 95 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Security Monitoring Policy | ||
|
|
Daily for suspicious email attachment. On demand for internal investigations. |
| 3. | Audit Logging: |
| a) | Audit logs recording user activities, exceptions, and security events shall be generated and stored, in accordance with TSM record retention policy requirements and procedures, to assist in investigations and access control monitoring processes. |
| b) | Information systems processing PII, PHI, financial and employee sensitive information shall generate audit log records each time a user accesses, creates, updates, or archives the information via the system. The audit logs shall include: |
| a. | Unique user identifier. |
| b. | A unique data subject (e.g., the patient) identifier. |
| c. | Function performed by the user (e.g., log-in, record creation, access, update, etc.) |
| d. | Time and date when the function was performed. |
| e. | Type of event that occurred (e.g., success or failure). |
| f. | Event Information (e.g., files handled). |
| g. | The account(s) and administrator(s) or operator(s) involved (when applicable) |
| h. | Process(es) involved. |
| i. | Before and after values when action involves updating a data element, if feasible. |
| c) | Grant, modify, or revoke access rights, including adding a new user or group, changing user privilege levels, changing file permissions, changing database object permissions, changing firewall rules, and user password changes. |
| d) | System, network, or services configuration changes, including installation of software patches and updates, or other installed software changes. |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#20 | Page 96 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Security Monitoring Policy | ||
| e) | System administrator and system operator activities shall be logged and regularly reviewed. |
| 4. | Protection of Audit Log Information: |
| a) | Access to TSM system audit tools and audit trails shall be safeguarded from unauthorized access and used to prevent misuse or compromise of logs. Authorized and unauthorized access attempts to the audit system and audit trails shall be logged and protected from modification. |
| b) | Logging controls shall protect against unauthorized changes and promptly back up of audit trail files to a centralized log server or media that is difficult to alter. |
| VII. | Attachments: |
ATTACHMENT G - IT & Cyber Security Incident Response Plan [Core-15(c)]
| Version Control |
Effective Date
|
Approved By (include position name)
|
Amendment
|
| 1 | 09/01/2016 | ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, CIO | 1 |
| 2 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#21 | Page 97 | |||
| Effective Date: 09/01/2016 | |||||
| Approval Date: 09/01/2016 | |||||
| Department: Information Security | Last Review Date: 08/11/2016 | ||||
| Policy Name: | Technical Vulnerability Management Policy | ||||
|
Drafted by: ▇▇▇▇ ▇▇▇▇▇▇, IT Compliance Supervisor
|
Reviewed by: ▇▇▇▇▇▇ ▇. ▇▇▇▇▇▇▇, Information & Cyber Security Director |
Approved by: ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, Chief Information Officer
|
|||
| I. | Purpose: |
The purpose of this policy is to define requirements to manage and reduce risks that could result from the exploitation of technical vulnerabilities by implementing an effective, systematic, and repeatable process with measurements included to confirm its effectiveness.
| II. | Scope: |
This policy applies to TSM and its subsidiaries employees, temporary workers, contractors, business partners, third party vendors and physical facilities where TSM provides services to its customers.
| III. | Policy: |
This policy help the organization assess the potential risks and vulnerabilities to the confidentiality, integrity and availability of information systems [Core-15(a)].
Triple-S Management Corporation (TSM) has developed and adopted the Technical Vulnerability Management Policy to provide management with direction and support to assess and manage technical vulnerabilities that could impact ePHI confidentiality, integrity and availability.
| IV. | Definitions: |
Vulnerability: A weakness of an asset or group of assets that can be exploited by one or more threats.
| V. | Responsibilities: |
| 1. | All Triple-S Management Corporation (TSM) and its subsidiaries employees, temporary workers, contractors, business partners and third party vendors, without exception, must comply with the information security policies. Any employee found to have violated such Policies may be subject to disciplinary actions, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated. Triple-S Management Corporation (TSM) reserves the right to audit networks, systems, or procedures on a periodic basis to ensure compliance with this policy. |
In addition, all TSM personnel shall not interfere with federal or state investigations or disciplinary proceedings by willful misrepresentation or omission of facts or by the use of threats or harassment against any person.
| 2. | Exceptions |
The Information & Cyber Security Director or Triple-S Management must approve any exception to the policy in advance.
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#21 | Page 98 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Technical Vulnerability Management Policy | ||
| 3. | Non-Compliance |
An employee found to have violated this policy may be subject to disciplinary action, up to and including termination of employment.
| VI. | Procedure: |
The following practices help the organization assess the potential risks and vulnerabilities to the confidentiality, integrity and availability of information systems [Core-15(a)].
| 1. | TSM shall implement a technical vulnerability management process that includes periodic vulnerability assessment activities for the in scope systems. |
| 2. | TSM has adopted the following frequency for conducting the external and internal vulnerability and penetrations assessment of the organization IT assets: |
| Type of Assessment | Frequency |
| External | Quarterly |
| Internal | Twice Per Fiscal Year |
| 3. | Mitigation activity shall be prioritized based on the severity of the vulnerability, the current threat environment and the business use of the vulnerable asset. |
| 4. | Shielding shall be used to protect vulnerable assets until mitigation is completed, if applicable. |
| 5. | The root cause of vulnerabilities shall be identified and eliminated, whenever applicable, through improvements in network and server configuration policies, and better change management and administrative processes. |
| 6. | TSM shall develop applications based on secure coding guidelines to prevent common coding vulnerabilities in software development applicable to internal and external public facing web applications and interfaces. |
| 7. | TSM system and application configurations standards shall be consistent with industry- accepted system hardening standards. Refer to TSM System Hardening Guidelines checklist. |
| 8. | The following activities shall be adopted within the technical vulnerability management process and roles and responsibilities defined and established: |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#21 | Page 99 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Technical Vulnerability Management Policy | ||
| a) | Discovery: To identify new technical vulnerabilities using vulnerability scans and ethical hacking assessments performed by a third-party. |
| b) | Prioritization: The prioritization activities shall be based on external threat information and internal risk rating related to the affected information asset and with a predefined inventory of systems. Based on its relevance, identified vulnerabilities shall be sorted or discarded and then prioritized. |
| c) | Shielding/Mitigation: Current IT techniques and processes shall be used to shield vulnerable assets until mitigation work is completed. High-priority vulnerabilities shall be mitigated immediately and the root causes eliminated. |
| d) | Test/Change Management: Before the implementation into the production environment, and whenever applicable, the new countermeasure or patch shall be tested in a test environment. Appropriate change management procedures should be followed and a patch calendar scheduled shall be in place. |
| e) | Monitoring: Periodically, monitor the security state of the IT environment and the current status of vulnerability mitigation activities. The discovery step need to be continuous, and all subsequent vulnerability management steps should be repeated as part of an ongoing process. |
| VII. | Attachments: |
N/A
| Version Control |
Effective Date
|
Approved By (include position name)
|
Amendment
|
| 1 | 09/01/2016 | ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, CIO | 1 |
| 2 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#22 | Page 100 | |||
| Effective Date: 09/01/2016 | |||||
| Approval Date: 09/01/2016 | |||||
| Department: Information Security | Last Review Date: 08/11/2016 | ||||
| Policy Name: | Teleworking | ||||
|
Drafted by: ▇▇▇▇ ▇▇▇▇▇▇, IT Compliance Supervisor
|
Reviewed by: ▇▇▇▇▇▇ ▇. ▇▇▇▇▇▇▇, Information & Cyber Security Director |
Approved by: ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, Chief Information Officer
|
|||
| I. | Purpose: |
The purpose of this policy is to define requirements for managing and reducing risks associated with teleworking activities. The policy and the requirements are designed to minimize the potential exposure of TSM IT assets from damages which may result from theft of equipment and information, the unauthorized disclosure of information including ePHI, unauthorized remote access to the organization’s internal systems and/or misuse of the IT assets of the organization.
| II. | Scope: |
This policy applies to TSM and its subsidiaries employees, temporary workers, contractors, business partners, third party vendors and physical facilities where TSM provides services to its customers.
| III. | Policy: |
This policy help the organization prevent confidentiality and security breaches [Core-15(b)] and [Core-13(b)].
Triple-S Management Corporation (TSM) has developed and adopted the Teleworking Policy to provide management with direction and support for the implementation of appropriate security measures for employees working from remote locations and working from home.
| IV. | Definitions: |
| 1. | Teleworking: Is defined as working at home or at other off-site locations that are linked electronically (via computer, fax, etc.) to a central office or principal place of employment. |
| 2. | VPN: A method employing encryption to provide secure access to a remote computer over the Internet. |
| 3. | Encryption: Cryptographic transformation of data (called "plaintext") into a form (called "cipher text") that conceals the data's original meaning to prevent it from being known or used. |
| 4. | Remote Access: Any Connection to TSM network(s) or information systems that originates from a computer or device located outside of TSM network. |
| 5. | Session locking: Means locking screens on workstations after a certain amount of inactivity. |
| V. | Responsibilities: |
| 1. | All Triple-S Management Corporation (TSM) and its subsidiaries employees, temporary workers, contractors, business partners and third party vendors, without exception, must |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#22 | Page 101 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Teleworking | ||
comply with the information security policies. Any employee found to have violated such Policies may be subject to disciplinary actions, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated.
| 2. | TSM reserves the right to audit networks, systems, or procedures on a periodic basis to ensure compliance with this policy. |
In addition, all TSM personnel shall not interfere with federal or state investigations or disciplinary proceedings by willful misrepresentation or omission of facts or by the use of threats or harassment against any person.
| 3. | Exceptions |
Any exception to the policy must be approved by the Information & Cyber Security Director in advance.
| 4. | Non-Compliance |
An employee found to have violated this policy may be subject to disciplinary action, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated.
| VI. | Procedure: |
The following practices help the organization prevent confidentiality and security breaches [Core-15(b)]:
TSM shall only authorize teleworking activities if they comply with TSM’s security requirements and controls for remote access connections. TSM shall consider that any teleworking facility is essentially an extension of the TSM network and any teleworking user that connects without appropriate security controls could result in the exposure of company and ePHI confidential information resulting in a signification impact to the entire organization. At a minimum the following requirements shall be implemented for authorized teleworking users:
| 1. | General Requirements: |
| a) | Only authorize teleworking users shall be allowed. |
| b) | Business managers are responsible for requesting and authorizing the access based upon the needs of the department for the user to perform teleworking functions. |
| c) | TSM business managers shall ensure that authorized teleworking users read and acknowledged understanding the organization Employee Manual and Information Security policies for performing teleworking functions. |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#22 | Page 102 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Teleworking | ||
| d) | Training on Information Security (IS) and privacy responsibilities shall be required for all authorized teleworking users. |
| e) | TSM will provide corporate approved computers (i.e. laptops) to teleworking authorized users. The assigned computer will comply with the organization standard image and security controls including but not limited to: |
| o | Corporate approved MS Windows license and image. |
| o | Corporate approved anti-virus, anti-malware and firewall system. |
| o | Corporate approved Data Loss Prevention system. |
| o | Corporate approved encryption system. |
| o | Corporate approved Virtual Private Connection (VPN) system. |
| f) | Authorized teleworking users shall use the assigned corporate equipment to conduct teleworking functions. |
| g) | TSM computer equipment located at the user teleworking location shall not be used for personal activities or lent to friends or family members. |
| h) | Teleworking users shall not install unauthorized software in the assigned teleworking equipment. |
| i) | TSM teleworking equipment and media taken off the premises shall be encrypted and not be left unattended in unsecured places or high risk locations such as inside automobiles. |
| j) | Adequate insurance coverage shall be in place to protect off-site TSM computer equipment. |
| k) | TSM maintains ownership over the corporate assets (e.g. computer, peripherals, etc.) used by teleworking authorized personnel. |
| 2. | Account Administration: |
| a) | Teleworking user access requests must also meet the User Access Policy and Remote Access Policy requirements for secure remote connections. |
| b) | Business manager are responsible for requesting revocation of remote accesses to TSM systems, and returning TSM assigned equipment when the teleworking activities are terminated. |
| c) | Business managers are responsible for the timely notification of employee terminations and transfers to the Human Resources department. |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#22 | Page 103 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Teleworking | ||
| 3. | Teleworking User Requirements: |
| a) | Verifiable unique IDs shall be required for all teleworker users accessing TSM network by a remote connection. |
| b) | Authorized teleworkers must use the Symantec VIP two factor authentication system establish the remote connection to TSM network. |
| c) | The authorized users is responsible for maintaining appropriate protection of at the teleworking site to protect the assigned equipment against theft, the unauthorized disclosure of information, and the unauthorized remote access to TSM internal systems. |
| d) | The use of home WiFi networks is permitted as long as the WiFi is password protected and the WiFi encryption protocol is enabled. The WPA encryption protocol is the minimum required. |
| e) | ePHI information shall never be stored outside the corporate provided equipment. |
| f) | ePHI or company confidential information shall never be printed when working from a teleworking facility. |
| g) | Home-working controls shall be applied, including lockable filing cabinets, clear desk and clear screen, and access controls for computers and secure communication with the office. |
| 4. | Teleworking Document Management: [Core-13(b)] |
| a) | Authorized teleworking users must avoid storing and printing documents containing PHI, PII and company confidential information while working remotely. |
| b) | Teleworking users must place in a secured location documents containing PHI, PII and company confidential information when not in use. |
| c) | Authorized portable storage devices must be encrypted if they are to be used to stored PHI, PII or company confidential information. |
| 5. | Teleworking Control of Assigned Equipment: [Core-13(b)] |
| a) | For decommissioning of company assigned equipment the user must return the required to the Desk Top Management team who will coordinate the process as outlined in the Retention & Disposal procedure. |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#22 | Page 104 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Teleworking | ||
| VII. | Attachments: |
ATTACHMENT F - Retention & Disposal procedure [Core-13(b)]
| Version Control |
Effective Date
|
Approved By (include position name)
|
Amendment
|
| 1 | 09/01/2016 | ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, CIO | 1 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#23 | Page 105 | |||
| Effective Date: 09/01/2016 | |||||
| Approval Date: 09/01/2016 | |||||
| Department: Information Security | Last Review Date: 08/11/2016 | ||||
| Policy Name: | Third Party Services Risk Management | ||||
|
Drafted by: ▇▇▇▇ ▇▇▇▇▇▇, IT Compliance Supervisor
|
Reviewed by: ▇▇▇▇▇▇ ▇. ▇▇▇▇▇▇▇, Information & Cyber Security Director |
Approved by: ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, Chief Information Officer
|
|||
| I. | Purpose: |
The purpose of this policy is to define requirements and establish systematically approach for management of risks associated with the contracting of third party service providers.
| II. | Scope: |
This policy applies to TSM and its subsidiaries employees, temporary workers, contractors, business partners, third party vendors and physical facilities where TSM provides services to its customers.
| III. | Policy: |
This policy help the organization assess the potential risks and vulnerabilities to the confidentiality, integrity and availability of information systems [Core-15(a)].
Triple-S Management Corporation (TSM) has developed a Third Party Services Risk Management Policy also known as Vendor Risk Management to ensure that third party service providers maintain adequate security controls to manage TSM PII and/or PHI information. The policy also require management monitor the level of services contracted.
| IV. | Definitions: |
None
| V. | Responsibilities: |
| 1. | All Triple-S Management Corporation (TSM) and its subsidiaries employees, temporary workers, contractors, business partners and third party vendors, without exception, must comply with the information security policies. Any employee found to have violated such Policies may be subject to disciplinary actions, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated. |
| 2. | TSM reserves the right to audit networks, systems, or procedures on a periodic basis to ensure compliance with this policy. |
In addition, all TSM personnel shall not interfere with federal or state investigations or disciplinary proceedings by willful misrepresentation or omission of facts or by the use of threats or harassment against any person.
| 3. | Exceptions |
Any exception to the policy must be approved by the Information & Cyber Security Director in advance.
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#23 | Page 106 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Third Party Services Risk Management | ||
4. Non-Compliance
An employee found to have violated this policy may be subject to disciplinary action, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated.
| VI. | Procedure: |
The following practices help the organization assess the potential risks and vulnerabilities to the confidentiality, integrity and availability of information systems [Core-15(a)].
