MASTER SERVICES AGREEMENT CALL HANDLING SERVICES
CONFIDENTIAL TREATMENT
CALL HANDLING SERVICES
THIS AGREEMENT (the “Agreement”) is made effective as of this 22nd day of June, 2013, (the “Effective Date”) by and between Comcast Cable Communications Management, LLC., a Delaware Limited Liability Company, with offices at 0000 XXX Xxxxxxxxx Xxxxxxxxxxxx, XX 00000-0000 (“Comcast”) and StarTek, Inc., a Delaware corporation, with offices at 0000 X. Xxxxxxxxx Xxx., Xxxxx 000, Xxxxxxxxx Xxxxxxx, XX 00000 (“Vendor”).
SECTION I
1.1 Vendor agrees to provide customer service services to Comcast for Comcast products and services (“Comcast Products”); including various business processes and support (the “Services”). The Services are more particularly described in a statement of work (“SOW”) which specifically references this Agreement as may be executed from time to time between the parties. In the event of a conflict between this Agreement and an SOW, the provisions contained within this Agreement shall control.
1.2 Vendor hereby accepts such appointment and agrees actively and continuously to exert its best efforts, on Comcast’s behalf, to provide the Services. Vendor will provide the Services during the hours of operation identified in the applicable SOW (the “Operation Hours”).
____________________
[*] = Certain confidential information contained in this document, marked with brackets, has been omitted and filed separately with the Securities and Exchange Commission pursuant to a request for confidential treatment made pursuant to Rule 24b-2 under the Securities Exchange Act of 1934, as amended.
CONFIDENTIAL TREATMENT
1.3 Comcast reserves the right to: (i) add to, alter or subtract from the Services, including, but not limited to the Operation Hours, upon [*] ([*]) days prior written notice to Vendor provided, however, that Vendor shall have the right to terminate this Agreement and/or any SOW affected by such change within [*] ([*]) days following receipt of notice of any change in Vendor’s sole discretion and (ii) perform the same or similar types of Services itself or utilizing third parties.
SECTION II
All policies, procedures, scripts, descriptions, terms, conditions and prices utilized by Vendor for the Comcast Products shall be the policies, procedures, scripts, descriptions, terms, conditions and prices authorized by Comcast in writing or otherwise provided to Vendor by Comcast. Vendor shall not under any circumstances utilize other policies, procedures, scripts, descriptions, terms, conditions and prices for any Comcast Product without the prior written authorization of Comcast. Comcast reserves the right to add to, alter or subtract from the Comcast Products as well as any policies, procedures, scripts, descriptions, terms or conditions related thereto upon prior written notice to Vendor.
SECTION III
3.1 Comcast will pay Vendor the base compensation for the Services set forth in an SOW. In addition to the base compensation, if an SOW provides for a Bonus Rate paid to Vendor if Vendor meets or exceeds the Service Level Target(s) (as both terms are defined in the applicable SOW) for the fiscal month, Comcast will pay Vendor additional compensation as set forth in the SOW. The Bonus Rate is determined by multiplying the achieved Bonus percentage set forth in the SOW by the Productive Hours Rate set forth in the SOW.
3.2 Vendor will provide Comcast with an itemized monthly invoice for the Services stating the Productive Hours Rate, Training Rate and Overtime Rate (to the extent such are provided for and defined in the applicable SOW), along with any other information that Comcast may request from time to time. If applicable, invoices for Bonus Rate payments due to Vendor (the “Bonus Invoice”) shall be submitted monthly by Vendor no later than [*] ([*]) business days after Vendor sends to Comcast Vendor’s invoice for Productive Hours, Training and Overtime Hours. Vendor shall submit all invoices to Comcast electronically in accordance with Comcast’s electronic payment policies then in effect and provided to Vendor in writing from time to time or made available for review at xxxx://xxx.xxxxxxx.xxx/xxxxxxxxxx/?XXXxxxxxxxxxxxx and xxxxx://xxxxxxx.xxxxxxxxxx.xxx/xxxxxxxx/xxxxx (the “Electronic Payment Policies”). Invoices shall be deemed received [*] ([*]) business day after proper submission in accordance with the Electronic Payment Policies. Comcast reserves the right to reject any invoice not submitted in accordance with the Electronic Payment Policies. Comcast has no obligation to pay any compensation to Vendor invoiced by Vendor more than [*] ([*]) months after the Services are provided.
3.3 All undisputed charges shall be payable within [*] ([*]) days of Comcast’s receipt, subject to Comcast’s review and verification of Vendor’s invoice and Bonus Invoice. In the event
that Comcast disputes any charges on a Vendor’s invoice or Bonus Invoice, Comcast shall provide to Vendor in writing the amounts of the charges in dispute along with a brief description of the basis for the dispute. Comcast and Vendor shall each act in good faith and use commercially reasonable efforts to promptly resolve such disputed charges.
3.4 Vendor represents that the prices, terms, warranties, and benefits contained in this Agreement or any SOW are equal to or better than those offered to any other comparable customer of Vendor. If Vendor offers services or goods to any other customer, purchasing substantially similar or less quantity or volume of such services or goods than Comcast, at a lower price, more favorable terms, more favorable warranties, or more favorable benefits during the Term of this Agreement, Comcast shall receive such terms, warranties or benefit prospectively and retrospectively. Upon request by Comcast, an officer of Vendor shall certify that Vendor is in compliance with this Section 3.4.
3.5 The amounts to be paid by Comcast under this Agreement do not include any state, provincial or local sales and use taxes, however designated, which may be levied or assessed on the Services. With respect to such taxes, Comcast will either furnish Vendor with an appropriate exemption certificate on a timely basis or pay to Vendor, upon presentation of invoices therefore, such amounts as Vendor may by law be required to collect or pay, provided that Vendor will use reasonable efforts to minimize the amount of any such tax. Comcast shall have no obligation to Vendor with respect to other taxes, including, but not limited to, those taxes relating to Vendor’s net or gross income or revenue, license, occupation, or real or personal property.
SECTION IV
4.1 Vendor shall provide the Services on a continuing basis throughout the Term of this Agreement and as set forth in an SOW and shall diligently perform all other duties that are required to be performed hereunder or as set forth in an SOW. Vendor agrees to meet service level commitments set forth in an SOW.
4.2 Vendor shall comply with all laws, rules and regulations governing its activities and applicable to the Services.
4.3 Vendor shall provide a data file to Comcast, on a daily basis of customers who have requested to be placed on a Do Not Call List. Comcast shall incorporate the information obtained from the file into the appropriate subscriber management databases.
4.4 Vendor shall maintain complete and accurate records with respect to its activities hereunder in accordance with all applicable laws, rules, and regulations as well as with the terms and conditions of this Agreement and/or any SOW. Without limiting the generality of the foregoing, Vendor shall maintain throughout the Term of this Agreement and for a period not less than [*] ([*]) years thereafter: (i) all advertising, brochures, scripts, promotional and call handling materials that are substantially different than those provided by Comcast and (ii) the name and the last known address and phone number for all current and former employees directly involved in performing
Vendor’s obligations pursuant to this Agreement. Further, Vendor shall provide to Comcast its Federal Taxpayer Identification Number (or equivalent), State Identification Number (or equivalent) and such other information specified in an SOW.
4.5 No Vendor personnel performing the Services shall perform any work for any other telecommunications provider who is a customer of Vendor during the Term of this Agreement. Vendor agrees that during the Term of this Agreement, it will not solicit any employee of Comcast for the express intent of employment with Vendor, provided that nothing herein shall prohibit any general advertisement for employment opportunities, which is not specifically targeted at any particular employee.
4.6 In exercising its rights and performing its obligations under this Agreement or any SOW, Vendor shall conduct its business and represent Comcast in a professional, ethical, legal and businesslike manner. Vendor agrees that it will: (i) utilize only competent personnel; (ii) conduct its operations at all times in such a manner that its actions or the actions of its personnel will not jeopardize Comcast’s and its parent’s, affiliates’ and subsidiaries respective relationships with governmental authorities, communities in which Comcast or Vendor operates and with Comcast’s actual and potential customers; and (iii) ensure that personnel maintain a polite, cooperative manner when dealing with any and all prospective and actual customers. Comcast shall have the right for any reason, not inconsistent with applicable laws, rules or regulations, to request that Vendor discontinue using any person or persons for the Services. Any such request shall be fulfilled to the best of Vendor’s ability immediately upon receipt of Comcast’s written notice to Vendor. Vendor shall not furnish such person(s) so removed to perform the Services, without the prior written consent of Comcast.
4.7 Vendor shall implement and comply with Security Protocols established by Comcast and attached hereto as Exhibit A. Upon reasonable prior notice, Comcast may audit Vendor for compliance with the Security Protocols. Any cost of audit shall be borne by Comcast, except in the event that a material breach of the Security Protocols is discovered during any audit, Vendor shall reimburse Comcast for the reasonable costs incurred in performing such audit. Comcast reserves the right to amend such Security Protocols from time to time as deemed necessary in its sole discretion, provided that Vendor shall have [*] ([*]) days from the date Comcast notifies Vendor of such change to implement the change. Any failure to comply with Security Protocols shall be deemed a material breach of this Agreement, giving rise to Comcast’s right to immediately terminate this Agreement. in its sole discretion without notice or opportunity to cure. The parties agree that it may be difficult, if not impossible, to determine damages in the event of a material breach of the Security Protocols. Vendor agrees to pay as liquidated damages, and not as a penalty, an amount equal to [*] percent ([*]%) of the preceding [*] months ([*]) of invoices in the event of any material breach of the Security Protocols occurs, however in no event shall this amount exceed [*] dollars ($[*]). The parties agree that this amount is reasonable and commensurate with the anticipated loss to Comcast resulting from such breach and is agreed to as a fee, not a penalty.
4.8 Vendor agrees to secure and maintain, at its sole cost and expense:
(i) Commercial General Liability Insurance for damage claims due to bodily injury (including death), or property damage caused by or arising from acts or omissions of Vendor with limits of no less than [*] Dollars ($[*]) per occurrence and [*] Dollars ($[*]) annual aggregate. Coverage is to include coverage for personal and advertising liability and contractual liability;
(ii) Workers’ Compensation insurance in compliance with all statutory requirements;
(iii) Errors and Omissions liability insurance with limits of no less than [*] Dollars ($[*]) per claim and [*] Dollars ($[*]) annual aggregate;
(iv) Cyber-Liability, e-commerce liability or media professional liability insurance with limits of no less than [*] Dollars ($[*]) per occurrence and [*] Dollars ($[*]) annual aggregate; and
(v) Umbrella Liability insurance with limits of no less than [*] Dollars ($[*]) per occurrence and [*] Dollars ($[*]) annual aggregate.
(vi) Crime insurance, including third party Crime with limits of no less than [*] Dollars ($[*]) per occurrence.
(a) Vendor shall name Comcast and its parent, subsidiaries, affiliates, and assigns, and their respective directors, officers, employees, and agents, and any other party reasonably required by Comcast, as additional insured’s on all such General Liability policies. All policies shall be written with an insurance company licensed to do business in the state where services are provided, and having an AM Best rating of no less than A- VIII. Vendor shall provide [*] ([*]) days prior written notice of cancellation or material changes to any required policy. Maintenance of the foregoing insurance will in no way be interpreted as relieving Vendor of any responsibility whatsoever under this Agreement with respect to liability or indemnification.
(b) Vendor will provide to the notice address named herein, no later than [*] ([*]) days before commencing work hereunder, and prior to the expiration of each policy, a certificate or certificates evidencing the insurance coverage and endorsements required herein. The acceptance or failure to reject any such certificate shall not constitute a waiver by Comcast of the requirements herein. Should Vendor fail to provide acceptable proof of the required insurance, Comcast shall have the right, but not the obligation, to withhold all payment until proof of the required insurance is provided, or terminate this Agreement immediately upon written notice to Vendor.
4.9 Vendor shall cause a Background Check (as defined below) to be completed on all personnel assigned by Vendor to provide Services hereunder prior to the date such Services commence and shall not assign personnel to provide Services hereunder if the results of any Background Check, or Vendor’s actual knowledge, indicate that such personnel may pose a risk to
Comcast property, employees, subscribers or Comcast Proprietary Information. The parties understand and agree that the nature of the information that Vendor personnel may access, as well as the requirements of applicable law, may change from time-to-time, and in such cases, the parties will work together in good faith to modify this Section 4.9 and/or the applicable SOW to address any such changes. Notwithstanding the performance of any Background Check, Vendor shall be legally responsible for all acts of its personnel. For purposes of this Section 4.9, a “Background Check” means a background investigation performed by an agency in good standing with the National Association of Professional Background Screeners, and shall include, but not be limited to, a check of felony and misdemeanor criminal convictions (federal, state and county) for at least the immediately preceding [*] ([*]) year period, as well as searches of the national terrorist watch list and relevant national and state sex offender registries. In addition, subject to applicable law, Vendor will perform a drug screen on all personnel prior to initial hire.
4.10 Vendor shall cause its subcontractors and employees with access to the information contained on Comcast’s billing systems to complete the designated form attached hereto as Exhibit E. Vendor shall retain such forms and shall submit the Contractor CPNI Certification form attached hereto as Exhibit F within [*] ([*]) days of the date set forth above. Thereafter, the Vendor shall submit the Contractor CPNI Certification form as new subcontractors and employees are provided with access to Comcast’s billing systems.
4.11 Except as otherwise set forth in this Agreement or an SOW, Vendor is solely responsible for furnishing all equipment, software, systems, tools, documentation, licenses, permits, approvals, supplies and other tangible and intangible items necessary to provide the Services and perform its obligations under this Agreement.
4.12 Vendor will monitor and record its compliance with the Service Level Guarantees (as defined in an applicable SOW) on an on-going basis throughout the Term of this Agreement. Vendor shall use a Comcast approved (or if made available to Vendor by Comcast, a Comcast supplied monitoring tool (e.g., Click2Coach, Witness, or NICE)) that is equipped to monitor calls with both voice and screen capture. Vendor shall conduct periodic support reviews with Comcast upon the prior written request of Comcast.
4.13 Vendor shall provide Comcast with unimpeded password protected remote access to Vendor’s monitoring tools (e.g., tools used to monitor to Vendor’s personnel performing the Services on a random basis and/or to review electronic responses on a random basis, including, but, not limited to, remote monitoring of all live calls to all toll free numbers Comcast sends to Vendor) prior to Vendor commencing to provide the Services. Vendor shall ensure that the remote monitoring capability provided to Comcast complies with applicable State and Federal laws. Comcast reserves the right to audit Vendor’s performance of this Agreement and the Services by whatever means Comcast deems appropriate with or without notice to Vendor, including, but not limited to, customer surveys, monitoring calls and/or other work related activities (either onsite or remotely) provided as a part of the Services to the extent permitted under applicable law. Comcast may utilize Comcast personnel or third parties to conduct such audits. If requested by Comcast, Vendor will provide Comcast with copies of all records of Vendor’s performance of the Services, including, but not limited to, phone records, reports and such other information and records in the format requested
by Comcast. The results of any audits conducted by Comcast (or its designated third parties) shall be conclusive in determining Vendor’s attainment of each of the Service Level Guarantees
4.14 Vendor agrees to maintain dedicated quality assurance staff focused on monitoring the customer quality experience and ensuring Vendor is adhering to Comcast’s Quality Support Guidelines. As used herein, “Comcast Quality Support Guidelines” are a Comcast developed set of defined behaviors and performance criteria to which all CSRs are measured regarding their interaction with Comcast customers or prospective customers from a quality perspective. Vendor will perform [*] ([*]) evaluations per CSR per month. Vendor’s quality assurance staff will assess CSR and team leader evaluations and identify calibration gaps. If gaps are identified, the quality assurance staff will develop corrective action plans to eliminate the identified gap(s).
4.15 Vendor will equip the facilities where the Services are performed (the “Designated Facilities”) to Comcast’s general architecture specifications for the Services as set forth in Exhibit C Technical Requirements attached hereto. Comcast shall have the right to review all Vendor systems, including, but not limited to, all devices, equipment, ports, circuits, network bandwidth and any perform other technical and system review(s) upon [*]([*]) business days notice written notice to Vendor.
(a)Vendor’s personnel performing the Services will connect to Comcast’s telecommunications services, virtual desktop systems, and customer care tools, via dedicated circuit path between the party’s networks. The network design should allow Vendor’s traffic to traverse a primary path but be capable of failing over to a secondary path in the event of a circuit outage on the primary path as set forth in Exhibit D -Telecommunications Requirements attached hereto. The dedicated circuits will be acquired from at least [*] diverse providers with sufficient bandwidth to support the specified number of seats at the Designated Facilities. Subject to mutual agreement and specified in the applicable SOW, these dedicated circuits will be procured and managed by either Vendor or Comcast. Unless otherwise set forth in the SOW, Comcast shall not be responsible to reimburse Vendor for losses due to downtime of a dedicated circuit resulting in Vendor’s personnel not being able to perform Services,
(b)Vendor shall provide USB headsets for Vendor personnel who require the use of a telephone to provide the Services.
(c)Vendor’s workstations shall meet minimum workstation hardware requirements, operating system and software requirements as specified below and as otherwise set forth in the applicable SOW which are subject to change, pursuant to the Change Management process set forth in Section 12 of the applicable SOW
Workstation Requirements:
• | Core Intel i5 processor with 4GB of RAM or equivalent with a 80GB 7200 RPM SATA hard drive and integrated Intel video with integrated audio |
• | Windows XP Professional operating system or higher |
CONFIDENTIAL TREATMENT
• | 17-19” Dell LCD display (or its equivalent) in a non-widescreen format or 19-20” in widescreen format. |
(d)Any request by Vendor or Comcast to change network or Internet connectivity must be communicated to the other party in writing for approval a minimum of [*] ([*]) days prior to the requested date of change. If such request if made by Vendor, Comcast may, at its sole discretion, decline the change request or require additional changes to the request. Any change to network or Internet connectivity shall be planned and executed in a coordinated way, so as eliminate or minimize downtime of the Services.
4.16 In the event of the termination or expiration of an SOW, Vendor shall, at Vendor’s cost, return to Comcast all Comcast Equipment (as defined below), and all other tangible or intangible items of Comcast then in Vendor’s possession or control within [*] ([*]) days of such termination or expiration, unless the Comcast Equipment, tangible or intangible items are being used by Vendor to provide Services under another SOW, in which case such Comcast Equipment, tangible or intangible items may be retained by Vendor until the expiration or termination of such SOW. Comcast Equipment shall be returned via a major carrier and with insurance equal to the current market value (as supplied by Comcast). Vendor shall provide Comcast with the shipment tracking numbers upon shipment. Any Comcast Equipment which is damaged, lost, stolen or otherwise missing will be billed to Vendor at the full replacement value.
4.17 Vendor will maintain the network and server operating systems to industry standard patch levels.
4.18 Vendor shall meet or exceed the following: (i) [*]% telecommunications availability, (ii) [*]% Internet availability and (iii) [*]% local area network (“LAN”) availability as measured on a monthly basis (collectively, the “Network Service Levels”). In the event that Vendor’s owned and operated network facilities do not meet the [*]% uptime and availability requirements, Vendor shall provide in such report details regarding how such uptime and availability will be met.
(a) Voice and data quality over Vendor’s owned and operated network facilities shall at a minimum meet the relevant industry quality standards.
(b) Within [*] ([*]) days after the end of each calendar quarter, Vendor shall provide to Comcast a report that sets forth the service level metrics of its telecommunications/internet suppliers for the calendar quarter.
(c) With respect to the infrastructure related to each Network Service Level, Comcast shall be entitled to do a site audit of Vendor’s architecture upon at least [*] ([*]) hours prior notice to Vendor. Changes to any infrastructure architecture related to the Network Service Levels must be communicated to and approved by Comcast in advance of the changes so as to ensure Comcast adequate time to prepare for the change in infrastructure. Vendor shall notify Comcast: (i) at least [*] ([*]) weeks in advance of any scheduled maintenance related to the network facility or Vendor’s telecommunications infrastructure with a plan and such maintenance shall be subject to the reasonable approval of Comcast
and (ii) immediately, in the case of emergency maintenance. Any Productive Hours or other Vendor compensation lost due to maintenance shall not be billable to Comcast. Vendor shall supply a quarterly review and plan for addressing any issues related to the Network Service Levels. Vendor will provide Comcast with monthly reports on Vendor’s metrics related to the Network Service Levels.
4.19 Vendor will provide a dedicated training staff, training facilities and training materials. Vendor will provide adequate trainer staffing levels to meet the training needs of Vendor personnel providing the Services, as determined by Vendor. Vendor shall ensure that all individuals responsible for training Vendor’s personnel to perform the Services have been properly trained in the performance of the Services. Unless otherwise set forth in an SOW, Vendor shall be responsible for developing, managing, and maintaining all aspects of Vendor’s training curriculum, including the development, management and maintenance of training materials, and the training of its personnel. Comcast shall have the right to review and approve the content of all training curriculum and materials prior to its use by Vendor. Comcast shall have the right, at its sole discretion, to observe any training class for Vendor personnel providing the Services.
4.20 Vendor will appoint a primary relationship manager and a backup to manage the relationship established by this Agreement (the “Vendor Relationship Manager”). The Vendor Relationship Manager will: (i) have overall managerial responsibility for the Services; (ii) attend Comcast executive level meetings and planning sessions as requested by Comcast; (iii) serve as Vendor’s primary liaison with Comcast’s Relationship Manager; and (iv) coordinate, oversee, and monitor Vendor’s performance of the Services with the applicable Vendor managers responsible for such performance. The Vendor Relationship Manager will be responsible for the set up and maintenance of Comcast’s branding collateral, as provided by Comcast, in specified areas of the Designated Facilities.
4.21 Vendor will appoint a technical account manager and a backup to oversee the technology required to support the Services (the “Technical Account Manager”). The Technical Account Manager will: (i) have overall managerial responsibility for Vendor’s technology; and (ii) serve as the primary liaison to Comcast as to the Vendor’s technology with Vendor Relationship Manager. Promptly following the Effective Date, each party shall provide the other party with the name, telephone number, facsimile number and electronic mail address of their respective Relationship Managers. In addition to any notice requirements set forth in this Agreement, all significant communications relating to this Agreement will be directed to Relationship Managers for each party. Either party may change their Relationship Managers at any time during the Term of this Agreement by notifying the other party of such change.
4.22 Key Vendor Personnel means Vendor’s employees in key positions that are deemed by Comcast to be critical to the success of the Services including: Trainer(s), Quality Analyst(s), Workforce Management personnel, Development Lead(s), Vendor shall assign Key Vendor Personnel to support the Services during the term of an SOW. Vendor may replace Key Vendor Personnel without providing Comcast with prior notice provided that the replacement has the same skill sets in all material respects as the Key Vendor Personnel being replaced. Comcast shall have
the right to review the resume of such new Key Vendor Personnel. Comcast will not be charged for any time necessary to train replacement Key Vendor Personnel.
