TRAVEL TECHNOLOGIES GROUP, L.P. d/b/a TRAVEL TECHNOLOGIES GROUP SERVICE BUREAU AGREEMENT
Exhibit 10.18
TRAVEL TECHNOLOGIES GROUP, L.P.
d/b/a TRAVEL TECHNOLOGIES GROUP
This Service Bureau Agreement (this “Agreement”) is made and entered into this 24th day of July, 2000 (the “Effective Date”) by and between TRAVEL TECHNOLOGIES GROUP, L.P., d/b/a TRAVEL TECHNOLOGIES GROUP, located at 0000 Xxxxxxx Xxxx, Xxxxxx, XX 00000 (hereinafter “TTG”) and American Express Travel Related Service Company, Inc., located at World Financial Center, American Express Tower, 000 Xxxxx Xxxxxx, Xxx Xxxx, Xxx Xxxx 00000, XXX (hereinafter “User”).
Subject to the terms and conditions in this Agreement, TTG hereby agrees to provide User certain services through the use of TTG’s software product and related manuals and documentation specified on Exhibits A, B, C, and D attached hereto, and incorporated herein by reference.
| 1. | Definitions |
| 1.1. | Acceptance – Written confirmation from User to TTG issued in accordance with Section 2.7 hereof, that an Enhancement, or the development and integration work required hereunder, developed by TTG pursuant hereto, functions and performs in accordance with applicable specifications and service level requirements. |
| 1.2 | Affiliated Travel Agencies – Franchisees or other travel agencies to which User provides services, products, or User’s Confidential Information, but excluding those agencies whose only relationship to User is the acceptance of User’s credit card for payment. |
| 1.3 | Enhancement – Changes to the Software that provide additional features and/or functionality not included within the Standard Services, expanding the capabilities of the Software in existing or new functional areas. |
| 1.4 | Global Distribution System or GDS – A computer system or network used to check and make reservations of a travel related nature, including without limitation, Amadeus, Appolo/Galileo, Sabre and Worldspan. |
| 1.5 | Improvements – New functionality that addresses areas that were not covered in the initial or subsequent release Software Release for a Product, or so significantly expands a function as to be considered a new function. |
| 1.6 | Modification – Changes to the Software that affect existing functionality. Normally this includes streamlining processes, revising screens for clarity, etc. |
| 1.7 | Product – A logical grouping of Software Releases, in object code only, and related documentation, which are sold by a specific product name. |
| 1.8 | Service Bureau – Computer facility, located at the TTG Service Bureau offices located at 0000 Xxxxxxx Xxxx, Xxxxxx, XX 00000, from which TTG will provide services and data information to the User. |
| 1.9 | Software – Collectively, all of the Software Releases created by TTG from time to time, with respect to the Products identified on Exhibits A and B. |
| 1.10 | Software Release – A complete or partial delivery of software implemented at TTG’s discretion that updates all or some portion of the Software or serves as the basis for a Modification, Improvement or Enhancement and resides on the servers at the TTG Dallas facility. |
| 1.11 | Standard Services – All of the services and Products described in this Agreement, including Exhibits A and B hereto, together with such other Products and services as the parties shall |
| mutually agree, for the processing of travel transactions in North America; provided, however User shall be entitled to utilize the Standard Services provided pursuant hereto for the processing of transactions in North America notwithstanding that User may choose to provide services in connection with such transactions outside of North America. |
| 1.12 | User Data – All data and information relating to User, its Affiliated Travel Agencies and their respective clients, client travelers, customers and users that are generated, received, transmitted, used or stored in connection with the provision of the Standard Services, the Products or other services provided by or on behalf of TTG hereunder or otherwise. |
| 2. | Scope Of Services |
| 2.1 | TTG shall provide the Standard Services to User and its Affiliated Travel Agencies, together with any Modifications, Improvements, or new Software Releases relating to the Standard Services, as soon as such Modifications, Improvements or new Software Releases are offered generally by TTG; provided, however in the event the development costs for any such Modification, Improvement or New Software Release were paid by an third party customer of TTG and TTG charges all of its customers for the use of such Modification, Improvement or new Software Release, User shall pay for the use of same in accordance with the provisions of Section 4.4 hereof. The Standard Services shall be provided at the pricing set forth in Exhibit A and Section 4.4 hereof, and in accordance with the terms of this Agreement, including without limitation, the service level requirements of Exhibit C and the security standards set forth in Exhibit D as modified from time to time by User in accordance with Section 22. TTG shall not, without User’s consent, modify (i) the composition or nature of the services, or (ii) the manner in which the services are provided or delivered. |
| 2.2 | As part of the Standard Services, TTG shall maintain and enforce at the Service Bureau safety and physical security procedures that are (a) at least equal to industry standards for such types of service locations, (b) at least as rigorous as those procedures in effect at such location as of the Effective Date, and (c) which provide all appropriate technical and organizational safeguards against accidental or unlawful destruction, loss, alteration or unauthorized disclosure or access of User Data and all other data owned by User and accessible by TTG hereunder. User shall have the right to establish back up security for data and to keep back up data and data files in its possession if it chooses. If User requests additional safeguards for User Data other than as required by this Agreement including the Exhibits hereto, TTG shall provide such additional safeguards at User’s expense, which shall be the actual cost of such additional safeguards. Without limiting the generality of the foregoing, TTG shall take all reasonable measures to secure and defend against “hackers” and other who may seek to modify or access the Service Bureau or access any User Data or information found therein without the consent of User, and to correct same to its original form in the event that it is modified without the consent of User. TTG shall report to User in a timely fashion any breaches of security, unauthorized changes to or access to the Service Bureau or User Data that has or is likely to disrupt, cause embarrassment to User or any of its Customers or in any way diminish the quality of the services provided hereunder. TTG shall use its best efforts to remedy such breach of security or unauthorized changes within two (2) days of any such breach of security or unauthorized changes. |
| 2.3 | The Software necessary to provide and support the Standard Services and any Enhancements developed pursuant to this Agreement will at all times hereunder run and reside at the Service Bureau. The Software will be run by TTG according to the provisions of this Agreement and such other of User’s specific needs and requests as are mutually determined and agreed by the parties. TTG will compile and transmit to User on a monthly basis such portions of the User Data as User may require, strictly in accordance with User’s instructions. |
| 2.4 | TTG shall provide to User all of the reporting described on Exhibit B. Additionally, TTG hereby grants to User the nonexclusive, royalty free license to use TTG’s “EnCoRRe Reports” software |
- 2 -
| or any successor thereto, provided by TTG to User, to generate and run such other reports as User may desire from the information and User Data transmitted to User pursuant to Section 2.3 above. |
| 2.5 | The Software will include adaptations for use with all GDS systems including, but not limited to, Amadeus, Apollo/Galileo, Sabre and Worldspan. User may request other specific Enhancements to the Software. TTG agrees to negotiate in good faith with User towards the development of such Enhancements and User agrees to pay for such requested Enhancements) at prices, terms and conditions no less favorable than those offered by TTG to any other party. These payments for Enhancements entitle User exclusivity to the use of these new Enhancements for not less than six (6) months after implementation and Acceptance. In the event TTG makes the Enhancement available for general use, such reimbursement shall be made to User, immediately upon receipt by TTG of payment from its customers, in installments equal to fifty percent (50%) of the amounts paid to TTG by its customers for such Enhancement TTG and User may agree, prior to the development of any Enhancements, to develop an Enhancement at a rate less than that set form in this Section 2.4 and the parties may further agree correspondingly to limit exclusivity to less than 6 months. |
| 2.6 | Both parties will periodically discuss and review User’s competitive environment which would include a review of User’s competitors’ technology, cost or pricing structure and service offerings, to the extent such information is known (and with respect to TTG, to the extent that disclosure of such information is not restricted by contractual obligation to a third party). If there is significant financial impact from new or improved process or technology: (1) which would reduce costs or improve service; (2) which would make competitors’ costs for services at or below User’s cost for comparable services; or (3) which would make competitors’ service offerings superior to those of User, then, the parties shall jointly determine, in good faith, if a change in technology, cost or services should be made, in accordance with the provisions of Section 12. |
| 2.7 | Within thirty (30) days of the Effective Date, the parties shall jointly develop detailed specifications (the “Specifications”) for the tasks involved in the integration and customization of the Software and the Products necessary to enable TTG to provide the fulfillment, file finishing, internal and external customer documentation, ticketing and other services to be provided hereunder in accordance with the standards established in the Specifications and this Agreement, including Exhibit C hereto. The Specifications shall include a detailed plan for these development tasks to include, without limitation, programming, testing, integration and implementation (the “Development Plan”). Development of all items called for in the Development Plan shall be complete within sixty (60) days of the Effective Date. |
| 2.8 | Upon completion of the development of all items called for in the Development Plan and within ninety (90) days after the Effective Date, TTG shall complete implementation and integration of the developed materials in accordance with the Development Plan. Upon completion of such implementation and integration, TTG shall certify in writing to User that such implementation and integration work is complete and ready for acceptance testing by User. After User’s receipt of this notice, User shall commence acceptance testing as soon as reasonably practicable and shall complete such testing within ten (10) days. The acceptance testing shall be conducted to demonstrate to User that the developed materials and the integration thereof functions and performance in accordance with the applicable specifications and performance criteria as defined in the Specifications which are consistent with the service levels as defined in Exhibit C. In the event of rejection by User, User will notify TTG, specifying the nature of such failure in reasonable detail, and TTG shall have fifteen (15) days in which to correct the problem after which User will re-conduct the acceptance test within a fifteen (15) day period and the notification procedures will be repeated. |
| 2.9 | In the event there is no Acceptance by User within the timeframes described above, and such lack of Acceptance is based on a delay attributable to TTG, its agents or subcontractors, then the number of unique record locator numbers required to be processed pursuant hereto (as set forth in A.1 of Exhibit A hereto) for User to obtain best pricing shall be reduced by 100,000 for each day |
- 3 -
| of delay until Acceptance. Alternatively, in the event there is no Acceptance with 100 days of the Effective Date attributable to TTG, its agents or subcontractors, User may terminate this Agreement and receive a full refund of that portion of the Implementation Fee, as defined on Exhibit A hereto, paid by User upon execution of this Agreement. |
| 2.10 | As part of the services provided hereunder, TTG shall implement and manage disaster recovery plans and backup plans, substantially in the form of Exhibit F, for the computer equipment and operating environment from which the services will be provided. Within thirty (30) days of the execution of this Agreement, and at least once every quarter during the term of this Agreement, TTG will (i) update and test the operability of the disaster recovery plan in effect at that time, (ii) upon User’s request, certify to User that the disaster recovery plans are fully operational, and (iii) upon discovery by TTG promptly provide User with a notice of a disaster and implement the disaster recovery plans upon the occurrence of any such disaster affecting the provision or receipt of TTG’s services. Whenever a disaster causes TTG to allocate limited resources between or among TTG’s customers and affiliates, User shall receive at least the same priority in respect of such allocation as TTG’s affiliates and TTG’s other commercial customers. |
| 2.11 | TTG shall maintain accurate records in connection with the payment and performance provisions under this Agreement. At User’s expense, User may appoint an independent, nationally recognized, certified public accountant bound in confidence and reasonably acceptable to the TTG to inspect and audit the TTG’s relevant records to ensure compliance with the payment and performance terms of this Agreement. Such inspection and audit shall be during normal business hours upon at least ten (10) days prior notice and shall not interfere unreasonably with the TTG’s business activities. Each party agrees to cooperate with the other in conducting such audit. Inspections and audits shall be made no more frequently than twice a year. User shall also have the right to audit TTG’s operations and related records, in accordance with the foregoing notice and procedural and frequency provisions, to ensure compliance with its data protection, security, and other obligations under this Agreement. In the event User discovers any substantial noncompliance with its security, redundancy, and disaster recover policies then in effect, TTG shall reimburse User for the reasonable costs of such audit, and shall remedy any such noncompliance within thirty (30) days of completion of the audit. |
| 2.12 | TTG shall use its highest level of commercially reasonable efforts to enter into binding agreements with all GDS providers, with terms at least as long as the Initial Term, granting to TTG all rights necessary to TTG to provide the Standard Services and perform all of TTG’s obligations hereunder within 180 days after the Effective Date; provided, however, TTG must enter into such agreements within one year after the Effective Date. TTG shall provide notice to User of each such agreement as and when entered. |
| 3. | Proprietary Rights; Confidentiality |
| 3.1 | User acknowledges that the Software and the related documentation, embody valuable confidential and proprietary information of TTG, the development of which required the expenditure of considerable time and money by TTG, and are protected by United States copyright law and international treaty. User shall treat such information so received in confidence and shall not use, copy, disclose, nor permit any of its personnel (excepting those employees with a “need to know”) to use, copy, or disclose the same, or the existence of same, for any purpose that is not specifically authorized under this Agreement. By virtue of this Agreement, User acquires only the non-exclusive right as described above to receive the services provided by TTG through the use of its proprietary Software and related documentation, and does not acquire any rights of ownership in such materials. TTG, or its licensor, at all times retain all right, title and interest in the Software, related documentation, and, subject to Section 2.5 above, any derivatives thereof. |
| 3.2 | TTG acknowledges and agrees that User Data is, or will be and remain, the exclusive property of User and shall be deemed valuable confidential and proprietary information of User. TTG hereby waives any interest, title, lien or right to any such data. All User Data shall be used by TTG only |
- 4 -
| as necessary to perform its obligations hereunder. In no event shall User Data be (i) disclosed, sold, assigned, leased, or otherwise provided to any party other than User, or (ii) commercially exploited by or on behalf of TTG, its affiliates, employees, subcontractors or agents. Upon expiration or termination of this Agreement for any reason or upon request by User, all User Data shall be returned to User in the media and form requested by User, and TTG shall erase or destroy all User Data remaining in TTG’s possession or control. |
| 3.3 | User recognizes and acknowledges that any unauthorized use or disclosure of the Software by User may cause TTG irreparable damage for which other remedies may be inadequate, and User hereby acknowledges as proper any request to a court of competent jurisdiction by TTG for injunctive or other equitable relief seeking to restrain such unauthorized use or disclosure. |
| 3.4 | TTG and User acknowledge that as a result of the performance of their respective responsibilities under this Agreement, User will obtain access to confidential and proprietary information of TTG and TTG will obtain access to confidential and proprietary information concerning User’s business, customers, methodologies and strategies (all such information, with respect to each party, the “Confidential Information”). All such Confidential Information of the other party shall be deemed to be confidential and proprietary unless such Confidential Information is; (i) is already known to the receiving party free of any restriction at the time it is obtained from the disclosing party; (ii) is subsequently learned from an independent third party free of any restriction and without breach of this Agreement; (iii) is or becomes publicly available through no wrongful act of either party; (iv) is independently developed by one party without reference to any Confidential Information of the other; or (v) is required to be disclosed pursuant to a requirement of a governmental agency or law so long as the parties provide each other with timely written prior notice of such requirements. |
| 3.5 | TTG and User shall not use any of the other party’s Confidential Information for any purpose other than to perform their respective responsibilities under this Agreement. TTG and User shall each take the same measures to protect the Confidential Information of the other party received by it as it prudentially should take with respect to its own Confidential Information, including, but not limited to, instructing its employees, vendors, agents, and independent contractors of the foregoing and requiring them to be bound by appropriate confidentiality agreements. Nothing in this Agreement shall be deemed to prevent TTG or User from providing information to their respective independent contractors who are retained to assist in the performance of such party’s obligations hereunder provided that the conditions set forth herein are complied with by such party and its independent contractors and any such independent contractor is not a competitor of the other party. Notwithstanding the foregoing, in the event that TTG seeks public or private financing, TTG will provide User with prior written notice of any proposed disclosure regarding this Agreement, (including the Exhibits hereto) which notice shall specifically identify the information to be disclosed, the manner of disclosure and the parties to whom TTG intends to seek such disclosure, and no such proposed disclosure shall be made in connection therewith, without User’s prior approval, which approval shall not be unreasonably withheld. User shall provide its comments to title proposed disclosure within ten (10) days of its receipt of the foregoing notice. In that connection, the parties will cooperate in seeking and jointly produce an acceptable redacted version of the Agreement (including Exhibits thereto) and the parties will use good faith reasonable efforts to obtain acceptable confidential treatment from any governmental agency or self regulatory authority and/or acceptable confidentiality agreements form any applicable non-governmental parties, in each case sufficiently protective of each party’s Confidential Information. |
| 3.6 | Neither party shall issue a press release or make any public statement announcing this relationship until such press release or public statement has been mutually agreed. Any publicity or press release relating to this Agreement must be received in writing for review and approval of the other party and shall not be released unless or until written approval is received from the other party. |
| 3.7 | The parties acknowledge that, in the event of a breach of Section 3.2, 3.3, 3.4, or 3.5 by either party, the other party will likely suffer irreparable damage that cannot be fully remedied by monetary damages. Therefore, both parties agree that either party shall be entitled to seek and |
- 5 -
| obtain injunctive relief against any such breach in any court of competent jurisdiction and terminate this Agreement immediately upon written notice to the other party. The rights of either party under this section shall not in any way be construed to limit or restrict the right to seek or obtain other damages or relief available under this Agreement or applicable law. |
| 4. | Pricing and Payment |
| 4.1 | The fees for the services provided pursuant to this Agreement are set forth on Exhibit A attached hereto. All payments will be made in immediately available U.S. Dollars without withholding, deduction or offset (except as otherwise provided in Exhibit C) according to the payment schedule set forth on Exhibit A, and regardless of whether User collects any fees from its customers. User shall pay interest on all amounts not paid when due at the rate of 1.5% per month or the highest lawful rate whichever is less. |
| 4.2 | The service fees do not include any charge for taxes and User is solely responsible for paying any and all national and local taxes (including any and all export/import taxes and customs duties) attributable to the services rendered by TTG or any authorized distributor in connection with this Agreement, excluding only taxes based upon the net income of TTG or an authorized distributor. |
| 4.3 | TTG agrees to refund, on a pro-rata basis, to User for any licenses the User has purchased within 12 months from the de-installation of the software. The amount of the refund will be calculated by multiplying the license fee mat was paid by User (exclusive of any maintenance, installation and training times) (x) 1 minus (-) the fraction with the denominator of 12 and the numerator of the number of months since the license fee was paid to TTG. Within 30 days of the execution of this agreement, User shall notify TTG of all licenses it has purchased within the last 12 months of the effective date of this agreement. |
| 4.4 | TTG agrees to * , as provided herein. TTG represents that * . If, during the term of this Agreement, * . In addition, if TTG makes any service commitments or enters into any service level agreements * . In determining whether terms or commitments are * for purposes of this Section 4.4 the parties shall consider the terms concerning * that are modified or configured in a manner requested by User and not typically provided * . |
| 4.5 | In the event that subsequent to the Effective Date TTG enters into an agreement to provide any or all the Standard Services * and the provisions of Section 4.4 are not applicable, then TTG shall * . |
- 6 -
* CONFIDENTIAL TREATMENT REQUESTED
| 5. | Representations and Warranties |
| 5.1 | TTG warrants and represents (i) that the Software, the Products, and any Enhancements, Modifications and Improvements thereto (collectively hereinafter, the “System”) shall function and perform in accordance with all documentation therefor provided to User, the Specifications applicable thereto, and the terms of this Agreement, including the Exhibits hereto; (ii) that: (a) as of the Effective Date, it has agreements in place with each GDS identified in Section 2.4 above, which allow it to carry out and complete the activities contemplated hereunder; and (b) it has fully tested and has in production interfaces to each such GDS; (iii) it has all necessary rights, licenses and approvals required to perform its obligations hereunder and to operate and provide the System and all other products and services provided hereunder to User in accordance with this Agreement; (iv) neither the System or any service provided by TTG hereunder to User, nor any portion or use thereof in accordance with this Agreement, will infringe upon or violate any patent, copyright, trade secret or other proprietary or personal right of any third party; (v); TTG’s performance hereunder will be rendered using sound, professional practices and in a competent and professional manner by knowledgeable, trained and qualified personnel; (vi) all obligations owed to the third parties with respect to the activities contemplated to be undertaken by TTG pursuant to this Agreement are or will be fully satisfied by TTG so that User will not have any obligations (other than obligations set forth in this Agreement) with respect thereto; (vii) TTG’s obligations hereunder are not in conflict with any other TTG obligations or agreement (in writing or otherwise) with any third party; (viii) TTG will comply with all applicable foreign, federal, state and local laws, rules and regulations in the performance of its obligations hereunder; (ix) TTG will comply with User’s Privacy Policy, Internet Customer Privacy Statement and Web Site Rules and Regulations, as the same are posted from time to time on the User website, in the performance of its obligations hereunder; (x) TTG will not otherwise commit any act of willful or grossly negligent misconduct that results in a breach of a right of privacy; and (xi) at all times during the term of this Agreement, TTG will comply with the User Security Protocol set forth in Exhibit D in the performance of its obligations hereunder; and (xii) at all times during the term of this Agreement, TTG shall have either through its own direct agreements with all GDS providers or indirectly through the agreements of its affiliated companies with all GDS providers, all of the rights necessary to provide all of the Standard Services and perform all TTG’s obligations hereunder. |
| 5.2 | TTG further represents and warrants that the System shall provide accurate results using data having date ranges spanning the twentieth (20th) and twenty-first (21st) centuries (e.g., years 1900-2100). Without limiting the generality of the foregoing, TTG warrants that the System shall (a) manage and manipulate data involving all dates from the 20th and 21st centuries without functional or data abnormality related to such dates; (b) manage and manipulate data involving all dates from the 20th and 21st centuries without inaccurate results related to such dates; (c) have user interfaces and data fields formatted to distinguish between dates from the 20th and 21st centuries; and (d) represent all data related to include indications of the millennium, century, and decade as well as the actual year. |
| 5.3 | TTG will not be liable to User for any claim or defect arising from or based upon (i) any alteration or modification by User of the Software; or (ii) the compilation of User Data and submission to User to the extent such compilation and submission are conducted strictly in accordance with User’s instructions and the terms hereof; or (iii) except with respect to (x) TTG’s obligation to maintain at all times during the terms of this Agreement all of the rights, necessary to provide the Standard Services and perform all of its obligations hereunder, and (y) the obligations of TTG to comply with the requirements established in Exhibits D and F hereof, any other cause beyond the control of TTG or its affiliated companies. |
| 5.4 | EXCEPT AS EXPRESSLY PROVIDED IN THIS SECTION 5, NO EXPRESS OR IMPLIED WARRANTY IS MADE BY TTG WITH RESPECT TO ANY SERVICE, PRODUCT, SOFTWARE RELEASE, DATA COMPILATION OR ANY OTHER MATTER, INCLUDING, WITHOUT LIMITATION, ANY IMPLIED WARRANTIES OR CONDITIONS OF |
- 7 -
| MERCHANTABILITY, SATISFACTORY QUALITY OR FITNESS FOR A PARTICULAR PURPOSE. |
| 6. | Limitations of Liability |
| 6.1 | BOTH PARTIES AGREE THAT THE TTG’S LIABILITY (UNDER BREACH OF CONTRACT, NEGLIGENCE, STRICT LIABILITY OR OTHERWISE), IF ANY, FOR ANY DAMAGES RELATING TO THIS AGREEMENT SHALL NOT INCLUDE CONSEQUENTIAL, INCIDENTAL, INDIRECT, SPECIAL OR OTHER DAMAGES OF ANY KIND, INCLUDING LOSS OF PROFITS, EVEN IF TTG HAS BEEN ADVISED OF THE LIKELIHOOD OF THE OCCURRENCE OF SUCH DAMAGES. |
| 6.2 | BOTH PARTIES AGREE THAT USER’S LIABILITY (UNDER BREACH OF CONTRACT, NEGLIGENCE, STRICT LIABILITY OR OTHERWISE), IF ANY, FOR ANY DAMAGES RELATING TO THIS AGREEMENT SHALL BE LIMITED TO ACTUAL DAMAGES, SHALL NOT, EXCEPT IN THE CASE OF A BREACH BY USER OF ITS OBLIGATIONS UNDER SECTIONS 3.2, 3.3, 3.4 OR 3.5 HEREOF, EXCEED AMOUNTS PAID BY USER DURING THE TERM HEREOF, AND SHALL NOT INCLUDE CONSEQUENTIAL, INCIDENTAL, INDIRECT, SPECIAL OR OTHER DAMAGES OF ANY KIND, INCLUDING LOSS OF PROFITS, EVEN IF USER HAS BEEN ADVISED OF THE LIKELIHOOD OF THE OCCURRENCE OF SUCH DAMAGES. |
| 7. | Indemnification |
| 7.1 | TTG agrees to defend, indemnify and hold harmless User and the Affiliated Travel Agencies, and each of their respective directors, officers, employees and agents from and against any and all third party claims, demands, liabilities, losses, costs, damages or expenses, including reasonable attorneys’ fees and costs of settlement, resulting from or arising out of: (i) the System or any portion thereof or the use of the System or any portion thereof actually or allegedly infringing or violating any patents, copyrights, trade secrets, licenses, or other property rights of any third party, (ii) any breach of TTG’s representations and warranties herein; (iii) the failure of TTG to comply with the User Security Protocol set forth in Exhibit D hereto or the User Privacy Principles; or (iv) the failure of TTG to comply with its obligations under any and all laws, rules, or regulations applicable to TTG or the services or Products provided hereunder. |
| 8. | Term and Termination |
| 8.1 | This Agreement and the obligations hereunder will commence on the Effective Date and will continue for a period of five (5) years (the “Initial Term”) unless terminated as provided herein, and shall be renewable automatically for two consecutive one year periods (each such one year period a “Renewal Term”), unless User shall provide to TTG written notice of its intention not to renew at least sixty (60) day prior to the conclusion of the Initial Term or the first Renewal Term, as the case may be. |
| 8.2 | Either party may terminate this Agreement and the rights granted herein if the other party breaches any of the provisions of this Agreement or the Standard Services or Software do not meet User’s requirements, as a result of market conditions referred to in 2.6 above and (i) fails to remedy such breach within thirty (30) days after receiving written notice thereof, or (ii) provided the breach does not relate to a monetary obligation, fails to (a) commence a good faith action to remedy such breach within thirty (30) days after receiving written notice thereof, and (b) diligently pursue such action to conclusion within sixty (60) days after receiving written notice thereof. Termination of this Agreement does not constitute either parties’ exclusive remedy for breach or non-performance by the other party and each party is entitled to seek all other available remedies, both legal and equitable, including injunctive relief. Notwithstanding the foregoing, a dispute regarding amounts payable by User pursuant to this Agreement shall not constitute a breach hereof so long as User pays TTG all undisputed amounts owed hereunder. |
- 8 -
| 8.3 | Should either party (1) admit in writing its inability to pay its debts generally as they become due; (2) make a general assignment for the benefit of creditors; (3) institute proceedings to be adjudicated a voluntary bankrupt; (4) consent to the filing of a petition of bankruptcy against it; (5) be adjudicated by a court of competent jurisdiction as being bankrupt or insolvent; (6) seek reorganization under any bankruptcy act; (7) consent to the filing of a petition seeking such reorganization; or (8) have a decree entered against it by a court of competent jurisdiction appointing a receiver, liquidator, trustee, or assignee in bankruptcy or in insolvency covering all or substantially all of such party’s property or providing for the liquidation of such party’s property or business affairs; then, in any such event, the other party, at its option and without prior notice, may terminate this Agreement effective immediately. |
| 8.4 | Upon termination of this Agreement for any reason, TTG’s obligation to provide the services hereunder pursuant to the terms and at the prices set forth herein shall, upon User’s request, continue for a period up to sixty (60) days and shall thereafter immediately cease. Irrespective of whether User requests services during a Transition Period, TTG shall cooperate and provide such assistance as is necessary to transfer the services provided hereunder to another vendor or to User, and TTG shall be compensated for these efforts in accordance with Section 4.4 hereof; provided, however, if termination results from the breach of this Agreement by User or pursuant to Section 8.5 hereof, User shall pay in advance for services during the Transition period at TTG’s then standard rates TTG will be responsible for submitting to User the data compilation for the portion of the month up to and including the effective termination date and for the duration of the transition period, if any. |
| 8.5 | Either party may, at its option, after one year, terminate this Agreement upon 90 days written notice if User’s business is changed or modified and provided further that User no longer has a requirement to have the services provided for under this Agreement. The parties further agree that only in the event of a termination for convenience by User in accordance with this Section 8. 5, User shall not obtain the services provided for in this Agreement from any third party or have these services performed by User or any of User’s subsidiaries or affiliates for the remainder of the Initial Term. |
| 8.6 | The provisions of Sections 3, 5, 6, 7 and 8 hereof survive the termination of this Agreement. |
| 8.7 | TTG agrees to put object code and source code for the Software, Enhancements, Modification sand Improvements thereto, as well as the documentation therefor, and shall include all other materials necessary or appropriate to create, provide, operate and maintain all of the Standard Services, in escrow with an independent third party escrow agent located in the United States, acceptable to User, which acceptance shall not be unreasonably withheld (“Escrow Materials”). The parties shall enter into an escrow agreement substantially in the form attached hereto as Exhibit “G”. |
| 9. | Solicitations |
| 9.1 | User and TTG agree that during the term of this Agreement and for a period of one (1) year thereafter, neither User, with respect only to its Corporate Services Division, nor TTG will, directly or indirectly, recruit or solicit any person known to it to be an employee of the other party and involved in the provision or supervision of the Standard Services without the prior written consent of the other party. |
| 10. | General |
| 10.1 | This Agreement, including the Exhibits attached hereto, represents the entire understanding and agreement between the parties, and supersedes any and all previous discussions and communications. No employee or agent of TTG and no distributor for TTG is authorized to make any additional representations or warranties related to the services provided hereunder or the Software. Any subsequent amendments and/or additions hereto are effective only if in writing and |
- 9 -
| signed by both parties. TTG may assign any of its rights or duties under this Agreement with the prior written consent of User, such consent not to be unreasonably withheld or delayed. User may also assign this Agreement to any of its affiliates, provided that any such assignment shall not release User from its obligations under this Agreement. Subject to the foregoing limitation on assignment, this Agreement is binding upon and inures to the benefit of the successors and assigns of the respective parties hereto. |
| 10.2 | This Agreement is to be interpreted in accordance with the laws of the State of New York. It is understood and agreed that the parties will use their best endeavors to amicably resolve any dispute or difference arising from this Agreement. |
| 10.3 | Headings of paragraphs in this Agreement are inserted for convenience only, and are in no way intended to limit or define the scope and/or interpretation of this Agreement. |
| 10.4 | The failure of either party at any time to require performance by the other party of any provision hereof is not to affect in any way the full rights of such party to require such performance at any time thereafter, nor is the waiver by either party of a breach of any provision hereof to be taken or held to be a waiver of the provision itself or any future breach. No waiver shall be effective unless made in writing. |
| 10.5 | The parties hereto are independent contractors, and nothing in this Agreement is to be construed to create a partnership, joint venture, or agency relationship between TTG and User. |
| 10.6 | If any part, term, or provision of this Agreement is held to be illegal, unenforceable, or in conflict with any law of a federal, state, or local government having jurisdiction over this Agreement, the validity of the remaining portions or provisions are not be affected thereby. |
| 10.7 | Any notice given pursuant to this Agreement is to be in writing and is to be given by personal service or by first class mail, postage prepaid to the addresses appearing at the beginning of this Agreement, or as changed through written notice to the other party. Notice given by personal service is to be deemed effective on the date it is delivered to the addressee, and notice mailed is to be deemed effective on the fifth (5th) day following its placement in the mail addressed to the addressee. |
| 10.8 | It is the intent of the parties to enter into other agreements relating to TRX, Inc. (“TRX”) providing additional services to User including, but not limited to, corporate online fulfillment services (“OFS”) products, back office processing and MIS systems. The parties shall negotiate in good faith during the next twelve (12) months, regarding such additional agreements. These agreements may include, among other provisions, a joint venture in reference to OFS corporate services for User corporate clients as well as providing for warrants and/or equity participation by User in TRX, Inc. If within the time period specified above the parties are unable to negotiate additional agreements satisfactory to both parties, hereof, User will have, upon written notice to TRX, the right to re-negotiate the price terms or terminate this Agreement. |
| 10.9 | Insurance requirements shall be a subsequently mutually agreed by the parties. |
| 10.10 | The parties shall act reasonably and in good faith to reach agreement with respect to any item or matter herein to be determined or established upon the mutual agreement of the parties. |
| 10.11 | All rights and licenses granted under or pursuant to this Agreement by TTG to User shall be deemed, for purposes of the United States Bankruptcy Code (the “Code”) to be licenses to rights to “intellectual property” as defined under the Code. TTC agrees that User, as Licensee of such rights under this Agreement, shall retain and may fully exercise all of its rights and elections under the Code. TTG further agrees that in the event of commencement of bankruptcy proceedings by or against TTG, User shall be entitled to retain all of its rights under this Agreement. If TTG files Chapter 11 or Chapter 7 bankruptcy or ceases its business operations without a successor, then |
- 10 -
| TTG shall grant User an irrevocable (until TTG emerges from Chapter 11 bankruptcy), perpetual (until TTG emerges from Chapter 11 bankruptcy), worldwide license to use only internally in furtherance of the purposes of this Agreement, the Escrow Materials (until TTG emerges from Chapter 11 bankruptcy) to the Software and would thereby authorize any Escrow Agent under this Agreement to release such Escrow Materials (until TTG emerges from Chapter 11 bankruptcy) at which time User will return all Escrow Materials to the Escrow Agent (pursuant to the Escrow Agreement set forth in Exhibit G. Except for a release pursuant to Chapter 7 bankruptcy or for ceasing business operations without a successor, the obligations to continue to pay the fees specified hereunder shall continue. |
| 11. | Joint Oversight Committee |
| 11.1 | JOC Procedures. The following representatives will comprise a joint oversight committee (the “JOC”) which will meet at least quarterly. The functions of such committee, among other things, will be to review and analyze the performance of the parties based on the service performance standards specified in this Agreement. |
| TTG Designee: |
TTG Account Representative |
|||||
| User Designee: |
User Account Representative |
If a JOC Member resigns or leaves its employer, the party with a vacancy will promptly appoint a replacement.