TSM shall implement develop and implement a Third Party Service Provider Risk Management Program to ensure that security requirements and service levels are met:
| 1. | Service Delivery: It shall be ensure that security controls, service definitions, and delivery levels included in the third party service delivery agreement are implemented, operated, and maintained by the third party. |
| 2. | Monitoring and Review: The services, reports, or records provided by third party shall be regularly monitored and reviewed, and audits shall be carried out regularly to govern and maintain compliance with the service delivery agreements. |
| 3. | Managing Changes: Changes to the provision of service, including maintaining and improving existing information security policies, procedures, and controls, shall be managed, taking account of the criticality of business systems and processes involved and re-assessment of risk. |
| VII. | Attachments: |
ATTACHMENT H - Third Party Services & Risk Management procedure [Core-15(a)].
| Version Control |
Effective Date
|
Approved By (include position name)
|
Amendment
|
| 1 | 09/01/2016 | ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, CIO | 1 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#24 | Page 107 | |||
| Effective Date: 09/01/2016 | |||||
| Approval Date: 09/01/2016 | |||||
| Department: Information Security | Last Review Date: 08/11/2016 | ||||
| Policy Name: | User Access | ||||
|
Drafted by: ▇▇▇▇ ▇▇▇▇▇▇, IT Compliance Supervisor
|
Reviewed by: ▇▇▇▇▇▇ ▇. ▇▇▇▇▇▇▇, Information & Cyber Security Director |
Approved by: ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, Chief Information Officer
|
|||
| I. | Purpose: |
The purpose of this policy is to define requirements to establish, document and review access control mechanism to ensure that users have the minimum access required to conduct their business activities. [Core-15(a) & Core-15(b)]
| II. | Scope: |
This policy applies to TSM, its subsidiaries, employees, temporary workers, contractors, business partners and third party vendors contracted by TSM to provide services to its customers.
| III. | Policy: |
Triple-S Management Corporation (TSM) has developed and adopted the User Access Policy to provide management with direction and support for the implementation of appropriate logical and physical user access controls. [Core-15(a) & Core-15(b)]
TSM has adopted appropriate user access measures (logical and physical) to ensure the confidentiality, integrity and availability of sensitive information and the organization IT assets. This policy is critical for securing Protected Health Information (PHI), Personally Identifiable Information (PII) and Electronic Protected Health Information (ePHI) and ensuring compliance with HIPAA minimum use requirement. [Core-15(a) & Core-15(b)]
Authorization to programs, systems and databases required to access any information on TSM networks, either via local or remote access, must be approved by management and authenticated using unique user’s ID’s and passwords. [Core-15(a) & Core-15(b)]
Logical and physical access controls shall be implemented based on the employee job function and role. The applications, systems and databases accesses shall be granted according to the employee job function and business needs to prevent unauthorized access to information stored in TSM systems and physical facilities. [Core-15(a) & Core-15(b)]
| IV. | Definitions: |
| 1. | Authentication: The process of verifying a user identity in order to grant access to a system according a specific role or profile. |
| 2. | Logical Access: Access to a computer or network system through an authentication protocol. |
| 3. | Unique User ID: The sole identifier of a user, usually a user name. |
| 4. | Privilege Access: Access of an administrator or super user. |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#24 | Page 108 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | User Access | ||
| 5. | Remote Access: Is the ability to get access to a computer or a network from a remote location. |
| V. | Responsibilities: |
| 1. | All TSM and its subsidiaries employees, temporary workers, contractors, business partners and third party vendors, without exception, must comply with the information security policies. |
| 2. | TSM reserves the right to audit networks, systems, or procedures on a periodic basis to ensure compliance with this policy. |
In addition, all TSM personnel shall not interfere with federal or state investigations or disciplinary proceedings by willful misrepresentation or omission of facts or by the use of threats or harassment against any
| 3. | Exceptions |
Any exception to the policy must be approved by the Information & Cyber Security Director in advance.
| 4. | Non-Compliance |
Any employee found to have violated the policy may be subject to disciplinary actions, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated.
| VI. | Procedure: |
| 1. | General Requirements |
| a) | TSM shall define a formal procedure to manage the user access provisioning and de- provisioning processes. The procedure must be designed to prevent unauthorized access to the IT assets and systems used by the organization. [Core-15(a) & Core- 15(b)] |
| b) | Division managers must assign Application Owners for each business application. In case the application has multiple modules specific Application Owners can be assigned to each module. [Core-15(a) & Core-15(b)] |
| c) | Access rights shall be reviewed by management based on the process and scheduled defined by the Information Security Group. At a minimum managers and supervisors shall review and certify its employee user accesses on an annual basis. [Core-15(a) & Core-15(b)] |
| d) | Completing the user access review and certification process is an essential component to ensure compliance with the HIPAA minimum use requirement. [Core-15(a) & Core- 15(b)] |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#24 | Page 109 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | User Access | ||
| e) | Display the approved proper system use notification message or banner before providing access to TSM systems. The notification must provide the required privacy and security notices consistent with key industry regulations and standards such as HIPAA and HiTrust. [Core-15(a) & Core-15(b)] |
| f) | Logical and physical access to information and application systems and functions by users and support personnel shall be restricted in accordance with their job functions and responsibilities. [Core-15(a) & Core-15(b)] |
| 2. | Access Request (User Access Provisioning) |
| a) | Users shall obtain formal approval for the use of TSM information assets and applications by completing the official TSM access request form or submitting an approved request via email. [Core-15(a) & Core-15(b)] |
| b) | Access to TSM information systems shall be authorized by the appropriate requester manager or supervisor, before user is allow to login into TSM systems. [Core-15(a) & Core-15(b)] |
| c) | Authorized logical access requests must be based on the employee job functions and scope of responsibility. [Core-15(a) & Core-15(b)] |
| d) | All user access authorizations shall be granted following the minimum access necessary concept in order to allow the users to perform their job functions with the minimum necessary accesses. [Core-15(a) & Core-15(b)] |
| e) | All physical access to TSM buildings and offices shall be processed by the Corporate Security Group. Users shall obtain formal approval by TSM management before physical access is granted. For further information, (refer to the Corporate Policy Manual, Policy of ID Cards and Access). [Core-15(a) & Core-15(b)] |
| 3. | User Account Administration |
| a) | The user account management process, as well as privileged access authorizations shall be restricted and controlled through a formal documented process via the use of the User Access Request Form or by submitting an approved email. [Core-15(a) & Core-15(b)] |
| b) | The business managers or the Application Owners are responsible for conducting user’s access reviews and certification process on an annual basis. Following this process is required ensure that granted logical accesses, correspond with the employee’s job function and duties and remain restricted to authorized personnel only. [Core-15(a) & Core-15(b)] |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#24 | Page 110 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | User Access | ||
Completing the user access review and certification process is an essential component to ensure compliance with the HIPAA minimum use requirement. [Core-15(a) & Core- 15(b)]
| c) | Unnecessary accounts shall be removed, disabled or otherwise secured. [Core-15(a) & Core-15(b)] |
| d) | Ensure that default accounts that are not required are removed or disabled. [Core-15(a) & Core-15(b)] |
| e) | Ensure that default application or system accounts that are required are protected with a strong password compliant with the TSM password rules. [Core-15(a) & Core-15(b)] |
| 4. | Termination (User Access De-Provisioning) |
The Division of Human Resources will maintain an updated list of active employees and temporally personnel. [Core-15(a) & Core-15(b)]
| a) | All terminations of regular and temporary employees shall be immediately notified to the Human Resources department. [Core-15(a) & Core-15(b)] |
| b) | The SAP system will provide the ISG with an automated notification of all regular and temporary employee terminations. [Core-15(a) & Core-15(b)] |
| c) | The ISG will terminated the access to the LAN based on the requested effective date of the termination. [Core-15(a) & Core-15(b)] |
| d) | The ISG will terminated the access to other applications in a 5 working day’s period. [Core-15(a) & Core-15(b)] |
| e) | The ISG will remove or disable Active Directory accounts that have been inactive for a period of sixty (45) days or more. [Core-15(a) & Core-15(b)] |
| f) | All terminations of contractor and/or the service provider employees shall be immediately notified to the ISG. [Core-15(a) & Core-15(b)] |
| g) | The ISG will terminated the access to the LAN by the contractor and/or the service provider on the requested effective date of the termination. [Core-15(a) & Core-15(b)] |
| h) | The ISG will terminated the access to other applications used by the contractor and/or the service provider in a 5 days working day’s period. [Core-15(a) & Core-15(b)] |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#24 | Page 111 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | User Access | ||
| i) | The user that ends his employment or contractual relationship with TSM, shall not by any means attempt to access the networks and information systems of TSM. [Core- 15(a) & Core-15(b)] |
| 5. | Transfers |
| a) | Transfer of employees between departments, companies or affiliates will be processed by the Information Security Group as a termination. [Core-15(a) & Core-15(b)] |
| b) | It is the responsibility of the new Manager or Supervisor to complete the User Access Request Form with the required new accesses based on the employee job function. User accesses can also be requested via email. [Core-15(a) & Core-15(b)] |
| 6. | Database User Accesses |
| a) | Only authorized personnel shall have administrator access to administrative functions to TSM databases. [Core-15(a) & Core-15(b)] |
| b) | Users shall not have direct access to TSM databases. [Core-15(a) & Core-15(b)] |
| 7. | Emergency User Accesses |
The following conditions will be defined and considered as emergency situations: [Core- 15(a) & Core-15(b)]
| o | Disaster condition; |
| o | Application, system or database problem which results in system downtime or very poor performance; |
| o | Application, system or database problem and that cannot be replicated in the test environment and the problem is causing significant operational problems. |
| a) | The request for emergency access must be generated by a manager or higher level of the area where the need arises. [Core-15(a) & Core-15(b)] |
| b) | The justification for the emergency access shall be documented in the Serena Business Manager ticketing system. The justification must include the approval of the division Vice-President (VP) or the affiliate director and the estimated date until when the access will be required. If for some reason the form cannot be completed in time, a notification must be send by e-mail to the Information Security Group (ISG) and complete the form the next business day. [Core-15(a) & Core-15(b)] |
| c) | The ISG unit will evaluate any emergency access request and shall determine its approval. [Core-15(a) & Core-15(b)] |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#24 | Page 112 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | User Access | ||
| d) | On emergency cases or outside working hours, it is the responsibility of the requesting manager to notify the administration and/or data center Information Security Group personnel. [Core-15(a) & Core-15(b)] |
| VII. | Attachments: |
N/A
| Version Control |
Effective Date
|
Approved By (include position name)
|
Amendment
|
| 1 | 09/01/2016 | ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, | 1 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#25 | Page 113 | |||
| Effective Date: 09/01/2016 | |||||
| Approval Date: 09/01/2016 | |||||
| Department: Information Security | Last Review Date: 08/11/2016 | ||||
| Policy Name: | Information Security Risk Analysis | ||||
|
Drafted by: ▇▇▇▇ ▇▇▇▇▇▇, IT Compliance Supervisor
|
Reviewed by: ▇▇▇▇▇▇ ▇. ▇▇▇▇▇▇▇, Information & Cyber Security Director |
Approved by: ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, Chief Information Officer
|
|||
| I. | Purpose: |
The purpose of this Policy is to define requirements and establish the appropriate actions and priorities for developing and implementing TSM’s information security risk analysis process; managing information security and business continuity risks; and implementing controls to protect against identified risks.
| II. | Scope: |
This Policy applies to TSM and workforce members who are authorized to access information systems maintained by TSM and the ePHI that is processed, stored, and transmitted on such systems. This Policy forms part of the conditions of employment or contracting with TSM, as applicable, of all workforce members at all levels. For purposes of this policy, “workforce members” shall include TSM’s employees, volunteers, trainees, contractors, agents, interns, temporary staff, and other persons whose conduct, in the performance of work for TSM, is under the direct control of TSM, whether or not they are paid by TSM.
| III. | Policy: |
This policy help the organization assess the potential risks and vulnerabilities to the confidentiality, integrity and availability of information systems [Core-15(a)].
Triple-S Management Corporation, on behalf of itself and its direct and indirect affiliates and subsidiaries (collectively referred to herein as “TSM”), has adopted this Information Security Risk Analysis Policy (“Policy”) to protect the confidentiality, integrity, and availability of the electronic protected health information (“ePHI,” as defined in 45 C.F.R. § 160.103) that it processes, stores and transmits, and to protect the information systems on which such ePHI is processed, stored and transmitted. This Policy aids TSM in preventing, detecting, containing, and correcting threats and vulnerabilities to ePHI and the information systems on which it is processed, stored and transmitted, and meeting its obligations with regard to information security.
The risk analysis process described in this Policy is a key requirement to comply with HIPAA, HiTrust and ISO 27001 security requirements.
TSM shall conduct an enterprise wide assessment of risk, including the likelihood and magnitude of harm, from the unauthorized access, use, disclosure, disruption, modification, or destruction of its information systems and the ePHI that such systems process, store, or transmit.
| IV. | Definitions: |
N/A
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#25 | Page 114 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Information Security Risk Analysis | ||
| V. | Responsibilities: |
| 1. | All Triple-S Management Corporation (TSM) and its subsidiaries employees, temporary workers, contractors, business partners and third party vendors, without exception, must comply with the information security policies. Any employee found to have violated such Policies may be subject to disciplinary actions, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated. Triple-S Management Corporation (TSM) reserves the right to audit networks, systems, or procedures on a periodic basis to ensure compliance with this policy. |
In addition, all TSM personnel shall not interfere with federal or state investigations or disciplinary proceedings by willful misrepresentation or omission of facts or by the use of threats or harassment against any person.
| 2. | Exceptions |
The Information & Cyber Security Director or Triple-S Management must approve any exception to the policy in advance.
| 3. | Non-Compliance |
An employee found to have violated this policy may be subject to disciplinary action, up to and including termination of employment.
| VI. | Procedure: |
The following practices help the organization assess the potential risks and vulnerabilities to the confidentiality, integrity and availability of information systems [Core-15(a)].
| 1. | In order to conduct a thorough enterprise wide risk analysis, TSM shall include each of the following elements in its risk analysis process: |
| a) | Data Collection: Identify where the ePHI is stored, received, maintained or transmitted. |
| b) | Identify and Document Potential Threats and Vulnerabilities: Identify and document reasonably anticipated threats to ePH. |
| c) | Access Current Security Measures: Assess and document the security measures TSM implemented, maintained and managed to safeguard ePHI. This assessment shall include security measures required by the HIPAA Security Rule and whether the existing security measures are configured, used and maintained properly. |
| d) | Determine the Likelihood of Threat Occurrence: Determine the probability of potential risk to ePHI. Document all reasonably anticipated combinations of threats and vulnerabilities with associated likelihood estimates that may impact the confidentiality, availability and integrity of ePHI. |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#25 | Page 115 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Information Security Risk Analysis | ||
| e) | Determine the Potential Impact of Threat Occurrence: Determine the impact of potential risk to ePHI. Document all reasonably anticipated potential impacts associated with the occurrence of threats triggering or exploiting vulnerabilities. |
| f) | Determine the Level of Risk: Assign risk levels for all threat and vulnerability combinations identified during the risk analysis should be assigned. |
| g) | Finalize Documentation: Document the risk analysis and maintain such documentation for future reference. |
| h) | Periodic Review and Updates to the Risk Analysis: Conduct continuous information security risk analyses to identify when updates are needed. To ensure that the risk analysis process is integrated into the risk management process, the information security risk analysis shall be conducted or reviewed as new technologies and business operations are planned and as existing technologies and business operations change. Below is a non-exclusive list of events when a risk analysis shall be conducted or reviewed: |
| o | Security incident is experienced; |
| o | Change of ownership occurs; |
| o | Turnover in key staff or management; and |
| o | Plans to incorporate new technology. |
In the absence of any of the events listed above, TSM shall conduct or review a risk analysis at least annually.
| i) | Monitoring of Risk Mitigation Plan: Establish a process to monitor the status of the risk mitigation plan, which shall occur at least quarterly. |
| j) | Reporting to Board: Provide an executive level presentation, including the key areas of risks and the status of the defined risk mitigation plan, to the Board of Directors at least annually. |
This Policy shall be supported by additional policies, standards, guidelines, procedures, and processes.
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#25 | Page 116 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Information Security Risk Analysis | ||
| VII. | Attachments: |
ATTACHMENT I - Information Security Risk Analysis Procedure [Core-15(a)]
| Version Control |
Effective Date
|
Approved By (include position name)
|
Amendment
|
| 1 | 09/01/2016 | ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, CIO | 1 |
| 2 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#26 | Page 117 | |||
| Effective Date: 09/01/2016 | |||||
| Approval Date: 09/01/2016 | |||||
| Department: Information Security | Last Review Date: 08/11/2016 | ||||
| Policy Name: | Business Continuity Management | ||||
|
Drafted by: ▇▇▇▇ ▇▇▇▇▇▇, IT Compliance Supervisor
|
Reviewed by: ▇▇▇▇▇▇ ▇. ▇▇▇▇▇▇▇, Information & Cyber Security Director |
Approved by: ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, Chief Information Officer
|
|||
| I. | Purpose: |
Triple-S Management Corporation (TSM) is committed to its customers, employees, stakeholders and suppliers. To insure the effective safety of people and the availability of essential products and services, TSM establishes this Business Continuity Management Policy in support of a comprehensive program for emergency response, business continuity, disaster recovery and business recovery.
| II. | Scope: |
This policy applies to TSM and its subsidiaries employees, temporary workers, contractors, business partners, third party vendors and physical facilities where TSM provides services to its customers.
| III. | Policy: |
Triple-S Management Corporation (TSM) has developed and adopted the Business Continuity Management Policy to provide management with direction and support for the implementation of a Business Continuity Program (BCP) in accordance with the organization business requirements and applicable laws and regulations. TSM recognizes that information is an important asset and it is important to protect the confidentiality of the information being managed, maintain its integrity and ensure its availability.
This policy provides the requirements for planning, implementation, activation and governance processes to counteract interruptions to business activities and to protect critical business functions from the effects of major failures of information systems or disasters and to ensure their timely resumption.