4.23 Vendor shall ensure skilled network facility repair personnel are available 7 days a week, 24 hours a day, 365 days a year to manage of Vendor’s network facilities (the “Network Personnel”). The Network Personnel shall have detailed knowledge of all systems used by Vendor to provide the Services and be capable of providing support and information to identify and resolve issues related to the Vendor’s network facilities. Network Personnel shall be on site [*] ([*]) minutes prior to the start of the Operation Hours (as defined in the applicable SOW) until [*] ([*]) minutes after the end of the Operation Hours as well as during any installation or maintenance of Vendor’s network facilities. Vendor shall provide Comcast with information regarding an outage of Vendor’s network facilities as soon as such information is available, including, but not limited to, the anticipated timeframe for resolution of the outage. Vendor shall provide the name, telephone number, facsimile number and electronic mail address of Vendor contacts to whom any telecommunications or network outage or latency problems are to be directed.
4.24 Vendor agrees to provide Comcast with daily, weekly and/or monthly report(s) of its performance under this Agreement in a format acceptable to Comcast, including, but not limited to, all reports listed in the applicable SOW. The parties agree to meet on a quarterly basis during the Term of this Agreement at a time and location determined by Comcast to review and discuss the performance of this Agreement and related matters such as planning, forecasting, new services and such other matters as Comcast deems appropriate. Any Vendor action items from such meetings must be followed-up on within [*] ([*]) hours, unless otherwise agreed to by Comcast. In addition to the reports set forth herein, Vendor will supply Comcast with a preliminary report within [*] ([*]) hours following any outage resulting in a loss of [*] or more Productive Hours and a complete post mortem within [*] ([*]) hours following the outage.
SECTION V
5.1 Comcast shall pay Vendor for its performance of the Services, pursuant to Section III.
5.2 Comcast shall comply with all laws, rules and regulations governing its activities under this Agreement.
5.3 Comcast shall keep Vendor informed of the descriptions, prices, terms and conditions under which the Comcast Products shall be provided, and Comcast shall review and approve/disapprove all scripts and other sales and marketing materials developed by Vendor on a timely basis.
5.4 Comcast shall invoice or arrange to invoice customers obtained by Vendor for the Comcast Products. Vendor shall have no right or obligation to xxxx or to collect any payments from actual or potential customers for Comcast Products, nor shall Vendor so xxxx and/or collect. Should
Vendor receive any payments for Comcast Products hereunder directly from a customer, Vendor shall immediately tender such payments to Comcast.
5.5 Comcast agrees that during the Term of this Agreement that it will not solicit any employee of Vendor for the express intent of employment with Comcast, provided that nothing herein shall prohibit any general advertisement for employment opportunities, which is not specifically targeted at any particular employee.
5.6 Comcast shall provide and maintain the Comcast online information systems, equipment and software necessary to provide the Services as determined by Comcast (the “Comcast Equipment”) including: Comtrac, Casper, Grand Slam, Agent Dash Board, Offer Management Tool, Links to relevant reporting tools, Outage Board, Rate Guide, Pinnacle, OCR Tool, Quality Assurance reporting portal, TTS, Einstein, and Cafe. The Comcast Equipment shall not include the equipment or software which Vendor is required to provide under this Agreement or an SOW. Vendor will provide Comcast with an estimate of all costs associated with software and/or hardware to be paid for by Comcast, if applicable. Comcast shall respond within [*] ([*]) business days of receiving the estimate. If Vendor does not receive a response within [*] ([*]) business days such estimate shall be deemed denied. Vendor shall not purchase any such software and/or hardware without the prior written approval from Comcast. Comcast shall retain title to Comcast Equipment at all times. Vendor shall not create or permit to be created any liens or encumbrances on Comcast Equipment. Comcast shall be responsible for providing and maintaining all equipment within Comcast’s firewall as it relates to providing connectivity for Vendor’s workstation infrastructure including, but not limited to, the network, servers, routers, hubs, data service units, and network information servers necessary to perform the Services.
5.7 If the Comcast Equipment is defective, Comcast, at its expense, shall repair or replace the defective Comcast Equipment; provided, however; this shall not apply to any Comcast Equipment that has been lost or damaged because of misuse, disaster (including, but not limited to, fire, flood, or earthquake) or theft while in the possession of the Vendor. In the event Comcast repairs or replaces such lost or damaged Comcast Equipment, Vendor shall pay the full replacement cost within [*] ([*]) days of the date of receipt of Comcast’s invoice.
5.8 If applicable to an SOW, Comcast shall provide Vendor with [*] ([*]) days advance written notice of the Service Level Targets (as defined in the SOW) for each fiscal month.
5.9 Promptly following the Effective Date, Comcast shall provide Vendor with a master copy of relevant documentation and materials for the Comcast Products as applicable to the Services. Alternatively, Comcast may provide such information electronically. Vendor may copy and circulate copies of such materials to its personnel who will be performing the Services provided it preserves the intellectual property marks or confidentiality marks contained on such materials. Vendor shall cease the use of and return the master copy and any and all copies of such documentation and materials to Comcast upon the termination of this Agreement as well as those materials developed by Vendor specific to the Services containing Comcast Proprietary Information.
CONFIDENTIAL TREATMENT
5.10 Comcast will appoint at least one relationship manager to manage the relationship with the Vendor established by this Agreement (the “Comcast Relationship Manager”). The Comcast Relationship Manager will: (i) have overall managerial responsibility for Comcast’s responsibilities under this Agreement; and (ii) serve as the primary liaison with Vendor Relationship Manager.
SECTION VI
6.1 Vendor will indemnify and hold Comcast and its respective partners, directors, officers, agents and employees (the “Indemnities”) harmless from and against all claims, demands suits, proceedings, damages, costs, expenses, liabilities (including, without limitation, reasonable legal fees) or causes of action (collectively, “Liabilities”) brought against or incurred by any Indemnitee for: (i) injury to persons (including physical or mental injury, libel, slander and death); (ii) loss or damage to property; (iii) violations of applicable laws, applicable permits, codes, ordinances or regulations by Vendor; (iv) damages arising from a data security breach involving Vendor’s local network environment; or (v) any claims arising out of or in connection with Vendor’s obligation pursuant to this Agreement or any other liability, resulting from the negligence or willful misconduct of Vendor, its officers, agents, employees, or subcontractors in the performance of this Agreement. If Vendor and Comcast jointly cause such Liabilities, the Parties will share the liability in proportion to their respective degree of causal responsibility. Comcast will indemnify and hold Vendor and its respective partners, directors, officers, agents and employees harmless from and against all claims, demands, suits, proceedings, damages, costs, expenses, liabilities (including without limitation, reasonable legal fees) or causes of action (collectively, “Liabilities”) brought against or incurred by Vendor for: (i) any claims arising out of or in connection with Comcast’s obligation pursuant to this Agreement or any other liability resulting from the negligence or willful misconduct of Comcast, its officers, agents or employees in the performance of this Agreement.
6.2 Notwithstanding anything in this Agreement to the contrary, if a Fine (as defined below) is charged or owed due to Vendor’s failure to make the PCI Environment (as defined below) PCI Compliant as set forth in Exhibit A, Vendor will indemnify, defend, and hold Comcast harmless from and against such Fine. If a Fine is charged or owed due in material part to Comcast, including Comcast’s hardware, software, network (excluding the services provided by another service provider/vendor), Vendor will have no indemnity obligations related to such Fine, provided that Vendor has notified Comcast that it is unable to be PCI Complaint due to Comcast prior to the assessment of such Fine. If a Fine is charged or owed partially due to Vendor’s failure to make the PCI Environment PCI Compliant, Vendor shall only be liable for Vendor’s proportionate amount of such Fine as determined based on any specific percentage attribution of causation determined by the entity charging, determining, or owed the Fine, or if no such attribution is specified, on a pro rata basis between Vendor and the other parties identified as responsible for such failure. A “Fine” shall mean any administrative or breach based fines or penalties levied against Comcast specifically for its failure to be PCI compliant.
12
COMCAST CONFIDENTIAL
US.54162848.01
PARTY’S BREACH OF SECTION X (RELATING TO CONFIDENTIALITY) OF THIS AGREEMENT (IN EACH CASE, WITH RESPECT TO WHICH THESE LIMITATIONS SHALL NOT APPLY), UNDER NO CIRCUMSTANCES WILL EITHER PARTY BE LIABLE TO THE OTHER PARTY (WHETHER BASED IN CONTRACT, TORT, OR OTHER LEGAL OR EQUITABLE GROUNDS) FOR INDIRECT, INCIDENTAL, CONSEQUENTIAL, SPECIAL OR EXEMPLARY DAMAGES (EVEN IF THAT PARTY HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES), INCLUDING BUT NOT LIMITED TO, LOSS REVENUE OR ANTICIPATED PROFITS OR LOST BUSINESS.
SECTION VII
Except as otherwise provided in this Agreement, an SOW or as otherwise agreed to in writing by the parties, Comcast shall be responsible for all expenses incurred by Comcast in the performance of Comcast’s obligations under this Agreement and/or SOW. Vendor shall be responsible for all costs and expenses arising out of or relating to the provision of the Services and all other resources required for Vendor to perform its obligations under this Agreement or an SOW.
SECTION VIII
8.1 Except as expressly provided in Section 8.2, Vendor shall not be deemed by anything contained in this Agreement or done pursuant to it to acquire any right, title or interest in or to the use of the name “Comcast,” the Comcast service marks, or in or to any trademark or service xxxx now or hereafter owned by or used by Comcast or any parent, subsidiary or affiliate thereof (the “Marks”).
8.2 Vendor shall not use the Marks in its business, trade or corporate name without the express written consent of Comcast. To the extent that this Agreement expressly authorizes use of such Marks, such use by Vendor is permitted solely for purposes of the Vendor’s performance of its obligations under this Agreement, and such Marks may not, in any instance, be used to promote the services of Vendor or of any provider of products or services other than Comcast.
8.3 Immediately upon termination of this Agreement, Vendor will turn over to Comcast any materials using any Xxxx, unless Comcast has consented to ongoing use by the Vendor of such Marks pursuant to a separate agreement.
SECTION IX
9.1 Neither party shall be deemed by anything contained in this Agreement or done pursuant to it to acquire any right, title or interest in or to any design, invention, improvement, process, methodology, ideas, know-how, techniques or system now or hereafter embodied in any Comcast Product or in any hardware, software or middleware provided by a party to the other party,
whether or not such design, invention, improvement, process or system is patented or patentable under the laws of any country.
9.2 Comcast shall have the right to acquire the right to use (by ownership, license or otherwise) for itself and any of its subsidiaries or affiliates any customer service systems and any other system, process, tool, method, procedure or information developed by Vendor in connection with providing the Services on terms reasonably acceptable to Comcast and Vendor.
SECTION X
10.1 Both parties agree that all information furnished to it by the other party which is identified as being proprietary or confidential or which the receiving party knows or has reason to know is confidential, trade secret or proprietary information (the “Proprietary Information”) is to be treated in a confidential manner and shall remain the sole and exclusive property of the providing party. Proprietary Information may not be directly or indirectly disseminated to any third party without the prior written consent of the disclosing party; provided, however, that the receiving party may disclose the same to its employees and subcontractors that have a need to know because of their involvement in this Agreement and have agreed to maintain the confidential nature of the Proprietary Information. Both parties acknowledge that the Proprietary Information of the other party is a valuable asset of the disclosing party, that any unauthorized disclosure or use thereof may cause irreparable harm and loss, that monetary damages may not be sufficient to compensate, and that injunctive relief is an appropriate remedy to prevent any actual or threatened unauthorized use or disclosure of the Proprietary Information. Without limiting the foregoing, the terms and conditions of this Agreement are Proprietary Information. Both parties shall return any copies of Proprietary Information to the disclosing party upon the request of the disclosing party and upon the termination or expiration of this Agreement.
10.2 The confidentiality and non-disclosure obligations set forth herein do not apply to any portion of the Proprietary Information that (i) is or becomes public knowledge through no fault of the receiving party; (ii) is disclosed to the receiving party without a restriction on disclosure by a third party that has the lawful right to disclose the same; or (iii) is required to be disclosed by the receiving party pursuant to a lawful and formal request of a governmental or regulatory authority (so long the receiving party provides the disclosing party with prior written notice of such governmental or regulatory request and a reasonable opportunity under the circumstances to contest such request).
10.3 Neither party shall use any confidential information belonging to a third party in furtherance of their obligations hereunder, unless otherwise authorized by that third party.
10.4 Comcast must pre-approve and control the dissemination of any public announcement, press release or other publicity arising from or in connection with this Agreement or any SOW including, but not limited to: (i) the existence and financial terms of this Agreement or SOW; (ii) any contractual awards that may occur as a result of this Agreement or SOW; and (iii) any Comcast Product information.
10.5 Vendor hereby acknowledges that Comcast has a special responsibility under the law to keep personally identifiable information of its customers (“PII”) private and confidential. PII is subject to the subscriber privacy protections set forth in Section 631 of the Cable Communications Policy Act of 1984, as amended (47 USC Sec. 551), as well as other applicable federal and state laws. Vendor agrees that it shall use such information in strict compliance with Section 631, all other applicable laws governing the use, collection, disclosure and storage of such information, and the protocols set forth hereunder. In addition to and without limiting the foregoing, in no event shall Vendor use, disclose or in any way provide personally identifiable information of a customer in violation of 47 USC 551 (as amended and supplemented, “Section 551”) and Vendor further agrees to comply with all requirements and provisions of Section 551.
10.6 The provisions of this Section 10 shall survive the expiration or termination of this Agreement.
SECTION XI
11.1 All actual customers who contact Vendor concerning the Comcast Products are customers of Comcast and not customers of Vendor. Vendor hereby agrees that Comcast holds all title, right, possession in its customers and that no such title, right, possession and dominion shall pass to Vendor hereunder.
11.2 All customer information, including, but not limited to, customer names, addresses, telephone numbers, email addresses, service selections and the like, shall constitute Comcast Proprietary Information, regardless of whether or not such information is specifically identified as such. Vendor shall use such customer information for no other purpose or purposes other than those expressly authorized in this Agreement or an SOW.
11.3 Vendor, its affiliates and subsidiaries, and their respective employees and agents, hereby agree that they shall not directly or indirectly induce, influence or suggest that any actual or prospective Comcast customer purchase, contract for, or switch to any non-Comcast product or service. Comcast shall have the right to enforce this Section XI by obtaining an injunction or specific performance from any court of competent jurisdiction. Additionally, if Vendor its affiliates and subsidiaries, and their respective employees and agents or its subcontractors violates this Section XI, Comcast, in addition to the right to terminate the Agreement pursuant to Section XII, shall be entitled to recover reasonable attorneys’ fees in redressing said breach. The provisions of this Section XI shall survive the termination of this Agreement. The remedies set forth herein are cumulative and are in addition to, and not in limitation of, other remedies available at law or in equity. None of the remedies specified in this Section XI for any default or breach of this Agreement shall be exclusive.
SECTION XII
TERM AND TERMINATION
12.1 The term of this Agreement shall commence on the Effective Date and shall continue in full force and effect thereafter for one (1) year unless terminated earlier in accordance with this Agreement (the “Initial Term”). The Agreement shall automatically renew for additional one (1) year periods (each a “Renewal Term”) unless written notification of cancellation is provided by either party no less than sixty (60) days prior to the termination of the then current Term. The Initial Term and the Renewal Term, if any, are collectively the “Term.”
12.2 Comcast may, at its election, terminate this Agreement and/or any SOW without cause on ninety (90) days written notice to Vendor; provided, however, Comcast shall continue to be obligated to Vendor for payment for all unpaid fees for Services rendered by Vendor as of the termination date (except to the extent otherwise provided for in this Agreement and/or the applicable SOW).
12.3 Comcast may, at its election, terminate this Agreement and/or any SOW immediately if an order by any court or governmental authority with proper jurisdiction deems the activities of either party to be in conflict with an applicable law, rule or regulation, if Comcast loses any authorization, franchise or permit necessary to provide the Comcast Products, or if Comcast ceases to provide such Comcast Products.
12.4 Comcast may, at its election, terminate this Agreement, and/or any SOW if a material breach by Vendor occurs, and such material breach continues for a period of thirty (30) days after written notice from Comcast to Vendor specifying the breach.
12.5 Vendor may, at its election, terminate this Agreement and/or any SOW if a material breach by Comcast occurs, and such material breach continues for a period of thirty (30) days after written notice from Vendor to Comcast specifying the breach.
12.6 Comcast may, at its election, terminate this Agreement and/or any SOW if Vendor becomes insolvent or makes an assignment for the benefit of its creditors, or if a committee of creditors or other representative is appointed to represent its business, or if a voluntary or involuntary petition under any section of a bankruptcy or similar act shall be filed by or against the Vendor and the Vendor fails to discharge the petition or to obtain dismissal of the petition within ten (10) days following the appointment of such committee or representative.
12.7 Vendor may, at its election, terminate this Agreement and/or any SOW if Comcast becomes insolvent or makes an assignment for the benefit of its creditors, or if a committee of creditors or other representative is appointed to represent its business, or if a voluntary or involuntary petition under any section of a bankruptcy or similar act shall be filed by or against Comcast and Comcast fails to discharge the petition or obtain dismissal of the petition within ten (10) days following the appointment of such committee or representative.
12.8 Except as expressly set forth in this Agreement, no termination of this Agreement and/or any SOW shall affect any accrued rights or obligations of either party as of the effective date of such termination, nor shall it affect any rights or obligations of either party which are intended by the parties to survive any such termination. Any remedies set forth in this Agreement for a
termination by Comcast due to breach of this Agreement by Vendor are cumulative and are in addition to, and not in limitation of, other remedies available at law or in equity. None of the remedies specified in this Agreement for any default or breach of this Agreement shall be exclusive, unless expressly set forth in this Agreement.
12.9 In connection with any termination or non-renewal of this Agreement or an SOW, Vendor agrees to assist Comcast with a smooth and efficient transition of the Services to a third party designated by Comcast or to Comcast. Such transition shall be for the period designated in the notice of termination but shall not exceed [*] ([*]) months (the “Transition Period”). Such transition shall include, without limitation: (i) such reasonable assistance, advice and training as Comcast may request, (ii) the assignment or sublicensing of any third party licenses used by Vendor in providing the Services, (iii) making available to Comcast on reasonable terms any third party services being used by Vendor in providing the Services, (iv) a continuation of the Services during the Transition Period, and (v) such other reasonable assistance as Comcast may request. If Comcast terminates this Agreement or an SOW pursuant to Section 12.4 above, Vendor shall pay all of Comcast’s costs associated with transitioning the Services to a third party designated by Comcast or to Comcast. In the event such Transition Period extends after the Term of this Agreement, Vendor’s performance of the Services and Comcast’s payment therefore during the Transition Period shall be governed by the applicable SOW and this Agreement.
SECTION XIII
13.1 Neither party to this Agreement is an agent, partner or employee of the other; rather, the parties are independent contractors. Vendor shall not be treated as an employee of Comcast for any purpose, including, but not limited to, state or federal income tax, the Federal Unemployment Tax Act, Federal Insurance Contributions Act, the Social Security Act or any other state, federal, provincial or other unemployment or employment security act. Vendor is not authorized to make any promise, warranty or representation on Comcast’s behalf with respect to the Comcast Products or to any other matter, except as expressly authorized in writing by Comcast.
13.2 Each party acknowledges that it has separate responsibility for all applicable federal, state, provincial and local taxes for itself and any of its employees and each party agrees to indemnify and hold the other harmless from any claim or liability therefore.
13.3 Each party understands and agrees that its employees shall not be entitled to participate in health or disability insurance, retirement or pension benefits, if any, to which employees of the other party may be entitled.
SECTION XIV
14.1 Comcast is an equal opportunity employer and is a federal contractor. Consequently, the parties agree that, to the extent applicable, they will comply with Executive Order 11246, The
Vietnam Era Veterans Readjustment Assistant Act of 1974 and Section 503 of the Vocational Rehabilitation Act of 1973 and also agree that these laws are incorporated herein by reference.
SECTION XV
15.1 Vendor represents and warrants that (i) the execution, delivery and/or performance of this Agreement or an SOW will not conflict with or result in any breach of any provision of the charter, by-laws or other governing instruments of Vendor or any agreement, contract or legally binding commitment or arrangement to which Vendor is a party, and (ii) Vendor is not subject to any limitation or restriction (including, without limitation, non-competition, and confidentiality arrangements) that would prohibit, restrict or impede the performance of Vendor’s obligations under this Agreement or an SOW. If any of the foregoing representations or warranties should prove untrue, Vendor shall be deemed in material breach of this Agreement.
15.2 Comcast warrants and represents to the best of its knowledge that at no time during the Term of this Agreement will the use of any services, information, materials, techniques, or products directly provided by Comcast infringe upon any third party’s patent, trademark copyright, or other intellectual property right, nor make use of any misappropriated trade secret. No statements contained in any written information furnished to Vendor by or on behalf of Comcast in connection with this Agreement to the best of Comcast’s knowledge contain any untrue statement of a material fact or omit any material fact necessary to make the statement not misleading.
SECTION XVI
16.1 Vendor will supply Comcast with a copy of its written disaster avoidance and recovery plan (the “DAR Plan”). The DAR Plan shall contain procedures designed to safeguard Comcast’s Proprietary Information and the availability of the Services, throughout the Term and shall include, without limitation, the following:
(i) Fire Protection. Consisting of the appropriate type and quality of equipment required to provide effective fire protection that it is regularly reviewed and updated, with smoke detectors (with remote enunciators and zone indicators) and automatic sprinkler systems in any computer areas.
(ii) Power. Multiple levels of power backup designed to provide uninterrupted operation of Vendor equipment and Comcast Equipment in the event of a loss of power in accordance with Comcast’s Technical Requirements (attached hereto as Exhibit C). Power
requirements shall include multiple feeds to Vendor site(s) from different processing stations of the local power company which furnishes the main power to Vendor site(s).
(iii) Equipment/Air Conditioning. Multiple levels of protection against loss of cooling, including a primary backup system which shall provide adequate backup cooling capacity, and a secondary backup system, which shall be capable of providing continuous cooling during a power outage so as to maintain Vendor equipment and Comcast Equipment at all times within the tolerances specified by the appropriate manufacturer.
(iv) Computer Equipment. Appropriate backup equipment that is capable of maintaining operations in the event of hardware failures at Designated Facilities with detailed, written recovery procedures which its personnel are familiar with which enable Vendor personnel to switch to backup hardware with minimal impact to Comcast.
(v) Power Generation. Details related to the frequency and load (for or partial) tests of Vendor’s power generating capacity.
(vi) Testing. Testing to ensure Vendor’s compliance with the DAR Plan performed at Designated Facilities [*] per year. The testing shall include, but not be limited to, testing of hardware, installation and operation of all systems, processing of data and generation of reports, and testing of telecommunications facilities. The Vendor shall supply test results to Comcast within [*] weeks of each test. Failure to successfully complete the test will require re-testing within [*] ([*]) days of the original test. Vendor shall ensure that it will not fail testing more than [*] ([*]) times in any [*] month period.
(vii) Recovery Procedures. Appropriate recovery procedures and automated recovery tools for a call center operations facility.
(viii) Operations Interruptions. Restoration of the Services as expeditiously as possible in the event of an unscheduled interruption. Vendor shall notify Comcast within [*] ([*]) minutes of an unscheduled interruption. Notification will follow Comcast’s escalation process related to the report of technology related outages.
(ix) Time Frames For Recovery. Time frames for restoration of Comcast’s Services. Vendor shall work with telecommunications carriers and equipment vendors to restore service as expeditiously as possible. Any recovery times will be considered as downtime to Comcast.
