Managed Services Agreement
EXHIBIT 99.1

This Services Agreement (this Agreement) is made as of June 12, 2009 (the “effective date”), by and between ProNet Solutions, Inc., an Arizona corporation maintaining its corporate offices at 0000 Xxxx Xxxxxx Xxxxxx Xxxxxxxxx, Xxxxx 000, Xxxxxxx, Xxxxxxx 00000 (ProNet), and American River Bankshares (ARB), an California corporation maintaining offices at 0000 Xxxxxxxxx Xx, Xxxxx 000, Xxxxxx Xxxxxxx, XX 00000.
WITNESSETH
Whereas, ARB desires to engage ProNet to provide an outsourced solution for managing and supporting the enterprise LAN/WAN network to ARB in connection with a “managed services” solution (“Services”); and
Whereas, ProNet is willing to provide such services to ARB upon the terms and conditions set forth herein.
Now, therefore, in consideration of the mutual promises and covenants contained herein, the parties agree as follows:
|
|
|
|
|
|
1. |
SCOPE OF SERVICES |
|
|
|
|
|
|
|
|
a. |
ProNet agrees to undertake the services set forth on Schedule A, the Managed Services for Technology Platform Support Proposal (“Proposal”), attached hereto and incorporated herein by this reference. ProNet may be retained to provide additional services beyond the Services subject to agreement between ARB and ProNet, which additional services shall be subject to the terms and conditions of this Agreement. |
|
|
|
|
|
|
|
|
b. |
In performing the Services under this Agreement, ProNet shall report and be responsible to the Chief Information Officer of ARB or such other person(s) as may be subsequently designated by ARB. This person shall also be designated as the Bank’s Relationship Manager for ProNet unless otherwise requested by ARB. |
|
|
|
|
|
|
2. |
TERM |
|
|
|
|
|
|
|
|
a. |
The initial term of this Agreement shall commence upon July 1, 2009 and shall last for three (3) years. |
|
|
|
|
|
|
3. |
COMPENSATION |
|
|
|
|
|
|
|
|
a. |
During the term of this Agreement, ARB agrees to pay to ProNet, as full and complete payment for the performance of the Services, the fees actually incurred for the Services as set forth in Schedule A (the “Fee”). ARB acknowledges that this fee structure enables it to predict the technology cost of their growth and expansion. ProNet acknowledges that it is not entitled to any other compensation of any kind whatsoever unless specifically indicated on Schedule A or covered by a separate written agreement between the parties. |
|
|
|
|
|
|
|
|
b. |
“Fees” are due and payable monthly upon receipt of invoice. ARB shall be invoiced no later than the 15th day of the month preceding the month in which the services are rendered, with the payment terms being net 30 days. Any amounts remaining unpaid by the due date shall be subject to a late fee of 1.5% per month |
All information contained herein is
Confidential
Page 4 of 43

|
|
|
|
|
|
|
|
|
of the outstanding balance. In the event any undisputed amounts due are knowingly or intentionally left unpaid beyond the 30th day after payment is due, ARB shall pay a collection fee of $500 per outstanding invoice and be subject to the termination provisions provided for below in Section 9. Any invoice submitted by ProNet shall be deemed correct unless ARB provides written notice to ProNet within 15 days of the invoice date specifying the nature of the disagreement. ARB agrees that it shall neither make nor assert any right of deduction or set-off from invoices submitted by ProNet for ProNet Services. |
|
|
|
|
|
|
4. |
PRONET’S REPRESENTATIONS AND OBLIGATIONS |
|
|
|
|
|
|
|
|
|
a. |
ProNet represents and warrants to ARB that they are not now nor shall they be a party to any other agreement or under any obligation to or restriction by any third party which would prevent ProNet from entering into this Agreement or which would adversely affect this Agreement, ProNet’s performance of the Services or any of the undertakings set forth herein in any manner. |
|
|
|
|
|
|
|
|
|
|
b. |
ProNet agrees to keep all necessary records relating to the performance of the Services as ARB may direct. |
|
|
|
|
|
|
|
|
|
|
c. |
ProNet warrants that the provision of the Services shall be in accordance with all applicable federal, state and local laws, including any law, order or regulatory provision concerning equal employment opportunities by federal contractors, and to ARB’s reasonable satisfaction. |
|
|
|
|
|
|
|
|
|
|
d. |
ProNet acknowledges and agrees that the results of all of the Services are the sole and exclusive property of ARB. Upon request or upon the termination of this Agreement, ProNet shall promptly deliver to ARB all notes, writings, lists, files, reports, correspondence, tapes, cards, technical data or any product or document (whether maintained in tangible documentary form, or in computer memory or other electronic format) that ProNet or ProNet’s employees produced or received while performing the Services. |
|
|
|
|
|
|
|
|
|
|
e. |
Privacy of Consumer Financial Information |
|
|
|
|
|
|
|
|
|
|
|
All capitalized terms used in this Section and not otherwise defined shall have the meanings set forth in the Federal “Privacy of Consumer Financial Information” Regulation (12 CFR Part 40), as amended from time to time (the “Privacy Regulation”), issued pursuant to Section 504 of the Xxxxx-Xxxxx-Xxxxxx Act (15 X.X.X 0000 et seq.). The parties acknowledge that the Privacy Regulation governs disclosures of nonpublic information about consumers. |
|
|
|
|
|
|
|
|
|
|
|
ProNet further hereby represents and warrants that it will comply with all aspects of the California Information Privacy Act or any other State statute, regulation, or ruling with regard to maintaining the confidentiality of consumer information. |
|
|
|
|
|
|
|
|
|
|
|
ProNet hereby represents and warrants as follows with respect to any Nonpublic Personal Information which ProNet may become aware of or receive while engaged under this contract. ProNet agrees it shall: |
|
|
|
|
|
|
|
|
|
|
|
|
|
i. |
Comply with the terms and provisions of the Privacy Regulation, including, without limitation, the provisions regarding the sharing of Nonpublic Personal Information (as defined in the Privacy Regulation); |
|
|
|
|
|
ii. |
Not disclose or use any Nonpublic Personal Information that it obtains from ARB and/or any of its subsidiaries, except to carry out the |
All information contained herein is
Confidential
Page 5 of 43

|
|
|
|
|
|
|
|
|
|
|
|
|
purposes for which ARB provided such Nonpublic Personal Information, or as otherwise permitted by the Privacy Regulation and other applicable Federal, State or local laws and ARB’s privacy policies and procedures; |
|
|
|
|
|
iii. |
Not make any changes to its security measures that would increase the risk of an unauthorized access; and |
|
|
|
|
|
iv. |
Not disclose any Nonpublic Personal Information obtained by ProNet to any other entity, except as follows; |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
a. |
To ARB’s Affiliates, with the prior consent of ARB; |
|
|
|
|
|
|
|
b. |
To ProNet’s affiliates, provided, that its affiliates may, in turn, disclose and use the information only to the extent that ProNet may disclose and use the information; |
|
|
|
|
|
|
|
c. |
To an unaffiliated third party with the prior consent of ARB, in the ordinary course of business in order to carry out the activity for which the information was disclosed to ProNet pursuant to one of the following exceptions to the Privacy Regulation; |
|
|
|
|
|
|
|
d. |
As necessary to effect, administer or enforce a transaction that a consumer requests or authorizes; |
|
|
|
|
|
|
|
e. |
In connection with servicing or processing a financial product or service that a consumer requests or authorizes, or maintaining or servicing the consumer’s account with ARB; |
|
|
|
|
|
|
|
f. |
With the consent or at the direction of the consumer; or |
|
|
|
|
|
|
|
g. |
To protect the confidentiality or security of ARB’s records pertaining to the consumer, service, product or transaction; to protect against or prevent actual or potential fraud, unauthorized transactions, claims or other liability; for required institutional risk control; for resolving consumer disputes or inquiries; to persons holding a legal or beneficial interest relating to the consumer, or acting in a fiduciary or representative capacity on behalf of the consumer; to provide information to insurance rate advisory organizations, guaranty funds or agencies, or ARB’s attorneys, accountants and auditors; to the extent specifically permitted or required under other provisions of law, to law enforcement agencies, a state insurance authority, self-regulatory organizations or for an investigation on a matter related to public safety; to a consumer reporting agency in accordance with the Fair Credit Reporting Act; to comply with Federal, State or local laws, rules and other applicable legal requirements, or a properly authorized civil, criminal or regulatory investigation, or subpoena or summons; or to respond to judicial process or government regulatory authorities having jurisdiction over ARB for examination, compliance or other purposes as authorized by law. |
|
|
|
|
|
|
|
|
|
|
ProNet shall permit ARB to audit its operations for compliance with this Section upon reasonable notice from ARB. |
|
|
|
|
|
|
|
|
|
|
|
Notwithstanding any other term to the contrary contained herein, this Section regarding Privacy or Consumer Financial Information shall survive any termination, cancellation, expiration and/or rescission of this Agreement. |
|
All information contained herein is
Confidential
Page 6 of 43

|
|
|
|
|
|
5. |
CONFIDENTIALITY |
|
|
|
|
|
|
|
|
a. |
The term “Confidential Information” shall mean this Agreement and all proprietary information, data, trade secrets, business information and other information of any kind whatsoever which: (a) a Party (“Discloser”) discloses, in writing, orally or visually, to the other Party (“Recipient”) or to which Recipient obtains access in connection with the negotiation and performance of this Agreement, and which (b) relates to: (i) the Discloser, or (ii) in the case of ProNet as Recipient, ARB. Its customers and employees, and its third-party vendors or licensors who have made confidential or proprietary information available to ARB. ARB Confidential Information shall include Customer Information, as described below. ProNet acknowledges that ARB has a responsibility to its customers to keep information about its customers and their accounts (“Customer Information”) strictly confidential. ProNet represents and warrants that it will keep such Customer Information strictly confidential. |
|
|
|
|
|
|
|
|
b. |
ProNet shall not disclose or use ARB Confidential Information other than to carry out the purposes for which ARB or one of its Affiliates disclosed such ARB Confidential Information to ProNet. ProNet shall not disclose any ARB Confidential Information other than on a “need to know” basis and then only to: (a) its employees or officers, provided, however that each such employee or officer have entered into a confidentiality agreement, that is enforceable under the laws of each applicable jurisdiction, with terms no less restrictive than the terms hereof; (b) Affiliates of ProNet, only if approved by ARB and provided that such Affiliates shall be restricted in use and redisclosure of ARB Confidential Information to the same extent as ProNet, and provided further that the Affiliate’s employees or officers have each entered into a confidentiality agreement, that is enforceable under the laws of each applicable jurisdiction, with terms no less restrictive than the terms hereof; (c) to Subcontractors, only if approved by ARB and provided further that such Subcontractors and each of their employees and officers have entered into a confidentiality agreement, that is enforceable under the laws of each applicable jurisdiction, with terms no less restrictive than the terms hereof; (d) to independent contractors, agents, and consultants hired or engaged by ARB, provided, however, that ProNet has confirmed that all such persons are subject to a confidentiality agreement, enforceable under that laws of the United States, California and each applicable non-U.S. jurisdiction, which shall be no less restrictive than the provisions of this Section; or (e) as required by applicable law and regulation, order of any court or government agency or rule of a self-regulatory agency (collectively, “Legal Process”), or as otherwise permitted by the Agreement, either during the Term of this Agreement or after the termination of this Agreement. The restrictions set forth herein shall apply during the Term and after the termination of this Agreement. |
|
|
|
|
|
|
|
|
c. |
ARB, as Recipient, hereby agrees on behalf of itself and its employees, officers, Affiliates and its Subcontractors that Supplier Confidential Information will not be disclosed or made available to any person for any reason whatsoever, other than on a “need to know” basis and then only to: (a) its employees and officers and Affiliates; (b) its Subcontractors and other third parties, provided that all such persons are subject to a confidentiality agreement which shall be no less restrictive than the provisions of this Section, or (c) as required by Legal Process, or as otherwise permitted by this Agreement, either during the Term of this Agreement or after the termination of this Agreement. |
|
|
|
|
|
|
|
|
d. |
Prior to any disclosure of Confidential Information as required by Legal Process, the Recipient shall: (i) notify the Discloser of any, actual or threatened compulsion of disclosure, and any actual legal obligation of disclosure |
All information contained herein is
Confidential
Page 7 of 43