TSM shall establish a Business Continuity Management Program (BCMP) that will define the minimum requirements for the organization to address the continuity of mission critical operations. Additionally, TSM shall assign resources with specific roles and responsibilities to develop implement and oversee the business continuity plans in compliance with the business continuity management program.
| IV. | Definitions: |
| 1. | Business Continuity (BC) Planning: An organization’s risk management strategy for threats that may terminate or significantly disrupt core business. It involves mitigation activities and contingency planning for response and recovery actions. (Note: BC planning necessarily embraces disaster recovery and emergency management planning.) |
| 2. | Business Continuity (BC) Program: An ongoing funded process that is supported by senior management, comprising all BC planning, plans, arrangements, practices and processes |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#26 | Page 118 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Business Continuity Management | ||
with which to achieve required BC outcomes in compliance with BC aims and agreed expectations.
| 3. | Business Continuity Management (BCM): The development, implementation and maintenance of strategies, plans, resources and actions to ensure the continued achievement of critical objectives in the event of a significant, untoward, crisis event. |
| 4. | Crisis: An untoward event that potentially or actually results in disruption to day-to-day functioning of a part or the whole of an organization, sufficient to require management to divert a portion of their attention, time, energy and resources away from business-as-usual activities. (Note: for BC purposes, the term ‘crisis’ is used generically to refer to a significant, crisis/emergency/disaster event). |
| 5. | Event: The occurrence of a particular set of circumstances that creates an actual or potential emergency or disaster or other crisis situation. |
| 6. | Risk: The chance of something happening that will have an impact upon objectives. |
| V. | Responsibilities: |
| 1. | Business Continuity Management (BCM) is a strategic, tactical and operational issue. It is a shared responsibility of TSM, including management and employees from all business units throughout the organization. In order to implement the Business Continuity Management Program (BCMP), TSM has defined the Contingency Management Team (CMT) which is responsible to execute the Crisis Management process for TSM, by timely responding to emergencies or events which threatens the business continuity of the company and by having an effective communication with employees, customers, and the media if necessary through various communications devices and methods. |
| 2. | All Triple-S Management Corporation (TSM) and its subsidiaries employees, temporary workers, contractors, business partners and third party vendors, without exception, must comply with the information security policies. Any employee found to have violated such Policies may be subject to disciplinary actions, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated. |
| 3. | TSM reserves the right to audit networks, systems, or procedures on a periodic basis to ensure compliance with this policy. |
In addition, all TSM personnel shall not interfere with federal or state investigations or disciplinary proceedings by willful misrepresentation or omission of facts or by the use of threats or harassment against any person.
| 4. | Exceptions |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#26 | Page 119 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Business Continuity Management | ||
Any exception to the policy must be approved by the Information & Cyber Security Director in advance.
| 5. | Non-Compliance |
An employee found to have violated this policy may be subject to disciplinary action, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated.
| VI. | Procedure: |
| 1. | Business Continuity Management Program |
| a) | The Business Continuity Management Program (BCMP) involves the minimum requirements to develop and implement the Business Continuity (BC) plans. The program shall include, at a minimum, documenting processes such as: |
| b) | Governance, which specifies formal roles and responsibilities, resource assignment and budget planning. |
| c) | Risk Assessment & Business Impact Analysis, which evaluates of potential threats (natural, technical or human), that may impact TSM’s assets from achieving its business and operational goals and the actions needed to prevent or minimize the effects of potential loss. |
| d) | Emergency Response, which establishes the immediate reaction and response to an emergency situation focusing on ensuring life safety and reducing the severity of the incident. |
| e) | Crisis Management, which establishes the overall coordination of TSM’s response to crisis in an effective, timely manner with the goal of avoiding or minimizing damage to TSM, profitability, reputation and ability to operate until specific business continuity plans are activated. |
| f) | Business Continuity / Disaster Recovery, which defines the process of developing and documenting procedures that enable TSM to respond to an event that lasts for an extended period of time and return to performing its critical functions after an interruption. |
| g) | Communications, which establishes communication process with employees, government, customers and all affected shareholders. |
| h) | Awareness and Training, which creates and maintains awareness and training to enhance the skills required to develop and implement the business continuity management processes. |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#26 | Page 120 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Business Continuity Management | ||
| i) | Exercise, Evaluation and Corrective Actions, which are performed for the purpose of training team members and validating the business continuity plans shall be tested every two years or yearly if requested by the Chief Information Officer or the Chief Technology Officer in order to ensure that the plan is still effective.. Exercise results identify plan gaps and limitations and are used to improve the business continuity plans. |
| j) | Coordination with Third Parties, which establishes the coordination of activities and the integration of resources with third parties with the objective of managing a disrupting event or an exercise. |
| k) | Audit and Compliance, which establishes applicable procedures to be aligned with laws and regulatory requirements. |
| l) | Budgeting, annual budgeting for adequate levels of initial development and on-going maintenance of BC planning is the responsibility of TSM Senior Management. |
| m) | Program Maintenance, which establishes the management process of keeping TSM’s Business Continuity Management Program up-to-date and aligned with the corporate Business Continuity strategies. |
| VII. | Attachments: |
N/A
| Version Control |
Effective Date
|
Approved By (include position name)
|
Amendment
|
| 1 | 09/01/2016 | ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, CIO | 1 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#27 | Page 121 | |||
| Effective Date: 09/01/2016 | |||||
| Approval Date: 09/01/2016 | |||||
| Department: Information Security | Last Review Date: 08/11/2016 | ||||
| Policy Name: | Patch and Vulnerability Management Policy | ||||
|
Drafted by: ▇▇▇▇ ▇▇▇▇▇▇, IT Compliance Supervisor
|
Reviewed by: ▇▇▇▇▇▇ ▇. ▇▇▇▇▇▇▇, Information & Cyber Security Director |
Approved by: ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, Chief Information Officer
|
|||
| I. | Purpose: |
In today’s dynamic and heterogenous networks desktops, servers and communication equipment are prone to software/hardware development errors. Operating systems and software applications are more affected than other types of equipment. This creates a fertile environment for malware to compromise systems and networks containing critical systems. To mitigate these potential threats Grupo Triple S has established a policy to identify vulnerabilities and mitigate them in a timely fashion.
| II. | Scope: |
This policy applies to all computer, servers and communication systems of Grupo Triple S found in all subsidiaries of the corporation without exception. It applies to all operating systems brands and versions. It applies to all licensed and open-source applications.
| III. | Policy: |
It is the policy of Grupo Triple S to identify and mitigate in a reasonable timely fashion all the application and operating system vulnerabilities identified by Vendor and National Vulnerabilities databases applicable to the corporate inventory of computers, servers and communication equipment.
This policy complies with the Patch and Vulnerability Management recommendations found in NIST Special Publication 800-40 version 2.
| IV. | Definitions: |
| 1. | PVG – Policy and Vulnerability Group |
| 2. | NVD – National Vulnerability Database |
| 3. | Vdb – Vulnerability Database |
| 4. | CAB – Change Advisory Board |
| V. | Responsibilities: |
| 1. | It is the responsibility of the Information Security Group of Triserve to carry out this policy. It is the responsibility of the Infrastructure Group of Triserve to assist in this process providing accurate equipment inventory. It is the responsibility of the Change advisory board to meet monthly to discuss, approved or deny the implementation of vulnerability mitigation techniques. It is the responsibility of business application owners to accept risks when threat mitigation is not an option as it could adversely affect daily corporate operations. |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#27 | Page 122 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Patch and Vulnerability Management Policy | ||
| 2. | Exceptions |
Any exception to the policy must be approved by the Information & Cyber Security Director in advance.
| 3. | Non-Compliance |
Any employee found to have violated the policy may be subject to disciplinary actions, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated.
| VI. | Procedure: |
| 1. | The Infrastructure Management Supervisor and/or its designators must use an automatic tool to create and maintain a Corporate IT Asset Inventory of computers, servers and communications equipment used by the organization. The Microsoft Active Directory is a suitable tool to create and maintain such inventory database. |
| 2. | The Information Security Group and/or its designators must use an automatic tool to perform a monthly IT asset scan and provide the differences between the IT asset scan results and the Corporate IT Asset Inventory to the Infrastructure Management Supervisor and/or its designators for processing. |
| 3. | The Information Security Group and/or its designators must use an automatic tool to create and maintain a Corporate Vulnerability Database. This database must include an up to date list of vulnerabilities from vendor specific sites and national vulnerability databases. |
| 4. | On a monthly basis, the Information Security Group and/or its designators must use an automatic tool to identify vulnerabilities applicable to the corporate IT asset inventory. |
| 5. | The Information Security Group will identify CRITICAL and IMPORTANT security patches for deployment. |
| 6. | The TriServe software architecture supervisor and the TriServe data center operation team must review the list of recommended patches for deployment and provide approval full or partial of the recommended patches prior to deployment. If partial a valid justification must be provided. Possible reasons for not installing a patch include: |
| a) | Application is not compatible with the recommended patch. |
| b) | Operating System (OS) is not compatible with the recommended patch. |
| 7. | The Information Security Group and/or its designators must use an automatic tool to apply corresponding patches to the following environments in the specific time windows as follows: |
| a) | Test Environment: Any given time window |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#27 | Page 123 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Patch and Vulnerability Management Policy | ||
| b) | Development Environment: Any day from 8PM to 6AM. |
| c) | Quality Assurance Environment: From 8PM to 6AM Tuesdays and Wednesdays. |
| d) | Production Core Systems (PROD-CORE): From 1:00 AM to 6:00 AM 2nd and 3rd Sunday of the month. |
| e) | Production Non-Core Systems (PROD-NON CORE): From 10:00 PM to 5:00 AM on Fridays. |
| 8. | After receiving approval for the installation of the recommended patches the Information Security Group will coordinate the installation process based upon the agreed deployment scheduled. |
| 9. | If patches are not available, Information Security Group and/or its designators must identify and apply applicable alternate mitigation techniques to the following environments in the specific time windows as follows: |
| a) | Test Environment: Any given time window |
| b) | Development Environment: Any day from 8PM to 6AM. |
| c) | Quality Assurance Environment: From 8PM to 6AM Tuesdays and Wednesdays. |
| d) | Production Core Systems (PROD-CORE): From 1:00 AM to 6:00 AM 2nd and 3rd Sunday of the month. |
| e) | Production Non-Core Systems (PROD-NON CORE): From 10:00 PM to 5:00 AM on Fridays. |
| 10. | If alternate mitigation techniques are not available or recommended for a vulnerability or set of vulnerabilities, the Information Security Group and/or its designators must identify the application business owner and request the business owner to fill out a risk acceptance form. The business owner must fill out a risk acceptance form that must include a remediation plan with implementation dates. |
| 11. | If the business owner can or will not accept the risk, the Information Security Group and/or its designators must prepare a removal procedure for the affected software, system or hardware. |
| 12. | After approval from CAB, the Information Security Group and/or its designators must use an automatic tool to apply corresponding patches or implement alternate configuration adjustment techniques to: |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#27 | Page 124 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Patch and Vulnerability Management Policy | ||
| a) | Quality Assurance Environment: From 8PM to 6AM Tuesdays and Wednesdays. |
| b) | Production Core Systems (PROD-CORE): From 1:00 AM to 6:00 AM 2nd and 3rd Sunday of the month. |
| c) | Production Non-Core Systems (PROD-NON CORE): From 10:00 PM to 5:00 AM on Fridays. |
| VII. | Attachments: |
ATTACHMENT I - Information Security Patch and Vulnerability Management Procedure
| Version Control |
Effective Date
|
Approved By (include position name)
|
Amendment
|
| 1 | 09/01/2016 | ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, CIO | 1 |
| 2 |
Schedule J10
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
 |
| IT Controls Questionnaire |
| Instructions: |
| This is an assessment of the Triple-S Management Group (TSM) business partner’s compliance level with the TSM Information Security & Control Policies. This is a requirement to establish a business relationship between the business partner and a TSM operating company. The TSM corporate policies, as well as industry based regulations, provides a broad set of security requirements that must be met for adequate management of TSM business information. Business partners of TSM are required to meet the policies and regulations for information that they may have access to or manage for TSM, depending upon the nature of the work that they are doing for TSM and the sensitivity of the information. This questionnaire is intended to help the TSM operating company determine whether the business partner’s security practices and controls are acceptable relative to the organization policies and requirements. An independent validation of the answers may be conducted through an on-site visit and review at the discretion of the TSM operating company. The answers and validation will be used to formulate an overall position, which will then help determine whether the TSM operating company wishes to engage in a contract with the business ▇▇▇▇▇▇▇ and, if so, how security requirements should be captured in such a contract to ensure compliance with the TSM security controls. In the event that the business partner’s security policies and procedures do not sufficiently meet the requirements set forth by TSM operating company, TSM may request satisfactory remediation or termination of the business relationship. If a contractual relationship currently exists between the business partner and the TST operating company, collaboration on an acceptable resolution for any identified issues will be required. Consider all answers from the perspective of the facilities, personnel, systems, applications, and networks with access, or potential access, to TSM systems or information. Different questionnaires must be completed for each physical location involved in the relationship that will have access, or potential access, to TSM classified information assets. TSM classified information is all NON-PUBLIC information. All questions are in YES / NO format to allow for easy completion and evaluation, but a few questions request additional information. In the event of a NO answer, response sections (comments) are provided for the business partner to elaborate on alternative controls or to provide clarification. These responses will be considered when evaluating the completed questionnaire to determine whether an answer is acceptable. If a question is not applicable, please ▇▇▇▇ the answer NO and explain in the comments section why the question is not applicable. |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.

 |
IT Securty Risk Assessment
General Information
| Company Information: | |
| Company Name: | |
| Address: | |
| Name of representative: | |
| Representative title: | |
| Services to be rendered | |
| Email: | |
| Phone: | |
| website: | |
| Name of who responded this questionnaire (must be IT related personnel): | |
| Name: | |
| Position or Title: | |
| Email: | |
| Phone: | |
| Application Information (If this not apply please leave a comment below and continue): | |
| Application Name: | |
| Description or purpose: | |
| Name of representative: | |
| Does this application manages Protected Health Information (PHI), Personal Identifiable Information (PII) or other confidential information such as financial records? (Indicate volume of records, exchange methods and frequency) | |
| website: | |
| Subcontractors Information in this engagement context (If this not apply please leave a comment below): | |
| Subcontractor Name: | |
| Address: | |
| Name of representative: | |
| Representative title: | |
| Email: | |
| Phone: | |
| website: | |
| Services Description | |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.