(x) Maintenance Of Safeguards. Safeguards throughout the Term against destruction, loss, or alteration of Comcast’s data, which are no less rigorous than those Comcast uses to protect Comcast data.
16.2 Any changes to the DAR Plan must be presented for review and approval by Comcast prior to implementation. The DAR Plan shall be reviewed by the parties on a quarterly basis and updated during the Term using American Institute of Certified Public Accountants standards as
guidance. All personnel required under the DAR Plan shall have a current copy of the DAR Plan and shall be trained on the DAR Plan. In the event of a disaster, Vendor shall use its best efforts to migrate the Services to another site within [*] ([*]) hours of such disaster. Notwithstanding, the foregoing, in the event of a disaster which impairs Vendor’s ability to provide the Services, Comcast shall have the right in its reasonable discretion to immediately perform the Services itself or to have the Services performed by a third party.
16.3 Vendor acknowledges and agrees that Vendor will not receive reimbursement for Productive Hours or other compensation lost due to a disaster even if Vendor meets the requirements of the DAR Plan. Notwithstanding anything in this Agreement to the contrary, Vendor further acknowledges and agrees that a failure to perform its obligations under this Agreement shall not be excused where such failure is caused by a failure to implement, update, or maintain the DAR Plan.
SECTION XVII
17.1 Assignability. This Agreement is fully assignable by Comcast, provided, however, in the event Comcast assigns this Agreement Vendor shall have the right to terminate this Agreement for a period of [*] ([*]) days after the effective date of such assignment by providing [*] ([*]) days prior written notice. Vendor acknowledges that Vendor has been selected to participate in Comcast’s call handling program after evaluation by Comcast of Vendor’s financial stability and reputation in the business community, as well as the individual abilities and reputation of Vendor’s management and work force. Accordingly, the parties agree that neither this Agreement, nor any SOW or any right or obligation hereunder, is assignable, in whole or in part, whether by operation of law or otherwise, by Vendor, without the prior written consent of Comcast. In the event of a permitted assignment or transfer, this Agreement and any SOW shall be binding upon and inure to the benefit of the parties hereto and their authorized successors and assigns.
17.2 Subcontractors. Vendor agrees that it will not subcontract or attempt to subcontract any of its duties or obligations hereunder without the prior written consent of Comcast. Vendor’s use of a subcontractor does not release Vendor from any of its liabilities or obligations under this Agreement and/or an SOW. Vendor is responsible for all actions and omissions of its subcontractors that are performing for or acting on behalf of Vendor.
17.3 Counterparts. This Agreement may be executed in two counterparts, each of which shall be deemed an original, but both of which together shall constitute one and the same instrument.
17.4 Severability. In the event any provision of this Agreement and/or an SOW is held to be illegal or unenforceable, that provision shall be limited or eliminated to the minimum extent necessary so that this Agreement and/or an SOW shall otherwise remain in full force and effect and be enforceable.
17.5 Force Majeure. Neither party shall be responsible for any delay or failure in performance of any part of this Agreement and/ or an SOW to the extent such delay or failure is caused by any force majeure condition, including, but not limited to, act of God, labor dispute,
strike or government requirement. If any such condition occurs, the party delayed or unable to perform shall promptly give notice to the other party, and, among other remedies, the affected party may, at its discretion, extend the Term of this Agreement up to the length of time the condition has endured.
17.6 Waiver. The failure of either party to enforce at any time any provision of this Agreement and/or an SOW, or its failure to exercise any option that is herein provided, or its failure to require at any time performance of any provision herein by that party shall in no way affect the validity of, or act as a waiver of, this Agreement and/or an SOW, or any part thereof, or any right of that party thereafter to enforce it.
17.7 Amendment and Modification. Except as provided in this Agreement, any amendment or modification of any provision in this Agreement, including modification of any SOW, will not be effective unless the amendment or modification is in writing and signed by both parties. Such amendment and modification shall be enforceable by its terms when signed by both parties.
17.8 Governing Law. This Agreement shall be governed and construed in all respects in accordance with the laws of the Commonwealth of Pennsylvania. The parties agree that any controversy or dispute arising out of or relating to this Agreement shall be settled by binding arbitration in Philadelphia, Pennsylvania, in accordance with the rules of the American Arbitration Association then in force. The arbitration shall be governed by the United States Arbitration Act, and judgment upon the award rendered by the arbitrator(s) may be entered by any court having jurisdiction thereof.
17.9 Notices. All notices required or permitted hereunder shall be in writing and addressed to the respective parties as set forth below, which may from time to time be modified, and such notice shall be delivered by hand or by registered or certified mail, postage prepaid.
If to Comcast: | Comcast Cable Communications Management, LLC One Comcast Center 1701 JFK Boulevard Philadelphia, PA 19103-2838 Attention: Sr. Vice President of Customer Service |
with copies to: | Comcast Cable Communications Management, LLC One Comcast Center 1701 JFK Boulevard Philadelphia, PA 19103-2838 Attn: General Counsel, Cable Legal Comcast Cable Communications Management, LLC One Comcast Center 1701 JFK Boulevard Philadelphia, PA 19103-2838 Attn: Sr. Vice President, Cable Procurement |
If to Vendor: | |
with a copy to: | ________________________ ________________________ Attention: _______________ |
17.10 Entire Agreement. This Agreement, together with any SOW, recitals and all exhibits incorporated therein by reference, constitutes the entire agreement of the parties hereto and supersedes all prior representations, proposals, discussions and communications, whether oral or in writing.
17.11 Captions and Headings. The captions and headings of this Agreement or an SOW are for convenience and reference only and in no way define, limit, or describe the scope or intent of this Agreement or any portion thereof, nor affect it in any way the meaning or interpretation of this Agreement.
SECTION XVII
18.1. Vendor hereby represents, warrants and covenants that:
(a) Vendor and any of its owners, affiliates, officers, directors, employees and agents involved in providing services under this Agreement, will comply with all applicable anti-corruption laws, including the U.S. Foreign Corrupt Practices Act, UK Bribery Act, and any other applicable jurisdiction where the Services are provided;
(b) In carrying out its responsibilities under the Agreement, neither Vendor nor any of its owners, affiliates, officers, directors, employees or agents will offer, promise or give anything
of value, directly or indirectly to: (i) any public or elected official or officer, employee (regardless of rank) or person acting on behalf of a national, provincial, or local government, department, agency, instrumentality, state-owned or state–controlled company, public international organization (such as the United Nations or World Bank), political party or entity that is financed in large measure through public appropriations, is widely perceived to be performing government functions, or has its key officers and directors appointed by a government and (ii) any party official or any candidate for political office and any person acting on behalf of any governmental entity referred to in clause (i) or candidate for public office (“Government Officials”), in order to influence official action or otherwise obtain an improper business advantage
(c) In carrying out its responsibilities under the Agreement, neither Vendor nor any of its owners, affiliates, officers, directors, employees or agents will offer, promise or give anything of value, directly or indirectly, to (i) any other person while knowing that all or any portion of the money or thing of value will be offered or given to a Government Official in order to influence official action or otherwise obtain an improper business advantage or (ii) to any other person in order to induce them to perform their work duties disloyally or otherwise improperly;
(d) No government is investigating or has in the past five years conducted or initiated threatened any investigation of Vendor or any of its owners, affiliates, officers, directors or employees for alleged violation of anti-corruption laws.
18.2 In the event Comcast has a reasonable basis to believe that a breach of any of the representations, warranties and covenants in this Section has occurred or will occur, Comcast may suspend work under any and all SOWs until such time as it is satisfied that no breach has or will occur. Comcast shall provide notice to Vendor in the event it believes a breach of any of the representations, warranties and covenants in this Section has occurred or will occur and provide a reasonable description of the basis for such belief. Comcast shall not be liable to Vendor for any claim, losses or damages whatsoever related to its decision to suspend work under an SOW in accordance with this provision.
18.3 In the event of an actual breach of any of the representations, warranties and covenants in this Section, this Agreement may be immediately terminated by Comcast upon written notice to Vendor. In addition to and not in lieu of Vendor’s indemnification obligations under this Agreement, Vendor shall further indemnify and hold Comcast harmless against any and all claims, losses or damages arising from or related to such breach or Comcast’s termination this Agreement due to such breach, or both.
18.4 In no event shall Comcast be obligated under this Agreement to take any action or omit to take any action that Comcast believes, in good faith, would cause it to be in violation of any laws, including the U.S. Foreign Corrupt Practices Act, or the UK Bribery Act.
18.5 In carrying out its responsibilities under this Agreement, Vendor will not provide any meals, gifts, gratuities, entertainment or travel to any Government Official without the prior approval of Comcast.
CONFIDENTIAL TREATMENT
18.6 Comcast shall, at its own cost, have the right to audit Vendor’s compliance with this Section and applicable laws and regulations. Upon request by Vendor or at the discretion of the Company, Comcast shall select an independent third party to conduct such audit. Vendor shall fully cooperate in any such audit conducted by or on behalf of Comcast. Any such audit shall be conducted upon not less than [*] ([*]) business days’ notice.
an SOW
IN WITNESS WHEREOF, the parties have executed this Agreement as of the date first above written.
COMCAST CABLE COMMUNICATIONS MANAGEMENT LLC | |
BY: /s/ Xxxxx Xxxxxxxxxxxxx | BY: /s/ Xxxx X. Xxxxxxx |
NAME: Xxxxx Xxxxxxxxxxxxx | NAME: Xxxx Xxxxxxx |
TITLE: EVP & Chief Procurement Officer | TITLE: President & CEO |
DATE: 11/25/13 | DATE: 1-6-14 |
WITNESS BY: | WITNESS BY: |
NAME: | NAME: |
DATE: ______________________________ | DATE: ______________________________ |
25
COMCAST CONFIDENTIAL
US.54162848.01
EXHIBIT A: SECURITY PROTOCOLS
I. PII. Vendor hereby acknowledges that Comcast has a special responsibility under the law to keep personally identifiable information of its customers (“PII”) private and confidential. PII is subject to the subscriber privacy protections set forth in Section 631 of the Cable Communications Policy Act of 1984, as amended (47 USC Sec. 551), as well as other applicable federal and state laws. Vendor agrees that it shall use such information in strict compliance with Section 631, all other applicable laws governing the use, collection, disclosure and storage of such information, and the protocols set forth hereunder.
II. Confidentiality Agreements. Vendor agrees to restrict disclosure of PII to those employees, contractors, or sub-contractors with a need to know and who are bound by contract to the confidentiality provisions herein. Such confidentiality agreements shall further restrict disclosure of any and all PII and usage data, activity data or other information collected from or about or otherwise regarding Comcast’s Subscribers whether in individual or aggregate form. To the extent that Vendor has access to or collects such usage data, it does so solely on behalf of Comcast pursuant to its obligations hereunder and shall maintain the confidentiality of such data in accordance with Comcast’s then applicable privacy policies, privacy statements and applicable law. Vendor shall not collect or maintain such usage data except to the extent necessary to perform its obligations under this Agreement. Vendor shall retain employee and contractor confidentiality agreements for a period of one year following termination of this Agreement.
III. Building Security. Vendor shall ensure that the Designated Facilities or any facility where Vendor stores any Comcast Proprietary Information are physically secure at all times in accordance with Vendors Security Plan (as defined below) and standard call center industry practice, including after business hours. All authorized employees or contractors with access to such facilities shall be issued and required to carry employee identification. Visitors to such facilities shall be escorted at all times.
IV. Encryption. Any PII or usage data that is collected or obtained by Vendor must be stored and transmitted in encrypted or otherwise secure form. In the event of a breach of security of any system, website, database, equipment or storage medium or facility that results in unauthorized access to PII or usage data by any third party (including any employee or subcontractor of Contractor that is not authorized to access such information), Vendor shall notify Comcast immediately and make best efforts to resecure its systems immediately.
V. Remote Access. To the extent that Vendor is authorized to gain remote access to Comcast’s networks or equipment for purposes of performing its obligations hereunder, Vendor shall ensure that:
a. | Access is restricted to authorized employees. |
b. | Comcast is provided with a list of all such authorized employees upon request. |
c. | Remote access is used solely for purposes of fulfilling Vendor’s obligations under this Agreement and only to access equipment or software that is directly involved in Vendor’s |
performance of its obligations hereunder and not to access any other Comcast or third party systems, databases, equipment or software.
d. | Remote access is obtained through a secure connection. |
e. | Compliance with the applicable policies, standards and or requirements set forth in Exhibit D - Telecommunications Specifications. Upon Comcast’s request, Vendor will perform and provide results of periodic security audits of its access system and methods and will change authentication elements periodically to maintain the integrity and security of Vendor’s access. |
VI. User ID, Password, Device Administration. Vendor is responsible for the ongoing administration of User IDs, Password for Comcast tools and systems and peripheral devices installed on equipment which has access to Comcast tools and systems. As such, Vendor must take appropriate and reasonable measures to ensure:
a. | User IDs are unique to each employee |
b. | Access privileges do not exceed what is necessary for the performance of the Comcast approved activity |
c. | Terminated employee User IDs are disabled immediately and a formal process to remove physical access for CSRs in a timely manner upon separation from Vendor. |
d. | User IDs are audited monthly and the results of the audit are provided to Comcast upon request. |
e. | All Vendor network and systems access are controlled by enforcing strong passwords (e.g. 8 characters should include lower, uppercase letters and at least one special character. i.e. !@#$%). |
f. | All passwords shall be changed every 90 days, and no duplicate passwords are allowed in the last 7 password changes. Access must be locked after three failed attempts to enter a password. First time passwords for new user accounts which are set to a unique value and must be changed immediately upon first logon. |
g. | Peripheral devices including but not limited to wireless network adapters, USB external drives, CD/DVD drives, and other devices that may result in a breach of these security protocols are disabled. |
h. | Workstations connected to Comcast’s network cannot be used for purposes other than for the provision of the Services, including, but not limited to access unrelated websites or the download and installation of third party software or applications. |
VII. Security Plan. The Vendor must have a documented security plan approved by Comcast for all of Vendor’s systems that are necessary to support the Services (the “Security Plan”). The plan must include:
a. | Security awareness programs are in place to communicate policies and best practices to personnel on a regular basis. |
b. | A formal process to dispose of technology assets with management approval prior to disposal. |
c. | A formal process to remove all data from technology assets before disposal. |
d. | A formal process to evaluate and implement critical security patches based on business need. |
e. | A formal process to ensure default system settings, such as default permissions, accounts and passwords have been configured in accordance with Vendor security policies. |
f. | A formal process to forward audit logs to a centralized log collection facility for mutually agreed upon systems for monitoring and archiving. |
g. | A formal process to deploy host-based firewalls on all desktops or laptops with access to Comcast Proprietary Information. |
h. | A formal process to secure backup tapes. |
i. | A formal process to approve physical access to the facilities by authorized personnel prior to a person being granted access. |
j. | A formal process to review all physical access to facilities on a regular basis to assure access is commensurate with job responsibilities. |
k. | If applicable, a formal process to apply similar security controls and framework for work from home CSRs as are applied for CSRs in Designated Facilities. |
VII. Social Media, Removal of Proprietary Information. Vendor is responsible for taking appropriate and reasonable measures to ensure Comcast Proprietary Information is not disseminated by Vendor employees or contractors in public forums. Vendor shall further prohibit physical removal of any item containing Comcast’s Proprietary Information from any Vendor facility, regardless of the format in which it is stored, including but not limited to, disks, hard drives, or hard copy.
VIII. PCI Compliance. In the event Vendor engages in payment card transactions as a part of the services provided to Comcast, Vendor shall comply with the Payment Card Industry Data Security Standards (“PCI DSS”) and any amendments or restatements of the PCI DSS during the
Term of this Agreement. Vendor accepts responsibility for the security of customer credit card data in its possession, even if all or a portion of the services to Comcast are subcontracted to third parties.
IX. Network Traffic Routing. Vendor’s network traffic routing policy shall protect Comcast’s information security and data integrity. There shall be no opportunity for the mingling of Comcast’s Proprietary Information with other non-Comcast traffic. Vendor’s network traffic routing policy shall ensure only traffic destined for Comcast targets is directed to the point-to-point virtual private network (“VPN”) between Vendor and Comcast and any other traffic, including local network traffic and general Internet traffic, is not directed to the VPN.
X. Anti-Virus. Vendor shall maintain industry standard methods for defense against malware/trojan/virus infection. Vendor shall maintain a program of anti-malware/anti-virus updates to keep Vendor desktops free of infection. Vendor shall at regular intervals desktop execute scans and/or desktop image refresh actions to ensure workstation integrity and minimize the likelihood of infection.
X. Protocol Exceptions: Exceptions to the stipulated protocols may be granted with prior written consent from Comcast.
29
COMCAST CONFIDENTIAL
US.54162848.01
CONFIDENTIAL TREATMENT
EXHIBIT B: PARTNER CONNECTION REQUEST POLICIES
In granting access to Comcast networks, Comcast assumes certain risks caused by systems beyond the administrative control of Comcast Information Technology controls and Comcast Information Security controls. To limit those risks, Comcast requires that all third party partners connecting to Comcast internal networks take reasonable actions to ensure that the third party partner network does not negatively impact the confidentiality, integrity, and availability of Comcast Information Assets, and that the confidentiality of Comcast information on third party partner systems is adequately maintained.
While Comcast requires vendors accessing its network to take reasonable measures to protect their information assets, Comcast provides no assistance to third party partners on matters of network configuration, computer security, or application assistance, other than that which is deemed necessary by Comcast to connect to Comcast Information Assets.
Policy | Applicable | Not Applicable |
Third Party Partner Requirements | X | |
Payment Card Industry Data Security Standards | X | |
Access Control Policy | X | |
Authentication Policy | X | |
Change Management Policy | X | |
Employee Personal Information Security Policy | X | |
Payment Card Protection Policy | X | |
Software Compliance Policy | X | |
30
COMCAST CONFIDENTIAL
US.54162848.01
CONFIDENTIAL TREATMENT

Comcast Cable Communications, Inc.
Information Technology
Third Party Partner Requirements
1.0 Purpose
This purpose of these requirements is to establish secure standards under which third party companies can remotely access Comcast Information Assets for the purpose of conducting business related to Comcast.
These requirements apply to all connections allowing third party companies access to non-public Comcast information assets from a location external to Comcast facilities. These requirements apply regardless of connection type, and include, but are not limited to, dedicated connections, virtual private networks, and dial-up connections.
These requirements apply to all systems connecting to the Comcast network, any systems containing information obtained from the Comcast network, and any systems holding data about Comcast customers, systems, or business operations.
3.1 General
Third party vendor connections are to be used only for the purposes of conducting Comcast business
The third party vendor Is responsible for any Comcast equipment at their premises, excluding activities involving configuration and maintenance of said equipment
Configuration of Comcast equipment at third party vendor locations is only to be done under the direction of authorized Comcast personnel
Third party vendors will only be allowed access to necessary systems, and will be granted the least amount of access to achieve the business objective, as determined by Information Protection and the Firewall Operations Center
All access control mechanisms used to restrict access to Comcast data will be controlled by Comcast and will be located on Comcast controlled equipment
It is the responsibility of all Comcast employees, employees of other companies covered by a Comcast Partner Connection Request, contractors, consultants, and any other parties with access to Comcast data and/or systems to ensure that all policies and procedures relating to third party access of Comcast Information Assets are followed.
31
COMCAST CONFIDENTIAL
US.54162848.01
CONFIDENTIAL TREATMENT | ||
 | Comcast Cable Communications, Inc. | |
Information Technology | ||
No third party network connection will be granted without a fully completed Comcast Partner Request that has been approved by the appropriate zone security group and a properly executed confidentiality agreement approved by the Comcast legal team.
While Comcast requires vendors accessing its network to take reasonable measures to protect Information assets, Comcast provides no assistance to third party partners on matters of network configuration, computer security, or application assistance, other than that which is deemed necessary by Comcast to connect to Comcast Information Assets. Any third party partner needing assistance with these Items should be directed to their IT support organization.
3.2 Auditing
Any aspects of third party network connections and third party handling of Comcast Information Assets are subject to inspection and auditing by Comcast or its designated agent, including, but not limited to, on-site inspections of third party partner facilities, Inspection of electronic communications traveling between Comcast and the third party partner, third party partner processes and procedures, and electronic assessment of third party partner networks which access Comcast Information Assets.
Only third party partner personnel approved through this process are allowed access to Comcast Information Assets
The third party partner must notify the CPOC immediately when third party partner personnel are no longer using their account for access to Comcast Information Assets
The third party partner must notify Comcast immediately of any security incident on the third party network that may affect Comcast data, access credentials, or Comcast Information Assets
The third party partner shall return all Comcast owned equipment upon termination of the third party connection or reimburse Comcast for the replacement cost of said equipment, the cost of which shall be determined by Comcast
The third party partner shall return or destroy all Comcast proprietary or confidential data that is no longer used to support work currently being performed for Comcast
The third party partner will notify Comcast immediately of any changes to information contained within the Partner Connection Request, including contacts, authorizers, user information, and location information
The third party vendor will provide reasonable security, as determined by software vendor guidance and/or industry consensus standards on computer and network security, to protect any systems connecting to the Comcast network, any systems containing information obtained from the Comcast network, and any systems holding data about Comcast customers, systems, or business operations
All computers accessing Comcast Information Assets will have up to date operating system security patches and application security patches applied
All computers accessing Comcast information Assets will have up to date and properly configured anti-virus software with up to date virus detection signature files. An automated method will be used for keeping anti-virus signature files up to date with the most current release.
All computers accessing Comcast Information Assets and any systems holding information about Comcast customers, systems, or business operations will have controls in place that require the use of strong passwords (at least eight characters, changed regularly, consisting of upper-case and lower-case letters, numbers, and special characters and symbols) to access such Information
CONFIDENTIAL TREATMENT | ||
 | Comcast Cable Communications, Inc. | |
Information Technology | ||
All third party vendor systems accessing Comcast Information Assets will be protected by a firewall, either at the network perimeter or at the local computer, which will be configured to block unsolicited and/or unwanted network connections
Comcast has sole discretion in determining the adequacy and completeness of the security controls required by the third party partner
Any third party partner found in violation of these requirements may have their third party connection suspended
Comcast may terminate the third party partner connection without notice if it is believed that the connection is adversely affecting the security of Comcast or of Comcast Information Assets

Payment Card Industry (PCI)
Data Security Standard
Version 1.1
Release: September, 2006
34
COMCAST CONFIDENTIAL
US.54162848.01
Build and Maintain a Secure Network
Requirement 1: Install and maintain a firewall configuration to protect cardholder data
Requirement 2: | Do not use vendor-supplied defaults for system passwords and other security parameters |
Protect Cardholder Data
Requirement 3: | Protect stored cardholder data |
Requirement 4: | Encrypt transmission of cardholder data across open, public networks |
Maintain a Vulnerability Management Program
Requirement 5: | Use and regularly update anti-virus software |
Requirement 6: | Develop and maintain secure systems and applications |
Implement Strong Access Control Measures
Requirement 7: | Restrict access to cardholder data by business need-to-know |
Requirement 8: | Assign a unique ID to each person with computer access |
Requirement 9: | Restrict physical access to cardholder data |
Regularly Monitor and Test Networks
Requirement 10: | Track and monitor all access to network resources and cardholder data |
Requirement 11: | Regularly test security systems and processes |
Maintain an Information Security Policy
Requirement 12: | Maintain a policy that addresses information security |
Preface
This document describes the 12 Payment Card Industry (PCI) Data Security Standard (DSS) requirements. These PCI DSS requirements are organized in 6 logically related groups, which are “control objectives.”