| 11.2 | Management Representatives |
Each party hereby appoints the following individual as its Management Representative for purposes of this Agreement:
| TTG: |
Xxxxx Xxxxxxxx |
|||||
| User: |
Xxxxxxx Xxxxxxxx |
If a Management Representative resigns or leaves its employer, the party with a vacancy will promptly appoint a replacement. If either party fails to designate a Management Representative at its own initiative, it shall do so within three business days of a written request from the other party to do so.
| 12. | Dispute Resolution. |
| 12.1 | Initial Procedures. The parties shall make all reasonable efforts to resolve all disputes without resorting to litigation. If a dispute arises between the parties regarding the determination of the appropriate response to a change in technology, cost or services pursuant to Section 2.6 hereof (“Market Conditions Dispute”), the JOC Representatives will attempt to reach an amicable resolution. If either JOC Representative determines that an amicable resolution cannot be reached to a Market Conditions Dispute, such JOC Representative shall submit such dispute in writing to each party’s Management Representatives, who shall use their best efforts to resolve it or to negotiate an appropriate modification or amendment. |
| 12.2 | Escalation. Except as otherwise provided in the termination provisions hereof, neither party shall be permitted, with respect to a Market Conditions Dispute, to exercise any other remedies until the later of (i) the date that either Management Representative concludes in good faith that an amicable resolution of the dispute through continued negotiation is unlikely, or (ii) thirty (30) days following the date that either party notified a Management Representative pursuant to Section 12.1. In the event the parties are unable to resolve such dispute in accordance with the procedures set forth in this Section 12, either party may terminate this Agreement upon written notice to the other party. |
- 11 -
| Travel Technologies Group, L.P. |
American Express Travel Related Services | |||||||||
| d/b/a Travel Technologies Group |
||||||||||
| By: |
Travel Technology, LLC |
Signed: |
/s/ Xxxxxxxx X. Xxxxxxxx | |||||||
| Its: |
General Partner |
Name: |
Xxxxxxxx X. Xxxxxxxx | |||||||
| Title: | Senior Vice President | |||||||||
| By: |
TRX, Inc. | |||||||||
| Its: | Member | |||||||||
| By: |
/s/ Xxxxx Xxxxxxx |
|||||||||
| Name: |
Xxxxx Xxxxxxx |
|||||||||
| Its: |
Executive Vice President | |||||||||
- 12 -
[Note to Client: Review Exhibit carefully as it contains important business terms]
EXHIBIT A
Services and Fees
| Quantity |
|
Fee | ||
| 1 | EnCoRRe™ Service Bureau A.1 |
* | ||
| For Period of * from Execution of Agreement |
* | |||
| CRS Screen Highlighter with Infolink and Southwest Direct1 |
* | |||
| Implementation Fee |
* | |||
| Minimum * usage and support fee |
* |
Payment Schedule
| Due at Contract Execution |
|||||
| Implementation fee |
$ | * | |||
| Due at start of production and processing |
$ | * | |||
| Total Implementation Fee |
* | ||||
| Usage and support fees, etc. |
See A.2 & scale A.3 |
| 1 | Unlimited licenses provided to User locations. Licenses must be renewed every 12 months, but shall in all events remain royalty free and shall be on terms not inconsistent with the terms herein. In the event of a conflict between the terms of such licenses and this Agreement, the terms of this Agreement shall control. User does installation. All training will take place in TTG’s Dallas facility. On-site support is available at the rates set forth in Exhibit E. |
| A.1 | Usage and support fee will be reduced to * User has processed * unique record locator numbers. |
| A.2 | Usage and support fees will be * based on actual number of unique record locator numbers for the first * after the Effective Date. Invoices are * . |
| A.3 | Beginning in the sixth month following contract signing, the * amount will represent the greater of the usage and support fees as calculated above or the * usage and support fee outlined as follows: |
| • Months 6 through 9: |
* | |||
| • Months 10 through 12: |
* | |||
| • Months 13 though contract termination: |
* | |||
| A.4 | User bears all responsibility for fees including, but not limited to, access, installation and maintenance of a GDS line. |
| A.5 | Telephone Support Fees in accordance with pricing and terms * . |
| A.6 | Client Customization Fees in accordance with pricing and terms * . |
- 13 -
* CONFIDENTIAL TREATMENT REQUESTED
Exhibit B
EnCoRRe™ Service Bureau
The EnCoRRe Service Bureau provides an efficient and effective plan to successfully implement a universal mid-office quality assurance solution to enhance the file finishing of all PNRs generated by the User world-wide, regardless of GDS used. The system is designed to be scaleable enough to accommodate an implementation of any size.
Utilization of a Service Bureau and TTG’s staff of trained mid-office experts, means there would be no need for the User staff and train personnel to execute software implementation at multiple regional sites. The exact same set of routines being run on all User’s PNRs, there can be a single uniform standard of reservation finishing delivered to all User’s clients. Having all PNRs in a centralized location also provides User a complete source for data mining to maximize vendor usage, identify savings opportunities, and more. Reports breaking out data will be available via the Internet, giving User’s managers access to this data at any time. Ramp-up time is no longer an issue, as users can take advantage of numerous routines already available in the system.
EnCoRRe’s powerful Oracle database allows the mid-office quality assurance system to work on all major GDSs simultaneously. EnCoRRe can take a single set of business rules and apply them to reservations booked by multiple travel agencies, across the globe. This advanced functionality provides large, multi-national corporations and major travel agencies with the potential to reap significant savings in travel through universal policy-compliant testing of PNRs and maximized efficiency in mid-office.
EnCoRRe is an “ultimately configurable” enterprise solution to current mid-office issues. Data generated by EnCoRRe routines provides global corporations with a unified and consistent service for back-office usage and reconciliation. The strength offered by the system’s Oracle database also provides a handy and accessible data depository for agencies and corporations.
EnCoRRe performs virtually all CRS processes, including file finishing and ticketing. From a skeleton reservation it will perform all the necessary functions normally done by a travel agent. EnCoRRe shall handle remarks, reporting information, exception rules, internal and external customer documentation, and more. The system can also schedule ticketing and complete that process. It is designed to work directly with an automated booking system to communicate any issues that come up directly to the traveler via E-mail, fax, or PDA device, and run the tickets accordingly, thus creating a totally automated environment.
EnCoRRe will generate web-based reports to aid both clients and managers. Using Business Objects software, these reports will be the result of the finest mid-office data mining available in the travel industry today. EnCoRRe will be able to provide:
| • | Ad-hoc reporting |
| • | A high-security standard |
| • | Automatic scheduling of reports |
| • | Automatic publishing and distribution of reports |
| • | Customization to accommodate any client |
| • | Graphing |
| • | Branching by division and sub-division |
- 14 -
Exhibit B Con’t
Product Description
CRS Screen Highlighter with ResNotes™
CRS Screen Highlighter® with ResNotes is a utility loaded on the GDS LAN or stand alone PC, which allows the travel agency to designate colorful, attention-grabbing attributes and special messages to passenger name records (PNRs) and traveler profiles. Highlighter can help assure that important quality control messages and traveler profile information are never again ignored or overlooked by busy travel agents. Some capabilities of the system are:
| • | Identifies CEO, VIP, and frequent flyer numbers |
| • | Calls attention to “last day to purchase” fares |
| • | Highlights penalties and restrictions |
| • | Can keep track of travelers who have saved non-refundable tickets |
| • | Reminds agents of visa requirements |
PNR messages from supervisory or support personnel as well as messages from manual or automated quality control sources such as the EnCoRRe system can be highlighted for special notice and action!
Highlighter runs on all Windows-based GDS. The program contains a library of highlights, which can be edited or deleted as the user elects. New highlights are added using a “point & click” set-up program and assisted by onscreen “help” balloons. The user can select from a library of sound (WAV) files, color options, fonts-and attributes supported by their Windows environment. The system provides weekly suggestions for effective use.
Highlighter is takes up a small amount of memory on the PC file server and should not slow down “screen refresh” or response time. The program enables features to be turned off for particular travel counselors as needed.
ResNotes allow the user to “tag” complete messages to the GDS text for customer service advice, proprietary rate and fare information or additional product or support information.
Highlights or ResNotes messages can be added or changed by supervisory personnel from any workstation. Customer service staff can also input information that can be accessed instantly and automatically by the travel counselor at the time a reservation is being made.
INSTALLATION REQUIREMENTS:
The following items should be present and ready at customer site prior to arrival of the TTG installer:
| • | At least one AT (80386 or preferably 80486) class IBM compatible PC or an operational GDS-supplied LAN made up of IBM compatible PCs which meets the following minimum criteria: |
| • | 8MB Ram |
| • | Windows 3.1 or Windows for Workgroups installed. |
| • | One high density floppy disk drive, either 3.5” or 5.25” (must be specified) |
| • | Minimum 40MB free file server disk space |
| • | Color graphics monitor |
- 15 -
Exhibit B Con’t
InfoLink™
The primary function of this product is to be able to share / copy / etc. files (primarily CRS Screen Highlighter® files) over TCP/IP connections to the Internet.
InfoLink capabilities and features include:
| • | Allows the user/travel manager to update Highlighter files and then automatically transfer them to all their users via the Internet. This will allow adds and updates which will synchronize files at the counselor level. |
| • | The receptacle for all the file information (the Server) can be hosted at TTG or maintained at the user/travel manager’s pre-determined location. |
| • | When a company administrator (example: one machine at a User agency location) has been assigned, they will make the file adds/updates and set up groups of users who have rights to get those files. This information goes to the Server (at TTG or other host site) via the Internet. |
| • | The end users (example: the Highlighter 4 Admin machines at various locations) will automatically call or “poll” the Server (at TTG or other host site) via the Internet. Once access is gained, they can see if there are adds/updates that they have rights to, collect those files, and put them in the correct shared directory. |
| • | At this point, counselor sets will look to the Highlighter 4 Admin’s machine for any highlight updates they have been given rights to get. |
INSTALLATION INFORMATION & REQUIREMENTS:
The minimum system hardware and software requirements for InfoLink include:
| • | Intel Pentium or compatible running at 60 MHz or more |
| • | VGA compatible display (16 colors or more) |
| • | 16 MB of free hard disk space |
| • | 16 MB of RAM |
| • | One 3.5 inch floppy drive and/or a CD ROM drive (for installation) |
| • | Windows 95 or Windows 98 |
| • | A mouse or other pointing device |
| • | Internet connectivity (access to The Internet) |
This requires a non dial-up connection to the Internet using TCP/IP protocol. If a firewall exists, port 1088 and port 1090 must be open unrestricted. A later version will not have the restriction of ports 1088 and 1090.
- 16 -
Exhibit B Con’t
Southwest Direct™
Southwest Direct is a Windows application that allows agents direct access to the Southwest Airlines booking system via dedicated modem and phone line, which is shared on the Apollo Focal Point network. It enables the agent to shop real time availability, book flights, issue electronic tickets, and will move the booking into the Apollo system automatically.
System Requirements: The minimum requirement for Southwest Direct is an IBM-compatible 386 computer with 4 megabytes of RAM, running Windows 3.0, 3.1 or Windows for Workgroups. Additional RAM will increase system performance. In order to fully utilize all the features of Southwest Direct, the program should be run in a network environment. For optimal performance, an IBM-compatible 486/33 or greater computer with a fast video card and 4 megabytes of RAM or more of RAM is recommended.
Modem Requirements: For a modem to work with Southwest Direct, it must have 9600 bps or better speed and be a Xxxxx compatible modem. Use of a 16550 Universal Asynchronous Receiver/Transmitter (UART) is recommended.
- 17 -
Exhibit C
Service Level Agreement
Hours of Operation
| • | The TTG Service Bureau is staffed 24 hours a day, Monday through Friday. Weekends will be staffed * hours per day at an agreed-upon range of hours * . |
| • | Weekend support after the agreed-upon range of hours is provided via pager and calls will be returned * . |
| • | The TTG Service Bureau will be brought down no more than once monthly for regular maintenance. |
| • | All scheduled downtime will be communicated to the customer in advance and at agreed upon dates and times. |
| • | TTG shall maintain up time for the System at * . For unscheduled down time greater than * per month, TTG will reimburse by credit against actual xxxxxxxx, the number of unique record locator numbers not processed during the time at which the system is unavailable for use. |
Support Services
| • | Failures identified as not related to, or caused by TTG products included in the agreement, but inhibiting the use of, will be the responsibility of TTG to manage to resolution |
| • | The TTG Service Bureau will be the first point of contact for Support issues identified by the User’s Technical Help Desk. |
| • | TTG will provide monthly reporting based on issues opened and system availability |
Processing Times
| • | AMEX TO PROVIDE VOLUME ESTIMATES: TTG will ensure that EnCoRRe will process * of the unique record locator numbers on queue in * or less for all “rush queues”, as that term is generally understood in the industry, when CRS access is available and volume levels do not exceed * of the scheduled volume levels described on Exhibit D hereto. |
| • | AMEX TO PROVIDE VOLUME ESTIMATES: TTG will ensure that EnCorre will process * of the unique record locator numbers on queue in * or less for all “work queues”, as that term is generally understood in the industry, when CRS access is available and volume levels do not exceed * of the scheduled volume levels described on Exhibit D hereto. |
Implementation
| • | TTG will provide training to User Support and Training organizations as part of this agreement at no additional cost. Training is to consist of: |
| • | Prior to first implementation, * training (Train the Trainer) sessions of not less than 10 members per class at either the TTG facility, or a facility to be mutually agreed upon by TTG and User. |
| • | Quarterly Train the Trainer sessions of not less than * classes at the TTG facility. |
| • | Additional on-site training provided to User at the Users expense with 30 day written notice. |
| • | TTG will provide an implementation plan acceptable to User for EnCoRRe, CRS Screen Highlighter, Infolink and Southwest Direct. User will need to designate a group of contacts to interface with the dedicated TTG staff to facilitate implementation, on-going technical integration and application of the products and services. |
| • | TTG will develop and program a standard routine library of unique record locator number checks and finishing routines acceptable to User that will be in production by the agreed implementation date. |
| • | At User’s expense, TTG will develop and program an agency specific routine library of unique record locator number checks and finishing routines acceptable to User and accessible only by the User. |
- 18 -
* CONFIDENTIAL TREATMENT REQUESTED
| • | TTG reserves the right to delay programming any new related EnCoRRe routines if the request is received within * business days of implementation. |
| • | TTG reserves the right to delay the programming of any agency specific EnCoRRe requests received prior to or during implementation until TTG and User are satisfied that the existing routines are functioning properly. |
| • | TTG will complete EnCoRRe requests for new programming and modifications of existing programming received after implementation as follows: |
| • | Within * of the written request for each routine that can be developed in Quality Check/Reservation Editor. |
| • | Within * business days if the routine requires Power CoRRe programming. |
| • | TTG may advise the agency contact that programming efforts will take longer, but not to exceed * business days. |
| • | TTG will provide the programming within the time periods referred to except if the parties believe in the exercise of reasonable judgement that the time periods have to be extended. Under such circumstances the parties will agree on a reasonable timetable which is acceptable to both parties. |
Staffing
| • | Strategic Partner — TTG will assign an individual to serve as lst point of contact for designated senior level User contacts. The Strategic Partner is responsible for coordinating implementation, on-going technology integration and application of TTG products and services. |
| • | The Application Service Analysts (ASA) – TTG will assign a mutually agreed upon number of implementation staff which will act as: |
| • | 1st point of contact for all EnCoRRe programming requests, PNR processing requests and any other EnCoRRe related issues for a group of designated customer contacts. |
| • | 1st point of contact for all CRS Screen Highlighter installation, implementation, programming requests, PNR processing requests and any other CRS Screen Highlighter related issues for a group of designated customer contacts. |
| • | 1st point of contact for all Southwest Direct installation and implementation requests and Southwest Direct related issues for a group of designated customer contacts. |
| • | Post-implementation, the ASA(s) will act as second level support for a group of designated customer contacts. |
| • | The ASA(s) is a TTG employee and therefore is governed by TTG employee policies and procedures. |
| • | TTG’s ASA will advise customers when additional capacity is required to keep agreed upon service levels. |
| • | The ASA will be scheduled to work 8 hours a day, Monday through Friday. |
| • | If the ASA is not available, the TTG Service Bureau staff will be able to assist with most non-programming, PNR turnaround-time queries. |
| • | The ASA is responsible for the development, programming, management and implementation of the EnCoRRe routine library. |
| • | The ASA will occasionally review the entire routine library to determine opportunities to increase the performance of existing EnCoRRe routines. |
On-site Support
| • | TTG will assist with on-site implementation of CRS Screen Highlighter at reservations centers with 10 or more GDS workstations. |
| • | TTG will bear the cost of providing on-site support within * to resolve site specific issues not correctable by TTG remote support Once on-site, if the parties determine the problem is with the User’s hardware or LAN configuration and not with the TTG software, User will bear the costs associated with the on-site visit. |
| • | TTG will travel to an agency site to assist with performance issues if the agency technology contact has worked directly with TTG and remote troubleshooting techniques have been exhausted. |
- 19 -
* CONFIDENTIAL TREATMENT REQUESTED
| • | If the parties determine that the problem is due to functionality that is not performing as documented, TTG will be responsible for travel expenses incurred by ASA. |
Travel Expenses
| • | User is responsible for travel expenses of TTG representative in accordance with User’s policies as in existence from time to time. |
| • | All travel related expenses to be billed will require pre-approval by the User. |
- 20 -
Exhibit D
Security Standards/Protocol
[Exhibit D-1]
American Express Travel Related Services Company
INFORMATION SECURITY REQUIREMENTS
Vendor shall allow both scheduled and unscheduled on-site inspections by Amex. Vendor agrees to comply with all reasonable recommendations that result from such inspections.
Vendor shall maintain an adequate level of physical security controls over the facility including, but not limited to, appropriate alarm systems, access controls (including off-hours controls), visitor access procedures, security guard force, fire suppression, video surveillance, and staff egress searches.
Vendor shall maintain an adequate level of data security controls including, but not limited to, logical access controls including user sign-on identification and authentication, data access controls (e.g. password protection of Amex applications, data files, and libraries), accountability tracking, anti-virus software, secured printers, restricted download to disk capability, and provision for system backup.
Vendor shall maintain an adequate level of controls in configuring and operating voice systems, especially as regards fraudulent use of 800 numbers, PBX switches, and other voice networks.
Vendor shall maintain an adequately secured and environmentally controlled computer room facility, with access restricted to only approved staff
Vendor shall document and provide to Amex copies of all internal security policies and standards (including escalation procedures for non-compliance) for Amex review upon execution of this contract or amendment.
Vendor shall provide to Amex a copy of the most recent third party data processing audit or review, as conducted by the Vendor’s external auditors. In addition, Vendor shall provide to Amex copies of any related data processing audits from their internal auditors.
As required by the Amex Customer Privacy Principles, vendor acknowledges that it has been advised of same and agrees to adopt those particular rules and practices that are jointly deemed appropriate by Amex and Vendor.
Vendor shall have a documented sensitive trash disposal program at each location. Sensitive trash is defined as any material that contains Amex proprietary data/information including, but not limited to, cardmember and service establishment data/information.
Vendor shall ensure at each site that no shared environments exist with other businesses for all WANs, LANs, network connections, dial-up connections, DASD, distributed systems, or any other computer systems and that appropriate data controls are implemented.
Vendor shall maintain a set retention period for all security data or events (i.e., reports).
Vendor shall provide to Amex a copy of its disaster recovery plan for each location handling Amex business, including the location of its recovery sites. All critical applications supporting Amex business, as jointly determined by Amex and Vendor, will undergo a valid and documented test of the disaster recovery plan at least annually. Vendor shall provide a summary of the results of these tests to Amex.
- 21 -
Vendor shall execute background checks on all employees assigned to work on Amex businesses and provide a listing of such employees to Amex on a monthly basis. Such background checks will include drug screening and checks for criminal activity, as well as credit history checks where appropriate.
Vendor agrees to cooperate fully with Amex in any investigations of possible fraudulent activity by Vendor’s employees.
Each Vendor employee who is granted direct access to any Amex system(s) shall sign both the confidentiality agreement and the workstation rules and regulations document attached hereto and abide by all terms contained therein. All Vendor employees accessing Amex’s systems via a dial-up connection must utilize Amex-owned or leased equipment.
Vendor employees may only access, make maintenance changes to, or perform financial adjustments on those Amex accounts required by their job. In addition:
| 1. | They may not access their own account for any reason. |
| 2. | They may not access another Vendor employee’s account if they have personal knowledge that the account holder is a Vendor employee. |
| 3. | They may not access an account held by anyone they know outside of work. |
| 4. | They may not access any account that they are not required to access. |
Vendor management shall retain sole responsibility for granting access to Amex systems (“Vendor Security Administrators”) for all Vendor employees and users.
Vendor Security Administrators shall be authorized and approved by Amex.
Vendor Security Administrators shall document all procedures for user ID requests, transaction authorization, and system use.
Vendor Security Administrators shall review all violation reports and take action as necessary to prevent unauthorized access and use of Amex systems.
Vendor agrees that all of its employees who are users of any Amex system will be fully informed of, and monitored for adherence to, all information security requirements listed in this addendum.
Vendor will encourage its employees to report suspected violations of access to Amex systems or of any of the Customer Privacy Principles to their management for investigation and action.
Vendor agrees that user IDs and passwords for Amex systems will be controlled as follows:
| 1. | * . |
| 2. | * . |
| 3. | * . |
| 4. | * . |
| 5. | * . |
| 6. | * . |
Vendor understands that all access to Amex systems may be monitored at will by Amex for compliance with these information security requirements.
- 22 -
* CONFIDENTIAL TREATMENT REQUESTED
Vendor agrees to document consequence management policies for violations of these information security requirements.