IT Securty Risk Assessment
| Questionnaire Analysis | ||||
| Question | All Questions2 | Service Provider Answer (Yes, No, 0=Not Applicable) |
Service Provider Notes | |
| Q1 | Does your company have a dedicated information security staff? | |||
| Q2 | Does your company have a documented information security training and awareness program? | |||
| Q3 | Do all PCs have properly configured and enabled commercial anti-malware software installed and running at all times? If yes, please specify the product used in the “Comment” section below. | |||
| Q4 | Are anti-malware signature files installed no later than 72 hours after release by the vendor? | |||
| Q5 | Are all personnel involved in processing customer (i.e., TST) information appropriately trained for the handling of that information? | |||
| Q6 | Are all personnel required to complete annual information security training? | |||
| Q7 | Is there a background check process in place for new hiring personnel. | |||
| Q8 | Does your company have defined policies or procedures to ensure the proper control and protection of customer classified information when held in storage, transmitted electronically, or transferred via physical means? | |||
| Q9 | Does all sensitive information (i.e. PKI) is encrypted over a public network, such as the Internet? | |||
| Q10 | Are all paper documents containing customer classified information filed and locked away when not in use? | |||
| Q11 | Are paper and film-based media containing customer classified information destroyed using secured destruction devices or processes? | |||
| Q12 | Is the use of non-Company approved Instant Messaging and File-Sharing software outside of your Intranet prohibited? | |||
| Q13 | Do your policies require segregation of duties (i.e., account authorization rights and application/transaction capabilities must not be granted to the same individual)? | |||
| Q14 | Are access control lists reviewed at least annually? | |||
| Q15 | Is there a process in place to authorize user accounts? | |||
| Q16 | Are user accounts disabled upon termination of employment or upon termination of a business relationship? | |||
| Q17 | Does your company have a password policy? | |||
| Q18 | Are all systems configured to ensure password length/complexity rule combinations: 1) passwords with a minimum length of 8 characters that contain characters from at least 3 complexity classes such as upper/lower case, numerals, special characters... | |||
| Q19 | Are user passwords required to be changed at least every 90 days? | |||
| Q20 | Is the user required by policy to change a temporary or initial password after first use? | |||
| Q21 | Are default system passwords or PINs immediately changed during or immediately after the installation process? | |||
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
| Q22 | Are user IDs delivered via a separate medium or at a separate time from the password? | |||
| Q23 | Does your password delivery process require confirmation of the recipient’s identity before delivery? | |||
| Q24 | Is all external access to your company network through an access control system (i.e., Firewall)? If yes, please specify the product used in the “Comment” section below. | |||
| Q25 | Do the firewalls deny all inbound and outbound traffic that doesn’t have a documented business purpose? | |||
| Q26 | Is intrusion detection system enabled? | |||
| Q27 | Do all firewalls log traffic and suspicious activity? | |||
| Q28 | If remote sessions on the firewall are permitted, are logs of the time, date, duration, and user IDs recorded? | |||
| Q29 | Is there a policy in place to ensure mobile devices are configured to protect customer information stored, processed or transmitted by those devices? | |||
| Q30 | Is there the capability to encrypt customer data on the mobile device? | |||
| Q31 | Is there the capability to remotely wipe the TST information stored on the mobile device? | |||
| Q32 | After 60 days of non-use, are Mobile Devices wiped and their users’ access revoked? | |||
| Q33 | Does your company have a policy that dictates cryptographic standards for the protection of information? | |||
| Q34 | If so, does your policy meet the following cryptographic standards for encryption (symmetric AES, 3DES with at least 128 bits, asymmetric – RSA with at least 2048 bits)? | |||
| Q35 | Are all sensitive file transmissions (i.e. PHI) encripted? | |||
| Q36 | Are all backups containing sensitive information (i.e. PHI) encrypted? | |||
| Q37 | Is there a security monitoring and reporting process in place? | |||
| Q38 | Does the process define the time frame for addressing security events? | |||
| Q39 | Is there a process to notify customers when their systems are affected by an incident? | |||
| Q40 | Does your company utilize intrusion detection technology? | |||
| Q41 | Are intrusion detection mechanisms deployed at all external business partner connection points? | |||
| Q42 | Do critical intrusion detection events generate an alarm? | |||
| Q43 | Are your policies consistent with government laws, regulations, and directives such as: HIPAA, GLBA, SOX, PCI, etc…? | |||
| Q44 | Does your company have a documented information systems business continuity and disaster recovery plan? | |||
| Q45 | Is the Continuity of Business and Disaster Recovery Plan reviewed and exercise at least once a year? | |||
| Q46 | Does your company have a physical security policy that establishes requirements for ensuring the physical protection of information assets? | |||
| Q47 | Are physical access rights revoked immediately after an employee or contractor is terminated? | |||
| Q48 | Are entrances and exits monitored to prevent unauthorized removal of customer or company property? |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
| Q49 | Does the policy require users to be individually identified and authenticated prior to being permitted access to any company networking and computing resources? | |||
| Q50 | Is there a process to authorize remote and wireless access points in your network? | |||
| Q51 | Are remote access sessions to your network logged? | |||
| Q52 | Is strong encryption (using the 3DES or AES algorithm with at least a 128 bit key) enforced at the remote and wireless entry points? | |||
| Q53 | Does your company have a System Administration and Management Security Policy (or policies)? | |||
| Q54 | Does your company have an up-to-date inventory of all your hardware and software assets? | |||
| Q55 | Does your company have a documented configuration management process? | |||
| Q56 | Do standard configurations exist for laptops/desktops and servers? | |||
| Q57 | Is there a process in place to periodically scan infrastructure assets for vulnerabilities? If yes, please specify frequency of scans in Comments below. | |||
| Q58 | Is there a process in place to ensure the timely installation of security patches? | |||
| Q59 | Do you have a procedure to apply security patches immediately in the event there is an immediate threat or major vulnerability? | |||
| Q60 | Are computing devices configured to lock (or disable) user accounts after 5 invalid attempts within 15 minutes (or less)? | |||
| Q61 | Are computing devices configured to lock user interfaces after 15 minutes (or less) of inactivity? | |||
| Q62 | Does your company have documented policies and procedures for data backup? | |||
| Q63 | Do backups include system data and application/business data? | |||
| Q64 | Are backups geographically separated from the original sources? | |||
| Q65 | Are logs protected against changing, overwriting, or deletion? | |||
| Q66 | Do devices with logging enabled have access to sufficient mass storage to maintain logs for 90 days? | |||
| Q67 | Does the company maintain a Cyber Insurance Policy? | |||
| Q68 | Does the company have a SOC 1 Type II report for the service being offered? | |||
| Q69 | Does the company have a SOC 2 Type II report for the service being offered? | |||
| Q70 | Is the company ISO 27001 certified? | |||
| Q71 | Is the company HiTrust certified? | |||
| Q72 | Are the services being proposed to be provided from a USA location? | |||
| Q73 | Will the data be hosted in the USA? |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.


Security Checklist for Acquired Systems: Please indicate if the application proposed meets the following securitry requirements. If the requirement is not met please explain in detail what mitigation controls you have in place. If the requirement is not applicable please explain why. If an application will no be offered as part of this engagement please explain and do not answer this worksheet.
| APPLICATION QUESTIONS | YES/NO | Explain if not in compliance or if it is not applicable |
| AREA 1 - AUTHENTICATION AND PASSWORD MANAGEMENT | ||
| 1. Password length with minimum of 8 characters | ||
| 2. Maximum password age of 30 days | ||
| 3. Password require combination of characters (at least one the following characters: Lowercase alphabetic, uppercase alphabetic, numeric, and special characters) | ||
| 4. Account lockout threshold (locked after 3 invalid logon attempts) | ||
| 5. Reset user’s session after 30 minutes of inactivity. | ||
| 6. Temporary password should be change automatically at first log-in. | ||
| 7. Prevent re-use of passwords (previous 15 passwords cannot be reused). | ||
| 8. Require user to re-authenticate previous to performing critical transactions. | ||
| AREA 2 - ACCESS CONTROLS | ||
| 9. Application must be able to generate user’s access report upon request (other attributes: with header, title of report, timestamp, user id, description, role, status, etc.) | ||
| 10. Restrict access security-relevant configuration privileges to only authorized users. | ||
| 11. Implement ability of disabling desired user accounts upon request. | ||
| 12. Disable user’s accounts after 90 days of inactivity | ||
| 13. Implement two factor-authentication to power users, master users, and sensitive accounts. | ||
| 14. Restrict access to files or other resources, including those outside the application's direct control, to only authorized users. | ||
| AREA 3 - ACCOUNTABILITY AND REPORTING | ||
| 15. System and user’s account auditing functions. | ||
| 16. Restrict access to logs to only authorized individuals | ||
| 17. Audit logs cannot be altered | ||
| 18. Protection of sensitive information (such as PHI, social security, financial information) displayed in reports to authorized personnel only. | ||
| 19. Log all administrative functions, including changes to the security configuration settings. | ||
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
| AREA 4 - SYSTEM CONFIGURATION | ||
| 20. Avoid the use of “root” account (at different level such as DB, App, O/S, tools…) | ||
| 21. Remove test code or any functionality not intended for production, prior to deployment | ||
| 22. Remove unnecessary information from HTTP response headers related to the OS, web-server version and application frameworks | ||
| 23. The security configuration store for the application should be able to be output in human readable form to support auditing | ||
| 24. Isolate development environments from the production network and provide access only to authorized development and test groups. | ||
| AREA 5 - DATABASE SECURITY | ||
| 25. The application should use the lowest possible level of privilege when accessing the database | ||
| 26. Remove or change all default database administrative passwords | ||
| 27. The application should connect to the database with different credentials for every trust distinction (e.g., user, read-only user, guest, ▇▇▇▇▇▇▇▇▇▇▇▇▇▇) | ||
| ▇▇▇▇ ▇- FILE MANAGEMENT | ||
| 28. Require authentication before allowing a file to be uploaded | ||
| 29. Prevent or restrict the uploading of any file that may be interpreted by the web server | ||
| 30. Ensure application files and resources are read-only | ||
| 31. Scan user uploaded files for viruses and malware |
Schedule K
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
SCHEDULE K
REPORTS
| Schedule K | Supplier Confidential |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
schedule K
Reports
| 1. | Introduction |
| (a) | Introduction. In compliance with Section 18.2 of the General Terms and Conditions, this Schedule K defines the Parties’ approach to reporting including (i) defining the operational reporting framework, and (ii) specifically identifying certain operational reports to be produced and provided by Supplier as part of the Services. |
| (b) | Defined Terms. |
| (i) | “Management Report” means reporting by Supplier to Triple-S management, with respect to the Functions outsourced to Supplier, in order to provide Triple-S visibility into the relevant aspects of Triple-S’ business and the Services. |
| (ii) | “Governance Reports” means any reporting required to support contract Governance, the Governance Plan, or as otherwise required by Schedule F (Governance). |
| (iii) | “Operational Report” means a written summary or detail of operations which is produced as part of or as an output to the Services. |
| (iv) | “Regulatory Report” means any reporting required by Regulators or applicable Laws or reporting required due to changes in Law. |
| (v) | “Reports” means collectively Governance Reports, Management Reports, Operational Reports, and Regulatory Reports. |
Any capitalized terms used but not otherwise defined in this Schedule K (Reports) will have the meaning provided in the Schedule AA (Glossary) or elsewhere in the Agreement.
| 2. | REPORTING FRAMEWORK |
| 2.1 | Supplier Reporting Commitment. |
Supplier shall provide at no additional charge to Triple-S the following Reports:
| (a) | Each Report generated by Triple-S for the Services in the twelve (12) months prior to the Service Commencement Date (“Existing Reports”), unless and until Triple-S confirms in writing that such Report is no longer required; |
| (b) | Regulatory Reports including Reports reasonably necessary to prepare for and respond to a regulatory audit or inquiry; |
| (c) | Governance Reports; |
Triple-S / Supplier Confidential
Page 1
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule K
Reports
| (d) | Management Reports that Triple-S reasonably requires as part of its management and oversight of the Services and Supplier; |
| (e) | Reports set forth in Sections 7 through 9 of this Schedule K; and |
| (f) | Any new versions of Reports developed during implementation of new Triple-S Systems to ensure continuity of accurate Reporting. |
| 2.2 | New Report Requests or Modifications to Existing Reports. |
All requests by Triple-S for: (i) new Reports, or (ii) modifications to Reports shall be Changes that will be subject to the Change Control Process.
| 2.3 | Access to Data for Triple-S Reporting Purposes. |
As of the Service Commencement Date, Triple-S will continue to have the same access as Triple-S had as of the Effective Date to all transactional data for the Services.
| 3. | FREQUENCY OF REPORTS |
Supplier shall provide the Reports at the current frequency as of the Services Commencement Date for all Existing Reports.
| (a) | If a Report is identified with a frequency of “Weekly”, Supplier shall provide such Report by the close of business Tuesday on the following week. In the event that a holiday occurs on either Monday or Tuesday, delivery shall be by close of business Wednesday of the following week. |
| (b) | If a Report is identified with a frequency of “Monthly”, such Report shall be provided at the same time as all other monthly Reports and no later than the tenth (10th) day of the following month (or the first Business Day after the tenth (10th) day if the tenth (10th) day is not a Business Day). |
| (c) | If a Report is identified with a frequency of “Quarterly”, such Report shall be provided by the tenth (10th) day of the following quarter (or the first Business Day after the tenth (10th) day if the tenth (10th) day is not a Business Day). |
| (d) | If a Report is identified with a frequency of “Semi-Annually”, such Report shall be provided by the tenth (10th) day of the following semi-annual period (or the first Business Day after the tenth (10th) day if the tenth (10th) day is not a Business Day). |
| 4. | REPORT DELIVERY |
All Reports shall be available on a SharePoint site or using the reporting solution described in Section 5 below.
Triple-S / Supplier Confidential
Page 2
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule K
Reports
| 5. | REPORTING SoLUTION |
Supplier will develop and deliver to Triple-S a reporting solution as set forth below (“Reporting Solution”). Supplier will use Planview to post reports and/or links to reports. Triple-S will have its own client instance in Planview and will be able to use the Planview collaboration portal, where reports and reporting links will be made available to Triple-S. Triple-S will identify the users that will be authorized to access Planview and Supplier will work with Triple-S to provide and manage such access as needed for Triple-S to access reports through Planview.
| 6. | Reporting Activities During Transition |
The Parties agree that within ninety (90) days of the Effective Date, they will catalog the existing Reports that are in scope pursuant to Section 2.1(a) above.
| 7. | Account level Reports |
Supplier shall provide Triple-S the following account-level reports:
| 7.1 | Strategic Relationship Reports |
| Ref | Report | Report Description | Frequency |
| 7.1.1 | Strategic Review Report |
Supplier shall provide an overall enterprise level report highlighting the following: (a) Relationship Review (i) Results accomplished against Triple-S business goals (ii) Benefits delivered (iii) Directional alignment (b) Strategic initiatives for next half year (i) From both Triple-S and Supplier (ii) Partnership opportunities (iii) Priorities (c) Status update on key initiatives and action items from last Strategic Review Report (d) Customer satisfaction |
Semi-Annually |
| 7.1.2 | Quarterly Business Review Report |
Supplier shall provide an overall enterprise report encompassing all Services delivered to Triple-S to include a quarterly view on the following, as appropriate: (a) Key enterprise Service delivery highlights and failures (b) Operational metrics (c) Productivity metrics (d) Escalations review (e) Key learning and focus areas (f) Process improvement initiatives (g) Key activities planned for the next period |
Quarterly |
Triple-S / Supplier Confidential
Page 3
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule K
Reports
| 7.2 | Commercial Contract Reports |
| Ref | Report | Report Description | Frequency |
| 7.2.1 | Change Notice Log |
Supplier shall provide a report specifying the status of all pending Change Notices. (a) Control number and dates associated with each Change Notice (e.g., request date, beginning of implementation, expected completion); (b) Name of the Party requesting the Change; (c) Brief description of the Change Notice; and (d) Current status of the Change Notice. The status of the Change Notice shall be categorized as one of the following stages: (a) “Open” (i.e., the Change Notice has been created and registered); (b) “In Review” (i.e., the Change Notice has been created and is being reviewed by Triple-S pending approval to proceed); (c) “Approved” (i.e., the Change Notice has been approved by both Parties and is awaiting implementation); (d) “On Hold” (i.e., the Parties wish to suspend implementation of the Change but anticipate that the Change will be implemented at a later date); (e) “Completed” (i.e., all implementation tasks have been completed and the Change has been implemented); or (f) “Closed” (i.e., completed and not implemented). |
Upon request |
| 7.3 | Supplier Services Reports |
| Ref | Report | Report Description | Frequency |
| 7.3.1 | Monthly Business Review Report |
Supplier shall provide a report of the Supplier Services highlights during the previous month including: (a) Key enterprise Service delivery highlights and failures (b) Operational metrics (c) Productivity metrics (d) Escalations review (e) Key learning and focus areas (f) Process improvement initiatives (g) Key activities planned for the next period |
Monthly |
| 7.3.2 | Implementation Plan Status Report |
Supplier shall provide a report of the Supplier Implementation Status including: (a) Deliverable actual vs. projected timeline for overall program (b) Deliverable actual vs. projected timeline for each work stream (BPO, ITO, Reporting, etc.) (c) Interwork stream dependencies and action items to address |
Weekly / Monthly |
Triple-S / Supplier Confidential
Page 4
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule K
Reports
| Ref | Report | Report Description | Frequency |
|
(d) Risk items and mitigation to address to maintain implementation timeline (e) Overall adjustments needing to be made to implementation plan for ad hoc items identified during KA/KT for both ITO/BPO (f) Program closeout of implementation items as deliverables are achieved and delivered |
|||
| 7.3.3 | Service Level Performance Report | Report of performance against all Service Levels pursuant to Schedule B (Service Level Methodology). | Monthly |
| 7.3.4 | Governance Action Items | Supplier shall provide a report of items discussed, items needing action and/or resolution, tracking item/action “owner” to gain resolution during the governance meeting to track to item close. | Monthly |
| 7.4 | Project Reports |
| Ref | Report | Report Description | Frequency |
| 7.4.1 | Project Status Report |
Supplier shall provide a report for each Project in process highlighting the following: (a) Overall status of the Project (b) Effort and cost metrics (c) Actual vs. estimated hours, including updated estimate-to-complete (d) Forecast of Project performance (e) Execution highlights (f) Current risk and issue tracker (g) Identified Problems (h) Service introduction preparation status and alignment review (i) Additional reporting requirements as defined by the Triple-S designated Project Manager |
Weekly |
| 8. | claims services reports |
Supplier shall provide Triple-S the following reports relating to the Claims Services:
| Ref | Report | Report Description | Frequency |
| 8.1 | Claim Inventory Reports |
Reports describing the following information regarding the Claims Services: · Time and Claim count reporting; |
Daily / Weekly / YTD |
Triple-S / Supplier Confidential
Page 5
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule K
Reports
| Ref | Report | Report Description | Frequency |
|
· Claim volume by engine, time, status; · Claims under various LOBs; · Claim auto-processing, autofail and pended; and · Void and re-processed Claim reports. |
|||
| 8.2 | Service Level Performance Report | Supplier will provide a monthly report as described in Schedule B that details the overall performance of each Service Level and it’s “met” or “not met” of the goal metric. | Monthly |
| 8.3 | Claims Performance | % of Claims Auto-Adjudicated. The result shall be calculated in accordance with the following formula: (i) Number of Claims Auto-Adjudicated by Supplier divided by (ii) total number of Claims Auto-Adjudicated by Supplier during each month. | Monthly |
| 8.4 | Average Claims Adjudication Cycle Time | Average Claims -Adjudication Time. The average time taken for a Claim to be Adjudicated by Supplier during each month. | Monthly |
| 8.5 | Cycle Time | Average Claims Adjustment processing Time. The average time taken for a Claim to be Adjusted by Supplier during the month. | Monthly |
| 8.6 | Inventory Tracking – Claims aged 10 days | Number and value of Claims aged > ten (10) calendar days (reported by volume of Claims and Claim value (i.e., dollars)). Number and value of Claims in the processing queue for more than ten (10) calendar days. | Monthly |
| 8.7 | Inventory Tracking – Claims aged 25 days | Number and value of Claims aged > twenty-five (25) calendar days (reported by volume of Claims and Claim value (i.e., dollars)). Number and value of Claims in the processing queue for more than twenty-five (25) calendar days. | Monthly |
| 8.8 | Inventory Tracking – Claims aged over 30 days | Number and value of Claims aged > thirty (30) calendar days (reported by volume of Claims and Claim value (i.e., dollars)). Number of and value of Claims in the processing queue for more than thirty (30) calendar days | Monthly |
| 8.9 | Inventory Tracking – Adjustments aged over 10 days |
Number and value of Adjustments aged > ten (10) calendar days (reported by volume of Adjustments and Adjustment value (i.e., dollars)). Number and value of Adjustments in the processing queue for more than ten (10) calendar days
|
Monthly |
| 8.10 | Inventory Tracking – Adjustments | Number and value of Adjustments aged > twenty-five (25) calendar days (reported by volume of Adjustments and Adjustment value (i.e., dollars)). Number and value of | Monthly |
Triple-S / Supplier Confidential
Page 6
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule K
Reports
| Ref | Report | Report Description | Frequency |
| aged over 25 days | Adjustments in the processing queue for more than twenty-five (25) calendar days. | ||
| 8.11 | Inventory Tracking – Adjustments aged over 30 days |
Number and value of Adjustments aged > thirty (30) calendar days (reported by volume of Adjustments and Adjustment value (i.e., dollars)). Number and value of Adjustments in the processing queue for more than thirty (30) calendar days.