The following table illustrates commonly used elements of cardholder and sensitive authentication data; whether storage of each data element is permitted or prohibited; and if each data element must be protected. This table is not exhaustive, but is presented to illustrate the different types of requirements that apply to each data element.
PCI DSS requirements are applicable if a Primary Account Number (PAN) is stored, processed, or transmitted. If a PAN is not stored, processed, or transmitted, PCI DSS requirements do not apply.
Data Element | Storage Permitted | Protection Required | PCI DSS Req. 3.4 | |
Cardholder Data | Primary Account Number (PAN) | YES | YES | YES |
Cardholder Name* | YES | YES* | NO | |
Service Code* | YES | YES* | NO | |
Expiration Date* | YES | YES* | NO | |
Sensitive Authentication Data** | Full Magnetic Stripe | NO | N/A | N/A |
CVC2/CVV2/CID | NO | N/A | N/A | |
PIN / PIN Block | NO | N/A | N/A | |
* These data elements must be protected if stored in conjunction with the PAN. This protection must be consistent with PCI DSS requirements for general protection of the cardholder environment. Additionally, other legislation (for example, related to consumer personal data protection, privacy, identity theft, or data security) may require specific protection of this data, or proper disclosure of a company’s practices if consumer-related personal data is being collected during the course of business. PCI DSS; however, does not apply if PANs are not stored, processed, or transmitted.
** Sensitive authentication data must not be stored subsequent to authorization (even if encrypted).
These security requirements apply to all “system components.” System components are defined as any network component, server, or application that is included in or connected to the cardholder data environment. The cardholder data environment is that part of the network that possesses cardholder data or sensitive authentication data. Adequate network segmentation, which isolates systems that store, process, or transmit cardholder data from those that do not, may reduce the scope of the cardholder data environment. Network components include but are not limited to firewalls, switches, routers, wireless access points, network appliances, and other security appliances. Server types include but are not limited to the following: web, database, authentication, mail, proxy, network time protocol (NTP), and domain name server (DNS). Applications include all purchased and custom applications, including internal and external (Internet) applications.
Build and Maintain a Secure Network
Requirement 1: Install and maintain a firewall configuration to protect cardholder data
Firewalls are computer devices that control computer traffic allowed into and out of a company’s network, as well as traffic into more sensitive areas within a company’s internal network. A firewall examines all network traffic and blocks those transmissions that do not meet the specified security criteria.
All systems must be protected from unauthorized access from the Internet, whether entering the system as e-commerce, employees’ Internet-based access through desktop browsers, or employees’ e-mail access. Often, seemingly insignificant paths to and from the Internet can provide unprotected pathways into key systems. Firewalls are a key protection mechanism for any computer network.
1.1 | Establish firewall configuration standards that include the following: |
1.1.1 | A formal process for approving and testing all external network connections and changes to the firewall configuration |
1.1.2 | A current network diagram with all connections to cardholder data, including any wireless networks |
1.1.3 | Requirements for a firewall at each Internet connection and between any demilitarized zone (DMZ) and the internal network zone |
1.1.4 | Description of groups, roles, and responsibilities for logical management of network components |
1.1.5 | Documented list of services and ports necessary for business |
1.1.6 | Justification and documentation for any available protocols besides hypertext transfer protocol (HTTP), and secure sockets layer (SSL), secure shell (SSH), and virtual private network (VPN) |
1.1.7 | Justification and documentation for any risky protocols allowed (for example, file transfer protocol (FTP), which includes reason for use of protocol and security features implemented |
1.1.8 | Quarterly review of firewall and router rule sets |
1.1.9 | Configuration standards for routers. |
1.2 | Build a firewall configuration that denies all traffic from “untrusted” networks and hosts, except for protocols necessary for the cardholder data environment. |
1.3 | Build a firewall configuration that restricts connections between publicly accessible servers and any system component storing cardholder data, including any connections from wireless networks. This firewall configuration should include the following: |
1.3.1 | Restricting inbound Internet traffic to Internet protocol (IP) addresses within the DMZ (ingress filters) |
1.3.2 | Not allowing internal addresses to pass from the Internet into the DMZ |
1.3.3 | Implementing stateful inspection, also known as dynamic packet filtering (that is, only “established” connections are allowed into the network) |
1.3.4 | Placing the database in an internal network zone, segregated from the DMZ |
1.3.5 | Restricting inbound and outbound traffic to that which is necessary for the cardholder data environment |
1.3.6 | Securing and synchronizing router configuration files. For example, running configuration files (for normal functioning of the routers), and start-up configuration files (when machines are re-booted) should have the same secure configuration |
1.3.7 | Denying all other inbound and outbound traffic not specifically allowed |
1.3.8 | Installing perimeter firewalls between any wireless networks and the cardholder data environment, and configuring these firewalls to deny any traffic from the wireless environment or from controlling any traffic (if such traffic is necessary for business purposes) |
1.3.9 | Installing personal firewall software on any mobile and employee-owned computers with direct connectivity to the Internet (for example, laptops used by employees), which are used to access the organization’s network. |
1.4 | Prohibit direct public access between external networks and any system component that stores cardholder data (for example, databases, logs, trace files). |
1.4.1 | Implement a DMZ to filter and screen all traffic and to prohibit direct routes for inbound and outbound Internet traffic |
1.4.2 | Restrict outbound traffic from payment card applications to IP addresses within the DMZ. |
1.5 | Implement IP masquerading to prevent internal addresses from being translated and revealed on the Internet. Use technologies that implement RFC 1918 address space, such as port address translation (XXX) or network address translation (NAT). |
Requirement 2: Do not use vendor-supplied defaults for system passwords and other security parameters
Hackers (external and internal to a company) often use vendor default passwords and other vendor default settings to compromise systems. These passwords and settings are well known in hacker communities and easily determined via public information.
2.1 | Always change vendor-supplied defaults before installing a system on the network (for example, include passwords, simple network management protocol (SNMP) community strings, and elimination of unnecessary accounts). |
2.1.1 | For wireless environments, change wireless vendor defaults, including but not limited to, wired equivalent privacy (WEP) keys, default service set identifier (SSID), passwords, and SNMP community strings. Disable SSID broadcasts. Enable WiFi protected access (WPA and WPA2) technology for encryption and authentication when WPA-capable. |
2.2 | Develop configuration standards for all system components. Assure that these standards address all known security vulnerabilities and are consistent with industry-accepted system hardening standards as defined, for example, by SysAdmin Audit Network Security Network (SANS), National Institute of Standards Technology (NIST), and Center for Internet Security (CIS). |
2.2.1 | Implement only one primary function per server (for example, web servers, database servers, and DNS should be implemented on separate servers) |
2.2.2 | Disable all unnecessary and insecure services and protocols (services and protocols not directly needed to perform the devices’ specified function) |
2.2.3 | Configure system security parameters to prevent misuse |
2.2.4 | Remove all unnecessary functionality, such as scripts, drivers, features, subsystems, file systems, and unnecessary web servers. |
2.3 | Encrypt all non-console administrative access. Use technologies such as SSH, VPN, or SSL/TLS (transport layer security) for web-based management and other non-console administrative access. |
2.4 | Hosting providers must protect each entity’s hosted environment and data. These providers must meet specific requirements as detailed in Appendix A: “PCI DSS Applicability for Hosting Providers.” |
Protect Cardholder Data
Encryption is a critical component of cardholder data protection. If an intruder circumvents other network security controls and gains access to encrypted data, without the proper cryptographic keys, the data is unreadable and unusable to that person. Other effective methods of protecting stored data should be considered as potential risk mitigation opportunities. For example, methods for minimizing risk include not storing cardholder data unless absolutely necessary, truncating cardholder data if full PAN is not needed, and not sending PAN in unencrypted e-mails.
3.1 | Keep cardholder data storage to a minimum. Develop a data retention and disposal policy. Limit storage amount and retention time to that which is required for business, legal, and/or regulatory purposes, as documented in the data retention policy. |
3.2 | Do not store sensitive authentication data subsequent to authorization (even if encrypted). |
Sensitive authentication data includes the data as cited in the following Requirements 3.2.1 through 3.2.3:
3.2.1 | Do not store the full contents of any track from the magnetic stripe (that is on the back of a card, in a chip or elsewhere). This data is alternatively called full track, track, track 1, track 2, and magnetic stripe data |
In the normal course of business, the following data elements from the magnetic stripe may need to be retained: the accountholder’s name, primary account number (PAN), expiration date, and service code. To minimize risk, store only those data elements needed for business. NEVER store the card verification code or value or PIN verification value data elements. Note: See “Glossary” for additional information.
3.2.2 | Do not store the card-validation code or value (three-digit or four-digit number printed on the front or back of a payment card) used to verify card-not-present transactions |
Note: See “Glossary” for additional information.
3.2.3 | Do not store the personal identification number (PIN) or the encrypted PIN block. |
3.3 | Mask PAN when displayed (the first six and last four digits are the maximum number of digits to be displayed). |
Note: This requirement does not apply to employees and other parties with a specific need to see the full PAN; nor does the requirement supersede stricter requirements in place for displays of cardholder data (for example, for point of sale [POS] receipts).
3.4 | Render PAN, at minimum, unreadable anywhere it is stored (including data on portable digital media, backup media, in logs, and data received from or stored by wireless networks) by using any of the following approaches: |
• | Strong one-way hash functions (hashed indexes) |
• | Truncation |
• | Index tokens and pads (pads must be securely stored) |
• | Strong cryptography with associated key management processes and procedures. |
The MINIMUM account information that must be rendered unreadable is the PAN.
If for some reason, a company is unable to encrypt cardholder data, refer to Appendix B: “Compensating Controls for Encryption of Stored Data.”
3.4.1 | If disk encryption is used (rather than file- or column-level database encryption), logical access must be managed independently of native operating system access control mechanisms (for example, by not using local system or Active Directory accounts). Decryption keys must not be tied to user accounts. |
3.5 | Protect encryption keys used for encryption of cardholder data against both disclosure and misuse. |
3.5.1 | Restrict access to keys to the fewest number of custodians necessary |
3.5.2 | Store keys securely in the fewest possible locations and forms. |
3.6 | Fully document and implement all key management processes and procedures for keys used for encryption of cardholder data, including the following: |
3.6.1 | Generation of strong keys |
3.6.2 | Secure key distribution |
3.6.3 | Secure key storage |
3.6.4 | Periodic changing of keys |
• | As deemed necessary and recommended by the associated application (for example, re-keying); preferably automatically |
• | At least annually. |
3.6.5 | Destruction of old keys |
3.6.6 | Split knowledge and establishment of dual control of keys (so that it requires two or three people, each knowing only their part of the key, to reconstruct the whole key) |
3.6.7 | Prevention of unauthorized substitution of keys |
3.6.8 | Replacement of known or suspected compromised keys |
3.6.9 | Revocation of old or invalid keys |
3.6.10 | Requirement for key custodians to sign a form stating that they understand and accept their key-custodian responsibilities. |
Sensitive information must be encrypted during transmission over networks that are easy and common for a hacker to intercept, modify, and divert data while in transit.
4.1 | Use strong cryptography and security protocols such as secure sockets layer (SSL) / transport layer security (TLS) and Internet protocol security (IPSEC) to safeguard sensitive cardholder data during transmission over open, public networks. |
Examples of open, public networks that are in scope of the PCI DSS are the Internet, WiFi (IEEE 802.11x), global system for mobile communications (GSM), and general packet radio service (GPRS).
4.1.1 | For wireless networks transmitting cardholder data, encrypt the transmissions by using WiFi protected access (WPA or WPA2) technology, IPSEC VPN, or SSL/TLS. Never rely exclusively on wired equivalent privacy (WEP) to protect confidentiality and access to a wireless LAN. If WEP is used, do the following: |
• | Use with a minimum 104-bit encryption key and 24 bit-initialization value |
• | Use ONLY in conjunction with WiFi protected access (WPA or WPA2) technology, VPN, or SSL/TLS |
• | Rotate shared WEP keys quarterly (or automatically if the technology permits) |
• | Rotate shared WEP keys whenever there are changes in personnel with access to keys |
• | Restrict access based on media access code (MAC) address. |
4.2 | Never send unencrypted PANs by e-mail. |
Maintain a Vulnerability Management Program
Requirement 5: Use and regularly update anti-virus software or programs
Many vulnerabilities and malicious viruses enter the network via employees’ e-mail activities. Anti-virus software must be used on all systems commonly affected by viruses to protect systems from malicious software.
5.1 | Deploy anti-virus software on all systems commonly affected by viruses (particularly personal computers and servers) |
Note: Systems commonly affected by viruses typically do not include UNIX-based operating systems or mainframes.
5.1.1 | Ensure that anti-virus programs are capable of detecting, removing, and protecting against other forms of malicious software, including spyware and adware. |
5.2 | Ensure that all anti-virus mechanisms are current, actively running, and capable of generating audit logs. |
Unscrupulous individuals use security vulnerabilities to gain privileged access to systems. Many of these vulnerabilities are fixed by vendor-provided security patches. All systems must have the most recently released, appropriate software patches to protect against exploitation by employees, external hackers, and viruses. Note: Appropriate software patches are those patches that have been evaluated and tested sufficiently to determine that the patches do not conflict with existing security configurations. For in-house developed applications, numerous vulnerabilities can be avoided by using standard system development processes and secure coding techniques.
6.1 | Ensure that all system components and software have the latest vendor-supplied security patches installed. Install relevant security patches within one month of release. |
6.2 | Establish a process to identify newly discovered security vulnerabilities (for example, subscribe to alert services freely available on the Internet). Update standards to address new vulnerability issues. |
6.3 | Develop software applications based on industry best practices and incorporate information security throughout the software development life cycle. |
6.3.1 | Testing of all security patches and system and software configuration changes before deployment |
6.3.2 | Separate development, test, and production environments |
6.3.3 | Separation of duties between development, test, and production environments |
6.3.4 | Production data (live PANs) are not used for testing or development |
6.3.5 | Removal of test data and accounts before production systems become active |
6.3.6 | Removal of custom application accounts, usernames, and passwords before applications become active or are released to customers |
6.3.7 | Review of custom code prior to release to production or customers in order to identify any potential coding vulnerability. |
6.4 | Follow change control procedures for all system and software configuration changes. The procedures must include the following: |
6.4.1 | Documentation of impact |
6.4.2 | Management sign-off by appropriate parties |
6.4.3 | Testing of operational functionality |
6.4.4 | Back-out procedures |
6.5 | Develop all web applications based on secure coding guidelines such as the Open Web Application Security Project guidelines. Review custom application code to identify coding vulnerabilities. Cover prevention of common coding vulnerabilities in software development processes, to include the following: |
6.5.1 | Unvalidated input |
6.5.2 | Broken access control (for example, malicious use of user IDs) |
6.5.3 | Broken authentication and session management (use of account credentials and session cookies) |
6.5.4 | Cross-site scripting (XSS) attacks |
6.5.5 | Buffer overflows |
6.5.6 | Injection flaws (for example, structured query language (SQL) injection) |
6.5.7 | Improper error handling |
6.5.8 | Insecure storage |
6.5.9 | Denial of service |
6.5.10 | Insecure configuration management |
6.6 | Ensure that all web-facing applications are protected against known attacks by applying either of the following methods: |
• | Having all custom application code reviewed for common vulnerabilities by an organization that specializes in application security |
• | Installing an application layer firewall in front of web-facing applications. |
Note: This method is considered a best practice until June 30, 2008, after which it becomes a requirement.
Implement Strong Access Control Measures
Requirement 7: Restrict access to cardholder data by business need-to-know
This requirement ensures critical data can only be accessed by authorized personnel.
7.1 | Limit access to computing resources and cardholder information only to those individuals whose job requires such access. |
7.2 | Establish a mechanism for systems with multiple users that restricts access based on a user’s need to know and is set to “deny all” unless specifically allowed. |
Requirement 8: Assign a unique ID to each person with computer access
Assigning a unique identification (ID) to each person with access ensures that actions taken on critical data and systems are performed by, and can be traced to, known and authorized users.
8.1 | Identify all users with a unique user name before allowing them to access system components or cardholder data. |
8.2 | In addition to assigning a unique ID, employ at least one of the following methods to authenticate all users: |
• | Password |
• | Token devices (e.g., SecureID, certificates, or public key) |
• | Biometrics. |
8.3 | Implement two-factor authentication for remote access to the network by employees, administrators, and third parties. Use technologies such as remote authentication and dial-in service (RADIUS) or terminal access controller access control system (TACACS) with tokens; or VPN (based on SSL/TLS or IPSEC) with individual certificates. |
8.4 | Encrypt all passwords during transmission and storage on all system components. |
8.5 | Ensure proper user authentication and password management for non-consumer users and administrators on all system components as follows: |
8.5.1 | Control addition, deletion, and modification of user IDs, credentials, and other identifier objects |
8.5.2 | Verify user identity before performing password resets |
8.5.3 | Set first-time passwords to a unique value for each user and change immediately after the first use |
8.5.4 | Immediately revoke access for any terminated users |
8.5.5 | Remove inactive user accounts at least every 90 days |
8.5.6 | Enable accounts used by vendors for remote maintenance only during the time period needed |
8.5.7 | Communicate password procedures and policies to all users who have access to cardholder data |
8.5.8 | Do not use group, shared, or generic accounts and passwords |
8.5.9 | Change user passwords at least every 90 days |
8.5.10 | Require a minimum password length of at least seven characters |
8.5.11 | Use passwords containing both numeric and alphabetic characters |
8.5.12 | Do not allow an individual to submit a new password that is the same as any of the last four passwords he or she has used |
8.5.13 | Limit repeated access attempts by locking out the user ID after not more than six attempts |
8.5.14 | Set the lockout duration to thirty minutes or until administrator enables the user ID |
8.5.15 | If a session has been idle for more than 15 minutes, require the user to re-enter the password to re-activate the terminal |
8.5.16 | Authenticate all access to any database containing cardholder data. This includes access by applications, administrators, and all other users |
Requirement 9: Restrict physical access to cardholder data
Any physical access to data or systems that house cardholder data provides the opportunity for individuals to access devices or data and to remove systems or hardcopies, and should be appropriately restricted.
9.1 | Use appropriate facility entry controls to limit and monitor physical access to systems that store, process, or transmit cardholder data. |
9.1.1 | Use cameras to monitor sensitive areas. Audit collected data and correlate with other entries. Store for at least three months, unless otherwise restricted by law |
9.1.2 | Restrict physical access to publicly accessible network jacks |
9.1.3 | Restrict physical access to wireless access points, gateways, and handheld devices. |
9.2 | Develop procedures to help all personnel easily distinguish between employees and visitors, especially in areas where cardholder data is accessible. |
“Employee” refers to full-time and part-time employees, temporary employees and personnel, and consultants who are “resident” on the entity’s site. A “visitor” is defined as a vendor, guest of an employee, service personnel, or anyone who needs to enter the facility for a short duration, usually not more than one day.
9.3 | Make sure all visitors are handled as follows: |
9.3.1 | Authorized before entering areas where cardholder data is processed or maintained |
9.3.2 | Given a physical token (for example, a badge or access device) that expires and that identifies the visitors as non-employees |
9.3.3 | Asked to surrender the physical token before leaving the facility or at the date of expiration. |
9.4 | Use a visitor log to maintain a physical audit trail of visitor activity. Retain this log for a minimum of three months, unless otherwise restricted by law. |
9.5 | Store media back-ups in a secure location, preferably in an off-site facility, such as an alternate or backup site, or a commercial storage facility. |
9.6 | Physically secure all paper and electronic media (including computers, electronic media, networking and communications hardware, telecommunication lines, paper receipts, paper reports, and faxes) that contain cardholder data. |
9.7 | Maintain strict control over the internal or external distribution of any kind of media that contains cardholder data including the following: |
9.7.1 | Classify the media so it can be identified as confidential |
9.7.2 | Send the media by secured courier or other delivery method that can be accurately tracked. |
9.8 | Ensure management approves any and all media that is moved from a secured area (especially when media is distributed to individuals). |
9.9 | Maintain strict control over the storage and accessibility of media that contains cardholder data. |
9.9.1 | Properly inventory all media and make sure it is securely stored. |
9.10 | Destroy media containing cardholder data when it is no longer needed for business or legal reasons as follows: |
9.10.1 | Cross-cut shred, incinerate, or pulp hardcopy materials |
9.10.2 | Purge, degauss, shred, or otherwise destroy electronic media so that cardholder data cannot be reconstructed. |
Regularly Monitor and Test Networks
Requirement 10: Track and monitor all access to network resources and cardholder data
Logging mechanisms and the ability to track user activities are critical. The presence of logs in all environments allows thorough tracking and analysis if something does go wrong. Determining the cause of a compromise is very difficult without system activity logs.
10.1 | Establish a process for linking all access to system components (especially access done with administrative privileges such as root) to each individual user. |
10.2 | Implement automated audit trails for all system components to reconstruct the following events: |
10.2.1 | All individual user accesses to cardholder data |
10.2.2 | All actions taken by any individual with root or administrative privileges |
10.2.3 | Access to all audit trails |
10.2.4 | Invalid logical access attempts |
10.2 5 | Use of identification and authentication mechanisms |
10.2.6 | Initialization of the audit logs |
10.2.7 | Creation and deletion of system-level objects. |
10.3 | Record at least the following audit trail entries for all system components for each event: |
10.3.1 | User identification |
10.3.2 | Type of event |
10.3.3 | Date and time |
10.3.4 | Success or failure indication |
10.3.5 | Origination of event |
10.3.6 | Identity or name of affected data, system component, or resource. |
10.4 | Synchronize all critical system clocks and times. |
10.5 | Secure audit trails so they cannot be altered. |
10.5.1 | Limit viewing of audit trails to those with a job-related need |
10.5.2 | Protect audit trail files from unauthorized modifications |
10.5.3 | Promptly back-up audit trail files to a centralized log server or media that is difficult to alter |
10.5.4 | Copy logs for wireless networks onto a log server on the internal LAN. |
10.5.5 | Use file integrity monitoring and change detection software on logs to ensure that existing log data cannot be changed without generating alerts (although new data being added should not cause an alert). |
10.6 | Review logs for all system components at least daily. Log reviews must include those servers that perform security functions like intrusion detection system (IDS) and authentication, authorization, and accounting protocol (AAA) servers (for example, RADIUS). |
Note: Log harvesting, parsing, and alerting tools may be used to achieve compliance with Requirement 10.6.
10.7 | Retain audit trail history for at least one year, with a minimum of three months online availability. |
Requirement 11: Regularly test security systems and processes
Vulnerabilities are being discovered continually by hackers and researchers, and being introduced by new software. Systems, processes, and custom software should be tested frequently to ensure security is maintained over time and with any changes in software.
11.1 | Test security controls, limitations, network connections, and restrictions annually to assure the ability to adequately identify and to stop any unauthorized access attempts. Use a wireless analyzer at least quarterly to identify all wireless devices in use. |
11.2 | Run internal and external network vulnerability scans at least quarterly and after any significant change in the network (such as new system component installations, changes in network topology, firewall rule modifications, product upgrades). |
Note: Quarterly external vulnerability scans must be performed by a scan vendor qualified by the payment card industry. Scans conducted after network changes may be performed by the company’s internal staff.