Vendor shall ensure all workstations which allow access to Amex data are segregated and are equipped with appropriate access control, including password protection and [*} data backup procedures, virus protection, and are software compliant. A screen saver requiring entry of a password is required for all PC workstations that are capable of displaying Amex data and is an acceptable alternative to logging the user off the system. All such PCs must be positioned to face away from any common areas of the facility.
- 23 -
* CONFIDENTIAL TREATMENT REQUESTED
Confidentiality Agreement
The nature of your work at (“ ”) for American Express Travel Related Services Company, Inc., and its affiliates (collectively the “Company”) involves your access to trade secrets, confidential information, files, records and forms of the Company (collectively “Confidential Information”). Confidential Information includes, but is not limited to, any information relating to the Company organizational structure, marketing philosophy and objectives, project plans, data models, strategy and vision statements, business initiatives, business requirements, systems design, methodologies, processes, competitive advantages and disadvantages, financial results, product features, systems, operations, technology, customer lists, customer account information, products development, advertising or sales programs and any other information which would give the Company an opportunity to obtain an advantage over its competitors or which the Company is ethically obligated to protect from unauthorized sources. None of such information shall be deemed to be in the public domain.
The Company desires to protect its Confidential Information and therefore requires that you agree, as a condition of your performing services for the Company pursuant to the Company’s agreement with to safeguard all Confidential Information and not to reveal Confidential Information to any third party (including, without limitation, at conferences, seminars, meetings of professional organizations or by publication in journals or granting of interviews to journalists and other members of the news media) or use Confidential Information for your own benefit or the benefit of any third party, except to the extent necessarily required for the performance of your services.
You agree not to discuss Confidential Information of the Company in public places.
You agree that any work product produced or developed by you in the performance of your services for the Company shall be Confidential Information subject to this Agreement and such work product is, and shall remain, the property of the Company.
You also agree to help safeguard the Company’s customers’ expectations of privacy by exercising diligence and care in the handling of Confidential Information relating to them.
By signing below, you indicate that you understand the above terms and that, as a condition of performing services for the Company, you agree to adhere to them.
| Your Signature | ||||
| Printed Name | Date | |||
- 24 -
Workstation Rules And Regulations
As a part of your job, you will have access to various Amex Cardmember accounts. Following are the rules and regulations that govern that access; these must be followed in detail by every employee who is granted access.
| A. | ACCESS TO AMEX CARDMEMBER ACCOUNTS |
| 1. | You may not access your own account for any reason. |
| 2. | You may not access another employee’s account if you have personal knowledge that the account holder is an employee. |
| 3. | You may not access an account held by anyone you know outside of work. |
| 4. | You may not access any account that you are not required to access as part of your job responsibility. |
| B. | USE OF YOUR PASSWORD AND IDENTIFICATION NUMBER |
*
| C. | MONITORING |
All terminals are subject to monitoring and terminal monitoring may occur simultaneously with telephone monitoring. In addition, you should understand that all transactions in the system are recorded by the computer. Printouts listing all transactions by employee identification number and password are monitored on a regular basis.
These rules are extremely important. Any employee who willfully disregards these rules and regulations is subject to discipline, up to and including discharge from employment.
I have read and understand the above regulations and agree to comply with them.
| Vendor/Officer Signature | Printed Name | Date | ||||||
| Other Vendor Signature | Printed Name | Date | ||||||
- 25 -
* CONFIDENTIAL TREATMENT REQUESTED
[Exhibit D-2]
GLOBAL TECHNOLOGY STANDARDS
MINIMUM SECURITY BASELINE STANDARD
- 26 -
Table of Contents
| 1.0 SUMMARY |
28 | |
| 2.0 SCOPE |
28 | |
| 3.0 STANDARDS DESCRIPTION |
29 | |
| 4.0 EXCEPTION CRITERIA |
42 | |
| 5.0 COMPLIANCE MEASUREMENT |
43 | |
| 6.0 FREQUENTLY ASKED QUESTIONS |
43 | |
| 7.0 IMPLEMENTATION / MIGRATION SCHEDULE |
43 | |
| 8.0 STANDARDS RELATED INFORMATION |
43 | |
| 9.0 STANDARDS ENABLEMENT TEAM CONTACTS |
43 | |
| 10.0 LIST OF RECENT CHANGES |
44 | |
| 11.0 DEFINITIONS |
44 | |
| APPENDIX |
44 | |
- 27 -
| 1 | 1.0 Summary |
Information, and the technology used to support that information, has significant value to American Express. Both the information and the technology are subject to various threats that, if realized, could result in direct financial loss to American Express. In addition, financial loss may also occur due to indirect factors such as:
| • | Loss of customer confidence; |
| • | Embarrassment to the American Express reputation; |
| • | Loss of competitive position; |
| • | Degradation of employee productivity or morale; and |
| • | Failure to meet legal or regulatory requirements. |
To manage these threats, a minimum set of control requirements called the American Express Minimum Security Baseline (MSB) has been developed. It defines the minimum required sets of security features, mechanisms, and assurances that must be employed on systems which process, store, or communicate American Express information. This Security Standard, along with guidelines and procedures, has been developed to meet the Company’s requirements for confidentiality, integrity, accountability, and availability applicable to American Express systems, networks, and information. A risk assessment will be performed as required to further define the risk and magnitude of loss that could occur from inadvertent or deliberate destruction, alteration or disclosure of information and denial of service. Please refer to the Risk Assessment and Management Standard.
The MSB constitutes the minimum Information Protection controls that American Express will accept for the protection of American Express information. American Express information and associated American Express resources will be protected against unauthorized access, accidental or unauthorized modification, disclosure, or destruction in accordance with MSB requirements.
When implemented, the MSB requirements will provide the appropriate levels of Identification & Authentication, Authorization (Access Control), Accountability, Backup, and Physical Security necessary to protect American Express information.
It is the responsibility of the Business Unit Manager to assure that the MSB described in this document is implemented and maintained on a current basis. All new and revised technologies and business processes must incorporate the controls from this document before becoming operational. The responsible Business Unit Manager must prepare a Request for Deviation for business systems where MSB controls are not implemented. The justifications for not including MSB controls include cost, existing compensating controls in the system, or a management decision to accept the associated risk.
| 2.0 | Scope |
| 2.1 | Applicable Organizations |
This Standard applies to all components of American Express (AMEX), including all subsidiaries, affiliates, and any agents.
| 2.2 | Business Impact |
This Standard is deemed to be Xxxxx 0 priority. This Standard was established to meet AMEX strategies and goals relating to Information Systems Security throughout American Express. These strategies and goals address and incorporate methodologies to ensure AMEX’s compliance to regulatory and legal requirements. Failure to conform to this Standard will have significant impact on AMEX. Immediate migration to this Standard is required. “Immediate” is defined as within one year of this Standard’s issuance.
- 28 -
| 2.3 | Coverage |
This Standard covers all Information Systems (IS) environments operated by AMEX or contracted with a third party by AMEX. The term “IS environment” defines the total environment and includes, but is not limited to, all documentation, physical and logical controls, personnel, hardware (e.g., Mainframe, distributed, desktop, network devices), software, and information.
| 2.4 | Regulatory Issues |
This standard is intended to meet regulatory requirements.
| 2.5 | Inquiries |
For interpretations or questions, regarding this standard, contact your Regional Security Officer (RSO) or the Information Protection Group (IPG).
| 3.0 | Standards Description |
American Express MSB requirements are derived in part from the United States Government’s Trusted Computer System Evaluation Criteria (TCSEC) Controlled Access Protection (“C2”) requirements. These requirements have been modified to reflect current computer industry “Best Practices” and security considerations. This was done to ensure that American Express computing security requirements are compliant with globally-accepted standards for “trusted” systems.
The MSB is structured according to an eight part model. The figure below identifies the components of the model and depicts their relationship.
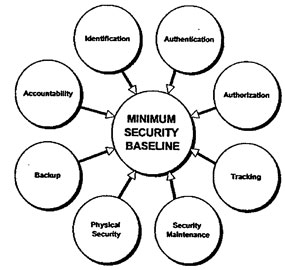
- 29 -
* CONFIDENTIAL TREATMENT REQUESTED
| 3.1 | Applying the Minimum Security Baseline |
The MSB control requirements must be applied consistently to all American Express information and technology. However, in some cases the impact of replicated controls across multiple environments may be inefficient and costly. To help reduce the redundancy, a series of technical standards have been produced. The objectives of these technical standards are to:
*
This process views information and technology as a composite. This single view approach can be applied to stand-alone and networked environments alike and identifies security interdependencies across technologies. The result is a cost effective and efficient implementation of one requirement across multiple technologies rather than implementation of redundant control solutions for each technology.
| 3.2 | Minimum Security Baseline Requirements |
The definition of each component of the MSB is as follows:
| 1. | Identification & Authentication—where each User of a system is required to be uniquely identified and authenticated to the system (usually by the required use of an individually-assigned User ID and password combination) to establish accountability. |
| 2. | Access Control—where the system is set up to assure that Users are only granted access to information and resources required to support their job function. |
| 3. | Accountability Tracking—where the system keeps track of selected security-relevant events (such as log-ins, log-outs, file accesses, etc.) and stores the audit trail information in a system-protected file in order to provide a means of accountability (also referred to as auditing). |
| 4. | Security Maintenance—is the process for establishing and maintaining a supporting infrastructure for the MSB. |
| 5. | Backup—is the process of producing a duplicate copy of information for the purpose of restoring that information at a later date (key issues are availability and continuity of information). |
| NOTE | #1: Backup must not be confused with the broader subject of Business Continuity Planning (BCP). See the Standard on Business Continuity Planning. |
| NOTE | #2: Backup is separate and distinct from record retention. See the Standard on Vital Records. |
| 6. | Physical Security - See Standard on Physical Security |
| 7. | Risk Assessment - See Standard on Risk Assessment and Management |
| 8. | Data Classification - See Standard on Data Classification Management |
| 9. | Illicit Code - See Standard on Illicit Code |
| 10. | Dial-Up/Remote Control - See Standard on Dial-Up/Remote Control |
- 30 -
* CONFIDENTIAL TREATMENT REQUESTED
| 11. | IS User Conduct - See Standard on IS User Conduct |
| 12. | Application Development - See Standard on Application Development |
| 13. | Network Security - See Standard on Network Security |
| 14. | Security Education & Awareness - See Standard on Security Education & Awareness |
| 3.3 | Identification and Authentication |
| 3.3.1 | Objective |
Identification is the process of uniquely distinguishing one User from another to establish accountability.
Authentication is the process of verifying the identity of a User. This can be accomplished by determining:
| • | What a User knows, e.g. * . |
| • | What a User has, e.g. * . |
| • | What a User is, e.g. * and/or |
| • | A combination of the above. |
The goals of Identification and Authentication are to:
| • | Establish the identity of a User; |
| • | Verify the claimed identity; and |
| • | Provide unique accountability for the actions that the User performs. |
| 3.3.2 | Identification and Authentication Requirements |
| • | Each User must be uniquely identified. For example, a system user ID must not be assigned to more than one person. |
| • | Each User must be identified and authenticated before performing any actions on the system. |
| • | After the User successfully completes the Identification and Authentication process, * . |
| • | The authentication process must be limited to * . |
- 31 -
* CONFIDENTIAL TREATMENT REQUESTED
| • | Identification and Authentication must both be completely processed by the system prior to displaying the failed attempt indicator. All messages associated with failed log-ins shall be non-descriptive. |
| • | Only the IPG administrator and/or an approved process can * . |
| • | * . |
| • | A single User identifier must not be permitted to have processes originating from * . For example, a user must not * . |
| • | Users employing Internetworking (any public network) to access American Express information and technology remotely, (e.g., dial-up via the public telephone network, LAN, WAN, Internet, or wireless networking), must use * . |
| • | A User identifier that has been inactive for a period of * . The intervention of an * . If an exception to this is required, for example an * . |
| • | User identifiers shall be purged from the system after * . |
| • | The following message must appear on all screens prior to any logos or banners, and before the initial Identification and Authentication process: |
THIS SYSTEM IS RESTRICTED TO AUTHORIZED USERS.
UNAUTHORIZED INDIVIDUALS ATTEMPTING ACCESS CAN BE PROSECUTED.
| • | All vendor supplied USERID’s must be * . Privileged vendor supplied USERID’s must be * . |
- 32 -
* CONFIDENTIAL TREATMENT REQUESTED
| 3.3.3 | Password and PIN Requirements |
| • | Authentication information, e.g., password or PIN, must never be disclosed to another User or shared among Users. |
| • | New or re-enabled User identifiers must be * . |
| • | Passwords must not be written down on printed documents, post-it notes, etc. * . |
| • | Passwords must be protected using * |
| • | The password must not * . |
| • | Passwords must have a maximum lifetime of * (Exempt from this control are * ). |
| • | The password change process must force re-authentication. The current password must be * . |
| • | A * is required to prevent * . |
| • | Passwords are required to be * . |
| • | Passwords must contain at least * . |
| • | A * is deemed acceptable and in compliance with the intent of this document. |
| • | * . |
| 3.3.4 | Recommended Password Guidelines |
The following are recommendations for selecting passwords:
| • | Passwords must be entered by means of * in a function key or hot button. |
| • | Passwords must not be the same as * . |
- 33 -
* CONFIDENTIAL TREATMENT REQUESTED
| • | Passwords must * . Avoid passwords that contain: |
| * |
| 3.3.5 | Digital Token Requirements |
| • | Authentication may be accomplished with a * . |
| • | A digital token * . |
| • | Digital tokens must be * . |
| • | Digital tokens * . |
| 3.4 | Access Control |
| 3.4.1 | Objective |
Access Control is the process of assuring that only properly approved users are granted access to information.
The goals of Access Control are to:
| • | Permit access to information and technology on a need-to-know, job function-related basis. |
| • | Ensure that users are prevented from gaining access to information and technology for which they are not authorized. |
- 34 -
* CONFIDENTIAL TREATMENT REQUESTED
| 3.4.2 | Access Control Requirements |
| • | Access to information and technology must be authorized only by * . |
| • | Access to information and technology must be on a need-to-know, job function basis. Users must only have the minimum access rights and privileges needed to perform a particular function or transaction. |
| • | Access rights specified by an individual User * . |
| • | At least annually, a review of User access rights to information and technology must be conducted by the Information Protection Group. Review of this information must be conducted by the business process owner with oversight by the IPG. |
| • | At least semi-annually, a review of User access to information and technology identified as High Risk in the Risk Assessment Process must be conducted by the Information Protection Group. |
| • | Access must be controlled to restricted information including: |
| • | Security commands, programs, utilities, and databases; |
| • | Program libraries; |
| • | Job or process execution statement files; |
| • | User authorization profiles; |
| • | Accountability tracking logs; and |
| • | Backup files containing any of the above. |
| • | * |
| • | Access to system documentation, e.g., application documentation, User manuals, etc., must be restricted on a need-to-know, job function basis. |
| • | The development, implementation, and maintenance of application software must be approved by the Business Owner, and must be in compliance with the MSB, as well as, the American Express Application Development Standard. |
| • | All purchased, commercial software must be approved by the Business Owner, and be licensed and implemented in such a way as to be in compliance with the MSB, as well as, any applicable American Express Global Technology Standards. |
| • | The Business Unit Manager must notify the Information Protection Group immediately upon transfer, change of job responsibilities, or leave of absence of a User (employee or third-party). |
| • | When the Information Protection Group is notified that a User has transferred, changed job responsibilities, or taken a leave of absence, the Information Protection Group must immediately take steps to ensure that the User’s access privileges are revoked if those privileges no longer apply. |
| • | The Business Unit Manager must immediately notify the Information Protection Group upon termination of a User, i.e., an employee or third party. When the Information Protection Group is notified of a user termination, the Information Protection Group must take immediate action to revoke the User’s access privileges. |
- 35 -
* CONFIDENTIAL TREATMENT REQUESTED
| • | Virus prevention technology, (e.g., virus scanning software) must be implemented for any platform susceptible to viruses. |
| 3.4.3 | Requirements for Segregation of Duties |
| • | The principle of segregation of duties will be enforced. |
*
| 3.5 | Accountability Tracking |
| 3.5.1 | Objective |
Accountability Tracking is the process of gathering information related to the interaction between Users and information. This information provides a means of reconstructing events for investigative purposes and establishing individual accountability.
The goals of Accountability Tracking are to:
| • | Provide for the logging of events; |
| • | Ensure that each event is associated with a particular User; |
| • | Provide a mechanism to retrieve and report information on logged events; and |
| • | Report on the effectiveness of the Minimum Security Baseline requirements. |
- 36 -
* CONFIDENTIAL TREATMENT REQUESTED
| 3.5.2 | Requirements |
| • | Specific security events must be recorded. These events are: |
*
| • | Specific information must be included in the tracking record associated with each event: |
*
| • | Authentication information, e.g., passwords, PINs, and * must never appear as part of the tracking record. |
| • | Accountability tracking information must be maintained for a * after it is collected. Retention may be extended by legal, regulatory or investigative requirements. |
| 3.6 | Security Maintenance |
| 3.6.1 | Objective |
Security Maintenance is the infrastructure to support the security surrounding American Express information and technology.
The goals of Security Maintenance are grouped into four areas:
| • | Security Administrative Procedures - Provides the comprehensive documented procedures for all functions related to Information Protection (See Section 3.6.2). |
| • | Security Technology Infrastructure - Ensures that the proper technology exists to effectively administer Information Protection (See Section 3.6.3). |
| • | Contracts with Third Parties - Ensures that the requirements of the MSB are extended to Third Parties (See Section 3.6.4). |
| • | Requirements for Change Control - Preserves the integrity of development, test, and production environments (See Application Development Standard). |
| 3.6.2 | Requirements for Security Administrative Procedures |
- 37 -
* CONFIDENTIAL TREATMENT REQUESTED
| • | Procedures must be documented, implemented, and maintained for all Information Protection maintenance functions. These procedures must define: |
| • | The method used to validate and archive Identification and Authentication requests; |
| • | The method used to validate and archive Authorization (Access Control) requests; |
| • | The procedures used to create, delete, disable, and enable Identification and Authentication mechanisms; |
| • | The steps used to permit and revoke access to information; |
| • | The process for monitoring and reporting Accountability Tracking (Audit) information; |
| • | The frequency of backup for Accountability Tracking information; |
| • | Methods used to monitor the effectiveness of security controls; |
| • | The method used to document management reviews of these procedures; and |
| • | The process by which security violations are monitored, reported, and escalated. |
- 38 -
| • | The structures, rules, conventions, ranges and limits used to implement the Information Protection infrastructure must be documented. This includes: |
| • | The conventions used for Identification and Authentication mechanisms; and |
| • | The associations between Users and information to which they have access. |
| • | Identification and Authentication requests, and Authorization (Access) requests, must be retained and archived for |
| • | * . |
| • | The Information Protection Group must review Identification and Authentication violations daily and escalate when necessary. |
*
| • | The Information Protection Group must authenticate the identity of a User by establishing a positive identification. Positive identification of the User will only be established by: |
*
| • | The Business Unit Manager must immediately notify * . |
| • | A procedure must be documented and implemented to allow access to information and technology during an emergency or other unplanned or unscheduled event. This process must be as secure as possible while still allowing a timely response by information technology support personnel. Appropriate accountability tracking and |
- 39 -
* CONFIDENTIAL TREATMENT REQUESTED
| reporting on the use of this process must be included. The procedure must call for the notification of the Information Owner and the disabling of the privileged identifiers at the end of the emergency. |
| • | * . |
- 40 -
* CONFIDENTIAL TREATMENT REQUESTED
| 3.6.3 | Requirements for Security Technology Infrastructure |
| • | The technology must permit a segregation between * . |
| • | The following minimum controls must be provided by the Information Protection functions within the technology: |
| • | * ; |
| • | * ; |
| • | * ; |
| • | * ; |
| • | * ; |
| • | * ; |
| • | * ; |
| • | * ; |
| • | * ; |
| • | * ; |
| • | * ; |
| • | * ; |
| • | * ; |
| • | * ; |
| • | * ; |
| • | * |
| • | * . |
| • | Separate and controlled development, test and production environments must be established. |
| • | All modifications to the production environment must follow a documented change control procedure that describes the migration path from development to test to production. |
| • | The Information Owner must authorize all migration of software between environments. |
| 3.6.4 | Contracts with Third Parties |
| • | Contracts with Third Parties must include the following provisions: |
| • | All Third Parties (individuals or employees of Third Party businesses) must adhere to all American Express Security Policies and Standards; |
| • | Physical access granted to Third Parties must be defined and limited on a need-to-perform, job function basis; and |
| • | Third Parties must sign Non-disclosure Agreements as a condition of the contract. |
| 3.7 | Backup |
- 41 -
* CONFIDENTIAL TREATMENT REQUESTED
| 3.7.1 | Objective |
Backup is the process of making backup copies of information for the purpose of restoring that information at a later date.
The goals of Backup are to:
| • | Ensure the continued availability and accessibility of information; |
| • | Minimize the cost of a disruption, e.g., operational error, disaster, or sabotage that causes damage to, or destruction of, information; and |
| • | Provide duplicate up-to-date information for recovery purposes with the same level of integrity and quality. |
| 3.7.2 | Reference |
| • | See the Standard on Business Continuity Planting (BCP). |
| 3.7.3 | Requirements |
| • | The Information Owner is responsible for designating the frequency of information backup. |
| • | If the Information Owner does not designate a frequency for backup, the information must be backed up on a * |
| • | * |
| • | * |
| • | * |
| • | The MSB requirements described within this document must be in place for backup copies of information, whether on-site or off-site. Vendors that assist American Express with the backup of information must also adhere to these controls. |
| • | Backup copies of purchased software must be in accordance with the vendor’s license agreement. |
| • | Unauthorized copying of purchased commercial software is considered software piracy and is a violation of copyright law and American Express policy. |
| • | Backup copies of purchased commercial software must not be used on any computer outside of those in the original license, with the exception of contingency testing. |
| • | Procedures must be documented and implemented that describe the methodology for the backup of information. |
| • | When the technology used to process, store, or communicate information is changed, backup procedures must also be updated. |
| 2 | 4.0 Exception Criteria |
- 42 -
* CONFIDENTIAL TREATMENT REQUESTED
Requested exceptions to the standards must be submitted to the Regional Security Officer (RSO) who is responsible for the requestors area. Exception requests must utilize the standard exception request form. Exceptions will be reviewed by the RSO, who may request that a risk analysis be performed to determine what security measures are appropriate. Exceptions may be granted after the RSO determines that an appropriate compensating control exists. Approved exceptions will be viewed as short term resolutions. The point-of-arrival for all groups is to be 100% compliant to the standards. A schedule to reach compliance must be included with the approved exception.
Exceptions will be logged and maintained in a historical file with the Regional Security Officer.
| 3 | 5.0 Compliance Measurement |
Periodic reviews by the Information Protection group and/or Corporate Audit will be performed to determine if a department is in compliance with the standard. In addition, approved exception will be taken into consideration as part of the review.
The RSO will document their review findings and forward copies to the TL for Information Protection, the local business management and the senior business leadership team. In the areas where a department is found not to be compliant, the department will be required to respond in writing, identifying what the department will do to get to standard.
| 4 | 6.0 Frequently Asked Questions |
Following is a list of frequently asked questions relating to this Standard.
| 6.1 | What does Identification and Authentication mean? |
Each user of a system is required to be uniquely identified and authenticated to the system (usually by the required use of individually assigned User Id and password combination) to establish accountability.
| 5 | 7.0 Implementation / Migration Schedule |
To be identified after associated procedures for this Standard are prepared and issued.
| 6 | 8.0 Standards Related Information |
| 8.1 | Standard on Physical Security |
| 8.2 | Standard on Business Continuity Planning |
| 8.4 | Standard on Encryption |
| 8.5 | National Computer Security Center - Trusted Computer System Evaluation Criteria (TCSEC) |
| 7 | 9.0 Standards Enablement Team Contacts |
| 9.1 | Champion |
X. XxXxxxx (AET - Global Relationship Leader)
Xxxxx Feamow (AET - Technologies Leader, Information Protection)
| 9.2 | Xxxxxxx |
Xxxx Xxxxxx (Operations Leader, Information Protection) *
| 9.3 | Others |
None
- 43 -
* CONFIDENTIAL TREATMENT REQUESTED
| 8 | 10.0 List of Recent Changes |
| Date |
Change |
Reason for Change |
| 11.0 | Definitions |
| Client/Server | In TCP/IP the model of interaction in distributed data processing in which a program at one site sends a request to a program at another site and awaits a response. The requesting program is called a client; the answering program is called a server. | |
| Domain | The part of a computer network in which the data processing resources are under common control. In computer security, all of the objects that a subject can access. | |
| ACL | Access Control List is a collection of all access rights for one object. It is a list associated with an object that Identifies all the subjects that can access the object and their access rights. | |
| Risk Assessment | An evaluation, in terms of annualized loss expectancy, of assets, vulnerabilities of a system, and possible threats to its security. | |
| Physical Security | The protection of people or property by means such as barriers, locks and guards. | |
| Backup | The procedure, technique or hardware used to recover lost or destroyed data or to keep a system operating. The act of saving some or all of the objects on a system, on tape or on disk. | |
| Identity Token | A device such as a smart card, a metal key, or some other physical token carried by a system user that allows user identity validation. | |
| Terminology | The use of words that must and require in this standard means that this is a mandatory requirement. The use of should, may or can means a recommended guideline. | |
| 9 | Appendix |
None.
- 44 -
[Exhibit D-3]
IS GLOBAL TECHNOLOGY
PHYSICAL SECURITY STANDARD
- 45 -
Table of Contents
| 1. |
SUMMARY |
47 | ||
| 2. |
SCOPE |
47 | ||
| 2.1. |
Applicable Organizations |
47 | ||
| 2.2. |
Business Impact |
47 | ||
| 2.3. |
Coverage |
47 | ||
| 2.4. |
Regulatory Issues |
47 | ||
| 2.5. |
Inquiries |
47 | ||
| 3. |
STANDARDS DESCRIPTION |
47 | ||
| 3.1. |
Building Physical Access Control Standards |
47 | ||
| 3.2. |
Baseline Physical Access Controls |
48 | ||
| 3.3. |
Additional Physical Access Controls (Datacenter buildings) |
48 | ||
| 3.4. |
Control Standards |
48 | ||
| 3.5. |
Supporting Infrastructure Physical Access Controls |
50 | ||
| 3.6. |
Employee Termination or Change in Job Responsibility |
50 | ||
| 3.7. |
Management of Computing Resources |
51 | ||
| 3.8. |
Environmental Threats and Controls |
51 | ||
| 3.9. |
Sign Posting |
52 | ||
| 3.10. |
Insurance |
52 | ||
| 4. |
EXCEPTION CRITERIA |
52 | ||
| 5. |
COMPLIANCE MEASUREMENT |
52 | ||
| 6. |
FREQUENTLY ASKED QUESTIONS |
53 | ||
| 6.1. |
To what extent is physical security of information every person’s responsibility? |
53 | ||
| 6.2. |
What would “appropriate laptop security” devices include? |
53 | ||
| 6.3. |
How do I report a physical security related concern such as a door that is frequently left open or a broken lock? |
53 | ||
| 7. |
IMPLEMENTATION / MIGRATION SCHEDULE |
53 | ||
| 8. |
STANDARDS RELATED INFORMATION |
53 | ||
| 9. |
STANDARDS ENABLEMENT TEAM CONTACTS |
53 | ||
| 9.1. |
Champion |
53 | ||
| 9.2. |
Xxxxxxx |
53 | ||
| 9.3. |
Others |
53 | ||
- 46 -
| 10 | ||||
| 11 | ||||
| 12 | 1. Summary |
Physical Security is the process of protecting information and technology from physical and environmental threats. Physical access to information processing areas and their supporting infrastructure (communications, power, and environmental) must be controlled to prevent, detect, and minimize the effects of unintended access to these areas (e.g., unauthorized information access, or disruption of information processing itself).