|
Monthly |
| 8.12 | Production | Number of manual Claims processed each month. | Monthly |
| 9. | it services reports |
Supplier shall provide Triple-S the following reports relating to the IT Services:
| Ref | Report | Report Description | Frequency |
| 9.1 | Support Reports |
Reports describing the following information relating to support Functions as part of the IT Services: · Incident influx; · Incident backlog; · Incident closures; · Incident priority; · Incident aging; · Incident MTTR (meant time to repair); and · Incident meant time to respond |
Daily / Weekly / YTD |
| 9.2 | Problem Management |
Reports describing the following information relating to Problem management Functions as part of the IT Services: · Problem influx; · Problem backlog; · Problem closures; · Problem by application; and · Problem aging. |
Daily / Weekly / YTD |
| 9.3 | Change & Release Management |
Reports describing the following information relating to Problem management Functions as part of the IT Services: · Planned releases; · Release status; and · Release quality. |
Per release cycle |
| 9.4 | Support |
Reports describing the following information relating to support and Service Level compliance Functions as part of the IT Services: · P1 Incidents; · P2 Incidents; |
Daily / Weekly / YTD |
Triple-S / Supplier Confidential
Page 7
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule K
Reports
| Ref | Report | Report Description | Frequency |
|
· P3 Incidents; and · Application downtime. |
|||
| 9.5 | Application Services |
The following reports relating to application services Functions as part of the IT Services: · Executive summary of application status; · Application health check; · Production uptime / downtime; and · Application status. · Health of the B2B interfaces, automated reporting, and batch processes |
Daily / Weekly / YTD |
| 9.6 | Infrastructure Assets |
Asset Management reporting shall be performed at a minimum as defined by regulatory needs. Additional reporting of assets may be performed as agreed by the Parties. Asset Management items may include the following. · Physical server and desktop assets. · Virtual server and desktop assets. · Network appliances · Other assets in the public and private IP space. · Storage Assets (SAN/NAS/Direct Attached/Cloud)). |
Per regulatory requirements |
| 9.7 | Network Performance |
Network Performance monitoring and reporting shall be performed at a minimum as defined by regulatory needs. Additional reporting of assets may be performed as agreed by the Parties. Network Performance Indicators may include the following.
· Ingress and egress traffic statistics on network interfaces.
· Server performance metrics that may include performance indicators regarding availability, response time, packet loss, and temperature.
· Performance indicators regarding service response time. |
Per regulatory requirements |
| 9.8 | Security – Vulnerability |
Vulnerability Scans and Vulnerability Scan reporting shall be performed at minimum as defined by regulatory needs. Vulnerability Scans and Vulnerability Scan Reporting may be performed more frequently on high value assets as agreed by the Parties. Vulnerability Reports may include such items as follows.
· IP Address/Subnets scanned, vulnerability or violation indicated, and last scan date. |
Per regulatory requirements |
Triple-S / Supplier Confidential
Page 8
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule K
Reports
| Ref | Report | Report Description | Frequency |
| 9.9 | Identity and Access Management (Includes Privileged Users) |
Identity & Access Management (IAM) reporting shall be performed at minimum as defined by regulatory needs. IAM monitoring and reporting will be defined largely by determining business goals, but some examples of IAM reports may include the following.
· Identity & Access Provisioning, De-provisioning, and Attestation Audits.
· Privileged access notification for high value targets
· Audit & Reporting
· Administrative activities (User accounts and Access policies)
· User logins & Application access
· Application services availability |
Per regulatory requirements |
| 9.10 | System/Security Logs |
System & Security logs shall be collected on assets and functions performed at a minimum as defined by regulatory needs. Log sources and event configuration shall be determined by business requirements and goals. Configuration standards and management shall be put in place to ensure the collection of logs throughout the environment. Some events collected may include the following as examples.
· System Events – Success/Failure
· Hardware Events – Success/Failure
· Directory Service Events – Domain controller record of Active directory changes
· Security Log – Events set for auditing with local or global group policies
· Application Log – Start/Stop/Failure events |
Per regulatory requirements |
Triple-S / Supplier Confidential
Page 9
Schedule L
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
SCHEDULE L
IT SECURITY ADDENDUM
| Schedule L | IT Security Addendum |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
MASTER SERVICES AGREEMENT
SCHEDULE L
IT SECURITY ADDENDUM
Except as noted in the exceptions list below, Supplier shall comply with the requirements of the policies attached as Appendix 1 (IT Security Policies) to this Schedule L (IT Security Addendum) as such policies are applicable to Vendors of Triple-S and the Services.
Exceptions
Supplier’s obligation to comply with the policies listed in Appendix 1 below shall not include the obligation to comply with the following policies or requirements contained therein:
| 1. | Any requirements directly related to Functions retained by Triple-S under the Agreement; |
| 2. | Any requirement reserving Triple-S audit rights to networks and systems is only applicable to Triple-S environments, and not to Supplier hosted environments, except as set forth in Schedule M (Audit and Record Retention Requirements). |
| 3. | Any provisions regarding employment and discipline of Supplier Personnel. Supplier will follow Supplier’s internal guidelines regarding employment and discipline of Supplier Personnel; provided, however, that this exclusion does not limit the other obligations of the Parties with respect to Supplier Personnel set forth in the Agreement. |
| 4. | Any requirement directing employees to report to Triple-S Privacy Office. Supplier Personnel will report as required through Supplier’s privacy, security and compliance reporting channels, and Supplier will report to Triple-S as required under the Agreement; |
| 5. | Policy ISP#3 – Section VI.4, requirement that Supplier scan the network at least on a weekly basis to detect the presence of unauthorized component or devices. Supplier shall scan workstations used to provide the Services. Supplier shall begin monitoring the network for unauthorized components or devices after Triple-S implements a capable network access control solution. If Triple-S desires to engage Supplier to implement such solution, it will be Application Support Services and/or a Special Infrastructure Project, as applicable. |
| 6. | Policy ISP#4 – Section VI.1.b, requirement to comply with TSM Record Retention Policy. Supplier shall meet the record retention requirements set forth in Schedule M; |
Triple-S / Supplier Confidential
Page 1
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Schedule L
IT Security Addendum
| 7. | Policy ISP#4 – Section VI.7, requirement to store all important and critical Triple-S information in the “My Documents” folder and to ensure that the “My Documents” folder of the user will not be backed-up. Supplier will comply with this policy after Triple-S updates the policy to reflect Triple-S’s use of OneDrive; |
| 8. | Policy ISP#8, Section VI.1.n, requirement to perform a full functional Disaster Recovery test on an annual basis. Supplier will perform Disaster Recovery tests for the applicable In-Scope Applications and the servers, as identified in the Business Impact Analysis; |
| 9. | Policy ISP#20 – Section VI.3.b, requirement to have log view records for all systems. |
| 10. | Policy ISP#21 – Section VI.2.b, requirement required vulnerability and penetration assessments. Supplier shall perform vulnerability and penetration assessments in coordination with Triple-S and its third party vendor; |
| 11. | Policy ISP#22 – Section VI.3.b, requirement for teleworkers to use the Symantec VIP two factor authentication system to establish remote connection to the network. For this requirement, Supplier may use a different, but comparable solution, as Symantec VIP; |
| 12. | Policy ISP#25 – Section VI.1.i, requirement to quarterly monitor the risk mitigation plan. Supplier will comply with the requirements set forth in Schedule M; and |
| 13. | Policy ISP#27 – Section VI.7, requirement to apply patches during the listed time windows. Supplier will have the ability to implement patches outside of the defined windows for any patches to address security, vulnerability, or business critical patches in order to maintain a secure and stable environment. |
Triple-S / Supplier Confidential
Page 2
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
FINAL EXECUTION VERSION
SCHEDULE L
APPENDIX 1 – IT SECURITY POLICIES
| Schedule L, Appendix 1 | Triple S / Supplier Confidential |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.

IT and Information Security Policies
Approved by and Date
|
Issued by: ▇▇▇▇▇▇ ▇. ▇▇▇▇▇▇▇, Cyber & Information Security Director |
Effective Date: Sep 1, 2016 | |
| Revised by: ▇▇▇▇▇▇ ▇. ▇▇▇▇▇▇▇ | Date Revised: Aug. 11, 2016 | Version: 1.2 |
|
Approved by: ▇▇▇▇ ▇▇▇▇ ▇▇▇▇, Chief Information Officer (CIO) |
||
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
Table of Contents
| Acceptable Use | 1 |
| Anti-virus and Anti-Spyware | 10 |
| Asset Management Policy | 14 |
| Backup & Retention | 18 |
| Change Management | 23 |
| Clear Desk & Clear Screen | 27 |
| Data Classification | 30 |
| Data Integrity and Interoperability | 35 |
| Encryption and Cryptographic ▇▇▇▇▇▇▇▇▇▇ | ▇▇ |
| General Information Security | 45 |
| Information Exchange | 49 |
| IT Compliance Management | 54 |
| Network Security | 61 |
| Password Management | 66 |
| Physical and Environmental Security | 70 |
| Remote Access | 75 |
| Removable Device Management | 79 |
| Retention and Disposal | 83 |
| Security Awareness and Training | 88 |
| Security Monitoring Policy | 91 |
| Technical Vulnerability Management Policy | 97 |
| Teleworking | 100 |
| Third Party Services Risk Management | 105 |
| User Access | 107 |
| Information Security Risk Analysis | 113 |
| Business Continuity Management | 117 |
| Patch and Vulnerability Management Policy | 121 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#1 | Page 1 | |||
| Effective Date: 09/01/2016 | |||||
| Approval Date: 09/01/2016 | |||||
| Department: Information Security | Last Review Date: 08/11/2016 | ||||
| Policy Name: | Acceptable Use | ||||
|
Drafted by: ▇▇▇▇ ▇▇▇▇▇▇, IT Compliance Supervisor
|
Reviewed by: ▇▇▇▇▇▇ ▇. ▇▇▇▇▇▇▇, Information & Cyber Security Director |
Approved by: ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, Chief Information Officer
|
|||
| I. | Purpose: |
The purpose of this policy is to establish what is considered acceptable (and also unacceptable) use of computer and related media in TSM in order to reduce unauthorized access to sensible information (i.e. corporate, personnel and EPHI information), security breaches and of course avoid legal issues associated with such breaches.
| II. | Scope: |
This policy applies to all TSM and its subsidiaries employees, temporary workers, contractors, business partners, third party vendors and physical facilities where TSM provides services to its customers.
| III. | Policy: |
This policy help the organization prevent confidentiality and security breaches. The policy also help identify how individually-identifiable health information should be used.
Triple-S Management Corporation (TSM) has developed and adopted the Acceptable Use Policy to provide management with direction, support and protection for inappropriate, unauthorized, and even illegal actions performed by users, whether the action is performed knowingly (intentionally) or by ignorance.
Internet systems that includes: desktop computers, laptops and other mobile media (tablets, smartphones), file transfer protocols, operating systems, network accounts, electronic mail, all electronic storage media, are the property to TSM. All of these resources are to be used only for business, never for personal use.
TSM shall ensure that all the in scope parties are formal communicated of TSM Information Security Policies. TSM has implemented training programs to guide users on the importance of properly using the information of TSM, and at the same time raise awareness of existing regulations and corporate policies and procedures to ensure full compliance with all the requirements.
Access to the TSM information systems and applications will be provided to users to support business activities and only on a need-to-know basis to perform their jobs responsibilities.
| IV. | Definitions: |
| 1. | Blogging: The activity of adding new entries to a blog or website usually designed to present the owner’s thoughts and ideas, observations, opinions and experiences. |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#1 | Page 2 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Acceptable Use | ||
| 2. | Honeypot: A location in network that is expressly set up to attract and study malware that attempts to penetrate the network or computer system. |
| 3. | Honeynets: Contains one or more honey pots, which are computer systems on the Internet expressly set up to attract and "trap" people who attempt to penetrate other people's computer systems. |
| 4. | Proprietary Information: The information that is not considered public. This may include: corporate, financial and system information. |
| 5. | Spam: Any electronic junk mail received by users and most unsolicited e-mail. |
| 6. | Cloud Platform: A system where applications or systems may be run in an environment composed of utility services in an abstract environment, such as the Internet. Internet- based computing, where shared resources, data and information are provided to computers and other devices on-demand. |
| 7. | Cloud Storage: A popular method used for data storage on the Internet. This could be free or paid. |
| 8. | Mobile device: Any portable equipment used in technology. |
| 9. | BYOD: An acronym for Bring Your Own Device. A custom on the corporate culture where the employer approves the use of employee personal devices such as phones and tablets for the daily job function. |
| 10. | Jail Break: Term used to unlock the operating system of a smartphone, tablet or any portable device without its default security system. |
| 11. | Root: Rooting gives the user administrator rights to alter the OS, tweak the hardware and unlock the phone from its carrier. |
| V. | Responsibilities: |
| 1. | All Triple-S Management Corporation (TSM) and its subsidiaries employees, temporary workers, contractors, business partners and third party vendors, without exception, must comply with the information security policies. Any employee found to have violated such Policies may be subject to disciplinary actions, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated. Triple-S Management Corporation (TSM) reserves the right to audit networks, systems, or procedures on a periodic basis to ensure compliance with this policy. |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#1 | Page 3 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Acceptable Use | ||
In addition, all TSM personnel shall not interfere with federal or state investigations or disciplinary proceedings by willful misrepresentation or omission of facts or by the use of threats or harassment against any person.
| 2. | Exceptions |
The Information & Cyber Security Director or Triple-S Management must approve any exception to the policy in advance.
| 3. | Non-Compliance |
An employee found to have violated this policy may be subject to disciplinary action, up to and including termination of employment.
| VI. | Procedure: |
| 1. | The following General Use and Ownership practices help the organization prevent confidentiality and security breaches: |
| a) | All users should know that all generated information through TSM networks and systems is property of TSM. |
| b) | A physical inventory of all TSM devices and the authorized personnel to use the devices (e.g. Laptops, Desktops Computers, and Corporate Cellphones among others) shall exist and be updated frequently. All devices shall be labeled with either a TSM inventory number, or logo for proper identification. |
| c) | Authorized users may access, use or share TSM proprietary information only to the extent it is authorized and necessary to fulfill the user assigned job duties (e.g. minimum necessary).[Core-16(a)] [Core 15(b)] |
| d) | All users shall be liable for the protecting the information stored on systems, applications, directories and network devices belonging to TSM and shall exercise good judgment regarding the reasonableness of the use of the equipment and the information. [Core- 15(b)] |
| e) | For security and network maintenance purposes, TSM, authorized individuals shall supervise and monitor equipment, system and network traffic. [Core-15(a)(b)(c)] |
| f) | TSM reserves the right to audit network and systems if necessary on a periodic basis to ensure compliance with this policy. [Core-15(a)(c)] |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#1 | Page 4 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Acceptable Use | ||
| g) | All system accesses will be disabled and/or deleted upon termination of employee, completion of contract, end of service of non-employee, or disciplinary action arising from violation of this policy. In the case of a change in job function and/or transfer the original access will be discontinued, and only reissued if necessary and a new request for access is approved. [Core-15(b)] |
| 2. | Security and Proprietary Information: |
The following Security and Proprietary Information protection practices help the organization prevent confidentiality and security breaches [Core-15(b)].
| a) | Providing access to another individual, either deliberately or through failure to secure its access is prohibited. |
| b) | All computing devices must be secured with a password-protected screensaver with the automatic activation feature set at 10 minutes or less. The user must lock the screen or log off when the device is unattended. |
| c) | Posting by employees from a TSM email address or systems on blogs or social networking sites is prohibited unless posting is in the course of business duties. |
| 3. | Unacceptable Use: |
The following activities are not considered an acceptable use of the organization information and information assets. Not following these recommendations could place individually- identified health information and company information at risk. Note that some users may be exempted from some of the restrictions during the course of their legitimate job responsibilities (e.g., system administrator staff may have a need to disable the network access of a host if that host is disrupting production services).