|
|
|
|
|
|
|
|
|
immediately upon becoming so obligated, and (ii) cooperate with the Discloser’s reasonable, lawful efforts to resist, limit or delay disclosure. Nothing in this Section shall require any notice or other action by ARB in connection with requests or demands for Confidential Information by its supervisory regulators. |
|
|
|
|
|
|
|
|
e. |
All Work Product, works-in-progress, notes, data, reference materials, memoranda, documentation and records in any way incorporating or reflecting any of ARB Confidential Information and all proprietary rights therein, including copyrights, will belong exclusively to ARB. Upon the termination or expiration of this Agreement, or at any time upon the request of ARB, ProNet shall return all ARB Confidential Information, including Customer Information, in the possession of ProNet or in the possession of any third party over which ProNet has or may exercise control. ARB shall have the right to require ProNet to verify, to ARB’s satisfaction, that all ARB Confidential Information has been returned. ProNet agrees to fully cooperate with ARB’s requests for verification. Verification may include ARB conducting an on-site audit of ProNet’s systems and facilities and/or ProNet executing a sworn affidavit stating that it does not have in its possession or under its control any other documents, contracts, computer code, computer data or other materials, in tangible or electronic form, that pertain to ARB Confidential Information. |
|
|
|
|
|
|
|
|
f. |
With the exception of the obligations related to Customer Information, the obligations of confidentiality in this Section shall not apply to any information which a Party rightfully has in its possession when disclosed to it by the other Party, information which a Party independently develops, information which is or becomes known to the public other than by breach of this Section or information rightfully received by a Party form a third party without the obligation of confidentiality. |
|
|
|
|
|
|
|
|
g. |
ProNet agrees that under no circumstances shall any of ProNet’s employees, officers, Affiliates or Subcontractors, whether full-time or part-time, connect to any ARB data, for purposes of downloading, extracting, storing or transmitting information through personally owned, rented or borrowed equipment including, but not limited to, laptops, PDAs, and cell phones. Any exceptions are at variance with ARB policy and must be approved in advance according to ARB policy guidelines. |
|
|
|
|
|
|
|
|
h. |
All Confidential Information shall remain the property of the Discloser or its licensors. Except to the extent expressly provided herein, this Agreement shall not be construed as conferring on a Recipient an express or implied license or an option for a license for any patent, copyright, trademark, license right or trade secret owned or obtained by the Discloser. |
|
|
|
|
|
|
|
|
i. |
All media releases, public announcements and public disclosures by either Party, or their Representatives, employees or agents, relating to this Agreement or the name or logo of ARB, and ARB Affiliate, any other business entity under common control with ARB, or ProNet, including, without limitation, promotional or marketing material, but not including any disclosure required by legal, accounting or regulatory requirements beyond the reasonable control of the releasing Party, shall be coordinated with and approved by the other Party in writing prior to the release thereof. |
|
|
|
|
|
|
|
|
j. |
“ProNet Information” means: (a) confidential plans, information, research, development, trade secrets, business affairs (including that of any ProNet client, supplier, or affiliate), and other proprietary material of ProNet that is marked with |
All information contained herein is
Confidential
Page 8 of 43

|
|
|
|
|
|
|
|
|
a restrictive legend, or if not so marked with such legend or is disclosed orally, is identified as confidential at the time of disclosure (and written confirmation thereof is promptly provided to ARB); and (b) ProNet’s proprietary services “best practices”, software tools, documentation, and all techniques, methods, logic, architecture, and designs embodied or incorporated therein (whether or not any such information is marked with a restrictive legend). |
|
|
|
|
|
|
|
|
k. |
Notwithstanding any provision in this Agreement to the contrary, this obligation shall survive the termination of this Agreement. |
|
|
|
|
|
|
6. |
BUSINESS CONTINUITY AND INFORMATION SECURITY PLANS |
|
|
|
|
|
|
|
|
a. |
Business Continuity Plan |
|
|
|
|
|
|
|
|
|
|
|
|
1. |
Within thirty (30) calendar days of the Effective Date of the Agreement and subject to the review and approval of ARB, ProNet shall establish and maintain, for each Service, contingency plans, recovery plans and proper risk controls to ensure ProNet’s continued performance under this Agreement (“Business Continuity Plan”). The Business Continuity Plan shall address testing, control functions, accountability and corrective actions to be immediately implemented, as necessary, and provide additional details as required for the continued performance of the Services or as specified by ARB. |
|
|
|
|
|
2. |
ProNet shall update and provide to ARB for its review and approval, at least annually, copies of its Business Continuity Plan and all business continuity exercise final reports. ProNet shall engage in business continuity testing at least annually. If requested, ProNet shall allow ARB to observe its business continuity tests. |
|
|
|
|
|
|
|
|
b. |
Information Security Plan |
|
|
|
|
|
|
|
|
|
|
|
|
1. |
ProNet acknowledges that ARB is required to comply with the information security standards required by law, regulation and rule of self-regulatory organization, as well as ARB’s internal security program for information and systems protection. |
|
|
|
|
|
2. |
Within thirty (30) days of the Effective Date of the Agreement and subject to the review and approval of ARB, ProNet shall establish, maintain and comply with an information security plan (“Information Security Plan”), which shall contain at least those elements specified by ARB in Schedule B and such other elements that ARB may require after consultation with ProNet. |
|
|
|
|
|
3. |
On at least an annual basis, ProNet shall review, update and revise its Information Security Plan, subject to ARB’s review and approval. At ARB s request, ProNet shall make modifications to its Information Security Plan or to the procedures and practices thereunder to conform to ARB’s security requirements as they exist from time to time. |
|
|
|
|
|
4. |
ProNet’s Information Security Plan shall be designed to: |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
i. |
Ensure the security, integrity and confidentiality of Confidential Information; |
|
|
|
|
|
|
ii. |
Protect against any anticipated threats or hazards to the security or integrity of such information; and |
|
|
|
|
|
|
iii. |
Protect against unauthorized access to or use of such information that could result in substantial harm or inconvenience to the person that is the subject of such information. |
All information contained herein is
Confidential
Page 9 of 43

|
|
|
|
|
|
|
|
c. |
Notice of Security Breach |
|
|
|
|
|
|
|
|
|
|
|
|
1. |
ProNet shall notify ARB’s Relationship Manager and its security incident command central of any known or suspected security breach of its system or facilities containing ARB Confidential Information or any other breach of Confidential Information relating to this Agreement within 24 hours after discovery, if the information was, or is reasonably believed to have been, acquired by an unauthorized person. ProNet agrees to fully cooperate with ARB with the preparation and transmittal of any notice, which ARB may deem appropriate or required by law, to be sent customers or to other affected third parties regarding the known or suspected security breach. ProNet’s Information Security Plan shall include a written response program addressing the appropriate remedial measures it shall undertake in the event that there is an information security breach. |
|
|
|
|
|
2. |
ProNet shall cause all Subcontractors and other persons and entities whose services are part of the Services ProNet delivers to ARB or who hold Confidential Information and Customer Information to implement an information security program and plan substantially equivalent to ProNet’s. ProNet shall include or cause its agents and contractors to include in a written agreement with such persons substantially the provisions of this Section. |
|
|
|
|
|
|
|
|
d. |
Compliance with ARB’s Privacy Policy |
|
|
|
|
|
|
|
|
|
|
|
|
1. |
In establishing and maintaining its Information Security Plan and in meeting its obligations regarding protection of Confidential Information and in otherwise performing the Services contemplated under this Agreement, ProNet represents and warrants that it will at a minimum comply with ARB Privacy Policy, set forth as Schedule F, and as may be revised by ARB from time to time. |
|
|
|
|
|
2. |
In addition, ProNet represents and warrants that in performing the Services, it will comply with all applicable privacy laws and regulations of the United States, including the Xxxxx-Xxxxx-Xxxxxx Act provisions, 15 U.S.C. Section 6801 et seq., and that it will use best efforts to protect ARB’s Customer Information from identity theft. e. Failure by ProNet to comply with the provisions of this Section shall constitute a material breach of the Agreement. |
|
|
|
|
|
|
7. |
REGULATORY AGENCIES, REGULATIONS and LEGAL REQUIREMENTS |
|
|
|
|
|
|
|
|
a. |
ARB agrees to comply with applicable regulatory requirements and procedures for use of Services established by ProNet. |
|
|
|
|
|
|
|
|
b. |
Records maintained and produced for ARB (“ARB Files”) may be subject to examination by such Federal, State, or other governmental regulatory agencies as may have jurisdiction over ARB business to the same extent as such records would be subject if maintained by ARB on its own premises. ARB agrees that ProNet is authorized to give all reports, summaries, or information contained in or derived from the data or information in ProNet’s possession relating to ARB when formally requested to do so by an authorized regulatory or government agency. When legally permissible, ProNet will notify ARB of all such requests for materials prior to providing requested information to the requesting party. |
|
|
|
|
|
|
|
|
c. |
ARB agrees to comply with applicable regulatory and legal requirements, including without limitation: |
|
|
|
|
|
|
|
|
|
|
|
|
i. |
submitting a copy of this Agreement to the appropriate regulatory agencies prior to the date Services commence; |
All information contained herein is
Confidential
Page 10 of 43