Access control is established by imposing standards for protection at the building, processing area, and supporting infrastructure areas. Environmental threat control protects information and technology against environmental hazards, e.g., fire, water. The level of control imposed on these areas will reflect the nature of the importance of the information handled or supported by the area to corporate operations.
| 13 | 2. Scope |
| 13.1 | 2.1. Applicable Organizations |
This Standard applies to all components of American Express (AMEX), including all subsidiaries and affiliates.
| 13.2 | 2.2. Business Impact |
This Standard is deemed to be Xxxxx 0 priority. This Standard was established to meet AMEX strategies and goals relating to Information Systems Security throughout American Express. These strategies and goals address and incorporate methodologies to ensure AMEX’s compliance to regulatory and legal requirements. Failure to conform to this Standard will have significant impact on AMEX. Immediate migration to this Standard is required. “Immediate” is defined as within one year of this Standard’s issuance.
| 13.3 | 2.3. Coverage |
This Standard covers all Information Systems (IS) environments operated by AMEX or contracted with a third party by AMEX. The term “IS environment” defines the total environment and includes, but is not limited to, all documentation, physical and logical controls, personnel, hardware (e.g., Mainframe, distributed, desktop, network devices), software, and information.
| 13.4 | 2.4. Regulatory Issues |
This standard is intended to meet regulatory requirements.
| 13.5 | 2.5. Inquiries |
For interpretations or questions, regarding this standard, contact your Regional Security Officer (RSO) or the Information Integrity Group (II).
| 14 | 3. Standards Description |
| 14.1 | 3.1. Building Physical Access Control Standards |
The building access control standards implemented must be commensurate with the type of information processing that is occurring at the physical location. Buildings containing a designated data center will necessarily employ stricter access controls than those which do not.
- 47 -
There are also minimum physical access controls which must be practice to govern access to all buildings in an effort to protect information resources. The following standards specify the baseline controls for all buildings and additional standards appropriate for buildings which house a datacenter.
| 14.2 | 3.2. Baseline Physical Access Controls |
All buildings must employ the following measures to safeguard the information resources they contain:
| • | A security guard force to protect against unauthorized access to the building. Guards must be on duty during all hours of expected building operation and conduct internal inspections of the building to ensure appropriate security. |
| • | External monitoring of conditions around the building must be conducted. This can be accomplished by external security guard patrols, outside camera monitoring or a combination of both methods where appropriate. Outside lighting must effectively be deployed to support building monitoring. |
| • | Off-hour (other than normal business hours) access to building entrances must be achieved by the use of a Card or Token Access system. |
| • | A Visitor Access procedure must be followed which requires the following for non-employees to gain entrance to the building: |
| • | Sign-in with the security guard in a Visitors Log that is retained and reviewed. |
| • | Wearing of a visitor badge to inform personnel that a non-employee is in the area. Visitors must produce picture identification to obtain the badge from the security guard. |
| • | Escort of the visitor by American Express personnel while the visitor is in the building. |
| • | Property passes must be issued by the property owners and verified by the security guard to effect removal of American Express property from the building. |
| • | A sensitive trash program must be in place for each location. |
| 3.3. | Additional Physical Access Controls (Datacenter buildings) |
Inspection of incoming and outgoing packages (e.g., bags, briefcases, boxes, etc.) must be conducted to ensure against unauthorized materials entering or leaving the building.
| • | The Card Access or Token system used for off hours access must record individual personnel entrance and exit times in an audit trail that is retained and reviewed regularly. |
| • | All visits by non-datacenter building personnel must be authorized in advance by datacenter management with appointments confirmed by security guard personnel. |
| • | A separately access controlled area must be designated for storage of magnetic tapes, diskettes, etc. |
| 3.4. | Control Standards |
Information Processing areas include not only datacenters but also computer networks and workstations located in the business units that utilize them to conduct daily business. Physical access controls will differ depending on emphasis that management has put on securing access to
- 48 -
* CONFIDENTIAL TREATMENT REQUESTED
the information being processed (centralized datacenter control or business unit and end user discretion). The following details the appropriate controls for access to information contained at both the datacenter and business unit network levels.
3.4.1. Datacenter Physical Access
The information processed here is normally deemed critical to American Express operations and is of a sensitive nature in terms of confidentiality issues. Correspondingly, access controls to the datacenter require a high level of personnel restriction and authentication to safeguard the information processed therein. Normal access control standards utilized within datacenters must include:
| • | Controlled access for authorized individuals to gain entrance. |
| • | Logging of access for audit trail purposes. |
| • | Regular review of the authorization list for datacenter access. |
| • | A visitor access log to record non-datacenter personnel visits including vendor, maintenance, and cleaning crew people. All visitors must be escorted while in the datacenter. |
| • | Internal monitoring of datacenter activity by security guards, and closed circuit television (CCTV). |
| • | Entrance/Exit alarms to warn against unauthorized access attempts. Intrusion detection alarm systems must be used for installations which may be left unattended. These must either be part of 24 hour security control or connected to a security company or law enforcement agencies. Alarm systems must be checked periodically. |
| • | Appropriate physical construction standards to discourage unauthorized access attempts such as: |
| • | Either true floor to ceiling datacenter perimeter walls or motion detectors in the drop ceiling (and under the raised floor) to detect unauthorized access attempts. |
| • | The absence of entrance vulnerabilities such as windows or external hinges on entrance doors to the datacenter. |
3.4.2. Business Unit Network Server Physical Access
Local area networks (LANs) utilized by the business units to accomplish their functions must have the following physical access control standards applied:
| • | Network servers must be located in an area free from physical dangers (e.g., high traffic areas, water leaks, fire hazards, etc.) |
| • | Access to the servers must be physically restricted to authorized personnel (network administrators) by locating them in a closed area (e.g., a locked office). Additionally, [*] must be prevented. |
| • | Software scheduled to be installed on the network server must be scanned for viruses on a separate machine before being loaded. |
3.4.3. Business Unit End User Workstation Physical Access
| • | Workstations must be located in an area free from physical dangers (e.g., high traffic areas, water leaks, fire hazards, etc.). |
- 49 -
* CONFIDENTIAL TREATMENT REQUESTED
| • | Workstations must be secured via security cabling to prevent unauthorized removal from premises. |
| • | Workstations connected to the network must store sensitive information on file server drives as much as possible. Information stored on floppy disks must be physically secured in a manner appropriate to its sensitivity levels. |
| • | Software to be used on the workstation must be scanned for viruses. |
3.4.4. End User Portable Laptop Computers Physical Access
| • | Due to the high risk of loss due to portability, laptop computers must be traceable to individual users, and sensitive data (to the extent possible) must not be stored on the unit’s permanent disk drive. |
| • | Portable laptop computers containing sensitive data (non-disclosure) must be protected using a * |
| • | All portable laptops must be physically secured via an appropriate security device during any period that the unit is left unattended in American Express’ offices (normal business hours inclusive). |
| 3.5. | Supporting Infrastructure Physical Access Controls |
Access to facilities that support information processing systems such as the telecommunications room, the emergency power source room (generators, batteries, etc.), the air conditioning unit room and closed areas where network hubs may be stored must be restricted to authorized individuals. Deprival of infrastructure services can jeopardize continuity of information processing and impact operations as a whole. As such, the physical access controls afforded these support systems must reflect the importance of the information processing systems they serve. *
| 3.6. | Employee Termination or Change in Job Responsibility |
If an employee has a change in their job responsibility or is terminated for any reason, all of the following items in their possession, which control physical access to information must be returned, when applicable. These items include:
| • | Keys/Combination to safes and control panels; |
| • | Keys/Combination to filing cabinets; |
| • | Keys/Combination to Entrances/doors; |
| • | Terminal/PCs; |
| • | Telecommunications equipment; |
| • | Diskette boxes; and |
| • | Personal Authentication Devices, Secure ID Cards, Random Password Generators, etc. |
If keys have not been returned, it may be necessary to replace locks which protect sensitive information. Combination locks must be changed at the discretion of Management.
All Copyright, Licensed and Business Confidential Information held on magnetic media as data, programs, operating systems and utilities, must be returned, recorded, and checked.
- 50 -
* CONFIDENTIAL TREATMENT REQUESTED
| 3.7. | Management of Computing Resources |
Information Integrity Group is responsible for the movement of all types of information system media and equipment. The user must not relocate or remove any equipment without the expressed consent of the Information Integrity Group.
II is responsible for all changes to the network configuration and attached workstations. To ensure that all networking policies, standards, and procedures are being adhered to, monitoring software may be installed across all LANs and non-American Express Corporate LANs connected to the network.
| 3.8. | Environmental Threats and Controls |
3.8.1. Backup Power for Power Outage situations
Mainframe and Network computer systems and their supporting infrastructure (air conditioning systems and security alarm systems where applicable) must have a dependable, consistent electrical power supply that is free from surges and interference that could affect operation of the equipment.
Back up power is necessary to ensure that computer services are in a constant state of readiness and to help avoid damage to equipment if normal power is lost. A back up Uninterruptible Power Supply (UPS System) must be utilized for the computer systems and supporting equipment. Where appropriate, generators and batteries must also be employed to ensure survivability of operations. In areas susceptible to outages of more than 15 to 30 minutes, diesel generators are recommended. Back up power facilities must be regularly tested to ensure reliable functionality.
3.8.2. Emergency Power-off Switches
In datacenters, emergency power off switches, that shut off all power supplies, must be installed and be readily accessible with posted notices showing their location. Where justified, the use of these switches must be protected against unauthorized physical access.
In datacenters and network server closed areas, automatic emergency lighting must be provided for use during power outages.
3.8.4. Water Sensors and Temperature/Humidity Alarms
The computer environment must be protected from all forms of water, temperature and humidity damage. Locations with the potential for water damage must be avoided when selecting information processing areas (e.g., locations below ground level, or those under sewer lines, showers, cafeterias, or similar facilities where water or drainage malfunctions could occur).
In datacenter environments, sensors and alarms must be installed to monitor the environment surrounding the equipment to ensure that air, humidity and cooling water temperatures remain within the levels specified by equipment design. Water sensors must be placed in the floor and ceiling to ensure leakage detection. If proper conditions are not maintained, alarm systems must be configured to summon operations and maintenance personnel to correct the situation before a business interruption occurs.
3.8.5. Fire Detection and Suppression Controls
Measures must be taken to minimize the risks and effects of a fire occurring within the information processing areas, or from spreading into these areas from an adjoining location. The degree of automatic fire detection and suppression mechanisms deployed depends upon the criticality of the operation attributed to the information processing system. Datacenters must have Halon or approved equivalent systems or dry pipe sprinkler systems and heat sensors installed, while closed area network server rooms may
- 51 -
* CONFIDENTIAL TREATMENT REQUESTED
only have smoke detectors and fire extinguishers. Regardless, fire detection and suppression mechanisms must be utilized in the information processing areas. Where possible, detection devices must notify appropriate personnel.
3.8.6. Site Construction capabilities
The building which contains the information processing areas must minimally conform to regional construction regulations especially with regard to natural physical security threats (fire, flood, earthquake, hurricane, etc.). Selection of new sites must consider the presence of such threats and avoid high risk conditions where possible.
| 3.9. | Sign Posting |
The information processing area or data center site must not be identified by external signs, notices or maps.
| 3.10. | Insurance |
Insurance coverage must complement an effective system of physical security controls as a countermeasure against threat realization and impact on American Express’ operations. The following items must be considered in regards to associated asset values versus insurance cost to mitigate losses.
| • | IS equipment and facilities |
| • | Employee fidelity |
| • | Media reconstruction |
| • | Extra expense |
| • | Business interruption |
| • | Errors and omissions |
| • | Loss of items in transit |
| • | Liability to customers resulting from EFT systems activities |
| 15 | 4. Exception Criteria |
A request for an exception to the standards must be submitted, on the standard Exception Request Form, to the responsible document Xxxxxxx. The document Xxxxxxx will log and maintain exception requests in a historical file.
The document Xxxxxxx will review the exception request, and may require that a risk analysis be performed. If the document Xxxxxxx determines that an appropriate compensating control exists, an exception may be approved.
An approved exception is viewed as a short term solution only; the point-of-arrival for all groups is to become 100% compliant to the standards. The request for an exception must include a schedule to reach 100% compliance.
However, if a schedule to reach compliance cannot be provided, owing to extenuating circumstances, then the security and integrity for this particular case must be guaranteed by appropriate compensating controls. Cases where a schedule to reach compliance cannot be provided, will be reviewed by the document Xxxxxxx on an annual basis.
| 16 | 5. Compliance Measurement |
The Information Integrity group will perform periodic reviews to determine if a department is in compliance with the standard. Additionally, periodic reviews by other internal control groups and/or Corporate Audit may be performed to determine if a department is in compliance with the standard. Approved exceptions will be taken into consideration as part of the review.
- 52 -
The RSO will document their review findings and forward copies to the TL for Information Integrity, the local business management and the senior business leadership team. In the area where a department is found not to be compliant, the department will be required to respond in writing, identifying what the department will do to get to standard.
| 17 | 6. Frequently Asked Questions |
Following is a list of frequently asked questions relating to this Standard.
| 17.1 | 6.1. To what extent is physical security of information every person’s responsibility? |
Adherence to the Physical Security Standard is required by all persons involved with AMEX. The responsibility for each individual varies based on their role in the organization.
| 17.2 | 6.2. What would “appropriate laptop security” devices include? |
Laptop security devices include laptop lock cable mechanisms and locking docking stations. Other devices may be available. Contact II for guidance on approved devices.
| 17.3 | 6.3. How do I report a physical security related concern such as a door that is frequently left open or a broken lock? |
Depending on the case, the process must involve Facilities and II when applicable. The Facilities department should have request forms for repairs / workorders which depending on cost will require upper management approval.
| 18 | 7. Implementation / Migration Schedule |
To be identified after associated procedures for this Standard are prepared and issued.
| 19 | 8. Standards Related Information |
8.1 Standard on Risk Assessment and Management
| 20 | 9. Standards Enablement Team Contacts |
| 20.1 | 9.1. Champion |
Xxxx Xxxxx (GRL - AETO)
| 20.2 | 9.2. Xxxxxxx |
Xxxxx Xxxxxxx (TL - Information Integrity)
| 20.3 | 9.3. Others |
| Information Integrity |
00-000-000* | |||
| * Xxxxxxxx Xxxxxx |
00-000-000* | |||
| * Xxxx Xxxxxx |
00-000-000* | |||
| * Xxxxx Xxx |
00-000-000* | |||
| * Xxxxx Xxxx |
* |
- 53 -
* CONFIDENTIAL TREATMENT REQUESTED
Exhibit E
Anticipated Volumes
| Month (after Effective Date) |
Number of Unique Record Locator Numbers | |
| * |
* | |
| * |
* | |
| * |
* | |
| * |
* | |
| * |
* | |
| * |
* |
Volumes may be revised and future volumes established by mutual agreement of the parties.
- 54 -
* CONFIDENTIAL TREATMENT REQUESTED
Exhibit F
Disaster Recovery/Backup Plans
EnCoRRe Service Bureau
Disaster and Recovery Procedures
21 May, 2000
Introduction:
The following information is specific to the EnCoRRe Service Bureau running in our facilities in Dallas, Texas. Many of the same policies and procedures for business continuity are in place for all TRX data center locations.
The procedures and contact information detailed in this document is confidential and subject to change.
The following have been identified as part of the disaster and recovery team.
Xxx Xxxxxxx
Director of Network Administration
Office: *
Home: *
Cell: *
Xxxx XxXxxxx
VP of Product Support
Office: *
Home: *
Cell: TBD
Xxxx Xxxxxxxxx
VP of Product Development
Office: *
Home: *
Cell: *
Xxxxx Xxxxxx
Director of Database Administration
Office: *
Home: *
Onsite Support
Office: *
Cell: *
Backup and Storage Procedures:
A complete database backup is created nightly using * automated backup processes. This backup is created while the production system is fully operational and the backup created has complete data integrity.
- 55 -
A full system backup is done weekly consisting of all system files, database files, and operating system. This backup is automatically transferred to DLT tape.
TRX maintains *
Weekly backups are created of the client workstation files and applications and stored offsite. Full monthly backups are maintained *.
All tapes are available to be * .
Contact information for the offsite facility is:
Name: Xxxxxx Xxxxx Vault Storage
Phone: *
Hardware:
| • | Database Servers: |
All logical disk devices on the EnCoRRe database server utilize a * to protect the data in the event of a physical disk failure. Each controller has a dedicated * background process that will inform administrative staff of a failure via email. A defective drive can be quickly identified and replaced without customer impact. Spare hard drives are kept onsite.
Critical parts for the Compaq database servers are housed onsite. Non-critical parts can be obtained at Compaq’s and HP’s parts facilities in Dallas. Parts from these facilities can be over-nighted to TRX’s location and available within 24 hours.
In case of total server failure, a second server used for web based reporting will be used for quick recovery. This second server does not have the same capacity as the production server and will result in diminished service however, it will enable TRX to continue processing of critical reservations (rush queue only). Fail over to this second server would take approximately *
| • | Workstations: |
Client workstations are rack mounted, industrial grade, PC’s. Extra parts as well as complete spares are kept onsite in case of failure. In case of failure, there would be no impact upon service levels.
21.1 Power:
Network servers, database servers, workstations, gateways, etc. are all protected from power outages and “spikes” by an * This system can sustain operations for up to four hours. Stress tests are done quarterly. In case of fail over, each UPS notifies administrative staff via email and pager.
If power is not restored within * minutes, non-critical systems (monitors, email servers, etc.) are brought down to sustain power as long as possible. Customers are notified of the potential for downtime and the unscheduled downtime communication plan begins.
Once the UPS reaches * of remaining capacity, customers are notified and the systems are brought down until power is restored. Customers are notified hourly and as soon as power is restored.
TRX has * and * offsite monitoring. Each unit is tested and serviced monthly.
TRX is currently pricing the purchase and installation of a diesel generator for continuous backup.
- 56 -
* CONFIDENTIAL TREATMENT REQUESTED
UPS Contact Information:
Name: Digital Environmental Solutions of Dallas
Phone: *
Fire:
In case of fire, the current system in the data center is “wet” and will activate only over the hot zone. The onsite staff has “dry” extinguishers available. The onsite staff has been trained in fire prevention and will take all necessary steps to put out the fire and contact the fire department if necessary. TRX is researching an automated and “dry” fire prevention system.
Cooling:
The data center is cooled by two 10 ton Liebert air conditioning and de-humidifying systems. In case of failure, a single unit can provide enough cooling to keep the system running until the second system is repaired.
TRX has * and * offsite monitoring and * emergency support. Each unit is tested and serviced monthly.
A/C Contact Information:
Name: *
Phone: *
Data center Access:
Access is controlled to the building, the suite, and to the data center via picture identification swipe cards. Only pre-authorized staff is allowed into the data center and access is kept to a minimum.
GDS Access:
The EnCoRRe service bureau is dependent upon GDS access provided by several GDS suppliers. The customer provides the access to these GDS’s and support levels are provided under an agreement the customer has with each GDS. Downtime response provided by the GDS can vary however, TRX is provided premium support levels from all GDS vendors.
| • | Gateways: |
Gateways are workstations used to communicate from the client workstations to the GDS host. TRX uses a third party gateway provided by * . Spare software and hardware are kept onsite in case of system failure. Multiple gateways are used for redundancy. In case of failure, the applications will automatically fail over to the redundant gateway.
| • | CRS Lines: |
Redundant lines are installed to provide access to the GDS host. Downtime is minimal. In case of CRS failure, the following are called:
| • | SABRE |
*
| • | Galileo/Apollo |
*
| • | Worldspan |
- 57 -
* CONFIDENTIAL TREATMENT REQUESTED
*
| • | Amadeus |
*
Communications Plan:
| • | Scheduled Downtime: |
Downtime for routine maintenance, upgrades, system administration, etc. will be considered “scheduled”. Scheduled downtime will be kept between * All scheduled downtime will be communicated by email in advance and kept to a preset calendar.
The initial downtime calendar will be determined and distributed during implementation. Each month, notification will be sent by email containing the date and duration for scheduled downtime that month as well as any changes in the scheduled downtime schedule.
| • | Unscheduled Downtime: |
Downtime for immediate bug fixes, hardware failure, CRS failure, etc. will be considered “unscheduled”. Notification will be sent by email as soon as possible containing the cause of the downtime and estimated or actual duration. Additional notifications will be sent by email every hour and upon system startup.
| • | Logging |
Data center staff log all scheduled and unscheduled downtime, system alarms, and steps taken to recover. This log is used to determine overall system uptime and steps required improving uptime performance.
| • | Remote monitoring |
TRX is in the process of creating a web based monitoring application that will allow our customers to view a “dashboard” of all system processes and status. PNR’s on queue, workstations running, database capacity, PNRs processed by hour, etc. will be displayed.
- 58 -
* CONFIDENTIAL TREATMENT REQUESTED
Exhibit G
Escrow Agreement
[TBD]
- 59 -
ESCROW AGREEMENT
“Effective Date”: , 2000
TTG: (referred to as “Depositor”)
Travel Technologies Group L.P.
0000 Xxxxxxx Xxxx
Xxxxxx, Xxxxx
Amexco:
American Express Travel Related Services Company, Inc.
World Financial Center
American Express Tower
000 Xxxxx Xxxxxx
Xxx Xxxx, Xxx Xxxx 00000
ESCROW AGENT: (referred to as “Escrow Agent”)
[TBD]
This Escrow Agreement (“Agreement”) is made and entered into as of the Effective Date set forth above, by and among TTG identified by name above (referred to in this Agreement as the “Depositor” or “TTG”), Amexco (“Amexco”) and the escrow agent whose name and address is set forth above (“Escrow Agent”).
Depositor and Amexco have entered into a Service Bureau Agreement with an effective date of , 2000 (“Services Agreement”), under which Amexco has licensed certain Software, Enhancements, Modifications, Improvements, and Software Releases from Depositor. The Services Agreement further provides for the escrow of materials relating to the Software, Enhancements, Modifications, Improvements, and Software Releases (“Escrow Materials”) and this Agreement is entered into for the purpose of effectuating such an escrow arrangement in connection with the Services Agreement and the Software, Enhancements, Modifications, Improvements, and Software Releases identified therein. Depositor and Amexco acknowledge that Escrow Agent has no knowledge of the terms and conditions contained in the Services Agreement and that Escrow Agent’s only obligations shall be set forth herein or in any other writing signed by Depositor, Amexco and Escrow Agent Depositor and Amexco agree that all terms capitalized as defined terms in this Agreement shall have the meaning given them in the Services Agreement, unless otherwise defined in this Agreement.
ARTICLE 1: Deposit of Escrow Materials; Recordkeeping
1.1 On or before delivery of the Software and all Enhancements, Modifications, Improvements, or Software Releases, as the case may be, to Amexco or for general release, Depositor shall deliver to the Escrow Agent, for deposit under this Agreement in Atlanta, Georgia, a current and complete copy of the program source code, object code, documentation and any other materials required by the Services Agreement or mutually agreed to by Depositor and Amexco to be deposited in escrow (“Escrow Materials”). A specific description of the Escrow Materials required is set forth on the attached Exhibit A, which is incorporated and made a part of this Agreement.
1.2 Within thirty (30) days of the installation of any new Enhancement, Modification, Improvement or Software Release, TTG shall deliver to the Escrow Agent, for deposit in accordance with this Agreement, any and all changes to the Escrow Materials which correspond to changes, if any, made to the Software. All materials deposited hereunder shall be considered “Escrow Materials” as die term is used herein.
- 60 -
1.3 The Escrow Materials may be removed and/or exchanged only on written instructions signed by Depositor and Amexco, or as otherwise provided in this Agreement.
ARTICLE 2: Location of Escrow Materials
2.1 The Escrow Materials shall be administered by Escrow Agent from the location specified on Exhibit C and shall not be moved to any other location without the express written consent of Amexco and Depositor. Escrow Agent shall notify Depositor in writing of any change in location.
2.2 Amexco shall have the right, at any time upon at least ten (10) days’ written notice to Depositor and Escrow Agent, upon receipt of consent by TTG which shall not be unreasonably withheld or delayed, to select and designate a new escrow agent to replace the Escrow Agent hereunder. Upon such notice and upon payment of any outstanding fees due Escrow Agent, Escrow Agent shall completely, safely and securely transfer the Escrow Materials to the new escrow agent (which will then become the “Escrow Agent” hereunder) and confirm such transfer in writing to Amexco and Depositor. Amexco shall be responsible for all costs, fees and expenses in connection with the new escrow arrangement.
ARTICLE 3: Verification of Escrow Materials
3.1 When Escrow Agent receives the Escrow Materials accompanied by Exhibit A attached hereto, Escrow Agent will conduct a deposit inspection by visually matching the labeling of the tangible media containing the Escrow Materials to the item descriptions and quantity listed on Exhibit A hereto, payment for which shall be made by Amexco.
3.2 Escrow Agent is entitled to be paid its standard fees and expenses applicable to the services provided. Escrow Agent shall notify Amexco, the party responsible for payment of all Escrow Agent’s fees, at least ninety (90) days prior to any increase in fees. For any services not listed on Escrow Agent’s standard fee schedule attached hereto as Exhibit C, Escrow Agent will provide a quote prior to rendering the service, if requested.
3.2.1 Escrow Agent shall not be required to perform any services unless the payment for such services and any outstanding balances owed to Escrow Agent are paid in full. All other fees are due payable within thirty (30) days of receipt of invoice and are the sole responsibility of Amexco. If invoiced fees are not paid, Escrow Agent may terminate this Agreement; provided, however, that any non-payment of fees may be remedied in accordance with the Material Breach provisions set forth in Article 6 hereof. If there is a discrepancy in fees owed to Escrow Agent, then Amexco and Escrow Agent shall agree to discuss this matter on a good faith basis.
3.3 In addition and upon Amexco’s request, Escrow Agent shall be authorized to perform any additional verification services which are available from Escrow Agent from time to time specified on the attached Exhibit D, including, without limitation, services necessary to verify the completeness, accuracy and functionality of the Escrow Materials and to ensure that the Escrow Materials conform and correspond to the Software, Enhancements, Modifications, Improvements and Software Releases available to Amexco under the Services Agreement.
3.3.1 Upon request, Escrow Agent will furnish Amexco with a current copy of the charges for additional verification services which are available from Escrow Agent hereunder. Amexco shall be responsible for payment of any such charges directly to Escrow Agent and Depositor shall have no responsibility for same.
3.3.2 Escrow Agent shall promptly notify Depositor of any verification services requested by Amexco and shall promptly provide Depositor with a copy of any technical verification report rendered by Escrow Agent in connection with such an engagement.
3.4 Escrow Agent shall report to Amexco in writing the results of all verification services performed on Escrow Materials upon completion of same and shall send a copy to Depositor.
- 61 -
3.5 No more frequently than once annually, Amexco shall be entitled to audit and inspect the Escrow Materials in the possession of the Escrow Agent to verify the completeness, accuracy and functionality of the Escrow Materials, and to ensure that the Escrow Materials conform and correspond to the Software, Enhancements, Modifications, Improvements and Software Releases available to Amexco under the Services Agreement. A representative of the Escrow Agent shall be present at all times during any such inspection by Amexco.
ARTICLE 4: Release and Return of Escrow Materials
4.1 Amexco shall be entitled to request a release of and obtain the Escrow Materials from the Escrow Agent if: (i) TTG ceases doing business and its business is not continued by another corporation or entity; (ii) TTG becomes insolvent; (iii) TTG makes a general assignment for the benefit of creditors; (iv) TTG suffers or permits the appointment of a receiver for its business or assets; (v) TTG avails itself of, or becomes subject to, any proceeding under the Federal Bankruptcy Act or any other statute of any state or country relating to insolvency or the protection of rights of creditors; or (vi) fails to meet its maintenance and support obligations in accordance with the provisions of the Services Agreement, and such failure is not fully remedied in accordance with Section 8.2 of the Services Agreement and within ten (10) days of Amexco’s written notice to TTG of its intent to request a release of the Escrow Materials (hereinafter referred to as a “Depositor Default”), then notwithstanding any other rights and remedies to which Amexco may be entitled, Amexco shall immediately have the right to obtain a copy of the Escrow Materials from the Escrow Agent upon written notice as provided in this Agreement.