11.3 | Perform penetration testing at least once a year and after any significant infrastructure or application upgrade or modification (such as an operating system upgrade, a sub-network added to the environment, or a web server added to the environment). These penetration tests must include the following: |
11.3.1 | Network-layer penetration tests |
11.3.2 | Application-layer penetration tests. |
11.4 | Use network intrusion detection systems, host-based intrusion detection systems, and intrusion prevention systems to monitor all network traffic and alert personnel to suspected compromises. Keep all intrusion detection and prevention engines up-to-date. |
11.5 | Deploy file integrity monitoring software to alert personnel to unauthorized modification of critical system or content files; and configure the software to perform critical file comparisons at least weekly. |
Critical files are not necessarily only those containing cardholder data. For file integrity monitoring purposes, critical files are usually those that do not regularly change, but the modification of which could indicate a system compromise or risk of compromise. File integrity monitoring products usually come pre-configured with critical files for the related
operating system. Other critical files, such as those for custom applications, must be evaluated and defined by the entity (that is the merchant or service provider).
Maintain an Information Security Policy
Requirement 12: Maintain a policy that addresses information security for employees and contractors
A strong security policy sets the security tone for the whole company and informs employees what is expected of them. All employees should be aware of the sensitivity of data and their responsibilities for protecting it.
12.1 | Establish, publish, maintain, and disseminate a security policy that accomplishes the following: |
12.1.1 | Addresses all requirements in this specification |
12.1.2 | Includes an annual process that identifies threats and vulnerabilities, and results in a formal risk assessment |
12.1.3 | Includes a review at least once a year and updates when the environment changes. |
12.2 | Develop daily operational security procedures that are consistent with requirements in this specification (for example, user account maintenance procedures, and log review procedures). |
12.3 | Develop usage policies for critical employee-facing technologies (such as modems and wireless) to define proper use of these technologies for all employees and contractors. Ensure these usage policies require the following: |
12.3.1 | Explicit management approval |
12.3.2 | Authentication for use of the technology |
12.3.3 | List of all such devices and personnel with access |
12.3.4 | Labeling of devices with owner, contact information, and purpose |
12.3.5 | Acceptable uses of the technologies |
12.3.6 | Acceptable network locations for the technologies |
12.3.7 | List of company-approved products |
12.3.8 | Automatic disconnect of modem sessions after a specific period of inactivity |
12.3.9 | Activation of modems for vendors only when needed by vendors, with immediate deactivation after use |
12.3.10 When accessing cardholder data remotely via modem, prohibition of storage of cardholder data onto local hard drives, floppy disks, or other external media. Prohibition of cut-and-paste and print functions during remote access.
12.4 | Ensure that the security policy and procedures clearly define information security responsibilities for all employees and contractors. |
12.5 | Assign to an individual or team the following information security management responsibilities: |
12.5.1 | Establish, document, and distribute security policies and procedures |
12.5.2 | Monitor and analyze security alerts and information, and distribute to appropriate personnel |
12.5.3 | Establish, document, and distribute security incident response and escalation procedures to ensure timely and effective handling of all situations |
12.5.4 | Administer user accounts, including additions, deletions, and modifications |
12.5.5 | Monitor and control all access to data. |
12.6 | Implement a formal security awareness program to make all employees aware of the importance of cardholder data security. |
12.6.1 | Educate employees upon hire and at least annually (for example, by letters, posters, memos, meetings, and promotions) |
12.6.2 | Require employees to acknowledge in writing that they have read and understood the company’s security policy and procedures. |
12.7 | Screen potential employees to minimize the risk of attacks from internal sources. |
For those employees such as store cashiers who only have access to one card number at a time when facilitating a transaction, this requirement is a recommendation only.
12.8 | If cardholder data is shared with service providers, then contractually the following is required: |
12.8.1 | Service providers must adhere to the PCI DSS requirements |
12.8.2 | Agreement that includes an acknowledgement that the service provider is responsible for the security of cardholder data the provider possesses. |
12.9 | Implement an incident response plan. Be prepared to respond immediately to a system breach. |
12.9.1 | Create the incident response plan to be implemented in the event of system compromise. Ensure the plan addresses, at a minimum, specific incident response procedures, business recovery and continuity procedures, data backup processes, roles and responsibilities, and communication and contact strategies (for example, informing the Acquirers and credit card associations) |
12.9.2 | Test the plan at least annually |
12.9.3 | Designate specific personnel to be available on a 24/7 basis to respond to alerts |
12.9.4 | Provide appropriate training to staff with security breach response responsibilities |
12.9.5 | Include alerts from intrusion detection, intrusion prevention, and file integrity monitoring systems |
12.9.6 | Develop process to modify and evolve the incident response plan according to lessons learned and to incorporate industry developments. |
12.10 | All processors and service providers must maintain and implement policies and procedures to manage connected entities, to include the following: |
12.10.1. Maintain a list of connected entities
12.10.2. Ensure proper due diligence is conducted prior to connecting an entity
12.10.3. Ensure the entity is PCI DSS compliant
12.10.4. Connect and disconnect entities by following an established process.
Appendix A: PCI DSS Applicability for Hosting Providers
Requirement A.1: Hosting providers protect cardholder data environment
As referenced in Requirement 12.8, all service providers with access to cardholder data (including hosting providers) must adhere to the PCI DSS. In addition, Requirement 2.4 states that hosting providers must protect each entity’s hosted environment and data. Therefore, hosting providers must give special consideration to the following:
A.1 | Protect each entity’s (that is merchant, service provider, or other entity) hosted environment and data, as in A.1.1 through A.1.4: |
A.1.1 | Ensure that each entity only has access to own cardholder data environment |
X.0.0 | Xxxxxxxx each entity’s access and privileges to own cardholder data environment only |
A.1.3 | Ensure logging and audit trails are enabled and unique to each entity’s cardholder data environment and consistent with PCI DSS Requirement 10 |
A.1.4 | Enable processes to provide for timely forensic investigation in the event of a compromise to any hosted merchant or service provider. |
A hosting provider must fulfill these requirements as well as all other relevant sections of the PCI DSS. Note: Even though a hosting provider may meet these requirements, the compliance of the entity that uses the hosting provider is not necessarily guaranteed. Each entity must comply with the PCI DSS and validate compliance as applicable.
Appendix B: Compensating Controls
Compensating Controls – General
Compensating controls may be considered for most PCI DSS requirements when an entity cannot meet a technical specification of a requirement, but has sufficiently mitigated the associated risk. See the PCI DSS Glossary for the full definition of compensating controls.
The effectiveness of a compensating control is dependent on the specifics of the environment in which the control is implemented, the surrounding security controls, and the configuration of the control. Companies should be aware that a particular compensating control will not be effective in all environments. Each compensating control must be thoroughly evaluated after implementation to ensure effectiveness.
The following guidance provides compensating controls when companies are unable to render cardholder data unreadable per requirement 3.4.
For companies unable to render cardholder data unreadable (for example, by encryption) due to technical constraints or business limitations, compensating controls may be considered. Only companies that have undertaken a risk analysis and have legitimate technological or documented business constraints can consider the use of compensating controls to achieve compliance.
Companies that consider compensating controls for rendering cardholder data unreadable must understand the risk to the data posed by maintaining readable cardholder data. Generally, the controls must provide additional protection to mitigate any additional risk posed by maintaining readable cardholder data. The controls considered must be in addition to controls required in the PCI DSS, and must satisfy the “Compensating Controls” definition in the PCI DSS Glossary. Compensating controls may consist of either a device or combination of devices, applications, and controls that meet all of the following conditions:
1. Provide additional segmentation/abstraction (for example, at the network-layer)
2. | Provide ability to restrict access to cardholder data or databases based on the following criteria: |
• | IP address/Mac address |
• | Application/service |
• | User accounts/groups |
• | Data type (packet filtering) |
3. Restrict logical access to the database
• | Control logical access to the database independent of Active Directory or Lightweight Directory Access Protocol (LDAP) |
4. Prevent/detect common application or database attacks (for example, SQL injection).
Access Control Policy
The scope of this security policy includes all application and systems and/or equipment that are owned or operated by Comcast Corporation and its subsidiaries (“Comcast”)*, whether the information is on electronic media, printed as hardcopy, or transmitted over public/private networks. At its discretion, the Comcast Business Technology Alignment Council reserves the right to modify the scope of the policy at any point in time.
Information security requires the participation of and support from all employees and persons with access to company systems and information. It is the responsibility of every employee, (referred to herein as “Users”) to help ensure that all information and data are kept secure and available for use by authorized Users.
This policy applies to all Comcast users who have access to, support, administer, manage, or maintain Comcast information systems.
This policy will be reviewed on a yearly basis by the Risk Management Working Group. All revisions will be presented to the Business Technology Alignment Council for approval.
Comcast’s applications and systems are essential to its success. Therefore, access to all applications and systems will be granted in a controlled manner driven by business requirements subject to the approval of the designated application or system owner and the zone security group. Employees will be explicitly granted access to information or systems. There is no implicit right of access.
The process to manage access to information must include:
• | Proper documentation, management and responsibilities of all users; |
• | Development and implementation of access control mechanisms, both technical and non-technical, to protect unauthorized access to applications and systems; |
• | Proper monitoring of access and use of applications and systems; and, |
• | Proper controls for authorized remote access to information. |
Controls must be developed, implemented, monitored and maintained to create user accountability and to prevent any compromise of the confidentiality, availability and integrity of applications and systems.
Employee Acceptable Use Agreement
Authentication Policy
Employee Remote Access and Teleworking Policy
*Application of this Policy to certain content, commerce, and sports-related subsidiaries of Comcast Corporation will be made on a case by case basis.
Users must read and acknowledge the Acceptable Use Policy as part of their acknowledgment of the Employee Handbook prior to being granted access to Comcast applications and systems.
Users must obtain permission from the designated Application or System owner and demonstrate a justifiable business case to access data. Authorization must be documented and authorization forms must be retained for historical purposes. Application and System Owners will grant access on a need to know basis, as required by job functions. Access requestors must not approve their own access. Applicable legislation and/or regulatory restrictions must be considered when granting access to data or systems.
Before receiving access to systems, Comcast employees and contractors must undergo background checks performed by Human Resources or the contracting company. Background checks may include criminal checks and verification of employment records. At the discretion of Human Resources, certain Comcast positions may require more or less extensive background checks.
User access must be modeled based upon job description, duties, or function. The use of roles provides consistent and efficient administration of access rights. Application and System owners must understand the security controls and privileges for the systems they are responsible for in order to make and recommend appropriate controls.
When users change roles within the company, their access must be immediately changed to reflect the new job responsibilities; new access must be added and old access that is no longer required must be removed.
(Formerly):
Access for users who change roles or transfer to other areas of the business must be immediately given the access required for the new role. Access that is no longer required for the new role must be removed or disabled immediately.
When access is granted, users are responsible for all system activity under their unique account. Users have the responsibility to protect their account by creating and maintaining passwords compliant with the Authentication Policy sections 2.4 and 2.5. In addition, users are responsible for maintaining the confidentiality of their unique ID and password by not sharing it with any other party.
The following warning banner must be displayed before users connect, locally or remotely, to Comcast’s internal computer networks:
“This system is solely for the use of authorized Comcast employees and contractors. Comcast reserves the right at any time to monitor usage of this system to ensure compliance with the Comcast Access Control and Acceptable Use Policies, all applicable Comcast policies that apply to electronic communications and all applicable laws. Your use of this system constitutes your acceptance of and agreement to all applicable Comcast electronic communications policies, your consent to monitoring by Comcast, and your express
agreement to use this system in compliance with all applicable laws. Any unauthorized use of or access to this system may result in a revocation of your user privileges, other disciplinary action up to and including termination of employment or contract, or referrals to law enforcement officials including the provision of evidence of any unauthorized use or access to law enforcement.”
All Windows-based workstations and servers must be configured with updated anti-virus software. User must never attempt to disable anti-virus software.
Designated Application and System owners must re-evaluate the privileges granted to Comcast users periodically to ascertain that the access is still commensurate with the user’s job responsibilities.
Type of System | Review |
Subscriber Billing | Monthly |
All other Financials | Quarterly |
All other Information Systems | At least Annually |
User IDs found to be invalid must be disabled and investigated immediately by Management.
Non-employee User IDs and access privileges, including vendor and business partner IDs, must be re-evaluated every six months. User IDs found to be invalid must be disabled and investigated immediately.
Designated Application and System owners are responsible for monitoring certain user activity on applications and systems by periodically reviewing application and system logs.
At a minimum, application and system owners must configure and review logs that describe the following:
• | User authentication failure and success |
• | User privilege change failure and success |
• | User audit log access failure and success |
Access logs must be retained for a period of 12 months.
2.11 Temporary Access Control Privileges
If privileged access must be temporarily granted to a user, the privilege must be removed at a pre-set expiration time. All temporary access must be approved in writing by the appropriate application or system owner.
2.12 Terminated Employees and Contractors
User IDs of terminated or resigned users must be disabled from all information systems immediately upon notification from Human Resources and/or the responsible business unit or department. Every week, Human Resources must send a summary email notification of all new departures to all relevant system administration teams.
3.1 Unauthorized Testing of Comcast Applications and Systems
Comcast employees with full-time responsibility for information security and Internal Audit are chartered by the Audit Committee, Zone Owner or the Risk Management Working Group to perform information security tests to ensure the company is adequately protecting applications and systems. All other users must not test, or attempt to compromise internal controls unless specifically approved in advance and in writing by Divisional IT Management.
Users must not exploit vulnerabilities or deficiencies in information systems security to damage systems or information. Users must not attempt to access assets beyond those they have been authorized to obtain or modify other users’ level of access, unless specifically approved in advance and in writing by the Divisional IT Management. Vulnerabilities found by users must be promptly reported to Divisional IT Management.
3.2 Modification and Testing of Production Data
System privileges allowing the modification of Comcast production information must be restricted to production applications. Privileges must be established such that users are not able to modify production data in an unrestricted manner. Users may only modify production data in predefined ways that preserve or enhance its integrity. Users must be permitted to modify production data only when employing a controlled process approved by the application or system owner.
3.3 Remote Access Methods
Users must use only remote access solutions approved and authorized by the appropriate Zone Owner and meeting the requirements set by the Employee Remote Access and Teleworking Policy.
Acronym / Term | Definition |
Access Control | Refers to mechanisms and policies that restrict access to computer or network devices. These mechanisms prevent the unauthorized use of applications and systems. |
Applications and Systems | Systems including workstations, operating systems, network, application and web application software, Personal Digital Assistants, cable telecommunications equipment and network software. Also included are any other technology platforms that contribute to and support business operations. |
Enterprise Zone and Service Delivery Zone | The Enterprise Zone includes all Comcast-owned and operated networks, with the exception of the Service Delivery Zone. The Service Delivery Zone includes the customer-facing network managed by National Engineering & Technical Operations. |
Production Data | Customer, employee and other business information stored in or processed by Information Assets. |
Users | All Comcast employees, contractors and consultants. |
Zone Owner | Comcast Senior Executives responsible for oversight of the Service Delivery and Enterprise Zones. Xxxx Xxxxxx is the Owner of the Service Delivery Zone and Xxxxxx Xxxx is the Owner of the Enterprise Zone. |
Zone Security | The dedicated security professionals in each zone, whose management representatives report to the Zone Owners. |
Authentication Policy
The scope of this security policy includes authentication to all applications and systems and/or equipment that are owned or operated by Comcast Corporation and its subsidiaries (“Comcast”)*. At its discretion, the Comcast Business Technology Alignment Council reserves the right to modify the scope of the policy at any point in time.
Applications and systems in the scope of this policy include all operating systems, application and web application software, Personal Digital Assistants, cable telecommunications equipment and network software.
Information security requires the participation of and support from all employees and persons with access to company systems and information. It is the responsibility of every employee, consultant, temporary employee, and contractor of Comcast (collectively known as “users”) to help ensure that all information and data are kept secure and available.
1.1 Audience
This policy is mandatory for all Comcast users who have access to, support, administer, manage, or maintain Cable applications and systems. Subscribers are not subject to this policy.
1.2 Policy Maintenance
This policy will be reviewed on a yearly basis by the Risk Management Working Group. All revisions will be presented to the Business Technology Alignment Council for approval.
1.3 Policy Statement
Authentication is the verification of a user’s identity that is attempting to access an application or system. Authentication also refers to the verification of the origin of a transmitted message. Authentication establishes audit trails and accountability controls for access granted or transactions processed. Authentication methods use up to four factors generally summarized as “what you know,” “what you have,” “what you are,” and “what you do.”
All Comcast applications or systems require at least single factor authentication. Zone Owners may require that specific applications or systems require two-factor authentication due to risk.
Comcast’s applications and systems are essential to its success. Therefore, management must consistently enforce authentication to all applications and systems to protect the confidentiality, integrity, and availability of applications and systems and the accountability of users’ actions.
1.4 Related Policies and Documents
Change Management Policy
Systems Development Policy
*Application of this Policy to certain content, commerce, and sports-related subsidiaries of Comcast Corporation will be made on a case by case basis.
CONFIDENTIAL TREATMENT

2.1 Unique, Individual Accounts
All users must have unique, individual accounts to establish accountability for all actions on Comcast applications or systems. Shared user accounts are prohibited
2.2 Default Accounts and Passwords
All default user passwords must be changed at the first login. All default application, database, and system passwords must be changed before going into production. If this is not possible, the passwords must be changed at the first login.
Default user accounts that are provided with purchased software must be disabled or the account names changed upon installation. Default accounts must be used only for designated maintenance tasks and must not be employed for daily use.
2.3 Test Accounts
All test or development User IDs and passwords must be removed prior to implementation into the production environment.
2.4 Minimum Authentication Requirements
The creation and maintenance of application and system passwords must meet minimum security requirements. These minimum authentication requirements include the following:
• | All passwords must have at least eight (8) characters. |
• | Words that would be found in a dictionary must not be included in the password. |
• | All passwords must be composed of upper and lower case alphabetic and non-alphabetic characters. Account names and passwords must not include the user’s personally identifiable information, such as the user ID, birth date, social security number or anniversary date. |
• | Password history is a security setting that determines the number of unique passwords that have to be associated with a user account before the old password can be reused. This setting must be a minimum of eight (8) passwords. |
• | Passwords must have a minimum age of three (3) days so that users can not repeatedly change their password back to an old value. |
• | Applications and systems must require users to change their passwords at least every sixty (60) days. |
• | The number of consecutive attempts to enter an incorrect password must be limited to five (5) unsuccessful attempts, after which the User ID must automatically suspend for one day. |
• | Inactive or dormant User IDs must be disabled after 30 days of inactivity for all accounts not associated with active employees. Inactive accounts must then be deleted after an additional 180 days of inactivity. |
• | All passwords must be promptly changed if they are suspected of being disclosed, or are known to have been disclosed, to unauthorized parties. |
2.5 Security Requirements for Administrator-Level Authentication
Administrator-level authentication to applications and systems requires the following controls in addition to the minimum requirements in section 2.4.
• | Special characters must be included in the password. |
• | Privileged account passwords must be changed quarterly (four times per year). Where a higher level of assurance is required and manageable, Zone Security may require more frequent privileged password changes. |
CONFIDENTIAL TREATMENT

• | A formal change request must be created each time a generic administrator account is used (examples: built-in Administrator account in Windows, root in UNIX). The change request must meet the requirements in the Change Management Policy. |
• | If the use of a built-in administrator account is discovered and can not be explained, the use must be investigated and the password must be changed. |
• | All passwords of privileged accounts must be promptly changed upon the termination, resignation, or transfer of any privileged user who knew the passwords to those accounts. |
2.6 Service Accounts
Service accounts, such as those used by processes and inter-application authentication, must meet the following minimum requirements:
• | All passwords must have at least eight (8) characters. |
• | Words that would be found in a dictionary must not be included in the password. |
• | All passwords must be composed of upper and lower case alphabetic, non-alphabetic and special characters. |
• | All passwords must be promptly changed upon the termination, resignation, or transfer of any privileged user who knew the passwords to those accounts. |
• | If the use of a service account is discovered and can not be explained, the use must be investigated and the password must be changed. |
Service accounts must have the least privilege possible to perform their single designated task. For example, where possible, service accounts must not have administrator privileges or interactive logon shells. This reduces the chance that a service account will be used in an unauthorized manner.
2.7 Password Storage, Transmission and Display
System administrators are responsible for ensuring that passwords are protected during storage, transit and use. This includes, but is not limited to:
• | Passwords must not be written down and left in a place where unauthorized persons might discover them. |
• | Passwords must not be stored in readable form in batch files, automatic login scripts, software macros, terminal function keys, in computers without access control, or in other locations where unauthorized persons might discover them. |
• | Applications and systems must be designed, tested, and controlled to prevent the retrieval of stored passwords. Any unauthorized method utilized to reveal a password is prohibited. |
• | Passwords must be encrypted when held in storage and encrypted when transmitted electronically over untrusted networks. |
• | The display of passwords must be masked, suppressed, or otherwise obscured so that unauthorized parties will not be able to observe them as they are entered or stored. |
2.8 Additional Authentication
Zone Owners may choose to require a higher standard for authenticating to operating systems and applications. This could include, but is not limited to, higher security account policy and/or two-factor authentication to access sensitive applications or systems.
2.9 Remote Access Authentication
Zone Security may require that remote access methods over untrusted networks to applications and systems that require a high level of assurance must use two-factor authentication. For example, a remote user must authenticate with his or her user-ID and password, and another authentication method such as a token-based card.
Remote interactive sessions that are not active for 30 minutes must be automatically terminated. For those systems that cannot automatically terminate connections, password protected screen savers or terminal locks must be activated. Users must not attempt to circumvent the use of these controls.
2.10 Applications and Systems that Cannot Enforce Standards
If an application or system, due to technical reasons, cannot adhere to the minimum standards, the system administrator must enforce them manually. For example, if password aging is not possible, the system administrator must age passwords manually in accordance with section 2.4.
Definitions
Acronym / Term | Definition |
Applications and systems | Systems including workstations, operating systems, network, application and web application software, Personal Digital Assistants, cable telecommunications equipment and network software. Also included are any other technology platforms that contribute to and support business operations. |
Enterprise Zone and Service Delivery Zone | The Enterprise Zone includes all Comcast-owned and operated networks, with the exception of the Service Delivery Zone. The Service Delivery Zone includes the customer-facing network managed by National Engineering & Technical Operations, |
Privileged Users | Any User with access greater than normal user-level access. This may include, but is not limited to, access to HR or Financial records, employee or subscriber data, or access to system tools and administrator-level accounts. |
Service Accounts | Service accounts are used exclusively by systems and applications. Service accounts are never used by normal users to log into a system or application. It is critical that these accounts have complex passwords that are known to as few employees as possible, because it is difficult to manage changes to these accounts and password changes are infrequent. It is also critical that service accounts have the least privilege possible so that if they are compromised, they will be of little use to an unauthorized user. Examples of service accounts include database connection strings and accounts used to start processes on Windows and UNIX systems. |
System Administrator | An operating system, application, database or other specialty technology administrator. |
Two-Factor Authentication | Security-enhanced authentication that requires two forms of individual authentication. This will usually be a User ID and password combination AND a soft token, certificate, or hard token (like RSA SecurelD). The principle behind two-factor authentication requires users to use something that they know (password), and something that they have (token, thumb print) to authenticate. |
Untrusted Network | A network or connection where the complete circuit is not owned and operated by Comcast. The Internet and Comcast subscriber networks are considered Untrusted networks. |
Users | All Comcast employees, contractors and consultants. |
Zone Owner | Comcast Senior Executives responsible for oversight of the Service Delivery and Enterprise Zones. Xxxx Xxxxxx is the Owner of the Service Delivery Zone and Xxxx Xxxxxx is the Owner of the Enterprise Zone. |
Zone Security | The dedicated security professionals in each zone, whose management representatives report to the Zone Owners. |
Change Management Policy
The scope of this change management policy defines the requirements for enacting changes on applications and systems that can affect programs, system software, hardware, or any other aspect of the information-processing environment owned or operated by Comcast Corporation and its subsidiaries (“Comcast”)*. At its discretion, the Comcast Business Technology Alignment Council reserves the right to modify the scope of the policy at any time.