|
|
|
|
|
|
|
|
|
|
|
|
ii. |
providing adequate notice to the appropriate regulatory agencies of the termination of this Agreement or any material changes in Services; |
|
|
|
|
|
iii. |
retaining records of its technology configurations, settings, and policies as required by regulatory authorities; and |
|
|
|
|
|
iv. |
maintaining, at its own expense, such casualty and business interruption insurance coverage for loss of records from fire, disaster, or other causes, and taking such precautions regarding the same, as may be required by regulatory authorities. |
|
|
|
|
|
|
8. |
LIMITATION OF LIABILITY |
|
|
|
|
|
|
|
|
a. |
Neither Party shall be liable to the other for any special, indirect, incidental, consequential, punitive or exemplary damages, including, but not limited to, lost profits, even if such Party has knowledge of the possibility of such damages provided, however, that the limitations set forth in this Section shall not apply to or in any way limit the indemnity, confidentiality or information security obligations under this Agreement or damages caused by ProNet, its employees, its Affiliates, or its Subcontractors gross negligence or willful misconduct. ARB may not assert any claim against ProNet more than 2 years after such claim occurred. ProNet’s aggregate liability for any and all causes of action relating to services shall be limited to the total fees paid by ARB to ProNet for services resulting in such liability in the 2 month period preceding the date the claim occurred. |
|
|
|
|
|
|
9. |
TERMINATION |
|
|
|
|
|
|
|
|
a. |
Except as provided elsewhere in this Section 9, either party may terminate this Agreement in the event of a material breach by the other party not cured within 90 days following written notice stating, with particularity and in reasonable detail, the nature of the claimed breach. |
|
|
|
|
|
|
|
|
b. |
Remedies contained in this Section 9 are cumulative and are in addition to the other rights and remedies available to ProNet under this Agreement, by law or otherwise. |
|
|
|
|
|
|
|
|
c. |
If ARB: |
|
|
|
|
|
|
|
|
|
|
|
|
1. |
defaults in the payment of any sum of money due per the terms of Section 3 above; |
|
|
|
|
|
2. |
utilizes in house IT services or any other party to manage the technology platform in a manner that disrupts the efficient delivery of the ProNet Managed Services solution described herein; or |
|
|
|
|
|
Then, in any such event, ProNet may, upon 30 day written notice, terminate this Agreement. ARB agrees to reimburse ProNet for any expenses ProNet may incur, including reasonable attorneys fees, associated with the foregoing action. |
|
|
|
|
|
|
|
|
|
d. |
If ARB commits an act of bankruptcy or becomes the subject of any proceeding under the Bankruptcy Code or becomes insolvent or if any substantial part of ARB’s property becomes subject to any levy, seizure, assignment, application, or sale for or by any creditor or governmental agency, then, in any such event, ProNet may, upon 30 day written notice, terminate this Agreement and be entitled to recover from ARB as liquidated damages an amount equal to the present value of all payments remaining to be made hereunder for the remainder of the initial term or any renewal term of this Agreement. For purposes of the |
All information contained herein is
Confidential
Page 11 of 43

|
|
|
|
|
|
|
|
|
preceding sentence, present value shall be computed using the “prime” rate (as published in The Wall Street Journal) in effect at the date of termination and “all payments remaining to be made” shall be calculated based on the average bills for the 3 months immediately preceding the date of termination. ARB agrees to reimburse ProNet for any expenses ProNet may incur, including reasonable attorneys fees, in taking any of the foregoing actions. |
|
|
|
|
|
|
|
|
e. |
ARB may terminate this Agreement by paying a termination fee based on the remaining months of the current term of this Agreement, the amount to be determined by multiplying ARB’s previous six-month average monthly billing of ProNet’s Managed Services by 50% times the remaining months of the current term if terminated during the first year of the current term; 30% times the remaining months if terminated during the second year of the current term, and; 20% times the remaining months if terminated during the third year of the current term. The termination fee, as provided in this Section 9(d), shall not exceed $250,000. |
|
|
|
|
|
|
10. |
INDEMNIFICATION |
|
|
|
|
|
|
|
|
a. |
ARB agrees to hold harmless, indemnify, and defend ProNet and its officers, owners, employees, agents, representatives, insurers, and affiliated or related entities from and against all claims or actions based upon or arising out of any damage or injury to persons or property caused by the negligence of ARB and/or its employees sustained by ProNet in connection with ProNet’s performance of services under this contract or to be performed by ProNet or its employees or agents of ProNet. |
|
|
|
|
|
|
|
|
b. |
ProNet agrees to hold harmless, indemnify, and defend ARB and its officers, owners, employees, agents, representatives, parents, subsidiaries, affiliates, directors, insurers, from and against (1) all claims or actions based upon or arising out of any damage or injury to persons or property incurred by ARB, its officers, owners, employees, agents, representatives, parents, subsidiaries, affiliates, directors, and insurers caused by ProNet in connection with ProNet’s performance of the services hereunder, whether performed by ProNet or its employees or agents of ProNet; (2) any failure of ProNet to comply with its obligations herein; (3) any violation by ProNet of any statute or regulation, including any state or federal tax, labor relations, wage and hour, employment discrimination, wrongful termination or other employment related statute or policy with respect to ProNet or any employees of ProNet performing services, or (4) any untrue or inaccurate representation by ProNet in this Agreement. |
All information contained herein is
Confidential
Page 12 of 43

|
|
|
|
|
|
|
|
11. |
NOTICES |
||
|
|
|
|
|
|
|
|
|
|
Any notice required or permitted to be given hereunder shall be in writing and shall be either (i) delivered personally by hand, (ii) sent by registered or certified mail, or (iii) sent by recognized qualified overnight delivery service (e.g. Federal Express). All such notices shall be sent postage prepaid to the addresses of each party set forth below or to such other address or addresses as shall be designated in writing in the same manner. |
|
|
|
|
|
|
|
To ProNet: |
To ARB: |
|
|
|
|
|
|
ProNet Solutions, Inc. |
Same address as noted above |
|
|
Attn: Xxxxxxx X. Xxxxx, President |
|
|
|
0000 Xxxx Xxxxxx Xxxxxx Xxxxxxxxx, Xxxxx 000 |
|
|
|
Xxxxxxx, Xxxxxxx 00000 |
|
|
|
|
|
|
|
|
|
12. |
AUDIT and FINANCIAL CONDITION |
||
|
|
|
|
|
|
|
|
|
|
a. |
ProNet provides for periodic independent audits of its operations. ProNet shall provide ARB with a copy of such audits of ProNet within a reasonable time after its completion, and shall also provide a copy of such audit to the appropriate regulatory agencies, if any, having jurisdiction over ProNet’s provision of services. |
|
|
|
|
|
|
|
|
|
|
b. |
ProNet shall provide ARB and the appropriate regulatory agencies so requiring a copy of ProNet Solutions, Inc.’s consolidated financial statements. |
|
|
|
|
|
|
|
|
|
|
c. |
ProNet shall provide ARB with an annual Due Diligence document that shall include, but not be limited to: insurance coverage’s, security policies, backup strategies and plans, and copies of disaster recovery testing of ProNet’s company and processes. |
|
|
|
|
|
|
|
|
|
|
d. |
ProNet will provide ARB with a copy of any and all third party reviews or audits of ProNet Solutions’ operations. Such reviews, as required by the various regulatory agencies, will be performed by independent third parties, and any charges for such reviews or audits shall be distributed evenly to all contracted ProNet parties. ProNet will provide the bank with any and all such invoices and costs of the reviews shall be prorated, and will be invoiced separately for said costs as incurred. |
|
|
|
|
|
|
|
|
|
|
e. |
During regular business hours, ARB may, at its sole expense and on a mutually agreed upon date (which shall be no more than thirty (30) Business Days after written notice), time, location and duration perform or arrange for a site visit and/or confidential audit of ProNet’s operations, facilities, financial records, and security and business continuity systems. If ProNet is not in substantial compliance with the requirements of the Performance Measurements, ARB shall be entitled, at ARB’s expense, to perform additional such audits. ARB will provide to ProNet a copy of each report prepared in connection with any such audit within thirty (30) calendar days after it prepared or receives such report. ProNet agrees to promptly take action at its expense to correct those matters or items that require correction. If any audit discloses material variances from the Performance Measurements or a material breach by ProNet of the provisions of this Agreement, ProNet shall be deemed in default of this Agreement. |
All information contained herein is
Confidential
Page 13 of 43

|
|
|
|
|
|
|
|
|
|
f. |
ProNet will fully cooperate and provide access to, and submit to examination, supervision and information requests by ARB’s federal and state governmental regulators. At ARB’s expense, ProNet will provide such regulators with prompt access to ARB’s records held by ProNet and to the procedures and facilities of ProNet relating to the Services provided under this Agreement. |
|
|
|
|
|
|
|
|
|
|
g. |
ProNet will give prior notice to ARB of requests by regulatory authorities to examine ProNet’s records regarding ARB. At ARB’s written request, ProNet shall reasonably cooperate with ARB in seeking a protective order with respect to such records. |
|
|
|
|
|
|
|
|
13. |
FORCE MAJEURE |
||
|
|
|
|
|
|
|
|
|
|
a. |
No failure, delay or default in performance of any obligation of a party to this Agreement shall constitute an event of default or breach of the Agreement to the extent that such failure to perform, delay or default arises out of a cause, existing or in the future, that is beyond the control and without negligence of such party including, but not limited to: action or inaction of governmental, civil or military authority; fire; strike; lockout or other labor dispute (but not including delays caused by Subcontractors or suppliers); war; terrorist act; riot; theft; flood; earthquake or other natural disaster. The party affected by such cause shall take action to minimize the consequences thereof. A party desiring to rely upon any of the foregoing as an excuse for failure, default or delay in performance shall give to the other party prompt written notice in writing of the facts which constitute such cause when the cause arises; and, when the cause ceases to exist, shall give prompt notice thereof to the other party. ProNet may not rely on the foregoing without first using best efforts to deploy the applicable elements of its Business Continuity Plan, developed pursuant to Section Six (6) of this Agreement. |
|
|
|
|
|
|
|
|
|
|
b. |
The affected party will give notice to the other party of any force majeure condition under this Section 13. If ProNet postpones or extends any performance date under this Agreement pursuant to this Section for longer than thirty (30) days, ARB, by written notice given during the postponement or extension, may immediately terminate, without liability, ProNet’s right to render any further performance of the Services affected by the force majeure condition. |
|
|
|
|
|
|
|
|
14. |
MISCELLANEOUS PROVISIONS |
||
|
|
|
|
|
|
|
|
|
|
a. |
This Agreement is binding upon the parties and their respective successors and permitted assigns. Neither this Agreement nor any interest may be sold, assigned, transferred, pledged, or otherwise disposed of by ARB, whether pursuant to change of control or otherwise, without ProNet’s prior written consent. ARB agrees that ProNet may subcontract certain services to be performed hereunder. Any such subcontractors shall be required to comply with all applicable terms and conditions and ProNet will remain liable for the performance or nonperformance of the Services. From time to time, ProNet may recommend to ARB that it purchase certain third party products or services, which ProNet will pass through and invoice to ARB. ARB may choose whether or not to use these products or services, and ProNet will not be liable for any failures of the products or services to perform. However, ProNet will exercise due care in installing, implementing and using any such third party products or services. |
All information contained herein is
Confidential
Page 14 of 43