4.2 Escrow Agent shall deliver the Escrow Materials, or a copy thereof, to Amexco only in the event that:
(a) Escrow Agent receives:
(i) written notification from Amexco of the occurrence of a Depositor Default;
(ii) evidence satisfactory to Escrow Agent that Amexco has previously notified Depositor of such Depositor Default in writing;
(iii) a written demand that the Escrow Materials be released and delivered to Amexco;
(iv) a written undertaking from Amexco that the Escrow Materials being supplied to Amexco will be used only as permitted under the terms of the Services Agreement; and
(v) specific instructions from Amexco for this delivery.
(b) Amexco shall, concurrently with its submission of the items in Section 4.1(a) above to Escrow Agent, send by certified mail to Depositor a photostatic copy of all such documents.
(c) Within five (5) business days of its receipt of the articles in Section 4.1 (a) above, Escrow Agent shall release and deliver a copy of the Escrow Materials to Amexco.
(d) Notwithstanding the release of the Escrow Materials as provided in Section 4.1(c) above, Depositor shall have thirty (30) days from the date on which Depositor receives the documents described in Section 4.1(b) above (“Objection Period”) to notify Amexco of its objection (“Objection Notice”) to the release of the Escrow Materials to Amexco and to request that the issue of Amexco’s entitlement to a copy of the Escrow Materials be submitted to arbitration in accordance with the following provisions:
(i) If Depositor shall send an Objection Notice to Amexco during the Objection Period, the matter shall be submitted to, and settled by arbitration by, a panel of three (3) arbitrators chosen by the New York Regional Office of the American Arbitration Association in accordance with the rules of the American Arbitration Association. The arbitrators shall apply New York law. All three (3) arbitrators shall be reasonably familiar with the computer software industry. The decision of the arbitrators shall be binding and conclusive on all parties involved, and judgment upon their decision may be entered in a court of competent jurisdiction. All costs of the arbitration incurred by Depositor and Amexco, including reasonable attorneys’ fees and costs, shall be paid by the Depositor or Amexco as determined by the arbitration. If, however, Amexco refuses to submit to such
- 62 -
binding arbitration, the matter shall not be submitted to arbitration and Depositor may submit the matter to any court of competent jurisdiction in an interpleader or similar action.
4.3 Escrow Agent shall be entitled to act in reliance upon any Amexco instructions, instrument, or signature reasonably believed to be genuine and shall assume that any Amexco officer giving any written notice or instruction, which is consistent with this Agreement, has been duly authorized to do so on behalf of Amexco. Similarly, Escrow Agent shall have no duty to inquire as to whether Amexco or Depositor is in compliance with the provisions of the Services Agreement relating to the release of Escrow Materials and shall have no liability to Depositor or Amexco for relying on Amexco’ notice.
4.4 If the Services Agreement between Amexco and Depositor has expired, been terminated or cancelled and if Amexco has not notified Escrow Agent to release the Escrow Materials hereunder as contemplated under Section 4.1 above, then Escrow Agent may return or destroy the Escrow Materials at the request of Depositor; provided, however, that Escrow Agent shall not return or destroy any such Escrow Materials unless Escrow Agent has received written certification from Amexco that no event or condition has occurred which would permit Amexco to obtain the release and delivery of such Escrow Materials under this Agreement. Notwithstanding the foregoing, if Amexco has not provided said written certification within thirty (30) days from Escrow Agent’s notice of termination, then at Escrow Agent’s option, Escrow Agent may return or destroy the Escrow Materials.
4.5 Each party shall designate an authorized individual as a contact for the purposes set forth hereunder and individuals shall be specified on the attached Exhibit E.
4.6 Any release of Escrow Materials to Amexco shall remain subject to the confidentiality obligations set forth below and in the Services Agreement. Escrow Materials shall be utilized by Amexco for its maintenance and support requirements in accordance with the Services Agreement only, and no other purpose whatsoever.
4.7 In the event of a release of the Escrow Materials to Amexco pursuant to this Article 4, Depositor shall and does hereby license to Amexco, subject to such condition, the right to use, copy, modify, maintain and update the Deposit Materials in any manner necessary or appropriate to enable Amexco to use the Deposit Materials to perform the Standard Services and any other obligations of Depositor under the Services Agreement. Any such modifications to the Deposit Materials made by Amexco shall be the property of Amexco. The foregoing license is fully paid-up, perpetual and irrevocable; provided, however, the foregoing license shall terminate if all of the following shall be performed by Depositor: (i) Depositor shall remedy the Depositor Default giving rise to the release; (ii) Depositor shall provide Amexco with adequate assurances of Depositor’s ability and commitment not to cause or permit any future Depositor Default; (iii) Depositor shall fully and completely enhance, improve or modify the Deposit Materials and Software to include all Software Releases implemented since the release of the Deposit Materials so that the Software, as implemented and operating to provide the Standard Services to Amexco, is the then current version of the Software, and (iv) Depositor shall reimburse Amexco for all costs and expenses incurred by or on behalf of Amexco in the development, implementation, operation, maintenance and support of Deposit Materials during the pendency of Amexco’s use thereof pursuant to the provisions of this Agreement.
ARTICLE 5: Confidentiality of Escrow Materials
5.1 Escrow Agent acknowledges that Depositor considers the Escrow Materials to be confidential and trade secrets of Depositor, and Escrow Agent agrees that unless Escrow Agent has obtained Depositor’s written consent, Escrow Agent shall keep the Escrow Materials confidential and prevent their disclosure to any person, firm or enterprise other than to employees or representatives of Escrow Agent involved in the performance of Escrow Agent’s obligations under this Agreement, to employees and representatives of Depositor, and to Amexco under the specific release provisions specified in this Agreement.
5.2 Escrow Agent may copy Escrow Materials to the extent necessary to preserve and safely store the Escrow Materials, to perform the verification services required and permitted under this Agreement, and to provide copies to Amexco as and when permitted hereunder. On all such copies, Escrow Agent shall reproduce any proprietary rights and/or confidentiality notices which were on the Escrow Materials at the time of their deposit with Escrow Agent.
- 63 -
ARTICLE 6: General
Payment: Escrow Agent may invoice Amexco and Amexco shall be responsible for all fees and/or charges applicable hereunder and Amexco agrees to pay each invoice properly rendered hereunder within thirty (30) days after its receipt.
Liability: Amexco and Depositor agree that Escrow Agent is acting as an independent agent and stakeholder hereunder and, provided that Escrow Agent acts in accordance with the terms and conditions set forth in this Agreement, Escrow Agent shall not be held liable by Amexco or Depositor for the proper performance of Escrow Agents obligations under this Agreement. Further, except for any unauthorized acts by Escrow Agent under this Agreement, Amexco and Depositor shall agree to be liable for and shall indemnify, defend and hold Escrow Agent harmless from and against any claims, actions, losses or damages, including, without limitation, reasonable attorneys’ fees, other costs and/or expenses actually incurred by Escrow Agent relating in any way to this Agreement. No party hereunder shall be liable, to any other party hereunder, for any indirect, special, punitive, exemplary or consequential damages arising out of or in connection with this Agreement.
Termination: Upon the release, return, destruction or transfer of the Escrow Materials as permitted hereunder or upon termination due to a material breach, all further obligations and/or rights of Escrow Agent under this Agreement shall terminate; provided, however Escrow Agent is not the party in breach.
Material Breach: In the event of any material breach of this Agreement by one party, the other parties may (reserving cumulatively all other remedies and rights under this Agreement and in law and in equity) terminate this Agreement, by giving thirty (30) days’ written notice thereof; provided, however, that any such termination shall not be effective if the party in breach has cured the breach of which it has been notified prior to the expiration of said thirty (30) days.
Notices: Except as otherwise specifically provided, all notices shall be in writing and delivered personally or mailed to the addresses of the parties set forth at the beginning of this Agreement, to the attention of the undersigned at the address(es) set forth at the beginning of this Agreement or to such other address or addressee as any party may designate by written notice and in the case of Amexco, to the Office of the General Counsel, American Express Travel Related Services Company, Inc., American Express Tower, World Xxxxxxxxx Xxxxxx, Xxx Xxxx, Xxx Xxxx 00000-0000. Notices shall be deemed given when delivered or when placed in the mail as specified herein.
Bankruptcy: Amexco, Depositor and Escrow Agent acknowledge that this Escrow Agreement is an “agreement supplementary to” the Services Agreement as provided in Section 365(n), Title 11 of the United States Code (“Bankruptcy Code”). If Depositor, as a debtor in possession, or a trustee in bankruptcy appointed pursuant to the Bankruptcy Code, rejects the Services Agreement or this Agreement, then subject to any other rights Amexco may have, Amexco may elect to retain its rights under the Services Agreement and this Agreement as provided in the current Bankruptcy Code or any amendments and/or successor statutes. Unless earlier notified by Amexco, Depositor and Escrow Agent, individually and collectively, agree that unless they have received notice from Amexco that it does not wish to make such election or exercise any such rights, neither Escrow Agent nor Depositor shall interfere with the rights of Amexco in the Services Agreement and/or this Agreement.
Assignment: The parties may not assign this Agreement or any of their rights and obligations hereunder without the written consent of each of the other parties involved in this Agreement and any such attempted assignment shall be void; provided however, that (A) Amexco may require the transfer of Escrow Materials to a new escrow agent (as permitted hereunder), upon written notice to and consent of Depositor (such consent not to be unreasonably withheld or delayed) and in accordance with Section 2.2, without the consent of Escrow Agent, and (B) Amexco may assign this Agreement, and/or any of its rights and/or obligations hereunder, in their entirety, (including all licenses granted to Amexco hereunder) to, (i) in the case of any merger or sale of its assets, to any entity which acquires all or substantially all of Amexco’s assets or any succession in a merger or acquisition of Amexco, upon written notice to Depositor without the consent of Depositor, or (ii) in the case of an internal restructuring, to a wholly-owned subsidiary or affiliated company, upon written notice to Depositor without the consent of Depositor, and (W) does not adversely affect Depositor’s rights under the Services Agreement; (X) does not increase Depositor’s obligations under the Services Agreement; (Y) does not limit or reduce Amexco’s
- 64 -
obligations under the Services Agreement; and (Z) does not expand or otherwise increase Amexco’s rights under the Services Agreement, including but not limited to the scope of the license and/or Amexco’s right to indemnification as granted therein.
Severability: In the event any provisions of this Agreement are held to be invalid, illegal or unenforceable, the remaining provisions of this Agreement shall be unimpaired.
Governing Law: In all respects this Agreement shall be governed by the substantive laws of the State of New York without regard to conflict of law principles.
Modification/Amendments: No modification, amendment, supplement to or waiver of this Agreement or any of its provisions, whether by conduct or otherwise, shall be binding unless made in writing and duly signed by the parties. A failure or delay, by any party at any time, to enforce any of the provisions, or to exercise any option, or to require performance, shall in no way be construed to be a waiver or modification of this Agreement.
IN WITNESS WHEREOF, the parties have duly executed this Agreement on the dates indicated below.
| AMERICAN EXPRESS TRAVEL | TRAVEL TECHNOLOGIES GROUP. L.P. | |||||||
| RELATED SERVICES COMPANY, INC. | ||||||||
| By: |
By: |
|||||||
| Name: |
Name: |
|||||||
| (Type or Print) | (Type or Print) | |||||||
| Title: |
Title: |
|||||||
| Date: |
Date: |
|||||||
| [ESCROW AGENT] | ||||||||
| By: |
||||||||
| Name: |
||||||||
| Title: |
||||||||
| (Type or Print) | ||||||||
| Date: |
||||||||
- 65 -
EXHIBIT A TO THE ESCROW AGREEMENT
LIST OF ESCROW MATERIALS FOR INITIAL DEPOSIT
Source code, object code, and all relevant documentation, commentary, and other similar materials, for the Software, Enhancements, Modifications, Improvement and Software Releases, and any other materials required by Section 8.7 of the Service Agreement.
Include the following form with each deposit
Product Name:
Prepared and Confirmed by:
Title: Date:
Signature:
Type of deposit:
Initial Deposit
Update Deposit to replace current deposits
Other (please describe)
Items Deposited:
| Quantity | Media Type | Description of Material | ||||
| A) | _____ | _________ | ______________________________________________ | |||
| B) | _____ | _________ | ______________________________________________ | |||
| C) | _____ | _________ | ______________________________________________ | |||
- 66 -
EXHIBIT B
Product Name:
Version #:
Prepared and Confirmed by:
Title: Date:
Signature:
Initial Deposit
Update Deposit to replace current deposits
Other (please describe)
Items Deposited:
Quantity Media Type Description of Material
A)
B)
C)
(please copy page as necessary)
- 67 -
EXHIBIT C TO THE ESCROW AGREEMENT
ESCROW AGENT’S STANDARD FEE SCHEDULE
Initialization fee (one time only) $
Location where Deposit Materials shall be kept by Escrow Agent:
_______________________________________________
_______________________________________________
_______________________________________________
* Annual maintenance/storage fee $
includes two Deposit Material updates
includes one cubic foot of storage space
Additional Services Available:
Additional Updates $ /Product
(above two per year)
Additional Storage Space $ /Cubic foot
Payable by Licensee or Producer Only Upon Release Request:
Due Only Upon Licensee’s or Producer’s
Request for Release of Deposit Materials $ 100/Product per Licensee for
initial 2 hrs. and $ 50/hour for each additional hour
[Escrow Agent] benefits its clients by offering extended services including: software testing & verification, media conversion, document capture & retrieval, image processing, high-speed laser printing, data conversion, information software and IT consultancy.
Fees due in full, in US dollars, upon receipt of signed contract or deposit material, whichever comes first.
Thereafter, fees shall be subject to their current pricing, provided that such prices shall not increase by more than 10% per year. The renewal date for this Agreement will occur on the anniversary of the first invoice.
If other currency acceptance is necessary, please contact your Account Manager to make arrangements.
- 68 -
EXHIBIT D TO THE ESCROW AGREEMENT
ESCROW AGENT’S VERIFICATION SERVICES
Verification prices vary greatly and are priced per project.
- 69 -
EXHIBIT E TO THE ESCROW AGREEMENT
AUTHORIZED CONTACTS
AMEXCO:
TTG:
Escrow Agent:
- 70 -
Addendum A to Service Bureau Agreement dated July 24, 2000
By and Between TRX Technology Services, L.P. (formerly known as Travel Technologies Group, L.P.) and American Express Travel Related Service Company, Inc.
Effective Date of this Addendum: March 9, 2001
Exhibit A is amended with the addition of the following:
As of the Effective Date of this Addendum, User will be charged * sent by the EnCoRRe Service Bureau, * This pricing will be in addition to any other fees charged for the Services.
Acknowledgment
User acknowledges to have read the Service Bureau Agreement referenced above, understands and agrees to be bound by the Terms and Conditions of said Agreement. TRX and User agree that these documents represent the complete and exclusive statement of agreement between the parties and supersede all proposals or prior agreements, verbal or written, and any other communications between the parties relating to the subject matter of these Agreements.
| Travel Technologies Group, L.P. |
American Express Travel Related Service Company, Inc. | |||||||
| Signed: |
/s/ Xxxxx Xxxxxxxx |
Signed: |
/s/ Xxxxxxx Xxxxxxxx | |||||
| Name: |
Xxxxx Xxxxxxxx |
Name: |
Xxxxxxx Xxxxxxxx | |||||
| Title: |
General Manager and EVP |
Title: |
VP, Corporate Travel Solutions | |||||
* CONFIDENTIAL TREATMENT REQUESTED
Amendment #1 to
between
TRX Technology Services, L.P.
f/k/a Travel Technology Group, L.P.
and
American Express Travel Related Service Company, Inc.
This Amendment (“Amendment”) is between TRX Technology Services, L.P. a Georgia limited partnership formerly known as Travel Technology Group, L.P. (“TRX”) and American Express Travel Related Service Company, Inc. a New York corporation (“User”). TRX and User have previously entered into a Service Bureau Agreement dated July 24, 2000 and Addendum, dated March 9, 2001 (collectively, the “Agreement”), which is incorporated herein by reference. The parties desire to amend and revise the Agreement solely as set forth in this Amendment. Unless otherwise set forth in this Amendment, the terms defined within the Agreement and its Exhibits, Schedules, and Attachments shall also apply to this Amendment.
WHEREAS, TRX owns and operates a service bureau service called EnCoRRe; and
WHEREAS, TRX will provide mid-office processing with EnCoRRe or AE Lite; and
| 1. | Definitions. Any capitalized terms not defined herein shall have the meaning ascribed to them in the Agreement. |
| 1.1. | “AE Lite” means the service bureau service customized expressly for User and described in Schedule A to this Addendum. |
1.2. “Intellectual Property Rights” means all rights in and to trade secrets, patents, copyrights, trademarks, know-how, as well as moral rights and similar rights of any type under the laws of any governmental authority, domestic or foreign.
1.3. “User Marks” means all trademarks, service marks, logos and other distinctive brand features of User including, without limitation, the trademarks, service marks and logos described in Schedule B.
| 2. | Grant of Rights. |
2.1 Grant of Rights by TRX. TRX hereby grants to User the right to use AE Lite under the terms and conditions of Section 2 of the Agreement.
2.2 Grant of Rights by User. Subject to the terms and conditions of this Amendment and the Agreement, User hereby grants to TRX a limited, nonexclusive, non-transferable, worldwide, royalty-free license to use, reproduce, display, and transmit the User Marks, as provided by User, solely within AE Lite for use by User. User reserves the right to revoke this license at any time by providing TRX with written notice.
| 3. | Ownership. |
3.1 By TRX. User acknowledges and agrees that nothing in this Amendment or the Agreement will confer in User any right of ownership in AE Lite. Any enhancement to the Software will be governed by Section 2.5 of the Service Bureau Agreement. No licenses are granted by either party except for those expressly set forth in this Agreement.
3.2 By User. TRX acknowledges and agrees that nothing in this Amendment or the Agreement will confer in TRX any license or right of ownership in the User Brand Features.
3.3 Survival. This Section 3 shall survive termination or expiration of this Amendment or the Agreement.
| 4. | Pricing and Payment. |
Deletion of Section 4.1 in Agreement. The parties acknowledge that Section 4.1 and Exhibit A of the Agreement are hereby deleted and replaced with the terms set forth in the new Section 4.1 below and Exhibit A attached to this Amendment. Except as specified herein, this Section 4 supplements Section 4 in the Agreement
4.1 Pricing. The fees for the services provided pursuant to the Agreement and this Amendment are set forth on Exhibit A attached hereto. Except as set forth in Section 4.2. all payments shall be *
* CONFIDENTIAL TREATMENT REQUESTED
*
4.2 Reconciling Payment. TRX shall reconcile each * Any overpayment by User shall be credited towards User’s account and such credit shall be reflected on the following * after such obligation accrued. Any underpayment by User shall be included in the following * Payment method shall be via the * System.
4.3. Payment Transition Plan. The parties acknowledge that prior to the signature date of this Agreement, User paid fees in arrears. The parties agree to the following transition plan to move User to prepayments:
a) Notwithstanding anything to the contrary in Section 4.1, User shall begin prepayment of * .
b) Beginning with the invoice for August 2002, TRX shall invoice User for estimated fees according to the methodology described in Section 4.1. TRX shall invoice User for August 2002 transactions no later than the twentieth day of July 2002. User shall pay such fees no later than *
c) User acknowledges that it shall make * for both *
| 5. | Retroactive Effect. The parties agree that these terms shall be effective retroactive to April 1, 2002. |
| 6. | Term of the Agreement. “The parties agree that the Initial Term of the Agreement (as specified in Section 8.1 of the Agreement) shall be extended for one year to a six-year Initial Term, unless terminated as provided in the Agreement, and shall be renewable automatically for two consecutive one year periods (as set forth in the Agreement), unless User provides TRX with notice of its intention not to renew at least sixty (60) days prior to the conclusion of the Initial or any Renewal Term. |
| 7. | User Obligations. |
7.1 Additional U.S. Accounts. User agrees that it shall use reasonable business efforts to migrate selected accounts to EnCoRRe or AE Lite no later than December 31, 2002, and that the pricing terms herein are partially in consideration of such migration.
* CONFIDENTIAL TREATMENT REQUESTED
7.2 Additional International Accounts. User agrees that it shall use reasonable business efforts to migrate User’s additional operations to EnCoRRe or AE Lite within twenty-four (24) months of the signature date of this Amendment.
| 8. | Publicity and Marketing Activities. |
8.1 Use of User Marks. TRX shall have the right to use the User Marks only as shown in Schedule B for the purpose of presentations for potential clients in private meetings. This use is granted based on current relationship and business conditions and is subject to change at the sole discretion of User. TRX does not have the right to use User Marks on its sales collateral and client lists without User’s prior written authorization from the AMEX Public Affairs department. Any such User-authorized use shall conform to User’s trademark usage guidelines, if any, as such guidelines are presented in writing to TRX from time to time.
8.2 Press Releases. TRX shall not use the user’s name, logo, trademarks or service marks in any advertising, publicity releases, client listing or any other materials or in any other manner without the user’s prior written approval from the user’s Public Affairs department. Neither party shall issue a press release or make any public statement relating to the relationship set forth in this Amendment until such press release or public statement has been mutually agreed. Any press or media coverage in connection with this Amendment will be subject to the prior written approval of both parties consistent with Section 3.6 of the Agreement.
8.3 Marketing Events. The parties agree that User may provide opportunities to participate in User customer events or forums and that TRX may, in its sole discretion, choose to participate in said User customer events and forums. User agrees to provide reasonable notice to TRX of any such events. Additionally, User may provide TRX with sponsorship opportunities for User events that it makes available to its other technology providers.
8.4 Quarterly Meeting. The parties agree to meet quarterly to discuss User’s technology needs and ways TRX can meet such needs. Such meeting shall be at a mutually agreed upon location, date, and time, and each party shall bear its own expenses for such meetings.
| 9. | Miscellaneous. |
9.1 Balance of Terms Unchanged. Except as expressly set forth in this Amendment, the terms and conditions of the Agreement shall continue in full force and effect. This Amendment shall be effective as of the 1st day of April 2002 (“Amendment Effective Date”).
9.2 Entire Agreement. The Agreement, along with this Amendment, including the Exhibits and Schedules attached hereto, represents the entire understanding and agreement between the parties with respect to the subject matter hereof, and supersedes any and all previous discussions and communications. Any subsequent amendments and/or additions hereto are effective only if in writing and signed by both parties.
9.3 Precedence. In the event of a conflict between the Agreement and this Amendment, this Amendment shall control and govern.
9.4 Audits. TRX agrees that, during the term hereof, it will not perform “audits” of American Express on behalf of any third party. TRX’s failure to comply with the terms of this Section shall be deemed a material breach of the Agreement and American Express shall be entitled to exercise its rights under Section 8.2 of the Agreement. In the event American Express engages TRX directly for the provision of audit services, the results of such audit shall be considered Confidential Information as such term is defined in Section 3.4 of the Agreement. For purposes of this Section 9.4, “audit” shall mean analysis of third party corporate entities’ travel-related contracts with American Express for the purpose of determining whether incentives and discounts offered by American Express to its corporate clients have been properly administered
| TRX TECHNOLOGY SERVICES, L.P. | AMERICAN EXPRESS TRAVEL RELATED SERVICE COMPANY, INC. | |||||||
| BY: |
/s/ Xxxxx Xxxxxxxx |
BY: |
/s/ Xxx Xxxxxx | |||||
| NAME: |
Xxxxx Xxxxxxxx |
NAME: |
Xxx Xxxxxx | |||||
| TITLE: |
GM |
TITLE: |
Manager, Global Procurement | |||||
| DATE: |
7/15/02 |
DATE: |
6/27/02 | |||||
SCHEDULE A
PRODUCT DESCRIPTION
EnCoRRe Service Offering
| • | Res EditorSM quality control routines |
| • | Seat SearchSM |
| • | Low Fare SearchSM |
| • | Waitlist Clearance™ |
| • | Frequent Flyer UpgradeSM |
| • | Auto-Ticketing Routines |
| • | PowerCoRReSM Routines |
| • | Web Reporting |
AE Lite Service Offering
| • | A finite set of Res EditorSM quality control routines |
| • | Limited masking for capturing for MIS fields from PNR’s |
| • | Seat SearchSM |
| • | Low Fare SearchSM |
| • | Waitlist CIearanceSM |
| • | Web Reporting |
SCHEDULE B
USER MARKS

EXHIBIT A
PRICING TERMS
EnCoRRe Pricing
| Average Unique Record Locator Numbers * |
Price per Unique Record Locator Number* | ||
| * |
$ | * | |
| * |
$ | * | |
| * |
$ | * | |
| * |
$ | * | |
| * | Usage and support fee will be reduced to * per unique record locator number after User has processed * unique record locator numbers. |
All requests for additional Power CoRRe routines will be billed at *
AE Lite Pricing
One-Time Implementation Fee *
| Average Unique Record Locator Numbers * |
Price per Unique Record Locator Number* | ||
| * |
$ | * | |
| * |
$ | * | |
| * |
$ | * | |
| * |
$ | * | |
| * |
$ | * | |
| * | TRX will use existing American Express GDS lines and Terminal Addresses for servicing this product and pricing does not include Auto-Ticketing or any Power CoRReSM routines except for those routines that were developed to establish the AE LiteSM product offering. All requests for additional routines will be billed at * |
* CONFIDENTIAL TREATMENT REQUESTED
Amendment #2 to
between
TRX Technology Services, L.P.
f/k/a Travel Technology Group, L.P.
and
American Express Travel Related Service Company, Inc.
This Amendment (“Amendment”) is between TRX Technology Services, L.P., a Georgia limited partnership formerly known as Travel Technology Group, L.P., (“TRX”) and American Express Travel Related Service Company, Inc., a New York corporation (“User”). TRX and User have previously entered into a Service Bureau Agreement dated July 24, 2000 and Addendum, dated March 9, 2001 (collectively, the “Agreement”), which is incorporated herein by reference. The parties desire to amend and revise the Agreement solely as set forth in this Amendment. Unless otherwise set forth in this Amendment, the terms defined within the Agreement and its Exhibits, Schedules, and Attachments shall also apply to this Amendment.
1
| 1. | CONSTRUCTION OF AGREEMENT. |
Except for Section 11 of this Amendment, in no way shall this Amendment revise or alter the terms of the Initial Agreement or Amendment #1. For purposes of RESX and AE Interactive, this Amendment applies only to User’s Interactive Unit.
| 2. | DEFINITIONS. |
Any capitalized terms not defined herein shall have the meaning ascribed to them in the Initial Agreement.
2.1 “AE Interactive” - Means TRX’s proprietary service bureau service customized expressly for User’s Interactive operational units and described in Exhibit B to this Amendment.
2.2 “Interactive Unit” - Means User’s Interactive Operations unit currently headquartered at 15000 XX 00xx Xxxxxx, Xxxxx Xxxxx, XX xith additional offices at New York, New York; Montreal, Canada, Nice, France; Phoenix, AZ; Stockholm, Sweden; or any other location for such operations that may hereinafter be utilized, including other wholly owned User Corporate Travel units selling and servicing interactive booking and fulfillment including operations in Australia and Latin America.”
2.3 “RESX Services” - Means the service that User shall offer its customers, in its sole discretion, whereby TRX provides access, use and support of TRX’s proprietary online booking service for User’s customers over the Internet, as described in Exhibit H, Description of RESX Services. RESX Services and ResAssist shall be used interchangeably in this Amendment.
2.4 “Smart Alert” - Means a nonrefundable ticket tracking and notification service that is available for use with EnCoRRe, AE Lite and AE Interactive for an additional fee.