| a) | Under no circumstances an employee of TSM is authorized to engage in any activity that is illegal under local, state, federal or international law while utilizing TSM owned resources. [Core-15(b)] |
| b) | Violations of the rights of any person or company protected by copyright, trade secret, patent or other intellectual property, or similar laws or regulations, including, but not limited to, the installation or distribution of "pirated" or other software products that are not appropriately licensed for use by TSM. [Core-15(b)] |
| c) | Unauthorized copying of copyrighted material including, but not limited to, digitization and distribution of photographs from magazines, books or other copyrighted sources, |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#1 | Page 5 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Acceptable Use | ||
copyrighted music, and the installation of any copyrighted software for which TSM or the end user does not have an active license is strictly prohibited. [Core-15(b)]
| d) | The use or installation of unauthorized software, including obtaining data and/or software from external networks is prohibited. [Core-15(b)] |
| e) | Accessing data, a server or an account for any purpose other than conducting TSM business, even if you have authorized access, is prohibited. [Core-16(a)] |
| f) | Exporting software, technical information, encryption software or technology, in violation of international or regional export control laws, is illegal. The appropriate management should be consulted prior the export of any material that is in question.[Core-15(b)] |
| g) | Introduction of malicious programs into TSM network environment (e.g., viruses, worms, Trojan horses, e-mail bombs, ransomware, etc.). [Core-15(b)] |
| h) | Revealing your account password to others or allowing use of your account by others. This includes family and other household members when work is being done at home. [Core-15(b)] |
| i) | Using a TSM information technology asset to actively engage in procuring or transmitting material that is in violation of sexual harassment or hostile workplace laws in the user's local jurisdiction. |
| j) | Making fraudulent offers of products, items, or services originating from any TSM account. |
| k) | Making statements about warranty, expressly or implied, unless it is a part of normal job duties. |
| l) | Effecting security breaches or disruptions of network communication. Security breaches include, but are not limited to, accessing data of which the employee is not an intended recipient or logging into a server or account that the employee is not expressly authorized to access, unless these duties are within the scope of regular duties. For purposes of this section, "disruption" includes, but is not limited to, network sniffing, pinged floods, packet spoofing, denial of service, and forged routing information for malicious purposes. [Core- 15(b)] |
| m) | Port scanning or security scanning is expressly prohibited unless prior notification to the Information Security Group is made. [Core-15(b)] |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#1 | Page 6 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Acceptable Use | ||
| n) | Executing any form of network monitoring which will intercept data not intended for the employee's host, unless this activity is a part of the employee's normal job/duty. [Core- 15(b)] |
| o) | Circumventing user authentication or security of any host, network or account. [Core- 15(b)] |
| p) | Introducing honeypots, honeynets, or similar technology on the TSM networks. [Core- 15(b)] |
| q) | Using any program/script/command, or sending messages of any kind, with the intent to interfere with, or disable, a user's terminal session, via any means, locally or via the Internet/Intranet/Extranet. [Core-15(b)] |
| r) | Providing confidential information about TSM employees to parties outside TSM. [Core- 15(b)] |
| 4. | Email and Communication Activities: |
The following practices help the organization prevent confidentiality and security breaches and therefore are prohibited [Core-15(b)]:
| a) | Sending unsolicited email messages, including the sending of "junk mail" or other advertising material to individuals who did not specifically request such material (email spam). |
| b) | Any form of harassment via email, telephone or texting, whether through language, frequency, or size of messages. |
| c) | Unauthorized use, or forging, of email header information. |
| d) | Creating or forwarding "chain letters", "Ponzi" or other "pyramid" fraudulent schemes of any type. |
| e) | Use of unsolicited email originating from within TSM networks or other information technology service providers on behalf of, or to advertise, any service hosted by TSM or connected via TSM network unless this activity is part of normal business activity. |
| f) | Posting the same or similar non-business-related messages to large numbers of Usenet newsgroups (newsgroup spam). |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#1 | Page 7 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Acceptable Use | ||
| g) | Employees should never open e-mails received from unknown senders as these e-mails may contain malware. |
| 5. | Blogging and Social Media: |
The following practices help the organization prevent confidentiality and security breaches [Core-15(b)]:
| a) | Blogging by employees, whether using Triple-S Management Corporation (TSM) property and systems or personal computer systems, is also subject to the terms and restrictions set forth in this Policy. Blogging from TSM systems is also subject to monitoring. |
| b) | Users shall also carefully control what information they post on social media accounts and to whom this information is available. This particularly applies to users who actively participate on social media sites as part of their company job function, in order to network with customers and promote brand awareness. |
| c) | TSM Confidential Information policy also applies to blogging. As such, Employees are prohibited from revealing any TSM confidential or proprietary information, trade secrets or any other material covered by TSM Confidential Information policy when engaged in blogging. |
| d) | Employees shall not engage in any blogging that may harm or tarnish the image, reputation and/or goodwill of TSM and/or any of its employees. Employees are also prohibited from making any discriminatory, disparaging, defamatory or harassing comments when blogging or otherwise engaging in any conduct prohibited by TSM Non- Discrimination and Anti-Harassment policy. |
| e) | Employees shall also not attribute personal statements, opinions or beliefs to TSM when engaged in blogging. If an employee is expressing his or her beliefs and/or opinions in blogs, the employee shall not, expressly or implicitly, represent itself as an employee or representative of TSM. Employees shall assume any and all risk associated with blogging. |
| f) | Apart from following all laws pertaining to the handling and disclosure of copyrighted or export controlled materials, TSM trademarks, logos and any other TSM intellectual property shall also not be used in connection with any blogging activity. |
| 6. | Cloud Base Storage Sites: |
The following practices help the organization prevent confidentiality and security breaches [Core-15(b)]:
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#1 | Page 8 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Acceptable Use | ||
Triple-S Management Corporation (TSM) has contracted the services of “Box” (cloud platform). This is the TSM authorized cloud platform for the secure online storage of TSM files.
| a) | User access to “Box” shall be authorized by the Information & Cyber Security Director to support business activities, only in a need-to-know basis to allow the authorized users to perform their jobs functions and responsibilities. |
| b) | All files, data and information with PHI, PII, ePHI or any other sensitive information property of TSM store using the cloud platform (Box) shall be encrypted with PGP or other mechanisms. |
| c) | The use of cloud base store sites such as (Dropbox, OneDrive, Google Drive, Amazon, Copy, and iCloud) are not considered an acceptable use. The Users shall not storage any type of TSM data and/or information. All users shall maintain and protect the confidentiality of all TSM data and information systems. |
| d) | Users shall not use the designated TSM “Box” account for personal use. The storage of files, music, pictures or other data not related to TSM business purposes is prohibited. |
| 7. | Mobile Devices: |
The following practices help the organization prevent confidentiality and security breaches [Core-15(b)]:
This policy establishes the rules for the proper used of mobile devices (BYOD/Corporate Owned) whenever it is use to access to Triple-S Management Corporation (TSM) networks or corporate email, in order to protect the confidentiality of sensitive data, the integrity of data and applications, and the availability of services at TSM, as well as corporate assets (confidentiality and integrity) and continuity of the business (availability).
TSM reserves the right to disconnect any device or disable the access to TSM networks or application services without notification. The users shall use his or her devices always in an ethical manner and agrees to adhere to the TSM applicable policies and procedures.
| a) | Mobile devices must be passwords/PIN protected. |
| b) | Users shall maintain the original device operating system and keep the device current with security patches and updates, as released by the manufacturer. |
| c) | Users shall not “Jail Break” nor “Root” the device (installing software that allows the user to bypass standard built-in security features and controls). |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#1 | Page 9 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Acceptable Use | ||
| d) | Users agree to delete any sensitive business files that may be inadvertently downloaded and stored on the device, and that is not going to be used anymore. |
| e) | Users are responsible for security and backing up all personal information on their mobile devices. |
| f) | Users must take appropriate precautions to prevent others from obtaining access to their mobile device(s). |
| g) | Mobile devices user credentials (User-ID, PIN, and Password) shall not be share with other personnel. |
| h) | Employees are responsible for immediately notifying to TSM in case of device loss or theft. |
| i) | Selected TSM mobile device activities can be tracked and monitored. |
| VII. | Attachments: |
N/A
| Version Control |
Effective Date
|
Approved By (include position name)
|
Amendment
|
| 1 | 09/01/2016 | ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, CIO | 1 |
| 2 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#2 | Page 10 | |||
| Effective Date: 09/01/2016 | |||||
| Approval Date: 09/01/2016 | |||||
| Department: Information Security | Last Review Date: 08/11/2016 | ||||
| Policy Name: | Anti-virus and Anti-Spyware | ||||
|
Drafted by: ▇▇▇▇ ▇▇▇▇▇▇, IT Compliance Supervisor
|
Reviewed by: ▇▇▇▇▇▇ ▇. ▇▇▇▇▇▇▇, Information & Cyber Security Director |
Approved by: ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, Chief Information Officer
|
|||
| I. | Purpose: |
The purpose of this policy is to establish requirements which must be followed by all users of the organization and be met by all computers connected to the TSM network. The adoption and enforcement of the policy help reduce the organization risk against malicious programs such as malware, botnets and computer viruses.
Computer viruses, malware, botnets and spyware are some of the most significant threats against computer environment connected to the Internet. The Internet has made the propagation of malicious programs part of the global cyber-crime industry. This industry today counts with computer viruses, malware, botnets and spyware program developers as well as formal distribution and harvesting channels. One of the main goals of the cyber-crime industry is to steal customer sensitive information and promote fraud and cyber-espionage against individuals and corporations. The channel is highly effective due to the following factors:
| 1. | Easy and rapid access to the internet by cyber criminals. |
| 2. | Cyber-criminals leverage the very low cost of the internet channel. |
| 3. | Billions of users connected to the internet provide a great incentive to cyber-criminals to harvest this channel for committing fraud. |
| 4. | Most internet users have a very low level of awareness cyber-crime and cyber-crime techniques. |
| 5. | Global nature of the internet makes criminal prosecution harder. |
For these reasons proper maintenance and operation of the anti-virus and anti-spyware system is one of the primary security layers used by TSM to protect its IT assets against malware and other types of attacks. The anti-virus and antispyware system is designed to detect and protect the IT assets based on the Windows operating system used by TSM.
| II. | Scope: |
This policy applies to TSM and its subsidiaries employees, temporary workers, contractors, business partners, third party vendors and physical facilities where TSM provides services to its customers.
| III. | Policy: |
This policy help the organization prevent confidentiality and security breaches [Core-15(b)].
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#2 | Page 11 |
| Effective Date: 09/01/2016 | ||
| Approval Date: 09/01/2016 | ||
| Department: Information Security | Last Review Date: 08/11/2016 | |
| Policy Name: Anti-virus and Anti-Spyware | ||
Triple-S Management Corporation (TSM) has developed and adopted the Anti-Virus and Anti- Spyware Policy to provide management with direction and support for the implementation of safeguards to detect, prevent and recover, against malicious programs such as malware, botnets and computer viruses.
| IV. | Definitions: |
| 1. | Virus: A program that enters a computer usually without the knowledge of the operator. Some viruses are mild and only cause messages to appear on the screen, but others are destructive and can wipe out the computer's memory or cause more severe damage. |
| 2. | Botnet: A network of computers created by malware and controlled remotely, without the knowledge of the users of those computers. |
| 3. | Malware: Software that is intended to damage or disable computers and computer systems. Including computer viruses, worms, trojan horses, ▇▇▇▇▇▇ ▇▇▇▇, spyware, adware and other malicious programs. |
| 4. | Spyware: Software that aims to gather information about a person or organization without their knowledge and that may send such information to another entity. |
| V. | Responsibilities: |
All Triple-S Management Corporation (TSM) and its subsidiaries employees, temporary workers, contractors, business partners and third party vendors, without exception, must comply with the information security policies. Any employee found to have violated such Policies may be subject to disciplinary actions, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated.
TSM reserves the right to audit networks, systems, or procedures on a periodic basis to ensure compliance with this policy.
In addition, all TSM personnel shall not interfere with federal or state investigations or disciplinary proceedings by willful misrepresentation or omission of facts or by the use of threats or harassment against any person.
| 1. | Exceptions |
Any exception to the policy must be approved by the Information & Cyber Security Director or Triple-S Management in advance.
| 2. | Non-Compliance |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#2 | Page 12 |
| Effective Date: 09/01/2016 | ||
| Approval Date: 09/01/2016 | ||
| Department: Information Security | Last Review Date: 08/11/2016 | |
| Policy Name: Anti-virus and Anti-Spyware | ||
Any employee found to have violated the policy may be subject to disciplinary actions, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated.
| VI. | Procedure: |
| 1. | TSM Microsoft based Windows servers, workstations and laptop computers must have TSM's approved and supported anti-virus and anti-spyware agent installed and scheduled to run at regular intervals. [Core-15 (b)] |
| 2. | The anti-virus and anti-spyware agent and its virus and spyware signature database must be configured for performing automatic updates of the system malicious program database. [Core-15 (b)] |
| 3. | All new software and files downloaded from the internet must be subject to screening by the anti-virus and anti-spyware system before being allowed in the internal network. [Core- 15(c)] |
| 4. | The Desktop Management Group (DMG) is responsible for removing from the TSM network virus-infected computers until they are verified as virus-free. Confirmation of the verification shall be send to the Information Security Group. [Core-15(c)] |
| 5. | The Infrastructure Management Group (IMG) is responsible for removing from the TSM network virus-infected servers until they are verified as virus-free. Confirmation of the verification shall be send to the Information Security Group. [Core-15(c)] |
| 6. | The Information Security Group is responsible for creating procedures to ensure that anti- virus and anti-spyware software is run at regular intervals, to confirm that computers are verified as virus-free. [Core-15 (b)] |
| 7. | Audit logs shall be generated and be maintained of the checks performed by the anti-virus software. Audit logs of the anti-virus and anti-spyware system will be managed by the Information Security group. [Core-15(c)] |
| 8. | Employees, temporary personnel, contractors and Service providers granted access to the TMS network are prohibited from performing any activities with the intention to create and/or distribute malicious programs into TSM's networks (e.g., viruses, spyware, malware, worms, Trojan horses, e-mail bombs, etc.) are prohibited, in accordance with the TSM Acceptable Use Policy. [Core-15(b)] |
| 9. | Machines with operating systems other than those based on Microsoft Operating System are exempted from this policy. [Core-15 (b)] |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#2 | Page 13 |
| Effective Date: 09/01/2016 | ||
| Approval Date: 09/01/2016 | ||
| Department: Information Security | Last Review Date: 08/11/2016 | |
| Policy Name: Anti-virus and Anti-Spyware | ||
| VII. | Attachments: |
N/A
| Version Control |
Effective Date
|
Approved By (include position name)
|
Amendment
|
| 1 | 09/01/2016 | ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, CIO | 1 |
| 2 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#3 | Page 14 | |||
| Effective Date: 09/01/2016 | |||||
| Review Date: 06/05/2016 | |||||
| Department: Information Security | |||||
| Policy Name: | Asset Management Policy | ||||
|
Drafted by: ▇▇▇▇ ▇▇▇▇▇▇, IT Compliance Supervisor
|
Reviewed by: ▇▇▇▇▇▇ ▇. ▇▇▇▇▇▇▇, Information & Cyber Security Director |
Approved by: ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, Chief Information Officer
|
|||
| I. | Purpose: |
The purpose of this policy is to define requirements to ensure that IT assets are clearly identified and that an inventory of all IT assets is maintained and updated ton ensure accountability and protection of the electronic information stored in the asset. [Core-15(b)]
| II. | Scope: |
This policy applies to TSM and its subsidiaries employees, temporary workers, contractors, business partners, third party vendors and physical facilities where TSM provides services to its customers.
| III. | Policy: |
Triple-S Management Corporation (TSM) has developed and adopted the IT Asset Management Policy to provide management with direction and support to ensure that management requires ownership, defines responsibilities and maintains accountability for the protection of the organization computing assets. [Core-15(b)]
| IV. | Definitions: |
None
| V. | Responsibilities: |
| 1. | All Triple-S Management Corporation (TSM) and its subsidiaries employees, temporary workers, contractors, business partners and third party vendors, without exception, must comply with the information security policies. Any employee found to have violated such Policies may be subject to disciplinary actions, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated. |
| 2. | TSM reserves the right to audit networks, systems, or procedures on a periodic basis to ensure compliance with this policy. |
In addition, all TSM personnel shall not interfere with federal or state investigations or disciplinary proceedings by willful misrepresentation or omission of facts or by the use of threats or harassment against any person.
| 3. | Exceptions |
Any exception to the policy must be approved by the Information & Cyber Security Director or Triple-S Management in advance.