|
|
|
|
|
|
|
|
|
|
b. |
The captions or heading in this Agreement are for convenience only and shall not be considered a part of or affect the construction or interpretation of any provision of this Agreement. |
|
|
|
|
|
|
|
|
|
|
c. |
This Agreement may be executed in two or more counterparts, each of which shall be deemed an original, but all of which shall constitute one and the same instrument. The parties may evidence execution of this Agreement by faxing a signed counterpart to the other party, which shall be deemed an original. |
|
|
|
|
|
|
|
|
|
|
d. |
This Agreement has been executed in the state of California and shall be governed by the laws thereof; and the state of California shall be the sole and exclusive forum for the resolution of all disputes arising under or relating to this Agreement. |
|
|
|
|
|
|
|
|
|
|
e. |
The invalidity or unenforceability of any term, provision, clause, or any portion thereof, of this Agreement shall in no way impair or effect the validity or enforceability of any other provision of this Agreement, which remains in full force and effect. |
|
|
|
|
|
|
|
|
|
|
f. |
No failure or delay by a party to insist upon the strict performance of any term or condition under this Agreement or to exercise any right or remedy available under this Agreement at law or in equity, and no course of dealing between the parties, shall imply or otherwise constitute a waiver of such right or remedy, and no single or partial exercise of any right or remedy by any party will preclude any other or further exercise thereof. Except as otherwise provided in Section 9, all rights and remedies provided in this Agreement are cumulative and not alternative and are in addition to all other available remedies at law or in equity. |
|
|
|
|
|
|
|
|
|
|
g. |
All claims, disputes and other matters in question arising out of or relating to this Agreement or the breach or interpretation thereof shall be resolved by binding arbitration before a representative member, selected by the mutual agreement of the parties, of the Judicial Arbitration and Mediation Services, Inc. (“JAMS”), in accordance with the rules and procedures of JAMS then in effect. In the event JAMS is unable or unwilling to conduct such arbitration, or has discontinued its business, the parties agree that a representative member, selected by the mutual agreement of the parties, of the American Arbitration Association, San Francisco, CA (“AAA”), shall conduct such binding arbitration in accordance with the Commercial Arbitration rules AAA and procedures of the AAA then in effect. Notice of the demand for arbitration shall be filed in writing with the other party to this Agreement and with JAMS (or AAA, if necessary). In no event shall the demand for arbitration be made after the date when institution of legal or equitable proceedings based on such claim, dispute or other matter in question would be barred by the applicable statute of limitations. Any award rendered by JAMS or AAA shall be final and binding upon the parties, and as applicable, their respective legal representatives, agents, successors and assigns, and may be entered in any court having jurisdiction thereof. Any arbitration hereunder shall be conducted in California unless otherwise agreed to by the parties. |
|
|
|
|
|
|
|
|
|
|
|
The parties expressly state that it is their intent to arbitrate disputes between them. Therefore, this Agreement shall be construed so as to be consistent with applicable federal and California state law, and to be enforceable to the maximum extent allowable by law to provide arbitration as the forum to resolve their disputes. If necessary, any portion of this Agreement that is unenforceable by law shall be stricken, and the arbitrator or the court, as the case may be, shall have the power to reform this Agreement to the extent necessary to comply with |
All information contained herein is
Confidential
Page 15 of 43

|
|
|
|
|
|
|
|
|
|
|
applicable law and to give effect to the parties’ intent that they shall arbitrate their disputes. Each party shall pay their own attorney’s fees and costs, except that if applicable law allows the prevailing party to recover attorney’s fees, costs, and expenses, the parties agree the arbitrator may award the prevailing party reasonable attorney’s fees, costs, and expenses incurred in the arbitration. |
|
|
|
|
|
|
|
|
|
|
|
All proceedings and documents prepared in connection with any arbitration shall be confidential and, unless otherwise required by law, the subject matter thereof shall not be disclosed to any person other than the parties in the proceedings, their counsel, witnesses and experts, the arbitrator, and, if involved, the court and court staff. |
|
|
|
|
|
|
|
|
|
|
h. |
ARB and ProNet agree not to hire each others employees during the term of this Agreement and for a period of 12 months after any termination or expiration thereof, except with the other parties prior written consent. |
|
|
|
|
|
|
|
|
|
|
i. |
This Agreement constitutes the entire agreement between the parties relating to the subject matter hereof. The Agreement supersedes all prior understandings, negotiations and discussions, written or oral, of the parties relating to the Services. Any alteration or modification of any of the provisions in this Agreement or any termination or replacement of this Agreement shall not be valid unless in writing and signed by the parties. |
|
|
|
|
|
|
||
|
|
|
IN WITNESS WHEREOF, the undersigned parties have executed this Agreement the day and year first above written. |
||||
|
|
|
|
|
|
|
|
|
|
PRONET SOLUTIONS, INC. |
|||
|
|
|
|
|
|
|
|
|
By: |
/s/ Xxxxx Xxxxxx |
|
By: |
/s/ Xxxxx Xxxxxxx |
|
|
|
|
|
||
|
|
Name: |
Xxxxx Xxxxxx |
|
Name: |
Xxxxx Xxxxxxx |
|
|
|
|
|
||
|
|
Title: |
EVP, CIO |
|
Title: |
VP - Financial |
|
|
|
|
|
||
|
|
Date: |
6-12-09 |
|
Date: |
6-16-09 |
|
|
|
|
|
||
All information contained herein is
Confidential
Page 16 of 43

SCHEDULE A
DETAILED MANAGED SERVICES DESCRIPTION
|
|
|
|
|
|
1. |
SPECIFICATION OF SERVICES TO BE RENDERED: |
|
|
|
|
|
|
|
The Services to be provided by ProNet are in detail on Exhibit A (Proposal) attached hereto and incorporated herein by this reference. Exhibit A is the service that will be provided to ARB. |
All information contained herein is
Confidential
Page 17 of 43

Schedule B
Information Security Requirements
|
|
|
|
|
|
1. |
Information Security Program |
|
|
|
|
|
|
|
|
a. |
ProNet acknowledges that ARB is required to comply with the information security standards required by applicable law, regulation and rule of self-regulatory organizations, as well as with its own information security policies and procedures. ProNet shall use best efforts to assist ARB to so comply. |
|
|
|
|
|
|
|
|
|
|
|
|
i. |
Within thirty (30) days of the Effective Date of the Agreement and subject to the review and approval of ARB, ProNet shall establish, maintain and comply with a written information security plan (“Information Security Plan”), which shall contain at least those elements specified by ARB herein, and as specifically listed in Appendix A, and such other elements that ARB may require after consultation with ProNet. The Information Security Plan shall have been approved by ProNet’s senior management authority. The Plan shall fulfill the security objectives both for information maintained in computerized systems and for information printed, maintained or displayed on other physical media. |
|
|
|
|
|
|
|
|
b. |
On at least an annual basis, ProNet shall review, update and revise its Information Security Plan, subject to ARB’s review and approval. At ARB’s request, ProNet shall make modifications to its Information Security Plan or to the procedures and practices thereunder to conform to ARB’s security requirements as they exist from time to time. |
|
|
|
|
|
|
|
2. |
Reporting and Audits |
|
|
|
|
|
|
|
|
|
|
a. |
Upon prior written notice and at a mutually acceptable time within ten (10) days after receipt of such notice, ARB Representatives, e.g., external audit consultants, may audit or inspect ProNet’s information security program and facilities to assure ARB Confidential Information is adequately protected. ARB will determine the scope of such audits, which may extend to other ProNet resources (other systems, environmental support, recovery processes, etc.) used to support ProNet’s information systems and Confidential Information handling. ProNet will inform ARB of any internal auditing capability it possesses and permit ARB’s personnel to consult on a confidential basis such internal auditors at all reasonable times. ProNet regularly and on special request will provide regular reports on implementation of its information security program and its Information Security Plan for ARB. |
|
|
|
|
|
|
|
|
|
|
b. |
ProNet acknowledges and agrees that regulatory agencies may audit ProNet’s information security performance at any time during normal business hours. The audit may include both methods and results under this Agreement. |
|
|
|
|
|
|
|
|
|
|
c. |
ProNet shall deliver to ARB within 30 days after ProNet’s receipt thereof, a copy of any preliminary or final report of audit reviewing ProNet’s information security program by any third-party auditors retained by ProNet, including any management letter such auditors submit, and on any other audit or inspection, e.g., a SAS 70 (Operational Controls) audit, upon which ARB and ProNet mutually agree. |
|
|
|
|
|
|
|
|
|
|
d. |
ProNet shall insure that all Subcontractors, Affiliates and other persons and entities whose services are part of the Services ProNet provides to ARB or who hold Confidential Information to implement an information security program and plan substantially equivalent to ProNet’s. ProNet shall include or cause its agents and Subcontractors to include in a written agreement with such persons substantially the provisions of this |
|
All information contained herein is
Confidential
Page 18 of 43

|
|
|
|
|
|
|
|
|
Section. ProNet agrees to provide ARB with a copy of those parties’ information security plans upon ARB’s request. |
|
|
|
|
|
|
|
|
e. |
ProNet shall review the effectiveness of its information security program at least annually and shall revise its program in light of any relevant changes in technology, the sensitivity, nature and quantity of the Confidential Information it holds, internal or external threats to information and ProNet’s own changing business arrangements. ProNet shall report in writing at least annually to its management authority on its execution of its information security program and on the review called for in the preceding sentence and any resulting revision and shall provide a copy of each such report to ARB for its review and approval. |
|
|
|
|
|
|
3. |
Time of the Essence |
|
|
|
|
|
|
|
|
a. |
ProNet acknowledges and agrees that time is of the essence with respect to its information security obligations set forth herein. If ProNet fails to carry out the obligations herein to ARB’s reasonable satisfaction or to do so on the schedules called for herein, ARB may terminate this Agreement for material breach. |
All information contained herein is
Confidential
Page 19 of 43