2.5 “Custom Modifications” - Means changes to RESX, AE Interactive, and Smart Alert (the “Services”), requested by User and agreed to by TRX, that change existing functionality of the software to meet specific needs of User, for which User will be charged an additional fee or fees that will be negotiated and mutually agreed to in writing. Ownership of all custom modifications and all proprietary rights related thereto shall remain with TRX.
| 3. | GRANT OF RIGHTS. |
3.1 Grant of Rights by TRX. TRX hereby grants to User the right to use the RESX Service, AE Interactive, and Smart Alert under the terms and conditions of this Amendment on a worldwide basis. The grant of rights herein is limited solely to the Interactive Unit for the RESX Service and AE Interactive. User shall not, in any event, authorize third parties to further distribute Smart Alert, RESX Services or AE Interactive, provided however that travel agencies that have either signed a franchise or licensee agreement with User (“Representatives”) or in which User holds a minority interest (“Joint Venture Partners”) may distribute and resell the RESX Service to their customers as such Representatives or Joint Venture Partners designated solely in User’s discretion, upon notice to TRX in accordance with this Amendment. User shall designate such Representatives and Joint Venture Partners that may distribute and resell the AE Interactive and RESX Service under the terms set forth herein and TRX shall not grant rights pursuant to this Amendment to any other Representative or Joint Venture Partner. For designated Representatives and Joint Venture Partners, User agrees to provide service and support for the RESX Service, including performing implementation, issue research and
2
tracking, end user support and communication on product functionality in a manner similar to how User provides these services to its online booking clients. User shall indemnify and hold harmless TRX from third party claims of a designated Representative or Joint Venture Partner with respect to the RESX Service due to the negligence or misconduct; acts or omissions; breach of any of the obligations, representations and warranties of User set forth herein; or breach of contract with an end user unless such claim is due to the negligence, misconduct, act, omission, breach of any obligation, representation or warranty or breach of contract of TRX.
3.2 Grant of Rights by User. Subject to the terms and conditions of this Amendment and the Agreement, User hereby grants to TRX a limited, non-exclusive, non-transferable, worldwide, royalty- free license to use, reproduce, display, and transmit the User Marks (as defined in Section 1.3 of Amendment #1 to the Initial Agreement), as provided by User, solely within AE Interactive, the RESX Services and Smart Alert for use by User as specified and approved by User. User reserves the right to revoke this license at any time by providing TRX with written notice.
3.3 No Exclusivity. It is expressly understood and agreed that this Amendment does not grant either party an exclusive privilege to provide or receive the services and products or comparable products and services, as the case may be, provided by TRX hereunder. User may contract with other suppliers for the procurement of comparable products or services, and TRX may contract with other distributors for the distribution of its products and services.
| 4. | OWNERSHIP. |
4.1 By TRX. User acknowledges and agrees that nothing in this Amendment or the Agreement will confer in User any right of ownership in RESX, Smart Alert, or AE Interactive. No licenses are granted by either party except for those expressly set forth in this Amendment. TRX further agrees that the processes and services within User’s Interactive Unit fulfillment centers and operations are highly confidential and proprietary to User, and under no circumstances will information on these processes or operations be shared outside of TRX, and within TRX they will be shared only on a “need to know” basis in order to provide the services under this Amendment. TRX further agrees that the business requirements given to TRX to customize AE Interactive for use by User, as well as the configuration settings and programming performed by TRX to customize AE Interactive for use within User’s Interactive Unit fulfillment centers, will b e highly confidential and proprietary to User and will not be shared outside of TRX and only within TRX on a “need-to-know” basis to provide services under this Amendment.
4.2 By User. TRX acknowledges and agrees that nothing in this Amendment or the Agreement will confer in TRX any license or right of ownership in the User Marks.
| 5. | SUPPORT SERVICES PROVIDED. |
5.1 During the term of this Amendment, and in addition to the attached Service Level Agreement in Exhibit A, TRX will provide the following maintenance and support services for AE Interactive and the RESX Service (the “Services”) to User:
| (a) | Electronic Support. TRX will provide reasonable consultation and support to User’s Operational Representatives via the Internet in response to inquiries from User regarding the operation of the Services, including both technical and User |
3
| issues, and consultation regarding how to use the Services to meet particular needs. |
| (b) | Telephone Support. TRX will provide support by telephone in response to Severity Level I or Severity Level 2 Errors for the RESX Services, as defined in Exhibit A. |
| (c) | New Releases. TRX will provide to User, * , use of such Enhancements and Upgrade Releases to AE Interactive which are generally made available at no charge too there service bureau users, together with the relevant documentation. TRX reserves the right to charge an additional fee for any Custom Modifications to AE Interactive. All Software and Software Releases made available to User under this Amendment shall be subject to the terms and restrictions set forth in the Agreement. |
| (d) | Error Correction. In the event User encounters an error, bug or malfunction in the Services, User shall promptly provide written notice to TRX, describing the problem and indicating the severity of same. TRX shall verify the cause of the problem, and if the error is due to any act or omission of TRX, TRX’s sole obligation shall be to use its commercially reasonable efforts to correct the reported problem. Further, TRX agrees that it shall make all high priority errors known to User in a reasonable timeframe after TRX becomes aware of such error. TRX MAKES NO REPRESENTATION OR WARRANTY THAT ALL BUGS, ERRORS OR MALFUNCTIONS CAN BE CORRECTED, NOR THAT THE SERVICES WILL OPERATE ERROR FREE. |
| (e) | On-Site Support. If, at User’s request, the maintenance and/or support requires a visit to the User’s facilities, User shall bear all of TRX’s out-of-pocket expenses for travel, lodging, meals and similar costs, in addition to the on-site visit fee as set forth on Exhibit B-2 hereto. |
| 6. | PRICING AND PAYMENT. |
6.1 Pricing. The fees for the Services provided pursuant to this Amendment are set forth on Exhibit B hereto. TRX will invoice User for all amounts due. TRX shall utilize the * to facilitate invoicing and payment.
6.2 Payment. All transaction fee payments shall be paid no later than * in immediately available U.S. Dollars without withholding, deduction or offset. User shall * The estimate shall be * For example, * TRX shall invoice * including as well any reconciliations for overpayments or underpayments as calculated according to Section 6.3. Such * is not contingent upon User’s collection efforts from its customers. User shall pay interest on all amounts not paid when due at the rate of * or the highest lawful rate, if less. Any credit due User shall be reconciled against * after such credit obligation accrued. If User in good faith disputes the amount of any invoice, User shall have ten (10) days from the receipt of said invoice to provide
4
* CONFIDENTIAL TREATMENT REQUESTED
TRX with a written “Dispute Notice”, detailing the amount and nature of any dispute regarding such invoice. If User tenders a Dispute Notice, User shall not be relieved of its obligation to pay any undisputed amounts as required under this Amendment. After TRX has received the Dispute Notice, both parties shall work in good faith to diligently come to terms regarding the disputed amount. If no resolution is reached within seven (7) days of TRX’s receipt of a Dispute Notice, TRX shall, in its sole discretion, continue negotiations or submit the matter to binding arbitration in accordance with the Initial Agreement.
6.3 Reconciling Payment. TRX shall reconcile each * against actual transaction costs for * . Any overpayment by User shall be credited towards User’s account and such credit shall be reflected on the following * after such obligation accrued. Any underpayment by User shall be included as a debit in the following * . Payment method shall be via *
| 7. | TERM OF THIS AMENDMENT. |
7.1 The initial term (“Initial Term”) of this Amendment shall be three (3) years from the Effective Date of this Amendment. This Amendment shall automatically renew for successive one (1) year terms unless either party provides the other with written notice of cancellation of this Amendment at least one hundred eighty (180) days prior to the expiration of the then-current term.
7.2 TRX may provide written notice of its intention to increase fees in any term after the Initial Term. TRX will work in good faith to provide such notice including all details of the new pricing at least three hundred and sixty five (365) days prior to expiration of the then current term. If the proposed new fees are unacceptable to User, User must provide written notice of termination at least one hundred eighty (180) days prior to the expiration of the then current term.
| 8. | USER OBLIGATIONS. |
8.1 User shall designate one (1) User representative to serve on the TRX RESX Advisory Group. The named individual will actively participate in meetings, as reasonably scheduled and assist TRX in establishing standards for the use of the service (the initial RESX Advisory Representative being named on Exhibit C).
8.2 User shall designate three (3) Operational Representatives (the initial Operational Representatives being named on Exhibit C) who will be the contact persons through which all support and/or problem communications will be made. User’s Operational Representatives will train and support User’s clients. User may, from time to time, change or add Operational Representatives, which change shall be effective only upon TRX’s receipt of written notice thereof. User shall ensure that any appointed Operational Representative has successfully completed the TRX certification program.
| 9. | PRESS RELEASES. |
Except as provided in Section 3.2 and Section 10.16 of this Amendment and Section 8.1 of Amendment #1, TRX shall not use User Marks in any advertising, publicity releases, client listing or any other materials or in any other manner without the User’s prior written approval from the User’s Public Affairs department. Neither party shall issue a press release or make any
5
* CONFIDENTIAL TREATMENT REQUESTED
public statement relating to the relationship set forth in this Amendment until such press release or public statement has been mutually agreed. Any press or media coverage in connection with this Amendment will be subject to the prior written approval of both parties consistent with Section 3.6 of the Initial Agreement.
| 10. | RESX. |
10.1 Appointment. TRX hereby appoints User, for the Initial Term and any subsequent terms thereof of this Amendment, as a non-exclusive distributor of ResAssist, subject to all of the terms and conditions of this Amendment and the Initial Agreement, where applicable. TRX grants to User the right to directly promote, market, and resell the RESX Services (as such RESX Services are described in Exhibit H) to its customers subject to the terms herein. User shall have its customer execute an agreement no less restrictive or less protective of TRX than the minimum terms and conditions specified in Exhibit D.
10.2 Branding. User shall have the right to display the RESX Services using User’strademarks and other branding characteristics (including but not limited to the URL and domain name, tool bars, desktop icons, shortcuts and help screens), as determined by User. The RESX Services must include the “Powered by RESX” logo (to be provided by TRX to User) on the customer login screen in size and dimension mutually agreed to by both parties. All other references to TRX and RESX Service will be removed from the RESX Service sites.
10.3 Upgrades and Enhancements. All upgrades and enhancements (“Upgrades and Enhancements”) to the RESX Service that are made generally available will be made available to User at a date no later than they become available to TRX clients or other clients or other distributors and at pricing, terms and conditions that shall be no less favorable than those offered to other TRX distributors. User will have full access to use and distribute all features and services of the RESX Service, as such use is determined by User in its sole discretion. TRX reserves the right to charge an additional fee for any Custom Modifications.
10.4 Promotion. TRX agrees not to sell an end-to-end travel solution that includes Customer Care directly to clients with whom User has a then-current contractual relationship for travel services. For purposes of this Amendment, “Customer Care” shall mean the provision of assistance to travelers via telephone or other electronic means such as e-mail or online chat or any other means.
10.5 Functionality and GPS. TRX shall make commercially reasonable efforts to make available the same features and highly comparable functionality on RESX to User on each User reservation system including: SABRE, Apollo, Worldspan, Galileo, and in v3.0 of RESX,Amadeus, and any other reservation systems that TRX may offer to its clients and distributors for the Initial Term and any subsequent terms of this Amendment.
10.6 Restrictions. TRX reserves the right, in its sole discretion and with no less than thirty(30) days prior written notice to User, to modify, discontinue, add, adapt, or otherwise change any design or specification of the RESX Service or TRX’s policies, procedures, and requirements specified in or related hereto; provided, however, User shall have the right to provide any comments and requests to TRX that TRX continue to provide to User such portions of the RESX Service, at User’s sole discretion, to the extent that such portions of the RESX Service are deemed valuable to User. Further, TRX and User acknowledge and agree to discuss TRX continuing to provide such portions of the RESX Service and if requested by User TRX
6
agrees to provide a good faith estimate to User the cost for continuing to provide such portions of the RESX Service exclusively for User at User’s own expense.
10.7 Service Level Agreement. In addition to the requirements set forth in this Amendment,TRX agrees that its performance will meet or exceed each of the applicable terms of the Service Level Agreement (“SLA”) set forth in Exhibit A, as the same may be modified from time to time, subject to the limitations and in accordance with the provisions set forth in this Amendment.
10.8 Training & Support.
| (a) | Sales and Marketing Training. TRX agrees to provide in-depth sales training and support, to a reasonable number of User personnel on no less than an annual basis as agreed by the parties. Such training shall include the provision of functional documentation. It is the intent of both parties that User would be fully capable of independently selling, installing and providing customer service for the RESX Service (except for the obligations allocated to TRX under this Amendment).TRX will make its marketing and sales support personnel available to support User in joint sales calls, as User may reasonably request. |
| (b) | Administrator and Technical Support Training. Upon execution of this Amendment, in addition to the Sales and Marketing training specified in Section10.8(a) of this Amendment, User personnel shall be required to attend Administrator and Technical Support Training so that it may provide first level technical support to its customers. The training shall be conducted at the TRX facility and shall be provided at no additional charge for up to twenty (20) qualified User personnel per year. User shall be responsible for all travel and related expenses associated with its participation in such training. |
| (c) | Administrator and Technical Support Certification. After completion of Administrator Technical Support Training, each attendee at such training shall be required to take and pass an Administrator and Technical Support Training certification test which shall be no more stringent to User personnel than that required of TRX personnel who perform the same or similar services. Such passage shall be required before User may use the RESX Services to set up‘customer sites’ for its customers |
| (d) | Annual Recertification. Annually, after initial certification, at no additional cost to User (except for User’s expenses in attending such training), User’s personnel shall be required to attend additional administrator and technical support training and pass a recertification test. Failure to attend such training and pass such recertification test shall result in such User personnel’s inability to access the RESX Services for purposes of setting up customer sites and supporting its customers. In the event any individual User personnel fails to pass the recertification test, TRX agrees to re-administer the test after such personnel complete any additional training requirements requested by TRX. Any and all expense associated with such re-training and re-administration of tests shall be borne by User. |
| (e) | Implementation Certification. After completion of the Administrator and Technical Support Training and Certification, User’s personnel designated by |
7
| User who have completed such training and certification, shall participate in two (2) implementation projects. The criteria for receiving Implementation Certification shall be provided by TRX in writing. |
10.9 Rules of Engagement for Customers. User will be the point of contact for sales efforts to existing and prospective business travel service customers of User regarding the RESX Services.
10.10 Testing and Test Sites. TRX further agrees to provide User with additional RESX Service sites as mutually agreed by the parties but in no case less than five (5) sites with one on each GDS for the purposes of sales demonstrations, configuration testing, performance monitoring and product testing. TRX reserves the right to restrict User’s testing if such testing, in TRX’s sole and reasonable discretion, adversely impacts performance of the RESX Services generally in which case TRX will provide performance measurements that document the adverse impact to User and work in good faith to enable User to monitor TRX sites in ways that do not adversely impact the system. TRX also reserves the right to charge additional fees for GDS hits created or CPU/bandwidth usage as part of User’s testing of the system.
10.11 Clearances and Fees for Features. To the extent that fees are required to be paid to third parties, with the exception of GDS fees, for the permissible use of any functionality, feature or aspect of the Sites obtained by TRX from third parties (other than Customers), TRX shall promptly secure such rights and pay all necessary clearance fees without additional charge to User.
10.12 Reporting. TRX will provide User with a monthly report in a mutually agreed upon electronic format containing the following information about each and every Passenger Named Record (“PNR”) created by User and User’s customers within the RESX service:
User ID
Planner ID
User name
Planner name
Corporate ID
PNR record locator
Traveler’s first and last name
PNR’s created
In addition, TRX agrees to use commercially reasonable efforts to add to the information available in the monthly report to also include the booking date, the dates of travel, and whether the PNR included an air, car or hotel segment or any combination of the three. TRX will also provide a standard library of reports that are available to all RESX distributors. Upon request and for an additional fee TRX will create Custom Modifications to reports for User at the standard rates for custom programming found in Exhibit B-2.
10.13 Bug Fixes. All bug fixes shall be handled according to the terms of Section 5.1(d) of this Amendment and the SLA in Exhibit A.
10.14 Transition Services After Expiration or Termination. In connection with the termination of this Amendment for any reason except for User’s failure to pay in which case TRX shall have no obligations under this Section 10.13, TRX shall provide to User such termination assistance as User may reasonably request in order to provide an orderly transition from TRX to another supplier (“Transition Services”), including but not limited, to a redirect of User’s customer’s
8
URLs. TRX shall be reasonably compensated for its efforts in the transition of clients or client data to another vendor. User shall pay TRX its standard hourly rate specified in Exhibit B-2 for such termination assistance. User shall pay for all products and services provided by TRX pursuant to this Section, provided that if termination was by reason of a payment default by User, TRX shall not be obligated to provide such termination assistance. Such assistance shall be provided for up to * and shall begin on the expiration or termination date of the Amendment as specified in Section 7.1 of this Amendment. In the event of expiration or termination of this Amendment due to a breach by TRX, TRX shall provide Termination Services to User as detailed above * Except in the event of application of Section 10.18(b), TRX agrees not to directly solicit User’s clients for online booking services during the period of Transition Services, unless expressly authorized by User or User’s clients in writing.
10.15 Development Input. TRX agrees to meet frequently and regularly as part of the RESX Advisory Board and as reasonably requested by User to review status on product issues/bugs and to discuss the development and prioritization of new product features and enhancements. TRX agrees to take input and prioritization from User on the development of new features and give it as much if not more weight and prioritization as that of TRX’s other clients and distributors.
10.16 Information Protection Requirements. TRX agrees to comply with the requirements of Exhibit E of this Amendment. In the event that the terms of the Exhibit E of this Amendment conflict with any other terms of this Amendment, the terms of the Exhibit E of this Amendment shall prevail.
10.17 Press Releases. Neither party may issue press releases or publicity identifying the other using the other’s trademarks without the prior written approval of the other party.
10.18 Effect of Termination:
| (a) | Termination of Amendment. Upon termination of this Amendment: (1) User shall immediately cease marketing and use of the RESX Services, in any manner whatsoever except to support existing customers during the Transition Period as specified in Section 10.14 of this Amendment, and return all copies of documentation, marketing and other related materials to TRX; (2) all rights and licenses granted to User hereunder solely for the servicing and support of User’s customers (as of the effective date of termination) shall continue; (3) TRX shall terminate User’s access to the RESX Services for new customers; (4) all rights and licenses for User’s use of AE Interactive shall immediately cease; (5) all payments for AE Interactive shall be immediately due and payable; (6) all payments for RESX Services owed TRX shall continue to be due and payable according to the terms of this Amendment; (7) TRX shall cease all use of Users’ Marks as specified in Section 3.2 of this Amendment; and (8) TRX shall destroy all User customer data or return such data to User as requested by User in writing; provided, however, TRX may retain such User customer data solely for the purpose of supporting Users’ customers’ sites and for providing Transition Services to User. Notwithstanding anything to the contrary contained in this Amendment, Section 8.2 of the Initial Agreement shall apply for purposes of this Amendment. |
| (b) | Failure to Support Current Customers. Upon termination hereof, and solely in the event User fails to support its customers or pay fees as required by this |
9
* CONFIDENTIAL TREATMENT REQUESTED
| Amendment, TRX shall continue to process User’s customer’s transactions for a reasonable time (not to exceed thirty (30) days), or until such time as the customer: (1) enters into a User contract with a third party; (2) contracts directly with TRX for the provision of RESX Services; or (3) provides written notice to TRX of its desire to no longer utilize the RESX Services. |
| (c) | Survival. Provisions hereof which by their context and content are intended to survive termination hereof shall so survive, including Sections 4, 6, 10.16, 10.17 and 11.8, of this Amendment and Sections 3, 5, 6 and 7 of the Initial Agreement and as amended in this Amendment. |
10.19 Customer Attrition. TRX agrees that at the written request of User it will assume the service and support for any RESX Service site should the client leave User for any reason and such customer shall be handled according to the terms of Section 10.18(b).
10.20 Software Escrow. At User’s written request and expense, TRX agrees to enter into an escrow agreement with the escrow agent of TRX’s choice.
| (a) | If the parties under this Amendment agree in writing to put the source code upon which the RESX Services (“Source Code”) are based and the documentation related thereto for the Source Code into escrow (“Escrow Deposit”), TRX shall add User as a beneficiary to an escrow agreement (the “Escrow Agreement”) within thirty (30) days of the execution of this Amendment. |
| (b) | User shall be entitled to receive, and the Escrow Agreement shall provide for User to receive, a copy of the Escrow Deposit in the event any one of the following release conditions occur: |
| (i) | if TRX has availed itself of, or been subjected to by any third party, a proceeding in bankruptcy in which TRX is the named debtor, an assignment by TRX, or any other proceeding involving insolvency or the protection of, or from creditors, and same has not been discharged or terminated without any prejudice to User’s rights or interests under this Amendment within sixty (60) days; or |
| (ii) | if TRX (or a successor entity or authorized third-party) has ceased its ongoing business operations, or licensing of the RESX Services or any successor services thereto. |
| (c) | If TRX corrects any defects in, or provides any revisions, updates, modifications, enhancements, corrections or new releases to the RESX Services under this Amendment TRX shall within thirty (30) days of such release amend the Escrow Deposit and furnish the escrow agent with a corrected or revised copy of the Escrow Deposit. |
| (d) | Upon release of the Escrow Deposit, User will have a license to use the Escrow Deposit solely for the purpose of maintaining the Escrow Deposit. No ownership or other intellectual property right in the Source Code or Escrow Deposit is conveyed to User. The Escrow Deposit is provided to User for the sole and limited purpose of maintenance of the RESX Services in User’s business and all other rights, licenses, and obligations set forth herein shall continue in full force and effect. User acknowledges and agrees that it shall only use the Escrow |
10
| Deposit for this limited purpose. User further acknowledges that, other than expressly set forth in this Amendment, it has received no distribution rights whatsoever, by implication or otherwise, in the Escrow Deposit by execution of this Amendment or receipt of the Escrow Deposit. |
| (e) | User shall be entitled to verify that all Escrow Deposit required to be placed into escrow have been placed into escrow in accordance with this Amendment. |
10.21 Acceptance by User. For purposes of this Amendment, the following language for “Acceptance” relates to the RESX Services only and does not supercede the acceptance language contained in Sections 2.8 and 2.9 of the Initial Agreement: User shall conduct acceptance testing of the RESX Services as set up by TRX for User. After the parties have completed the modifications to private label the RESX Services (but in no event later than sixty (60) days after the Effective Date of this Amendment), the acceptance test shall be conducted, to demonstrate that the RESX Services perform in accordance with TRX specifications (specifically including the TRX specifications for functionality allowing trained and certified User personnel to install the RESX Service site without TRX assistance) and User specifications as set forth in Section 10.2 and Exhibit E of this Amendment. Such testing shall continue for a maximum of thirty (30) days. Upon completion of the testing, User shall notify TRX in writing of its acceptance. If the XXX Services do not pass the acceptance test, User shall notify TFX, specifying in reasonable detail in what respects the RESX Services have failed to perform. TRX shall work in good faith to correct any deficiencies disclosed by the acceptance test. User shall then repeat the test for an additional thirty (30) days. If the RESX Services fails to pass the second acceptance test, User shall have the option of: (1) immediately terminating the portions of this Amendment that relate to the User’s ability to distribute the RESX Services without penalty, except for the payment of transaction or other fees as detailed in this Amendment, or (2) continuing the acceptance test for a final thirty (30) day period; provided, however, that User’s termination option shall remain available to User during any such continuation.
10.22 Portal Integration. TRX agrees to work to make RESX functional and compatible with User’s proprietary portal that will be distributed to User’s corporate travel clients. This functionality will include the ability to:
| (a) | * |
| (b) | * |
| (c) | * |
| (d) | * |
| (e) | * |
11
* CONFIDENTIAL TREATMENT REQUESTED
| (f) | * |
User and TRX agree to work together and use commercially reasonable efforts to create detailed engineering specifications for the above listed functionality within ninety (90) days of the Effective Date of this Amendment. Within two (2) weeks of the completion of the detailed engineering specifications, TRX agrees to provide an estimate, in good faith, of timelines to develop the above-listed functionality, which timelines will then be mutually discussed and agreed upon, with TRX giving the development high priority on its development schedule. TRX agrees to use commercially reasonable efforts to complete the functionality within those mutually agreed timelines.
10.23 Third Party Content. TRX agrees that RESX as distributed by User will not contain links to any Internet Web sites or third-party content that contains advertising or promotional material for any goods and services other than User’s, except as specifically approved by User in writing.
10.24 PRDS Integration. TRX agrees to enable a regular feed from User’s Preferred Rate Database Service (PRDS) into RESX for the purpose of loading and updating information on client’s negotiated rates for individual hotel properties.
10.25 Service Fees by Vendor. TRX agrees to enable RESX to display and total additional service fees that User may wish to charge for any particular air, car or hotel vendor as configured and designated by User across any and all User client sites. User and TRX agree to work together and use commercially reasonable efforts to create detailed engineering specifications for the above listed functionality within * of the Effective Date of this Amendment. Within * of the completion of the detailed engineering specifications, TRX agrees to provide an estimate, in good faith, of timelines to develop the above-listed functionality, which timelines will then be mutually discussed and agreed upon, with TRX giving the development high priority on its development schedule. TRX agrees to use commercially reasonable efforts to complete the functionality within those mutually agreed timelines.
10.26 Preferred Supplier Uploads. TRX agrees to develop the ability to regularly upload databases of preferred supplier information in mutually agreed upon format into RESX so that User and User’s clients’ preferred suppliers will be highlighted and can be modified automatically by a database upload to the RESX system. User and TRX agree to work together and use commercially reasonable efforts to create detailed engineering specifications for the above listed functionality within * of the Effective Date of this Amendment. Within * of the completion of the detailed engineering specifications, TRX agrees to provide an estimate, in good faith, of timelines to develop the above-listed functionality, which timelines will then be mutually discussed and agreed upon, with TRX giving the development high priority on its development schedule. TRX agrees to use commercially reasonable efforts to complete the functionality within those mutually agreed timelines.
10.27 Mandatory Password Length. TRX agrees to enable RESX to require that passwords have a * that are a mix of numbers and letters in order to allow end users into the system, and to have this be configurable as designated by User across any and all User client sites. User and TRX agree to work together and use commercially reasonable efforts to create detailed engineering specifications for the above listed functionality within * of the Effective Date of this Amendment. Within * of the completion of the
12
* CONFIDENTIAL TREATMENT REQUESTED
detailed engineering specifications, TRX agrees to provide an estimate in good faith of timelines to develop the above-listed functionality, which timelines will then be mutually discussed and agreed upon, with TRX giving the development high priority on its development schedule. TRX agrees to use commercially reasonable efforts to complete the functionality within those mutually agreed timelines.
| 11. | MISCELLANEOUS. |
11.1 Amendment to Exhibit B of Amendment #1 shall be deleted in its entirety and replaced with Exhibit X-x attached hereto and incorporated herein.
11.2 .Balance of Terms Unchanged. Except as expressly set forth in this Amendment, the terms and conditions of the Agreement shall continue in full force and effect. This Amendment shall be effective as of the 6 day of June 2003 (“Effective Date”).
11.3 Entire Agreement. The Agreement, along with this Amendment, all previous amendments and addenda, including all Exhibits and Schedules attached hereto and thereto represent the entire understanding and agreement between the parties with respect to the subject matter hereof, and supersedes any and all previous discussions and communications regarding such subject matter. Any subsequent amendments and/or additions hereto are effective only if in writing and signed by both parties.
11.4 Precedence. With respect to the subject matter of this Amendment only, in the event of a conflict between the Agreement and this Amendment, this Amendment shall control and govern.