Systems in the scope of this policy include all production applications and systems maintained by Comcast or external vendors, production network and telecommunications infrastructure, production databases, production file and print servers, and the application of patches to employee workstation operating systems.
Excluded from the Change Management Policy are tasks that are considered part of the normal duties and functions of data center personnel. Some of these duties that are not applicable include, but are not limited to, daily tape backup operations, daily operation of call center telephony switches, and the creation or deletion of application and system IDs.
Information security requires the participation of and support from all employees and persons with access to company systems and information. It is the responsibility of every employee, consultant, temporary employee, and contractor of Comcast (collectively known as “users”) to help ensure that all information and data are kept secure and available.
1.1 Audience
This policy is mandatory for all Comcast users who are involved in the request, approval, programming, testing and/or implementation of information system software or hardware changes.
1.2 Policy Maintenance
This policy will be reviewed on a yearly basis by the Risk Management Working Group, a subcommittee of the Comcast Business Technology Alignment Council. All revisions will be presented to the Business Technology Alignment Council for approval.
1.3 Policy Statement
Comcast’s applications and systems are essential to its success. Therefore, changes to production-level applications and systems must be applied in a controlled manner so that the confidentiality, availability, and integrity of applications and systems are not compromised.
Changes to applications and systems must be approved and successfully tested prior to implementation into production. Application and System Owners are responsible for reviewing and approving requests for changes. In each zone, the Zone Owner is responsible for assigning additional change management approval roles.
Only authorized users are permitted to make changes to applications or systems once the proper approval has been received. Based upon a formal or informal risk assessment, Zone Owners may require that certain applications, systems or types of changes also require the approval of the applicable zone security group prior to being implemented in production.
*Application of this Policy to certain content, commerce, and sports-related subsidiaries of Comcast Corporation will be made on a case by case basis.
Systems Development Policy
2.1 Types of Changes
The change requester, with review of the application or system owner, is responsible for determining the type of Change Request to submit. There are three types of changes:
• | Emergency - When a system is down due to a failure or outage, “emergency” changes focus on service restoration. Section 3.0 describes the special requirements for emergency changes. |
• | Urgent - An “urgent” change is appropriate when an immediate business need must be met, that if not performed, may cause system down time or impact operational integrity. Urgent changes also include outside/third party scheduling beyond the normal control of Comcast. Examples include construction projects or circuit provisioning. |
• | Routine - A “routine” change introduces new services and capabilities or brings changes to existing services and capabilities, but does not meet the criteria defined above for emergency or urgent. Most changes are routine and are made in the course of normal operations. |
Changes required as part of a project to deploy new applications or systems into production must be requested as either Urgent or Routine. Since the changes do not involve applications or systems that are already in production, the change must not be requested as an Emergency.
2.2 Change Request Forms
Application and System owners must adequately document change requests, using a change request form approved by the applicable Zone Owner. The change request form must contain the following information:
• | Type of change |
• | Basic information about the change |
• | Business justification for the change |
• | How many users and/or subscribers are impacted |
• | Description of what will be done |
• | Nature of defect (if applicable) |
• | Description of testing performed |
• | Back-out procedures |
• | Systems impacted |
• | Notification distribution list |
• | Business and IT contact(s) |
2.3 Approval of Change Requests
Change requests must be approved by the application or system owner and other individuals appointed by the Zone Owner. A change requestor must never approve his or her own request. Business owners may delegate approval of changes as they deem appropriate.
2.4 Integrity of Change Requests
Automated or manual processes must protect documentation of change requests so that the scope and description of the change can not be modified after approval and prior to execution.
2.5 Communication of Changes
The Zone Owner is responsible for ensuring that application and system owners communicate changes to affected user groups and the owners of impacted applications and systems.
2.6 Documentation Retention Requirements
All change request forms, testing results, and evidence of approval must be retained for a period of one year for audit and compliance purposes, but can be retained for a longer period if the application or system owner feels the documentation is critical to the ongoing support of the application or system. Emergency request forms must also be documented in an incident or trouble log with evidence that the application or system owner approved the change either prior or subsequent to the emergency change.
3.1 Authorization of Emergency Changes
Emergency changes may only be requested to respond to an immediate threat to the confidentiality, integrity or availability of applications or systems. Emergency changes may be enacted only with the written or verbal approval of the application or system owner or their designated approver. The changes must be clearly and completely documented subsequent to the emergency using an Emergency Change Request form.
3.2 Emergency Change Request Forms
Emergency Change Request Forms must contain the same information as a standard change request form, but must also include the reason for the emergency and a description of remediation actions (including the permanent resolution). Emergency Change Request Forms must be completed within 48 hours of the changes. The Zone Owner may require Emergency Change Request Forms to be completed in 24 hours, depending on the sensitivity of the environment.
3.3 Temporary Accounts and Privileges
When a user requires a new account or elevated privileges to perform emergency changes, the account and/or privileges must be removed upon completion of the emergency session. New accounts and temporary access must be documented in the change request form. Also, if a privileged super-user password is provided to a change enactor during implementation of a change, that password must be changed upon completion of the change.
4.1 System Architecture
Separate and controlled environments must exist for development, testing, and production applications and systems. If separate development and testing environments are not feasible, a combined test and development environment may be used.
4.2 Access to Production Systems and Code
User privileges must be established such that users are not able to modify production data in an unrestricted manner. Users must have controlled access to production data through application interfaces and only through pre-defined processes.
When Comcast is in control of application source code through internal development or purchase, each application must have only one repository for production source code. Developers will retrieve the source code from this repository when modifying programs. All modifications to production source code must follow strict version control as described in section of the Systems Development Policy.
4.3 Segregation of Duties
Developers’ access privileges over production libraries must be restricted so they can only copy source code from production into their development area. Developers must not be permitted to move compiled programs directly into production.
5.1 Requirement for Testing
All changes to applications and systems must be successfully tested prior to implementation into production. Testing procedures must be properly documented in change request forms. If problems are noted during the testing process, the tester must document the problem and notify the application or system owner.
5.2 User Acceptance Testing
All major upgrades, modifications, and new systems must be tested by the appropriate users prior to installation of the software in production. User acceptance testing plans must include tests of all major functions, processes, and interfacing systems. Testing plans must be documented or referenced on the change request forms.
5.3 Test Data
Testing must occur in a development or controlled test environment with test data. Test data may include anonymized subscriber data or pre-designed test datasets. If subscriber data must be used because no test data exists, and if the anonymization of the data is cost prohibitive or otherwise infeasible, the application and/or systems used for testing must adhere to the same security policies and standards for production applications and systems. This includes, but is not limited to, password policies, encryption, operating system builds, third party connection agreements and policies, privacy policies, and network security.
Definitions
Acronym / Term | Definition |
Applications and Systems | For change management purposes, this definition includes financial applications, cable telecommunications equipment production application, web, database, domain and directory servers, firewalls, routers and network switches. Also included are any other technology platforms that contribute to and support business operations. |
Application or System Owner | The business owner of a Comcast application or network resource. |
Change | A Change is defined as the introduction of new products or services and capabilities or any modification made to existing systems, technologies, or services. |
Change Management | The process of requesting, testing, approving, scheduling, and communicating changes in an efficient and controlled manner to ensure there are no adverse effects to the business. |
Development environment | A controlled system environment where programmers may make changes prior to moving their final changes to the Test environment. |
Enterprise Zone and Service Delivery Zone | The Enterprise Zone includes all Comcast-owned and operated networks, with the exception of the Service Delivery Zone. The Service Delivery Zone includes the customer-facing network managed by National Engineering & Technical Operations. |
Production environment | The production environment consists of all hardware, software, middleware, and electrical circuitry associated with maintaining a technology, application, or system providing services to the corporation and our customers. |
Source code | Programming code that must be compiled to execute. Initially, a programmer writes a program in a particular programming language like C++ or Java. This form of the program is called the source program, or more generically, source code. To execute the program, however, the programmer must translate it into machine language, the language that the computer understands. |
Test / Pre-production environment | The area where programmers and users can execute a change to identify differences between expected and actual results. |
Users | All Comcast employees, contractors and consultants. |
Zone Owner | Comcast Senior Executives responsible for oversight of the Service Delivery and Enterprise Zones. Xxxx Xxxxxx is the Owner of the Service Delivery Zone and Xxxx Xxxxxx is the Owner of the Enterprise Zone. |
Zone Security | The dedicated security professionals in each zone, whose management representatives report to the Zone Owners. |
Employee Personal Information Security Policy
The scope of this security policy applies to the collection, storage, transmission, use, and deletion of Employee Personal Information (as defined below) obtained from employees in electronic and hard copy media by Comcast Corporation and/or its subsidiaries (“Comcast”)*. Ali Comcast employees and vendors or contractors working on behalf of Comcast must comply with this policy, in addition to applicable laws. At its discretion, the Comcast Business Technology Alignment Council reserves the right to modify the scope of the policy at any point in time.
Information security requires the participation of and support from all employees and persons with access to company applications and systems (as defined below) and information. It is the responsibility of every User (as defined below) to help ensure that all information and data are kept confidential, secure and only accessible to those individuals that have a need to know such information.
This policy applies to all Users and others, who have access to, administer, manage, or maintain Employee Personal Information.
This policy will be reviewed on a yearly basis by the Risk Management Subcommittee. All revisions will be presented to the Business Technology Alignment Council for review and approval.
Comcast records, stores and uses Employee Personal information, including sharing some of that information with third parties, in order to operate its business and meet its obligations as an employer. As is the case with all sensitive, valuable business data, Comcast will exercise reasonable care in protecting Employee Personal Information from unauthorized access and use both internally and externally.
A key principle of this policy is that only authorized Users may have access to Employee Personal Information and those Users must adhere to the general requirements of the Acceptable Use Policy. Potential Users of Employee Personnel Information must have a need to know to become authorized Users and have access to Employee Personal Information. Application and System owners must implement the minimum controls described in this policy to protect Employee Personal Information. This policy specifically prohibits any unauthorized or unlawful disclosure of Employee Personal Information and is designed to ensure, to the extent practicable, the confidentiality of Employee Personal Information. However, certain Employee Personal Information will be provided when either required by law or when requested by third parties for verification purposes. Furthermore, any violations of this policy will subject the employee to discipline, up to and including termination of employment. Nothing in this policy prevents an employee from disclosing his/her own personal information or engaging in any other conduct that is protected by law.
*Application of this Policy to certain content, commerce, and sports-related subsidiaries of Comcast Corporation will be made on a case by case basis.
Access Control Policy
Acceptable Use Policy
Partner Connection Request Form
Records Retention and Information Management Policy
Systems Development Policy
Third Party Connections Policy
Comcast determines the purposes for which data is to be collected, to ensure that our data collection supports reasonable business requirements, and does not use Employee Personal Information for purposes that are incompatible with those purposes.
Comcast provides certain employees with reasonable access to their Employee Personal Information and the ability to review and correct it, as applicable. It is the employee’s responsibility to ensure that all of his or her Employee Personal Information is accurate, complete and current.
While Employee Personal Information is in Comcast’s control, application and system owners are responsible for maintaining compliance with this and other applicable Comcast policies as they pertain to Employee Personal Information and data security generally.
Access to Employee Personal Information Systems must be managed according to the Access Control Policy.
Comcast does not transfer or provide access to Employee Personal Information to third parties unless those third parties agree to give the data the equivalent level of protection that Comcast provides, or another suitable level of protection as determined by Comcast. Third parties that store, transmit or process Employee Personal Information must sign a Partner Connection Request (PCR) document. The business owner of the third party relationship is responsible for keeping the PCR up to date and for meeting the other requirements in the Third Party Connections Policy.
3.4 Monitoring Access to Employee Personal information
When Users access Employee Personal Information Systems, access logs may record their actions. Application and system owners are responsible for reviewing access logs related to Employee Personal Information.
3.5 Development and Acquisition of Employee Personal Information Systems
Systems built, modified or acquired by Comcast for use in processing or storing Employee Personal Information must follow the requirements in the Systems Development Policy.
4.1 Compliance with Records Retention Policy
Comcast adheres to the requirements described in the Records Retention and Information Management Policy when storing and disposing of employee personal information, in addition to the minimum requirements described below.
4.2 Physical Security of Hard Copy Employee Personal Information
Hard copy Employee Personal Information must be secured in locked containers such as file cabinets whenever not in use. Keys must be available only to authorized Users
4.3 Backups of Employee Personal Information
Copies of Employee Personal Information must be backed up to tape or other removable storage media for disaster recovery purposes. Back-up media containing Employee Personal Information must be stored in a locked Comcast or other Comcast-authorized location only accessible by authorized Users.
4.4 Employee Personal Information Disposal
When Employee Personal Information is no longer required by the business and is not subject to any data retention policy, law or regulation, it must be disposed using a paper shredder, incinerator, or pulping. Alternately, a contracted service provider that applies one of these methods may be approved by Divisional IT management or the applicable authorized department head.
When electronic Employee Personal Information is no longer required by the business and is not subject to any data retention policy, law or regulation, it must be irretrievably deleted from systems, databases, e-mail servers, PC hard drives, and other storage devices. When the electronic media itself requires disposal, it must be degaussed, shred or incinerated.
Definitions
Acronym / Term | Definition |
Applications and systems | Systems including workstations, operating systems, network, application and web application software, personal digital assistants, cable telecommunications equipment and network software. Also included are any other technology platforms that contribute to and support business operations. |
Employee Personal Information | This data includes, but is not limited to, an employee’s name, home address, complete social security number, performance appraisals and disciplinary reports, and may include birth date and salary information when actually associated with other personally identifiable information such as the employee’s name. Also included are documents and information gathered during the pre-employment process including background reports, driver’s history, education and job verification, or any other information deemed personal in nature. |
Employee Personal Information Systems | Applications and Systems including databases that contain or process Employee Personal Information. |
Users | Ail Comcast employees, contractors and vendors who have access to Employee Personal Information. |
Zone Owner | Comcast Senior Executives responsible for oversight of the Service Delivery and Enterprise Zones. Xxxx Xxxxxx is the Owner of the Service Delivery Zone and Xxxx Xxxxxx is the Owner of the Enterprise Zone. |
Zone Security | The dedicated security professionals in each zone, whose management representatives report to the Zone Owners. |
The scope of this security policy includes electronic Payment Card Holder (hereafter referred to as “card holder”) data either stored by, or transmitted through applications and systems owned by Comcast Corporation and its subsidiaries (“Comcast”)*. This policy also includes hard copy card holder data in Comcast’s control. At its discretion, the Comcast Technology Council reserves the right to modify the scope of the policy at any point in time.
Information security requires the participation of and support from all employees and persons with access to company systems and information. It is the responsibility of every employee, consultant, temporary employee, and contractor of Comcast (collectively known as “users”) to help ensure that all information and data are kept secure and available.
1.1 Audience
This policy applies to all Comcast users who have access to, administer, manage, or maintain subscriber card holder data.
1.2 Policy Maintenance
This policy will be reviewed on a yearly basis by the Risk Management Subcommittee. All revisions will be presented to the Technology Council for approval.
*Application of this Policy to certain content, commerce, and sports-related subsidiaries of Comcast Corporation will be made on a case by case basis.
Among other methods, Comcast collects payments from its subscribers using payment cards and is reliant on the payment card industry’s infrastructure to ensure the timely receipt of these payments. In order to remain in good standing with subscribers and business partners, Comcast must comply with the Payment Card Industry (PCI) Data Security Standard for card holder data management. Therefore, Application and System Owners must take special care to understand these requirements to protect card holder data. Key principles of this policy include the following:
1. | Only select users must have access to card holder data and those users must adhere to the requirements of the Acceptable Use Policy. |
2. | Application and System Owners must implement the minimum controls described in this policy to protect card holder data. |
3. | Local operating units that handle payment card information must implement daily operational security procedures that meet requirements in the PCI Data Security Standard. |
Acceptable Use Policy
Access Control Policy
Incident Response Policy
Payment Card Industry (PCI) Data Security Standard
Records Retention and Information Management Policy
Remote Access and Teleworking Policy
Systems Development Policy
While card holder data is in Comcast’s control, application and system owners are responsible for maintaining compliance with this and other Comcast policies as they pertain to card holder data. Comcast must also comply with applicable state, local and federal regulations and laws, contractual and franchise agreements. Corporate Accounting and Corporate Legal must approve all third party agreements.
Systems built, modified or acquired by Comcast for use in processing or storing card holder data must follow the requirements in the Payment Card Industry Data Security Standard and the Systems Development Policy,
2.3 Monitoring Access to Card Holder Data
When users access payment card systems, access logs must record their access to card holder data. Application and system owners are responsible for reviewing access logs related to card holder data a minimum of once a month.
2.4 Incident Reporting
Incidents may include, but are not limited to, the loss of media containing card holder data or suspicion of unauthorized access to card holder data. These incidents must be reported according to the Incident Response Policy.
2.5 Payment Card Industry-Approved Compliance Auditing
Comcast must undergo an annual compliance audit. The audit must assess and report on compliance with the Payment Card Industry Data Security Standard. Comcast can elect to either self-certify or arrange for a third party audit performed by one of the PCI-approved auditors.
2.6 Masked Payment Card Numbers
Card holder data must be masked when displayed by systems and printed on paper. For verification purposes, it is acceptable for the last four digits of a payment card to be displayed. If a business need requires that a whole number must be displayed, application and system owners must approve and document the need.
2.7 Time-outs for Idle Sessions
Systems that store, process or allow read or write access to card holder data must time out or lock out after fifteen minutes of user inactivity. A Windows-based system may rely on the built-in Windows time-out to meet this requirement.
2.8 Remote Access to Card Holder Data
Remote access to card holder data, through switched IP networks or through dial-up connections, must be managed according to the Remote Access and Teleworking Policy. Cut-and-paste functionality must be disabled over dial-up connections so that card holder data can not be transferred or saved on to a remote system.
2.9 Anti-virus
Refer to section 2.8 of the Access Control policy.
2.10 Security Testing
Comcast must use an approved third party to perform quarterly vulnerability scans and periodic penetration tests of Internet-facing resources.
3.1 Physical Security of Hard Copy Card Holder Data
Hard copy card holder data must be secured in locked containers whenever not in use. Keys must be available only to authorized users. Hard copy card holder data must be labeled “Sensitive non-public” or “Confidential.”
3.2 Encryption of Card Holder Data
Electronic card holder data must not be stored or transmitted in human-readable form. When at rest or in transit, card holder data must be encrypted using a Zone Security-approved encryption method.
User passwords for accounts with access to card holder data must be encrypted both in transit and at rest.
3.3 Recording Card Holder Data
Card holder data must only be recorded in the minimum number of places to support required business purposes. Card holder data may only exist on approved applications and systems that are dedicated to payment card processing, storage or transmittal. Employees must not record card holder data in other places, like in local electronic fifes (Microsoft Excel, Word, e-mails) or in paper notes.
Phone system and application recordings, including automated voice and customer representative calls, must be configured not to record and store payment card information.
3.4 Electronic Copies and Backups of Card Holder Data
Electronic copies and backups of card holder data, specifically payment card numbers, must be encrypted using Zone Security-approved methods if backed up to tape or other removable storage media. Electronic copies and backup media containing card holder data must be clearly labeled as “Sensitive non-public” or “Confidential” and stored in a locked location only accessible by authorized users.
Backups must be stored in a secure off-site facility, which may be Comcast-owned or contracted to a third party, Backups must be transported using a secure and tracked courier.
3.5 Card Holder Data Disposal
Disposal times for card holder data must meet contractual requirements and the Records Retention and Information Management Policy.
When hard copy card holder data is no longer required by the business, it must be disposed using a cross-shredder, incinerator, or pulping. When electronic card holder data is no longer required by the business, it must be disposed using disk-wiping software that erases and writes over the data at least three times.
Card holder data must be automatically removed or destroyed when it exceeds its business use or its life span as defined in the Records Retention and Information Management Policy. Alternately, it is acceptable to use a quarterly manual process to remove card holder data that exceeds its retention schedule.
When the electronic media itself requires disposal, it must be degaussed, shred or incinerated. Alternately, a contracted service provider that applies one of these hard copy and/or electronic disposal methods may be approved by Divisional IT management.
4.1 Responsibility for Other Customer Payment information
Comcast has the responsibility to protect other personally-identifiable customer payment information while in Comcast’s custody. This includes, but is not limited to, bank account numbers, Electronic Funds Transmission (EFT) data, home addresses and contact information.
4.2 Applicability of Payment Card Protection Policy and Standards
Application arid system owners are responsible for maintaining compliance with sections 2.1, 2.3, 2.4, 3.1, 3.3 and 3.5 of this policy to protect the other customer payment card information described in section 4.1.
Definitions
Acronym / Term | Definition |
Access Control | Refers to mechanisms and policies that restrict access to computer or network devices. These mechanisms prevent the unauthorized use of information assets. |
Applications and systems | Systems including workstations, operating systems, network, application and web application software, Personal Digital Assistants, cable telecommunications equipment and network software. Also included are any other technology platforms that contribute to and support business operations. Applications and systems owners are responsible for third party content, while it is under Comcast’s control. Application and system owners have authority over how third party content is managed internally. |
Card Holder Data | Any personally identifiable data associated with a cardholder. This could be an account number, expiration date, name, address or social security number. |
Card Processing Environment | All systems used to process, transmit, and store cardholder data. (e.g. servers, desktops, routers, switches, firewalls, wireless devices). |
Comcast’s control | Comcast has custody of card holder data when the data is in Comcast’s control. Control begins upon receipt of the data, whether via telephone, electronic or hard copy transmissions. Control ends when Comcast disposes of the information. |
Payment Card Industry | A coalition of major credit and payment card providers. |
Payment Card Industry Data Security Standard | An industry best practices guide for managing card holder data. |
Payment Card Systems | Applications and systems including subscriber programs and databases that contain or process card holder data. |
Users | All Comcast employees, contractors and consultants. |
Zone Owner | Comcast Senior Executives responsible for oversight of the Service Delivery and Enterprise Zones. Xxxx Xxxxxx is the Owner of the Service Delivery Zone and Xxxxxx Xxxx is the Owner of the Enterprise Zone. |
Zone Security | The dedicated security professionals in each zone, whose management representatives report to the Zone Owners. |
Software Compliance Policy
The scope of this policy defines the requirements for managing compliance with third party software license agreements, for all software licensed by Comcast Corporation and its subsidiaries (“Comcast”)*. At its discretion, the Comcast Business Technology Alignment Council reserves the right to modify the scope of this policy at any time. This policy does not apply to Comcast owned software programs.