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#3 | Page 15 |
| Effective Date: 09/01/2016 | ||
| Review Date: 06/05/2016 | ||
| Department: Information Security | ||
| Policy Name: Asset Management Policy | ||
| 4. | Non-Compliance |
An employee found to have violated this policy may be subject to disciplinary action, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated.
| VI. | Procedure: |
| 1. | IT Asset Lifecycle Program |
TSM shall implement an IT Asset Lifecycle Program, monitor its effectiveness making changes as needed. TSM shall implement six (6) stages for the lifecycle of an IT asset. The following activities for each stage must include: [Core-15(b)]
| a) | Planning: Defining supporting processes, setting standards for configuration and retention, aligning purchase plans to business goals, collecting aggregate information on intended purchases, and negotiating volume discounts. |
| b) | Procurement: Requisitioning, approving, ordering, receiving and validating orders. |
| c) | Deployment: Tagging assets, entering asset information in a repository, configuring and installing assets including: |
| o | Disabling unnecessary or insecure services or protocols |
| o | Limiting servers to one primary function |
| o | Defining system security parameters to prevent misuse |
| d) | Management: Inventory / counting, monitoring usage, managing contracts for maintenance and support, and monitoring configuration. |
| e) | Support: Adding and changing configurations, repairing devices, and relocating equipment and software. |
| f) | Disposition: Removing assets from service, deleting storage contents, disassembling components for reuse, disposing of equipment, terminating contracts, disposing of equipment, and removing or eliminating assets from the active inventory. |
The inventory of IT assets shall include capital and non-capital assets. Capital assets are considered property, plant and equipment (assets that are usually capitalized). For capital assets an annual inventory must be performed at least once a year. [Core-15(b)]
Non-capital assets are those that are usually, due to the lower cost considered as a supply expense (i.e. pen drives, etc.). [Core-15(b)]
| 2. | Inventory of IT assets |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#3 | Page 16 |
| Effective Date: 09/01/2016 | ||
| Review Date: 06/05/2016 | ||
| Department: Information Security | ||
| Policy Name: Asset Management Policy | ||
The organization shall identify, tag and inventory all IT assets including information (e.g. ePHI, PII) and document the importance of these assets. The IT asset inventory shall include the information necessary to uniquely identify the IT asset. [Core-15(b)]
The inventory of IT assets shall include the following information elements (where applicable): [Core-15(b)]
| o | Equipment serial number. |
| o | Equipment or machine name. |
| o | Information system of which the component is a part. |
| o | Type of information system component (i.e. server, desktop, laptop, application, database, etc.). |
| o | Operating System (OS) type and version. |
| o | Service Pack (SP) level. |
| o | Presence of virtual machines |
| o | Application or database software version/license information (i.e. [***], MS SQL Server). |
| o | Physical location (i.e. building/room number). |
| o | Logical location (i.e. IP address, position with the IS architecture). |
| o | Media access control (MAC) address. |
| o | Ownership by position and role. |
| o | Operational status (i.e. Active/Inactive). |
| o | Primary and secondary system administrators. |
| o | Primary and secondary application administrators. |
| o | Primary business application owner. |
| o | Asset classification level based on data classification criteria (i.e. CONFIDENTIAL). |
| 3. | Equipment assigned to employees, temporary employees or contractors |
Records of property assigned to employees of the organization, temporary employees or contractors (laptops, tablets, cell phones, external drives, and similar peripherals) shall be maintained. [Core-15(b)]
The equipment record shall be used to ensure that all the assigned property is returned to the organization upon the employee termination or transfer out of the department or upon termination of the temporary employee contract or upon termination of the contractor contract. [Core-15(b)]
The manager of the employee or of the contractor is responsible for ensuring that during the employee exit process or the contractor termination process the assigned equipment is returned and that the IT asset inventory is updated. In case of laptops and notebooks the IT
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#3 | Page 17 |
| Effective Date: 09/01/2016 | ||
| Review Date: 06/05/2016 | ||
| Department: Information Security | ||
| Policy Name: Asset Management Policy | ||
asset shall be returned to the Desktop Management Group (DMG) for updating of the IT asset inventory. [Core-15(b)]
Laptops and any other equipment assigned to employees, temporary employees and contractors must be reviewed and updated annually. [Core-15(b)]
| 4. | IT Asset inventory |
TSM shall employ automated mechanisms to scan the network at least on a weekly basis to detect the presence of unauthorized components or devices (including hardware, firmware and software) into the information system. TSM shall disable network access by such components. [Core-15(b)]
| 5. | Inventory of Wireless Access Points (WAP) |
TSM shall maintain an inventory of Wireless Access Points (WAP). This inventory shall also be updated on an annual basis or when WAP are removed or added. [Core-15(b)]
| 6. | Ownership of IT Assets |
All IT assets must be assigned a System Owner who will be responsible for the asset (protection, storage, transfer protocols, destruction). Although property might be assigned to contractors or volunteers for business purposes, ownership will remain in TSM to the officer assigned such ownership. [Core-15(b)]
| 7. | Accepted use of IT Assets |
Refer to Acceptable Use Policy for details.
| 8. | Sensitive System Isolation |
Sensitive systems shall have a dedicated and isolated computing environment. [Core-15(b)]
| VII. | Attachments: |
N/A
| Version Control |
Effective Date
|
Approved By (include position name)
|
Amendment
|
| 1 | 09/01/2016 | ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, CIO | 1 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#4 | Page 18 | |||
| Effective Date: 09/01/2016 | |||||
| Approval Date: 09/01/2016 | |||||
| Department: Information Security | Last Review Date: 08/11/2016 | ||||
| Policy Name: | Backup & Retention | ||||
|
Drafted by: ▇▇▇▇ ▇▇▇▇▇▇, IT Compliance Supervisor
|
Reviewed by: ▇▇▇▇▇▇ ▇. ▇▇▇▇▇▇▇, Information & Cyber Security Director |
Approved by: ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, Chief Information Officer |
|||
| I. | Purpose: |
The purpose of this policy is to establish the organization backup and retention policy in order to protect the confidentiality, integrity and availability of critical data required to support TSM business operations.
| II. | Scope: |
This policy applies to all TSM and its subsidiaries equipment (e.g. laptops, desktops, servers etc.), data and systems, owned or operated by TSM where the organization provides services to its customers. In order to safeguard the information assets of TSM and to prevent the loss of data in the case of an accidental deletion or corruption of data, system failure, or a disaster.
| III. | Policy: |
This policy supports the organization plan for storage, maintenance and destruction information [Core-13b].
Triple-S Management Corporation (TSM) has developed and adopted the Backup and Retention Policy to provide management with direction and support for the implementation of secured and protected backup processes in order to ensure the availability of the critical business information in case of major disaster or system interruption. The implementation of robust backup and retention procedures also help minimize potential loss or corruption of critical data reducing the organization level of risk against unexpected interruptions and events.
| IV. | Definitions: |
| 1. | Backup: The activity of storing data, files or databases in a secured environment (equipment, cloud) in case of catastrophe or hardware failure. |
| 2. | Full Backup: A backup of a set of specified files, often the entire contents of a disk, regardless of when they were last modified. |
| 3. | Incremental Backup: Incremental backups only backup the files that have been modified since the last backup. If dump levels are used, incremental backup’s only backup files changed since last backup of a lower dump level. |
| 4. | Restore: The process of copying files forms a backup location to a hard drive or other acceptable media. A restore can be performed when backup data is needed and as part of a testing process. |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#4 | Page 19 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Backup & Retention | ||
| 5. | Encryption: Cryptographic transformation of data (called "plaintext") into a form (called "cipher text") that conceals the data's original meaning to prevent it from being known or used. |
| 6. | Retention: The period established to keep backup media. This period must be in compliance with local and Federal regulations. |
| V. | Responsibilities: |
| 1. | All Triple-S Management Corporation (TSM) and its subsidiaries employees, temporary workers, contractors, business partners and third party vendors, without exception, must comply with the information security policies. Any employee found to have violated such Policies may be subject to disciplinary actions, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated. |
| 2. | TSM reserves the right to audit networks, systems, or procedures on a periodic basis to ensure compliance with this policy. |
In addition, all TSM personnel shall not interfere with federal or state investigations or disciplinary proceedings by willful misrepresentation or omission of facts or by the use of threats or harassment against any person.
| 3. | Exceptions |
Any exception to the policy must be approved by the Information & Cyber Security Director or Triple-S Management in advance.
| 4. | Non-Compliance |
Any employee found to have violated the policy may be subject to disciplinary actions, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated.
| VI. | Procedure: |
This procedure supports the organization process for storage, maintenance and destruction information [Core-13b].
| 1. | Scheduling and Retention: |
| a) | TSM shall implement backup and retention schedules to ensure that application and system data are safeguarded against destruction and lost. |
| b) | TSM is committed to retain and preserve the application and system data for the period of time required by federal and local laws and with the requirements of the Record Retention policy. |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#4 | Page 20 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Backup & Retention | ||
| c) | Full and incremental backups shall be performed and verified on a daily, weekly, and monthly basis for Mainframe, Unix, Windows and VM ▇▇▇▇ base systems. |
| d) | A full backup shall be made at least once a month and will be retained for a minimum of one year. |
| e) | A full backup shall be made at least once a year and will be retained for a minimum of ten years. |
| f) | Full and incremental backups shall be performed for all business applications and databases. |
| g) | All backups shall be subject to verification on a daily, weekly, and monthly basis and backup error conditions should be monitored, log and notified to management for investigation and executions of the backup process. |
| h) | Automatic backup verification process shall be performed, to ensure backups are completed successfully and without error. |
| i) | Backups shall be monitored and problem management procedures shall be followed if error conditions are generated that could impact the integrity and completeness of the backup process. |
| j) | Procedures for retention, and storage of backup media shall be designed, implemented and documented. Backup tapes will be rotated on a daily, weekly, and monthly basis to a secured off-site storage facility (International Safe Deposit) and maintained according to a predefined retention schedule. |
| k) | Tape media inventory shall be performed on a monthly and quarterly basis for mainframe and distributed systems, respectively. |
| l) | Controls must be in place to ensure backup tapes data are not reuse until retention period expires. |
| 2. | Onsite and Offsite Storage: |
| a) | Depending on the criticality of the data, TSM shall ensure its preservation by moving the data to the contracted offsite backup storage facility using a data encryption mechanism. |
| b) | Data considered critical for the business continuity must be moved to an offsite storage at least once a week. |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#4 | Page 21 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Backup & Retention | ||
| c) | Network infrastructure backups, and system critical files must be moved to an offsite storage at least once a month. |
| d) | When the backup service is delivered by the third party, the service level agreement shall include the detailed protections to control confidentiality, integrity, and availability of the back-up information. |
| 3. | Storage Access and Security: |
| a) | All backup media must be stored in a secure area that is accessible only to authorized personnel. |
| b) | Physical and environmental controls shall be in place to protect the backup tapes. |
| 4. | Restorations: |
| a) | All restorations require approval from the designated Data Owner and/or Application Owner. The requestor must fill out a "Restore and Recovery Data" form. |
| 5. | Verification: |
| a) | The backup system shall be tested periodically by restoring a single random file from a random equipment, and manually inspecting it for accurate recovery. The recovery tests will be stored into secured temporary areas so that current "real" user copies of the files will not be overwritten. |
| b) | Backup verification processes must be enabled to facilitate the automatic backup verification purposes and adequate exception notification configured. |
| c) | Failed backups will be re-started twice automatically by the backup tools implemented at TriServe. |
| 6. | Documentation: |
| a) | Backup procedure must be documented. Procedure should describe how to execute backup process and the data restoration process. The procedure must include a list of all the systems and files that are backed up as well as frequency, retention and in-site / off-site backup details. |
| 7. | Responsibilities and other important consideration: |
| a) | Information that it is stored in the "My Documents" folder of the user (e.g. Desktop) will not be backed-up, it is the responsibility of the employee to store all important and critical TSM information in the "My Documents” folder. |
| VII. | Attachments: |
ATTACHMENT A - Backup & Retention Procedure [Core-13b]
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#4 | Page 22 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Backup & Retention | ||
| Version Control |
Effective Date
|
Approved By (include position name)
|
Amendment
|
| 1 | 09/01/2016 | ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, CIO | 1 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#5 | Page 23 | |||
| Effective Date: 09/01/2016 | |||||
| Approval Date: 09/01/2016 | |||||
| Department: Information Security | Last Review Date: 08/11/2016 | ||||
| Policy Name: | Change Management | ||||
|
Drafted by: ▇▇▇▇ ▇▇▇▇▇▇, IT Compliance Supervisor
|
Reviewed by: ▇▇▇▇▇▇ ▇. ▇▇▇▇▇▇▇, Information & Cyber Security Director |
Approved by: ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, Chief Information Officer
|
|||
| I. | Purpose: |
The purpose of this policy is to establish the requirements of the change management process required to control the request, approval and implementation of changes to TSM systems, applications and IT infrastructure. The objective of the policy if to help to minimize the risk of impact to TSM IT services and customers as well as resulting in the introduction of significant vulnerabilities in the TSM IT systems.
| II. | Scope: |
This policy applies to TSM and its subsidiaries employees, temporary workers, contractors, business partners, third party vendors and physical facilities where TSM provides services to its customers and host its IT systems, applications and IT infrastructure components.
| III. | Policy: |
This policy supports the organization data integrity process of electronic information [Core- 13(a)].
Triple-S Management Corporation (TSM) has adopted a Change Management Policy to provide management with direction and support for the implementation of processes and controls to effectively manage risks associated with changes to IT systems and the organization IT infrastructure. As a standard practice changes should be documented, approved, tested and validated. This policy is designed to ensure the organization designs and implement procedures and controls for management of the change management process. These processes and controls are required to meet operational and compliance requirements as well as reduce the level of risk for the organization by ensuring that changes are subject to an approval process before being deployed to the production environment.
| IV. | Definitions: |
| 1. | Change Management: A systematic approach to managing all changes made to a product or system. |
| 2. | Fallback: Actions to revert software implemented changes that failed and therefore it is requiring going back to the original state. |
| 3. | Outsourced software development: Software made by a third party contracted by an organization with specific requirements. |
| V. | Responsibilities: |
| 1. | All Triple-S Management Corporation (TSM) and its subsidiaries employees, temporary workers, contractors, business partners and third party vendors, without exception, must |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#5 | Page 24 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Change Management | ||
comply with the information security policies. Any employee found to have violated such Policies may be subject to disciplinary actions, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated.
TSM reserves the right to audit networks, systems, or procedures on a periodic basis to ensure compliance with this policy.
| 2. | In addition, all TSM personnel shall not interfere with federal or state investigations or disciplinary proceedings by willful misrepresentation or omission of facts or by the use of threats or harassment against any person. |
| 3. | Exceptions |
Any exception to the policy must be approved by the Information & Cyber Security Director in advance.
| 4. | Non-Compliance |
An employee found to have violated this policy may be subject to disciplinary action, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated.
| VI. | Procedure: |
This procedure supports the organization data integrity process of electronic information [Core-13(a)].
| 1. | Changes to Information Technology (IT) assets and systems, such as operating system, hardware, software, application, and network component shall follow the organization change management process. This process shall ensure that changes are documented, authorized, tested, approved and properly implemented. |
| 2. | For custom developed applications and the implementation of package applications, TSM shall ensure that data input validation controls are tested to ensure that the data is correct and appropriate. |
| 3. | The following activities shall be adopted within the change management process: |
| a) | Change Request Form (CR Form): Documentation of the change shall be completed explaining the purpose, details and consequences of the proposed change. All change requests shall be prioritized in terms of benefits, urgency, effort required and potential impact on TSM operations. The CR Form shall include Risk and Impact considerations about the proposed change. |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#5 | Page 25 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Change Management | ||
| b) | Version Control: Change requests and/or updates shall be controlled with version control numbers. Access to system files and program source code shall be restricted to authorized personnel and only authorized personnel shall have access to the version control system. |
| c) | Testing: Changes to TSM systems and IT infrastructure (i.e. servers, databases, applications, system access level and end-user access level) shall be tested in an isolated, controlled environment (where feasible) prior to implementation. The testing process shall verify that intended changes will meet the stated objectives and not cause operational problems, service interruptions or introduce security risks to the organization. |
| d) | Approval: All changes shall be approved prior to implementation. Approval of changes shall be based on the documented acceptance criteria (i.e. a change request form is completed and approved by TSM personnel, an impact assessment was performed and proposed changes were tested). All users, significantly affected by a change, shall be notified. The user representative such as the Application Owner shall sign-off on the change request form. |
| e) | Implementation: Implementation shall only be undertaken after appropriate testing and approval by the designated TSM stakeholders. Implementation of changes to the production environment shall be performed only by authorized TSM systems administrator or by the designated IT personnel such as Database administrator or the Application Administrator. Production systems shall only hold approved programs and required executable code. No development code or compilers shall reside in production systems. Any decision to upgrade (software) to a new release shall take into account the business requirements for the change, and the security and privacy impacts of the release. |
| f) | Fallback: Fallback procedures shall be defined and implemented. This includes defining procedures and roles and responsibilities for aborting/cancelling and recovering from unsuccessful changes and unforeseen events. |
| g) | Post Implementation: All changes shall be monitored once they have been implemented to check for unexpected behavior or incidents. |
| 4. | Emergency Changes shall follow documented procedures to ensure the proper control and authorization. |
| 5. | Outsourced software development shall be reviewed to ensure that the contracts shall have considerations for: code ownership, intellectual property rights, escrow arrangements, right to audit, requirements for quality of code, and technical support. |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#5 | Page 26 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Change Management | ||
| 6. | All internally developed software and all changes to internally developed software that will be accessible via the internet must be subject to a code verification process. The Quality Assurance Group to reduced risks associated with potential vulnerabilities at the application level establish a subscription to use the Code Scanning service to facilitated and conduct this verification process. |
| VII. | Attachments: |
ATTACHMENT B - Change Management process [Core-13(a)]
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#6 | Page 27 | |||
| Effective Date: 09/01/2016 | |||||
| Approval Date: 09/01/2016 | |||||
| Department: Information Security | Last Review Date: 08/11/2016 | ||||
| Policy Name: | Clear Desk & Clear Screen | ||||
|
Drafted by: ▇▇▇▇ ▇▇▇▇▇▇, IT Compliance Supervisor
|
Reviewed by: ▇▇▇▇▇▇ ▇. ▇▇▇▇▇▇▇, Information & Cyber Security Director |
Approved by: ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, Chief Information Officer
|
|||
| I. | Purpose: |
The purpose of this policy is to establish requirements for maintaining a “Clear Desk” & “Clear Screen” procedures where sensitive/confidential information about our employees, our intellectual property, our customers and our vendors is secure in locked areas and out of site.