11.5 For purposes of this Amendment, Section 6.2 of the Initial Agreement shall be amended to include the word “AND” at the very beginning of the fourth line so that it reads as follows:
“6.2 BOTH PARTIES AGREE THAT USER’S LIABILITY (UNDER BREACH OF CONTRACT, NEGLIGENCE, STRICT LIABILITY OR OTHERWISE), IF ANY, FOR ANY DAMAGES RELATING TO THIS AGREEMENT SHALL BE LIMITED TO ACTUAL DAMAGES AND SHALL NOT, EXCEPT IN THE CASE OF A BREACH BY USER OF ITS OBLIGATIONS UNDER SECTIONS 3.2, 3.3, 3.4 OR 3.5 HEREOF, EXCEED THE AMOUNTS P AID B Y U SER DURING THE TERM HEREOF, AND SHALL NOT INCLUDE CONSEQUENTIAL, INCIDENTIAL, INDIRECT, SPECIAL OR OTHER DAMAGES OF ANY KIND, INCLUDING LOSS OF PROFITS, EVEN IF USER HAS BEEN ADVISED OF THE LIKELIHOOD OF THE OCCURENCE OF SUCH DAMAGES.”
11.6 Export. In the event that any of the deliverables (or any component thereof) contains encryption, TRX shall provide the information set forth in Exhibit G of this Amendment.
TRX represents that it has complied with, and will continue to comply with, all applicable laws, rules and regulations of the United States or any foreign countries with respect to the exportation or importation of the deliverables, any modifications, enhancements or updates thereto, and any technical data derived therefrom, outside of the United States or into the United States or into another country, including, but not limited to obtaining any necessary consents and requesting or filing any documents with the U.S. respective regulatory agency (“USGOV”).
Unless the parties otherwise agree in writing, TRX shall have the responsibility under this Amendment to obtain approvals, consents, licenses, and/or permits required for any export or import of the deliverables, including, but not limited to making the appropriate filings with the
13
USGOV, and shall be solely responsible for all costs associated therewith. Each party will reasonably cooperate with the other in making the appropriate filings with USGOV and any applicable foreign authority and will provide any information, certificates or documents as are reasonably requested.
11.7 Equity Issuance. TRX (for purposes of this Section 11.7 shall be referred to as “Issuer”) and User are parties to a Warrant Agreement, dated July 24, 2000, in place, and such Warrant Agreement is in full force and effect. In addition, Issuer and User agree to evaluate, for a period of ninety (90) days from the date hereof, a new direct equity relationship whereby User would acquire up to five percent (5%) of the equity of Issuer (on a fully diluted basis) in shares of preferred stock of Issuer on terms that are mutually agreeable to Issuer and User. If Issuer and User are unable to come to mutually agreeable terms for a new direct equity relationship within the ninety (90) day period specified herein, User may submit a proposal regarding a new warrant relationship for Issuer’s review. To the extent User submits such a proposal, Issuer agrees to review such proposal promptly and use reasonable efforts to enter into a new warrant relationship with User within a reasonable time thereafter, it being understood that entering into such relationship shall be at Issuer’s sole discretion.
11.8 Indemnification and Limitation of Liability. For purposes of this Amendment only, the parties agree as follows:
| (a) | By TRX. TRX agrees to defend, indemnify, and hold harmless User, Representatives, Joint Venture Partners, other TRX authorized (in writing) users of the services provided under this Amendment, and entities controlled by, under common control with, or controlling User (control and controlling being defined as ownership of at least fifty percent (50%) of the equity interest), and each of their respective directors, officers, employees, and agents from and against any and all third party claims, demands, and liabilities, including reasonable attorneys fees, resulting from or arising out of: (i) the services provided under this Amendment actually or allegedly infringing or violating any patents, copyrights, trade secrets, licenses, or other intellectual property rights of a third party; (ii) any breach of TRX’s representations and warranties in this Amendment; or (iii) failure to comply with TRX’s obligations under any and all laws, rules or regulations applicable to TRX or the services provided under this Amendment. |
| (b) | By User. User agrees to defend, indemnify, and hold harmless TRX and entities controlled by, under common control with, or controlling TRX (control and controlling being defined as ownership of at least fifty percent (50%) of the equity interest), and each of their respective directors, officers, employees, and agents from and against any and all third party claims, demands, and liabilities, including reasonable attorneys fees, resulting from or arising out of: (i) any breach of User’s representations and warranties in this Amendment; or (ii) User’s knowing or intentional failure to comply with User’s obligations under any and all laws, rules or regulations applicable to User under this Amendment, except to the extent such violation arises out of TRX’s obligations hereunder. |
| (c) | Procedure. A party seeking indemnification (the “Indemnified Party”) shall promptly notify the other party (the “Indemnifying Party”) in writing of any claim for indemnification, provided, that failure to give such notice shall not relieve the |
14
| Indemnifying Party of any liability hereunder (except to the extent the Indemnifying Party has suffered actual material prejudice by such failure). The Indemnified Party shall tender sole defense and control of such claim to the Indemnifying Party. The Indemnified Party shall, if requested by the Indemnifying Party, give reasonable assistance to the Indemnifying Party in defense of any claim. The Indemnifying Party shall reimburse the Indemnified Party for any reasonable legal expenses directly incurred from providing such assistance as such expenses are incurred. The Indemnifying Party shall have the right to consent to the entry of judgment with respect to, or otherwise settle, an indemnified claim only with the prior written consent of the Indemnified Party, which consent shall not be unreasonably withheld; provided, however, that the Indemnified Party may withhold its consent if any such judgment or settlement imposes an unreimbursed monetary or continuing non-monetary obligation on such Party or does not include an unconditional release of that Party and its Affiliates from all liability in respect of claims that are the subject matter of the indemnified claim. |
| (d) | Limitation of Liability. EXCEPT FOR (A) A PARTY’S INDEMNIFICATION OBLIGATIONS UNDER THIS AMENDMENT, (B) A PARTY’S GROSS NEGLIGENCE OR WILLFUL MISCONDUCT, (C) A PARTY’S VIOLATION OF ITS CONFIDENTIALITY OBLIGATIONS HEREUNDER, (D) DEATH, BODILY INJURY OR PROPERTY DAMAGE CAUSED BY SUCH PARTY, THE PARTIES AGREE THAT EACH PARTY’S RESPECTIVE LIABILITY (UNDER BREACH OF CONTRACT, NEGLIGENCE, STRICT LIABILITY, OR OTHERWISE) IF ANY, FOR ANY DAMAGES RELATED TO THIS AMENDMENT SHALL NOT EXCEED THE GREATER OF THREE HUNDRED SEVENTY-FIVE THOUSAND DOLLARS ($375,000.00) OR THE AMOUNTS PAID OR PAYABLE BY USER DURING THE TERM HEREOF. EXCEPT FOR TRX’S INDEMNIFICATION OBLIGATIONS UNDER THIS AMENDMENT, NEITHER PARTY SHALL BE LIABLE FOR CONSEQUENTIAL, INCIDENTAL, INDIRECT, SPECIAL, OR OTHER DAMAGES OF ANY KIND, INCLUDING LOST PROFITS, EVEN IF ADVISED OF THE LIKELIHOOD OF THE OCCURRENCE OF SUCH DAMAGES. |
| TRX TECHNOLOGY SERVICES, L.P. | AMERICAN EXPRESS TRAVEL RELATED SERVICE COMPANY, INC. | |||||||
| BY: |
/s/ Xxxxx Xxxxxxxx |
BY: |
/s/ Xxxxxx Xxxxxx | |||||
| NAME: |
Xxxxx Xxxxxxxx |
NAME: |
Xxxxxx Xxxxxx | |||||
| TITLE: |
GM |
TITLE: |
SNR Manager | |||||
| DATE: |
June 6, 2003 |
DATE: |
June 10, 2003 | |||||
15
EXHIBIT A
SERVICE LEVELS
TRX agrees to provide the following services in support of ResAssist/RESX:
| 1) | The Support Services department will be staffed and available by phone and e-mail between the hours of * , Monday through Friday. The Support Services department will provide support to User personnel for all functional and technical problems with ResAssist/RESX. |
| 2) | The Data Center is monitored twenty four (24) hours per day, seven (7) days per week. |
| 3) | Customer Support Analysts will act as second level support for User’s designated Operational Representatives. |
| 4) | After hours, weekends, and during holidays, emergency support is provided via pager. Once paged, TRX support personnel will respond to the page via telephone call within * . |
| 5) | The Support Services department will not be staffed on the following days: |
| a. | New Year’s Day |
| b. | Memorial Day |
| c. | Fourth of July |
| d. | Labor Day |
| e. | Thanksgiving Day |
| f. | Friday following Thanksgiving |
| g. | Christmas Eve |
| h. | Christmas Day |
| i. | Saturday & Sunday |
Points of Contact and Escalation Plan:
| 1. | User’s Operational Representatives – respond to end user questions regarding use of the services; |
| 2. | Support Desk – assist User’s administrators with questions/issues regarding administration or functionality, initiate custom programming requests; |
| 3. | Support Manager – respond to administrative or functionality issues that are not resolved through standard support; |
| 4. | Director and/or Manager of Development – respond to custom programming requests, errors causing loss of functionality not resolved by intermediate workaround; |
| 5. | Vice President – final resolution of unresolved issues. |
16
* CONFIDENTIAL TREATMENT REQUESTED
Error Definition, Estimated Response and Status Notification Time Frames:
| SEVERITY LEVEL |
ERROR DEFINITION |
RESPONSE TIME |
1. STATUS | |||
| 1 | Substantial ratio of air, car or hotel reservations cannot be completed or travel policy cannot be enforced. Day-to-day functions are rendered unusable and no practical workaround is available. User’s IT personnel are unable to diagnose or rectify the problem. | Immediate work to start and best effort to rectify remotely within * . | Immediate notification upon discovery of a Severity 1 Error by phone. Updates every hour that give status of the error, details on the nature and severity of the error and estimates of time to resolution. Within * of resolution of the error, TRX will provide a root cause analysis of the error. | |||
| 2 | (1) An error in day-to-day function, rendering it unusable for a minor number of users or (2) a substantial number of users are affected by a problem with a workaround. | Rectify within * . | Immediate notification upon discovery of a Severity 2 Error. Updates every * that give status of the error, details on the nature and severity of the error and estimates of time to resolution. Within * of resolution of the error, TRX will provide a root cause analysis of the error. | |||
| 3 | Error in a non-mainstream day-to-day function, administrative and reservation processing bugs. | Rectify in next maintenance release. | Notification through mutually agreed upon channels and time frames; Updates on status each release. TRX will provide tracking numbers for each error. | |||
| 4 | Error in a non-mainstream day-to-day function that does not render the function unusable such as text changes, page layouts, isolated reservation problems. | Problem is given a low priority and every endeavor will be made to include it in the next version of Software released. | Notification through mutually agreed upon channels and time frames, Updates on status each release. TRX will provide tracking numbers for each error. | |||
17
* CONFIDENTIAL TREATMENT REQUESTED
System Availability
1) TRX will maintain an Overall Availability of ResAssist/RESX of 99%, as measured by TRX on a monthly basis, with exceptions as noted below. For purposes of calculating Overall Availability, the following are not counted against Overall Availability:
ResAssist/RESX not being available due to scheduled maintenance.
TRX envisages scheduled maintenance once monthly for a period of * . TRX will schedule this maintenance for * . TRX will communicate scheduled maintenance at least three regular business days in advance of such maintenance.
Factors beyond the control of TRX, including, GDS availability, GDS performance, User bandwidth or connectivity, general Internet connectivity or speed issues, etc.
2) As addressed in Section 10.10 of this Amendment, User may monitor the ResAssist/RESX system using Site Scope by Freshwater or similar software to determine an estimate of User Availability. User will consider ResAssist/RESX not available if the monitoring software is not able to perform any of the following functions and lack of performance is prevalent throughout the system: log in, request flights, see flight availability, request pricing, make reservations, or purchase tickets. User will eliminate from its calculation of availability errors clearly attributable to User’s monitoring software, network, bandwidth, site configuration (if solely the monitoring site is affected) or connectivity for the purposes of monitoring.
3) If User’s calculation of User Availability materially differs from TRX’s calculation of Overall Availability then the parties agree to use reasonable efforts to reconcile the calculations and TRX agrees to adjust its Overall Availability calculation if necessary based on these reconciliation procedures.
4) For every one percentage point below * Overall Availability as measured by TRX on a monthly basis, TRX will credit User with * against any fees due TRX for that same time period.
TRX will provide User with reporting on system availability as measured by TRX in its data center on a monthly basis. The reporting will include measures of server uptime, as well as measures of Overall Availability that approximate the performance of the system as used by an end user at a User client company.
On-site Support
A Customer Support Analyst will travel to a User location to assist with performance issues if the User’s site administrators have worked directly with Support Services and all remote troubleshooting techniques have been exhausted. User is responsible for all travel-related expenses and any applicable fees.
18
* CONFIDENTIAL TREATMENT REQUESTED
EXHIBIT B
FEES
Exhibit B-1
EnCoRRe Pricing:
| Average Unique Record |
Price per Unique Record Locator Number* | |
| * |
* | |
| * |
* | |
| * |
* | |
| * |
* |
All requests for additional PowerCoRRe routines will be billed at * .
AE Lite Pricing:
One-Time Implementation Fee *
| Average Unique Record |
Price per Unique Record Locator Number* | |
| * |
* | |
| * |
* | |
| * |
* | |
| * |
* | |
| * |
* |
| * | TRX will use existing User GDS lines and Terminal Addresses for servicing this product and pricing does not include Auto-Ticketing or any Power CoRRe routines except for those routines that were developed to establish the AE Lite product offering. All requests for additional routines will be billed at * . The price for AE Lite includes a * per Unique Record Locator Number increase due to the addition of the Frequent Flyer Upgrade module to the AE Lite product. This pricing will replace the pricing that is contained in Amendment #1 of the contract dated June 30th, 2002. The parties further agree that the new pricing for AE Interactive is retroactive to Dec 1st, 2002 to reflect the actual date the module was enabled for the service. |
19
* CONFIDENTIAL TREATMENT REQUESTED
AE Interactive is a mid-office quality control service that will include an agreed upon, finite set of Reservation EditorSM quality control routines, Auto-Ticketing and web-based reports to summarize AE Interactive activity. Any additional services that User may request will be provided by TRX for an additional fee.
AE Interactive implementation fee * .
Pricing for AE Interactive is * per unique record locator number processed.
In order for User to take advantage of the AE Interactive pricing, all unique record locator numbers must have a unique identifier contained within it so that TRX can determine that the record locator was created by an on-line booking tool, any unique record locator numbers not containing an unique identifier will not qualify for AE interactive pricing. AE Interactive will decipher the identifier for User. Any unique record locator numbers not generated from an on-line booking tool will be subject to EnCoRRe pricing.
For User’s client accounts enabled on the “Smart Alert” routine, Clients who are signed up for this service have their records identified within the PNR, if this code is present TRX places them on another queue. That determines whether the fare ticketed is nonrefundable. If it is, the record is set aside on a queue * if not, the PNR is disregarded.
Records identified as part of SmartAlert are revisited at pre-determined frequency (based on codes in the PNR for that customer) for email notification to travelers that they are holding a nonrefundable ticket * .
20
* CONFIDENTIAL TREATMENT REQUESTED
Exhibit B-2
RESX is a fully interactive, automated corporate travel information and reservation system that communicates directly with the GDS. User has access to real-time travel information, vendor displays, and policy controls.
RESX Pricing
For purposes of this Amendment pricing shall be * per PNR created within RESX where user either reserves or submits PNR for purchase and ticketing within the RESX system.
This pricing shall be increased in the following manner:
TRX shall not * to User during the initial term of this Amendment (‘TRX/User Initial Term”). During the three (3) year period following the TRX/User Initial Term (“Tagalong Period”), TRX shall limit its RESX transaction fee increases to no more than * for those customers that signed contracts with User during the Initial Term of this Amendment (“Customer Initial Term”). The limitation on increases during the Tagalong Period shall only apply to those customers of User with which it enters into a definitive agreement during the TRX/User Initial Term. Custom programming (Including the creation of custom log-in pages, graphic changes, and data bridge programming) is available at * and requires the execution of a custom work order.
The following fees are waived for purposes of this Amendment:
*
*
*
The above stated fees presume * by the GDS for the use of the Software. Should the affected GDSalter its pricing so as to materially increase or decrease TRX’s cost of fulfillment herein, TRX shall have the right to immediately amend the fees commensurate with the change.
Administrator and Technical Training and Certification – TRX agrees to train and certify up to * User personnel per year on the RESX product. Training will take place at the TRX training facilities in Dallas, TX. Any additional training required will be provided at a flat rate of * per employee. All T&E expenses are the responsibility of User.
On-site support is available at a rate of * per TRX employee as requested by User. All T&E expenses are the responsibility of the User.
21
* CONFIDENTIAL TREATMENT REQUESTED
EXHIBIT C
DESIGNATION OF USER REPRESENTATIVES
| Initial Operational Representatives: |
||||||
| Name: | ||||||
| Title: | ||||||
| Office Phone: | ||||||
| Fax: | ||||||
| E-mail Address: | ||||||
| Name: | ||||||
| Title: | ||||||
| Office Phone: | ||||||
| Fax: | ||||||
| E-mail Address: |
| RESX Advisory Representative: |
||||||
| Name: | ||||||
| Title: | ||||||
| Office Phone: | ||||||
| Fax: | ||||||
| E-mail Address: | ||||||
22
EXHIBIT D
MINIMUM TERMS AND CONDITIONS

Agreement for American Express Corporate Travel Online (CTO)
This shaded box will be completed by your American Express Account Manager
Account Manager: Region:
Phone: ( ) - Fax: ( ) -
Implementation Package: Green Gold
Fulfillment: EFC Other
Comments:
All information above must be completed. The information in this section is for internal informational purposes only and does form a part of the Agreement. A separate Implementation Form should be submitted as soon as possible via e-mail to: XXX.XXX.Xxxxxxx@xxxx.xxx. See instructions in CS Infosource. Executed contracts must be sent to Xxxxx Xxxxx, American Express, 000 Xxxxxxxx Xx., Xxxxxxxx, XX 00000-0000. Note: All pricing exceptions need to be approved in advance by Xxxx Xxxxxx (000) 000-0000.
Customer Information:
Full Legal Company Name (“Customer”):
Customer Contact Name:
Street Address:
City: State: Zip Code:
Phone: ( ) - Fax: ( ) -
E-Mail:
Billing Contact Name:
Street Address:
City: State: Zip Code:
Phone: ( ) - Fax: ( ) -
E-Mail:
Form of Payment Corporate Purchasing Card or Credit Card Number: Other:
23
By signing below, the parties represent that they have read this Agreement, consisting of this page; the Terms and Conditions; and the Pricing, Product Configuration, and Implementation Schedule attached hereto as Appendix A, and that the business entity (“Customer”) indicated above and American Express agree to be bound by this Agreement.
| CUSTOMER: |
AMERICAN EXPRESS TRAVEL RELATED | |||||||
| SERVICES |
||||||||
| COMPANY, INC. | ||||||||
| Name: |
Name: |
Xxxx Xxxxxx | ||||||
| Title: |
Title: |
Vice President, American Express Global | ||||||
| Interactive Group |
||||||||
| Signature __________________________________________ |
Signature: | |||||||
| Date: |
Date: |
|||||||
24
| 1. | DESCRIPTION OF SERVICES |
____s American Express Corporate Travel Online (CTO) Agreement (“Agreement”) is between American Express Travel Related Services Company, Inc. (“Company”,” we”, “us” and “our”) and the Customer identified on the first page of this Agreement (“Customer”, “you” and “your”). This Agreement covers your use of the CTO interactive travel-booking product, together with any associated documentation, materials and information (the “Product”). The Product is to be used primarily for the purpose of planning and making reservations for airline tickets, hotel accommodations and car rentals for business travel in the conduct of your own business and you will not redistribute or resell the Product. By signing this Agreement, or by your employees, agents or representatives using the Product, you agree to be bound by the terms and conditions contained herein. This Agreement becomes effective on the Effective Date set forth on the first page of this Agreement. All rights not specifically granted Customer under this Agreement are expressly reserved to us and/or our provider of the Product (“Provider”). Such Provider shall be at all times an intended third party beneficiary to this Agreement. Provider reserves the right, in it sole discretion, to modify, discontinue, add, adapt, or otherwise change any design or specification of the Product and/or policies, procedures, and requirements specified in or related hereto.
| 2. | FEES |
2.1. You agree to pay us fees as set forth in this Agreement and Appendix A, which is attached and incorporated herein, and such other fees as may be agreed-upon between the parties. We may change the Booking or Maintenance Fees upon thirty (30) days’ prior written notice to you. The Implementation Fee is payable to us upon signing of this Agreement by you. Maintenance Fees are payable to us upon the issuance of your first airline ticket using the Product, or within ninety (90) days of the Effective Date, whichever is earlier. Booking Fees will be payable per Transaction, beginning with the first airline ticket issuance, as set forth in Appendix A to this Agreement, which is attached and incorporated herein. Booking Fees do not include fees for fulfillment and _iceting of booked travel using the Product, which will be charged under a separate agreement with us or another travel service provider. You agree to pay for your use of the Product as set forth in this Agreement. Any requested services which we provide, in addition to those specifically set forth in this Agreement, may be subject to additional fees. You agree to pay for all debit memos we receive as a result of your use of the Product, unless such debit memos are solely due to our fault or negligence.
2.2. The parties hereby recognize that the financial terms of this Agreement are based upon certain assumptions about standard travel industry conventions, and about your service requirements. If there is a material change (i) in any rules, orders, laws or regulations, whether by a court of law, a government entity, an airline, the International Airline Travel Agency Network or the Airline Reporting Corporation, or any other applicable governing body, governing the manner in which we or other travel agents may operate, or (ii) in your service configuration, service needs, or the manner in which you use the Product, any of which result in additional fees, losses, costs, surcharges or expenses being imposed on us to perform this Agreement, then upon notice to you, we will have the right, beginning on the date of such material change, to increase the Booking Fee, Maintenance Fee, or other fees (the “Fees”) in an amount as reasonably necessary to compensate us for such additional fees, losses, costs, surcharges or expenses. We will provide you with written notice (the “Notice”) of any such change in the Fees. If upon receipt of such Notice, you do not accept the new Fees, you may terminate this Agreement immediately upon written notice to us within ten (10) business days of receipt of the Notice. Failure to provide written notice of termination within ten (10) business days shall constitute your acceptance of the new Fees.
| 3. | BILLING AND PAYMENT |
If we provide you with traditional travel services under a separate business travel services agreement or other similar agreement (“BTSA”), you will receive a single billing statement (“Statement”) in accordance with the terms and conditions of the BTSA, and payment terms will be as set forth in the BTSA. If you are not a party to a BTSA, you will receive a Statement monthly, setting forth the fees and other charges incurred for that month (“Amount Due”). We will automatically charge the Amount Due to the payment vehicle set forth on the first page
25
of this Agreement. The terms and conditions of said payment vehicle will govern payment of the Amount Due thereunder. If in any monthly billing period your revenue (as calculated in Section 4 below) exceeds all outstanding fees and charges (including Overdue Amount(s)), we will remit to you such net positive balance within forty-five (45) days of the billing date set forth on the Statement.
If for any reason we cannot collect the Amount Due, whether under your BTSA or otherwise, you agree to remit payment of the Amount Due within thirty (30) days of the billing date set forth on the Statement. All charges which remain unpaid after thirty (30) days (“Overdue Amount”) are subject to a monthly delinquency charge equal to the lesser of fifteen dollars ($15.00) or two percent (2%) of the Overdue Amount, subject to applicable law(s).
If we also provide you with E-Fulfillment Services under an EFC Contract between the parties, you will receive a combined Statement for both your use of the Product and the E-Fulfillment services.
| 4. | REVENUE SHARING. |
Commissions, Overrides and other revenue resulting from your use of the Product will only be received and collected on your behalf if fulfillment of your CTO travel reservations is requested by you under the terms and conditions of either (i) your BTSA; or( ii) your separate agreement with us for the provision of E-Fulfillment Services. If you procure fulfillment services from a source other than American Express, we will not receive, apportion or credit revenue to your account.
| 5. | INFORMATION; LIMITED WARRANTY |
You agree that we shall not have any liability whatsoever, for the accuracy, completeness, timeliness, or correct sequencing of the information, or for any decision made or action taken by you in reliance upon such information, the Product, or for interruption of any data, information, or any aspect of the Product. There is no warranty of merchantability, no warranty of fitness for a particular use, and no other warranty of any kind, express or implied, regarding any aspect the Product. We and the Provider shall use reasonable efforts to verify the cause of any errors the Product reported by Customer. Our and Provider’s sole obligation shall be to use reasonable efforts to correct the reported error. The Product is provided “AS IS” without, and we and the Provider make no and hereby disclaim all, warranties and representations, whether oral or written, or express, implied, or statutory, with respect to the use, misuse, or inability to use the Product, or any other products or services provided hereunder, their quality or reliability, or their merchantability, title, non-infringement of third party rights or fitness for a particular purpose.
| 6. | LIMITATIONS OF LIABILITY |
In no event will we be liable to you or anyone else for any consequential, incidental, special, indirect, exemplary or punitive damages, including but not limited to lost profits, lost business, losses and damages that result from inconvenience, delay or loss of use of the Product, even if we have been advised of the possibility of such damages or losses. You agree that our liability arising out of any kind of legal claim in any way connected with the Product will not exceed the total amount of fees you paid to us in connection with your use of the Product. We shall not be liable for any loss or damages resulting from a cause over which we do not have control, including without limitation: (i) any Supplier’s breach of contract, any Supplier’s failure to comply with applicable laws or any Supplier’s intentional, negligent or wrongful actions or omissions; or (ii) any other acts, omissions, negligence or conditions outside of our control, including without limitation, failure of electronic or mechanical equipment or communication lines, telephone or other interconnect problems, unauthorized access, theft, operator errors, severe weather, earthquakes, terrorist activities, social or labor unrest, mechanical or construction failures or difficulties, diseases, international or local laws, climactic conditions and strikes or other labor problems (each a “Force Majeure Event”). “Supplier” means any entity providing travel related services, including, but not limited to air, ground or water transportation, or accommodations, meals, tours, etc. In the event a Force Majeure Event continues unabated for thirty (30) days in such a manner as to prevent full performance of either party’s obligations under this Agreement, either party may terminate this Agreement upon written notice to the other party. We do not handle or process paper tickets, and we shall have no responsibility or liability with regard to
26
your unused electronic tickets and their application toward future travel. This Section 6 shall survive termination of this Agreement.
| 7. | PROPRIETARY INFORMATION |
The information accessible through the Product is protected by copyright. You agree not to reproduce, retransmit, disseminate, sell, distribute, publish, broadcast, circulate or commercially exploit the Product in any manner without our express consent, nor to use the Product for any unlawful purpose or for any purpose contrary to the terms of this Agreement. You agree to comply with reasonable written requests by us to protect the Product and our contractual, statutory and common law rights in the Product.
| 8. | TRADEMARKS AND SERVICE MARKS |
Neither party shall use the name or marks, refer to the identity of the other party in advertising, publicity, promotional marketing material or correspondence, unless the prior written consent of the other party has been obtained, provided, however, that we may use your name in materials containing lists of customers, which we may publish or use for promotional purposes from time to time.
| 9. | CONFIDENTIALITY |
Each party agrees to preserve the confidentiality of all the terms of this Agreement, and any information it has received from the other party in the performance of this Agreement which is not publicly available, provided, however, that we may disclose certain information in connection with our performance of this Agreement and with our billing and collections activities with respect to amounts due hereunder or due to us under other agreements. This provision shall survive the termination of this Agreement.
| 10. | IDENTIFICATION |
You are responsible for ensuring the confidentiality of your corporate ID, and the user ID(s) and password(s) of persons you authorize to use the Product. You will be responsible for all Transactions entered through and under your corporate ID, user ID(s) and password(s), and any such Transactions will be deemed to have been completed by you. You agree to maintain a current list of all persons authorized to use the Product and to notify us of changes to authorized personnel.
| 11. | TERM; TERMINATION |
This Agreement will be for a period of two (2) years from the Effective Date set forth above (“Term”). If we continue to service your account beyond the expiration date and with no new contract in place, we have the right to adjust the Fees retroactive to the expiration date of this Agreement. Either party may terminate this Agreement upon sixty (60) days’ written notice to the other party. We may terminate this Agreement immediately in the event of: (i) unauthorized use of the Product; (ii) breach of this Agreement; (iii) any disruption of our access to the Product; (iv) any materially adverse change that prevents your satisfactory fulfillment of the terms of this Agreement; or (v) termination of the Business Travel Services Agreement between us. Any terms of this Agreement which by their nature extend beyond the expiration or termination of this Agreement shall remain in effect for (3) years from the date of such expiration or termination and shall bind the parties and their legal representatives, successors, heirs, and assigns.
| 12. | NOTICES |
Unless notified otherwise in writing, you will send all notices to:
American Express Travel Related Services Company, Inc.