Appendix A
Information Security Plan Commitments
|
|
|
|
|
|
1. |
Protection |
|
|
|
|
|
|
|
|
1. |
ProNet shall develop and Maintain a written Information Security Plan (the “Plan”) called for in Schedule B and Section 6.b.2 of the Agreement for providing Services to ARB and for hosting or handling Confidential Information. This Plan, at a minimum, shall prescribe the architecture of ProNet’s System, Confidential Information placement within the system (if any), the security controls in place (e.g., firewall, web page security, intrusion detection, incident response process, etc.) and contain the information called for herein. The Plan shall also describe physical security measures in place to protect Confidential Information received or processed by ProNet, including those that will protect Confidential Information that has been printed or otherwise displayed in forms perceptible with or without the aid of equipment. This Plan must be reviewed and approved by ARB security representatives, in ARB’s discretion, before ARB will accept ProNet’s Services, disclose Confidential Information to ProNet or locate Confidential Information on ProNet’s systems. |
|
|
|
|
|
|
|
|
2. |
ProNet shall install and use a satisfactory change control process to ensure that access to its systems and to Confidential Information is controlled and recorded. ProNet shall notify ARB of any planned system configuration changes or other changes affecting the Plan applicable to Confidential Information. ARB may approve these types of changes prior to their becoming effective. |
|
|
|
|
|
|
|
|
3. |
ProNet shall cooperate with ARB-conducted security vulnerability (penetration) testing-on ProNet’s system, which may include unannounced security penetration tests by electronic methods. |
|
|
|
|
|
|
|
|
4. |
ProNet will take reasonable precautions to prevent the unintended or malicious loss, destruction or alteration of ARB’s files, Confidential Information, software and other property received and held by (if any) ProNet. ProNet shall maintain back-up files (including off-site back-up copies) thereof and of resultant output to facilitate their reconstruction in the case of such loss, destruction or alteration, in order to insure uninterrupted Services. |
|
|
|
|
|
|
2. |
Detection |
|
|
|
|
|
|
|
|
1. |
ProNet shall monitor its system and its procedures for security breaches, violations and suspicious (questionable) activity. This includes suspicious external activity (including, without limitation, unauthorized probes, scans or break-in attempts) and suspicious internal activity (including, without limitation, unauthorized system administrator access, unauthorized changes to its system or network, system or network misuse or Confidential Information theft or mishandling). Consistent with provisions of Section 6.b.2 of the Agreement, ProNet shall notify ARB of any known or suspected security breaches or suspicious activities, including without limitation unauthorized access attempts and service attacks (e.g. denial of service attacks). |
|
|
|
|
|
|
|
|
2. |
ProNet shall allow ARB to inspect the physical system equipment, operational environment and Confidential Information handling procedures without prior written notice. ProNet’s agreement with any contractor for provision of services to ProNet that will become part of or support ProNet’s services to ARB shall permit ARB to conduct the same inspection at the contractor. |
All information contained herein is
Confidential
Page 20 of 43

|
|
|
|
|
|
|
|
3. |
ProNet shall maintain for a mutually agreed-upon length of time, and afford ARB reasonable access to, all system records and logs. ARB may review and inspect any record of system activity or Confidential Information handling without prior notice. ProNet acknowledges and agrees that records of system activity and of Confidential Information handling may be evidence (subject to appropriate chain of custody procedures) in the event of a security breach or other inappropriate activity. Upon ARB’s request, ProNet shall deliver the original copies of such records to ARB for use in any legal, investigation or regulatory proceeding. |
|
|
|
|
|
|
|
|
4. |
ARB may monitor ProNet’s system. ARB shall discuss any intrusive monitoring processes with ProNet and may require ProNet assistance, at ARB’s expense, for installation, support and program resolution. This may include installation of ARB-owned equipment or processes or an information feed from ProNet to ARB’s monitoring processes. |
|
|
|
|
|
|
3. |
Response |
|
|
|
|
|
|
|
|
1. |
Consistent with the provisions of Section 6.b.2 of the Agreement, ProNet shall notify ARB, through ARB’s Relationship Manager and defined security escalation channel, in the event of a known or suspected breach of security or the detection of suspicious activity. |
|
|
|
|
|
|
|
|
2. |
ProNet shall cooperate fully with all ARB security investigation activities and abide by ARB’s guidelines for escalation and control of significant security incidents. ARB will provide a copy of said guidelines to ProNet, and such guidelines shall be treated as ARB’s Confidential Information. |
|
|
|
|
|
|
|
|
3. |
ProNet shall monitor industry-standard information channels (bugtraq, CERT, OEMs, etc.) for newly identified system vulnerabilities regarding the technologies and services provided to ARB and fix or patch any identified security problem in a timely manner. Unless otherwise expressly agreed in writing, “timely” shall mean that ProNet shall introduce such fix or patch as soon as commercially reasonable after ProNet becomes aware of the security problem. This obligation extends to all devices that comprise ProNet’s system e.g., application software, databases, servers, firewalls, routers and switches, hubs, etc., and to all of ProNet’s other Confidential Information handling practices. |
|
|
|
|
|
|
4. |
Information ProNet Shall Provide |
|
|
|
|
|
|
|
|
1. |
At ARB request, ProNet shall meet with ARB’s Information Security team to discuss information security issues in much greater detail at times reasonably requested by ARB and at mutually agreeable locations. ProNet shall discuss in detail and provide detailed information regarding the following topics, which shall be addressed in ProNet’s information security plan for ARB. ARB acknowledges and agrees that the information ProNet so provides is ProNet’s Confidential Information, as defined in this Agreement, and is valuable proprietary information of ProNet. ARB shall so treat all such information. |
All information contained herein is
Confidential
Page 21 of 43

|
|
|
|
|
|
|
|
|
2. |
Security Plan Features |
|
|
|
|
|
i. |
Visio Diagrams. The diagrams shall show the detail of the system architecture including, without limitation, the logical topology of routers, switches, Internet firewalls, management or monitoring firewalls, servers (web application and database), intrusion detection systems, network and platform redundancy. The diagrams shall include all hosting environments, including those provided by ProNet’s subcontractors. |
|
|
|
|
ii. |
Firewalls. State the specifications of the firewalls in use. Who manages them? Specify the services, tools and connectivity required to manage the firewalls. |
|
|
|
|
iii. |
Intrusion Detection Systems. Describe the intrusion detection system (“IDS”) environment and the security breach and event escalation process. Who managed the IDS environment? Specify the services, tools and connectivity required to manage the IDS environment. Is the IDS network or host based? |
|
|
|
|
iv. |
Change Management. Describe the change management process for automated systems used to provide services. Describe the process for information handling policies and practices. |
|
|
|
|
v. |
Business Continuity. Describe the business and technical disaster recovery management process. |
|
|
|
|
vi. |
System Administration Access Control. Describe the positions that perform administrative functions on servers, firewalls or other devices within the application and network infrastructure. What level of access is needed to perform functions? What are the access control mechanisms? Are access reports generated and reviewed periodically? Describe methods used to track/log the usage of each account. |
|
|
|
|
vii. |
Customer Access Control. Describe each logon process to be followed by ARB customers (including ARB employees) to obtain access to Services ProNet provides to ARB. |
|
|
|
|
viii. |
Access to Confidential Information in Human-Perceptible Forms. Describe policies, procedures and controls used to protect Confidential Information when it is printed or in other perceptible forms. How and how often are these policies, procedures reviewed and tested? What methods are used to ensure destruction of Confidential Information on hard copy? |
|
|
|
|
ix. |
Operating System Baselines. Describe ProNet’s operation system security controls and configurations. Examples: OS services that have been removed because not required by ProNet’s services to ARB. Current OS fixes that have not been applied, if any. |
|
|
|
|
x. |
Encryption. Describe in detail the technology and usage of encryption for protecting Confidential Information, including passwords and authentication information, during transit and in all forms and locations where it may be stored. |
|
|
|
|
xi. |
Application and Network Management. Specify the services, tools and connectivity required to manage the application and network environment. Who carries out the management functions? What level of physical security applies to managed devices? |
|
|
|
|
xii. |
Physical Security. Describe ProNet’s privacy and security policies. Are they in writing? Are they compatible with ARB’s? Describe how ProNet will comply with ARB privacy policies and security requirements. |
|
|
|
|
xiii. |
Location of Services. Are web servers on a separate segment of the network from the application and database servers? If not, explain the reason this has not been done. At ARB’s request, ProNet shall make reasonable efforts to maintain this separation. |
All information contained herein is
Confidential
Page 22 of 43

Virtual Network
Management Services
(VNMS)
Description of Services
|
|
|
“It’s more than just a technical solution.” |
|
|
|
Phone 000.000.0000 Fax 000.000.0000 |
|
Proprietary & Confidential |
Page 23 of 43

I. Executive Summary
American River Bankshares (ARB) has expressed interest in pursuing ProNet Solutions’ (ProNet) Virtual Network Management Support services (VNMS); an outsourced solution for managing and supporting the enterprise LAN/WAN network. It is recognized that an increased dependency on technology and an increasingly stringent regulatory environment has created a need for a more substantial planning and support mechanism for the IT environment. As such, ARB is exploring the option of outsourcing support of their LAN/WAN environment. Advantages to the financial institution would include:
|
|
|
|
|
|
|
Regulatory Compliance |
||
|
|
|
· |
Audit pressures and regulations require a documented and secure IT platform. ProNet’s VNMS ensures this, and assists bank management with any IT regulatory reviews. In addition, ProNet maintains compliance with recommended compliance standards (FFIEC) regarding security and best practices which includes the Gramm Xxxxx Xxxxxx and Sarbanes Oxley Acts. |
|
|
|
|
|
|
|
|
· |
ProNet will utilize its company resources and best efforts to maintain a satisfactory or higher rating. Should ProNet fail to do so, and it be determined that the failure to do so was within the control of ProNet, then ProNet shall immediately undertake all efforts to restore the compliance of those areas deemed insufficient at it’s own cost, and ARB will have the right to terminate the Agreement between ProNet and ARB at will. |
|
|
|
|
|
|
|
Improved End User Support and Productivity |
||
|
|
|
· |
As a result of combined Best Practices, strict Service Level Agreements (SLAs), results driven methodologies, and qualified engineering staff, ProNet will optimize the current IT environment while maximizing the investment ARB will make in technology. In addition, ProNet utilizes a Single Point Of Contact (SPOC) help desk solution that affords each ARB employee the opportunity to receive immediate and effective technical support. |
|
|
|
|
|
|
|
IT Strategic Planning |
||
|
|
|
· |
ProNet works with its customers to ensure that their investment in technology is providing a positive ROI and that they are building the technology platform that will drive company growth and regulatory compliance. |
|
|
|
|
|
|
|
Financial Institution Expertise |
||
|
|
|
· |
Through ProNet’s experience with financial institution technology platforms and regulatory reviews, ARB will have the confidence that its technology platform will be managed to industry and regulatory best practices. |
|
|
|
“It’s more than just a technical solution.” |
|
|
|
Phone 000.000.0000 Fax 000.000.0000 |
|
Proprietary & Confidential |
Page 24 of 43

|
|
|
|
|
|
|
3rd Party Vendor Management |
||
|
|
|
· |
ARB will utilize a number of 3rd party technology vendors to complete its technology offerings for its business needs. ProNet will work with and coordinate any 3rd party technology vendor related needs to ensure the efficient and optimal use of the technology investment. In essence, ProNet believes that it can enhance the problem resolution process by having its engineers identify and resolve issues with the 3rd party vendors in a direct fashion. Not only is this more timely, but it typically eliminates the need for the end user to be engaged. |
|
|
|
|
|
|
|
Cost Effectiveness |
||
|
|
|
· |
The Services provided and described in this proposal are provided to ARB on a “monthly fixed fee” basis. Since the pricing is based on the node count of the bank, ARB can establish a monthly budgeted amount for the WAN/LAN support component of the technology platform. This pricing model is intended to place significant emphasis on ProNet to maintain a standard and stable technology platform that reduces the amount of end user support related requests. In essence, the pricing model ensures that ARB will minimize its exposure to unexpected support needs, while ProNet will be “incented” to provide a proactive support model that reduces the reactive support required by ARB users. |
|
|
|
“It’s more than just a technical solution.” |
|
|
|
Phone 000.000.0000 Fax 000.000.0000 |
|
Proprietary & Confidential |
Page 25 of 43