1.1 Audience
This policy is mandatory for all Comcast employees and contractors. Comcast subscribers are not subject to this policy.
1.2 Policy Maintenance
This policy will be reviewed on a yearly basis by the Risk Management Working Group. The Business Technology Alignment Council will approve all revisions.
1.3 Policy Statement
Comcast licenses software from third parties for specific business purposes. As a licensee of third party software, Comcast must comply with the requirements set forth in all third party software license agreements. Non-compliance with these agreements may result in significant legal liability, loss of reputation, and financial loss. Only fully licensed software that is approved by divisional IT management may be used on Comcast applications and systems.
Since compliance with policies is of vital importance to Comcast’s success, Internal Audit is authorized to conduct assessments at their discretion with any scope they deem appropriate to measure Comcast’s compliance with software license agreements. All Comcast users are responsible for their own compliance with software license requirements.
1.4 Related Policies and Documents
Acceptable Use Policy
2.1 User Responsibilities
Users authorized to purchase software licenses on behalf of Comcast must comply with third party licensing agreements. These licensing agreements often contain specific restrictions (e.g., number of copies allowed to be installed, the number of computers the software can be installed on, or the number of concurrent users of the software allowed at any one time). Users must not install software in a manner inconsistent with the licensing agreement.
Contractors who install Comcast licensed software on their non-Comcast equipment are responsible for removing it at the end of the contract. If a contractor chooses to keep the software, he or she must purchase or license it.
All software licenses must be reviewed and approved by Comcast Legal in advance of being signed.
*Application of this Policy to certain content, commerce, and sports-related subsidiaries of Comcast Corporation will be made on a case by case basis.
Users must comply with the requirements in section 3.4 of the Acceptable Use Policy
There are many freeware and shareware programs available on the Internet and other locations that perform a wide variety of tasks. Some of these programs are ineffective, inefficient, not secure, or actually include malicious code to harm a computer or network. Because of this, only shareware and freeware approved by the Zone Owner and Divisional IT management may be installed on Comcast applications and systems, in accordance with section 2.5 of the Acceptable Use Policy. In addition, open source licenses must be reviewed by Corporate Legal.
All users of licensed software or shareware must strictly abide by applicable copyright laws and restrictions.
2.5 Software License Compliance Monitoring
Regional IT Management or Corporate Department Heads must monitor software usage on workstations and servers and determine whether Comcast is in compliance with its licensing agreements. Regional IT Management and Corporate Department Heads may use automated or manual processes and may work with Purchasing to monitor software compliance. When software is in violation of a license agreement, it must be immediately removed or purchased in accordance with Comcast purchasing procedures. Violations of software licenses may result in disciplinary action, up to and including termination.
Definitions
Acronym / Term | Definition |
Applications and systems | Systems including workstations, operating systems, network, application and web application software, Personal Digital Assistants, cable telecommunications equipment and network software. Also included are any other technology platforms that contribute to and support business operations. |
Department Heads | A list of senior management executives with responsibility for major areas of the business. For an updated list of Department Heads, contact the Human Resources department. |
Enterprise Zone and Service Delivery Zone | The Enterprise Zone includes all Comcast-owned and operated networks, with the exception of the Service Delivery Zone. The Service Delivery Zone includes the customer-facing network managed by National Engineering & Technical Operations. |
Freeware | Copyrighted software given away for free by the author. Although it is available for free, the author usually retains the copyright, which means that you cannot do anything with it that is not licensed by the author. Usually, the author allows people to use the software, but not sell it, for example. |
Licensed Software | Software for which Comcast has a right to use the program, but does not hold ownership rights in the program. Comcast must follow strict requirements and install the software only once for each license bought. |
Shareware | Software distributed on the basis of an honor system. Most shareware is delivered free of charge, but the author usually requests that you pay a small fee if you like the program and use it regularly. By sending the small fee, you become registered with the producer so that you can receive service assistance and updates. Shareware is usually copyrighted by the author. |
Users | All Comcast employees, contractors and consultants. |
Zone Owner | Comcast Senior Executives responsible for oversight of the Service Delivery and Enterprise Zones. Xxxx Xxxxxx is the Owner of the Service Delivery Zone and Xxxx Xxxxxx is the Owner of the Enterprise Zone. |
Zone Security | The dedicated security professionals in each zone, whose management representatives report to the Zone Owners. |
77
COMCAST CONFIDENTIAL
US.54162848.01
CONFIDENTIAL TREATMENT
EXHIBIT C
Agent On-Net SIP to Outsourcers
Conformance Notation
Throughout this document, the words that are used to define the significance of particular requirement are capitalized. These words are:
MUST | This word, or the adjective REQUIRED means that the item is an absolute requirement of this specification. The word MANDATORY may be used in lieu of MUST in certain circumstances. |
MUST NOT | This phrase means that the item is an absolute prohibition of this specification. |
SHOULD | This word or the adjective RECOMMENDED means that there may exist valid reasons in particular circumstances to ignore this item, but the full implications should be understood and the case carefully weighed before choosing a different course. |
SHOULD NOT | This phrase means that there may exist valid reasons in particular circumstances when the behavior is acceptable or even useful, but the full implications should be understood and the case carefully weighed before implementing any behavior with this label. |
MAY | This word or the adjective OPTIONAL means that this item is truly optional. One vendor may choose to include the item because a particular marketplace requires it or because it enhances the product, for example; another vendor may omit the same item. |
This section contains the definitions of terms that have specific meaning when used within this document.
E.164 | An International Telecommunication Union Telecommunication Standardization Sector recommendation which defines the international public telecommunication numbering plan used in the PSTN and some other data networks. It also defines the format of telephone numbers. E.164 numbers can have a maximum of 15 digits and are usually written with a + prefix. |
Abbreviations and Acronyms
This section contains the abbreviations and acronyms used within this document.
Acronym | Definition |
AC | Alternating Current |
ACK | Acknowledgement |
ACL | Access Control List |
APOP | Application Point of Presence |
AR | Aggregation Router |
CA | Call Agent |
CALEA | Communications Assistance for Law Enforcement Act |
CBONE | Comcast Backbone |
CCC | Call Content Channel |
CDC | Call Data Channel |
CDR | Charging Data Record |
CDV | Comcast Digital Voice |
CLASS | Custom Local Area Signaling Services |
CLI | Command Line Interface |
78
COMCAST CONFIDENTIAL
US.54162848.01
CONFIDENTIAL TREATMENT
CM | Communication Manager |
CMS | Call Management Server |
CMTS | Cable Modem Termination System |
CODEC | Compression/Decompression |
CRAN | Converged Regional Area Network |
DC | Direct Current |
DDDS | Dynamic Delegation Discovery System |
DDOS | Distributed Denial of Service |
DF | Delivery Function |
DIFFSERV | Differentiated Services |
DNS | Domain Name System |
DOS | Denial of Service |
DQOS | Dynamic Quality of Service |
DSCP | Differentiated Services Code Point |
TCS | TITAN Core Server |
TES | TITAN Edge Server |
E-SBC | Enterprise SBC |
EMS | Element Management System |
FQDN | Fully Qualified Domain Name |
GUI | Graphical User Interface |
HE | Head End |
HFC | Hybrid Fiber Coax |
HTTPS | Hyper Text Transfer Protocol Secure |
IBONE | Internet Backbone |
ICMP | Internet Control Message Protocol |
IETF | Internet Engineering Task Force |
IP | Internet Protocol (version 4) |
IPv4 | Internet Protocol version 4 |
Ipv6 | Internet Protocol version 6 |
IP Agent | software application with telephony features for agents in a contact center |
IXC | Inter-Exchange Carrier |
JR | Xxxxxx Rimmel |
MD5 | Message Digest 5 |
MG | Media Gateway |
MGC | Media Gateway Controller |
MTA | Multimedia Terminal Adapter |
NAPTR | Naming Authority Pointer |
NCS | Network Call Signaling |
NDC | National Data Center |
NE | Network Element |
NOC | Network Operations Center |
NPA-NXX | Numbering Plan Area – Numeric Numbering Exchange |
OAM&P | Operations, Administration, Maintenance, & Provisioning |
One-X Agent | Desktop software application built specifically to meet the needs of contact center agents |
OS | Operating System |
CONFIDENTIAL TREATMENT
OTN | Optical Terminal Node |
PAID | Privacy Asserted Identification |
POP | Point of Presence |
PSTN | Public Switched Telephone Network |
QoS | Quality of Service |
RADIUS | Remote Authentication Dial In User |
RCA | Root Cause Analysis |
REGEXP | Regular Expression |
RF | Radio Frequency |
RFC | Request for Comments |
RKS | Record Keeping Server |
RTCP | Real-Time Control Protocol |
RTP | Real-Time Protocol |
RU | Rack Unit |
SBC | Session Border Controller |
SDP | Session Description Protocol |
SFTP | Secure File Transfer Protocol |
SIP | Session Initiation Protocol |
SM | Session Manager |
SNMP | Simple Network Management Protocol |
SOAP | Simple Object Access Protocol |
SRP | SIP Route Proxy |
SRV | Service Record |
SS7 | System Signaling 7 |
SSH | Secure Shell |
SYSLOG | System Logging |
TCP | Transmission Control Protocol |
TITAN | Transactional IP Telephony Addressing & Numbering |
TLS | Transport Layer Security |
TN | Telephone Number |
TSI | Telecommunications Savings Initiative |
UDP | User Datagram Protocol |
URI | Uniform Resource Identifier |
VoIP | Voice Over Internet Protocol |
WSDL | Web Services |
WSV | Whole Sale Voice |
XML | Extensible Markup Language |
ARCHITECTURE
The CDV Toll Free On-Net has several projects within it. This “phase” will use the infrastructure that was put in place for the CDV Toll Free Calls On Net Phase 1, 2 and 3 call routing, as well as additional infrastructure required to make off-net connections to outsourcers.
This project is intended to provide an extension of Comcast’s internal PBX network to include outside parties (outsourcers). This could include, but not be limited to, configurations where the outsourcer “agents” will appear no differently than Comcast employees which are also configured as agents off the same PBX’s. As an option, Comcast
may choose, at least initially, to utilize a trunk-side connection to facilitate connectivity between Comcast PBX’s and the outsourcer PBX’s.
High Level Requirements
All requirements are referenced in Section 3.
This section presents the functional architecture of the connectivity required to outsourcers.
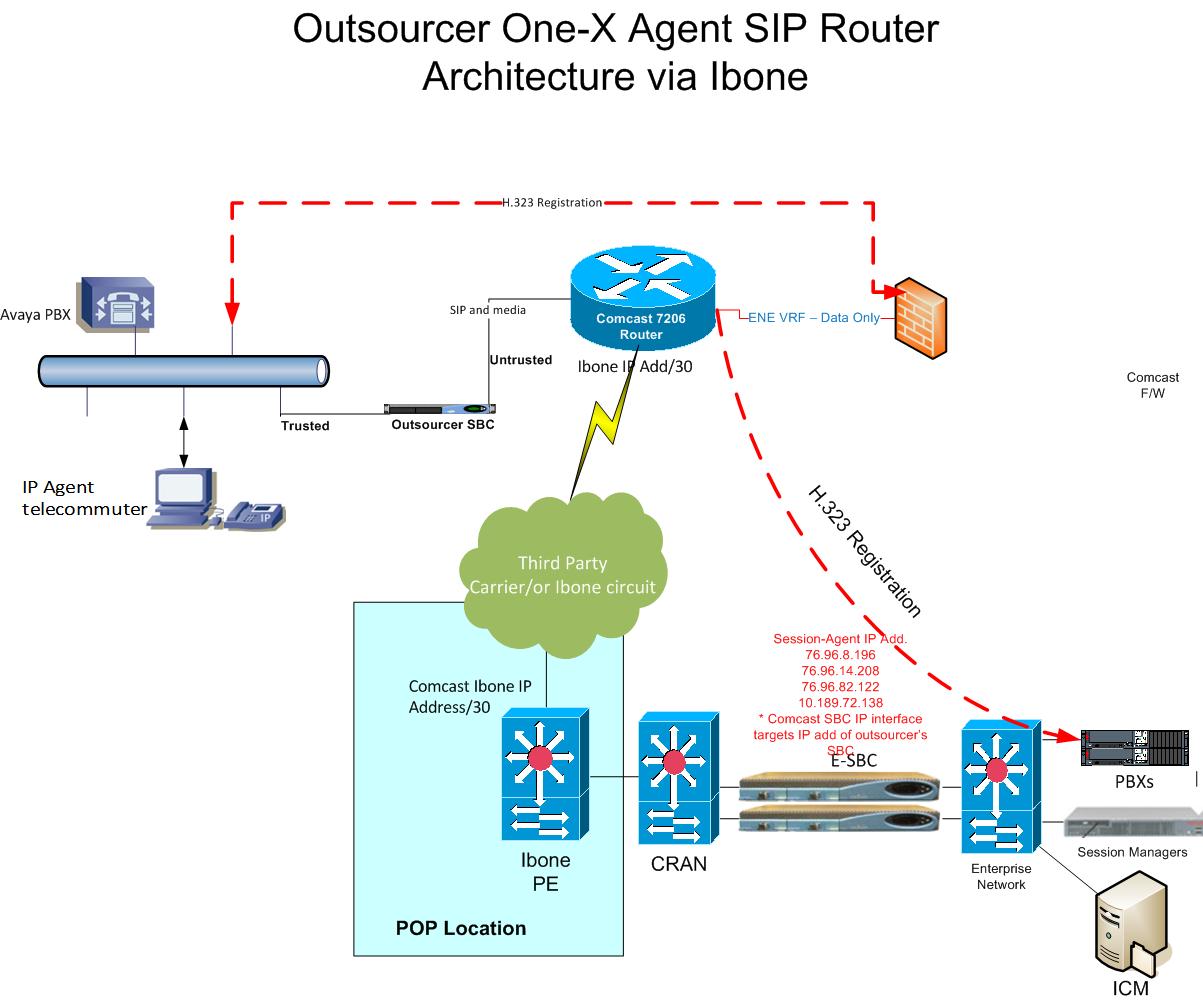
Figure 1 – Functional Architecture with Ibone Edge Circuit
81
COMCAST CONFIDENTIAL
US.54162848.01
CONFIDENTIAL TREATMENT
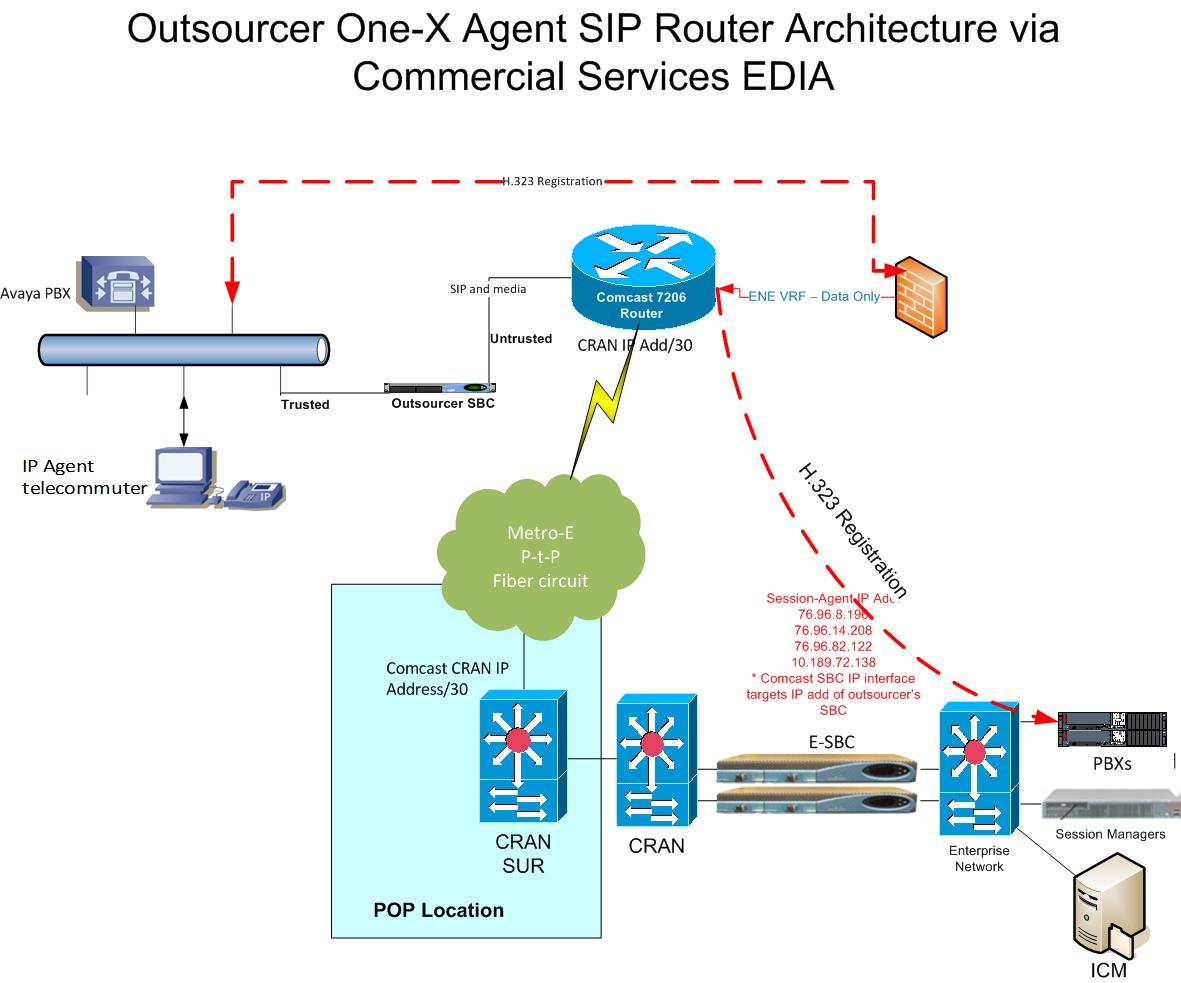
Figure 2 – Functional Architecture with Commercial Services EDIA Circuit
The SIP to outsourcer Architecture will include numerous components which will be used for redundancy/route-advance purposes to insure proper termination of the call.
E-SBC- Enterprise Network Session Border Controller that provides the demarcation between the enterprise network and the service delivery network that services the SIP signaling and media between Comcast and the outsourcers. The E-SBC provides the SIP B2B policy based call routing to route calls received from Comcast CDV infrastructure and signals the national ICM via SIP to allow the ICM to perform pre-routing as well as from Comcast division PBX/Avaya Session Managers. In addition, the E-SBC will receive the label from ICM that determines where to route the call to (Division Session Manager or to an outsourcer)
Avaya Session Manager – This device is signaled via SIP from the E-SBC to determine which PBX/CM to send the call.
Avaya Communication Manager – One-X Agent registers via H.323 to the Avaya CM PBX then CM connects call to outsourcer One-X agent via SIP signaling to the telecommuter mode One-X Agent. When agent answers ring, media is established over the SIP infrastructure (SBCs). The PBX routes the call either to an outsourcer One-X Agent or Comcast Call Center agents.
Comcast co-located router(s) installed at the outsourcer location – Provides the network connectivity from Comcast routed network to outsourcer Session Border Controller (SBC) to facilitate the SIP signaling and audio media to connect calls to the One-X Agent desktop/phone in addition to providing the routing for data traffic to the outsourcer that
includes analytics and the path for One-X Agents to register back to the Comcast PBXs via H.323 signaling and keep-alives.
Comcast co-located firewall(s) – Provides the security demarcation between Comcast sensitive data and the outsourcer network.
Avaya Call Management System (CMS) - database, administration, and reporting application to helps Comcast and outsourcer vendors identify operational issues and take immediate action to solve them. Division and Call center managers can view data and receive customized threshold and exception alerts, all in real time. They can also view historical reports to help them analyze trends, establish performance benchmarks, and plan new marketing or customer-service campaigns.
E-Workforce Management - Workforce Management provides forecasting and scheduling capabilities to contact centers. eWFM analyzes contact center agent performance as well as contact center performance trends. Automatically forecasts staffing requirements to meet call volumes and automating agent scheduling, Workforce Management ensures that businesses have the right workforce, with the right skills, to better serve customers.
Call Recording - Provides the capability to record, store, and play back voice interactions. Synchronizes agent’s on-screen activity to the audio recording, and provides agent performance evaluation tools for a complete view of customer interactions and their quality.
One-X Agent - Avaya one-X® Agent is a is a contact center agent desktop application that provides the outsourcer’s call center agent the IP telephony VoIP connections. Outsourcer One-X Agent registers back to the Comcast Avaya Communication Manager PBX in the telecommuter mode.
CVP (Cisco Voice Portal) – A Web Server application which interprets messages from the Cisco ICM; also consists of a Voice Browser that processes PSTN and IP telephone calls, converts the voice signals into events for processing by an application server, and acts upon VXML commands received from an application Server software and generates VXML documents that it uses to communicate with the Voice Browser.
ICM (Intelligent Contact Management) – Provides a virtualized contact center routing, reporting, and computer telephony integration across national and divisional customer care call routing platforms. The ICM will be signaled by the E-SBC via the Cube and CVP to provide pre-routing of every Customer Care toll free call using a translation route which defines a temporary DNIS number dedicated for the purpose of identifying the call. The ICM will respond with a 302 redirect and a label back to the E-SBC to alert the E-SBC where to route the call.
Dark Fiber – When a Comcast Point-of-Presence is located within proximity of an outsourcer Point-of-Presence, Comcast will install fiber optic connectivity between the Comcast demarcation and the outsourcer demarcation directly and the fiber will be lit by each side’s network router/switch.
Commercial Services EDIA Metro E – Also known as Metro Ethernet – A specific set of standards designed to provide parity among carriers and service providers. Where Comcast has EDIA footprint, outsourcer should implement this service.
Ibone Network – Comcast backbone network that peers with 3rd party carrier(s) to provide last mile p-t-p circuit to outsourcer location. Where Comcast does not have EDIA footprint, outsourcer should implement this service.
Point-to-Point – A carrier circuit that terminates a Comcast Point-of-Presence location to an outsourcer connection
Carrier circuits – Traditional or legacy means of connection when crossing between facilities through the “public domain.”
Network Architecture
Other than the pre-route dip that is provided for in Phase II of CDV Toll Free On-Net, Outsourcer IP/One-Agent deployment via SIP is independent of the other phases, and completely transparent to other phases of the Telecom Savings Initiative. Currently, calls routed to outsourcers require pre-routing for national toll free number, and temporarily, local market calls require AVP/U-IVR treatment, therefore the calls destined for a particular outsourcer will be part of the label to instruct the E-SBC which outsourcer to send the call. The routing from the E-SBC either uses dark fiber transport from a selected Comcast Head-End location to the outsourcer point-of-presence within the same proximity, or will be routed to the outsourcer from a carrier partner’s P-P service in locations utilizing a peering connection to a 3rd party carrier for those outsourcer locations Comcast Commercial Services does not have footprint.
Once the connectivity is in place, Outsourcer agents will be on par with Comcast agents and will be “seen” for their current state (available; unavailable; work; talk; etc.) as if they were on Comcast premises. This will provide Comcast with exactly the same statistical information for those agents as is had with Comcast agents.