This Policy is not only about security, but it is also part of the TSM Privacy Policies and it has the purpose to reduce the risk of security breaches in the workplace.
| II. | Scope: |
This policy applies to all TSM and its subsidiaries employees, temporary workers, contractors, business partners, third party vendors and physical facilities where TSM provides services to its customers.
| III. | Policy: |
This policy help the organization prevent confidentiality and security breaches [Core-15(b)] and provide guidance to employees on how to shred and destroy paper documents [CORE-13(b)].
Triple-S Management Corporation (TSM) has developed and adopted a Clear Desk & Clear Screen policy to ensure that sensitive/confidential information (on paper or electronic media) are removed from the end user workspace, locked away when the items are not in use or an employee leaves his/her workstation and clear screen for information assets. This Policy shall take into account the information classification, legal and contractual requirements, and the corresponding risks and cultural aspects of TSM.
| IV. | Definitions: |
None
| V. | Responsibilities: |
| 1. | All Triple-S Management Corporation (TSM) and its subsidiaries employees, temporary workers, contractors, business partners and third party vendors, without exception, must |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#6 | Page 28 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Clear Desk & Clear Screen | ||
comply with the information security policies. Any employee found to have violated such Policies may be subject to disciplinary actions, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated.
| 2. | TSM reserves the right to audit networks, systems, or procedures on a periodic basis to ensure compliance with this policy. |
In addition, all TSM personnel shall not interfere with federal or state investigations or disciplinary proceedings by willful misrepresentation or omission of facts or by the use of threats or harassment against any person.
| 3. | Exceptions |
Any exception to the policy must be approved by the Information & Cyber Security Director in advance.
| 4. | Non-Compliance |
An employee found to have violated this policy may be subject to disciplinary action, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated.
| VI. | Procedure: |
The following practices help the organization prevent confidentiality and security breaches [Core-15(b)]:
| 1. | Sensitive/Confidential business information in paper or electronic storage media shall be locked away in secure cabinets when not required, especially when the office is vacated for a short or extended period of time. |
| 2. | File cabinets containing business sensitive/confidential information shall be kept closed and locked when not in use or when not attended. |
| 3. | Keys used for access to confidential information shall not be left at an unattended desk and they shall be kept in a secure place. |
| 4. | Computer and terminals shall be logged off or protected with a screen and keyword locking mechanism controlled by a password (e.g., (“Ctrl+Alt+Del”) in Windows systems), token or similar user authentication mechanism that conceals information previously visible on the display when unattended and shall be protected by key locks, passwords, or other controls when not in use. |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#6 | Page 29 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Clear Desk & Clear Screen | ||
| 5. | Unattended portable computing devices such as laptops and tablets shall be either locked with a locking cable, locked away in a drawer or kept in a restricted area where only authorized employees are authorized to access. |
| 6. | Employee shall treat mass storage devices such as CD-ROM, DVD or USB drives as sensitive and secure them in a locked drawer when not in use. |
| 7. | Passwords shall not be written on sticky notes or posted on under a computer, nor shall they be left written down in accessible locations. |
| 8. | Incoming and outgoing mail points and unattended facsimile machines shall be protected and unauthorized use of photocopiers shall be prevented. |
| 9. | All printers, copiers and facsimile machines shall be cleared of documents as soon as they are printed to ensure that sensitive printouts are not left in printer trays for the wrong person to pick up. |
| 10. | When transporting documents with Sensitive/Confidential within facilities and through inter- office mail, information shall not be visible through envelope windows and envelopes shall be marked according its classification level (e.g., “Confidential”). |
| 11. | Sensitive/Confidential documents shall be placed in the official shredder bins/recycling bins or placed in the locked secured disposal recycling bins contracted by the organization for the secured destruction of the documents. [CORE-13(b)] |
| 12. | Whiteboard containing sensitive/confidential information shall be erased. [CORE-13(b)] |
| VII. | Attachments: |
N/A
| Version Control |
Effective Date
|
Approved By (include position name)
|
Amendment
|
| 1 | 09/01/2016 | ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, CIO | 1 |
| 2 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#7 | Page 30 | |||
| Effective Date: 09/01/2016 | |||||
| Approval Date: 09/01/2016 | |||||
| Department: Information Security | Last Review Date: 08/11/2016 | ||||
| Policy Name: | Data Classification | ||||
|
Drafted by: ▇▇▇▇ ▇▇▇▇▇▇, IT Compliance Supervisor
|
Reviewed by: ▇▇▇▇▇▇ ▇. ▇▇▇▇▇▇▇, Information & Cyber Security Director |
Approved by: ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, Chief Information Officer
|
|||
| I. | Purpose: |
The purpose of the Data Classification Policy is to ensure that TSM IT assets receive an appropriate level of protection based on the type of information stored and managed. As such the policy required a data centric and risk base focus for the design and implementation safeguard for protection of the most sensitive data including ePHI. [Core-15(b)]
| II. | Scope: |
This policy applies to TSM and its subsidiaries employees, temporary workers, contractors, business partners, third party vendors and physical facilities where TSM provides services to its customers.
| III. | Policy: |
Triple-S Management Corporation (TSM) has defined and documented a Data Classification Policy to provide management with direction and support for the proper handling of information considering the sensitivity and risk of such data. In order to ensure proper management, information must be first classified according to its level of risk and sensitivity considering local and federal regulations. The higher the sensitivity and risk, the higher the classification to be assigned and therefore more controls will be needed to ensure only authorized personnel can access such information. [Core-15(b)]
Users shall be made aware of their responsibilities for proper handling of information received, created, processed, stored, distributed and destroyed by TSM according to its sensitivity and assigned data classification level. [Core-15(b)]
| IV. | Definitions: |
| 1. | Information Owner: Responsible for determining who has access to the information he/she owns. Usually senior management or department head. |
| 2. | Information Custodian: Responsible for assigning the access to the information according to the instructions of the information owner. |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#7 | Page 31 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Data Classification | ||
| 3. | Information User: Responsible for the application of this policy in his/her daily activities in TSM and its subsidiaries. |
| V. | Responsibilities: |
| 1. | All Triple-S Management Corporation (TSM) and its subsidiaries employees, temporary workers, contractors, business partners and third party vendors, without exception, must comply with the information security policies. Any employee found to have violated such Policies may be subject to disciplinary actions, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated. |
| 2. | TSM reserves the right to audit networks, systems, or procedures on a periodic basis to ensure compliance with this policy. |
In addition, all TSM personnel shall not interfere with federal or state investigations or disciplinary proceedings by willful misrepresentation or omission of facts or by the use of threats or harassment against any person.
| 3. | Exceptions |
Any exception to the policy must be approved by the Information & Cyber Security Director in advance.
| 4. | Non-Compliance |
An employee found to have violated this policy may be subject to disciplinary action, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated.
| VI. | Procedure: |
| 1. | Classification Levels |
Four levels of data classification have been defined: [Core-15(b)]
| Level | Description | Examples |
|
PUBLIC
|
Information officially released by TSM for widespread public disclosure. | Press releases, public marketing materials, employment advertising, annual reports, product brochures, the public web site, etc. |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#7 | Page 32 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Data Classification | ||
|
INTERNAL
|
All forms of proprietary information originated or owned by TSM, or entrusted to it by others that is not considered sensitive or confidential. | General organization charts (with no names, only positions), policies, procedures, phone directories (excluding client contact information), some types of training materials. |
|
CONFIDENTIAL
|
Information for which the unauthorized disclosure or compromise would likely have an adverse impact on the company's competitive or financial position, or compromise regulatory compliance of local and Federal laws for protecting personal information. | Trade secrets & marketing, PHI or EPHI, operational, financial, employee user ID’s, passwords, PINs, or other personal identification devices, source code, and technical information integral to the success of our company. |
|
HIGHLY RESTRICTIVE
|
Includes information that is so sensitive that disclosure or usage would have a definite impact on the TSM’s business and future.
Significant restrictions and controls need to be applied.
|
Merger and acquisition information, reorganization documents, security protocol information, legal actions, strategic or tactical information of the organization and its subsidiaries, etc. |
| a) | All information generated by or for TSM, no matter the format: written, verbal, or electronic, is to be treated according to its classification level. [Core-15(b)] |
| b) | If the information is not labeled, personnel must assume it’s confidential. [Core-15(b)] |
| c) | Information that is labeled as public or internal use, but is in draft form or has not been formally approved, it should also be considered confidential. [Core-15(b)] |
| d) | All employees should familiarize themselves with the information labeling and handling guidelines included in the procedures document. [Core-15(b)] |
| e) | It should be noted that the sensitivity level classifications were created as guidelines and to emphasize appropriate measures that users have to take to protect TSM and third Party Confidential information. [Core-15(b)] |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#7 | Page 33 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Data Classification | ||
| f) | Nothing in this policy is, however, intended to prevent employees from engaging in concerted activity protected by law. [Core-15(b)] |
| 2. | Information Owner |
The Information Owner also known as the Application Owner is the leader of a business area or service who is directly responsible for the proper use of the area’s information under his/her management. Such use must be performed, based on the objectives of TSM business. The information owner is responsible for classifying the information, deciding who must have access to it and validating that the security is commensurate according to its assigned classification and that controls are implemented in consistency with such classification. The owner must also periodically review the classification, ensure it is kept up to date and ensure the classification is correct. [Core-15(b)]
Documentation that a physical inventory has been taken, for all locations, shall be retained in the organization’s central accounting office. [Core-15(b)]
| 3. | Information Custodian |
The Information Custodian also known as the Data Custodian is responsible for ensuring that access to TSM information is consistent with the information owner’s requirements and updating such access as personnel changes his responsibilities, is transferred to another unit (and therefore another information owner) and eliminating access if personnel is terminated. [Core-15(b)]
| 4. | Considerations |
The data classification process must consider: [Core-15(b)]
| a) | Business needs for sharing or restricting information. |
| b) | The business impacts associated with such needs. |
| c) | The aggregation effect in the classification process (consider groups of similar information assets and how their individual classification may impact the group or conglomerate of such assets: i.e. if similar information assets have been assigned different classifications, re-consider the classification of each one). |
| 5. | Information asset life cycle |
Information assets should be protected in all phases of their life cycle: received/created, processed, storing, transmittal and destruction. The protection must be according to the classification assigned. Details of how to protect the information asset will be presented in a procedure document. [Core-15(b)]
| 6. | Third Party Confidential Information |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#7 | Page 34 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Data Classification | ||
A subset of TSM Confidential information is "TSM Third Party Confidential" information. This is information that belongs to another corporation which has been entrusted to TSM by that company under non-disclosure agreements (NDA’s) and other contracts as part of the business agreement between both parties. Examples of this type of information include everything from joint business activities to vendor lists, customer orders, and supplier information. Information in this category ranges from extremely sensitive to information about the fact that we’ve connected a supplier / vendor into TSM network to support our operations. [Core-15(b)]
| VII. | Attachments: |
N/A
| Version Control |
Effective Date
|
Approved By (include position name)
|
Amendment
|
| 1 | 09/01/2016 | ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, CIO | 1 |
| 2 |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#8 | Page 35 | |||
| Effective Date: 09/01/2016 | |||||
| Approval Date: 09/01/2016 | |||||
| Department: Information Security | Last Review Date: 08/11/2016 | ||||
| Policy Name: | Data Integrity and Interoperability | ||||
|
Drafted by: ▇▇▇▇ ▇▇▇▇▇▇, IT Compliance Supervisor
|
Reviewed by: ▇▇▇▇▇▇ ▇. ▇▇▇▇▇▇▇, Information & Cyber Security Director |
Approved by: ▇▇▇▇ ▇▇▇▇ ▇▇▇▇▇▇, Chief Information Officer |
|||
| I. | Purpose: |
This policy provides direction for management of the information as a valuable and strategic resource through establishment of the required processes and controls to ensure the accuracy and integrity of the information managed by the organization.
| II. | Scope: |
This policy applies to TSM and its subsidiaries employees, temporary workers, contractors, business partners, third party vendors and physical facilities where TSM provides services to its customers.
| III. | Policy: |
This policy supports the organization data integrity process of electronic information [Core- 13(a)].
Information has most value when it is complete, accurate, relevant, accessible and timely (CARAT). This policy describes the commitment of Triple-S Management for designing, implementing, and maintaining procedures and controls for proper management of its information. This includes ensuring the accuracy and interoperability of the information managed by the core systems of the organization.
| IV. | Definitions: |
| 1. | Data: numbers, words or images that have yet to be organized or analyzed to answer a specific question. It is often interchangeable with the word ‘information’. |
| 2. | Data Quality: ensuring data is ‘fit for purpose’ and ‘right first time’, which includes the relevance, correctness, completeness and timeliness of all data held in all Trust systems |
| 3. | Document: smallest complete unit of recorded material which is accumulated to form a file. |
| 4. | Information: Produced through processing, manipulating and organizing data to answer questions, adding to the knowledge of the receiver. It is often interchangeable with the word data. |
| 5. | Information Management: a collection and management of information from one or more sources and the distribution of that information to one or more audiences. Management means the organization of and control over the planning, structure and organization, controlling, processing evaluating and reporting of information activities in order to meet the Trust’s objectives and to enable corporate functions in the delivery of information. |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#8 | Page 36 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Data Integrity and Interoperability | ||
| 6. | Software Life Cycle Development: The systems development life cycle (SDLC), also referred to as the application development life-cycle, is a term used in systems engineering, information systems and software engineering to describe a process for planning, creating, testing, and deploying an information system. |
| 7. | Change Management Process: Change Management (CM) refers to any approach to transitioning individuals, teams, and organizations using methods intended to re-direct the use of resources, business process, budget allocations, or other modes of operation that significantly reshape a company or organization. |
| 8. | Referential Integrity: Referential integrity is a relational database concept, which states that table relationships must always be consistent. In other words, any foreign key field must agree with the primary key that is referenced by the foreign key. |
| 9. | Data Purging: Data purging is a term that is commonly used to describe methods that permanently erase and remove data from a storage space. There are many different strategies and techniques for data purging, which is often contrasted with data deletion. Deletion is often seen as a temporary preference, whereas purging removes the data permanently and opens up memory or storage space for other uses |
| 10. | Sensitive Information: Sensitive information is defined as information that is protected against unwarranted disclosure. |
| V. | Responsibilities: |
| 1. | All Triple-S Management Corporation (TSM) and its subsidiaries employees, temporary workers, contractors, business partners and third party vendors, without exception, must comply with the information security policies. Any employee found to have violated such Policies may be subject to disciplinary actions, up to and including termination of employment. In the event the violation has been by a contractor and/or provider, the respective contract or service may be deemed terminated. Triple-S Management Corporation (TSM) reserves the right to audit networks, systems, or procedures on a periodic basis to ensure compliance with this policy. |
In addition, all TSM personnel shall not interfere with federal or state investigations or disciplinary proceedings by willful misrepresentation or omission of facts or by the use of threats or harassment against any person.
| 2. | Exceptions |
The Information & Cyber Security Director or Triple-S Management must approve any exception to the policy in advance.
| 3. | Non-Compliance |
CONFIDENTIAL TREATMENT REQUESTED. INFORMATION FOR WHICH CONFIDENTIAL TREATMENT HAS BEEN REQUESTED IS OMITTED AND MARKED WITH “[***]”. AN UNREDACTED VERSION OF THE DOCUMENT HAS ALSO BEEN FURNISHED SEPARATELY TO THE SECURITIES AND EXCHANGE COMMISSION AS REQUIRED BY RULE 24B-2 UNDER THE SECURITIES EXCHANGE ACT OF 1934, AS AMENDED.
|
|
Policy No.: ISP#8 | Page 37 | |
| Effective Date: 09/01/2016 | |||
| Approval Date: 09/01/2016 | |||
| Department: Information Security | Last Review Date: 08/11/2016 | ||
| Policy Name: | Data Integrity and Interoperability | ||
An employee found to have violated this policy may be subject to disciplinary action, up to and including termination of employment.
| VI. | Procedure: |
This procedure supports the organization data integrity process of electronic information [Core-13(a)].
| 1. | Data Accuracy and Trace-Ability: |
| a) | The organization will follow the System Development Life Cycle (SDLC) process for all internal system development activities. The SDLC provides a structured methodology for the design, development, testing and implementation of new systems and reduces the risk associated with errors that could be generated by the introduction of new programs. |
| b) | To promote data accuracy the organization promotes the adoption of relational databases structures for its core systems (e.g. [***]). In a relational database framework referral integrity between tables will be enforced by the definition of primary and secondary keys. Maintaining referential integrity ensures the consistency of the data stored by avoiding duplicate records and records with invalid information. |
| c) | To promote data accuracy new systems must be subject to user testing and certification steps. Test results must be documented and retained as part of the project documentation. |
| d) | To promote data accuracy system and applications must be designed to validate data fields registered by end users. For online systems data entry errors must notify the user by generating an error message. |
| e) | To promote data accuracy files received will be subject to a data validation process prior to processing. Records with errors will be reported and will require investigation and be subject to a clearance process in order to continue processing. |