II. Service Objectives
Regulatory Compliance
Financial institutions have realized a significant increase in the stringency of IT regulations and examinations. ProNet’s managed services solution ensures the institution’s technology platform is managed to best practices and gives the institution the peace of mind in knowing that its technology platform will meet regulatory review guidelines.
|
|
|
|
|
|
· |
ProNet assists ARB in both the preparatory work leading up to their regulatory audit, as well as assistance throughout the entire IT portion of the exam. ProNet will have a representative available to participate with ARB during the IT portion of the regulatory exam to ensure the financial institution is representing itself optimally. |
|
|
· |
Through assistance in regulatory examinations and detailed review of FFIEC requirements, ProNet provides financial institutions with the peace of mind in knowing that they are proactively maintaining regulatory compliance. |
|
|
· |
ProNet’s Information Security framework incorporates the protection of ARB’s customer non-public data and assists in compliance with the Xxxxx-Xxxxx-Xxxxxx Act. |
|
|
· |
ProNet provides ARB with reporting and documentation for the entire IT infrastructure. |
|
|
· |
ProNet’s detailed monthly reporting and trending analysis provides the institution with due diligence in justifying technology investments. |
|
|
· |
ProNet provides the financial institution with documentation used for Disaster Recovery for the technology platform infrastructure of ARB. |
|
|
· |
ProNet performs in depth semi-annual assessments on the health of ARB technology platform. |
|
|
|
“It’s more than just a technical solution.” |
|
|
|
Phone 000.000.0000 Fax 000.000.0000 |
|
Proprietary & Confidential |
Page 26 of 43

Improved End User Support and Productivity
All engineers from ProNet who would be supporting the ARB environment are skilled and certified in the standard technology platforms that ProNet supports. That, coupled with ProNet’s depth of staff (currently 100+ engineers), gives ARB a highly qualified, assigned staff of engineers to support their technology platform simultaneously. This depth of staff, coupled with the ability to perform most tasks and solve most issues remotely, provides ARB with an efficient technology platform management solution.
The Service Level Agreements (SLAs) for all Trouble Tickets are as follows:
Service Level Agreements
|
|
|
|
|
|
|
Priority Level |
|
Priority definition |
|
Service Level Agreement |
|
|
|
|||
|
|
|
|
|
Call Center response: Immediate |
|
1 |
|
Multiple users are down; |
|
Escalation: Within 15 minutes |
|
|
|
there is no work-around |
|
Problem Identification: Within 2 hours |
|
|
|
|
|
Resolution: Continuous until resolved |
|
|
|
|
|
|
|
|
|
|
|
Call Center response: Immediate |
|
2 |
|
One user is down; there is |
|
Escalation: Within 30 minutes |
|
|
|
no work-around |
|
Problem Identification: Within 4 hours |
|
|
|
|
|
Resolution: Continuous until resolved |
|
|
|
|
|
|
|
|
|
Multiple users are affected, |
|
Call Center response: Immediate |
|
3 |
|
but there is a work-around or |
|
Escalation: Within 4 hours |
|
|
|
a lower priority to resolve |
|
Problem Identification: Within 8 hours |
|
|
|
|
|
|
|
|
|
One user is affected, but |
|
Call Center response: Immediate |
|
4 |
|
there is a work-around or a |
|
Escalation: Within the next business day |
|
|
|
lower priority to resolve |
|
Problem Identification: Next business day |
|
|
|
|
|
|
§ PERFORMANCE GUARANTEES §
The ProNet Solutions, Inc.(“ProNet”) guarantee is to meet overall response times at a minimum of 95% of the time. Should ProNet fail to do so, a rebate of 20% of the monthly service fee will be issued.
|
|
|
“It’s more than just a technical solution.” |
|
|
|
Phone 000.000.0000 Fax 000.000.0000 |
|
Proprietary & Confidential |
Page 27 of 43

IT Strategic Planning
Through semi-annual assessments, monthly metric analysis and regulatory expertise, ProNet is able to assist the institution in developing a Technology Roadmap that serves as a strategic planning tool for technology initiatives at the financial institution. This Roadmap allows the financial institution to see what technology projects and expenditure will be required in the next 24 months.
ProNet works with the institution’s executive team and management to ensure that ARB’s technology plan drives into the overall financial institution business plan, and positions the organization for future success and regulatory compliance.
Financial Institution Expertise
Disaster Recovery – Technical Walkthrough and Testing
ProNet’s project management team will provide the bank with a structured, methodology-driven planning document to prepare the bank for business disruptions due to technology failures. In addition, a documented testing strategy will be implemented to mitigate the risks of these possible disruptions and provide the bank with confidence in their DR Plan.
Information Security Risk Assessment
Information Security Risk Management is the process of identifying, assessing, analyzing and reducing information security risks to an acceptable level by implementing the right mechanisms or countermeasures to maintain a level of risk that the business has justified.
ProNet has developed a thorough methodology that provides the framework for conducting an Information Security Risk Analysis. ProNet will utilize its proprietary methodologies and tools to assist ARB in the mitigation of information security risk at the company. This annual assessment will assist ARB in the protection of the confidentiality, integrity and availability of the bank’s data and the compliance with Xxxxx-Xxxxx-Xxxxxx 501b.
|
|
|
“It’s more than just a technical solution.” |
|
|
|
Phone 000.000.0000 Fax 000.000.0000 |
|
Proprietary & Confidential |
Page 28 of 43

Red Flags Program Development
ProNet has developed a thorough methodology that provides the framework for conducting a Red Flags Risk Analysis by implementing the right mechanisms or countermeasures to mitigate the risk of identity theft to your financial institution. ProNet will utilize its proprietary methodologies and tools to assist ARB in the mitigation of Red Flags risk at the company. This assessment is built to satisfy the final rules and guidelines of Sections 114 and 315 of the Fair and Accurate Credit Transactions Act of 2003 (FACT Act).
3rd Party Vendor Management Sample
|
|
|
|
|
|
|
Cores |
|
Applications |
|
Vendors |
|
|
|
|||
|
Fidelity |
|
Laser Pro |
|
Evault |
|
Fiserv |
|
Deluxe |
|
MessageLabs |
|
Xxxx Xxxxx |
|
Bankers Dashboard |
|
Websense |
|
Metavante |
|
Profit Stars |
|
XXXX |
|
DCI |
|
IPS Sendero |
|
CheckPoint |
|
OSI |
|
Accuity |
|
Citrix |
|
RDSI |
|
Bankers Toolbox |
|
Microsoft |
|
Xxxxxxx |
|
Goldleaf Financial Solutions |
|
Top Speed |
Cost Effectiveness
ProNet’s financial institution customer base has seen large economic advantages upon entering into ProNet’s managed services. These institutions gain access to ProNet’s best practice technology management, which ensures the efficiency of the technology platform and regulatory compliance.
|
|
|
|
|
|
· |
ProNet utilizes economies of scale to leverage enterprise wide tools that would otherwise only be affordable to large institutions. |
|
|
|
|
|
|
· |
ProNet’s fee structure allows ARB to maintain a planned monthly IT budget. |
|
|
|
|
|
|
· |
ProNet’s pricing structure enables the financial institution to predict the technology cost of their growth and expansion. The structure also eliminates the need for the financial institution to add additional technology FTEs in the organization, saving salary and benefits burden required by these individuals. |
|
|
|
“It’s more than just a technical solution.” |
|
|
|
Phone 000.000.0000 Fax 000.000.0000 |
|
Proprietary & Confidential |
Page 29 of 43

III. Scope of Service Coverage
The support identified in this proposal includes all ARB owned technology platform related hardware and software. ARB will maintain a 3rd party vendor (which ProNet will manage) for hardware break fix/escalation support for any hardware related issues.
The equipment supported includes:
|
|
|
|
|
|
|
Infrastructure |
||
|
|
|
· |
Routers |
|
|
|
· |
Switches |
|
|
|
· |
Firewalls |
|
|
|||
|
|
Servers |
||
|
|
|
· |
Hardware |
|
|
|
· |
Applications (ie – MS Office & Backoffice applications) |
|
|
|
· |
Firewalls |
|
|
|||
|
|
Workstations |
||
|
|
|
· |
Hardware |
|
|
|
· |
Operating Systems |
|
|
|||
|
|
Communications |
||
|
|
|
· |
Routers |
|
|
|
· |
Switches |
|
|
|
· |
Firewalls |
|
|
|||
|
|
Misc. |
||
|
|
|
· |
Backup (software & hardware) |
|
|
|
· |
Printers |
The services identified in this proposal do not include:
|
|
|
|
|
|
§ |
Any technology device and/or application that is not owned by ARB (e.g. home PCs, non bank-owned PDA’s, software games, etc.) |
Single Point of Contact (SPOC)
ProNet will provide a Single Point of Contact (SPOC) for all ARB
employees. The SPOC will act as the single point for all technology related
user requests. Each ARB owned piece of computer hardware will be affixed with
an appropriate decal identifying the appropriate phone number to call to
receive technical assistance from the SPOC engineers (e.g. 602 or 866 prefix).
The hours of operation for the SPOC will be:
|
|
|
|
|
|
|
§ |
7:00 a.m. to 6:00 p.m. Monday thru Friday |
|
|
|
|
o |
The SPOC will be closed on all nationally recognized holidays |
7 X 24 Monitoring of Technology Platform
ProNet will provide 7 X 24 monitoring of the infrastructure components
of the ARB technology platform (i.e. T1/Fiber/Frame Relay availability,
firewalls, routers, switches, and servers). In cases where 3rd party
vendors manage those infrastructure devices, ProNet will commence immediate
escalation (e.g. T1/Fiber/Frame Relay); however, in situations where the
escalation requires on-site support by ProNet, ProNet will commence escalation
at 6:00 a.m. of the next business day.
|
|
|
“It’s more than just a technical solution.” |
|
|
|
Phone 000.000.0000 Fax 000.000.0000 |
|
Proprietary & Confidential |
Page 30 of 43

IV. Service Overview
Network Management Best Practices for Managed Services Solution
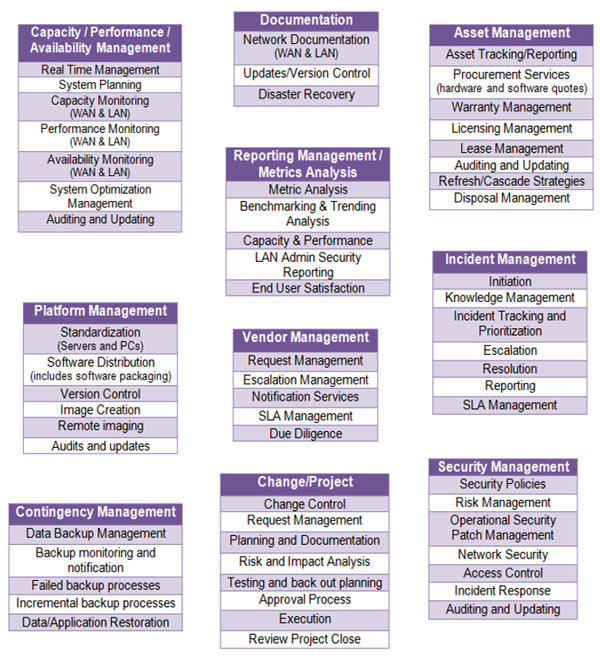
|
|
|
“It’s more than just a technical solution.” |
|
|
|
Phone 000.000.0000 Fax 000.000.0000 |
|
Proprietary & Confidential |
Page 31 of 43