National CDV Toll Free calls will be routed to the E-SBC from the CDV/IMS infrastructure and then will perform a pre-route “dip” to the Corporate ICM via the Cisco Voice Portal. When the Corporate ICM returns the label containing contact header information (DNIS) instructing the E-SBC to perform an ENUM query that returns a NAPTR instructing the E-SBC to route the call to either the appropriate Division Session Manager, then Division Communication Manager. If a call is routed to a Comcast call center agent that requires transferring the call to an outsourcer, the Comcast call center agent will perform a transfer that results and the Communication Manager will send transfer the call to an outsourcer One-X Agent registered to the Communication Manager.

Figure 4 CDV Toll Free On-Net Phase III Architecture
84
COMCAST CONFIDENTIAL
US.54162848.01
CONFIDENTIAL TREATMENT

Figure 5 CDV Toll Free On-Net Phase III Call Flow Dark Fiber to Outsourcers
Interfaces & Protocols
This section presents the interfaces and protocols will be used to traverse the backbone.
Table 1 – CDV Toll-Free on net Protocols
Elements Interfaced | Interface Protocol | Notes |
Interface between Enterprise and C/RAN networks | L2TPv3/MGRE Tunnels | 22 peering sites around the country where traffic moves between Enterprise and C/RAN networks. |
Interface between CDV and E-SBC | SIP | |
IBone Edge to Outsourcer via Carrier partner transport | L2TPv3/MGRE Tunnels | Dedicated on-site Comcast Router and Firewall/Egress of tunnel |
Commercial Services EDIA GigE service | L2TPv3/MGRE Tunnels | Dedicated on-site Comcast Router and Firewall/Egress of tunnel |
TECHNICAL REQUIREMENTS
This section summarizes the technical requirements for the Outsourcer connections.
Troubleshooting
Requirement Number | Requirement Title / Tag | Requirement Description | Explanatory Notes |
TROUC-01 | Real-time | The Outsourcers networks MUST support monitoring of real-time calling by site for selected Telephone Numbers. | An Ops Support Plan and SLA document will be provided in a separate document, prior to market launch |
TROUC-02 | Monitoring Tools | The Outsourcers networks MUST support monitoring of signaling flows via NgN or Empirix | |
TROUC-03 | QoS | The Outsourcers networks MUST support the monitoring of QoS for both SIP and RTP legs of a call. | TBD |
TROUC-04 | Traps | The Outsourcers networks MUST support traps for alarms of CDV network gear. | The SIP Ops team will receive traps for the E-SBCs and their respective router ports in addition to the CDV elements. This requirement has been covered under the Enterprise calling off net initiative. |
Enterprise Network Requirements
Features and Functions
Requirement Number | Requirement Title / Tag | Requirement Description | Explanatory Notes |
FFE-01 | Dialed Digits | The Enterprise network MUST accept dialed digits from SIP invite ReqURI and To headers. | Dial Plan will be consistent with current digit handling (dnis, etc.) |
FFE-02 | CgPN | The Enterprise network MUST accept CgPN from the Outsourcers networks in either Diversion/FROM headers. | |
FFE-03 | DTMF | The Enterprise network MUST support DTMF – G711 or G729 in band. This is an a=PCMU/8000/1 parameter within SDP of SIP messaging. | Must support transcoding at the enterprise stage |
FFE-04 | Music, Recording, Announcements and Tones | The Enterprise network MUST pass music, recording, announcements and tones to Callers. Two-way audio is established upon Enterprise network sending 200OK towards Outsourcers networks. | |
FFE-05 | Hang up release | The Enterprise network SHOULD send SIP BYE message upon called party hanging up. | |
FFE-06 | Add/Remove Enterprise sites | The Enterprise network SHOULD support the ability to add and remove Enterprise sites. | |
FFE-07 | XXXXX to CRAN | ENE/NETO peering input service policy will trust the CRAN standards of EF for bearer/rtp traffic and AF31 for the signaling traffic. EF is the enterprise standard for bearer traffic, and it will be the responsibility for Enterprise Network Engineering to provide high enough QoS priority through the proper packet markings and tunneling to maintain a high quality voice call. | |
FFE-08 | Access Lists | The Enterprise Network Router Configurations SHOULD include access list statements to filter or allow required voice traffic. | Already setup with Enterprise Calling off net initiative. |
FFE-09 | CgPN | The Enterprise Network MUST be able to route based on CgPN (diversion/from) in their SIP messaging to the CDV Network | |
Routing
Requirement Number | Requirement Title / Tag | Requirement Description | Explanatory Notes |
ROUTE-01 | Geo-diverse Zone Routing | The Enterprise and outsourcer networks MUST support the ability to accept calls to each site to geo-diverse E-SBC’s based upon zones. The network must provide redundancy for all outsourcer connections requiring each circuit to accommodate the full call volume to each outsourcer via the redundant route. | The Enterprise network must support the ability to route calls to geo-diverse E-SBC’s based upon the geographic location of the Enterprise calling site and deliver to diverse outsourcer locations. For example, Enterprise sites in the Northeast will route to the Manassas E-SBC as 1st choice and the Woodstock or Chicago E-SBC as 2nd choice. The specific zones will be detailed in the DDD. |
ROUTE-02 | Route Advancing | The Enterprise and outsourcer networks MUST respond with SIP 503 when unable to terminate call. | |
ROUTE-03 | SIP Refer | The Enterprise and outsourcer networks MUST support SIP REFER. | |
ROUTE-04 | Transfer | The Enterprise network MUST support transfer such that it does not use traditional trunk-to-trunk transfer as the primary solution. | |
ROUTE-05 | ICM | The Enterprise network MUST provide connection to the ICM infrastructure and other call routing platforms. | Must support REFER and/or 302 REDIRECT Signaling |
ROUTE-06 | XXX, TOW | The Enterprise network MUST support business level access to control Time of day, and Time of week routing. | This is Route IT function resolved using ENUM and ICM preroute dip |
ROUTE-07 | Real-time | The Enterprise network MUST support business level access to control Real-time control of traffic by area code. | This is Route IT function resolved using ENUM and ICM preroute dip |
ROUTE-08 | Overflow | The Enterprise network MUST support business level access to control overflow. | This is Route IT function resolved using ENUM and ICM preroute dip |
ROUTE-09 | EDIA | 1st choice for providing transport between Comcast Commercial Services aggregation location to outsourcer location | Ethernet fiber connection from SUR to outsourcer router within the Comcast footprint |
ROUTE-10 | Peering/Trunk to carrier partner(s) | 2nd choice to provide transport between Comcast point-of-presence to outsourcer via IBone edge utilizing a common partner carrier (AT&T, BT or Level3) | Via tunnel from XXxxx to Outsourcer located FW |
ROUTE-11 | Enterprise/CRAN peer via XXxxx routers | Comcast will provide tunneling through the Comcast SDN (ingress) and provide prioritization for VoIP traffic bound for the Outsourcers | Comcast to use existing onsite routers and firewalls to provide the egress of tunnels at the Outsourcer locations. |
ROUTE-12 | IBONE edge routing/CRAN SUR EDIA edge routing to outsourcers | Comcast will provide at least 2 redundant SIP transports routing from E-SBCs to selected IBONE edge or CRAN SURs to transport calls to Comcast outsourcers. | Comcast to coordinate with outsourcers to provide diverse routing to route calls to outsourcer agents. |
ROUTE-13 | Support for VDI data traffic | If decided for future deployment, the Enterprise Network will provide routing and transport for division VDI traffic in parallel with VoIP traffic | Not applicable for this project |
Reporting
Requirement Number | Requirement Title / Tag | Requirement Description | Explanatory Notes |
REPE-01 | MOU | The Enterprise and outsourcer networks MUST report the MOU for all calls sent to the Enterprise network. | TBD |
REPE-02 | Cost Analysis | The Enterprise network MUST support cost analysis reporting. | TBD |
REPE-03 | Capacity Planning | The Enterprise and Service Delivery networks SHOULD support call volume and interface utilization for tracking call activity and capacity planning. | Cariden modeling tool for Comcast SDN network |
REPE-04 | Call Reporting | The Enterprise network will enable Comcast and each outsourcer to collaborate call reporting and Work Flow Management (WFM) | TBD |
REPE-05 | Call Recording | The Comcast Enterprise network and outsourcer will support both Audio recording as well as Screen Recording - this allows Comcast to capture agent screen interactions as the call is being recorded, and save them into a single transaction that can be replayed in its entirety. | Type depending on outsourcer requirements and configuration |
REPE-06 | E-WFM | The Comcast Enterprise network and outsourcer will support work force management traffic that provides Comcast strategic workforce planning, workforce scheduling, quality and performance management, recording, surveying, coaching, eLearning and analytics. | |
Deployment Requirements
Requirement Number | Requirement Title / Tag | Requirement Description | Explanatory Notes |
CREQ-01a | Comcast Commercial Services Metro-E | Where Comcast Comm. Svcs. has footprint available, call will route to CRAN SUR. Commercial Services provides /30 to Comcast owned co-located router for p-t-p circuit as well as provide routing (static or ebgp) to advertise outsourcer SBC session-agent IP subnet. | Commercial Services performs site survey and determines fiber optic connectivity requirements. Outsourcer provides access to facility and provides CC with required physical information |
CREQ-01b | Comcast Ibone routing | Where no Comcast Comm. Svcs. footprint available, call will route to Ibone edge POP Ibone team provides /30 to Comcast owned co-located router for p-t-p circuit as well as provide routing (static or ebgp) to advertise outsourcer SBC session-agent IP subnet. Comcast will coordinate between outsourcer and 3rd party carrier to location demarcation. Outsourcer will provide connection from that demarcation to Comcast co-lo router | Cross-connected to 3rd party carrier for last mile to outsourcer. May require LEC to terminate to outsourcer demarcation |
89
COMCAST CONFIDENTIAL
US.54162848.01
CONFIDENTIAL TREATMENT
CREQ-02 | Comcast Enterprise Network co-located router installation | Enterprise Operations Engineering will stage and ship router(s) to outsourcer location. Comcast recommends outsourcer untrusted IP address be part of Comcast subnet. If outsourcer provided IP subnet, outsourcer provides routing to Comcast co-located router and coordinates SIP session-agent requirements with Comcast engineering. | Outsourcer will provide location contact, address, tel #, etc. Outsourcer will rack/stack/cable router to outsourcer SBC for SIP signaling and media and to Comcast co-located firewall for data and H.323 registration. |
CREQ-03 | Comcast Data Integrity/security | Comcast security team will support/stage/ship firewall to be installed at outsourcer location. | Outsourcer will provide location contact, address, tel #, etc. Outsourcer will rack/stack/cable firewall and provide physical connectivity to Comcast co-located router as illustrated by Comcast diagram. |
CREQ-04 | Comcast ORP/Operation Support | Comcast network/telecom/division support teams to provide ORP in coordination with outsourcer Operation Support team and if necessary, 3rd party carrier support/tech ops. | |
OREQ-01 | Outsourcer SBC | Outsourcer will provide a SBC to physically interface to the Comcast installed co-located router. Outsourcer will configure session-agents to peer with Comcast E-SBCs. | Comcast recommends providing the untrusted interface IP to route the session-agent. If outsourcer provides IP, outsourcer network needs to advertise and route to Comcast co-lo router |
OREQ-02 | Outsourcer VoIP network | Outsourcer will provide layer 1, 2 and 3 connectivity from outsourcer network to Comcast co-lo router to facilitate SIP signaling and audio/media to outsourcer SBC from designated router interface; | Coordinate with Comcast network engineering |
OREQ-03 | Outsourcer Data/H.323 network | Outsourcer will provide layer 1, 2 and 3 connectivity from outsourcer network to Comcast co-lo router to facilitate data and H.323 One-X Agent registration/keep-alives to outsourcer agent stations from designated router interface; | Coordinate with Comcast network engineering and division telecom |
OREQ-04 | One-X Agent | Outsourcer will install/facilitate agents’ desktop/phone for registration to Comcast division CMs. | Coordinate with Comcast corporate and division telecom |
OREQ-05 | Outsourcer Operation Support | Outsourcer support teams to provide network and telecom support in coordination with Comcast Telecom Operation Support team and if necessary, 3rd party carrier support/tech ops. | Coordinate with Comcast network engineering and corporate telecom |
Troubleshooting
Requirement Number | Requirement Title / Tag | Requirement Description | Explanatory Notes |
TROUE-01 | Real-time | The Enterprise network MUST support monitoring of real-time calling by site for selected Telephone Numbers. | An Ops Support Plan document will be provided in a separate document, prior to outsourcer launch |
TROUE-02 | Monitoring Tools | The Enterprise network MUST support monitoring of signaling flows | |
TROUE-03 | Traps | The Enterprise network MUST support traps for alarms of Enterprise network gear. | |
Not Supported
• | T38 Fax Transmission Standard |
• | Modem Pass-through |
91
COMCAST CONFIDENTIAL
US.54162848.01
CONFIDENTIAL TREATMENT
EXHIBIT D –TELECOMMUNICATIONS REQUIREMENTS
One-X Agent Requirements
THIS PAGE INTENTIONALLY LEFT BLANK
This Exhibit is intended to highlight the minimum requirements of what a 3rd Party requires to conduct business with Comcast. The 3rd Party provider is required to bring an enterprise-level network and telephony infrastructure to engage in business supporting Comcast. Comcast will provide the phone switch, ACD routing, and the majority of tools for agents, supervisors / team leads, managers, resource teams and call quality resources.
The 3rd Party will provide:
• | Network transport: two (2) geographically diverse 1-gigabyte connections within the continental United States. The locations will be required to hand-off data / voice / SIP connectivity. |
• | An SBC/SIP enabled PBX including agent handset / trunk to concurrent agent ratio 1.5 to 1. As an example, if there are 500 agents, there will be 750 trunks. |
• | Traditional desktop equipment to support Avaya One-X client specification and other applications as outlined herein. |
• | Adhere to Comcast QoS across all networks for voice |
Comcast Requirements
Comcast will host:
• | ACD routing functionality via One X Telecommuter |
• | Workforce Management |
• | Real-time Adherence |
• | Real-time Monitoring |
• | Call Recording |
• | VOC Survey |
• | IVR |
• | CTI |
Comcast will provide:
• | ECH data for historical reporting. |
• | Connectivity to 3rd Party DMARCS |
• | Process to request Group and Skilling Changes |
Architecture Overview – 3rd Party via Telecommuter
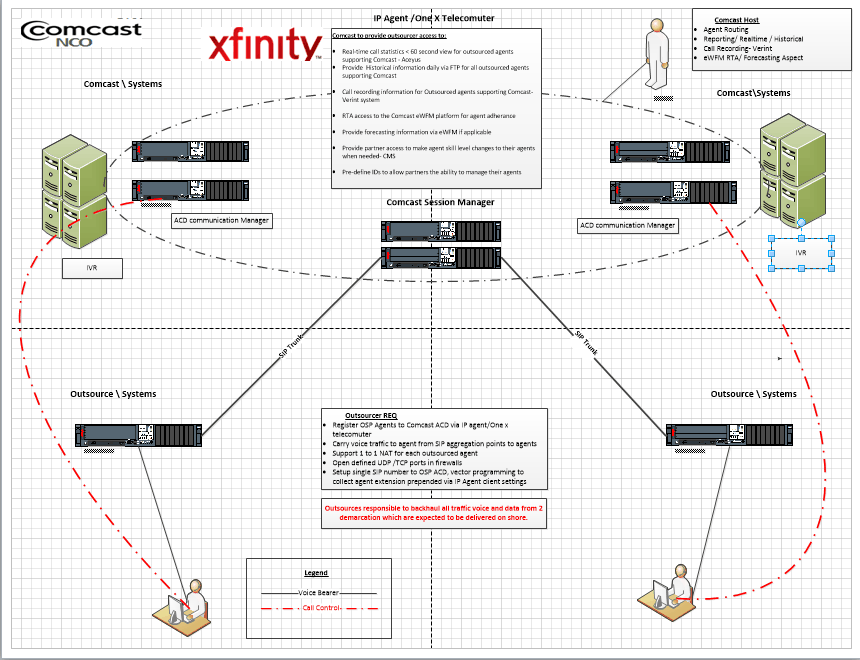
Figure 2 – 3rd Party via Telecommuter
Telecom Services Connectivity
• | 3rd Party will work with Comcast to provide sufficient circuits, bandwidth, and connectivity as required to handle Comcast’s traffic. 3rd Party will expected to carry all voice and data traffic from the agreed upon peering points to the physical location of the agents. Transcoding from g.711, g.729 or other will be the responsibility of the partner. |
• | 3rd Party must make every reasonable effort to provide the type and volume of connectivity desired by Comcast including but not limited to TDM and SIP connectivity. 3rd Party will expected to support 200% of their peak concurrent agents via SIP trunk and 100% of PSTN for backup failover routing |
• | This connectivity must be from the major carriers that Comcast uses to provide the advanced network features that help to support Comcast’s customer’s experience. These major carriers include but are not limited to carriers such as Comcast, ATT, Verizon, Sprint, and Level 3. In the event Comcast desires to change carriers then the parties will address such request in accordance with the Change Management process |
• | Services should be provided over robust, diversely routed facilities routed in order to insure maximum availability and resiliency. [Diversity requirements include sufficient separation of communication services to avoid an outage occurring simultaneously with both network service providers. |
• | Comcast has the option to have the telecom circuits/services terminating at 3rd Party’s Locations and in such event the parties will handle such Comcast request in accordance with the Change Management process. Comcast will be billed for any costs associated with the telecom circuits/services terminating at 3rd Party’s Locations. |
• | Comcast should have access to major call traffic statistics and CDR data for calls made or received in support of Comcast and its customers. 3rd Party shall work with Comcast to implement tools (if needed by Comcast) to support this requirement. 3rd Party partner will provide call details for traffic traversing their facilities upon |
CONFIDENTIAL TREATMENT
request, data would include but is not limited to, duration of call, number of calls, ANI, DNIS and MOS statistics.
Reporting
Comcast will provide the following
• | Real-Time Reporting – From Agent Groups up to Summary view – Aceyus |
• | Vendor Scorecard Creation – ECH Data to be published nightly for OSP consumption |
• | RGU – provided by national reporting team |
• | TSR Call Volume – provided by national reporting team |
• | Daily Call Volume – provided by national reporting team |
• | Line Adherence feeds – provided by national reporting team |
• | Queue-based Agent FCR - can be extracted from ECH data |
• | Financial Reporting – Invoicing provided through line adherence tool. |
Comcast QoS Settings
• | AF31 for signaling |
• | RTP Media AF46 or EF |
From a hex standpoint, it’s 0x68 for signaling and 0xb8 for media.
tos-settings | ||
media type | message | |
media-sub-type | ||
tos-value | 0x68 | |
media-attributes | ||
tos-settings | ||
media type | audio | |
media-sub-type | ||
tos-value | 0xb8 | |
media-attributes | ||
Tools/Connectivity
Comcast is responsible for delivering voice and data communication from Comcast systems to 3rd Party’s desired termination point(s). Comcast is responsible for all costs associated with providing 3rd Party the appropriate access to all Comcast Tools required for 3rd Party to provide the Services, including, but not limited to those noted below:
• | Comtrac |
• | Casper |
• | Grand Slam |
• | Agent Dash Board |
• | Offer Management Tool |
• | Links to relevant reporting tools |
• | Outage Board |
• | Rate Guide |
CONFIDENTIAL TREATMENT
• | Pinnacle |
• | OCR Tool |
• | Third party quality assurance firm’s reporting portal |
• | TTS |
• | Einstein |
• | Cafe |
CPNI Compliance
(Sub-Contractor Personnel)
Companies that provide voice services are required to certify to the FCC that they comply with the Customer Proprietary Network Information (CPNI) regulations. CPNI rules limit the circumstances under which voice service providers can sell additional services to customers and prohibit disclosure of CPNI to unauthorized third parties, so you may only discuss details of customer’s voice service account with the customer or someone designated by the customer. Since you may have access to CPNI, you are required to complete training. This requirement may be fulfilled when you familiarize yourself with this memo and sign below.
CPNI Rules
CPNI is information regarding an individual customer’s voice service, such as how many voice lines a customer has, how the service is arranged or provisioned, and information about to whom, where, how long and how often calls are made to or by a customer. Billing information and most information about a customer’s voice service is also CPNI. The customer’s name, address and phone number are not CPNI. All traditional telephone, as well as, interconnected VOIP service providers are required by the FCC to keep CPNI secure from unauthorized users. Individuals must not discuss or disclose any customer’s CPNI with any third party without the authorization of the customer.
Doing so may be a breach of your agreement with _____________________________,
[Insert your Sub-Contracting Company Name]
and may otherwise result in work no longer being assigned to you or your company. Also, it could expose the voice provider to extremely high fines.
If you mistakenly use CPNI information when speaking with or about a voice provider’s customer, or if you become aware of non-approved use of CPNI, immediately report it to
management of ___________________________.
[Insert your Sub-Contracting Company Name]
I acknowledge that I have read and understand this document.
_________________________________________________________________
Print Name
_________________________________________________________________
Signature Date
CONFIDENTIAL TREATMENT
CPNI Compliance
(Contractor Employee)
Companies that provide voice services are required to certify to the FCC that they comply with the Customer Proprietary Network Information (CPNI) regulations. CPNI rules limit the circumstances under which voice service providers can sell additional services to customers and prohibit disclosure of CPNI to unauthorized third parties, so you may only discuss details of customer’s voice service account with the customer or someone designated by the customer. Since you may have access to CPNI, you are required to complete training. This requirement may be fulfilled when you familiarize yourself with this memo and sign below.
CPNI Rules
CPNI is information regarding an individual customer’s voice service, such as how many voice lines a customer has, how the service is arranged or provisioned, and information about to whom, where, how long and how often calls are made to or by a customer. Billing information and most information about a customer’s voice service is also CPNI. The customer’s name, address and phone number are not CPNI. All traditional telephone, as well as, interconnected VOIP service providers are required by the FCC to keep CPNI secure from unauthorized users. Individuals must not discuss or disclose any customer’s CPNI with any third party without the authorization of the customer.
Doing so may result in disciplinary action up to and including termination of employment and could expose the voice provider to extremely high fines.
If you mistakenly use CPNI information when speaking with or about a voice provider’s customer, or if you become aware of non-approved use of CPNI, immediately report it to management of _______________________________.
[Insert Contractor Company Name]
I acknowledge that I have read and understand this document.
_________________________________________________________________
Print Name
_________________________________________________________________
Signature Date
97
COMCAST CONFIDENTIAL
US.54162848.01
EXHIBIT F
Contractor
CPNI CERTIFICATION
This certification is being submitted to:
Comcast Cable Communications Management, LLC
I ____________________ of _________________________________________
[INSERT CONTRACTING COMPANY NAME]
hereby certify that all individuals employed by or working on behalf of
____________________________, having access to Customer Proprietary Network
[INSERT CONTRACTING COMPANY NAME]
Information (CPNI), have been trained in the appropriate treatment and protection of CPNI. This training has been administered and completed in compliance with 47 U.S.C. Section 222 and all applicable Federal Communications Commission rules, regulations and orders, including but not limited to Subpart U of Part 64, of Title 47 of the Code of Federal Regulations.
It is further certified that all of the information stated above is accurate and truthful. It is understood that the presentation of false information may result in a breach of the agreement that the Contractor has with Comcast.
{Company Seal}
________________________ _______________________
Name Title
_________________________ _______________________
Signature Date