000 Xxxxxxxx Xx.
Xxxxxxxx, XX 00000-0000
Attn: Xxxxx Xxxxx
27
Unless you notify us otherwise in writing, we will send all notices to the name and address of the Customer Contact set forth on the first page of this Agreement.
| 13. | INDEMNIFICATION |
Each party agrees to indemnify and hold harmless the other party to the extent of any claims, liabilities, losses, damages and expenses (including, without limitation, reasonable attorneys’ fees) asserted against the other party and arising out of the indemnifying party’s negligent performance of, or failure to perform, any of its duties or obligations under this Agreement. This Section 13 shall survive termination of this Agreement.
| 14. | INTERNATIONAL REQUIREMENTS |
You agree to accept full responsibility to ensure that you and your travelers are knowledgeable about and in full compliance with any and all: (i) visa, passport and health documentation requirements; (ii) applicable local and international laws, rules or regulations (collectively the “International Requirements”), regarding any and all international travel booked through the Product. In no event will we have any responsibility for advising you or your travelers of International Requirements and we shall have no liability for your failure to be knowledgeable about or in full compliance with the International Requirements. In addition, only electronic tickets will be issued for international reservations originating outside of the United States. If an electronic ticket cannot be issued for any reason, the Product reservation will be released to the traditional booking office for fulfillment and additional charges may apply.
| 15. | DATA PROTECTION. |
Notwithstanding the Confidentiality provisions set forth in Section 9 hereof, Customer understands and agrees that we will: (i) disclose, exchange and receive information about Customer, Customer’s employees and the American Express Travel services utilized by Customer and Customer’s employees (the “Services”) to computerized reservation systems, airlines and other suppliers of travel and travel-related services, to expense management and __curement management services, and to companies within the American Express group of companies worldwide (including American Express-appointed representatives and licensees) to provision the Product and ancillary services to Customer as contemplated by this Agreement; (ii) disclose information about Customer, Customer’s employees and how Customer and Customer’s employees use the Product to Customer’s bank, the payment systems organizations selected by Customer, or Company’s bank, to permit the invoicing of and payment for the Services; (iii) use, process and analyze information about how Customer and Customer’s employees use the Product to develop reports and to enable us to maintain effective travel, expense, and procurement policies and procedures (the information used to develop these reports may be obtained from specified sources such as computerized reservation systems, airlines and other suppliers of travel and travel-related services, expense management and procurement management services and from our appointed representatives, licensees, agents and suppliers world-wide); (iv) use advanced technology and well-defined employee practices to help ensure that Customer and its employees’ information is processed promptly, accurately and in confidence; (v) retain such information only for so long as is appropriate for the purposes of this Agreement or as required by applicable law; and (vi) American Express will undertake all the above both within and outside the European Union. This will include processing Customer and Customer’s employees’ information in the United States of America and other countries outside the European Union in which data protection laws are not as comprehensive as in the European Union. However, we will endeavor to take appropriate steps to ensure that Customer and Customer’s employees’ information will have the same protection in the United States of America and the other countries outside the European Union as such information would have within the European Union. Customer shall be responsible for individually notifying Customer’s employees who use the Product that we will hold, process and disclose information about them and how they use the Product as described above. At an employee’s request, we will use their best efforts to tell such employee what we do with their personal information. If they ask, we will also __vide them with whatever information we hold about them. Employee requests and questions should be sent, in writing, to us as set forth in Section 10 herein. There may be a charge for this, as permitted by law. You shall also inform your employees that if they believe we hold any information about them that is incorrect or incomplete,
28
they should write to us at the above address. Any information that is found incorrect or incomplete upon receipt of written notice thereof will be corrected promptly.
| 16. | MISCELLANEOUS |
You may not assign this Agreement. We may assign this Agreement to our parent, subsidiaries or affiliates. Failure to enforce any term or condition of this Agreement shall not be a waiver of the right to later enforce such term or condition or any other term or condition of this Agreement. We have the right to change this Agreement at anytime. We will notify you of any change in writing at least ten (10) days in advance. If the changes are unacceptable to you, you may terminate this Agreement as described in Section 11 above. This Agreement is the entire agreement with respect to the subject matter hereof and supersedes any previous agreement with respect to your use of the Product. This Agreement will is governed by the laws of the State of New York, without reference to the choice of law doctrine of such state.
29
APPENDIX A
PRICING, PRODUCT CONFIGURATION AND IMPLEMENTATION SCHEDULE
1.
2. Monthly Maintenance* - Your monthly maintenance package must correspond to the implementation package selected.
| 3. 4. Green |
5. 6. Gold | |||
| Monthly Maintenance fee |
X |
Maintenance fees, in general, reflect the allocation of hardware and support required to run and maintain databases and servers and correspond to the complexity of your implementation package. Your maintenance fee refers primarily to the system overall, not individual company servicing.
| Booking Fee: | Fulfillment Fee: Fulfillment Fees are charged pursuant to your separate agreement for such services, as follows: | |
| $ (flat fee per Passenger Name Record (PNR) created). This fee is charged independent of all other fulfillment and transaction fees. |
E-Fulfillment Center (“EFC”): Client will be utilizing the Centralized Fulfillment Center in Miami. Please refer to your EFC Agreement for the fee. | |
|
Off-line Fulfillment: Client will not be utilizing the Centralized Fulfillment Center. Please refer to your Business Travel Services Agreement (if an American Express travel services client) or other similar agreement (if not an American Express travel services client). |
30
| 8 Package Eligibility Specifications |
Green |
Gold | ||
| Travel operations locations |
X | x | ||
| Policy groups |
X | x | ||
| Customized PNR fields |
X | x | ||
| Airline contracts |
X | x | ||
| Negotiated hotel properties |
X | x |
Note: If any of the individual package eligibility specifications are exceeded, the customer will be billed accordance with the American Express fee schedule then in effect for such additional services
| Mass Enrollment Procedures |
||||
| Client provides data file for travelers to be enrolled (e-mail address, first, middle, and last name) |
X | x | ||
| Responsibility for sign-ins and passwords |
X | x | ||
| Amex performs subsequent enrollments |
X | x | ||
| Amex provides Global Distribution System (GDS) extract/merge |
X | x |
31
9.
10. Implementation – Your implementation package includes only the services and materials listed below __ period of up to ninety (90) days from signing of this Agreement.
| 11. 12. Green |
13. 14. Gold | |||
| Implementation fee |
X | x | ||
| Review travel policy & operations for CTO configuration |
X | x | ||
| Travel manager orientation and implementation support |
X | x | ||
| TRAVELER ORIENTATION MATERIALS |
X | x | ||
| Traveler orientation sessions |
x | x | ||
| Advanced Product Features | ||||
| 15. |
X | x | ||
| 16. SuperSite** |
||||
Additional Services: Any services requested above and beyond the scope of the selected implementation package will be estimated by the implementation team in a work order and submitted for client approval prior to rendering of such additional services. Any change in the client’s service or product configuration or extract of the client’s database will be subject to such additional charges.
| * | If you require an Extranet connection, you will be charged an additional monthly communications fee, the amount to be determined after technical evaluation. Technical Support (Levels 1 and 2): For those with decentralized E-Fulfillment, technical helpdesk support for end-users (Level 1) is the responsibility of the customer through its IT helpdesk. For centralized E-Fulfillment users, technical helpdesk support is through the Navigation Center HelpDesk at the Miami E-Fulfillment Center. Amex will provide technical helpdesk support to authorized program administrators and to the customer’s IT helpdesk personnel only (Level 2). The customer must provide to Amex a list of program |
32
| administrators and other personnel authorized to contact the Amex support staff for Xxxxx 0 assistance. Maintenance fees cover Level 2 helpdesk technical support, but do not cover Level 1 end-user helpdesk technical support. Any end-user support requests made directly to the Amex Level 2 support staff will result in a charge to the customer for the applicable fee. |
33
INFORMATION SECURITY
Information Protection Requirements
Notwithstanding anything to the contrary contained in the Amendment to which this Exhibit E is attached and incorporated into, and in addition to and not in lieu of other provisions in the Amendment governing the treatment of AXP Data (as defined below) by TRX (referred to in this Exhibit E as “Vendor”), Vendor agrees to comply with all of the provisions of this Exhibit E and to cause all Vendor employees and Vendor agents, representatives, or subcontractors, and their respective employees, or any other party to whom Vendor may provide access to or disclose AXP Data (collectively and individually, “Vendor Disclosees”) to comply with all of the provisions of this Exhibit E.
“AXP Data” means * .
| 1) | Vendor warrants that, where required by applicable law, Vendor’s registrations with relevant regulatory bodies are current and adequate for the services to be supplied under the Amendment. |
| 2) | General. |
| a) | All AXP Data remains at all times the sole property of AXP. |
| b) | Vendor agrees to implement appropriate and reasonable measures designed to ensure the security and confidentiality of AXP Data, to protect AXP Data against any anticipated threats or hazards to the security or integrity of AXP Data, and to protect against unauthorized access to, or use of, AXP Data. |
| c) | Vendor must not * . |
| d) | Except as required for backup and archival purposes, for a period not to exceed * , Vendor must not retain all or any portion of the AXP Data, in any manner whatsoever, nor permit any parent, subsidiary, affiliate, third party, agent, employee or contractor, or their respective agents or employees to retain any such information, beyond the completion of performance of Vendor’s obligations under the Amendment. |
| e) | Vendor must not use the AXP Data for any purpose other than the purpose for which AXP Data was provided to Vendor as set forth in the Amendment and must cause all Vendor employees, agents, representatives, or any other party to whom Vendor may provide access to or disclose AXP Data to limit the use of AXP Data to that purpose. |
34
* CONFIDENTIAL TREATMENT REQUESTED
| f) | Vendor agrees to use commercially reasonable efforts to comply with all applicable AXP security policy standards and procedures as determined by AXP and provided to Vendor. |
| g) | Vendor must cause each Vendor Disclosee who is granted access to AXP Data to sign the Confidentiality and Workstation Rules Agreement attached hereto as Annex 1 or a document with substantially similar terms and conditions, and Vendor must cause each such Vendor Disclosee to comply with its terms. |
| 3) | Transfer to Third Parties. |
| a) | Vendor must not disclose AXP Data to any subcontractor, service provider, or any other third party (“Third Party”) without the prior approval of AXP unless such transfer of AXP Data to a Third Party by Vendor is for the sole purpose of fulfilling Vendor’s obligations under the Amendment. |
| b) | Vendor must not assign, transfer, or otherwise disclose AXP Data to a Third Party prior to causing the Third Party to execute a binding document committing the Third Party to comply with the Information Protection Requirements set forth in this Exhibit E. |
| 4) | Indemnity. |
| a) | Vendor will indemnify AXP for any loss or misuse of AXP Data by Vendor or its employees or by any Third Party to which Vendor discloses AXP Data. |
| b) | In the event of any actual or threatened unauthorized use or disclosure of AXP Data by Vendor’s employees or the employees of any Third Party to which Vendor has disclosed AXP Data, Vendor must enforce for AXP’s benefit through litigation, if necessary, all rights provided under law to compensate AXP for any damages arising out of such disclosure and to prevent any actual or further unauthorized use or disclosure of AXP Data. |
| 5) | Physical Security Controls. Vendor must document and maintain adequate: |
| a) | Physical security controls over all vendor facilities where AXP Data is filed or stored. * . |
| b) | * . |
| c) | Security and environmental controls over * , which will be used in conjunction with AXP Data, including restricting access to only approved staff. |
| 6) | Data Security Controls. Vendor must document and maintain adequate: |
| a) | Data security controls, such as but not limited to * . Vendor must ensure at each site that appropriate data controls are |
35
* CONFIDENTIAL TREATMENT REQUESTED
| implemented and that no shared environments exist with other businesses for all WANs, LANs, network connections, dial-up connections, DASD, distributed systems, or any other computer systems. |
| b) | Retention processes and policies for all security data events (i.e., reports) in accordance with legal and regulatory requirements. Examples include: * |
| c) | Controls in configuring and operating voice systems, especially as regards * . |
| 7) | Disaster Recovery. |
| a) | Vendor must have a documented, tested disaster recovery plan upon written request and must provide documentation of its disaster recovery plan to AXP for review and approval by AXP. Vendor must notify AXP of any revisions made to Vendor’s disaster recovery plan. |
| b) | Vendor’s disaster recovery plan must include * . |
| c) | Vendor’s disaster recovery plan must be designed to recover business operations from disaster. |
| d) | With respect to Sections 7(d), 7(e), and 7(f), at AXP’s expense, and Vendor’s written agreement, Vendor must ensure all disaster recovery plans are tested at least once each year. Upon written request, Vendor must provide to AXP the plans for all disaster recovery tests and documentation of disaster recovery test results. |
| e) | Vendor agrees that AXP or a designated third party may attend and/or review recovery plan testing and view test results. |
| f) | Vendor agrees to allow AXP to schedule integrated business recovery exercises with the Vendor upon request from AXP. |
| g) | Vendor must ensure that all reasonable precautions are taken to prevent and mitigate any disaster that may affect Vendor’s ability to provide services under the Amendment. |
| h) | Upon the occurrence of a disaster at any of the Vendor locations involved in the provision of services to AXP or where AXP Data is stored or utilized by Vendor, Vendor must immediately implement the disaster recovery plan and notify AXP of such implementation and any external dependencies necessary to implement the plan. |
| i) | Upon written request and within a mutually agreed timeframe, Vendor must provide to AXP a post-incident report that documents the implementation and efficacy of Vendor’s disaster recovery plan after the occurrence of a disaster at any of the Vendor locations involved in the provision of services to AXP or where AXP Data is stored or utilized by Vendor. |
| 8) | Employees. |
36
* CONFIDENTIAL TREATMENT REQUESTED
| a) | Vendor must, in accordance with applicable law, perform background checks on all employees assigned to perform Vendor’s obligations under the Amendment. |
| b) | Vendor’s policies must require its employees to report suspected violations of the Information Protection Requirements set forth in this Exhibit E and suspected violations of Vendor’s data security policies to Vendor management for investigation and action. |
| c) | Vendor must cooperate fully with AXP in any investigations of possible fraudulent or unauthorized use or access of AXP Data by Vendor’s employees. |
| d) | Vendor must implement and document consequence management policies for violations of the Information Protection Requirements set forth in this Exhibit E and for violations of Vendor’s data security policies. |
| 9) | Audits and Inspections. |
| a) | Upon written request, Vendor must document and provide to AXP copies of all internal security policies and standards relevant to performance hereunder (including escalation procedures for non-compliance) for AXP review. |
| b) | Vendor must allow scheduled and unscheduled on-site inspections by AXP with reasonable prior written notice during regular business hours. |
| c) | Vendor shall use commercially reasonable efforts to comply with all reasonable recommendations from AXP that result from such inspections to meet these Information Protection Requirements. Vendor must respond in writing within a mutually agreed timeframe no less than thirty (30) days to all recommendations that result from on-site inspections by AXP. |
| d) | Upon written request, Vendor must provide to AXP a copy of the most recent third party data processing audit or review, as conducted by the Vendor’s external auditors relevant to Vendor’s performance hereunder. In addition, Vendor must provide to AXP copies of any related audits that include data processing activities within their scope from Vendor’s internal auditors. |
| 10) | Right to Monitor Data. |
| a) | * . |
| b) | * . |
| 11) | Vendor Employees Access |
| a) | * . |
| b) | Vendor must ensure that all of its employees who are users of any AXP system will attend Security Awareness training, and will be fully informed (at least annually) of, and monitored for adherence to, these Information Protection Requirements. |
37
* CONFIDENTIAL TREATMENT REQUESTED
| 12) | Security Administration |
| a) | * . |
| b) | * . |
| c) | * . |
| d) | * . |
| 13) | Account Access. Vendor must cause Vendor Disclosees to access, make maintenance changes to, or perform financial adjustments only on those AXP accounts as required by their job responsibilities. In addition, Vendor must cause Vendor Disclosees to not access: |
| a) | * . |
| b) | * . |
| c) | * . |
| d) | * . |
| 14) | Access Management. Vendor must ensure that user IDs and passwords for AXP systems will be controlled as follows: |
| a) | * . |
| b) | * . |
| c) | * . |
| d) | * . |
| e) | * . |
| f) | Vendor must enforce the principle of segregation of duties. |
| 15) | Right to Monitor Access. Vendor agrees that all access to AXP systems * . |
| 16) | Workstation Controls. Vendor must ensure all workstations which allow access to AXP Data are controlled. All software used on any workstation must be properly licensed and |
38
* CONFIDENTIAL TREATMENT REQUESTED
| used in accordance with the applicable license agreement. All software used must be approved by AXP. All such workstations must be: |
| a) | * . |
| b) | * . |
| c) | * . |
| d) | * . |
| 17) | Activity Log; * . |
| 18) | Systems Security. |
| a) | Vendor must document and maintain adequate: |
| i. | * . |
| ii. | * . |
| b) | Vendor must perform maintenance access to production servers over a protected, dedicated network between Vendor’s corporate offices and the production systems. Vendor must not perform maintenance access to production servers over the Internet. |
| c) | * . |
| 19) | Operations Procedures |
| a) | * . |
| b) | * . |
| c) | * : |
| i. | * . |
| ii. | * . |
| iii. | * . |
| 20) | Data Separation. * . |
39
* CONFIDENTIAL TREATMENT REQUESTED
| 21) | Control Datastores. Any system which processes financial data must have * . |
| 22) | Remote Access Authentication. All remote access, whether to the production network (for technical operations staff), or to the corporate network (by remote travelers), must be * . |
| 23) | Encryption. |
| a) | * . |
| b) | * . |
| c) | Vendor hashes passwords with a proprietary and confidential algorithm. |
| d) | All database data must be encrypted prior to backup. |
| e) | Key management must occur in hardware devices. |
| f) | * . |
| g) | Vendor must allow the review of cryptographic controls and processes by AXP. |
| 24) | Development Separation. |
| a) | Procedures must exist to separate the application development process from the data it operates on. |
| b) | Development staff must not have access to the production servers; operations staff must not generally have access to the development source. |
| c) | Access controls on various servers must be used to ensure that these policies are adhered to. |
| 25) | Data used in development and test systems must not contain direct copies of production data under any circumstances. |
| 26) | Internet Security |
| b) | Vendor must document and maintain adequate: |
| i. | * . |
| ii. | * . |
| iii. | * . |
40
* CONFIDENTIAL TREATMENT REQUESTED
| c) | All systems must have provision to ensure that AXP Data or any other data cannot be downloaded by an unauthorized person(s) who has successfully gained control of a web server. This should occur through use of three tier architectures (web server tier, application server tier and database server tier). |
| 27) | Application Security. * . |
| 28) | Customer Authentication. |
| a) | * . |
| b) | * . |
| c) | * . |
| d) | * . |
| e) | * . |
| f) | * . |
| 29) | Internet Tracking and Reporting |
In connection with any and all work that Vendor does on behalf of AXP, Vendor agrees that it will not collect any personally identifiable information from any AXP on-line users/customers. Further, Vendor agrees to obtain the prior written approval of AXP before using any “tracking and reporting” technologies on Web pages that contain AXP branding, including, but not limited to, technologies designed to collect, track, store or classify user data, movements or preferences.
| 30) | Provisions Applicable to International Transfers of Personal Data. |
The provisions of this Section 30 apply to AXP Data that is transmitted across any international boundary.
The Parties will each comply with their respective obligations under any applicable laws relating to the collection, use, processing, protection or disclosure of data relating to individuals or corporations, including Personal Data (as defined below) during the provision of the Services (including European Directive 95/46/EC on the protection of individuals with regard to the processing of personal data and on the free movement of such data, and any legislation implementing such article, and any legislation implementing the same in the relevant state (collectively, the “Directive”)) (collectively, “Data Protection Laws”). Neither Party will do any act that puts the other Party in breach of its obligations under the Data Protection Laws and nothing in this Agreement will be deemed to prevent any Party from taking the steps it reasonably deems necessary to comply with the Data Protection Laws.
41
* CONFIDENTIAL TREATMENT REQUESTED
| a) | The Parties acknowledge that: |
| 1) | * ; |
| 2) | * ; |
| 3) | * |
| 4) | * |
| 5) | * . |
| b) | Vendor will, and will cause any Vendor Disclosees to, in a manner that conforms to any time-scales set out in the Directive, and, in any event, as soon as reasonably practicable, comply with any written request by AXP to: |
| 1) | * ; |
| 2) | * ; |
| 3) | * ; |
| 4) | * |
| 5) | * . |
| c) | Vendor will not without AXP’s prior written authorization: |
| 1) | * ; |
| 2) | * |
| 3) | * . |
| d) | Vendor will: |
42
* CONFIDENTIAL TREATMENT REQUESTED
| 1) | * ; |
| 2) | * . |
| e) | Vendor will indemnify AXP for any breach by Vendor or any Vendor Disclosee of its obligations with respect to data protection under the Amendment. |
| f) | Vendor acknowledges that to the extent it is obliged to comply with Article 17 of the Directive in respect of AXP Personal Data, it will comply with such Article 17 including without limitation the following obligations: |
| 1) | taking appropriate technical and organizational security measures in accordance with the requirements of the Agreement to safeguard against unauthorized and unlawful processing of AXP Personal Data and against accidental loss or destruction of, or damage to, AXP Personal Data; |
| 2) | only processing AXP Personal Data in accordance with written instructions given by AXP, including as set forth in the Amendment; |
| 3) | taking reasonable steps to ensure the reliability of those Vendor personnel and Vendor Disclosees that have access to AXP Personal Data; and |
| 4) | ensuring that all of the Vendor personnel and Vendor Disclosees involved in processing AXP Personal Data have undergone reasonably adequate training in the care and handling of AXP Personal Data. |
43
* CONFIDENTIAL TREATMENT REQUESTED
Annex 1
Confidentiality and Workstation Rules Agreement
The individual specified below (“you” or “your”), in connection with work performed for the company specified below (“Company”) may have access to trade secrets, confidential information, files, records and forms (collectively “Confidential Information”) of American Express Travel Related Services, Inc. and its affiliates (collectively, “American Express”). Confidential Information includes, but is not limited to, any information relating to American Express Card member accounts (“Accounts”), American Express organizational structure, marketing philosophy and objectives, project plans, data models, strategy and vision statements, business initiatives, business requirements, systems design, methodologies, processes, competitive advantages and disadvantages, financial results, product features, systems, operations, technology, customer lists, customer account information, product development, advertising or sales programs and any other information which would give American Express an opportunity to obtain an advantage over its competitors or which American Express is ethically obligated to protect from unauthorized sources. None of such information shall be deemed to be in the public domain.
American Express desires to protect its Confidential Information and therefore requires that you agree, as a condition of your performing services (“Services”) pursuant to American Express’ agreement with Company, to safeguard all Confidential Information and not to reveal Confidential Information to any third party (including, without limitation, at conferences, seminars, meetings of professional organizations or by publication in journals or granting of interviews to journalists and other members of the news media) or use Confidential Information for your own benefit or the benefit of any third party, except to the extent necessarily required for your performance of Services.
You agree not to discuss Confidential Information in public places.
You agree that any work product produced or developed by you in the performance of your Services shall constitute Confidential Information subject to this Agreement and such work product is, and shall remain, the property of American Express.
In connection with your use of American Express’ computer workstations and your access to American Express MIS systems, in addition to all other provisions of this Agreement, you agree that:
| • | You will not access your own Account for any reason; |
| • | You will not access another employee’s Account if you have personal knowledge that the account holder is an employee; |
| • | You will not access any Account held by anyone you know outside of work; |
| • | You will not access any Account that you are not required to access as part of your performance of the Services. |
You will sign off when you leave your workstation and sign back on when you return, including, but not limited to, time away from your desk for breaks, lunch, meetings, etc.
You will not give your password to any person and you are not to use another person’s password or identification number. Your password identifies you to the system. The computer system tracks all entries that are made by the person who makes them. If your password is used by anyone in a manner that results in errors or fraud, you would be held accountable for the errors or fraud.
All terminals are subject to monitoring and terminal monitoring may occur simultaneously with telephone monitoring. In addition, you should understand that all transactions in the system are recorded by the computer. Printouts listing all transactions by a personal identification number and password are monitored on a regular basis.
44
These rules are extremely important. Any employee who willfully disregards these rules and regulations is subject to discipline, up to and including discharge from employment.
You also agree to help safeguard American Express customers’ expectations of privacy by exercising diligence and care in the handling of Confidential Information relating to them.
By signing below, you indicate that you understand the above terms and that, as a condition of performing Services, you agree to adhere to them.
| COMPANY: |
||||||||
| Full Legal Name |
Your Name (print) | Date | ||||||
| Your Signature (Sign Here) |
||||||||
45
EXHIBIT F
Purposely left Blank
46
EXHIBIT G
DELIVERABLE ENCRYPTION INFORMATION
| 1. | Encryption Information |
Identify each hardware and software component of each of the Products having encryption capability by its respective unbundled part number and level of encryption.
| Product Component(s) |
Unbundled Part Number |
Level of Encryption(e.g. 40 bit, 56 bit, 128 bit etc.) |
Type (e.g. DES, Blowfish RC2, CAST etc.) | |||
| * | * | * | * |
| 2. | Export License Information |
Indicate in connection with each part number for each component the Commodity Classification or Export License or License Exception granted – for example, “Mass Market License Exception, TSU” Or “License Exception, ENC” by the USGOV, providing in each case the Export Control Classification Number (and Paragraph, if applicable), — and the date of the USGOV finding in each case.
47
* CONFIDENTIAL TREATMENT REQUESTED
| Product Component(s) |
Unbundled Part Number |
Export Control Classification Card |
Did you Classification? |
Did you Receive License? |
Did you Receive ENC? Provide |
USDOC/ Date of | ||||||
| * | * | * | * | * | * | |||||||
| 3. | Licensor’s Contact |
Identify Licensor’s export manager or contact responsible for filing or obtaining the export licenses or license exceptions for the Products.
| • | Not Applicable. This is a 3rd party component purchased from Nortel Networks |
| Name: |
| Address: |
| Telephone Number: |
48
* CONFIDENTIAL TREATMENT REQUESTED
| 4. | Import License Information |
Indicate in connection with each part number for each component whether any import license was applied for, granted or rejected, the name of the country granting the license, and whether or not the license extends to Licensor’s customers.
Not Applicable
| Product |
Unbundled |
Import |
Import License/ |
License/ |
Indicate if |
Country Granting | ||||||
Identify your Company’s Web Site, if any, where information can be found relating to the technical specifications and export or import of the Products.
Not Applicable
49
The RESX online booking engine is a fully-automated online travel information and reservation system that gives travelers quick and easy access to the information and tools they need to complete their own travel itineraries using a desktop PC or laptop.
Air, hotel, rail, and car rental bookings can be completed with a simple point and click reservation process. RESX allows travelers to build trip templates that actually speeds the booking process by reducing the amount of steps required to complete a reservation. Requiring only a basic Web browser, users can access the system anytime anyplace they have Internet access and a computer.
The RESX design is flexible and allows for customization and corporate branding. RESX provides group, as well as individual traveler-level administration for quick company-wide policy updates. Built on the .NET technology platform RESX has an open-architecture that allows for fast and simple integration to expense management systems and back office reconciliation systems.
The RESX booking engine was developed for the travel agency distribution model and all administration capabilities are intuitive to the user. With proper training distributors of the product can easily provide all first level support and customer service for their clients.
50