V. Reporting
On a monthly basis, metrics are generated and reviewed that capture trending of ticket types, resolution timeframes and user call volumes. These reports allow ProNet Solutions to analyze and apply proactive measures to common occurrence calls and tickets. This reporting also promotes planning for future enhancements and stability initiatives to ensure that the technology platform is available and productive for end users.
On a quarterly basis, security reporting on network access is documented and audited to ensure appropriate controls and processes are being followed for employee changes (e.g. new hires, terminations).
On a semi-annual basis, network performance and capacity reporting is reviewed with ARB as part of the Managed Services solution. ProNet Solutions will perform a Network Health Assessment (NHA), which includes a review and audit of the technology configurations, best practices and procedures, and network documentation to ensure that the network is performing as required and support for end users is at optimal levels.
|
|
|
THE NETWORK HEALTH ASSESSMENT REPORT INCLUDES: |
|
Executive Summary of the current health of
the environment and strategic |
|
Technology Roadmap that outlines strategic initiatives |
|
Detailed summary of issues and recommendations |
|
Documented checklists that detail the assessment process and methodology |
|
End user satisfaction survey results |
|
Detailed listing of Assets supported by ProNet Solutions |
|
Updated Network Documentation that includes LAN administration reporting |
Many
reports are available through ProNet’s client facing portal for the
Track Everything Database (XXX).
|
|
|
“It’s more than just a technical solution.” |
|
|
|
Phone 000.000.0000 Fax 000.000.0000 |
|
Proprietary & Confidential |
Page 32 of 43

Moves, Adds and Changes (MACs)
Rather than charge for ARB’s MAC activity on a Time & Materials basis, ProNet has proposed a flat monthly MAC charge that has been included in the bank’s monthly Managed Services fee. ARB’s Relationship Manager will re-examine this fee every six months to ensure that it effectively captures the bank’s MAC activity.
MACs are Moves, Adds or Changes that involve fewer than 5 workstations and do not require Relationship Project Management or a project plan. Typical MACs include:
|
|
|
|
|
|
Ø |
Purchase/install of hardware or software that is new to the environment |
|
|
Ø |
Installation or troubleshooting of Non-standard hardware/software |
|
|
Ø |
Implementation of software version upgrades |
|
|
Ø |
Implementation of software updates to multiple servers/PCs that requires onsite presence |
|
|
Ø |
Re-image of existing PCs for new users |
|
|
Ø |
Replacement of troubled hardware if a repair is available. |
|
|
Ø |
Installation of new version of software |
|
|
Ø |
Physical move of hardware or software to new location |
|
|
Ø |
Coordination of Equipment Disposal |
|
|
Ø |
Coordination of Cabling or other infrastructure work |
|
|
Ø |
Data transfer |
|
|
Ø |
Firewall changes |
|
|
Ø |
Refreshing old hardware |
MAC’s also encompass the proactive maintenance of hardware warranties and software licensing. For banks that are already in production at the time of signing, ProNet Solutions and the MAC Team will work with the main contact to acquire the bank’s hardware/software information for reporting and maintenance purposes for up to 90 days. After the 90 day period, the MAC Team will present the finding to the bank, and let them know of any compliance issues with warranties and licensing at that time. The MAC Team will present any quotes necessary for the bank to become compliant. From that point forward the MAC Team will track any new purchases and their expiration dates.
|
|
|
“It’s more than just a technical solution.” |
|
|
|
Phone 000.000.0000 Fax 000.000.0000 |
|
Proprietary & Confidential |
Page 33 of 43

Strategic Initiatives and Emerging Technologies
In addition to monthly managed services support, ProNet acts as the institution’s strategic consultant and project partner to accomplish the technology goals of ARB. Upon the managed services engagement, ProNet becomes intimately knowledgeable with the financial institution’s technology platform. Through this knowledge, ProNet is able to perform project-based work for ARB in a seamless, cost-effective fashion. This also allows the financial institution to reduce the number of vendors the institution is working with, which decreases coordination and due diligence burdens placed on the enterprise.
Strategic initiative work will be proposed by ProNet, with consultation from the financial institution. ARB signed acceptance will be required prior to initiation of project work.
Project Services:
Upgrades
|
|
|
|
|
|
Ø |
Application Version upgrades |
|
|
Ø |
Technology Platform Implementation/Upgrades (WAN/LAN) |
Growth Projects
|
|
|
|
|
|
Ø |
New branch locations |
|
|
Ø |
Mergers and acquisitions |
|
|
Ø |
Conversions and application rollouts |
Emerging Technologies
|
|
|
|
|
|
Ø |
VoIP |
|
|
Ø |
Citrix |
|
|
Ø |
Virtualization |
|
|
Ø |
Storage Area Networks (SANs) |
|
|
|
“It’s more than just a technical solution.” |
|
|
|
Phone 000.000.0000 Fax 000.000.0000 |
|
Proprietary & Confidential |
Page 34 of 43

Startup Requirements:
Support tools and/or other requirements necessary to begin full (VNMS) support services include:
|
|
|
|
|
|
· |
Remote access to the network through a standard firewall configuration and internet connection |
|
|
· |
Administrative access to the network |
|
|
· |
Physical access to the Server/Telco room |
|
|
· |
Installation of remote control and diagnostics tools for troubleshooting and remote resolution |
|
|
· |
Installation of security tools for Account/technology auditing |
|
|
· |
Vendor contacts and information for specific application and hardware support requirements |
|
|
· |
Access to ARB’s current network documentation, this includes equipment make, model, diagrams and any other supporting documentation |
|
|
· |
A commitment by ARB to create a “standard technology architecture” for the ARB technology environment. These commitments are dependent upon pricing proposed by ProNet: |
|
|
|
|
|
|
|
|
· |
Standardize on Tier 1 hardware platform |
||
|
|
|
|
§ |
Standardize anti-virus integration |
|
|
|
|
§ |
Create standard images for user profiles |
|
|
· |
Implement stable data backup solution for enterprise |
||
|
|
· |
Establish spare equipment policy for enterprise |
||
|
|
|
“It’s more than just a technical solution.” |
|
|
|
Phone 000.000.0000 Fax 000.000.0000 |
|
Proprietary & Confidential |
Page 35 of 43

Managed Security Solution
Malicious Activity
Description of Services
|
|
|
“It’s more than just a technical solution.” |
|
|
|
Phone 000.000.0000 Fax 000.000.0000 |
|
Proprietary & Confidential |
Page 36 of 43

Executive Summary:
As community banks are continuing to enhance the services provided to customers thru technology, it is essential that these banks provide adequate security measures that won’t compromise the confidence of the customers’ or present significant financial loss to the bank itself.
In essence, community banks now have the same sophisticated technology capabilities as that of larger enterprise financial institutions. This has created a new set of vulnerabilities that present significant risk and exposure to the bank. As such, community banks must now provide the same comprehensive security practices for the technology assets and information safeguarding. In fact, the regulatory agencies are modifying their expectations of technology security and expecting community banks to provide a comprehensive technology security program for its normal bank operations (e.g. Gramm Xxxxx Xxxxxx).
ProNet’s Managed Security Solution is a best practices driven approach to managing the security of the technology assets in a proactive, preventative manner, allowing immediate identification and remediation of security threats. While the MSS Solution detects these threats to the institution in a real-time manner, it is based on a proactive model that mitigates these threats prior to them affecting the ARB’s technology platform or customer information. As an overview, the fundamentals of the security service are:
|
|
|
|
|
24 X 7 X 365 Monitoring |
|
|
|
|
|
To ensure a “virtual” security management solution, ProNet’s MSS will manage ARB’s technology platform through our Security Operations Center (SOC) 24 hours a day 7 days a week 365 days a year. In addition to providing the confidence that ARB technology platform is always being monitored, ProNet will have the ability to escalate critical incidents in a real time capacity. |
|
|
|
|
|
Best Practices Approach to Security Management |
|
|
|
|
|
ProNet will employ a best practices approach to managing the security of ARB technology platform. The best practices approach will require software tools and skilled engineering resources to incorporate a support solution that identifies preventative measures to proactively mitigate threats, but also be capable of responding thru appropriate escalation procedures should a breach occur. The best practices approach to technology security management will give you the peace of mind in knowing that ARB technology assets are being virtually managed through a services approach that is geared towards providing a comprehensive preventative technology security solution that produces reliable, repeatable and consistent security threat mitigation techniques. |
|
|
|
“It’s more than just a technical solution.” |
|
|
|
Phone 000.000.0000 Fax 000.000.0000 |
|
Proprietary & Confidential |
Page 37 of 43

Layered Protection
Because no single security technique is foolproof or sufficient to prevent a security breach from occurring, a layered approach to managing the technology assets must be employed. As such, ProNet identifies the technology assets at four “layers” within ARB technology platform: external (perimeter); firewall; internal; and host. Thru the use of industry leading tools, coupled with our best practices support orientation, all layers within the bank’s technology platform will be protected from malicious attacks and threats. This defense-in-depth approach provides reliable, comprehensive coverage that is reinforced at multiple points.
Real-Time Incident Management
ProNet has established a formal incident management program that will formalize the escalation and reporting of any known threat attempt or actual breach. This service will also provide real time “event” notification to ARB to ensure that any legitimate threat be mitigated as soon as detected.
Proactive Security Management Practices
In addition to managing the layers of the bank technology platform, ProNet will employ tools and best practices that will proactively monitor those technology assets that pose a higher risk or vulnerability. Examples of such proactive monitoring would be: web site defacing, Pharming and Phishing schemes. This will give ARB the confidence and peace of mind that any threats will be identified immediately as they are launched, and that countermeasures will be undertaken immediately to mitigate the threat and impact to ARB.
Reporting
Through the integration of “best in class” monitoring and scanning tools, coupled with ProNet’s best practices methodology driven security support solution, ProNet’s security certified engineering team will provide meaningful reporting in a real time access mechanism to ARB. The value of this type of reporting will satisfy regulatory oversight requirements, but more importantly, it will create a forensic based mechanism in which security threats can be exposed and knowledgeable business decisions can be made with respect to future investments to provide additional layers of security for information based assets.
Total Cost of Ownership of Solution
Historically, community banks have foregone the use of sophisticated security tools and management practices due to the hardware and software cost outlays and staffing needs required by these solutions. By implementing a Managed Security Solution amongst ProNet’s entire Managed Services customer base and leveraging a security-certified engineering team across its community banks, ProNet has developed a robust solution at a cost-effective price point. The costs for this solution have been priced to fit banks as small as new de novo operations, to ensure all institutions can implement this required service.
|
|
|
“It’s more than just a technical solution.” |
|
|
|
Phone 000.000.0000 Fax 000.000.0000 |
|
Proprietary & Confidential |
Page 38 of 43

Service Objectives
24 X 7 X 365 Monitoring & Management
As a result of the need for constant protection and monitoring, ProNet manages the network environment through our Security Operations Center (SOC) 24 hours a day, 7 days a week, 365 days a year, that will provide the qualified security engineering analysts to respond to any alerts or breaches in a “virtual” capacity.
|
|
|
|
|
|
· |
ProNet’s team of certified security professionals will constantly monitor and manage your network security at the SOC. If there is an attempted breach, our team of experts are on hand to quickly eliminate or mitigate the incident. Their sole responsibility is to continually monitor your network, keeping it up-to-date with the latest threat signatures and scanning for malicious behavior. |
|
|
|
|
|
|
· |
ProNet’s dedicated team of security professionals are armed with the knowledge of your network’s weaknesses, higher priority assets, and likely areas of attack through the assessment process. Therefore, they can treat these points of importance with more sensitivity and attention. |
|
|
|
|
|
|
· |
Through the defense-in-depth strategy combined with the continuous monitoring of your network, ProNet provides community banks with the peace of mind in knowing that they are thoroughly protected and proactively maintaining regulatory compliance by providing a constant monitoring of the technology platform. |
Best Practices Security Management
ProNet’s MSS extends your network reliability through protection, and works in conjunction with ProNet’s VNMS to deliver more comprehensive, customized, and preventative security services. As a result of combined Best Practices, environmental knowledge, and qualified engineering staff, ProNet can more proficiently protect your IT environment, repair vulnerabilities, and prevent potentially damaging incidents through mitigation.
|
|
|
|
· |
ProNet’s Security Analysts leverage the VNMS expertise and experience in Community Banking technology management to build a better, more effective, customized security solution. ProNet allows ARB to concentrate on running their business by delivering the peace of mind that the bank s technology will be protected and monitored 24 x 7. |
|
· |
ProNet Solutions prides itself in providing enterprise wide security management best practices to the community banking environment. This is done by working with many financial institutions in order to gain advantages that are usually unavailable to individual community banks. This knowledge repository and economy of scale allows ProNet to deliver to ARB the leading edge security technology and preventative solutions. |
|
|
|
“It’s more than just a technical solution.” |
|
|
|
Phone 000.000.0000 Fax 000.000.0000 |
|
Proprietary & Confidential |
Page 39 of 43

Layered Protection
Since no single security technique is sufficient to protect the bank’s technology platform, ProNet will embrace a layered approach to managing the technology and information assets contained therein. Thru ProNet’s VNMS support, all components of the technology platform have been identified. Typically, ProNet identifies the following as layers to be monitored within a community bank’s technology platform: external (perimeter), firewall, internal, and host levels. ProNet will utilize a best practices approach and industry leading software tools to protect the bank s assets from malicious network attacks and threats at all levels of the network.
|
|
|
|
· |
ProNet’s approach to protecting ARB’s network and the assets that are linked to your network through the use of multiple security layers is described as defense-in-depth. Through an ongoing process of assessment, planning, implementation, testing, training, and integration ProNet customizes the security solution which provides the best defense of your network. |
|
· |
To provide a layered approach to protection, ProNet utilizes the following tools to form a comprehensive prevention and identification solution: Intrusion Prevention Devices, Firewall Monitoring Tools, Active Directory Oversight, Server and Desktop Protection Tools, Web Content Alerts and Incident Management Technology. All of the pertinent information from these tools are delivered to you via a condensed report summarizing ARB’s security activities. |
Real-Time Incident Management
As noted, the SOC will be staffed and operational on a 24 X 7 basis. Through constant monitoring, mitigation techniques, and best practices support approach ARB will have the confidence that its technology platform is being monitored at all times. Should an incident occur, the SOC will abide by a formal Incident Management Program that will provide ARB with immediate notification.
|
|
|
|
· |
All security events are aggregated, correlated, and monitored to provide the 24 X 7 security analysts with real-time incident monitoring. This level of awareness allows the security team to eliminate threats from damaging your network on a real-time basis. Tools will be utilized to establish forensic evidence of the threat, with the results being made available to ARB. |
|
· |
If a threat was able to penetrate the perimeter defenses, ProNet’s strict procedures and policies will be engaged to ensure immediate recovery and protection from future threats. These policies include the latest tools for detection, assessment, containment, response, archiving, and forensic reporting to provide a comprehensive set of actions should a security breach occur. |
|
|
|
“It’s more than just a technical solution.” |
|
|
|
Phone 000.000.0000 Fax 000.000.0000 |
|
Proprietary & Confidential |
Page 40 of 43

Proactive Security Practices
Although ProNet utilizes industry leading tools and has developed best practices to react to threats immediately, ProNet maintains a proactive orientation towards securing all technology assets in ARB’s environment. This includes proactive efforts to limit the potential damage of external attacks at damaging the brand image, reputation and credibility with ARB’s customers. Understanding that consumer confidence and trust is vital to the community banking relationship with its customers, ProNet has included the following processes to proactively limit this threat:
|
|
|
|
|
|
· |
Website Defacement Protection – ProNet will actively monitor your website to alert you when something has been altered or changed. This protective measure will enable you to be more responsive to attacks and unauthorized redirects from your website. |
|
|
· |
DNS Hijacking/Pharming – ProNet will actively monitor your Domain name records and alert you when the records have been changed. This protective measure will enable you to take action when a Domain name has been altered and users are being directed to a fraudulent site |
|
|
· |
Anti-Phishing – ProNet will actively provide round the clock efforts to discover Phishing sites targeting ARB and in the event you fall victim to Phishing and/or other forms of web based identity theft or fraud, ProNet will engage in the lawful deactivation of these websites. |
|
|
· |
Security Awareness – As a key component of the proactive effort, ProNet will work with ARB to establish effective employee Security awareness training. This proactive measure will educate your end users about common security threats and how to mitigate them. |
|
|
· |
Threat Response Program – ProNet will employ an aggressive Threat Response Program that will provide real time and aggressive response to any identified threats to ARB. This program will include immediate measures that ProNet can take to minimize the risk and impact of an identified threat, but also work with outside 3rd Party specialists who will provide an additional layer of comprehensive responsiveness to minimize the exposure to ARB and its customers. |
|
|
· |
Web Protect – ProNet provides protection from known malicious websites. When websites are browsed by end users they will be evaluated from malicious content and if detected they will be blocked. Providing a layer protection to unknown web browser based threats. |
|
|
· |
Vulnerability Management- ProNet will scan your internal network for vulnerabilities and mis-configurations on a quarterly basis. Any identified issues are remediated by your primary engineer. |
|
|
|
“It’s more than just a technical solution.” |
|
|
|
Phone 000.000.0000 Fax 000.000.0000 |
|
Proprietary & Confidential |
Page 41 of 43

Reporting
ProNet’s SOC Management team will provide ARB with the capability of accessing detailed reporting of the threats captured and mitigated thru the preventative measures deployed by the MSS. These reports will consist of meaningful visual representations of ARB’s security posture and are designed to capture trends, critical alerts, and types and levels of activity. These security metrics will be routinely generated from large data files that have accumulated from ARB’s device logs and then will be condensed into meaningful concise daily and monthly summaries of your network security activity.
|
|
|
|
· |
Threat discovery and detection reports will be generated that illustrate incident types, incident quantities, and what technology platform systems were targeted. |
|
· |
A major component of the reporting will be the “filtering of data”. The ProNet SOC will employ numerous tools to ensure that the reporting provided to ARB will be “filtered” of any “false positives” which are usually associated with the security reporting. Thru ProNet’s best practices approach, the reporting made available to ARB will be meaningful and accurate, with ARB being able to understand the reports with the understanding that the data contained therein is reliable in its accuracy. As the MSS solutions within ARB ages, the historical data will be utilized to establish trends and patterns. |
|
|
|
“It’s more than just a technical solution.” |
|
|
|
Phone 000.000.0000 Fax 000.000.0000 |
|
Proprietary & Confidential |
Page 42 of 43

Service Level Agreement and Guarantee
All Security Analysts from ProNet who would be protecting the ARB environment are skilled and certified. Should the ARB’s network encounter a threat, ProNet has established strict Service Level Agreements to ensure that effective threat management and incident response procedures are adhered to 24 X 7.
The Service Level Agreements (SLAs) for all Incidents are as follows:
|
|
|
|
|
|
|
|
|
Priority Level |
|
Priority Definition |
|
Examples |
|
Service Level Agreement |
|
|
|
|
||||
|
|
|
Immediate threat to the |
|
|
|
|
|
|
|
Confidentiality, |
|
|
|
|
|
|
|
Availability or Integrity |
|
Unauthorized access to |
|
SOC response: Immediate |
|
|
|
(CIA) of Private, |
|
server; Denial of service; |
|
Problem Identification: Within 15 minutes |
|
Red Alert |
|
Financial or Proprietary |
|
Massive worm/virus |
|
Escalation: Within 20 minutes |
|
|
|
information; or |
|
infection; Website |
|
Resolution: Continuous until resolved |
|
|
|
immediate threat to |
|
Defacement |
|
Bulletin: Upon resolution |
|
|
|
customers reputation. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Unauthorized access to |
|
|
|
|
|
Threat to CIA of |
|
workstation/laptop; |
|
SOC response: Immediate |
|
|
|
information that is not |
|
Unauthorized access to |
|
Problem Identification: Within 15 minutes |
|
Caution |
|
Private, Financial or |
|
network infrastructure |
|
Escalation: Within 20 minutes |
|
|
|
Proprietary in nature |
|
devices; Isolated |
|
Resolution: Continuous until resolved |
|
|
|
|
|
worm/virus infection |
|
Bulletin: Upon resolution |
|
|
|
|
|
|
|
|
|
|
|
|
|
Ongoing/persistent |
|
|
|
|
|
Persistent unsuccessful |
|
probes/Reconnaissance |
|
Incident Logged: Immediate |
|
Discovery |
|
probes or attacks |
|
attempts; Persistent |
|
|
|
|
|
|
|
unsuccessful authentication |
|
Alerting: Monthly Report |
|
|
|
|
|
attempts |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Probes/Reconnaissance |
|
|
|
|
|
|
|
attempts; Isolated |
|
|
|
|
|
Unsuccessful probes or |
|
unsuccessful authentication |
|
Incident Logged: Immediate |
|
Informational |
|
attacks; |
|
attempts; Human |
|
|
|
|
|
Informational |
|
Resources policy violations |
|
Alerting: Monthly Report |
|
|
|
notifications |
|
(Instant Messaging etc.) |
|
|
§ PERFORMANCE GUARANTEE §
The ProNet Solutions, Inc.(“ProNet”) guarantee is to meet overall response times at a minimum of 95% of the time. Should ProNet fail to do so, a rebate of 20% of the monthly service fee will be issued.
|
|
|
“It’s more than just a technical solution.” |
|
|
|
Phone 000.000.0000 Fax 000.000.0000 |
|
Proprietary & Confidential |
Page 43 of 43

